- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Evolving into the Manager Role
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for New managers wanting to become skilled in their management roles will benefit from this course Overview Describe the roles that a manager has in an organization Identify and nurture talent in your team Build a management vision for success Create strategies to motivate and empower your team Combine leadership qualities and influence skills to motivate your team Plan and manage effective meetings In this course, students will learn how to confidently acquire and build these skills through relevant discussions, team and individual activities. Private classes on this topic are available. We can address your organization?s issues, time constraints, and save you money, too. Contact us to find out how. 1. The Manager\'s Role Distinguishing a Manager\'s Role from Function Understanding Interpersonal, Informational, and Decision Roles 2. Building a Shared Vision Defining a Shared Vision Building a Strong Vision Creating and Communicating a Vision Statement Identifying Benefits of Your Vision 3. Leadership and Influence Identifying the Characteristics and Qualities of a Leader Modeling the Way and Enabling Others to Act Encouraging Your Inner Innovator and Mastering the Art of Persuasion Creating Mutual Respect Effectively Communicating and Reasoning with Others 4. Nurturing Talent Calibrating Talent Finding and Nurturing the Attributes that Meet Your Requirements Articulating Culture and Hiring for a Cultural Fit Looking to the Future - Developing and Executing a Plan Succession Planning Creating and Fostering Employee Engagement Coaching, Training, and Development 5. Delegation and Empowerment Working with Workgroups and Teams Delegating Progress Tracking and Reviewing Results 6. Building a Better Meeting Planning and Preparing a Meeting Identifying Proper Participants Creating an Agenda Evaluating the Use of Technology Additional course details: Nexus Humans Evolving into the Manager Role training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Evolving into the Manager Role course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

PERSON CENTRED REHABILITATION
By Inclusive Solutions
Person centred rehabilitation is designed to create a better life for an individual by the provision of an intense input designed to being about social change. This usually entails a series of visits focused on getting the person out and about to increase confidence, social skills and presence in their local community and to pursue goals and dreams. Usually, the work is carried out under the close clinical supervision of a practicing psychologist. Course Category Inclusion Person Centred Planning Visioning and Problem Solving Peer Support Description Person Centred Rehabilitation Person centred rehabilitation is designed to create a better life for an individual by the provision of an intense input designed to being about social change. This usually entails a series of visits focused on getting the person out and about to increase confidence, social skills and presence in their local community and to pursue goals and dreams. Usually, the work is carried out under the close clinical supervision of a practicing psychologist. PERSON CENTRED PLANNING A Person Centred Planning event would be carried out using the PATH or MAP process – majoring on dreams and goal setting leading to precise action planning. Facilitators would carry out the PATH or other person centred process. A large graphic will be one of the outcomes of the meetings this is a great visual record and a shared memory of the event. This will also inform the priorities for the later follow up inclusion facilitation work. Following the PATH event a ‘scoping report’ is created outlining what Inclusion Facilitation could offer and highlighting what dreams and goals the individual has. INCLUSION FACILITATION The PATH is also provides a good opportunity for the Facilitator to meet the focus person in a comfortable positive environment. Agreed visits from the Inclusion Facilitator are then carried out over a 3 month period. After this intensive input the Inclusion Facilitator will hand over to the existing family, carers and PA team to carry on where he or she has left off. This transition time is planned from the outset. An experienced psychologist needs to be there to support the facilitator at all times and will guide all work done by the inclusion facilitator. Is this just Support work? No! This is proactive engagement – doing whatever is required. This is not passively or reactively providing what is asked for – we are actively pursuing a good life for the individual. The work is built on careful research around a person’s interests and what opportunities exist locally There is community mapping There is work to tackle an individual’s own resistance and reluctance to engage more socially There is a need to engage with people in social settings that the individual attends to build bridges and connections – we are bridge builders You will need to build circles around a person There is a need to create the conditions in which friendships can flourish There is a need for direct psychological supervision and support throughout This work is short term and intense. The facilitator’s main aims will vary depending on the dreams and goals of the focus person. The basic aim of the inclusion facilitator is to better the focus person’s quality of life. Learning Objectives 1 To create a better life for the Individual. 2 Give Individual and family a clear vision of a good life and to support first steps towards this 3 To maximise individuals inclusion and connection with the wider community. 4 To help with friendship, social connection and education 5 To increase confidence, social skills and presence in their local community and to pursue goals and dreams. Who Is It For? Anyone who is involved in the rehabilitation of children or adults who have become disabled through accident or trauma and who is committed to helping them get their life back on track. Course Content Understanding ordinary needs – the dimensions of social inclusion Pursuing the dreams and goals of the individual Improving social skills Community Mapping Being comfortable in social environments Developing conversational skills Having a positive mindset Staying physically active Building relationships Help in meeting new people Create natural circles of support Creating a community circle Having positive body language Employment of support staff Pursuing personal interests If you like this you will almost certainly enjoy: Person Centred Planning using PATH and MAPs

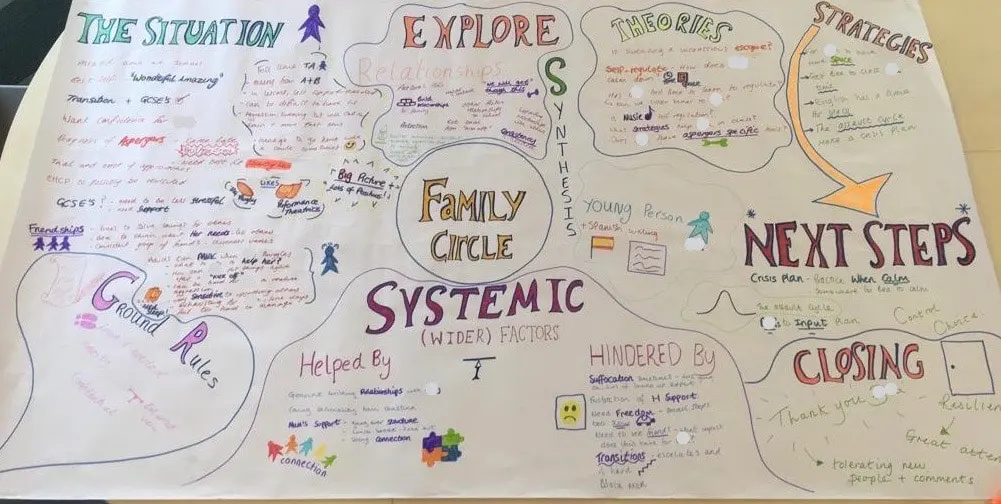
FAMILY CIRCLES
By Inclusive Solutions
Click to read more about this training, in which we demonstrate a live problem solving approach which is based on the active participation of family members. Course Category Inclusion Parents and Carers Behaviour and relationships Problem Solving Description In this training we demonstrate a live problem solving approach which is based on the active participation of family members. ‘Family Circles’ is an evolving new approach to problem solving with families and is based on our years of family work and the development and use of the Circle of Adults process. Inspired by our own Parent Solutions work and the Circle of Adults process as well as Family Group Conferencing and other Restorative Interventions we bring you Family Circles. Essentially the approach involves gathering a family together for a process that is facilitated but majors on the family members offering each other their wisdom and ideas. The approach is capacity focused, person centred approach to working with families rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for or doing things to families. This training can be modelled with a group of professionals or better still with a family. In our work with families we develop the importance of naming stories or theories and seeking linkages and synthesis between what is found out and explored about the family situation and its history. We like participants to sit with the uncertainty, to reflect on the question ‘why’ but without judgement of each other. Deeper reflections may span a whole range of perspectives from ‘within person’ considerations, to situational or systemic possibilities. Health or emotional issues can be reflected on alongside organisational or transactional aspects of what is going on for the family. The better the shared understanding the better the strategy or actions which emerge from these meetings. Quality hypotheses with a close fit to reality lead to more effective implementation in the real world. We encourage ‘loose’ thinking, a search for connections, deeper listening, an ‘open mind’, speculation and exploration without moral judgements. From this stance self-reflection as well as reflection on the situation can produce remarkable insights. The quality of theories or new stories generated is directly influenced by family members’ experiences and the models of learning, behaviour and emotion, systems, educational development, change and so on that they have been exposed to. Learning Objectives To provide opportunities for: Shared problem solving in a safe exploratory climate in which the family will find its own solutions. Individuals to reflect on their own actions and strategies An exploration of whole-family processes and their impact Emotional support and shared understandings of issues at a child, parent, family, school and community level. Feed back to each other on issues, ideas and strategies that are agreed to be worth sharing with them. Who Is It For? Anyone interested in working with families in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. Social Care teams School staff Community organisers Educational Psychologists Course Content True family empowerment Deepening shared stories and understandings Facilitating groups Problem solving process Handling family group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Process: Family members are welcomed: Introductions are carried out, ground rules and aims clarified whilst coffee is drunk. A recap from the last session is carried out: To follow up developments and reflections after the last meeting. One issue is selected for the main focus Issue presentation: The family member who raised the concern is asked questions to tell the ‘story’ of the issue or problem. Additional questions/information from the group about the problem are gathered: Ground rules may need to be observed carefully here. Individual participants need to be kept focused and prevented from leaping to premature conclusions or to making ‘helpful’ suggestions about strategy. Relationship aspects to the problem are explored. Metaphors and analogies are invited. How would a fly on the wall see your relationship? If you were alone together on a desert island, what would it be like? Impact of previous relationships/spillage from one relationship to another are explored. Eg what situation they are reminded of? For instance, does this situation remind you of any of those angry but helpless feelings you had with your other son when he was an adolescent? This provides opportunities to reflect on how emotions rub off on other people. The parent feels really frustrated, and on reflection we can see that so does the child System/Organisation factors (Family system/school and community systems and so on): What aspects help or hinder the problem? For instance, does the pastoral system of the local school provide space, or time and skilled personnel able to counsel this young person and work actively with their parents? Synthesis. At this stage the Graphic facilitator summarises what they have heard. They then go on to describe linkages and patterns in what they have heard. This can be very powerful. The person doing the graphic work has been able to listen throughout the presentation process and will have been struck by strong messages, emotions and images as they have arisen. The story and meaning of what is happening in the situation may become a little clearer at this point. Typical links may be ‘mirrored emotions’ strong themes such as loss and separation issues, or repeated processes such as actions triggering rejection. This step provides an excellent grounding for the next process of deepening understanding. What alternative strategies/interventions are open to be used? Brainstormed and recorded. ’Either/ors’ need to be avoided at this time also. This needs to be a shared session in which the family member who is presenting the concern contributes as much as anyone. Care is needed to ensure that this person is not overloaded with other people’s strategies. The final selection of strategy or strategies from the brainstormed list is the problem presenter’s choice. Strategies might include: a special time for the young person, a meeting with the child’s parents to explore how she is being managed at home and to share tactics, a home-school diary, counselling, or an agreed action plan that all are aware of, agreed sanctions and rewards and so forth. Strategies may productively involve processes of restitution and restoration, when ‘sorry’ is not enough. Making it right, rather than punishments or rewards, may then becomes the focus. First Steps. The problem presenter is finally asked to agree one or two first steps which they can carry out over the next 3-7 days. It can help to assign a ‘coach’ who will check in with them to ensure they have carried out the action they have named. This is a time to be very specific. Steps should be small and achievable. The person is just ‘making a start’. A phone call, or making an agreement with a key other person not present at the meeting would be ideal examples. Final reflections. Sometimes referred to as a ‘round of words’ help with closure for all involved. Reflections are on the process not the problem. In large families this is best done standing in a circle. In smaller groups all can remain sitting. Passing around a ‘listening stick’ or something similar such as a stone or light heighten the significance of the process ending and improve listening. Finally the problem presenter is handed the ‘Graphic’ this is their record of the meeting and can be rolled and presented ceremoniously by the facilitators for maximum effect! If you liked this course you may well like: Parent Solutions
Architecting on AWS
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for solutions architects, solution-design engineers, developers seeking an understanding of AWS architecting and individuals seeking the AWS Solutions Architect-Associate certification. Overview Identify AWS architecting basic practices. Explore using the AWS management tools: The AWS Console, Command Line Interface (CLI), and CloudFormation in a lab environment. Examine the enforcement of accounts security using policies. Identify the elements that build an elastic, secure, virtual network that includes private and public subnets. Practice building an AWS core networking infrastructure. Determine strategies for a layered security approach to Virtual Private Cloud (VPC) subnets. Identify strategies to select the appropriate compute resources based on business use-cases. Practice building a VPC and adding an Elastic Cloud Compute (EC2) instance in a lab environment. Practice installing an Amazon Relational Database Service (RDS) instance and an Application Load Balancer (ALB) in the VPC you created. Compare and contrast AWS storage products and services, based on business scenarios. Compare and contrast the different types of AWS database services based on business needs. Practice building a highly available, auto-scaling database layer in a lab. Explore the business value of AWS monitoring solutions. Identify the role of monitoring, event driven load balancing, and auto scaling responses, based on usage and needs. Identify and discuss AWS automation tools that will help you build, maintain and evolve your infrastructure. Discuss network peering, VPC endpoints, gateway and routing solutions based on use-cases. Discuss hybrid networking configurations to extend and secure your infrastructure. Discuss the benefits of microservices as an effective decoupling strategy to power highly available applications at scale. Explore AWS container services for the rapid implementation of an infrastructure-agnostic, portable application environment. Identify the business and security benefits of AWS serverless services based on business examples. Practice building a serverless infrastructure in a lab environment. Discuss the ways in which AWS edge services address latency and security. Practice building a CloudFront deployment with an S3 backend in a lab environment. Explore AWS backup, recovery solutions, and best practices to ensure resiliency and business continuity. Build a highly available and secure cloud architecture based on a business problem, in a project-based facilitator-guided lab. Architecting on AWS is for solutions architects, solution-design engineers, and developers seeking an understanding of AWS architecting. In this course, you will learn to identify services and features to build resilient, secure and highly available IT solutions on the AWS Cloud. Architectural solutions differ depending on industry, types of applications, and business size. AWS Authorized Instructors emphasize best practices using the AWS Well-Architected Framework, and guide you through the process of designing optimal IT solutions, based on real-life scenarios. The modules focus on account security, networking, compute, storage, databases, monitoring, automation, containers, serverless architecture, edge services, and backup and recovery. At the end of the course, you will practice building a solution and apply what you have learned with confidence. Prerequisites AWS Cloud Practitioner Essentials classroom or digital training, or Working knowledge of distributed systems Familiarity with general networking concepts Familiarity with IP addressing Working knowledge of multi-tier architectures Familiarity with cloud computing concepts 0 - Introductions & Course Map review Welcome and course outcomes 1 - Architecting Fundamentals Review AWS Services and Infrastructure Infrastructure Models AWS API Tools Securing your infrastructure The Well-Architected Framework Hands-on lab: Explore Using the AWS API Tools to Deploy an EC2 Instance 2 - Account Security Security Principals Identity and Resource-Based Policies Account Federation Introduction to Managing Multiple Accounts 3 - Networking, Part 1 IP Addressing Amazon Virtual Private Cloud (VPC), Patterns and Quotas Routing Internet Access Network Access Control Lists (NACLs) Security Groups 4 - Compute Amazon Elastic Cloud Compute (EC2) EC2 Instances and Instance Selection High Performance Computing on AWS Lambda and EC2, When to Use Which Hands-On Lab: Build Your Amazon VPC Infrastructure 5 - Storage Amazon S3, Security, Versioning and Storage Classes Shared File Systems Data Migration Tools 6 - Database Services AWS Database Solutions Amazon Relational Database Services (RDS) DynamoDB, Features and Use Cases Redshift, Features, Use Cases and Comparison with RDS Caching and Migrating Data Hands-on Lab: Create a Database Layer in Your Amazon VPC Infrastructure 7 - Monitoring and Scaling Monitoring: CloudWatch, CloudTrail, and VPC Flow Logs Invoking Events 8 - Automation CloudFormation AWS Systems Manager 9 - Containers Microservices Monitoring Microservices with X-Ray Containers 10 - Networking Part 2 VPC Peering & Endpoints Transit Gateway Hybrid Networking Route 53 11 - Serverless Architecture Amazon API Gateway Amazon SQS, Amazon SNS Amazon Kinesis Data Streams & Kinesis Firehose Step Functions Hands-on Lab: Build a Serverless Architecture 12 - Edge Services Edge Fundamentals Amazon CloudFront AWS Global Accelerator AWS Web Application Firewall (WAF), DDoS and Firewall Manager AWS Outposts Hands-On Lab: Configure an Amazon CloudFront Distribution with an Amazon S3 Origin 13 - Backup and Recovery Planning for Disaster Recovery AWS Backup Recovery Strategie Additional course details: Nexus Humans Architecting on AWS training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Architecting on AWS course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Security Engineering on AWS
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for security engineers, security architects, and information security professionals. Overview Identify security benefits and responsibilities of using the AWS Cloud Build secure application infrastructures Protect applications and data from common security threats Perform and automate security checks Configure authentication and permissions for applications and resources Monitor AWS resources and respond to incidents Capture and process logs Create and configure automated and repeatable deployments with tools such as AMIs and AWS CloudFormation This course demonstrates how to efficiently use AWS security services to stay secure in the AWS Cloud. The course focuses on the security practices that AWS recommends for enhancing the security of your data and systems in the cloud. The course highlights the security features of AWS key services including compute, storage, networking, and database services. You will also learn how to leverage AWS services and tools for automation, continuous monitoring and logging, and responding to security incidents. Prerequisites We recommend that attendees of this course have: Working knowledge of IT security practices and infrastructure concepts Familiarity with cloud computing concepts Completed AWS Security Essentials and Architecting on AWS courses 1 - Security on AWS Security in the AWS cloud AWS Shared Responsibility Model Incident response overview DevOps with Security Engineering 2 - Identifying Entry Points on AWS Identify the different ways to access the AWS platform Understanding IAM policies IAM Permissions Boundary IAM Access Analyzer Multi-factor authentication AWS CloudTrail 3 - Security Considerations: Web Application Environments Threats in a three-tier architecture Common threats: user access Common threats: data access AWS Trusted Advisor 4 - Application Security Amazon Machine Images Amazon Inspector AWS Systems Manager 5 - Data Security Data protection strategies Encryption on AWS Protecting data at rest with Amazon S3, Amazon RDS, Amazon DynamoDB Protecting archived data with Amazon S3 Glacier Amazon S3 Access Analyzer Amazon S3 Access Points 6 - Securing Network Communications Amazon VPC security considerations Amazon VPC Traffic Mirroring Responding to compromised instances Elastic Load Balancing AWS Certificate Manager 7 - Monitoring and Collecting Logs on AWS Amazon CloudWatch and CloudWatch Logs AWS Config Amazon Macie Amazon VPC Flow Logs Amazon S3 Server Access Logs ELB Access Logs 8 - Processing Logs on AWS Amazon Kinesis Amazon Athena 9 - Security Considerations: Hybrid Environments AWS Site-to-Site and Client VPN connections AWS Direct Connect AWS Transit Gateway 10 - Out-Of-Region Protection Amazon Route 53 AWS WAF Amazon CloudFront AWS Shield AWS Firewall Manager DDoS mitigation on AWS 11 - Security Considerations: Serverless Environments Amazon Cognito Amazon API Gateway AWS Lambda 12 - Threat Detection and Investigation Amazon GuardDuty AWS Security Hub Amazon Detective 13 - Secrets Management on AWS AWS KMS AWS CloudHSM AWS Secrets Manager 14 - Automation and Security by Design AWS CloudFormation AWS Service Catalog 15 - Account Management and Provisioning on AWS AWS Organizations AWS Control Tower AWS SSO AWS Directory Service

Certified Data Centre Facilities Operations Specialist (CDFOS)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for The primary audience for this course is anyone who works in and around IT, facilities or data centre operations and needs to understand and improve the daily operations including important processes such as lock-out/tag-out, the right process for installing/de-installing equipment, safety procedures, capacity management and much more. Overview The old believe that a fully redundant data centre facility will save the day is no longer true as many research outcomes have revealed that the majority of downtime is caused by the human factor. Policies, processes, procedures and work instructions should be carefully developed, ideally following relevant standards, to ensure an effcient and effective data centre operations which are also compliant to the required regulations. The CDFOS© (Certified Data Centre Facilities Operations Specialist) course is a three-day course which will enable participants to fully understand the requirements of running the day-to-day operations of a mission critical data centre. Participants will gain all the required competences for running the daily operations, understand which processes should be in place, and the critical elements of those processes and how to execute them. The course is fully aligned with the DCOS© (Data Centre Operations Standard). Data centre facilities operations management have proven to be the key differentiator between a data centre that is performing well or badly. Service Level Management Service Level Management Needs analysis Capability assessment Service portfolio and catalogue Service Level Agreements Reporting - Complaint procedure Customer satisfaction Service Improvement Process (SIP) Safety and Crisis Management Most common type of accidents and why they often happen The roles and responsibilities of appointed safety staff The importance of the OH&S or WHS manual Calibration of measurement and test equipment Proper lock-out/tag-out procedures Emergency response plan requirement for various potential emergencies The importance of Permit To Work Physical Security Standard Operating Procedures (SOP) for security Security risk assessment Security zones Physical inspections / security patrols Delivery of goods / holding area Entry control of individuals Badges and key management Security monitoring Security incident reporting Facilities Maintenance The importance of maintenance Maintenance definitions Maintenance operations procedures (MOP) Service reports Spare management Tools Housekeeping Data Centre Operations Shift handover Walk around duties Service management Release management Configuration management Floor management Equipment life cycle management Monitoring/Reporting/Control Monitoring requirements Facilities monitoring matrix Sensor / alarm point testing and calibration Notification matrix Escalation requirements Reporting Project Management Project management Project organization Project manager Initiation Planning Execution Monitor and control Closing Evaluation / lessons learnt Environmental Sustainability The importance of sustainability Environmental standards Power efficiency indicators Energy saving best practises Water management Sustainable energy usage Governance and Compliance The importance of document management The siz sub-processes of document management Asset management Requirements or asset recording Exam: Certified Data Centre Facilities Operations Specialist (CDFOS©) Certification exams are administered at the end of the course. The exam is a 90-minute closed book exam, with 60 multiple-choice questions. The candidate requires a minimum of 42 correct answers to pass the exam. Online exam results are known immediately and paper-based exam results will be known within one week. Additional course details: Nexus Humans Certified Data Centre Facilities Operations Specialist (CDFOS) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Certified Data Centre Facilities Operations Specialist (CDFOS) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Inclusion Facilitation
By Inclusive Solutions
Inclusion Facilitation (IF) is an approach to enhancing the inclusion, in a mainstream community of any child or young person who is experiencing difficulties in the world because of disability, personal crisis or because of their challenging behaviour towards others. The IF approach works by mobilising the young person’s natural supports to provide support and engage with the person in difficulty. Inclusion Facilitation is designed to create a better life for an individual by the provision of an intense input designed to being about social change. This usually entails a series of visits focused on getting the person out and about to increase confidence, social skills and presence in their local community and to pursue goals and dreams. Uniquely, the work is carried out under the close clinical supervision of a practicing psychologist. What is Inclusion Facilitation Work? ‘We do whatever it takes!’ Usually a Person Centred Planning event would be carried out using the PATHor MAP process – majoring on dreams and goal setting leading to precise action planning. An experienced psychologist alongside the inclusion facilitator would carry out a PATH. A large graphic will be one of the outcomes of the meetings this is a great visual record and a shared memory of the event. This will also inform the priorities for the inclusion facilitation work Optionally following the PATH event a ‘scoping report’ is created outlining what Inclusion Facilitation could offer and highlighting what dreams and goals the individual has. The PATH is also provides a good opportunity for the Facilitator to meet the focus person in a comfortable positive environment. 12 weekly visits from the Inclusion Facilitator followed by 5 monthly visits is our preferred model but we can be flexible with the delivery of this input. This is just a guideline, however we have received good results using this time frame. After this intensive input the Inclusion Facilitator will hand over to the existing family, carers and PA team to carry on where he or she has left off. This transition time is planned from the outset. An experienced psychologist is there to support the facilitator at all times and will guide all work done by the inclusion facilitator. Is this just Support work? No! This is proactive engagement – doing whatever is required. We are not just passively or reactively providing what is asked for – we are actively pursuing a good life for the individual. Our work is built on careful research around a person’s interests and what opportunities exist locally. We carry out community mapping. We actively work to tackle an individual’s own resistance and reluctance to engage more socially. We actively engage with people in social settings that the individual attends to build bridges and connections – we are bridge builders. We build circles around a person. We create the conditions in which friendships can flourish. We have direct psychological supervision and support throughout. This work is short term and intense. Enjoy participating in a multimedia workshop that will challenge, entertain and reach for your emotions. Learning Objectives 1.To be able to understand the values and wider context of inclusion. 2.To be able to set up and run an ‘Inclusion Facilitation project to improve the life chances and connections of a child or young person. 3.To understand and be able to maximise the power of the peer group in supporting relationships, achievement and behaviour. Course Content The course answers the questions: What do you do with the child who is isolated by their aggression and anger, through being different, disabled or new to the school or community? Practically how do we go about including high profile children or young people? How can we help some children be friends? We will cover: Inclusion values underpinning this work The Intentional Building of Relationships –‘Inclusion Facilitation’ work as an example Not doing it alone – The Importance of Teams in developing inclusive practice Practical setting up and running of IF work Lessons learned Stories of IF work

PEER MEDIATION
By Inclusive Solutions
Peer mediation is an approach to impacting on conflict resolution and bullying in primary and secondary schools by training pupils to be mediators or ‘counsellors’. This well proven, highly effective method of impacting on school based bullying is still viewed by some as radical. In this workshop participants are introduced to the key components of successful schemes. Our trainers have first hand experience of setting up school based schemes and sustaining these over time. Peer Mediation Training Guide Online Course now available via Teachable Platform – Peer Mediation Learn at your own pace… lots of text and video support Course Category Peer Support Description Peer mediation or peer counselling is an approach to impacting on bullying in primary and secondary schools by training pupils to be ‘Peer Mediators’ or ‘counsellors’. This well proven, highly effective method of impacting on school based bullying is still viewed by some as radical. We can provide training for staff or direct training with students across the age range – typically delivered over 6 short high impact, interactive learning workshops. For staff training, participants are introduced to the key components of successful schemes. Our trainers have first hand experience of setting up school based schemes and sustaining these over time. Enjoy participating in a multi media workshop that will challenge, entertain and reach for your emotions. Watch young people doing their stuff! Testimonials Thank you for the course – I really enjoyed it Learning Objectives To be able to understand the values and wider context of peer support To be able to set up and run a peer counselling scheme to reduce bullying To understand and be able to maximise the power of the peer group in supporting relationships, achievement and behaviour change Who Is It For ? Year 5 or Year 10 pupils Primary and secondary teachers Heads and Deputies SENCOs Learning Support and Guidance staff Advanced Skills Teachers Parents Local Authority Support Services Community Development workers Early Years and School based Practitioners Course Content The course answers the questions : What do you do with major bullying problems in school? Practically how do we go about recruiting and training pupils as counsellors? Will pupils be hurt if we involve them with bullies? Key Themes covered within the direct student training as well as in the staff development sessions- include: Issues of Confidentiality Welcoming your ‘client’ Using active listening skills Using Open and Closed Questions to enable your client to tell you his or her story How to reflect back feelings and how to check you have understood what the client has told you Exploring options for resolving the bullying issue with your client This video gives a brief taster of the work in a Nottingham Primary school. If you liked this course you may well like: PEER SUPPORT AS AN ANTI-BULLYING STRATEGY AT LOCAL AUTHORITY LEVEL

TEAMS: BUILDING CREATIVE TEAMS
By Inclusive Solutions
In this practical and engaging workshop there is input on team building, problem solving as a team, improving communication and handling conflict. This is participatory day of paper, pens, graphics, music and activity. There are no PowerPoint slides or even a projector and screen! Course Category Team Building and Leadership Early Years Inclusion Description Want a really creative, effective, inclusive team? In this practical and engaging workshop there is input on team building, problem solving as a team, improving communication and handling conflict. This is participatory day of paper, pens, graphics, music and activity. There are no PowerPoint slides or even a projector and screen! We keep the focus on interpersonal processes for getting the best out of the team. Making teams both creative and inclusive is fully explored and processes for maximising this examined. Effective leadership and management, which can transform teamwork through collaboration and consensus-building processes is covered. We refocus the team on its capacities and gifts as well as give insights into what to do when individuals are off track. The Native American medicine wheel guides us through four quadrants of leadership, vision, community and management.Harrison Owen in his work on ‘Open Space Technology’ depicts the ancient Medicine Wheel (Owen, 2003). This is derived from centuries of tradition among First Nation Americans and has informed many cultures in different ways. We have found this an extremely powerful metaphor for understanding the process of team and organisational change and renewal. The wheel of change begins in the north with a leading idea, for us – there is a better way of creating a team for inclusion. Travelling clockwise to the east we develop a shared vision of what this could look like in our setting, school or community. Then moving south we ask who needs to come with us on the journey. We wish to take as many community members along with us as we can. In an Early Years setting , this would mean enrolling the support of manager, the wider staff group, parents and ultimately children. Finally, at the west, we manage and implement the idea. We take action and turn the inclusive team into reality. The cycle of this medicine wheel is an excellent way to view change processes for any team, organisation or community. When we contemplate change, the risk is always that we will jump prematurely from the big ideas (leadership) to practice (management) and ignore the other two important phases of creating vision and engaging the wider community. When the going gets tough and the inclusion of a child or young person is beginning to seem extremely difficult if not impossible many will conclude that the child should no longer be present. We would like to challenge this. Why do we move so quickly to assuming the child is in the wrong place? Surely the real question should not be ‘do they belong here?’ – but rather – ‘what team support is needed here for this to work?’ Or even more fundamental, ‘who needs a team around them at this time?’ Who needs the team? Who is struggling with the inclusion most? Is it the young person, their practitioner or teacher, their headteacher, setting manager, their parent or even a member of the local support services? Whatever the answer a team may need to be built, rallied or reformed. The nature of and number of that team will depend upon the situation. Diversity of membership will most surely be important to strengthen the quality of the support and of the ideas generated. Use radical rethinking when creating a new team or when revitalising an existing one. Creating effective teams for inclusion requires a courageous capacity for understanding and nurturing change both within the team and with those who the team work with. Testimonials ‘What a fun, enjoyable day its been. Motivating and made me laugh not fall asleep!’?? ‘This was everything a team building day was supposed to be. I have learned a lot about the people I work with and my role within the organisation’ ‘I had reservations about attending yet another team building day but this was executed by two great facilitators and they worked with us so we truly understood what we were thinking and feeling.’ ‘Innovative and refreshing’ Learning Objectives Empowerment of team players Deepened insights into team processes Practical strategies for team building learned Processes for enhancing creativity of team members explored Celebration and recognition of existing strengths and talents Who Is It For ? Any team Course Content This course answers the following questions: How can we re-energise our team? How can we make our team more inclusive? What tools can we use to work creatively in our team? We work around the ancient medicine wheel as it guides us through the four processes of leadership, vision, community and management. We place leading ideas in front of your team including ‘no kvetching’ and shared promises. We create a shared vision of how your team would love to be. We explore who the team is. When are they at their best? What happens when someone is off track? What do they really need? How do we take the community with us at a time of change? Finally we look at the management role of the team. Getting things done together. We use problem solving together as our focus for this. Finally your team will be asked to reflect. What has the training meant to them? If you liked this you may like: SUPPORT AND SUPERVISION FOR LEADERS

Certificate in Business and Commercial Law (CBCL) - Virtual Learning
By EMG Associates UK Limited
Certificate in Business and Commercial Law (CBCL) - Virtual Learning Why Attend This course is designed for professionals with little or no prior legal background but who are required to make organizational decisions involving legal matters. It will provide participants with the fundamental principles of commercial law, including commercial contracts and negotiation, sale of goods, intellectual property rights and employee relations. It also covers all the legal aspects of setting up a business, running a business and closing a business Participants will gain an in-depth understanding of international commercial law with emphasis on the common law system. Participants will have the opportunity to learn and analyze key legal issues regarding contracts and the business as a whole which they are likely to encounter within their organization. Course Methodology In this interactive training course participants will frequently work in pairs as well as in larger groups to complete exercises as well as regional and international case studies. Course Objectives By the end of the course, participants will be able to: Apply legal rules and principles to speciï¬c commercial situations through consideration of relevant case law Negotiate commercial contracts complying with commercial and legal requirements Increase proï¬tability within their organization by selecting appropriate methods of distribution of goods Recognize and analyze how intellectual property rights aï¬ect their organization Evaluate and modify organizational employment practices complying with labor law requirements Target Audience This course is suitable for those with little or no formal training in commercial law yet would be required to understand the fundamentals of commercial law as it may directly impact their work. It will particularly beneï¬t directors and executives who have direct responsibility for legal decisions within the organization. In-house council new to the region, and those working within a legal department, will also ï¬nd this course highly beneï¬cial. Target Competencies Drafting Contracts Contract Negotiation Understanding Commercial Terms Understanding Employment Law Implementing Organizational Employment Practices Understanding Intellectual Property Understanding corporate restructuring Understanding the effect of breach of commercial contract terms Note The Dubai Government Legal Aï¬airs Department has introduced a Continuing Legal Professional Development (CLPD) programme to legal consultants authorised to practise through a licensed ï¬rm in the Emirate of Dubai. We are proud to announce that the Dubai Government Legal Aï¬airs Department has accredited EMG Associates as a CLPD provider. In addition, all our legal programmes have been approved. This PLUS Specialty Training Legal course qualiï¬es for 4 elective CLPD points. Overview of commercial & business law Areas of commercial and business law Types of commercial contracts Commercial contracts in the civil law and common law systems Sources of English law Civil law v Common law Civil law in the GCC Formalities for a binding contract Elements required for an enforceable contract Rules for contract interpretation implied terms v express terms identifying risks and how to minimise risks Structure of a commercial contract Preliminary documents in international transactions Memorandum of Understanding/ Heads of Terms. Are they legally binding? Commercial implications Boilerplate/ miscellaneous provisions- the important but forgotten clauses- beware! Force majeure v Frustration Notices Set oï¬ No waiver Entire Agreement/ non- reliance clause Times is of the essence Assignment v Novation Governing law Common mistakes in choice of law Jurisdiction clause Exclusive v Non-exclusive Factors in deciding the jurisdiction clause International dispute resolution Litigation Importance of Alternative Dispute Resolution (ADR) Arbitration Mediations Conciliation Negotiation Remedies for breach of contract Damages Specific performance Injunctions Advantages and disadvantages of different business forms Types of business vehicles Sole trader Partnerships Limited Liability Partnerships Companies Cross Border Transactions Distributorship Agency Joint Venture Acquisitions Share purchase v Business purchase Apportioning risks and liabilities through warranties and indemnities Negotiating warranties and indemnities Corporate insolvency Tests identifying insolvency Consequence for directors who fail to react to insolvency Types of insolvency Administration Receivership Creditor Voluntary Liquidation Compulsory Liquidation Commercial Tort Tort of negligence Defamation Libel Slander Recent case law on defamation Managing risk Prevention is better than cure: Eï¬ective risk management Intellectual Property Rights management Types of Intellectual Property copyright trademark patent design rights confidential information Assignment v Granting a license The law of passing off Intellectual Property in the GCC Employment law issues in the common law systems and the GCC Types of employment contracts Grounds for dismissal Wrongful dismissal Redundancy Unfair dismissal Commercial real estate in the GCC Leasehold Freehold
