- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1699 Basic courses in Liverpool delivered Live Online
Email Etiquette
By Nexus Human
This course is intended for Beginner-Moderate exposure is recommended for this course. The topics covered are cumulative in nature, and they require minimal understanding of email applications and composition. Overview The objective of the course is to give students the information needed to create emails that are written in a succinct, effective, and user-friendly manner. Students will learn how to set up an email subject, salutation, and will then work on how to write a credible email. In this course, students will learn about e-mail policies and learn how to write professional e-mail memos that convey appropriate messages. 1 - E-mail basics E-mail characteristics Writing online versus on paper Understanding the advantages and disadvantages of e-mail Understanding the cultural significance of e-mail E-mail programs Using an e-mail program to send e-mail When to use e-mail Communicating by e-mail Understanding when to avoid using e-mail Writing an e-mail message Using the MAIL acronym 2 - E-mail policies Company policies Avoiding improper e-mail messages Ensuring employee compliance to e-mail policies Copyright laws, viruses, and liability Avoiding copyright infringement Avoiding viruses Identifying e-mail liability 3 - E-mail features and security Features of an e-mail program Using attachments Using priority labels and signature files Features of an e-mail program Using attachments Using priority labels and signature files Discussing e-mail program options Securing e-mail Using encryption and digital signatures Using passwords 4 - E-mail messages Message headers Using headers E-mail message body Including proper greeting Structuring an e-mail message Closing an e-mail message 5 - E-mail effectiveness E-mail recipients Considering the factors that determine e-mail writing Anticipating recipient reaction Message management Managing your e-mail effectively 6 - Netiquette guidelines Netiquette style Using proper tone Following formatting guidelines Emoticons and abbreviations Using emoticons and electronic abbreviations 7 - Composing online correspondence Online communication Achieving the objective of the message Language and punctuation Improving online writing style Using punctuation correctly Efficient writing habits Constructing sentences Constructing paragraphs Editing e-mail messages

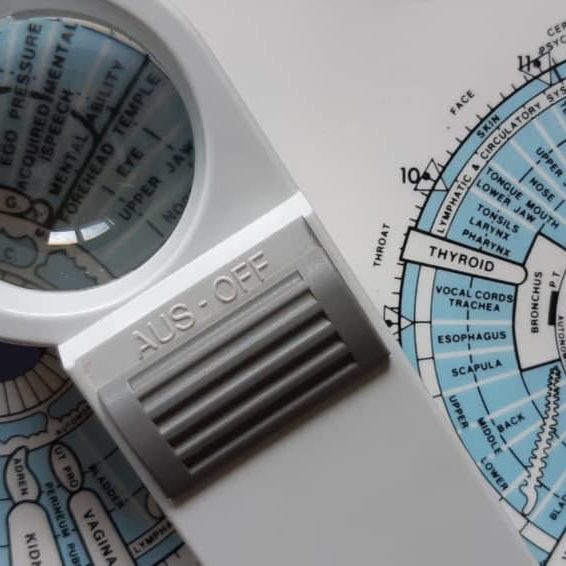
Iridology Diploma
By Plaskett International
LEARN HOW IRIDOLOGY CAN MAKE A HUGE CONTRIBUTION TO ANY COMPLEMENTARY PRACTICE A MESSAGE FROM THE AUTHOR I want to welcome you most warmly to the study of Iridology. Students of our course have taken their knowledge out into the world of practice and they have been able to see more penetratingly into the health of their patients. They have seen many truths about causes and effects in health and disease - that is what allows you to understand those extra things that make you into an even better healer. I think you are going to find this the most intriguing and absorbing study and, certainly, that is my sincere hope. As you precede, much of what you learn will amaze you and inspire wonder at the ways of the human body and mind. As you tread this very special road, I pass on to you the words that Bernard Jensen gave me years ago when I was his student, inscribed upon the inside cover of his book: “Seek the Higher Values in Life”. DR. LAWRENCE PLASKETT WHAT IS IRIDOLOGY? Iridology is the art of iris analysis. The iris is connected to the brain via the hypothalamus and can give naturopathic read outs on tissue conditions in various parts of the body. With training and practice it is possible to read signs indicative of biochemical, emotional and environmental influences that are hard to determine by other means. We can thus interpret health (and even aspects of personality) by close examination of the eyes, using suitable illumination and a magnifying glass. The close relationship between naturopathic iridology as an assessment tool and nutritional therapy and other naturopathic disciplines continues and grows closer. Now Iridology can make a huge contribution to complementary therapeutic practice and enhanced by our wonderful digital collection of eye photographs, the learning process with the Plaskett International College is a profound and exciting one. We teach Iridology quite separately from other topics and anyone who possesses, or expects to possess, a practitioner's qualification in any therapeutic discipline, may join the course. Course Duration 12 months Study Hours 200 hours Course Content 9 sections Course Fee £495 How Can Iridology Help Practitioners? Examples of how iridology can help practitioners Did you know that some iris features are so very plain that you can see them with the naked eye in ordinary social contact? You can see from two or three feet away in many cases that the person has a toxic digestive system (a strong wide dark ring around the pupil margin). You can often tell that the person has an overactive stomach (a narrow bright white ring very close to the pupil). You can tell when the skin is overlaid with toxins so that the skin's function in excreting toxins from the body is jeopardised (very narrow dark ring around the iris margin). You can tell in some people (rather advanced cases) that they suffer badly from sodium and potassium imbalance and have placed themselves at potential risk from cholesterol accumulation (the so-called corneal arcus, a white or off-white cloudy deposit, usually fairly thick, around the iris margin). Another example is the ring of spots or 'tophi' represented by the lymphatic rosary. Its mere presence tells one that there is sluggishness in the lymphatic system. When these tophi are darkly pigmented, the situation gives rise to concern for the possible generation of lymphatic illness. Using the precise positioning of iris reflex areas contained on the iris chart, one may distinguish many key points of analysis. Areas of stress and tension can be pinpointed by identifying 'contraction furrows’. Past injuries and adhesions show themselves as contortions of the normally regular and even iris fibres. You can answer questions like:- Is it the pancreas or the liver that is responsible for the trouble? Is the patient's hypertension caused by a defect of or toxic deposits in the particular brain area that is geared to control blood pressure? One of Jensen's rather dramatic illustrations is of the iris of a man who has just been shot. It shows the precise areas of tissue damage within the body and the response is very fast. The number of potential examples is almost without limit. The above may suffice to show the types of things that iridology can do for practitioners. We hope it will help you decide to study Iridology with the Plaskett International College. Course Overview The course covers the nature of iris observation, the nutritive zone, the iris chart, the chronic and acute, the intestinal and stomach zones and nerve collarette, the constitution type, respiratory system, lacunae, open lacuna, inherent weaknesses, the organs of elimination, other organs, special signs, complete diagnosis of a subject. The treatment of the topic follows the principles of Bernard Jensen in the USA. Once the basics have been learnt, the course teachings then extend considerably by bringing in the work of Dorothy Hall and of Dr Josef Deck, both of which are the subject of a special presentation during the course. The published insights of Farida Sharan and Harri Wolf, while not separately presented, also influence the presentation of the course material. Both the Australian School, (Dorothy Hall) and the German School, (Dr Deck/Harri Wolf), offer an added dimension to the study and interpretation of the constitution. PERSONALITY ASPECTS & CONSTITUTIONAL TYPES The study focuses upon the different personality aspects, which show up in different constitutional types. Dorothy Hall gives insights into what contributes to various different types of personality and their emotional and mental responses and their pre-dispositions to health or disease. Different sorts of people can have different priorities, preferences and imperatives built into their very nature from or before birth, sometimes determining the course of their entire lives and their attitudes to the world and to other people. AN EMPATHY BETWEEN PATIENT & PRACTITIONER The course teaches an understanding of these types and facilitates an empathy between patient and practitioner. It shows how people of the differing constitutional types are likely to go out of balance either mentally or emotionally and how their vulnerability to various physical ailments varies. The German School offers a very exciting and precise approach to the constitutional types, which is really quite different, but no less helpful. It highlights variations in the susceptibility to diseases of different organs and systems. THE 3 SCHOOLS OF THOUGHT It is a prime purpose of this course, not only to teach these differing positions, but also to demonstrate how it is that all three of these major schools of Iridology embody different aspects of the truth, how each is individually valuable and how a full and deep understanding of the meaning of 'constitution' can be gained through a sympathetic synthesis of the contributions from all three of these schools. BREAKDOWN OF THE COURSE SECTIONS In total there are 9 sections comprising of text, videos and iris images to study: SECTION 1 GENERAL PRACTICE AND AN ACCOUNT OF THE NUTRITIVE ZONE Areas Covered Iris colour Information that iridology can give us The structure of the eye and the iris Using the iris as an assessment tool The principle of reflex areas The Nutritive Zone Abnormality in the colon The Collarette (autonomic nerve wreath or anw) Diagnosis of the constitution based upon fibre structure Studies on images of real eyes SECTION 2 FEATURES OF THE FIBRES OUTSIDE THE COLLARETTE Areas Covered The general layout of fibres outside the collarette Inherent weaknesses First stage in further deterioration of an inherent weakness The meaning of darkness in the iris The development of discrete – open lacunae Lacunae Further notes about lightness and darkness amongst the fibres Healing lines Crypts Round the iris chart – the left iris Round the iris chart – the right iris Checking which structures and inside and which outside the collarette The organ systems The neural arc reflex SECTION 3 SPECIAL SIGNS Areas covered The corneal arcus (sodium ring, cholesterol ring, lipemic ring) The tophi (also lymphatic tophi or lymphatic rosary) Corneal Arcus The anaemia sign The catarrhal sign Acidity Grey background Scurf rim Circulatory ring Sphincter muscle (also called pupillary sphincter) Pigments (topastible or topolabile) Psoric spots Contrcation furrows Radial furrows SECTION 4 THE CONSTITUTIONS IN RELATION TO PERSONALITY TYPE AND DISEASE DISPOSITION Areas covered Very resilient Resilient average Moderately resilient Mildly resilient SECTION 5 MORE ABOUT WHITE SIGNS Areas covered Revision of distinctions between the different white signs Pictures of irises with white signs, with commentaries Further interpretation of the corneal arcus Further interpretation of the lytophi More general interpretation of the colour white SECTION 6 COLOURS IN THE IRIS AND OTHER SPECIAL SIGNS Areas Covered Yellow pigment in the iris Orange pigment Brown pigment Contraction furrows Radial furrows Psoric spots Pupillary border The “friendly fibrils” sign Summary of remedies SECTION 7 THE CONSTITUTION AND SIGNS ACCORDING TO THE GERMAN SCHOOL Areas Covered The German school of iridology Our approach to teaching the German school Introduction to the German constitutional types The lymphatic constitutions Mixed biliary constitution or biliary constitution Haematogenic (or haematogenous) constitution The way to use information on the German constitutions New signs that are specific to the German school Treatment recommendations for constitutional types SECTION 8 ADVANCED STUDIES OF THE IRIS Areas Covered Further details of the iris chart – its layout and its implications Neural arc reflex Deformation of pupil shape and position Advanced study of fibre separations, sinuosity, injuries & adhesions Lacunae of different shape and appearance The b3 bulge and the pterygium Working with genetically brown eyes SECTION 9 THE CONSULTATION & THE PRACTICALITIES Areas Covered Diagnosing pathology of individual critical organs Personality interpretations based upon the German school Conducting an iridology consultation Practical aspects of iris examination Making drawings of the iris and recording the data The uses, advantages and limitations of iris photography and its place in iridology practice Equipments and techniques of iris photography Using the computer to store and process digital images The interaction of signs Interpreting the whole iris in conjunction with the case study Pointers to treatment Carrying out case histories TESTIMONIALS Here's what students have to say about the course Emma Rubio, Health Coach Spain "As a Health Coach I decided to pursue my studies with the Plaskett College to become a Nutritional Therapist. For that, I am also studying Iridology. I am happy to have a tutor to answer my doubts and I like the flexibility that the College offers me. I love the subject of Iridology and the way it is explained, I also like having some videos of Dr Plaskett teaching Iridology as I admire him." Dr Ezequiel Lafontaine, Iridologist Puerto Rico "I LOVE IRIDOLOGY. I have over 30 iridology books, Italian, French, German, Spanish and English, plus over 4,000 photos from my own practice. I took this course for a refresher course and found the material was second to none." Mrs D. Moothy, Nutritional Therapist Mauritius “The distance learning courses have given me the opportunity to pursue my dreams through a program that was not only flexible and convenient for my schedule, but was also challenging and rewarding. I thoroughly enjoyed the readings and the assignments but most importantly, I enjoyed being able to do things at my pace. I must say that the most exciting and challenging course was the Iridology Diploma, and I am happy that I was able to do well in all the courses."
U5TR712 - IBM Maximo Asset Management - System Administration and Development v7.6x
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The audience includes implementers, developers, system administrators, project teams, database administrators and engine project technical teams. The audience also includes consultants that are looking to gain an understanding of Maximo Asset Management 7.6.0.x and the engine. Overview After completing this course, you should be able to perform the following tasks: List the components of Tivoli's process automation engine Understand Maximo modules and applications Understand Tivoli's Process Automation Engine Create the foundation data necessary for Maximo Asset Management Customize the engine database and applications Automate IBM Service Management applications using workflows Use the Maximo Work Centers Use the Integration Framework to import and export data This course is designed for anyone planning to use Maximo Asset Management and Tivoli?s process automation engine with one of the IBM System Management (ISM) products. It is a course that introduces you to the features and functions of both products. IBM Maximo Asset Management Overview This unit focuses on Maximo as an overall product and how Maximo assists companies with their asset management lifecycle. Tivoli Process Automation Engine This unit describes the functions of Tivoli?s process automation engine and introduces the products that are based on the engine. This unit also introduces Start Centers and basic navigation. Architecture and components This unit covers the architecture of Tivoli?s process automation engine. The various components that make up the system are described. The unit will address Java EE servers and the basic use of WebSphere© as it relates to the engine. The unit then covers the organization of the administrative workstation and system properties. The unit briefly describes the setup of the system for using attachments. Foundation Data This unit covers the creation of foundation data for Tivoli?s process automation engine. The foundation data is the software constructs that are necessary in the basic configuration of the product. These constructs include organizations, sites, locations, classifications, and various engine financial configurations. Security Security addresses the need to protect system resources from unauthorized access by unauthenticated users. Resources in the system are protected by Authentication and Authorization. Database architecture This unit illustrates the possible database configurations using the Database Configuration application. It also presents specific command lines that you can run to configure the changes made on the attributes of business objects using the Database Configuration application. Work Management Work Management is a collection of components and products that work together to form a powerful process and work management system. This unit provides a look at work management and focuses on using Work Management to generate, process, and complete work orders. Customizing an application This unit provides an overview of the Application Designer and Migration Manager. You will learn how to change, duplicate and create applications. You will learn the process to move from development, integration testing, user acceptance testing and moving to production. Automation This unit provides a high-level overview of key automation application programs and their functionality. It describes cron tasks, which are used to automate jobs in the system. The unit then discusses various communication tools in the system such as Communication Templates and the E mail Listener application. Finally, automated means of notification using escalations and actions are covered. Workflow This unit focuses on workflow. You learn about the Workflow Designer and its tools. You also learn how to modify an existing workflow and how to manage the included workflows. Reporting This unit provides an overview of the data analysis and reporting options that you can use in the system to analyze data. You create query by example (QBE) reports, result sets, key performance indicators (KPI), and query-based reports (QBRs). Students can optionally review Appendix A to learn how to create a simple enterprise report using Business Intelligence Reporting Tools (BIRT) designer. This report provides an example of how developers create more complex, widely used reports for users. Integration Framework In this unit, a high-level overview of the Integration Framework is provided. The Integration Framework architecture and components are described and basic configuration steps are described. The configuration and steps for loading and exporting data to and from the system are covered. You have the opportunity to practice them also. Budget Monitoring This unit provides information on a new feature introduced in Maximo 7.6.0.8, the Budget Monitoring application. In this application, you can create budget records to monitor transactions in a financial period. Inspection Tools and Tasks This unit introduces the new Inspection application. You can use the Inspections tools to create online inspection forms by using your desktop computer or laptop, and you can use the forms to complete an inspection by using your desktop computer, laptop, or tablet. Troubleshooting This unit focuses on troubleshooting as a systematic approach to solving a problem. The goal is to determine why something does not work as expected and to resolve the problem. It discusses the configuration of logging in the application. It also covers basic troubleshooting techniques, some important component logs, and information about obtaining help from Tivoli Support. Additional course details: Nexus Humans U5TR712 - IBM Maximo Asset Management - System Administration and Development v7.6x training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the U5TR712 - IBM Maximo Asset Management - System Administration and Development v7.6x course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Delivering Exceptional Customer Service on a Consistent Basis
By Beyond Satisfaction - Customer service Training
If you want your employees to improve their customer service skills and deliver an amazing experience to your customers, feel free to check out my Training course focusing on delivering the best customer care.

Configuring Juniper Networks Firewall/IPSec VPN Products
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for network engineers, support personnel, reseller support, and others responsible for implementing Juniper Networks ScreenOS firewall products. Overview After successfully completing this course, you should be able to:Explain the Juniper Networks security architecture.Configure administrative access and options.Back up and restore configuration and ScreenOS files.Configure a ScreenOS device in transparent, route, Network Address Translation (NAT), and IP version 6 (IPv6) modes.Discuss the applications of multiple virtual routers.Configure the Juniper Networks firewall to permit and deny traffic based on user defined policies.Configure advanced policy options.Identify and configure network designs for various types of network address translation.Configure policy-based and route-based VPN tunnels. This course is the first in the ScreenOS curriculum. It is a course that focuses on configuration of the ScreenOS firewall/virtual private network (VPN) products in a variety of situations, including basic administrative access, routing, firewall policies and policy options, address translation, and VPN implementations. The course combines both lecture and labs, with significant time allocated for hands-on experience. Students completing this course should be confident in their ability to configure Juniper Networks firewall/VPN products in a wide range of installations. Chapter 1: Course IntroductionChapter 2: ScreenOS Concepts, Terminology, and PlatformsChapter 3: Initial Connectivity Lab 1: Initial Configuration Chapter 4: Device Management Lab 2: Device Administration Chapter 5: Layer 3 Operations Lab 3: Layer 3 Operations Chapter 6: Basic Policy Configuration Lab 4: Basic Policy Configuration Chapter 7: Policy Options Lab 5: Policy Options Chapter 8: Address Translation Lab 6: Address Translation Chapter 9: VPN ConceptsChapter 10: Policy-Based VPNs Lab 7: Policy-Based VPNs Chapter 11: Route-Based VPNs Lab 8: Route-Based VPNs Chapter 12: IPv6 Lab 9: IPv6 Appendix A: Additional FeaturesAppendix B: Transparent Mode Lab 10: Transparent Mode (Optional) Additional course details: Nexus Humans Configuring Juniper Networks Firewall/IPSec VPN Products training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Configuring Juniper Networks Firewall/IPSec VPN Products course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Microsoft Access for Office 365: Part 2
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for This course is designed for students wishing to gain intermediate-level skills or individuals whose job responsibilities include constructing relational databases and developing tables, queries, forms, and reports in Microsoft Access for Microsoft 365. Overview In this course, you will optimize an Access database. You will: Provide input validation features to promote the entry of quality data into a database. Organize a database for efficiency and performance, and to maintain data integrity. Improve the usability of Access tables. Create advanced queries to join and summarize data. Use advanced formatting and controls to improve form presentation. Use advanced formatting and calculated fields to improve reports. Your training and experience using Microsoft© Access© has given you basic database management skills, such as creating tables, designing forms and reports, and building queries. In this course, you will expand your knowledge of relational database design; promote quality input from users; improve database efficiency and promote data integrity; and implement advanced features in tables, queries, forms, and reports. Extending your knowledge of Access will result in a robust, functional database for your users.This course is the second part of a three-course series that covers the skills needed to perform database design and development in Access.Microsoft© Access© for Office 365?: Part 1 : Focuses on the design and construction of an Access database?viewing, navigating, searching, and entering data in a database, as well as basic relational database design and creating simple tables, queries, forms, and reports.Microsoft© Access© for Office 365?: Part 2 (this course): Focuses on optimization of an Access database, including optimizing performance and normalizing data; data validation; usability; and advanced queries, forms, and reports.Microsoft© Access© for Office 365?: Part 3 : Focuses on managing the database and supporting complex database designs, including import and export of data; using action queries to manage data; creating complex forms and reports; macros and Visual Basic for Applications (VBA); and tools and strategies to manage, distribute, and secure a database.This course may be a useful component in your preparation for the Microsoft Access Expert (Microsoft 365 Apps and Office 2019): Exam MO-500 certification exam. Lesson 1: Promoting Quality Data Input Topic A: Restrict Data Input Through Field Validation Topic B: Restrict Data Input Through Forms and Record Validation Lesson 2: Improving Efficiency and Data Integrity Topic A: Data Normalization Topic B: Associate Unrelated Tables Topic C: Enforce Referential Integrity Lesson 3: Improving Table Usability Topic A: Create Lookups Within a Table Topic B: Work with Subdatasheets Lesson 4: Creating Advanced Queries Topic A: Create Query Joins Topic B: Create Subqueries Topic C: Summarize Data Lesson 5: Improving Form Presentation Topic A: Apply Conditional Formatting Topic B: Create Tab Pages with Subforms and Other Controls Lesson 6: Creating Advanced Reports Topic A: Apply Advanced Formatting to a Report Topic B: Add a Calculated Field to a Report Topic C: Control Pagination and Print Quality Topic D: Add a Chart to a Report

Palo Alto Networks : Cortex XDR 3.2: Prevention and Deployment (EDU-260)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Cybersecurity analysts and engineers and security operations specialists, as well as administrators and product deployers. Overview Successful completion of this instructor-led course with hands-on lab activities should enable you to: Describe the architecture and components of the Cortex XDR family Use the Cortex XDR management console, including reporting Create Cortex XDR agent installation packages, endpoint groups, and policies Deploy Cortex XDR agents on endpoints Create and manage Exploit and Malware Prevention profiles Investigate alerts and prioritize them using starring and exclusion policies Tune Security profiles using Cortex XDR exceptions Perform and track response actions in the Action Center Perform basic troubleshooting related to Cortex XDR agents Deploy a Broker VM and activate the Local Agents Settings applet Understand Cortex XDR deployment concepts and activation requirements Work with the Customer Support Portal and Cortex XDR Gateway for authentication and authorization This instructor-led training enables you to prevent attacks on your endpoints. After an overview of the Cortex XDR components, the training introduces the Cortex XDR management console and demonstrates how to install agents on your endpoints and how to create Security profiles and policies. The training enables you to perform and track response actions, tune profiles, and work with Cortex XDR alerts. The training concludes with discussions about basic troubleshooting of the agent, the on-premises Broker VM component, and Cortex XDR deployment. Course Outline Module 1 - Cortex XDR Overview Module 2 - Cortex XDR Main Components Module 3 - Cortex XDR Management Console Module 4 - Profiles and Policy Rules Module 5 - Malware Protection Module 6 - Exploit Protection Module 7 - Cortex XDR Alerts Module 8 - Tuning Policies Using Exceptions Module 9 - Response Actions Module 10 - Basic Agent Troubleshooting Module 11 - Broker VM Overview Module 12 - Deployment Considerations Additional course details: Nexus Humans Palo Alto Networks : Cortex XDR 3.2: Prevention and Deployment (EDU-260) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Palo Alto Networks : Cortex XDR 3.2: Prevention and Deployment (EDU-260) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Managing and Troubleshooting PCs - Part 1
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for If you are getting ready for a career as an entry-level information technology (IT) professional or personal computer (PC) service technician, the CompTIA© A+© Certification course is the first step in your preparation. Overview In this course, you will install, configure, optimize, troubleshoot, repair, upgrade, and perform preventive maintenance on personal computers, digital devices, and operating systems. You will:Identify the hardware components of personal computers and mobile digital devices.Identify the basic components and functions of operating systems.Identify networking and security fundamentals.Identify the operational procedures that should be followed by professional PC technicians.Install, configure, and troubleshoot display devices.Install and configure peripheral components.Manage system components.Manage data storage.Install and configure Microsoft Windows.Optimize and maintain Microsoft Windows.Work with other operating systems.Identify the hardware and software requirements for client environment configurations.Identify network technologies.Install and configure networking capabilities.Support mobile digital devices.Support printers and multifunction devices.Identify security threats, vulnerabilities, and controls.Implement security controls.Troubleshoot system-wide issues. In this course, you will acquire the essential skills and information you will need to install, upgrade, repair, configure, troubleshoot, optimize, and perform preventative maintenance of basic personal computer hardware and operating systems. Hardware Fundamentals Topic A: Personal Computer Components Topic B: Storage Devices Topic C: Mobile Digital Devices Topic D: Connection Interfaces Operating System Fundamentals Topic A: PC and Mobile Operating Systems Topic B: PC Operating System Tools and Utilities Networking & Security Fundamentals Topic A: Network Types Topic B: Network Components Topic C: Common Network Services Topic D: Cloud Concepts Topic E: Security Fundamentals Safety & Operational Procedures Topic A: Basic Maintenance Tools and Techniques Topic B: Personal and Electrical Safety Topic C: Environmental Safety and Materials Handling Topic D: Professionalism and Communication Topic E: Organizational Policies and Procedures Topic F: Troubleshooting Theory Supporting Display Devices Topic A: Install Display Devices Topic B: Configure Display Devices Topic C: Troubleshoot Video and Display Devices Installing & Configuring Peripheral Components Topic A: Install and Configure Input Devices Topic B: Install and Configure Output Devices Topic C: Install and Configure Input/Output Devices Topic D: Install and Configure Expansion Cards Managing System Components Topic A: Identify Motherboard Components and Features Topic B: Install and Configure CPUs and Cooling Systems Topic C: Install Power Supplies Topic D: Troubleshoot System Components Managing Data Storage Topic A: Identify RAM Types and Features Topic B: Troubleshoot RAM Issues Topic C: Install and Configure Storage Devices Topic D: Configure the System Firmware Topic E: Troubleshoot Hard Drives and RAID Arrays Installing & Configuring Microsoft Windows Topic A: Implement Client-Side Virtualization Topic B: Install Microsoft Windows Topic C: Use Microsoft Windows Topic D: Configure Microsoft Windows Topic E: Upgrade Microsoft Windows Optimizing & Maintaining Microsoft Windows Topic A: Optimize Microsoft Windows Topic B: Back Up and Restore System Data Topic C: Perform Disk Maintenance Topic D: Update Software Working with Other Operating Systems Topic A: The OS X Operating System Topic B: The Linux Operating System Customized Client Enviroments Topic A: Types of Common Business Clients Topic B: Custom Client Environments Networking Technologies Topic A: TCP/IP Properties and Characteristics Topic B: TCP/IP Topic C: Internet Connections Topic D: Ports and Protocols Topic E: Networking Tools Installing & Configuring Networking Capabilities Topic A: Configure Basic Windows Networking Topic B: Configure Network Perimeters Topic C: Using Windows Networking Features Topic D: Install and Configure SOHO Networks Supporting Mobile Digital Devices Topic A: Install and Configure Exterior Laptop Components Topic B: Install and Configure Interior Laptop Components Topic C: Other Mobile Devices Topic D: Mobile Device Accessories and Ports Topic E: Mobile Device Connectivity Topic F: Mobile Device Synchronization Topic G: Troubleshoot Mobile Device Hardware Supporting Printers & Multifunction Devices Topic A: Printer and Multifunction Technologies Topic B: Install and Configure Printers Topic C: Maintain Printers Topic D: Troubleshoot Printers Security Threats, Vulnerabilities, and Controls Topic A: Common Security Threats and Vulnerabilities Topic B: General Security Controls Topic C: Mobile Security Controls Topic D: Data Destruction and Disposal Methods Implementing Security Controls Topic A: Secure Operating Systems Topic B: Secure Workstations Topic C: Secure SOHO Networks Topic D: Secure Mobile Devices Troubleshooting System-Wide Issues Topic A: Troubleshoot PC Operating Systems Topic B: Troubleshoot Mobile Device Operating Systems and Applications Topic C: Troubleshoot Wired and Wireless Networks Topic D: Troubleshoot Common Security Issues

CV041 IBM z/OS and DB2 Basics for DB2 for z/OS DBA Beginners
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This beginning DB2 basic course is for z/OS database administrators who need to acquire the basic skills required to administer a DB2 database in a z/OS environment. Overview Describe several services provided in a z/OS environmentExplain workloads in the batch environmentExplain workloads in the online environmentDescribe job roles in a z/OS environmentLog On to TSO/ENavigate TSO/E and ISPFUse TSO commandsSetup and utilize JCL (Job Control Language)Utilize SDSFDescribe the different types of data sets in a z/OS environmentAllocate data sets and list data set information and contentCreate and modify data set contentGive an overview of the DB2 9 environmentDescribe and utilize DB2 ObjectsDescribe and utilize several DB2 UtilitiesDescribe the DB2I (DB2 Interactive Facility) environmentUse SPUFI (SQL Processing Using File Input) to compose and execute SQLSetup and execute DB2 CommandsUnderstand DB2 LoggingDescribe DB2 program preparation processUnderstand DB2 startup and shutdownUnderstand and utilize DB2 recovery strategies This course is intended for students looking to develop fundamental skills or recognition through lectures and hands-on exercises of TSO/E and ISPF, data sets, DB2 objects, Structured Query Language, DB2 commands, JCL and SDSF. Day 1 Welcome Unit 1: Introduction Unit 2: TSO/E and ISPF Exercise 1: TSO and ISPF Exercise 1 Review Unit 3: Data Sets (Data Sets and Sequential Data Sets) Exercise 2: Sequential Data Sets Exercise 2 Review Day 2 Unit 3: Data Sets (Partitioned Data Sets) Exercise 3: Partitioned Data Sets Exercise 3 Review Unit 3: Data Sets (VSAM Data Sets) Exercise 4: VSAM Data Sets Exercise 4 Review Unit 4: JCL and SDSF Exercise 5: JCL and SDSF Exercise 5 Review Day 3 Unit 5: DB2 Relational Database Concepts Unit 6: Structured Query Language (SQL) and SPUFI Exercise 6: SQL and SPUFI Exercise 6 Review Unit 7: DB2 Objects (Databases and Table Spaces) Exercise 7: Databases and Table Spaces Exercise 7 Review Unit 7: DB2 Objects (Tables, Indexes, and Views) Exercise 8: Tables, Indexes, and Views Exercise 8 Review Day 4 Unit 7: DB2 Objects (Qualified Names, Implicit Object Creation, and SQL Statements) Exercise 9: Qualified Names, Implicit Object Creation, and SQL Statements Exercise 9 Review Unit 8: The DB2 System Exercise 10: The DB2 System Exercise 10 Review Unit 9: DB2 Commands and Program Preparation Exercise 11: DB2 Commands Exercise 11 Review Day 5 Unit 10: DB2 Utilities Exercise 12: DB2 Utilities Exercise 12 Review Unit 11: DB2 Shutdown, Startup, and Recovery Exercise 13: DB2 Recovery Exercise 13 Review Unit 12: Course Summary Additional course details: Nexus Humans CV041 IBM z/OS and DB2 Basics for DB2 for z/OS DBA Beginners training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CV041 IBM z/OS and DB2 Basics for DB2 for z/OS DBA Beginners course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Managing Smaller Projects
By Underscore Group
Learn how to better apply project management techniques to manage small projects as part of your normal role.
