- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1792 Step courses in Cardiff delivered Live Online
CertNexus Certified CyberSec First Responder (CFR-410)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed primarily for cybersecurity practitioners preparing for or who currently perform job functions related to protecting information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. It is ideal for those roles within federal contracting companies and private sector firms whose mission or strategic objectives require the execution of Defensive Cyber Operations (DCO) or DoD Information Network (DoDIN) operation and incident handling. This course focuses on the knowledge, ability, and skills necessary to provide for the defense of those information systems in a cybersecurity context, including protection, detection, analysis, investigation, and response processes. Overview In this course, you will identify, assess, respond to, and protect against security threats and operate a system and network security analysis platform. You will: Assess cybersecurity risks to the organization. Analyze the threat landscape. Analyze various reconnaissance threats to computing and network environments. Analyze various attacks on computing and network environments. Analyze various post-attack techniques. Assess the organization's security posture through auditing, vulnerability management, and penetration testing. Collect cybersecurity intelligence from various network-based and host-based sources. Analyze log data to reveal evidence of threats and incidents. Perform active asset and network analysis to detect incidents. Respond to cybersecurity incidents using containment, mitigation, and recovery tactics. Investigate cybersecurity incidents using forensic analysis techniques. This course covers network defense and incident response methods, tactics, and procedures that are in alignment with industry frameworks such as NIST 800-61r2 (Computer Security Incident Handling Guide), US-CERT's National Cyber Incident Response Plan (NCIRP), and Presidential Policy Directive (PPD)-41 on Cyber Incident Coordination. It is ideal for candidates who have been tasked with the responsibility of monitoring and detecting security incidents in information systems and networks, and for executing standardized responses to such incidents. The course introduces tools, tactics, and procedures to manage cybersecurity risks, defend cybersecurity assets, identify various types of common threats, evaluate the organization's security, collect and analyze cybersecurity intelligence, and remediate and report incidents as they occur. This course provides a comprehensive methodology for individuals responsible for defending the cybersecurity of their organization. This course is designed to assist students in preparing for the CertNexus CyberSec First Responder (Exam CFR-410) certification examination. What you learn and practice in this course can be a significant part of your preparation. In addition, this course and subsequent certification (CFR-410) meet all requirements for personnel requiring DoD directive 8570.01-M position certification baselines: CSSP Analyst CSSP Infrastructure Support CSSP Incident Responder CSSP Auditor The course and certification also meet all criteria for the following Cybersecurity Maturity Model Certification (CMMC) domains: Incident Response (IR) Audit and Accountability (AU) Risk Management (RM) Lesson 1: Assessing Cybersecurity Risk Topic A: Identify the Importance of Risk Management Topic B: Assess Risk Topic C: Mitigate Risk Topic D: Integrate Documentation into Risk Management Lesson 2: Analyzing the Threat Landscape Topic A: Classify Threats Topic B: Analyze Trends Affecting Security Posture Lesson 3: Analyzing Reconnaissance Threats to Computing and Network Environments Topic A: Implement Threat Modeling Topic B: Assess the Impact of Reconnaissance Topic C: Assess the Impact of Social Engineering Lesson 4: Analyzing Attacks on Computing and Network Environments Topic A: Assess the Impact of System Hacking Attacks Topic B: Assess the Impact of Web-Based Attacks Topic C: Assess the Impact of Malware Topic D: Assess the Impact of Hijacking and Impersonation Attacks Topic E: Assess the Impact of DoS Incidents Topic F: Assess the Impact of Threats to Mobile Security Topic G: Assess the Impact of Threats to Cloud Security Lesson 5: Analyzing Post-Attack Techniques Topic A: Assess Command and Control Techniques Topic B: Assess Persistence Techniques Topic C: Assess Lateral Movement and Pivoting Techniques Topic D: Assess Data Exfiltration Techniques Topic E: Assess Anti-Forensics Techniques Lesson 6: Assessing the Organization's Security Posture Topic A: Implement Cybersecurity Auditing Topic B: Implement a Vulnerability Management Plan Topic C: Assess Vulnerabilities Topic D: Conduct Penetration Testing Lesson 7: Collecting Cybersecurity Intelligence Topic A: Deploy a Security Intelligence Collection and Analysis Platform Topic B: Collect Data from Network-Based Intelligence Sources Topic C: Collect Data from Host-Based Intelligence Sources Lesson 8: Analyzing Log Data Topic A: Use Common Tools to Analyze Logs Topic B: Use SIEM Tools for Analysis Lesson 9: Performing Active Asset and Network Analysis Topic A: Analyze Incidents with Windows-Based Tools Topic B: Analyze Incidents with Linux-Based Tools Topic C: Analyze Indicators of Compromise Lesson 10: Responding to Cybersecurity Incidents Topic A: Deploy an Incident Handling and Response Architecture Topic B: Mitigate Incidents Topic C: Hand Over Incident Information to a Forensic Investigation Lesson 11: Investigating Cybersecurity Incidents Topic A: Apply a Forensic Investigation Plan Topic B: Securely Collect and Analyze Electronic Evidence Topic C: Follow Up on the Results of an Investigation Additional course details: Nexus Humans CertNexus Certified CyberSec First Responder (CFR-410) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CertNexus Certified CyberSec First Responder (CFR-410) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

SHRM-CP/SHRM-SCP Certification Preparation
By Nexus Human
Duration 5 Days 30 CPD hours Earning your SHRM Certified Professional (SHRM-CP) or SHRM Senior Certified Professional (SHRM-SCP) credential makes you a recognized expert and leader in the HR field and a valuable asset to your organization, keeping you and your organization more competitive in today's economy. This professional distinction sets you apart from your colleagues, proving your high level of knowledge and skills. Students will be able to identify areas of strength and build on them. They will also see where they will need further concentrated study in preparation for their exam. 1 - INTRODUCTION The SHRM Body of Competency and Knowledge? (BoCK) The SHRM-CP and SHRM-SCP Certifications The SHRM Learning System© for SHRM-CP/SHRM-SCP 2 - HR COMPETENCIES Behavioral Competencies 3 - DOMAIN 1: PEOPLE Functional Area #1: HR Strategic Planning Functional Area #2: Talent Acquisition Functional Area #3: Employee Engagement and Retention Functional Area #4: Learning and Development Functional Area #5: Total Rewards 4 - DOMAIN 2: ORGANIZATION Functional Area #6: Structure of the HR Function Functional Area #7: Organizational Effectiveness and Development Functional Area #8: Workforce Management Functional Area #9: Employee and Labor Relations Functional Area #10: Technology Management 5 - DOMAIN 3: WORKPLACE Functional Area #11: HR in the Global Context Functional Area #12: Diversity and Inclusion Functional Area #13: Risk Management Functional Area #14: Corporate Social Responsibly Functional Area #15: U.S. Employment Law and Regulations 6 - FINAL EXAM/REVIEW/DISCUSSION Additional course details: Nexus Humans SHRM-CP/SHRM-SCP Certification Preparation training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SHRM-CP/SHRM-SCP Certification Preparation course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

QA Level 2 Award In Principles Of Risk Assessment (RQF) Face to Face: One-day course Virtual Classroom: Spread over 3 sessions of 2½ hr duration Don't run risks with the safety of your people - it will cost you a lot more when things start to go wrong... Risk Assessments are vital for Health and Safety, and vital for the whole process Course Contents: Main causes of Work-related Fatalities, Injuries and ill health Moral, Legal and Economic Reasons for Preventing Accidents and ill health at Work Key Terms associated with Risk Assessments in Health and Safety at Work:AccidentNear MissAccident TriangleHazardRiskRisk AssessmentSuitable and SufficientCompetence The Role of Risk Assessments in Accident and ill Health Prevention Legal Requirements for Risk Assessments Importance of Personal hygiene Basic Process for Undertaking a Risk Assessment The Five Steps of a Risk Assessment Benefits of this course: In 2020/21, a whopping 1.7 million people suffered from a work-related illness 441,000 of those sustained an injury 142 People, plus 60 members of the public, lost their lives... The estimated cost of injuries and ill health was £15 billion 28.2 million working days, or 108,045 working years, were lost due to work-related illnesses and injuries It is an employer's duty to protect the health, safety and welfare of their employees and other people who might be affected by their business. This includes providing sufficient information, instruction and training of employees, so they can work in a way that does not put themselves or others at risk Our QA Level 2 Award in Principles of Risk Assessment (RQF) course is ideal for all employees, helping them to create a better understanding of health and safety issues and risk assessments Accredited, Ofqual regulated qualification: QA Level 2 Award in Principles of Risk Assessment (RQF) training course is a nationally recognised, Ofqual regulated qualification accredited by Qualsafe Awards.This means that you can be rest assured that your Principles of Risk Assessment certificate fulfils the legal requirements and is a very good way to make sure you and your employees are trained appropriately.The Ofqual Register number for this course is 603/0857/9

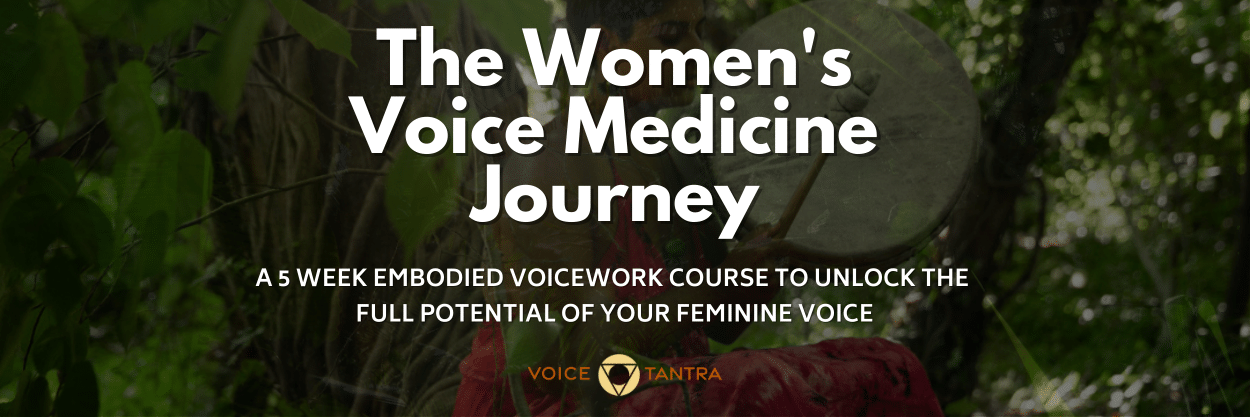
Welcome to the Women's Voice Medicine Journey. This is a female-designed, step-by-step programe, to teach you how you can truly activate and integrate some of the most essential Embodied Voicework tools to Free Your Voice and unleash your Creative Feminine Power.
Aspiring author? We know how frustrating it can be to have a brilliant story idea but feel stuck on where to start. The blank page can be intimidating, and finding the time and confidence to write can seem impossible. This Two-Day Creative Writing Workshop is designed specifically for beginners like you, ready to turn your novel dreams into reality! 🚀✍️

CompTIA PenTest+ (PenTest)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for IT professionals who want to develop penetration testing skills to enable them to identify information-system vulnerabilities and effective remediation techniques for those vulnerabilities. Target students who also need to offer practical recommendations for action to properly protect information systems and their contents will derive those skills from this course. This course is also designed for individuals who are preparing to take the CompTIA PenTest+ certification exam PT0-002, or who plan to use PenTest+ as the foundation for more advanced security certifications or career roles. Individuals seeking this certification should have three to four years of hands-on experience performing penetration tests, vulnerability assessments, and vulnerability management. Overview After completing this course, you will be able to plan, conduct, analyze, and report on penetration tests, including the ability to: Plan and scope penetration tests. Conduct passive reconnaissance. Perform non-technical tests to gather information. Conductive active reconnaissance. Analyze vulnerabilities. Penetrate networks. Exploit host-based vulnerabilities. Test applications. Complete post-exploit tasks. Analyze and report pen test results. Security remains one of the hottest topics in IT and other industries. It seems that each week brings news of some new breach of privacy or security. As organizations scramble to protect themselves and their customers, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the organizations seeking protection, and ever more lucrative for those who possess these skills. In this course, you will be introduced to some general concepts and methodologies related to pen testing, and you will work your way through a simulated pen test for a fictitious company. 1 - Outline Lesson 1: Scoping Organization/Customer Requirements Lesson 2: Defining the Rules of Engagement Lesson 3: Footprinting and Gathering Intelligence Lesson 4: Evaluating Human and Physical Vulnerabilities Lesson 5: Preparing the Vulnerability Scan Lesson 6: Scanning Logical Vulnerabilities Lesson 7: Analyzing Scanning Results Lesson 8: Avoiding Detection and Covering Tracks Lesson 9: Exploiting the LAN and Cloud Lesson 10: Testing Wireless Networks Lesson 11: Targeting Mobile Devices Lesson 12: Attacking Specialized Systems Lesson 13: Web Application-Based Attacks Lesson 14: Performing System Hacking Lesson 15: Scripting and Software Development Lesson 16: Leveraging the Attack: Pivot and Penetrate Lesson 17: Communicating During the PenTesting Process Lesson 18: Summarizing Report Components Lesson 19: Recommending Remediation Lesson 20: Performing Post-Report Delivery Activities Additional course details: Nexus Humans CompTIA Penetration Testing Certification (PenTest Plus) - (Exam PT0-002) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CompTIA Penetration Testing Certification (PenTest Plus) - (Exam PT0-002) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Weight Management Consultancy Diploma
By Plaskett International
LEARN HOW TO BECOME A WEIGHT MANAGEMENT CONSULTANT WITH THE CLIENT'S HEALTH & WELLBEING AT THE CORE. A MESSAGE FROM THE AUTHOR As you enter into this study, I want you to be fully aware of what lies before you. If you save people from overweight, you will also increase life-expectancy and/or prevent the onset of serious debilitating diseases. There will also be those clients whose life has been long limited in a psychological sense and you will be able to help them to restore their sense of verve and vitality so they can again live life to the fullest extent. This will be done through learning special expertise both technically and in person-to-person relations. With these words of encouragement, I warmly welcome you to this course of study where the amount of potential job satisfaction is incalculable. DR. LAWRENCE PLASKETT Course Duration 12 months Study Hours 200 hours Course Content 13 sections Course Fee £475 Course Overview The Plaskett Weight Management Consultancy course will provide you with a detailed, systematic and scientifically-based training, fuller than any other we know of in the field. It will enable you to practise as a well-informed Weight Management Consultant and most importantly, you will be able to help and support individuals in their quest to lose weight whilst maintaining health and well-being. Learn the Basic Elements of Nutrition You will gain an understanding of the basic elements of nutrition with a focus on the key nutrients in order to avoid deficiencies when working with weight loss clients. Create Individualised Weight Loss Programmes You will develop the confidence to be able to make informed choices from a wide span of weight loss options and avoid the use of rigidly fixed methods, thereby delivering programmes best suited to individual needs. Become a Skilled Adviser You will learn the skills to be able to counsel on a one-to-one basis, we believe that this favours the resolution of individual circumstances and problems. You will receive the training to see your clients through every stage of the process, thereby maximising their chances of success. Expand Practice of Current Health Professionals In addition to those wanting to set up practice as a Weight Management Consultant, this course is ideally suited to current health & fitness professionals looking to enhance their practice. BREAKDOWN OF THE COURSE SECTIONS The Weight Management Consultancy Diploma includes the following 13 sections: SECTION 1 BASIC SCIENCE SUPPORT Whilst our main concern will be with weight loss, we need to understand some of the basic aspects of nutrition. These deal with the key nutrients that we have to control to reduce weight. They will also help us to understand how to lose weight without developing deficiencies. In Section 1, we begin the study of nutrients and foods by looking at the main bulk nutrients that our diets contain: protein, carbohydrate and fat. Before one can consider individual vitamins and minerals, one has to know about the nutrients that make up most of our diets, namely the bulk nutrients. These are the suppliers of food energy and ultimately help to decide an individual's size. You will need to understand these so as to manipulate them with skill. Areas Covered What are the bulk nutrients? Chemical elements contained in the bulk nutrients Proteins Carbohydrates Fibre Fats The energy reserve role of fat The lipoproteins of the blood SECTION 2 UNDERSTANDING THE FIELD & NATURE OF THE PROBLEM This section introduces the basic ideas of the training. The purpose of this course of training is to enable the student to help others who are overweight or obese to lose weight, and to do so in a professional manner. At the same time, it aims to motivate you and empower you to set up a practice as a ‘Weight Management Consultant’ that will lead to your gaining a good reputation in this field, developing a panel of satisfied clients and bringing you both status and income. Since losing weight is not easy, one has to be aware of all the different methods and ramifications that are a part of this intriguing subject. The professionalism comes from knowing a number of different “ways in” to help the clients and also from being able to develop awareness of the individuality of each client. This will put you in a position to find the best and most successful route to weight loss for each person who consults you. This will mean giving individual advice, not just the same advice to everyone. By recognising individuality we earn the client’s trust and appreciation and we also increase the chances of achieving the fullest possible success by being in a position to find individual solutions to each client’s problem. Areas Covered The aims of the work The clients’ motives The clients themselves The clients’ knowledge of nutrition The place of psychology The arithmetical equation of body weight Ways of working Getting fat is all too easy – we review how it happens Definition and classification: criteria for weight normality SECTION 3 THE THEORY OF THE CAUSES OF OVERWEIGHT & OBESITY In this section we explore 'The Theory of what Causes Overweight and Obesity'. We look at the underlying reasons for this current epidemic scale of the problem in developed societies throughout the world. Understanding this will give you an insight into what needs to be done. The Weight Management Consultant clearly needs to understand as fully as possible the causes of obesity in order to be able to formulate good advice. It is necessary to understand that, although the ultimate cause is always eating more than the body requires, that factor is modified by many subsidiary factors. One, that always interests clients, is whether or not one may be predisposed by one’s inheritance to put on and retain weight, so we deal with this question. Areas covered Relative effect of genetics and environment Hormonal disturbance in obesity Slower than normal rates of energy expenditure The role of fat cells Role of the enzyme lipoprotein lipase SECTION 4 THE HEALTH CONSEQUENCES OF EXCESS WEIGHT It is well known that being overweight or obese increases the chances of contracting chronic illnesses. This section examines the types of illnesses involved and the way that their incidence is affected by body weight. From the standpoint of a Weight Management Consultant, the use of this information is to present clearly the vital benefits that your work can bring to your clients in terms of freedom from illness. This knowledge can augment your job satisfaction, especially when you can see the client’s health condition improving as weight comes down. That can be expected to happen sometimes, but of course not always. So, potentially this information can serve to inform your clients about the degree to which slimming down from an overweight or obese condition can help them to avoid very negative health consequences. By passing on parts of this data to some carefully selected clients, you may perhaps either improve their flagging motivation, or increase their satisfaction level with their early results or with the efforts they are making. Areas covered The connection between overweight and ill health The risk of early death Illness and death from cardiovascular disease Illness and death from diabetes mellitus Illness and death from hypertension Illness and death from respiratory problems Illness and death from gallbladder disease Illness and immobility from arthritis Illness from gout Illness and death from cancer SECTION 5 FIRST PRINCIPLES OF CORRECTING EXCESS WEIGHT In this section we approach the practical side of the Weight Management Consultant’s job. The greatest skill required of the Consultant is that of formulating the advice in a way that combines efficacy with client acceptability. The mistake most often made in the approach to weight reduction is to employ only one method yet in pursuing reduction in a person’s weight, it is best to come at the problem from multiple angles simultaneously. The person’s diet may well have to be the first and foremost approach however, the main alternative approaches involve several different ways of preventing excess food materials from being stored, leading to overweight. If control of the diet is the only method one employs, then so much depends upon strict dietary control that the will and the motivation of the client may be too severely tested. However, an approach in which dietary control takes pride of place, but is supported by a number of other approaches, is more likely to find client acceptability and is therefore more likely, ultimately, to be successful. In this section we list these “prevention of storage” approaches before dealing more fully with the diet. Areas covered Strategy of weight control Reduction of food intake The use of balanced hypocaloric diets Strategies for reducing food intake in practice Using foods intended to increase metabolic rate Mixtures of the various strategies SECTION 6 REDUCING WEIGHT THROUGH DIET & DIETARY COMPOSITION The principal purpose of this section is to understand the scope that we have to reduce food calories in the diet without necessarily reducing the total weight of food consumed. It looks closely at understanding and measuring food energy. Working in this way with diet is kindest to the clients and makes fewer demands upon their efforts and their will to succeed. Areas covered Understanding food energy The make-up of daily diets What does the body have to do with tis energy? Water content of foods The differing energy contents of food dry matter Substituting low-calorie for high-calorie foods The first stage of calorie reduction Combining diet with exercise A further stage of calorie reduction SECTION 7 SELECTING INDIVIDUAL FOODS The previous section talks mainly about the first principles of reducing calorie intake while keeping the weight of daily food dry matter level. This is done mainly by varying the extent to which each food class contributes to the overall diet; we simply reduce the proportions of those food classes with the higher calorie content. This section now looks within food classes to pick out those foods that, individually, have lower calorie content than the average for foods within the class concerned and make the best contribution to an individual client’s diet. This is a further step to calorie reduction without loss of food bulk. Areas covered Different foods within any given class have different calorific values Choosing foods within food classes for calorie reduction Specific recommendations for individual foods within each class Care needed in using the information Calorie contents of the “more suitable foods” Dietary results from substituting individual foods The necessary provision of dietary fat The quality of dietary protein The quantity of dietary protein Choosing foods for overall dietary suitability SECTION 8 BUILDING YOUR KNOWLEDGE OF FOODS INTO DIETS In the Sections that have gone before, we have noted several key strategies aimed at reducing the client’s intake of calories. This section gets down to the key job of building and structuring a diet to help each particular client - the aim now is to address the actual prescribing of diets to enable you to build upon the principles already learned and to give the client a workable diet that can achieve his or her aims. Areas Covered The adjusting and re-balancing of the food classes Calculating the food replacements Targeting individual foods SECTION 9 FIRST LOOK AT CONDUCTING CONSULTATIONS This section takes you through managing the consultation, helping you to structure the activity to provide a satisfactory experience for your clients. This is the basis for a good approach to weight reduction. The section culminates in the provision of example diet sheets with guidelines according to food classes and guidelines according to mealtimes and considers the benefits of both. Areas Covered The consultant’s surroundings and manner Direction of the early conversation Collection of the dietary data Weight-loss ideas come to you during the data collection Identifying the largest food contributions to overweight Balancing the food classes Writing down the guidelines Substitution of individual foods Reduction in the food bulk eaten Integrating the entire diet Example diet sheets SECTION 10 COUNTING CALORIES. BENEFITS OF EXERCISE. THE KETO DIET. In section 10 we cover the method of calculating the calories in everyday life. We look at the benefits of exercise for suitable clients and discuss more specific diets such as the ketogenic diet. Areas Covered Calculating the calories The benefits of exercise The ketogenic diet SECTION 11 PROMOTING GOOD HEALTH. UNDERSTANDING DRUG TREATMENTS. FOLLOW-UP GUIDELINES. Brings us to the section where we set about designing slimming programmes that are not only effective at weight loss, but also promote good health. To give you an insight into the potential problems, we also look at the drug treatments given for overweight by doctors. We also take you through the guidelines for follow-ups after the first consultation. Areas Covered Slimming programmes to promote good health Understanding drug treatments for overweight Follow-up guidelines SECTION 12 USE OF SUPPLEMENTS TO PROMOTE LOSS OF WEIGHT This section deals with non-food substances, or supplements that with help with weight loss. It looks at how they actually achieve this and discuss their effectiveness and safety implications for the individual. These include some micronutrients, herbs, enzyme inhibitors and sequestering agents. Areas Covered Inhibition of fat absorption Changing body composition Substances encouraging increased thermogenesis Appetite suppressants Enzyme inhibition Prevention of fat synthesis Nutrients that may accelerate metabolism Appendix 1 – some abstracts of key articles Appendix 2 – summary of modes of action SECTION 13 MANAGING This rather substantial last section deals with a fuller and final part on “Managing the Consultations”. This further develops your consultation skills and objective setting in weight management practice. It also addresses the tricky question of compliance and weight regain and how to avoid it. Finally, it looks at “Running your Practice as a Business” to ensure that you have a grasp of the business principles that you will need. Areas Covered Managing the consultations – basic methodology Note on progressive reduction in energy needs Construction of the overall prescription – different components Running your practice as a business Appendix (more about why the slimming process slows down) TESTIMONIALS Here's what students have to say about the course Mrs E. Marriott UK “The Plaskett course in Weight Management Consultancy has been a really good introduction into the importance of nutrition and balancing food groups to make up a healthy diet plan for those who are obese and wishing to lose weight. It would be good if you want to do it for your own understanding or if you are looking for a step into a professional qualification or practicing yourself. The tutors communicate with you and give you detailed feedback on assignments and the work is achievable within a year, quicker if your apply yourself. There is a lot of information in the course surrounding basic nutrients, composition of foods and on how to set up and run your own practice”.


