- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2703 Policy courses
Professional Certificate Course in Renewable Energy Policies and Sustainable Development in London 2024
4.9(261)By Metropolitan School of Business & Management UK
This course aims to provide learners with a comprehensive understanding of policymaking on renewable energy, market design and regulations, off-grid policies, decarbonization policies, international initiatives for climate change, energy burden, sustainable energy, and the circular economy. After the successful completion of the course, you will be able to learn about the following, Policymaking on Renewable Energy. Market Design and Regulations. Off-grid Policies. Polices on Decarbonization. International Initiatives for Climate Change. Energy Burden. Sustainable Energy. The circular economy. The aim of this course is to provide an in-depth understanding of renewable energy policymaking, market design, and regulations. This course will also explore off-grid policies and policies on decarbonization. Additionally, students will learn about international initiatives for climate change and the importance of reducing energy burden through sustainable energy solutions. The course will also cover the circular economy and its role in the energy transition. The course aims to provide a comprehensive understanding of renewable energy policy-making, market design, regulations, off-grid policies, decarbonization policies, international initiatives for climate change, energy burden, sustainable energy, and circular economy in order to promote a transition towards a sustainable energy future. VIDEO - Course Structure and Assessment Guidelines Watch this video to gain further insight. Navigating the MSBM Study Portal Watch this video to gain further insight. Interacting with Lectures/Learning Components Watch this video to gain further insight. Renewable Energy Policies and Sustainable Development Self-paced pre-recorded learning content on this topic. Renewable Energy Policies and Sustainable Development Put your knowledge to the test with this quiz. Read each question carefully and choose the response that you feel is correct. All MSBM courses are accredited by the relevant partners and awarding bodies. Please refer to MSBM accreditation in about us for more details. There are no strict entry requirements for this course. Work experience will be added advantage to understanding the content of the course. The certificate is designed to enhance the learner's knowledge in the field. This certificate is for everyone eager to know more and get updated on current ideas in their respective field. We recommend this certificate for the following audience. Renewable Energy Policy Analyst Sustainable Development Manager Climate Policy Advisor Renewable Energy Project Developer Environmental Compliance Specialist Energy Policy Researcher Sustainability Consultant Renewable Energy Policy Advocate Sustainable Energy Engineer Green Energy Program Manager. Average Completion Time 2 Weeks Accreditation 3 CPD Hours Level Advanced Start Time Anytime 100% Online Study online with ease. Unlimited Access 24/7 unlimited access with pre-recorded lectures. Low Fees Our fees are low and easy to pay online.

Anti Harassment and Bullying CPD Approved
By BAB Business Group
This course covers the commitments that will be laid out in your company's anti-harassment and bullying policy. It then explains the differences between harassment and bullying, the steps that can be taken if either of these occur in or out of work, and some case studies to illustrate the points covered throughout the course.

Become an exhibiting artist.
By Worcester Drawing School
About this event This is a 2 month program during which you will make a body of work, advertising and publicity during the first month and exhibit it during the second month. Includes 4 weekly tutorials, flyer design, help with hanging, private view, a 4 week exhibition, no commission on sales, and help taking the exhibition down. You can book this as a group of any size. Refund Policy Contact the organiser to request a refund.

An Understanding of Urinary Catheterisation and Catheter Care
By Guardian Angels Training
Our Urinary Catheterisation and Catheter Care training course, facilitated by registered nurses with first-hand clinical experience, are blended learning courses that allow participants to demonstrate theoretical and practical simulation within a classroom environment.

Management of Risk (M_o_R) Foundation: Virtual In-House Training
By IIL Europe Ltd
Management of Risk (M_o_R®) Foundation: Virtual In-House Training This M_o_R® Foundation course prepares learners to demonstrate knowledge and comprehension of the four elements of the M_o_R framework: Principles, Approach, Processes, Embedding and Reviewing and how these elements support corporate governance. The M_o_R Foundation Course is also a prerequisite for the M_o_R Practitioner qualification. What you will Learn At the end of the M_o_R Foundation course, participants will gain competencies in and be able to: Describe the key characteristics of risk and the benefits of risk management List the eight M_o_R Principles List and describe the use of the key M_o_R Approach documents Create Probability and Impact scales Define and distinguish between risks and issues Create a Risk Register Create a Stakeholder map Identify the key roles in risk management Use the key techniques and describe specialisms in risk management Undertake the M_o_R Foundation examination Introduction Introduction to the M_o_R course What is a risk? What is risk management? Why is risk management so important? Basic risk definitions The development of knowledge about risk management Corporate governance and internal control Where and when should risk management be applied? M_o_R Principles The purpose of M_o_R principles Aligns with objectives Fits the context Engages stakeholders Provides clear guidance Informs decision-making Facilitates continual improvement Creates a supportive culture Achieves measurable value Risk management maturity models M_o_R Approach Relationship between the documents Risk management policy Risk management process guide Risk management strategy Risk register Issue register Risk response plan Risk improvement plan Risk communications plan M_o_R Process Common process barriers Identify contexts Identify the risks Assess estimate Assess evaluate Plan Implement Communication throughout the process M_o_R Perspectives Strategic perspective Program perspective Project perspective Operational perspective Risk Specialisms Business continuity management Incident and crisis management Health and Safety management Financial risk management Environmental risk management Reputational risk management Contract risk management

Description Economic Indicators Diploma Introducing the Economic Indicators Diploma, a comprehensive online course tailored for those eager to understand the critical metrics that shape economies worldwide. This course provides learners with an in-depth understanding of the diverse array of indicators that gauge the health, stability, and trajectory of national and global economies. At the foundation of any economic analysis lies the profound understanding of its indicators. The Economic Indicators Diploma offers an overview of these tools, beginning with the basics of economic indicators. This foundational module helps participants grasp the importance of these metrics and how they can offer invaluable insights into the workings of an economy. An economy's overall health can often be measured by its Gross Domestic Product or GDP. This course unpacks GDP as the broadest economic indicator, detailing its components and highlighting its significance in policy-making and economic forecasting. The realm of employment is vital to any economy. The Economic Indicators Diploma provides a thorough exploration of employment indicators, helping participants discern the intricacies of the labour market. Understanding these metrics can unveil patterns, trends, and insights into the workforce and its relationship with economic growth or contraction. Price stability is a concern for consumers, businesses, and policymakers alike. The course sheds light on inflation as the prime price stability indicator. Participants will learn the causes, consequences, and the means to measure inflation, ensuring they can gauge its impact on purchasing power and economic decision-making. Interest rates and monetary policy are pivotal in directing an economy's course. This module elucidates the relationship between interest rates, central bank decisions, and their implications for consumers, investors, and businesses. A grasp of these concepts is crucial for anyone wishing to understand monetary dynamics and its influence on economic activity. On the global front, the balance of trade stands as a prominent international economic indicator. This course details the nuances of trade balances, imports, exports, and their ramifications for economic health and foreign relations. The housing market often mirrors an economy's vitality. This diploma elaborates on the housing market as an economic indicator, offering insights into housing demand, supply, prices, and their interplay with broader economic conditions. Moreover, the stock market is not just a place for investments; it is a reflection of economic health. The course delves into the relationship between stock market performance and a nation's economic wellbeing, providing learners with the tools to interpret market movements and their economic implications. Lastly, the mood of consumers and businesses can offer a pulse of the economy's health. The Economic Indicators Diploma covers consumer and business confidence indices, illustrating how sentiment can shape economic outcomes. The course wraps up with a conclusion on interpreting and using economic indicators. It equips learners with the skills to integrate various indicators, formulate economic forecasts, and make informed decisions in a financial, business, or policy context. Enrol in the Economic Indicators Diploma today and arm yourself with the knowledge to understand, interpret, and utilise these pivotal tools in the world of economics. Whether you're a student, a professional, or merely an enthusiastic learner, this course promises to enrich your understanding of the global economic landscape. What you will learn 1:The Basics of Economic Indicators 2:GDP: The Broadest Economic Indicator 3:Employment Indicators: Understanding Labour Market 4:Inflation: The Price Stability Indicator 5:Interest Rates and Monetary Policy 6:Balance of Trade: International Economic Indicator 7:The Housing Market as an Economic Indicator 8:Stock Market Performance and Economic Health 9:Consumer and Business Confidence Indices 10:Conclusion: Interpreting and Using Economic Indicators Course Outcomes After completing the course, you will receive a diploma certificate and an academic transcript from Elearn college. Assessment Each unit concludes with a multiple-choice examination. This exercise will help you recall the major aspects covered in the unit and help you ensure that you have not missed anything important in the unit. The results are readily available, which will help you see your mistakes and look at the topic once again. If the result is satisfactory, it is a green light for you to proceed to the next chapter. Accreditation Elearn College is a registered Ed-tech company under the UK Register of Learning( Ref No:10062668). After completing a course, you will be able to download the certificate and the transcript of the course from the website. For the learners who require a hard copy of the certificate and transcript, we will post it for them for an additional charge.
Explore the intricate world of Climate Science in this comprehensive course. From understanding the historical context of Anthropocene to dissecting the greenhouse effect and global warming, delve into topics like extreme weather events, ocean-climate interactions, and the nexus between climate change and energy systems. Equip yourself with insights into agriculture, health, and mitigation strategies, while mastering effective communication and advocacy. Uncover the complexities of global climate policy, international cooperation, and future scenarios. Join us to unravel the science behind Earth's climate change and be a catalyst for positive environmental change.

55399 Implementing and Managing Microsoft Intune
By Nexus Human
Duration 3 Days 18 CPD hours This three-day instructor-led course is aimed at modern device management professionals looking to manage their enterprise devices using Microsoft Intune. This course will cover Enrolment, Application Management, Endpoint Security and Windows Autopilot as well as Azure Active Directory Conditional Access and Identity Protection. The delegates will learn how to enroll devices, deploy applications and manage them to maximize user productivity and device security. 1: Introduction to Microsoft Intune Mobile Device Management Microsoft Intune Azure Active Directory AAD Identity Protection AAD Conditional Access 2: Microsoft Intune Device Management Enrolling Devices Device Compliance Device Profiles Device Updates 3: Microsoft Intune Application Management Application Management Deploying Applications Application Configuration Managing Applications Policy Sets and Guided Scenarios 4: Microsoft Intune Endpoint Security Security Baselines and tasks Antivirus Disk Encryption Firewall Atack Surface reduction Endpoint detection and response Account Protection 5: Deploying Windows with Windows Autopilot Windows Autopilot overview Preparing for Windows Autopilot deployment Deploying Windows 11 using Windows Autopilot 6: Microsoft Intune Additional and Premium Features Remote Help Tunnel for Mobile Application Management Endpoint Privilege Management Advanced Endpoint Analytics Additional course details: Nexus Humans 55399 Implementing and Managing Microsoft Intune training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55399 Implementing and Managing Microsoft Intune course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

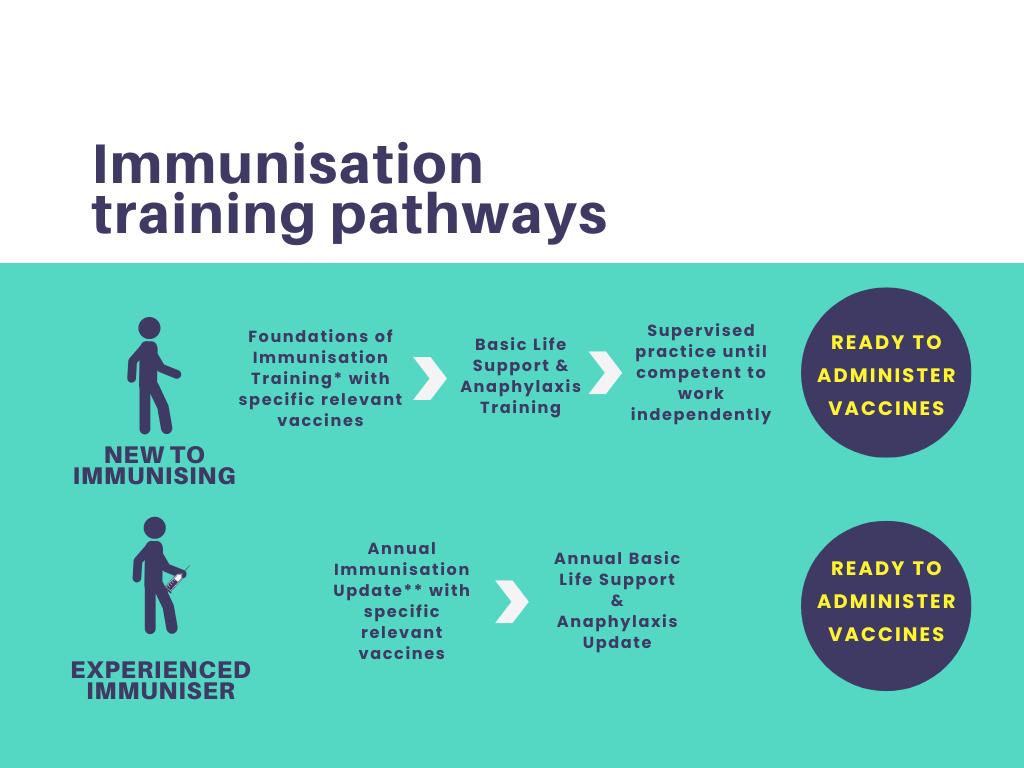
Foundations of Immunisation and Vaccines for Non-Registered Practitioners
By Guardian Angels Training
The "Foundations of Immunisation and Vaccines for Non-Registered Practitioners" course is fully compliant with the National Minimum Standards and Core Curriculum for Immunisation Training and is designed to equip non-registered healthcare professionals with a solid understanding of immunisation concepts, vaccine administration, and the importance of vaccination in public health.
M.D.D WINGMAN/WOMAN M.D.D SOCIALIZE PACKAGE (SINGLES)
4.9(27)By Miss Date Doctor Dating Coach London, Couples Therapy
This package is perfect if you have no one to go out with this weekend or you want to try some new venues without your usual friends. This weekend have some fun!!We will send an M.D.D Staff member to hang out with you for two weekends in a row go shopping, go to the cinema,go bowling,go for a meal,go to the gallery, museum or club this package is to keep you company on the weekend due to strict M.D.D policy there are no overnight stays,no visiting friends or colleagues and no visits to premises this package is for singles and people who want someone to go out with or get to meet new people and receive relationship coaching and guidance at the same time.We created this package as part of our upcoming fight loneliness campaign.We will pay for food and drinks charges Dating advice for singles 2 weekends Please contact for more information (03333443853) https://relationshipsmdd.com/product/m-d-d-socialize-package/

Search By Location
- Policy Courses in London
- Policy Courses in Birmingham
- Policy Courses in Glasgow
- Policy Courses in Liverpool
- Policy Courses in Bristol
- Policy Courses in Manchester
- Policy Courses in Sheffield
- Policy Courses in Leeds
- Policy Courses in Edinburgh
- Policy Courses in Leicester
- Policy Courses in Coventry
- Policy Courses in Bradford
- Policy Courses in Cardiff
- Policy Courses in Belfast
- Policy Courses in Nottingham