- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
4560 Operations courses delivered Online
Register on the Business Development Consultant today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The Business Development Consultant is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The Business Development Consultant Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the Business Development Consultant, all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16. Course Content Module 01: Introduction to Business Analysis Introduction to Business Analysis 00:15:00 Module 02: Strategic Analysis and Product Scope Strategic Analysis and Product Scope 00:29:00 Module 03: Business Development and Succession Planning Business Development and Succession Planning 00:25:00 Module 04: Planning & Forecasting Operations Planning & Forecasting Operations 00:22:00 Module 05: Supply Chain Management Supply Chain Management 00:21:00 Module 06: Procurement & Purchasing Management Procurement & Purchasing Management 00:22:00 Module 07: Operations Management Operations Management 00:25:00 Module 08: Project Management Project Management 00:20:00 Module 09: Performance Management Performance Management 00:19:00 Module 10: Managing Risk and Recovery Managing Risk and Recovery 00:27:00 Module 11: Quality Management Quality Management 00:22:00 Module 12: Business Environment Business Environment 00:17:00 Module 13: Organisational Skills Organisational Skills 01:17:00 Module 14: Process Management Process Management 00:25:00 Module 15: Retail Pricing Retail Pricing 00:33:00 Module 16: Management Skills for Leading Your Team Management Skills for Leading Your Team 00:18:00 Module 17: Communication Skills Communication Skills 00:26:00 Module 18: Conflict Management Conflict Management 00:15:00 Module 19: Talent Management Talent Management 00:19:00 Frequently Asked Questions Are there any prerequisites for taking the course? There are no specific prerequisites for this course, nor are there any formal entry requirements. All you need is an internet connection, a good understanding of English and a passion for learning for this course. Can I access the course at any time, or is there a set schedule? You have the flexibility to access the course at any time that suits your schedule. Our courses are self-paced, allowing you to study at your own pace and convenience. How long will I have access to the course? For this course, you will have access to the course materials for 1 year only. This means you can review the content as often as you like within the year, even after you've completed the course. However, if you buy Lifetime Access for the course, you will be able to access the course for a lifetime. Is there a certificate of completion provided after completing the course? Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate can be a valuable addition to your professional portfolio and can be shared on your various social networks. Can I switch courses or get a refund if I'm not satisfied with the course? We want you to have a positive learning experience. If you're not satisfied with the course, you can request a course transfer or refund within 14 days of the initial purchase. How do I track my progress in the course? Our platform provides tracking tools and progress indicators for each course. You can monitor your progress, completed lessons, and assessments through your learner dashboard for the course. What if I have technical issues or difficulties with the course? If you encounter technical issues or content-related difficulties with the course, our support team is available to assist you. You can reach out to them for prompt resolution.

Assembly Operative Training Course
By One Education
Stepping into the manufacturing or production sector? The Assembly Operative Training Course is your gateway to understanding the core responsibilities of modern assembly roles. Whether you're new to the field or looking to sharpen your knowledge, this online course covers the essentials with precision. From assembly line fundamentals to workplace safety, it ensures you're up to speed with current industry expectations – without needing to step onto a factory floor. Designed for convenience and clarity, the course simplifies technical jargon and gives learners confidence in understanding components, processes, and systems used in assembly work. With a focus on theoretical understanding and job-relevant procedures, it's tailored for those looking to gain valuable insight into one of the backbone functions of UK manufacturing and logistics. Accessible anytime, this training fits around your schedule, making learning as smooth as a conveyor belt on a good day. Key Features The Assembly Operative Training course includes the following offers: CPD Quality Standards Accredited Assembly Operative Training Course Lifetime Access No Hidden Fees 24/7 Tutor Support Certificate Available with reasonable price Discover a wealth of learning opportunities with our diverse range of online courses including Assembly Operative Training. From professional development to personal enrichment, we offer courses in a variety of subjects including business, technology, arts, languages, and more. This Assembly Operative Training course is carefully curated by industry experts and delivered through engaging multimedia content, interactive quizzes, and hands-on projects to ensure an immersive learning experience. Curriculum Module 1: Introduction To Assembly Operations Module 2: Assembly Tools And Materials Module 3: Assembly Line Setup And Maintenance Module 4: Health And Safety In Assembly Operations Module 5: Laws And Regulations In Manufacturing Module 6: Communication In Assembly Operations Module 7: Assembly Line Performance And Continuous Improvement Module 8: Advanced Assembly Techniques And Technologies Why This Online Course is Better for You: Unlike traditional classroom settings, our online Assembly Operative Training course offers flexibility and convenience tailored to fit your busy lifestyle. With 24/7 access to Assembly Operative Training course materials and the ability to learn at your own pace, you can study whenever and wherever it's most convenient for you. Plus, our online platform provides a supportive community of fellow learners and dedicated instructors to guide you every step of the way. CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Our Assembly Operative Training course is designed for anyone eager to expand their knowledge and skills, regardless of their background or experience level. Whether you're a working professional looking to upskill, a student seeking supplemental education, or an enthusiast pursuing a passion project, our courses are accessible to learners of all ages and abilities. Career path Invest in your future & unlock new career opportunities with our online Assembly Operative Training course. Gain valuable skills and credentials that are in high demand in today's competitive job market. Whether you're looking to switch careers, climb the corporate ladder, or start your own business, our Assembly Operative Training course provide the expertise & certification you need to succeed. Certificates Digital certificate Digital certificate - £9 Hard copy certificate Hard copy certificate - £15 A Hardcopy Certificate (international): £15 + £10 (postal charge) = £25

48-Hour Knowledge Knockdown! Prices Reduced Like Never Before! Looking to enhance your facilitation skills? Our Facilitation Skills Training course can help you become a proficient facilitator and lead successful meetings with ease. This course is part of a bundle of 11 relevant courses that are CPD-QS accredited, providing you with a competitive edge in the job market. The first course is QLS-endorsed, and you will receive a QLS hardcopy certificate for free with it. This certificate is a great way to showcase your skills and demonstrate your commitment to ongoing professional development. Throughout the course, you will learn how to plan, facilitate, and manage meetings effectively, as well as how to handle difficult situations and build consensus among participants. This course is designed to be interactive and engaging, with real-world examples and exercises to reinforce your learning. If you want to develop your facilitation skills and advance your career, this course is perfect for you. With facilitation skills in demand across a range of industries, this course will equip you with the skills you need to succeed. Enrol Now ! This Facilitation Skills Training Bundle Package includes: Course 01: Award in Facilitation Skills at QLS Level 2 10 Premium Additional CPDQS Accredited Courses - Course 01: Operations Management Training Course 02: Project Management Course Course 03: Strategic Planning Process Course 04: Quality Assurance (QA) Manager Course 05: Lean Process and Six Sigma Training Course Course 06: Workplace Health and Safety Course 07: Compliance Risk and Management Course 08: People Management Skills Course 09: Workplace Stress Management Diploma Course 10: Certificate Course in Creativity and Creative Problem Solving Why Prefer This Facilitation Skills Training Bundle? You will receive a completely free certificate from the Quality Licence Scheme Option to purchase 10 additional certificates accredited by CPD Get a free Student ID Card - (£10 postal charges will be applicable for international delivery) Free assessments and immediate success results 24/7 Tutor Support After taking this Facilitation Skills Training bundle courses, you will be able to learn: By the end of this course, you will be able to: Define the role of a facilitator and the key skills required Plan and prepare for effective meetings and workshops Facilitate discussions and manage group dynamics Use effective communication techniques to build consensus and resolve conflicts Apply different facilitation methods to achieve specific outcomes Evaluate the effectiveness of meetings and identify areas for improvement Create an action plan for ongoing personal and professional development ***Curriculum breakdown of Facilitation Skills Training*** Module One: Understanding Facilitation Module Two: Process vs. Content Module Three: Laying the Groundwork Module Four: Tuckman and Jensen's Model of Team Development Module Five: Building Consensus Module Six: Reaching a Decision Point Module Seven: Dealing with Difficult People Module Eight: Addressing Group Dysfunction Module Nine: About Intervention Module Ten: Intervention Techniques How is the Facilitation Skills Training Bundle Assessment Process? You have to complete the assignment questions given at the end of the course and score a minimum of 60% to pass each exam. Our expert trainers will assess your assignment and give you feedback after you submit the assignment. You will be entitled to claim a certificate endorsed by the Quality Licence Scheme after you successfully pass the exams. CPD 160 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Managers and team leaders who want to improve their facilitation skills HR professionals who need to facilitate workshops and meetings Project managers who need to lead effective meetings and workshops Trainers and coaches who want to enhance their facilitation skills Anyone who wants to develop their facilitation skills for personal or professional reasons Career path Operations Manager: £40,000 - £60,000 per year Project Manager: £35,000 - £70,000 per year Quality Assurance Manager: £30,000 - £50,000 per year Health and Safety Manager: £25,000 - £45,000 per year Compliance Manager: £35,000 - £60,000 per year HR Manager: £30,000 - £50,000 per year Training and Development Manager: £30,000 - £50,000 per year Certificates Award in Facilitation Skills at QLS Level 2 Hard copy certificate - Included After successfully completing the Course, you can order an original hardcopy Certificate of Achievement endorsed by the Quality Licence Scheme. This certificate will be delivered to your home, free of charge. To obtain the additional Quality License Scheme Endorsed Certificate, you will need to pay the corresponding fee based on the level of the courses: Level 1: £59 Level 2: £79 Level 3: £89 Level 4: £99 Level 5: £119 Level 6: £129 Level 7: £139 CPD QS Accredited Certificate Digital certificate - £10 Upon successfully completing the Bundle, you will need to place an order to receive a PDF Certificate for each course within the bundle. These certificates serve as proof of your newly acquired skills, accredited by CPD QS and will cost you £10 for each course. Also, the certificates are recognised throughout the UK and internationally. CPD QS Accredited Certificate Hard copy certificate - £29 International students are subject to a £10 delivery fee for their orders, based on their location.

Firefighter and Fire Safety Level 3 Diploma
By EduXpress
Our comprehensive program is meticulously crafted to equip you with the essential skills and knowledge required to thrive in your chosen field. Developed by seasoned professionals with years of industry experience, this course is ideal for those seeking to kickstart their careers or enhance their existing skill set. Featuring an engaging audio-visual presentation and easily digestible modules, our program facilitates a self-paced learning experience. Our dedicated online support team is available on weekdays to provide assistance throughout your journey. Key Learning Outcomes: Grasp the fundamentals and their practical applications. Cultivate the necessary skills for success in your field. Apply newfound knowledge to real-world scenarios. Develop effective solutions for relevant topics. Elevate your employability and career prospects. Designed to give you a competitive edge in the job market, this course offers lifetime access to materials and the flexibility to learn at your own pace, from the comfort of your home. Why Choose Us? Learn at your own pace with 24/7 online access to course materials. Benefit from full tutor support available Monday through Friday. Acquire essential skills in the convenience of your home through informative video modules. Enjoy 24/7 assistance and advice via email and live chat. Study on your preferred device - computer, tablet, or mobile. Gain a thorough understanding of the course content. Improve professional skills and earning potential upon completion. Access lifetime course materials and expert guidance. Enjoy the convenience of online learning with flexible schedules. Why Enroll in This Course? Our program provides a comprehensive introduction to the subject matter, laying a solid foundation for further study. It empowers students to acquire knowledge and skills applicable to both their professional and personal lives. Assessment: The course incorporates quizzes to evaluate your understanding and retention of the material. These quizzes pinpoint areas for further practice, allowing you to review course materials as needed. Successfully passing the final quiz qualifies you for a certificate of achievement. Career Path: Our course is meticulously designed to equip you for success in your chosen field. Upon completion, you'll have the qualifications to pursue diverse career opportunities across various industries. Course Content Firefighter and Fire Safety Level 3 Diploma Module 1: Introduction to Firefighting Module 2: Fire Safety and Prevention Module 3: Personal Protective Equipment (PPE) and Apparel Module 4: Firefighting Tools and Equipment Module 5: Fire Dynamics and Behaviour Module 6: Search and Rescue Operations Module 7: Water Supply and Fire Hose Operations Module 8: Fire Control and Extinguishment Techniques Module 9: Specialised Firefighting Operations Module 10: Health, Safety, and Wellbeing of Firefighters
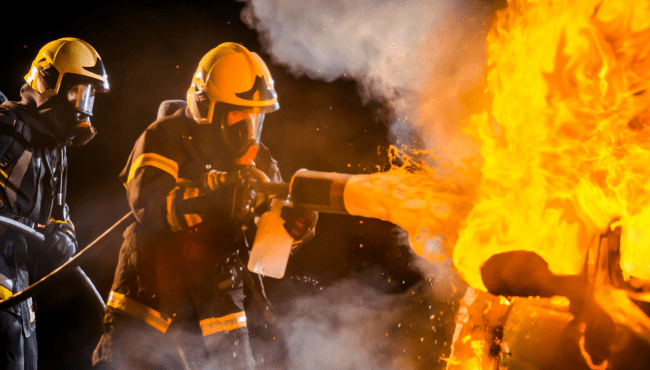
Social Housing Management (Property Development, Estate Agent & Security) - 8 Courses Bundle
By NextGen Learning
Unlock the doors to a brighter future with our comprehensive Social Housing Management (Property Development, Estate Agent & Security) bundle. Dive deep into property management, legal intricacies, and estate agency dynamics. Explore the nuances of residential property sales and learn to navigate property development challenges with finesse in the Social Housing Management (Property Development, Estate Agent & Security) bundle. Delve into eight immersive CPD Accredited courses, each a standalone course: Course 01: Social Housing Management Course 02: Residential Letting Course Course 03: Property law Level 2 Course 04: Property Management Training Course 05: Property Development Diploma Course 06: Residential Property Sales Course 07: Estate Agent Course 08: Security Management Diploma With Social Housing Management at its core, this Social Housing Management (Property Development, Estate Agent & Security) bundle is a holistic exploration of property realms. Amplify your expertise as you delve into each aspect, immersing yourself in a diverse spectrum of property-related knowledge. Elevate your career aspirations and embrace the realm of possibilities that Social Housing Management (Property Development, Estate Agent & Security) bundle offers. Learning Outcomes Grasp core principles, regulations, and operations of social housing management. Master addressing challenges for sustainable housing solutions. Excel in property valuation, marketing, and negotiation techniques. Navigate property law within social housing contexts. Optimize maintenance, tenant satisfaction, and value appreciation. Develop risk assessment and safety strategies for housing environments. Elevate your expertise with our dynamic bundle: Social Housing Essentials. This comprehensive Social Housing Management (Property Development, Estate Agent & Security) package empowers you to grasp the core principles, regulations, and operations of social housing management, setting the stage for a successful career in the housing sector. At its heart, this Social Housing Management (Property Development, Estate Agent & Security) bundle equips you with the fundamental knowledge needed to navigate the intricate landscape of social housing. Understanding these core principles is essential in today's ever-evolving housing sector. As you progress through the courses of the Social Housing Management (Property Development, Estate Agent & Security) bundle , you'll acquire a robust understanding of the regulations that govern social housing and the operational intricacies that drive its success. With real-world scenarios and case studies, in the Social Housing Management (Property Development, Estate Agent & Security) bundle, you'll gain actionable insights into effectively managing social housing projects. Discover how to address challenges head-on, ensuring the development of sustainable and inclusive housing solutions. Whether you're interested in property development, estate agency, or security management, our social Housing Management (Property Development, Estate Agent & Security) bundle provide a holistic view of the housing ecosystem. Unlock the doors to a fulfilling career where you can make a tangible impact. Equip yourself with the knowledge to navigate the complexities of social housing management confidently. Social Housing Management (Property Development, Estate Agent & Security) is not just a bundle of courses; it's a pathway to becoming a skilled professional equipped to tackle the challenges of the housing industry. Choose empowerment, choose expertise, choose Social Housing Essentials. CPD 80 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Aspiring Property Managers Real Estate Professionals Future Estate Agents Legal and Compliance Enthusiasts Property Development Seekers Security Management Aspirants Career path Property Manager: Efficient operations. Salary: £25K - £40K. Real Estate Agent: Social housing sales. Salary: £18K - £50K (incl. commission). Estate Agency Manager: Lead teams. Salary: £25K - £60K. Housing Officer: Tenant management. Salary: £20K - £35K. Property Developer: Solutions creator. Salary: £20K - £100K+. Compliance Specialist: Legal adherence. Salary: £25K - £45K. Certificates CPD Certificate Of Completion Digital certificate - Included 8 Digital Certificates Are Included With This Bundle CPD Quality Standard Hardcopy Certificate (FREE UK Delivery) Hard copy certificate - £9.99 Hardcopy Transcript - £9.99

Are you looking to improve your current abilities or make a career move? Our unique might help you get there! Expand your expertise with high-quality training - study the and get an expertly designed, great value training experience. Learn from industry professionals and quickly equip yourself with the specific knowledge and skills you need to excel in your chosen career through the online training course. This Business Management online training course is accredited by CPD with 10 CPD points for professional development. Students can expect to complete this course in around 09 hours. You'll also get dedicated expert assistance from us to answer any queries you may have while studying our course. The is broken down into several in-depth modules to provide you with the most convenient and rich learning experience possible. Upon successful completion of the course, you will receive an instant e-certificate as proof of comprehensive skill development and competency. Add these amazing new skills to your resume and boost your employability by simply enroling on this course. With this comprehensive course, you can achieve your dreams and train for your ideal career. The course provides students with an in-depth learning experience that they can work through at their own pace to enhance their professional development. You'll get a Free Student ID card by enroling in this course. This ID card entitles you to discounts on bus tickets, movie tickets, and library cards. Enroling on the course will ensure that you land your dream career faster than you thought possible. Stand out from the crowd and train for the job you want with the program. >> Course Curriculum << Module 01: Introduction to Business Management What Is Business Management? Management in Industry The Roles of an Owner Characteristics of Management Functions of Management Understanding Organisational Structure The Impact of Organisation Design Module 02: Operations Management The Concept of Product: Goods & Services Operations Management Defined The Operation System The Operations Objectives Factors to Consider Role of Operations Manager Module 03: Introduction to Business Analysis Definition Context Core Concepts Importance Knowledge Area Key Terms Module 04: Strategic Analysis & Product Scope Introduction What Is Strategy? Strategy Development External Environment Analysis Porter's Five Forces Model Internal Environment Analysis Degree of Actual & Potential Competition Competitive Strategy Analysis Achieving & Sustaining Competitive Advantage Module 05: Project Management What is Project Management? Constraints of a Project Project Life Cycle Understanding the Project Life Cycle Module 06: Business Development & Succession Planning Definition Laying the Groundwork to Develop a Business SWOT Analysis Process of Development Succession Planning Understanding the value of Succession Planning Elements of a Succession Plan Module 07: Business Process Management Fundamentals The Vision Phase The Design Phase The Modelling Phase The Execution Phase The Monitoring Phase Module 08: Planning & Forecasting Operations Demand & Forecasting Things to Know About Forecasting Forecasting Methods Aggregate Planning Planning for Product Pricing Relationship of Cost Structure to Pricing Module 09: Performance Management Definition Components The Three Phases of Performance Management Kolb's Learning Cycle Goal-setting Theory of Motivation The Importance of Motivation Module 10: Management of Cash & Credit Cash Management The Need for Cash Cash Budget What Is Cashflow? Cash Flow Problems Remedies for Cash Flow Problems Credit Management Module 11: Managing Risk & Recovery Introduction Planning Identifying Risks Creating Risk Categories Identifying the Project Risks Investigating the Results of Risk Identification Module 12: Quality Management Introduction Quality Policy Determination Benefit/Cost Analysis Preparing for Quality Control Quality Assurance Applying Module 13: Communication Skills Effective Listening Skills Verbal Communication Non-Verbal Communication Communication Strategies Module 14: Business Environment Importance Types of Business Environment Social Responsibility of a Business Ethics Module 15: Organisational Skills Organising Daily Work Organising Workplace Organising Resources Organising Tools Cultivating Organisational Habits Module 16: Negotiation Techniques Basic Types of Negotiations Phases of Negotiation Negotiation Techniques Strategies for Identifying Mutual Gain Effective Negotiation Practise Negotiation on Behalf of Others Module 17: Human Resource Management HRM Models of HRM The Role of the HR Department Aims of HRM HRM & personnel management Module 18: Motivation & Counselling The process of motivation Types of motivation Motivation theory Motivation strategies Module 19: Customer Service Introduction The Power of Positive Thinking in Customer Service Types of Difficult Customers & How to Help them How to Deal with Difficult Customers Aspects of Phone Etiquette Using Proper Phone Language Eliminate Phone Distractions Inbound Calls Outbound Calls Handling Rude or Angry Callers Module 20: Time Management Activities Planning & Prioritising Overcoming Procrastination Crisis Handling Organising Workspace to Make Better Use of Time Planning of Meetings Module 21: Conflict Management Definition of Conflict Benefits of Confrontation Prevention of Conflicts Anger Management Conflict Resolution Techniques CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? The Business Management Course has been professionally-designed for motivated learners who are looking to add a new skill to their CV and stand head and shoulders above the competition. Learn the latest industry-specific information with the Business Management - Course. Enrol on the Business Management Course and learn a new professional skill from anywhere, at any time! Requirements Enrol on the Business Management Course with no formal entry requirements! If you have a passion for knowledge and want to learn something new, register on the Business Management Course without any delay. We only ask that all students have a passion for learning and literacy, and be over the age of 16. Complete the Business Management Course online from your computer, tablet, or smartphone, and learn in a way that suits you. Career path After completing this Business Management Course, you are to start your career or begin the next phase of your career in this field. Our entire course will help you to gain a position of respect and dignity over your competitors. The certificate enhances your CV and helps you find work in the field concerned. Certificates CPD Accredited Certificate Digital certificate - £10 CPD Accredited Certificate Hard copy certificate - £29 If you are an international student, then you have to pay an additional 10 GBP as an international delivery charge.

Description: This Certified Security Leadership Officer (CSLO) - Complete Video Course covers everything you need to know about becoming a Certified Security Leadership Officer. In this course, you will learn about security management, risk management, encryption, information security - access control concepts, incident handling and evidence, operations security, and knowing network security. This course will help you to become a Certified Security Leadership Officer. It will give you an essential understanding of current security issues, best practices, and technology. You will be prepared to manage the security component of a business and its information technology security projects. A C)SLO will be able to better manage IT projects in a secure manner by possessing the essential, up-to-date knowledge and skills required to supervise the security component of any information technology project. Assessment: At the end of the course, you will be required to sit for an online MCQ test. Your test will be assessed automatically and immediately. You will instantly know whether you have been successful or not. Before sitting for your final exam you will have the opportunity to test your proficiency with a mock exam. Certification: After completing and passing the course successfully, you will be able to obtain an Accredited Certificate of Achievement. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. Who is this Course for? Certified Security Leadership Officer (CSLO) - Complete Video Course is certified by CPD Qualifications Standards and CiQ. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic background. Requirements Our Certified Security Leadership Officer (CSLO) - Complete Video Course is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path After completing this course you will be able to build up accurate knowledge and skills with proper confidence to enrich yourself and brighten up your career in the relevant job market. Security Management Security Management FREE 00:58:00 Risk Management Risk Management 00:35:00 Encryption Encryption 00:31:00 Information Security - Access Control Concepts Information Security - Access Control Concepts 00:31:00 Incident Handling and Evidence Incident Handling and Evidence 01:01:00 Operations Security Operations Security 00:48:00 Knowing Network Security Knowing Network Security 01:12:00 Mock Exam Mock Exam- Certified Security Leadership Officer (CSLO) - Complete Video Course 00:20:00 Final Exam Final Exam- Certified Security Leadership Officer (CSLO) - Complete Video Course 00:20:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Diploma in Port Management
By Training Tale
Diploma in Port Management online This Diploma in Port Management course is designed for professionals who want to expand their knowledge in order to meet their day-to-day challenges. The course will provide you with the knowledge and skills needed to advance professionally in port administration, port and harbour management, and port operations for the global maritime supply chain. This Diploma in Port Management course will allow you to gain a thorough understanding of the role of ports, particularly in international trade and logistic chain, as the "economic engine" of development. Learning Outcomes After completing this Diploma in Port Management course, learner will be able to: Gain a thorough introduction of port management Understand connecting hub port gateways to the inland infrastructure Understand port management and economic growth Understand port operations Special Offers of this Port Management Course This Port Management Course includes a FREE PDF Certificate. Lifetime access to this Port Management Course Instant access to this Port Management Course Get FREE Tutor Support from Monday to Friday in this Port Management Course [ Note: Free PDF certificate as soon as completing the Diploma in Port Management course ] Diploma in Port Management Industry Experts Designed this Diploma in Port Management course into 12 detailed modules. Detailed Course Curriculum of Diploma in Port Management Module 1: Introduction Module 2: Connecting Hub Port Gateways to the Inland Infrastructure Module 3: Port Management and Economic Growth Module 4: Port Operations Module 5: Port and Terminal Investment Module 6: Ships' Size, Ports' Size: A New Era Ahead Module 7: Strategic Alliances, Market Positioning, and Differentiation Module 8: Key Performance Indicators as Tools of Strategic Planning and Management Module 9: Leadership and Teambuilding Module 10: Port Authorities and Regulatory Framework Module 11: Ports as a Bridge to Maritime and Offshore Energy Activities Module 12: The Future of Ports Assessment Method of Port Management After completing each module of the Port Management Course, you will find automated MCQ quizzes. To unlock the next module, you need to complete the quiz task and get at least 60% marks. Certification of Port Management After completing the MCQ/Assignment assessment for this Port Management course, you will be entitled to a Certificate of Completion from Training Tale. Who is this course for? Diploma in Port Management This Diploma in Port Management course is ideal for anyone with an interest in ports as well as a desire to make their mark on an exciting, dynamic, and essential global maritime transport industry. Requirements Diploma in Port Management There are no specific requirements for this Diploma in Port Management course because it does not require any advanced knowledge or skills. Career path Diploma in Port Management After completing this Diploma in Port Management course you will have a wide range of options in the industry available to you, including: Port management Port agency Port operation Certificates Certificate of completion Digital certificate - Included

The 'Network Security and Risk Management' course provides comprehensive knowledge about security and risk management in the context of network systems. It covers essential topics such as asset security, security engineering, communication and network security, identity and access management, security assessment and testing, security operations, and software development security. Learning Outcomes: Understand the fundamental principles of security and risk management in network systems. Learn how to protect and manage assets in a network environment effectively. Gain insights into security engineering practices and their application in securing networks. Explore communication and network security protocols and techniques. Learn about identity and access management principles and their role in network security. Understand the process of security assessment and testing to identify vulnerabilities. Explore security operations and the implementation of security controls. Learn about software development security practices and their impact on network security. Why buy this Network Security and Risk Management? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Network Security and Risk Management you will be able to take the MCQ test that will assess your knowledge. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This Network Security and Risk Management does not require you to have any prior qualifications or experience. You can just enrol and start learning. Prerequisites This Network Security and Risk Management was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This Network Security and Risk Management is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Network Security and Risk Management Security and Risk Management 00:24:00 Asset Security 00:12:00 Security Engineering 00:15:00 Communication and Network Security 00:10:00 Identity and Access Management 00:10:00 Security Assessment and Testing 00:12:00 Security Operations 00:36:00 Software Development Security 00:13:00 Mock Exam Mock Exam- Network Security and Risk Management 00:20:00 Final Exam Final Exam- Network Security and Risk Management 00:20:00

Unlock the secrets of warehouse management with our comprehensive online course. Our program is designed to provide you with all the essential knowledge and skills to become a successful warehouse manager. We cover everything from the fundamentals of warehouse management to the latest technologies and inventory control techniques. Our course is CPD-accredited, which means that upon completion, you will receive a certification recognized by employers across the UK. Our curriculum is structured to ensure that you gain a thorough understanding of the core functions of warehouse management, including warehousing, supply chain management, inventory control, and cost management. Whether you're looking to start a career in warehouse management or simply want to improve your existing skills, our online course is the perfect solution. Join today and take your first step towards a successful career in warehouse management! Along with this Warehouse course, you will get 10 premium courses, an original hardcopy, 11 PDF certificates (Main Course + Additional Courses) Student ID card as gifts. This Warehouse Bundle Consists of the following Premium courses: Course 1: Warehouse Management Course 2: Freight Consultant Training Course 3: Manual Handling Level 2 Course 4: Operation Management and Retailing Course 5: Purchasing & Procurement Course - Level 3 Course 6: Risk Management Course 7: DSEAR Training Course 8: COSHH Awareness Level 3 Course 9: Fire Safety Awareness Level 2 Course 10: First Aid at Work Course 11: Time Management Enrol in Warehouse to advance your career, and use the premium study materials from Apex Learning. The Warehouse Management bundle incorporates basic to advanced level skills to shed some light on your way and boost your career. Hence, you can strengthen your Warehouse expertise and essential knowledge, which will assist you in reaching your goal. Moreover, you can learn from any place in your own time without travelling for classes. The course curriculum of Warehouse Management : Course 1: Warehouse Management Fundamentals of Warehouse Management Warehousing: Function, Benefits and Types of Warehousing Core Functions Of A Warehouse Management System Challenges Of Warehouse Management Technology In The Warehouse Supply Chain Management Concepts Warehouse Management Technologies to Adopt Order Picking in the Warehouse Managing Warehouse Inventory Organize the Storage of Inventory in a Warehouse Inventory Management Techniques Inventory Control Flow of Processing Cost Management Improve Warehouse Efficiency and Reduce Costs Certificate: PDF Certificate: Free (Previously it was £6*11 = £66) Hard Copy Certificate: Free (For The Title Course: Previously it was £10) CPD 110 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Warehouse Management course is ideal for: Logistics and supply chain professionals Warehouse managers and supervisors Operations managers Business owners and entrepreneurs Anyone interested in a career in warehousing Requirements This Warehouse course has been designed to be fully compatible with tablets and smartphones. Career path Warehouse Management Warehouse Manager - £25k-£50k/year Logistics Coordinator - £20k-£35k/year Supply Chain Analyst - £25k-£45k/year Inventory Control Specialist - £22k-£40k/year Operations Manager - £30k-£60k/year Shipping and Receiving Manager - £25k-£45k/year Certificates Certificate of completion Digital certificate - Included Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Warehouse) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.
