- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
867 Environment courses in Ashtead
EXPOSURE THERAPY PACKAGE M.D.D (SELF IMPROVEMENT)
4.9(27)By Miss Date Doctor Dating Coach London, Couples Therapy
Introducing the Exposure Therapy Package: Confront Your Fears, Embrace Resilience, and Regain Control Are you tired of being held captive by anxiety and fear? Miss Date Doctor’s Exposure Therapy Package offers you a proven and powerful approach to confront your fears, build resilience, and regain control over your life. Exposure Therapy is a specialized form of cognitive-behavioral therapy that helps individuals gradually face their fears in a safe and controlled environment. By systematically confronting anxiety-provoking situations, you’ll learn to retrain your brain’s response to fear, leading to reduced anxiety and increased confidence. Here’s how the Exposure Therapy Package can support you: Systematic Exposure: Under the guidance of our experienced therapists, exposure therapy will gradually introduce you to anxiety triggers in a controlled and supportive manner. As you confront your fears step-by-step, you’ll learn to manage anxiety more effectively. Fear Reduction: Exposure therapy helps desensitize your fear response by repeatedly exposing you to anxiety-inducing situations. Over time, your brain will adapt to these situations, leading to a reduction in anxiety levels. Empowering Coping Strategies: Our therapists will equip you with effective coping strategies to manage anxiety and distress during exposure sessions. These techniques will empower you to face challenges with increased confidence. Regaining Control: Exposure therapy provides a sense of control over anxiety-provoking situations. As you confront your fears, you’ll realize that you have the power to influence your response to anxiety, fostering a renewed sense of agency. Lasting Results: Exposure therapy is designed to produce long-lasting results. By learning to confront and manage fears, you’ll carry this resilience and newfound confidence into various aspects of your life. Customized Treatment: The Exposure Therapy Package is tailored to your specific fears and triggers. Your therapy sessions will be personalized to address your unique needs and challenges. Safe and Supportive Environment: Our therapists provide a safe and supportive environment during exposure sessions. You’ll have the guidance and encouragement needed to navigate anxiety-provoking situations with confidence. Exposure therapy is a transformational journey that allows you to break free from the grip of anxiety and reclaim your life. The Exposure Therapy Package at Miss Date Doctor is designed to empower you to face your fears, build resilience, and experience lasting relief from anxiety. Take the first step towards a more empowered and anxiety-free life with the Exposure Therapy Package. Embrace the journey of growth and regain control over your emotions and experiences. Confront your fears, unlock your potential, and step into a future filled with resilience and confidence. 3 x 1 hour sessions https://relationshipsmdd.com/product/exposure-therapy-package-m-d-d/

Microsoft Lync training course description This course teaches IT staff how to plan, design, deploy, configure, and administer a Microsoft Lync Server solution. The course emphasizes Lync Server Enterprise Unified Communications features focussing particularly on coexisting with and migrating from legacy communication services. The labs in this course create a solution that includes IM and Presence, Conferencing, and Persistent Chat. This course helps prepare for Exam 70-336. What will you learn Describe the Lync Server architecture. Install and deploy Lync Server. Use Lync Server management interfaces. Deploy and manage clients. Manage and administer dial-in conferencing. Design audio and video for web conferencing. Plan for instant message and presence Federation. Deploy and configure persistent chat in Lync. Configure archiving and monitoring services. Troubleshoot Lync Server. Describe the required daily, weekly, and monthly maintenance tasks. Use SIP commands and analyze SIP logs. Configure high availability features in Lync. Design load balancing in Lync Server. Backup and restore Lync Server data. Microsoft Lync training course details Who will benefit: Technical staff working with Microsoft Lync. Prerequisites: Supporting Windows 2008 or 2012. Duration 5 days Microsoft Lync training course contents Microsoft Lync Server architecture Lync Server architecture, Lync core capabilities, Lync design process, assessing infrastructure requirements and updating the design, planning for all Microsoft solutions framework phases. Designing a Lync Server topology Infrastructure requirements for Lync Server, using the planning tool, using topology builder, server infrastructure, documentation. Hands on Environment preparation and Lync Server pools. Users and rights in Microsoft Lync Server Managing Lync Server, role based access control. Hands on Using the management shell, configuring role-based access control. Client/device deployment and management Deploy and manage clients, prepare for device deployment, IP phones. Hands on Clients. Conferencing in Lync Server Introduction to conferencing in Lync Server, designing for audio\video and web conferencing, dial-in conferencing in Lync Server, managing and administering conferencing. Hands on Conferencing in Microsoft Lync. Designing and deploying external access Conferencing and external capabilities of Lync Server, planning for IM and presence federation, designing edge services. Hands on Deploying Edge Server and Configuring Remote Access, Validating the Edge Server. Deploying Lync Server persistent chat Overview of persistent chat architecture in Lync Server, designing persistent chat, deploying and persistent chat. Hands on persistent chat server. Monitoring and archiving The archiving service, the monitoring service, configuring archiving and monitoring. Hands on Archiving and monitoring in Lync Server. Administration and maintenance of Lync Lync Server troubleshooting tools, Lync Server operational tasks, Lync Server troubleshooting techniques. Hands on Lync administration tools, centralized logging service, analysing Lync Server logs and traces. High Availability in Lync Server High availability in Lync Server, configuring high availability in Lync Server, planning for load balancing, designing load balancing. Hands on Configuring database mirroring, experiencing a scheduled SQL Server outage, experiencing an unscheduled SQL Server outage. Disaster recovery in Lync Server Disaster recovery in Lync Server, tools for backing up and restoring Lync Server, critical Lync Server data to back up and restore, critical data to export and import, designing branch site resiliency. Hands on Configure pool pairing, experiencing a pool failure or outage. Planning a migration to Lync Server Coexistence and migration, migration steps, planning for clients and devices. Designing a client migration and device migration strategy. Hands on Creating a migration plan, documenting the migration phases.

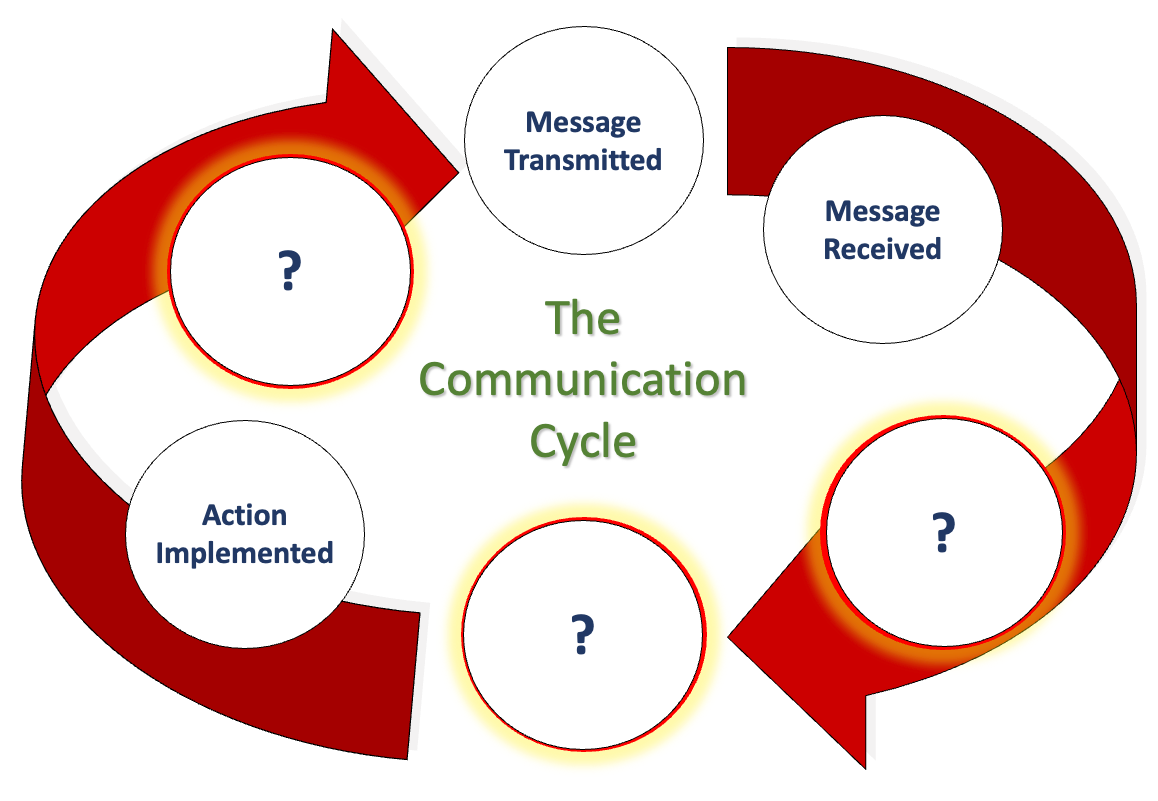
We communicate daily in many ways, including email, phone, text, Zoom, Teams, Google Meets, Slack, and even that old-fashioned thing, what was it now... oh yes, talking face-to-face. But, when we look at communication closely and really drill down into what we are doing in conjunction with how our brain works (neuroscience), how internal, organisational, and social politics control what we believe we can say, how hierarchical positioning impacts our honesty and how the lack of psychological safety means we say what we know others want to hear rather than what they need to hear…. It is oh so complicated! This workshop not only explores the concept of excellent communication, but we also want to hear what you believe it is too. We also delve into how organisational culture influences our perception of speaking up. Factors that hinder open and honest communication, and we work collaboratively towards removing these barriers to achieve a communication style that fosters trust and transparency, creating psychological safety. This workshop is particularly relevant to our Emotional Intelligence workshop (EI and Me). We firmly believe that developing emotional intelligence is the key to unlocking Clean Communication, a skill that is crucial for all of us, regardless of our roles and responsibilities, so that we thrive in our professional environment. If you want to see if we are correct, why not have us facilitate a workshop for you and see what you get by the end of it? LENGTH - Normally, one day. But please contact us to discuss your specific needs, or we can offer advice. NEXT WORKSHOP START - Please ask for more information as we deliver bespoke closed events for your people at your location or a mutually suitable location. WORKSHOP DELIVERY - The best environment for this workshop is face-to-face, but we can facilitate this workshop online. Suitability - Who should attend? Who Should Attend and Why? Who? - Perhaps think of this another way… who shouldn’t attend to ensure we can attain Clean Communication? There’s your answer. Why? - Every person needs to understand what we are saying above about how we get trapped in this organisational formatting which changes how we communicate and how it prevents us from communicating cleanly. EVERY organisation has this, despite what our values profess. And 'Values', that’s a whole other story. Workshop Content Using the 'Moccasin Approach'® to clean our personal and organisational communication LaPD’s Communication Cycle and what we must consider. (Can you work out what the ? represent above? Accountability and Responsibility raises its head in Communication. It has to. Bias, unconscious bias and its impacts on our communication. The conundrum of communicating with others and their styles (The TRAP). How would my perfect Manager/Leader communicate with me? Nonverbal communication (body language), rapport, Clean Communication. Negative communication can go viral (Self-Fulfilling Prophecy). Reflections, findings and goals (individual and team). Meeting our workshop objectives by listing five areas for development. Workshop delivery and venue This workshop is usually one day in duration, and it focuses solely on how we communicate with each other. It can also be a two-day event incorporating aspects of Emotional Intelligence (EI) with group, and individual activities to allow discussions about the various communication we need in your organisation. When you consider the content we deliver, we are sure you will understand why we always prefer to deliver our workshops, courses and programmes face-to-face. Face-to-face workshops and courses can be held at a location of your choice or, if you wish, a central UK location, such as the Macdonald Burlington Hotel in Birmingham, located directly across from the Birmingham New Street train station. We can deliver our workshops, courses and programmes online, although this will mean splitting elements into manageable learning events to suit the online environment.
Infection Control
By Prima Cura Training
Infection prevention and control is essential for all businesses, particularly where the working environment or work activities could put employees and those around them at risk of infection. This includes those working in healthcare, in close contact with people or animals, and those involved in the cleaning of human and animal waste. Infections can be easily spread, but by understanding the correct steps to take, the risk of their occurrence can be both prevented and controlled.

Securing UNIX systems training course description This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. What will you learn Secure UNIX accounts. Secure UNIX file systems. Secure UNIX access through the network. Securing UNIX systems course details Who will benefit: Linux technical staff needing to secure their systems. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Securing UNIX systems course contents Cryptography Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. Host Security Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. Access Control Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. Network Security Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

AAT Level 2 Certificate in Accounting
By London School of Science and Technology
This qualification delivers a solid foundation in finance administration and core accounting skills, including double-entry bookkeeping, basic costing and an understanding of purchase, sales and general ledgers. Course Overview This qualification delivers a solid foundation in finance administration and core accounting skills, including double-entry bookkeeping, basic costing and an understanding of purchase, sales and general ledgers. Students will also learn about accountancy related business and personal skills and be introduced to the four key themes embedded in the qualification: ethics, technology, communications and sustainability. The jobs it can lead to: • Account administrator • Accounts assistant • Accounts payable clerk • Purchase/sales ledger clerk • Trainee accounting technician • Trainee finance assistant Entry requirements: Students can start with any qualification depending on existing skills and experience. For the best chance of success, we recommend that students begin their studies with a good standard of English and maths. Course Content: Introduction to Bookkeeping: This unit provides students with an understanding of manual and digital bookkeeping systems, including the associated documents and processes. Students will learn the basic principles that underpin double-entry bookkeeping systems. Learning outcomes: • Understand how to set up bookkeeping systems. • Process customer transactions. • Process supplier transactions. • Process receipts and payments. • Process transactions into the ledger accounts. Principles of Bookkeeping Controls: This unit builds on the knowledge and skills acquired from studying Introduction to Bookkeeping and explores control accounts, journals and reconciliations. Students will develop the ability to prepare the value added tax (VAT) control accounts as well as the receivables and payables ledger accounts. They’ll use the journal to record a variety of transactions, including the correction errors. Students will be able to redraft the initial trial balance, following adjustments. Learning outcomes: • Use control accounts. • Reconcile a bank statement with the cash book. • Use the journal. • Produce trial balances. Principles of Costing: This unit gives students an introduction to the principles of basic costing and builds a solid foundation in the knowledge and skills required for more complex costing and management accounting tasks. Students will learn the importance of the costing system as a source of information that allows management to plan, make decisions and control costs. Learning outcomes: • Understand the cost recording system within an organisation. • Use cost recording techniques. • Provide information on actual and budgeted cost and income. • Use tools and techniques to support cost calculations. The Business Environment: This unit provides knowledge and understanding of key business concepts and their practical application in the external and internal environment in which students will work. Students will gain an understanding of the legal system and principles of contract law and an appreciation of the legal implications of setting up a business and the consequences this may have. This unit will also give an understanding of how organisations are structured and where the finance function fits. Learning outcomes: • Understand the principles of contract law. • Understand the external business environment. • Understand the key principles of corporate social responsibility (CSR), ethics and sustainability. • Understand the impact of setting up different types of business entity. • Understand the finance function within an organisation. • Produce work in appropriate formats and communicate effectively. • Understand the importance of information to business operations. DURATION 170-190 Hours WHATS INCLUDED Course Material Case Study Experienced Lecturer Refreshments Certificate

3G training course description This course is designed to give the delegate an understanding of the technologies used within a 3G UMTS mobile network. During the course we will investigate the UMTS air interface and the use of Wideband-Code Division Multiple Access (WCDMA) to facilitate high speed data access, together with HSPA to offer mobile broadband services. We will describe the use of soft handover rather than hard handover procedures and soft capacity sharing. The course includes a brief exploration of the UMTS protocol stack and the use of PDP Context and QoS support features. What will you learn Explain the 3G UMTS architecture. Describe the role of a Drifting & Serving RNC. Explain the use of ARQ & HARQ for mobile broadband. Describe how IMS integrates into the architecture. Describe the use of Media Gateway Controllers. Identify the temporary identities used within 3G UMTS. 3G training course details Who will benefit: Anyone working within the telecommunications area, especially within the mobile environment. Prerequisites: Mobile communications demystified Telecommunications Introduction Duration 2 days 3G training course contents D3GPP specifications 3GPP standards body, Evolution path, Frequency and bandwidth, Conceptual model, UMTS general architecture, UTRAN architecture & radio access bearer. CDMA principles CDMA principle, Code characteristics, Code requirements. CDMA requirements Synchronization, Power control, Soft handover, Rake receiver, Antenna consideration, Multi-user detection. Radio interface protocol architecture Access stratum & non-access stratum, Overall protocol structure, Logical and transport channels, Physical channels, Protocol termination. Layer 2 Protocols Medium Access Control (MAC) Protocol, Radio Link Control (RLC) Protocol, Packet Data Convergence Protocol (PDCP) protocol, Radio Interface for Broadcast/Multicast Services. Radio Resource Control (RRC) Protocol RRC Architecture, RRC Protocol State, Broadcast of information, RRC connection management, Radio bearer management, RRC connection mobility functions, Power control, Ciphering and Integrity. Mobile procedures Mobility management states and transitions, UMTS identities, Procedures in Idle mode (location updates, cell selection/ re-selection), Circuit-switched call set-up, Packet-switched context activation and context preservation, Data transfer initialization, Soft-handover procedure. Introduction to HSPA The need for high speed data, Fast HARQ, Improved scheduling, Additional channels, Soft combining, HS-DSCH codes, Uplink HSPA vs downlink HSPA, Full HSPA, Use of MIMO, Enhanced CELL_FACH.

LTE training course description This course is designed to give the delegate an understanding of the technologies used within a 3G UMTS mobile network. During the course we will investigate the UMTS air interface and the use of Wideband-Code Division Multiple Access (WCDMA) to facilitate high speed data access, together with HSPA to offer mobile broadband services. We will describe the use of soft handover rather than hard handover procedures and soft capacity sharing. The course includes a brief exploration of the UMTS protocol stack and the use of PDP Context and QoS support features. What will you learn Explain the 3G UMTS architecture. Describe the role of a Drifting & Serving RNC. Explain the use of ARQ & HARQ for mobile broadband. Describe how IMS integrates into the architecture. Describe the use of Media Gateway Controllers. Identify the temporary identities used within 3G UMTS. LTE training course details Who will benefit: Anyone working within the telecommunications area, especially within the mobile environment. Prerequisites: Mobile communications demystified Telecommunications Introduction Duration 2 days LTE training course contents LTE Introduction The path to LTE, 3GPP. LTE to LTE advanced. LTE Architecture The core, Access, roaming. Protocols: User plane, Control plane. Example information flows. Bearer management. Spectrum allocation. LTE technologies Transmission, reception, OFDMA, multiple antenna, MIMO. LTE Air interface Air interface protocol stack. Channels, Resource Grid, cell acquisition. Up and downlink controls. Layer 2 protocols. Cell acquisition Power on, selecting networks and cells. RRC connection. Attach procedure. Mobility management Roaming, RRC_IDLE, RRC_CONNECTED, cell reselection, handover, interoperation with UMTS and GSM networks. Voice and text IMS, QoS, policy and charging.

Search By Location
- Environment Courses in London
- Environment Courses in Birmingham
- Environment Courses in Glasgow
- Environment Courses in Liverpool
- Environment Courses in Bristol
- Environment Courses in Manchester
- Environment Courses in Sheffield
- Environment Courses in Leeds
- Environment Courses in Edinburgh
- Environment Courses in Leicester
- Environment Courses in Coventry
- Environment Courses in Bradford
- Environment Courses in Cardiff
- Environment Courses in Belfast
- Environment Courses in Nottingham

