- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Get Going With QuickBooks 2020 for Windows
By Nexus Human
Duration 2 Days 12 CPD hours Overview Automatic Payment Reminders for open customer invoices Ability to automatically include the PO# (purchase order number) to Invoice Emails Able to combine multiple emails which allows you to attach multiple sales or purchasing documents to a single email Quickly locate a company file using the new company file search feature Smart Help is an improved search experience that includes access to live experts through messaging and call back options The behind-the-scenes journal entry for transactions is now included. First-time QuickBooks users will learn the basic features of the software. Experienced QuickBooks users will quickly learn the new features and functionality of QuickBooks 2020. This course covers features that are in QuickBooks Pro and Premier 2020 Getting Started Starting QuickBooks Setting QuickBooks Preferences Components of the QuickBooks Operating Environment Using QuickBooks Help Identifying Common Business Terms Exiting QuickBooks Setting Up a Company Creating a QuickBooks Company Using the Chart of Accounts Working with Lists Creating Company Lists Working with the Customers & Jobs List Working with the Employees List Working with the Vendors List Working with the Item List Working with Other Lists Managing Lists Setting Up Inventory Entering Inventory Ordering Inventory Receiving Inventory Paying for Inventory Manually Adjusting Inventory Selling Your Product Creating Product Invoices Applying Credit to Invoices Emailing Invoices Setting Price Levels Creating Sales Receipts Invoicing for Services Setting Up a Service Item Changing the Invoice Format Creating a Service Invoice Editing an Invoice Voiding an Invoice Deleting an Invoice Entering Statement Charges Creating Billing Statements Processing Payments Displaying the Open Invoices Report Using the Income Tracker Receiving Payments for Invoices Making Deposits Handling Bounced Checks Working with Bank Accounts Writing a QuickBooks Check Voiding a QuickBooks Check Using Bank Account Registers Entering a Handwritten Check Transferring Funds Between Accounts Reconciling Checking Accounts Entering and Paying Bills Handling Expenses Using QuickBooks for Accounts Payable Entering Bills Paying Bills Entering Vendor Credit Using the EasyStep Interview Using the EasyStep Interview Additional course details: Nexus Humans Get Going With QuickBooks 2020 for Windows training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Get Going With QuickBooks 2020 for Windows course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Level 3 Food Safety and Hygiene for Supervisors
By Xpert Learning
About Course Xpert Learning Level 3 Food Safety and Hygiene for Supervisors Food Safety and Hygiene Level 3 for Supervisors This course is designed for anyone who is responsible for supervising or managing food handlers in a foodservice establishment. It covers the essential knowledge and skills needed to ensure that food is handled safely and hygienically, preventing the spread of foodborne illness. The course includes modules on: The importance of food safety and hygiene Personal hygiene and grooming Microbiological hazards Food allergens and cross-contamination Food handling, storage, and temperature Cleaning and sanitizing Food premises and pest control HACCP and legal requirements Food safety management controls The role of the food supervisor Who is this course for? This course is ideal for anyone who is responsible for supervising or managing food handlers in a foodservice establishment, including: Senior managers Bar managers Hotel managers Café managers Takeaway managers Business owners Head chefs Team leaders Supervisors If you are responsible for the safety of others, then this course is essential for you. It will give you the knowledge and skills you need to prevent foodborne illness and keep your customers safe. What Will You Learn? Understand your role in the supervision of food handlers Define food safety hazards and hygiene risks Prevent and control food safety hazards Develop and maintain an effective HACCP system Preserve food safely and hygienically Keep premises and equipment clean Control contamination through safe temperatures and storage Ensure that staff keep a good standard of personal hygiene Keep the workplace hygienic and safe for food preparation, cooking, and storage Course Content Module 01: Introduction to Food Safety What is food safety? Why is it important? What are food safety hazards? The obligations of food businesses. Introduction to Food Safety Module 02: Personal Hygiene & Grooming The importance of personal hygiene, hand washing technique, food service gloves, personal grooming, employee's illness and responsibility. Personal Hygiene & Grooming Module 03: Microbiological Food Hazards Biological hazards, physical hazards, chemical hazards, the 4 C's of food safety. Microbiological Food Hazards Module 04: Food Allergens & Cross Contaminations Food allergens, allergic reactions to different foods, allergen control, cross contamination, causes of cross contamination, preventing cross contamination. Food Allergens & Cross Contaminations Module 05: Food Handling, Storage and Temperature Food Handling, Storage and Temperature Module 06: Cleaning and Sanitising The importance of cleaning, cleaning, the 6 stages of cleaning, sanitising, cleaning schedule. Cleaning and Sanitising Module 07: Food Premises and Pest Control Food Premises and Pest Control Module 08: HACCP & Legal Requirements Module 08: HACCP & Legal Requirements Module 09: Food safety management controls Advantages of an FSMS FSMS Group The Key Steps Continual Improvement The FSMS monitoring and verification system Food safety management controls Model 10: The Role of the Food Supervisor Food Supervisor Importance of Food Supervisor Roles and Responsibility The Role of the Food Supervisor A course by Xpert Learning RequirementsThere are no formal entry requirements for the course, with enrollment open to anyone! Audience Restaurant Managers and Supervisors Chefs Food safety managers Business owners Senior Hotel Managers Senior Café Managers Audience Restaurant Managers and Supervisors Chefs Food safety managers Business owners Senior Hotel Managers Senior Café Managers

VMware NSX Advanced Load Balancer: Web Application Firewall Security [V22.x]
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Experienced system administrators and network administrators Overview By the end of the course, you should be able to meet the following objectives: Describe the NSX Advanced Load Balancer architecture, components, and main functions Explain the key features and benefits of NSX Advanced Load Balancer Explain and configure local load-balancing constructs such as virtual services, pools, health monitors, and related components Recognize web application breaches and threats Recognize multiple attack vectors such as web scraping, Layer 7 Denial of Service, brute force, and code injections Explain the components of NSX Advanced Load Balancer WAF that build a security pipeline to protect a web application from being attacked Describe how to configure the NSX Advanced Load Balancer WAF components Describe an NSX Advanced Load Balancer WAF operational task such as setting up an application with WAF, tuning the WAF Policy, and working with logs and analytics Explain the NSX Advanced Load Balancer WAF best practices for on-boarding a web application; configuring WAF settings for effective application security Explain how to size the NSX Advanced Load Balancer WAF data plane Explain the WAF Application learning feature, configuration of Application learning, Virtual Patching concepts, common caveats, and troubleshooting while deploying in any environment Recognize NSX Advanced Load Balancer Cloud Services that include threat Intelligence services Describe the Threat Intelligence service provided by NSX Advanced Load Balancer WAF and how the NSX Advanced Load Balancer WAF Threat Intelligence service receives live security threat feed for multiple attack vectors from Cloud Services (formerly Avi Pulse) Describe the NSX Advanced Load Balancer DataScript capabilities for detecting and defending against advance and zero-day attacks. Discuss the relevant NSX Advanced Load Balancer WAF logs and perform basic troubleshooting of applications that are protected by NSX Advanced Load Balancer WAF Explain the NSX Advanced Load Balancer WAF capability to protect Personally Identifiable Information (PII) This three-day course provides comprehensive training to install, configure, and manage a VMware NSX Advanced Load Balancer Web Application Firewall (WAF) solution. This course covers key NSX Advanced Load Balancer WAF features and functionality offered in the NSX Advanced Load Balancer 22.1.3 release for web security and application attack protection. Features include security pipeline, application learning, policy tuning, false positive mitigation, virtual patching, threat intelligence, troubleshooting, logs, analytics, and solution monitoring. Hands-on labs provide access to an NSX Advanced Load Balancer environment to reinforce the skills and concepts presented in the course. Course Introduction Introduction and course logistics Course objectives Introduction to NSX Advanced Load Balancer Illustrate NSX Advanced Load Balancer Explain NSX Advanced Load Balancer architecture and components Describe control plane clustering and high availability Describe data plane high availability mode Understand the common terminologies used with NSX Advanced Load Balancer Explain the NSX Advanced Load Balancer service elements Explain virtual service components and how to configure a virtual service Explain application profiles and network profiles Explain the pool configuration options and how to configure a pool Explain the available load-balancing algorithms Explain and configure SSL profiles and certificates Explain cloud connectors and cloud connector integration modes Explain multiple health monitor types Understand client logs Introduction to Application Security Understand web application security breaches and the implication of breaches Explain common terminologies related to Web Application Security Understand the different teams involved to secure applications Attacking Web Applications Understand the various web application security testing methodologies Understand the OWASP Top 10 vulnerabilities Understand the tools to generate a web application attack Describe a few types of web application attacks Types of Transport Understand different web traffic transport modes Describe web traffic and API traffic NSX Advanced Load Balancer WAF Components Understand the core design principles of NSX Advanced Load Balancer WAF Describe the NSX Advanced Load Balancer WAF components that build the WAF security pipeline Understand the NSX Advanced Load Balancer WAF configuration objects NSX Advanced Load Balancer WAF Operations Examine how to set up an application with WAF Describe considerations for the WAF policy Work with WAF logs and analytics Describe WAF policy tuning Describe the options available to remediate false positive mitigation NSX Advanced Load Balancer WAF Best Practices Describe technical and application considerations for onboarding an application front ended by WAF Describe best practices to remediate false positive mitigation. Describe how to manage a response from a back-end application server and client upload to the application server Describe the consideration for setting the rigidity of a WAF signature rule set Describe the options available to identify client traffic NSX Advanced Load Balancer WAF Sizing Understand how to do WAF data plane sizing in Greenfield and Brownfield deployments NSX Advanced Load Balancer WAF Custom Rules Understand WAF custom rules Describe the need and recommendation for custom rules Describe ModSecurity rules Understand the ModSecurity rule structure and explain how to construct the rule Analyze a sample custom rule for the use-case scenario for in-depth understanding of a custom rule NSX Advanced Load Balancer WAF Application Learning Understand the significance of Application Learning Explain the Positive Security Model architecture Describe the WAF multifaceted Application Learning technique to build an application model for creating positive security rules Describe how to view the data that is learned by the Application learning module Describe the WAF Virtual Patching technique to construct a WAF policy from Dynamic Application Security Testing (DAST) scanner results Understand the conditions for sharing WAF Learning Data and PSM Group in WAF Policy. Malware Protection Through ICAP in NSX Advanced Load Balancer Understand Malicious File Upload Protection and ICAP workflow Describe ICAP configuration and log analytics NSX Advanced Load Balancer IP Reputation Understand IP Reputation concepts and their integration with NSX Advanced Load Balancer Describe IP Reputation configuration, log analytics, and troubleshooting DataScript for Application Security Describe DataScript events and reference Describe application security using DataScript Explain how to troubleshoot DataScript issues Rate Limiting and DOS Describe and configure the NSX Advanced Load Balancer rate limiter technique Describe protection from denial of service (DoS) attacks and distributed DoS (DDoS) attacks in NSX Advanced Load Balancer Explain the Service Engine general advice and guidance for DDOS Bot Management Understand Bots Describe the Bot Management mechanism in NSX Advanced Load Balancer Describe how to configure NSX Advanced Load Balancer Bot Management Managing Personally Identifiable Information in NSX Advanced Load Balancer Understand Personally Identifiable Information (PII) Understand the scope of managing PII in NSX Advanced Load Balancer Describe how to configure the hidden PII in NSX Advanced Load Balancer logs using profiles and WAF rules. Threat Intelligence Introduce the Threat Intelligence service Describe the Threat Intelligence live security threat feed for multiple attack vectors Describe how to configure Threat Intelligence in NSX Advanced Load Balancer Application Programming Interface Security Define Application Programming Interface (API) Security Understand API authentication and authorization using virtual service authentication mechanisms used for a virtual service such as LDAP, SAML, JSON Web Token, and OAUTH Understand API Rate Limiting in NSX Advanced Load Balancer Understand the NSX Advanced Load Balancer WAF Protection for API Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware NSX Advanced Load Balancer: Web Application Firewall Security [V22.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware NSX Advanced Load Balancer: Web Application Firewall Security [V22.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware NSX Advanced Load Balancer: Web Application Firewall Security [V22.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Primavera P6 Professional Fundamentals Rel 19
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Analyst End User Implementer Manager Overview Create a Work Breakdown Structure Define roles and resources Assign roles Assign resources Analyze resources Optimize the project plan Understand data structures Create a project Add activities View calendars Create relationships Schedule the project Assign constraints Create reports Format schedule data Execute the project Enrolling in this course will help you understand P6 Professional's basic features and functionality so you can apply them to your organization's project management processes. You'll also learn how to manage projects on time and within budget Understanding P6 Data Describing Enterprise and Project-Specific data Logging In Opening an Existing Project Opening and Customizing Layouts Enterprise Project Structure Describing Components of EPS Creating a Project Create a project Navigating in the Projects Window Viewing Project Details Creating a Work Breakdown Structure Defining a Work Breakdown Structure Creating the WBS Hierarchy Adding Activities Describing an Activity and its Components Describing Activity Types Adding Activities Adding a Notebook Topic Adding Steps to an Activity Assigning Activity Codes Creating Relationships Viewing a Network Logic Diagram Relationship Types Creating Relationships Scheduling Performing a Forward and Backward Pass Describing Float Assigning Constraints Applying an Overall Deadline to a Project Apply a Constraint to an Activity Using Reflection Projects Creating a Reflection Project Merging Changes Formatting Schedule Data Grouping Activities Sorting Filtering Roles and Resources Describing Roles and Resources Viewing Dictionaries Assigning Roles Assigning Roles to an Activity Assign Rates on Roles Assigning Resources Assigning Resources Adjusting Budgeted Units/Time Analyzing Resources Displaying the Resource Usage Profile Optimizing the Project Plan Analyzing Schedule Dates Shortening a Project Schedule Analyzing Resource Availability Baselining the Project Plan Creating a Baseline Plan Display Baseline Bars on the Gantt Chart Project Execution and Control Describing Methods for Updating the Schedule Using Progress Spotlight Statusing Activities Rescheduling the Project Reporting Performance Describing Reporting Methods Running a Schedule Report Creating a report with the Report Wizard Additional course details: Nexus Humans Primavera P6 Professional Fundamentals Rel 19 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Primavera P6 Professional Fundamentals Rel 19 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Certified IT Specialist (CITS)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is most suited for IT professionals who have a need to understand the current requirements and core competences for managing IT in mission-critical environments. Overview After completion of the course the participant will be able to: 1. Provide guidance and implementation for IT strategy as set by senior IT and business management 2. Select and manage staff, implement training programs, career plan development and job rotation programs 3. Select, evaluate and negotiate vendors using RFI, RFP and selection criteria 4. Provide guidance for developing, testing and implementing business applications 5. Manage and/or assist in IT project management 6. Design and implement service management processes for incident, problem and change management 7. Understand the need for business continuity and design the business continuity plan 8. Review and implement information security practices and controls 9. Assist and initiate risk management practices 10. Understand and select new technologies such as cloud computing, big data, Internet of Things and social media to support business change demands 11. Select strategies for information management 12. Measure and improve quality of IT services CITS is designed to teach the skills, knowledge and competencies required of the modern IT specialist working at the senior professional, team-leader, supervisor or management level in IT management. IT Strategy The need for Information Technology Enterprise architecture Service catalogue Service level management Sustainable development IT Organisation Personnel need Roles and responsibilities Sourcing Selection process Hiring staff Managing staff Career planning Training / job rotation Performance appraisal Staff departures Vendor Selection / Management The importance of vendors Vendor selection Request For Information (RFI) Request For Proposal (RFP) Proposal evaluation Vendor reference checks Contract negotiation Contract management Vendor management Re-compete vendors Project Management Methodologies Project organisation Starting up / initiating Planning / initiation a project Risk Quality Scope Work / Product Breakdown Structure PERT diagram / Gantt chart Cost Communication Application Management Software Development Life Cycle (SDLC) Software Quality Assurance (SQA) Requirements Development Testing Adoption (implementation) Maintenance Service Management Incident management Problem management Change management Business Continuity Management Standards and guidelines Objectives Context Interested parties Scope Roles and responsibilities Resources and competences Awareness and communication Documentation Business Impact Analysis Risk Management Guidelines Context establishment Identification Analysis Evaluation Treatment Communication Monitoring and control Information Security Management Standards Confidentiality Integrity Availability Controls types Guideline for controls selection Control categories Information security awareness Security incident response Information and Knowledge Management Information management Data management Information management - technologies Business intelligence Data management - technologies Best practices in data governance Pitfalls in data governance Business Change Management Business change Frameworks, models and techniques Needs identification Cloud computing Social media / digital marketing Big data Internet of Things (IoT) Quality Management Standards, guidelines and frameworks Objectives Activities Services review Customer feedback Customer survey Key Performance Indicators (KPI) Metrics Scorecards and reports Quality register Exam Actual course outline may vary depending on offering center. Contact your sales representative for more information.

AWS Certified Solutions Architect - Associate
By Nexus Human
Duration 4.5 Days 27 CPD hours This course is intended for This course is intended for individuals who have basic knowledge on cloud computing; on-premise system administrators; IT specialists, interested in AWS and Cloud Technologies. Overview Upon successful completion of this course, students will know how to design and deploy scalable, highly accessible and fault-tolerant systems in AWS. In this course, students will learn the main 'Managed Service' offered by AWS; How to design and deploy scalable, highly accessible and fault-tolerant systems in AWS; How to choose the most appropriate AWS service. Introduction Course overview Exam Blue Print Public clouds & cloud economics AWS Overview & Whitepapers Setting up AWS Account Identity and Access Management (IAM) Local users, groups & roles SAML providers Policies Cross Account Access Best practices & Examples Lab Exam highlights Sample questions Simple Storage Service (S3) & Glacier Buckets Objects Lifecycle Configurations and permissions Custom bucket policies Best Practices & Examples Lab Exam highlights Sample questions Virtual Private Cloud (VPC) VPC Internet gateway vs NAT Gateway Elastic IPs Subnets & Routing tables Security Groups & Network Access Lists VPC Peering & Endpoints Managed VPN Connections Best Practices & Examples Lab Exam highlights Sample questions Elastic Compute Cloud (EC2) Instances Amazon Machine Images(AMIs) Elastic Block Store (EBS) Network & Security Load Balancers (ELB) Auto Scaling Groups (ASG) Instance Management Best Practices & Examples Lab Exam highlights Sample questions Route 53 Hosted Zones Health checks Traffic flow Best Practices & Examples Lab Exam highlights Sample questions Relational Database Service (RDS) Engine types Performance & Resilience Subnet groups Best Practices & Examples Lab Exam highlights Sample questions CloudWatch Dashboard and Metrics CloudWatch logs CloudWatch rules Best Practices & Examples Lab Exam highlights Sample questions Other AWS Services Simple Overview CloudFront DynamoDB Elasticache Redshift SQS SWF SNS Elastic Transcoder API Gateway Kenesis CloudFormation Exam highlights Sample questions Multiple AWS Services exercise Lab 1 - Architecting multi-tier environment Lab 2 - Configure backup and monitoring Practice Exam Additional course details: Nexus Humans AWS Certified Solutions Architect - Associate training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AWS Certified Solutions Architect - Associate course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

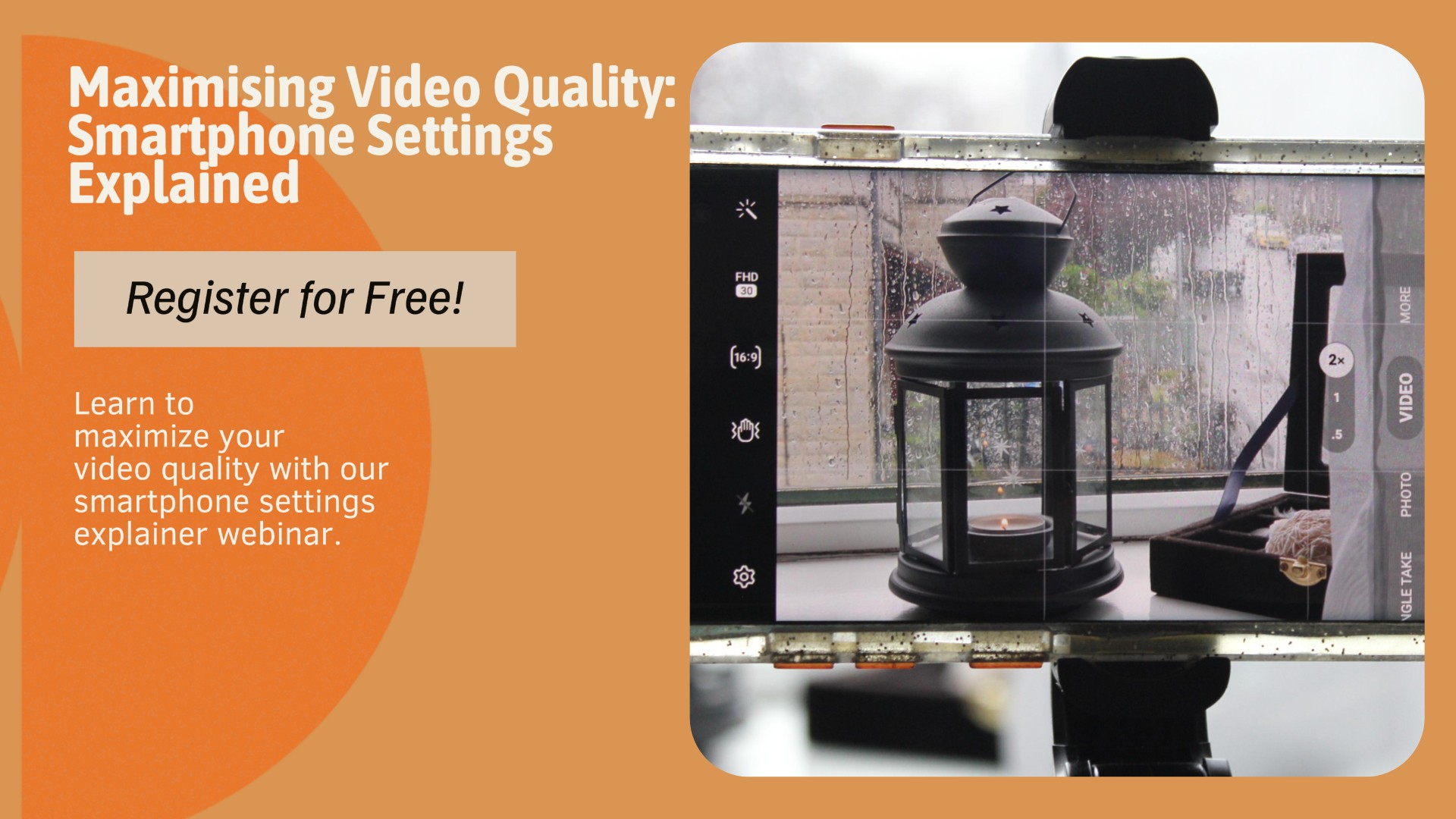
Maximise Video Quality: Smartphone Settings Explained (Free Webinar)
5.0(1)By Clockwork Eye Video Training
Join our free webinar to learn how to optimize the generic settings on any smartphone for creating high-quality videos. Perfect for small business owners and entrepreneurs looking to boost their online presence with professional video content.
Confidentiality and Data Protection
By Prima Cura Training
This confidentially & effective record keeping training course is aimed at assisting staff to understand what is expected of them regarding confidentiality, maintaining accurate up to date records and documents.

Cisco Deploying Cisco Jabber (DCJAB)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for System Engineers, Administrators, Architects, and Channel Partners Overview After you complete this course you will be able to: Describe the requirements for Jabber deploymentConfigure DNS, CUCM, IM&P, and Active Directory for Jabber integration This training course is designed to provide the necessary skills to deploy a Cisco Jabber© on premise solution. During class, students will train Cisco© Unified Communications administrators to meet the deployment requirements. Course Outline Module 1: Cisco Jabber Overview Module 2: Requirements for Jabber Deployment Module 3: Configuring CUCM for Jabber Deployment Module 4: Configuring IM&P for Jabber Deployment Module 5: DNS Configuration Module 6: Installing Cisco Jabber Module 7: Adding Photos to User Module 8: URI Dialing Module 9: Using Jabber Features Module 10: Collaboration Edge Module 11: Troubleshooting

This accredited qualification is ideal for anyone who requires training in conflict management. It is appropriate for a wide range of sectors and is suitable for anyone who has a customer facing role, dealing with service users or the public. It is also a useful qualification for individuals who would like a better understanding of how to prevent conflict situations from arising and feel more confident in being able to deal with situations if they arise. Subjects covered include the role of communication and the assessment of risks in conflict situations and follow up practices after such events. How long will it take me to achieve this qualification? This qualification is usually achieved by taking a 2 day course. How is the qualification assessed? The qualification is assessed through a 1 hour, 30-question, multiple-choice question examination. Candidates must achieve a score of at least 20 out of 30 in order to pass.
