- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
4246 Courses in Cardiff delivered Online
The Node JS: API Development with Swagger Interface Description Language course provides comprehensive training in creating APIs using Node.js and Swagger Interface Description Language. Participants will learn to develop robust APIs, design API specifications using Swagger, handle authentication, and implement API security. This course offers practical insights into building efficient APIs for web applications. Learning Outcomes: Understand the fundamentals of API development and its significance in web applications. Learn to set up and configure Node.js for building APIs. Explore the Swagger Interface Description Language for designing API specifications. Develop RESTful APIs using Node.js and Swagger for effective communication between applications. Implement authentication mechanisms and secure APIs using JWT (JSON Web Tokens). Master error handling and validation techniques for ensuring reliable API performance. Gain insights into API documentation and automatic generation using Swagger tools. Create interactive API documentation and test APIs using Swagger UI. Why buy this Node JS: API Development with Swagger Interface Description Language? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Node JS: API Development with Swagger Interface Description Language there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? Web developers interested in enhancing their API development skills. Node.js enthusiasts looking to build efficient and secure APIs. Backend developers aiming to understand Swagger for API specification. Software engineers seeking to master API authentication and security. Professionals wanting to improve their web application development knowledge. Prerequisites This Node JS: API Development with Swagger Interface Description Language does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Node JS: API Development with Swagger Interface Description Language was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path Node.js Developer: Specialize in building web applications using Node.js and APIs. Backend Developer: Design and implement APIs to support various web applications. API Developer: Develop, maintain, and optimize APIs for seamless data exchange. Web Application Developer: Create robust and efficient web applications using APIs. Software Engineer: Leverage API development skills for software product development. Course Curriculum Unit 01: Course Introduction Module 01: Introduction 00:01:00 Module 02: Goals & Prerequisites 00:03:00 Module 03: About the Instructor 00:01:00 Module 04: Open API Specification (OAS), Swagger & Node.js 00:09:00 Unit 02: Introduction to Swagger Module 01: Http and Swagger 00:09:00 Module 02: Swagger Tools 00:06:00 Module 03: Setup 00:06:00 Unit 03: Open API Specification (OAS) Module 01: Project Configuration 00:08:00 Module 02: Intro to Swagger Editor 00:06:00 Module 03: Project Explanation + GET Endpoint 00:13:00 Module 04: POST Endpoint 00:06:00 Module 05: PUT + DELETE Endpoint 00:08:00 Module 06: Challenge: Comments Endpoints 00:17:00 Unit 04: Node.js & Swagger Module 01: Get 00:11:00 Module 02: Post 00:08:00 Module 03: Put 00:07:00 Module 04: Delete 00:06:00 Module 05: Challenge: Add comment logic 00:18:00 Module 06: Deploy API in Heroku 00:06:00 Unit 05: Swagger Authorization with Json Web Tokens Module 01: Introduction to Json Web Tokens 00:07:00 Module 02: Authentication with Swagger and JWT 00:07:00 Unit 06: Final words Module 01: Thank you! 00:01:00 Assignment Assignment - Node JS: API Development with Swagger Interface Description Language 00:00:00

AWS Tutorial: AWS Solutions Architect and SysOps Administrator
By Packt
This course covers the best practices required for AWS Solutions Architect and AWS SysOps Administrator. Explore real-time 3-tier architecture addressing security, high availability, scalability, and resource optimization. Basic knowledge of Linux and a desire to adopt cloud models are all you need to get started.

Abrasive Wheels IIRSM & CPD Approved
By BAB Business Group
This course is aimed at anyone who uses abrasive wheels, or employs people who use abrasive wheels as part of their work. There are a wide range of tools and processes that use abrasive wheels and ensuring these are used correctly and safely is of paramount importance. Applications range from hand grinding to disc cutting. They can be used at all stages of a work process, for making preliminary cuts and scores in materials, or for fine polishing and finishing. Different wheels will have different properties and characteristics suitable for particular tasks. They also have different weaknesses and can pose different risks and hazards in handling and use. For this reason, it’s important that you always select the right abrasive wheel for the job and use it with the right machinery. This course covers the anatomy of an abrasive wheel, the dangers associated with their use, Storage and handling and much more.

AZ-204T00 Developing Solutions for Microsoft Azure
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Students in this course are interested in Azure development or in passing the Microsoft Azure Developer Associate certification exam. This course teaches developers how to create end-to-end solutions in Microsoft Azure. Students will learn how to implement Azure compute solutions, create Azure Functions, implement and manage web apps, develop solutions utilizing Azure storage, implement authentication and authorization, and secure their solutions by using KeyVault and Managed Identities. Students will also learn how to connect to and consume Azure services and third-party services, and include event- and message-based models in their solutions. The course also covers monitoring, troubleshooting, and optimizing Azure solutions. Prerequisites To be successful in this course, learners should have the following: Hands-on experience with Azure IaaS and PaaS solutions, and the Azure Portal. Experience writing in an Azure supported language at the intermediate level. (C#, JavaScript, Python, or Java) Ability to write code to connect and perform operations on, a SQL or NoSQL database product. (SQL Server, Oracle, MongoDB, Cassandra or similar) Experience writing code to handle authentication, authorization, and other security principles at the intermediate level. A general understanding of HTML, the HTTP protocol and REST API interfaces. 1 - Explore Azure App Service Examine Azure App Service Examine Azure App Service plans Deploy to App Service Explore authentication and authorization in App Service Discover App Service networking features 2 - Configure web app settings Configure application settings Configure general settings Configure path mappings Enable diagnostic logging Configure security certificates 3 - Scale apps in Azure App Service Examine autoscale factors Identify autoscale factors Enable autoscale in App Service Explore autoscale best practices 4 - Explore Azure App Service deployment slots Explore staging environments Examine slot swapping Swap deployment slots Route traffic in App Service 5 - Explore Azure Functions Discover Azure Functions Compare Azure Functions hosting options Scale Azure Functions 6 - Develop Azure Functions Explore Azure Functions development Create triggers and bindings Connect functions to Azure services 7 - Explore Azure Blob storage Explore Azure Blob storage Discover Azure Blob storage resource types Explore Azure Storage security features Discover static website hosting in Azure Storage 8 - Manage the Azure Blob storage lifecycle Explore the Azure Blob storage lifecycle Discover Blob storage lifecycle policies Implement Blob storage lifecycle policies Rehydrate blob data from the archive tier 9 - Work with Azure Blob storage Explore Azure Blob storage client library Create a client object Manage container properties and metadata by using .NET Set and retrieve properties and metadata for blob resources by using REST 10 - Explore Azure Cosmos DB Identify key benefits of Azure Cosmos DB Explore the resource hierarchy Explore consistency levels Choose the right consistency level Explore supported APIs Discover request units 11 - Work with Azure Cosmos DB Explore Microsoft .NET SDK v3 for Azure Cosmos DB Create stored procedures Create triggers and user-defined functions Explore change feed in Azure Cosmos DB 12 - Manage container images in Azure Container Registry Discover the Azure Container Registry Explore storage capabilities Build and manage containers with tasks Explore elements of a Dockerfile 13 - Run container images in Azure Container Instances Explore Azure Container Instances Run containerized tasks with restart policies Set environment variables in container instances Mount an Azure file share in Azure Container Instances 14 - Implement Azure Container Apps Explore Azure Container Apps Explore containers in Azure Container Apps Implement authentication and authorization in Azure Container Apps Manage revisions and secrets in Azure Container Apps Explore Dapr integration with Azure Container Apps 15 - Explore the Microsoft identity platform Explore the Microsoft identity platform Explore service principals Discover permissions and consent Discover conditional access 16 - Implement authentication by using the Microsoft Authentication Library Explore the Microsoft Authentication Library Initialize client applications 17 - Implement shared access signatures Discover shared access signatures Choose when to use shared access signatures Explore stored access policies 18 - Explore Microsoft Graph Discover Microsoft Graph Query Microsoft Graph by using REST Query Microsoft Graph by using SDKs Apply best practices to Microsoft Graph 19 - Implement Azure Key Vault Explore Azure Key Vault Discover Azure Key Vault best practices Authenticate to Azure Key Vault 20 - Implement managed identities Explore managed identities Discover the managed identities authentication flow Configure managed identities Acquire an access token 21 - Implement Azure App Configuration Explore the Azure App Configuration service Create paired keys and values Manage application features Secure app configuration data 22 - Explore API Management Discover the API Management service Explore API gateways Explore API Management policies Create advanced policies Secure APIs by using subscriptions Secure APIs by using certificates 23 - Explore Azure Event Grid Explore Azure Event Grid Discover event schemas Explore event delivery durability Control access to events Receive events by using webhooks Filter events 24 - Explore Azure Event Hubs Discover Azure Event Hubs Explore Event Hubs Capture Scale your processing application Control access to events Perform common operations with the Event Hubs client library 25 - Discover Azure message queues Choose a message queue solution Explore Azure Service Bus Discover Service Bus queues, topics, and subscriptions Explore Service Bus message payloads and serialization Explore Azure Queue Storage Create and manage Azure Queue Storage and messages by using .NET 26 - Monitor app performance Explore Application Insights Discover log-based metrics Instrument an app for monitoring Select an availability test Troubleshoot app performance by using Application Map 27 - Develop for Azure Cache for Redis Explore Azure Cache for Redis Configure Azure Cache for Redis Interact with Azure Cache for Redis by using .NET 28 - Develop for storage on CDNs Explore Azure Content Delivery Networks Control cache behavior on Azure Content Delivery Networks Interact with Azure Content Delivery Networks by using .NET

AI-050T00 Develop Generative AI Solutions with Azure OpenAI Service
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for The audience for this course includes software developers and data scientists who need to use large language models for generative AI. Some programming experience is recommended, but the course will be valuable to anyone seeking to understand how the Azure OpenAI service can be used to implement generative AI solutions. Note Generative AI is a fast-evolving field of artificial intelligence, and the Azure OpenAI service is subject to frequent changes. The course materials are maintained to reflect the latest version of the service at the time of writing. Azure OpenAI Service provides access to OpenAI's powerful large language models such as GPT; the model behind the popular ChatGPT service. These models enable various natural language processing (NLP) solutions to understand, converse, and generate content. Users can access the service through REST APIs, SDKs, and Azure OpenAI Studio. In this course, you'll learn how to provision Azure OpenAI service, deploy models, and use them in generative AI applications. Prerequisites Familiarity with Azure and the Azure portal. Experience programming with C# or Python. 1 - Get started with Azure OpenAI Service Access Azure OpenAI Service Use Azure OpenAI Studio Explore types of generative AI models Deploy generative AI models Use prompts to get completions from models Test models in Azure OpenAI Studio's playgrounds 2 - Build natural language solutions with Azure OpenAI Service Integrate Azure OpenAI into your app Use Azure OpenAI REST API Use Azure OpenAI SDK 3 - Apply prompt engineering with Azure OpenAI Service Understand prompt engineering Write more effective prompts Provide context to improve accuracy 4 - Generate code with Azure OpenAI Service Construct code from natural language Complete code and assist the development process Fix bugs and improve your code 5 - Generate images with Azure OpenAI Service What is DALL-E? Explore DALL-E in Azure OpenAI Studio Use the Azure OpenAI REST API to consume DALL-E models 6 - Use your own data with Azure OpenAI Service Understand how to use your own data Add your own data source Chat with your model using your own data Additional course details: Nexus Humans AI-050T00: Develop Generative AI Solutions with Azure OpenAI Service training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AI-050T00: Develop Generative AI Solutions with Azure OpenAI Service course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Optimizing Customer Assistance through Zendesk Excellence
By Compete High
ð Elevate Your Customer Assistance with 'Optimizing Customer Assistance through Zendesk Excellence' ð Are you ready to revolutionize your customer support game and take it to new heights? Introducing our groundbreaking online course: 'Optimizing Customer Assistance through Zendesk Excellence.' ð ð Unleash the Power of Zendesk: In today's fast-paced digital world, exceptional customer support is the key to business success. Our comprehensive course is designed to empower you with the knowledge and skills needed to harness the full potential of Zendesk, the leading customer service platform. Whether you're a beginner or a seasoned professional, this course is your gateway to mastering Zendesk like never before. ð ï¸ What You'll Learn: â Zendesk Essentials: Navigate through the platform effortlessly and maximize its core features. â Ticket Management Mastery: Streamline your support workflow for quicker issue resolution. â Automation Awesomeness: Implement time-saving automations for a more efficient support process. â Reporting and Analytics: Extract valuable insights to enhance your support strategy. â Integration Wizardry: Seamlessly integrate Zendesk with other tools for a unified support experience. ð¼ Who Can Benefit: Customer Support Representatives Service Desk Managers IT Professionals Business Owners Anyone committed to delivering exceptional customer experiences ð Course Highlights: ð¥ Engaging Video Lessons: Learn at your own pace with expert-led video tutorials. ð Comprehensive Study Material: Access downloadable resources for offline learning. ð¬ Interactive Discussions: Connect with fellow learners and industry experts. ð§ Practical Assignments: Apply your knowledge in real-world scenarios. ð Certification of Completion: Showcase your expertise with our accredited certification. ð Why Choose Our Course: Proven Expertise: Our instructors are Zendesk certified professionals with years of hands-on experience. Practical Focus: Learn skills you can apply immediately to enhance your customer support operations. Flexible Learning: Access the course anytime, anywhere, and on any device. ð Don't miss out on this opportunity to transform your customer assistance strategy! Enroll now in 'Optimizing Customer Assistance through Zendesk Excellence' and elevate your customer support to unprecedented levels of success. Course Curriculum Basic Overview 00:00 Pricing 00:00 Account Set Up 00:00 E-Mail Set Up 00:00 The Customers Experience with E-Mail Submission 00:00 Setting Up the Guide Center 00:00 Customer Experience with the Guide Center 00:00 Admin - Customer Settings 00:00 Adding Agents - Agent Settings 00:00 Ticket Settings 00:00 Setting a Customer Schedule 00:00 Admin - Account Settings - Part 1 00:00 Admin - Account Settings - Part 2 00:00 Admin - Business Rules - Automation 00:00 Business Rules - Triggers 00:00 Website Widget 00:00 Admin Channels - E-Mail - Part 1 00:00 Admin Channels - E-Mail - Part 2 00:00 Managing Ticket Views 00:00 Conclusion 00:00 Advanced Overview - Research 00:00 Social Media Channels 00:00 Enable Live Chat Channel 00:00 Ticket Forms 00:00 Ticket Fields 00:00 Managing the Ticket View 00:00 Adding Support Agents and Team Members 00:00 Managing Help Participants 00:00 Managing Applications -Autoresponders 00:00 Adding Applications - Mailchimp 00:00 Adding Applications - Webinars 00:00 Extending Applications - Zapier 00:00 Extending Applications - Zoom 00:00 Extending Applications - Stripe 00:00 Extending Applications - PayPal 00:00 Live Example - Editing Settings 00:00 Extending Applications - Zoom 00:00 Live Example - Customer Experience 00:00 Live Example - Extending Applications 00:00 Conclusion 00:00

Persuasive Design
By Experience Thinkers
Design for persuasion is a powerful approach that is too often overlooked. Learn the principles that are critical in designing both engaging and usable experiences.

Professional Certificate Course in Appraising E-commerce System in London 2024
4.9(261)By Metropolitan School of Business & Management UK
The aim of this course is to provide a comprehensive understanding of E-commerce Software systems and their practical applications. After the successful completion of this lecture, you will be able to: Understand and apply E-commerce Software systems. Understand E-commerce Websites, along with their types. Understand the concept of Supply Chain Management in E-commerce. Understand Product Sourcing, Strategic Sourcing, Outsourcing, and Offshoring in E-commerce. Understand What is an EFT Payment? And How Do e-Checks Work? Understanding Digital payment systems, currency and Payment Gateways. The aim of this course is to provide a comprehensive understanding of E-commerce Software systems and their practical applications. By the end of the course, students will be able to understand and identify different types of E-commerce websites and apply the concept of Supply Chain Management in E-commerce. Additionally, students will be able to comprehend the concepts of Product Sourcing, Strategic Sourcing, Outsourcing, and Offshoring in E-commerce. Furthermore, the course will also focus on the understanding of EFT Payment and e-Checks and how they work in the context of E-commerce. Students will also learn about Digital payment systems, currency, and Payment Gateways and their role in the E-commerce industry. Overall, the course will equip students with the knowledge and skills required to understand and apply various E-commerce Software systems and concepts to effectively operate in the dynamic E-commerce industry. The aim of this course is to provide a comprehensive understanding of E-commerce Software systems and their practical applications. By the end of the course, students will be able to understand and identify different types of E-commerce websites and apply the concept of Supply Chain Management in E-commerce. Additionally, students will be able to comprehend the concepts of Product Sourcing, Strategic Sourcing, Outsourcing, and Offshoring in E-commerce. Furthermore, the course will also focus on the understanding of EFT Payment and e-Checks and how they work in the context of E-commerce. Students will also learn about Digital payment systems, currency, and Payment Gateways and their role in the E-commerce industry. Overall, the course will equip students with the knowledge and skills required to understand and apply various E-commerce Software systems and concepts to effectively operate in the dynamic E-commerce industry. VIDEO - Course Structure and Assessment Guidelines Watch this video to gain further insight. Navigating the MSBM Study Portal Watch this video to gain further insight. Interacting with Lectures/Learning Components Watch this video to gain further insight. Appraising E-commerce System Self-paced pre-recorded learning content on this topic. Appraising E-Commerce System Put your knowledge to the test with this quiz. Read each question carefully and choose the response that you feel is correct. All MSBM courses are accredited by the relevant partners and awarding bodies. Please refer to MSBM accreditation in about us for more details. There are no strict entry requirements for this course. Work experience will be added advantage to understanding the content of the course. The certificate is designed to enhance the learner's knowledge in the field. This certificate is for everyone eager to know more and get updated on current ideas in their respective field. We recommend this certificate for the following audience. E-commerce System Appraiser E-commerce System Analyst E-commerce System Consultant E-commerce Business Analyst E-commerce Operations Manager E-commerce Technology Strategist E-commerce Architect E-commerce Project Manager E-commerce Quality Assurance Analyst E-commerce User Experience Designer Average Completion Time 2 Weeks Accreditation 3 CPD Hours Level Advanced Start Time Anytime 100% Online Study online with ease. Unlimited Access 24/7 unlimited access with pre-recorded lectures. Low Fees Our fees are low and easy to pay online.

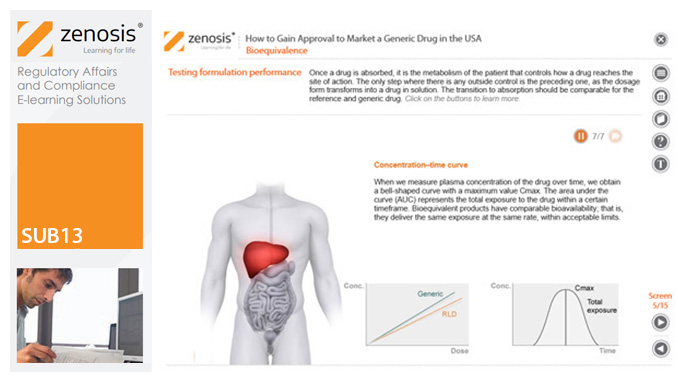
SUB13: How to Gain Approval to Market a Generic Drug in the USA
By Zenosis
This module outlines the legislative and regulatory context for the development of generic drugs and describes the essential role of the Abbreviated New Drug Application (ANDA) in gaining marketing approval. The use of information in the ‘Orange Book’ is explained, as is the role of patent certification in the application. The importance of establishing bioequivalence between a generic and its reference product is emphasised. The module specifies the content and format requirements for an ANDA submission and describes the FDA’s review and approval process. An outline is given of the Generic Drug User Fee Amendments (GDUFA) and the law’s effects on industry players.
24 Hour Flash Deal **25-in-1 Flutter App Development with Dart Mega Bundle** Flutter App Development with Dart Enrolment Gifts **FREE PDF Certificate**FREE PDF Transcript ** FREE Exam** FREE Student ID ** Lifetime Access **FREE Enrolment Letter ** Take the initial steps toward a successful long-term career by studying the Flutter App Development with Dart package online with Studyhub through our online learning platform. The Flutter App Development with Dart bundle can help you improve your CV, wow potential employers, and differentiate yourself from the mass. This Flutter App Development with Dart course provides complete 360-degree training on Flutter App Development with Dart. You'll get not one, not two, not three, but twenty-five Flutter App Development with Dart courses included in this course. Plus Studyhub's signature Forever Access is given as always, meaning these Flutter App Development with Dart courses are yours for as long as you want them once you enrol in this course This Flutter App Development with Dart Bundle consists the following career oriented courses: Course 01: Flutter & Dart Development Course Course 02: Building a TodoMVC Application in Vue, React and Angular Course 03: Mobile and Web Development with Ionic & Angular JS Course 04: Learn Spring & Angular Material with a Full Web Application Course 05: Code Your Own Drawing Application in Android Studio Course 06: Learn How To Create a Web App for iPad Course 07: Build Progressive Web Apps with Angular Course 08: Web Applications for Specialisation on Development Course 09: Complete Web Development Course 10: Start Your Career as Web Developer Course 11: Penetration Testing with OWASP ZAP: Mastery course Course 12: Web Application Penetration Testing Course 13: HTML and CSS Coding: Beginner to Advanced Course 14: Basics of WordPress Course 15: PHP Web Development with MySQL Course 16: JavaScript Functions Course 17: jQuery Masterclass Course: JavaScript and AJAX Coding Bible Course 18: Python Basic Programming Course 19: C Programming Language Course 20: C++ Programming Course 21: Advanced Diploma in User Experience UI/UX Design Course 22: Diploma in Front-End Web Development Course 23: Bash Scripting, Linux and Shell Programming Course 24: Responsive Web Design Course 25: Secure Programming of Web Applications The Flutter App Development with Dart course has been prepared by focusing largely on Flutter App Development with Dart career readiness. It has been designed by our Flutter App Development with Dart specialists in a manner that you will be likely to find yourself head and shoulders above the others. For better learning, one to one assistance will also be provided if it's required by any learners. The Flutter App Development with Dart Bundle is one of the most prestigious training offered at StudyHub and is highly valued by employers for good reason. This Flutter App Development with Dart bundle course has been created with twenty-five premium courses to provide our learners with the best learning experience possible to increase their understanding of their chosen field. This Flutter App Development with Dart Course, like every one of Study Hub's courses, is meticulously developed and well researched. Every one of the topics is divided into Flutter App Development with Dart Elementary modules, allowing our students to grasp each lesson quickly. The Flutter App Development with Dart course is self-paced and can be taken from the comfort of your home, office, or on the go! With our Student ID card you will get discounts on things like music, food, travel and clothes etc. In this exclusive Flutter App Development with Dart bundle, you really hit the jackpot. Here's what you get: Step by step Flutter App Development with Dart lessons One to one assistance from Flutter App Development with Dartprofessionals if you need it Innovative exams to test your knowledge after the Flutter App Development with Dartcourse 24/7 customer support should you encounter any hiccups Top-class learning portal Unlimited lifetime access to all twenty-five Flutter App Development with Dart courses Digital Certificate, Transcript and student ID are all included in the price PDF certificate immediately after passing Original copies of your Flutter App Development with Dart certificate and transcript on the next working day Easily learn the Flutter App Development with Dart skills and knowledge you want from the comfort of your home CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Flutter App Development with Dart training is suitable for - Students Recent graduates Job Seekers Individuals who are already employed in the relevant sectors and wish to enhance their knowledge and expertise in Flutter App Development with Dart Requirements To participate in this Flutter App Development with Dart course, all you need is - A smart device A secure internet connection And a keen interest in Flutter App Development with Dart Career path You will be able to kickstart your Flutter App Development with Dart career because this course includes various courses as a bonus. This Flutter App Development with Dart is an excellent opportunity for you to learn multiple skills from the convenience of your own home and explore Flutter App Development with Dart career opportunities. Certificates CPD Accredited Certificate Digital certificate - Included CPD Accredited e-Certificate - Free CPD Accredited Hardcopy Certificate - Free Enrolment Letter - Free Student ID Card - Free
