- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3726 Courses in Bradford delivered Live Online
AZ-500T00 Microsoft Azure Security Technologies
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for Azure Security Engineers who are planning to take the associated certification exam, or who are performing security tasks in their day-to-day job. This course would also be helpful to an engineer that wants to specialize in providing security for Azure-based digital platforms and play an integral role in protecting an organization's data. This course provides IT Security Professionals with the knowledge and skills needed to implement security controls, maintain an organization?s security posture, and identify and remediate security vulnerabilities. This course includes security for identity and access, platform protection, data and applications, and security operations. Prerequisites AZ-104T00 - Microsoft Azure Administrator Security best practices and industry security requirements such as defense in depth, least privileged access, role-based access control, multi-factor authentication, shared responsibility, and zero trust model. Be familiar with security protocols such as Virtual Private Networks (VPN), Internet Security Protocol (IPSec), Secure Socket Layer (SSL), disk and data encryption methods. Have some experience deploying Azure workloads. This course does not cover the basics of Azure administration, instead the course content builds on that knowledge by adding security specific information. Have experience with Windows and Linux operating systems and scripting languages. Course labs may use PowerShell and the CLI. 1 - Manage identities in Microsoft Entra ID Secure users in Microsoft Entra ID Secure groups in Microsoft Entra ID Recommend when to use external identities Secure external identities Implement Microsoft Entra Identity protection 2 - Manage authentication by using Microsoft Entra ID Configure Microsoft Entra Verified ID Implement multifactor authentication (MFA) Implement passwordless authentication Implement password protection Implement single sign-on (SSO) Integrate single sign-on (SSO) and identity providers Recommend and enforce modern authentication protocols 3 - Manage authorization by using Microsoft Entra ID Configure Azure role permissions for management groups, subscriptions, resource groups, and resources Assign built-in roles in Microsoft Entra ID Assign built-in roles in Azure Create and assign a custom role in Microsoft Entra ID Implement and manage Microsoft Entra Permissions Management Configure Microsoft Entra Privileged Identity Management Configure role management and access reviews by using Microsoft Entra Identity Governance Implement Conditional Access policies 4 - Manage application access in Microsoft Entra ID Manage access to enterprise applications in Microsoft Entra ID, including OAuth permission grants Manage app registrations in Microsoft Entra ID Configure app registration permission scopes Manage app registration permission consent Manage and use service principals Manage managed identities for Azure resources Recommend when to use and configure a Microsoft Entra Application Proxy, including authentication 5 - Plan and implement security for virtual networks Plan and implement Network Security Groups (NSGs) and Application Security Groups (ASGs) Plan and implement User-Defined Routes (UDRs) Plan and implement Virtual Network peering or gateway Plan and implement Virtual Wide Area Network, including secured virtual hub Secure VPN connectivity, including point-to-site and site-to-site Implement encryption over ExpressRoute Configure firewall settings on PaaS resources Monitor network security by using Network Watcher, including NSG flow logging 6 - Plan and implement security for private access to Azure resources Plan and implement virtual network Service Endpoints Plan and implement Private Endpoints Plan and implement Private Link services Plan and implement network integration for Azure App Service and Azure Functions Plan and implement network security configurations for an App Service Environment (ASE) Plan and implement network security configurations for an Azure SQL Managed Instance 7 - Plan and implement security for public access to Azure resources Plan and implement Transport Layer Security (TLS) to applications, including Azure App Service and API Management Plan, implement, and manage an Azure Firewall, Azure Firewall Manager and firewall policies Plan and implement an Azure Application Gateway Plan and implement an Azure Front Door, including Content Delivery Network (CDN) Plan and implement a Web Application Firewall (WAF) Recommend when to use Azure DDoS Protection Standard 8 - Plan and implement advanced security for compute Plan and implement remote access to public endpoints, Azure Bastion and just-in-time (JIT) virtual machine (VM) access Configure network isolation for Azure Kubernetes Service (AKS) Secure and monitor AKS Configure authentication for AKS Configure security for Azure Container Instances (ACIs) Configure security for Azure Container Apps (ACAs) Manage access to Azure Container Registry (ACR) Configure disk encryption, Azure Disk Encryption (ADE), encryption as host, and confidential disk encryption Recommend security configurations for Azure API Management 9 - Plan and implement security for storage Configure access control for storage accounts Manage life cycle for storage account access keys Select and configure an appropriate method for access to Azure Files Select and configure an appropriate method for access to Azure Blob Storage Select and configure an appropriate method for access to Azure Tables Select and configure an appropriate method for access to Azure Queues Select and configure appropriate methods for protecting against data security threats, including soft delete, backups, versioning, and immutable storage Configure Bring your own key (BYOK) Enable double encryption at the Azure Storage infrastructure level 10 - Plan and implement security for Azure SQL Database and Azure SQL Managed Instance Enable database authentication by using Microsoft Entra ID Enable and monitor database audit Identify use cases for the Microsoft Purview governance portal Implement data classification of sensitive information by using the Microsoft Purview governance portal Plan and implement dynamic mask Implement transparent data encryption? Recommend when to use Azure SQL Database Always Encrypted 11 - Plan, implement, and manage governance for security Create, assign, and interpret security policies and initiatives in Azure Policy Configure security settings by using Azure Blueprint Deploy secure infrastructures by using a landing zone Create and configure an Azure Key Vault Recommend when to use a dedicated Hardware Security Module (HSM) Configure access to Key Vault, including vault access policies and Azure Role Based Access Control Manage certificates, secrets, and keys Configure key rotation Configure backup and recovery of certificates, secrets, and keys 12 - Manage security posture by using Microsoft Defender for Cloud Implement Microsoft Defender for Cloud Identify and remediate security risks by using the Microsoft Defender for Cloud Secure Score and Inventory Assess compliance against security frameworks and Microsoft Defender for Cloud Add industry and regulatory standards to Microsoft Defender for Cloud Add custom initiatives to Microsoft Defender for Cloud Connect hybrid cloud and multicloud environments to Microsoft Defender for Cloud Identify and monitor external assets by using Microsoft Defender External Attack Surface Management 13 - Configure and manage threat protection by using Microsoft Defender for Cloud Enable workload protection services in Microsoft Defender for Cloud, including Microsoft Defender for Storage, Databases, Containers, App Service, Key Vault, Resource Manager, and DNS Configure Microsoft Defender for Servers Configure Microsoft Defender for Azure SQL Database Manage and respond to security alerts in Microsoft Defender for Cloud Configure workflow automation by using Microsoft Defender for Cloud Evaluate vulnerability scans from Microsoft Defender for Server 14 - Configure and manage security monitoring and automation solutions Monitor security events by using Azure Monitor Configure data connectors in Microsoft Sentinel Create and customize analytics rules in Microsoft Sentinel Configure automation in Microsoft Sentinel Additional course details: Nexus Humans AZ-500T00 Microsoft Azure Security Technologies training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AZ-500T00 Microsoft Azure Security Technologies course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

COMMUNICATIONS SKILLS FOR LEADERS
By Inclusive Solutions
Whatever your position in the team, good communications skills are vital. They are at the centre of every work place interaction and can make a real difference to your work environment. Here’s a worthwhile day to increase your skills in this area. These skills will not only help your personal growth but they will increase job satisfaction and in turn relationships with adults and children. Course Category Team Building and Leadership Visioning and Problem Solving Strategic Work Early Years Description “The leaders who work most effectively, it seems to me, never say ‘I’. And that’s not because they have trained themselves not to say ‘I’. They don’t think ‘I’. They think ‘we’; they think ‘team’. They understand their job to be to make the team function. They accept responsibility and don’t sidestep it, but ‘we’ gets the credit…. This is what creates trust, what enables you to get the task done.”PETER DRUCKER. Whatever your position in the team, good communications skills are vital. They are at the centre of every work place interaction and can make a real difference to your work environment. Here’s a worthwhile day to increase your skills in this area. These skills will not only help your personal growth but they will increase job satisfaction and in turn relationships with adults and children. With these new skills you will also increase your abilities in co-operative partnerships and network building. Communication is at the core of what you do; it’s how we influence people. We use it for persuading others, creating alliances, gaining support, motivating others and teaching. Being good at communicating with others will allow you to influence them and this in turn will make you more effective whilst making your job easier. A lot of our time at work consists of acting, taking or giving instructions. Past research shows that lack of good communication at the work place is not uncommon. This has a high cost including tension amongst staff and lower trust levels and effectiveness. Problems can be caused when communication problems result in instructions being misinterpreted. A simple discussion can be turned into a conflict just by poor communication. What communication skills are needed in the 21st century for the most effective leaders and managers of schools, colleges and early years settings? Would the following qualities make sense to you in describing your communication with staff, parents and your wider community? a high concern for both people and outcomes a style motivated by relationship building the flexibility to change leadership styles depending on the challenge the ability to follow as well as lead a team leadership style< able to communicate and engage the emotional support of staff quiet leadership with restraint, modesty and tenacity Perhaps you would add to or challenge this list of attributes? How do you deal with ‘yes buts’ and those who don’t do what you ask them to do? How do you motivate? How do you encourage? During this training we will explore your communication in a range of challenging situations and build consensus around desirable communication skills. Testimonials Be the first to comment on this training… Learning Objectives To explore effective communication skills for leaders and managers Self reflection and feedback opportunities To develop and extend your repertoire of communication skills Deepen your understanding of team members who don’t do what you ask and expect them to do Who Is It For? Leaders and managers of schools, colleges and early years settings Course Content Exploration of typical challenging situations- skill practice Building Shared Vision for communication Opportunities to develop and extend your communication skills for leadership in a safe environment

Level 3 Certificate in Understanding Autism
By Step Into Learning
Level 3 Certificate in Understanding Autism will provide further learning in autism for those that have already completed the level 2 qualification.

Mastering Telecoms Regulation
By Cullen International SA
Would you like to get up to speed on the key debates on telecoms regulation or refresh your understanding of the broader range of regulatory issues? Thanks to our online Telecoms Masterclass, you will understand all you need to know about telecoms regulation in the EU and other regions when applicable and relevant.

Time Management and Productivity: Virtual In-House Training
By IIL Europe Ltd
Time Management and Productivity: Virtual In-House Training Effective time management reduces stress and helps you better adhere to commitments. This course is designed to help you identify personal and organizational priorities and gain better control of where you focus your attention. You will explore the importance of planning and organizing, and you will practice sorting through and setting priorities. You will also learn how to set better time boundaries and manage the demands of others. Working with a time management framework, you will use a set of practical techniques to organize and manage your work to better deliver on your commitments. Techniques for overcoming procrastination will be addressed, as well as strategies for dealing with information overload. What you Will Learn Plan and prioritize each day's activities in a more efficient, productive manner Establish strategies to execute priorities and overcome procrastination Understand how to make trade-offs when faced with fire drills How to set and communicate boundary conditions Getting Started Introductions Course orientation Participants' expectations Foundation Concepts Exercise: A day in your life Resources to implement change Mind-set Tool-set Skill-set What is your time really worth? The dynamics of procrastination The myth of multi-tasking Brain Rules - how to optimize your efficiency Organization and Prioritization Time management best practices Goal setting Exercise: Identifying your priorities The importance of organization Time management framework Prioritizing time Time Management Techniques Tips for managing time Nine ways to overcome procrastination The STING technique Managing your time o Handling unplanned urgencies o Dealing with information overload Delegation and managing others' time Creating your personal action plan Summary Course summary and next steps Applying what you have learned

Cyber Security training course description The reliance of the world on the Internet and computer systems means the protection of information systems is vitally important. This is even more important smart devices and the Internet of Things increase the number of devices. This Cyber Security provides a concise overview on the threats and attacks that can happen along with the counter measures that can be taken. What will you learn Recognise the different types of attack. Describe the attacks that can be made against information systems. Describe the counter measures available. Cyber Security training course details Who will benefit: Non-technical staff working with computers. Prerequisites: None. Duration 1 day Cyber Security training course contents What is Cyber Security? Computer security, Policies, Types of security breach, denial of service, data manipulation, data theft, data destruction, security checklists, incident response. Attacks Physical access, Social engineering, Privilege escalation, Malware, Trojans, worms, viruses, rootkits, Backdoors, Denial of Service (DOS), Distributed DOS, Eavesdropping, Spoofing, Man the middle tampering. Countermeasures Prevention, detection, response. Physical, user accounts, Firewalls, IDS, AAA, authentication, cryptography, encryption, data integrity. Cyber security standards ETSI, ISO 27001, 27002, NIST, ISA/IEC 62443.

GDPR Awareness Training
By Training Centre
The GDPR came into effect in May 2018. This legislation is designed to guide organisations in their obligations relative to the processing of personal and sensitive data. About This Course Organisations are required to comply with the GDPR regardless of their size of business. If you process 'personal data', there is a potential need to be compliant with the legislation. The scope of the GDPR considers how this information is collected, stored, used, transported, shared and disposed of. To ensure organisations' understand this obligation, this interactive one-day course considers both scoping and auditing of an organisations processing activities, as well as an understanding of compliance with GDPR. Learning Outcomes; GDPR - what is it and how does it apply to us? Personal and sensitive data Lawful basis for processing Consent and the GDPR The Data Protection Act 2018 Data Subject rights The role of the ICO Data breach or Incident? Privacy by Design and by default GDPR Audit checklist Prerequisites There are no prerequisites to attend this course, however all attendees are expected to have a basic understanding of the Data Protection principles. What's Included? Refreshments & Lunch (Classroom courses only) Course Slide Deck Quizzes Who Should Attend? The course is designed for any member of the organisation whose role includes processing personal data. Data Protection Officers, Information Security team members or Information Governance Leads who may also see benefit in attending. Accreditation Assessment There is no exam with this course but delegates do receive a Course Attendance Certificate and an 8 hour CPD Certificate. Provided by This course is Accredited by NACS and administered by the IECB

Internet of Things training course description A concise overview course covering The Internet of Things and the technologies involved. Particular emphasis is placed on the high level architecture of IoT and the benefits achievable. What will you learn Describe the structure of the IoT List the technologies involved in IoT. Explain how IoT works. Internet of Things training course details Who will benefit: Non-technical staff working with IoT. Prerequisites: None. Duration 1 day Internet of Things training course contents What is IoT The Internet, what is IoT? IoT and M2M, IoT technologies, IoT architecture. Wired and wireless communication. IoT applications; Smart houses, smart cities, smart cars, wearable, environment, other domain specific IoTs. IoT architecture Physical objects, virtual objects, cloud computing, data capture, communications. Big data. Components Hardware, sensors, actuators, chips, firmware, embedded systems. Open source platforms. Power options: Battery, solar, PoE. IoT communication RF, ZigBee, Bluetooth, Bluetooth LE, RFID, WiFi, 802.11ah, mobile technologies. Wired. Arduino (as an example) Microcontrollers, the platform, development, Arduino software, reading from sensors, I2C, SPI. Arduino and the Internet, HTTP, WiFi, GSM. The cloud and IoT: Pachube, nimbits, ThingSpeak Security in IoT Authentication, Encryption, secure booting, firewalls.

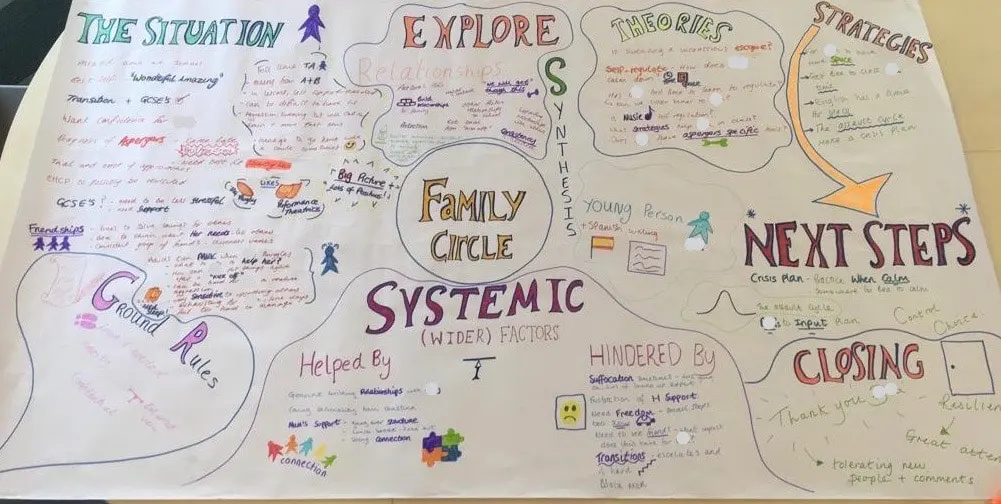
FAMILY CIRCLES
By Inclusive Solutions
Click to read more about this training, in which we demonstrate a live problem solving approach which is based on the active participation of family members. Course Category Inclusion Parents and Carers Behaviour and relationships Problem Solving Description In this training we demonstrate a live problem solving approach which is based on the active participation of family members. ‘Family Circles’ is an evolving new approach to problem solving with families and is based on our years of family work and the development and use of the Circle of Adults process. Inspired by our own Parent Solutions work and the Circle of Adults process as well as Family Group Conferencing and other Restorative Interventions we bring you Family Circles. Essentially the approach involves gathering a family together for a process that is facilitated but majors on the family members offering each other their wisdom and ideas. The approach is capacity focused, person centred approach to working with families rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for or doing things to families. This training can be modelled with a group of professionals or better still with a family. In our work with families we develop the importance of naming stories or theories and seeking linkages and synthesis between what is found out and explored about the family situation and its history. We like participants to sit with the uncertainty, to reflect on the question ‘why’ but without judgement of each other. Deeper reflections may span a whole range of perspectives from ‘within person’ considerations, to situational or systemic possibilities. Health or emotional issues can be reflected on alongside organisational or transactional aspects of what is going on for the family. The better the shared understanding the better the strategy or actions which emerge from these meetings. Quality hypotheses with a close fit to reality lead to more effective implementation in the real world. We encourage ‘loose’ thinking, a search for connections, deeper listening, an ‘open mind’, speculation and exploration without moral judgements. From this stance self-reflection as well as reflection on the situation can produce remarkable insights. The quality of theories or new stories generated is directly influenced by family members’ experiences and the models of learning, behaviour and emotion, systems, educational development, change and so on that they have been exposed to. Learning Objectives To provide opportunities for: Shared problem solving in a safe exploratory climate in which the family will find its own solutions. Individuals to reflect on their own actions and strategies An exploration of whole-family processes and their impact Emotional support and shared understandings of issues at a child, parent, family, school and community level. Feed back to each other on issues, ideas and strategies that are agreed to be worth sharing with them. Who Is It For? Anyone interested in working with families in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. Social Care teams School staff Community organisers Educational Psychologists Course Content True family empowerment Deepening shared stories and understandings Facilitating groups Problem solving process Handling family group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Process: Family members are welcomed: Introductions are carried out, ground rules and aims clarified whilst coffee is drunk. A recap from the last session is carried out: To follow up developments and reflections after the last meeting. One issue is selected for the main focus Issue presentation: The family member who raised the concern is asked questions to tell the ‘story’ of the issue or problem. Additional questions/information from the group about the problem are gathered: Ground rules may need to be observed carefully here. Individual participants need to be kept focused and prevented from leaping to premature conclusions or to making ‘helpful’ suggestions about strategy. Relationship aspects to the problem are explored. Metaphors and analogies are invited. How would a fly on the wall see your relationship? If you were alone together on a desert island, what would it be like? Impact of previous relationships/spillage from one relationship to another are explored. Eg what situation they are reminded of? For instance, does this situation remind you of any of those angry but helpless feelings you had with your other son when he was an adolescent? This provides opportunities to reflect on how emotions rub off on other people. The parent feels really frustrated, and on reflection we can see that so does the child System/Organisation factors (Family system/school and community systems and so on): What aspects help or hinder the problem? For instance, does the pastoral system of the local school provide space, or time and skilled personnel able to counsel this young person and work actively with their parents? Synthesis. At this stage the Graphic facilitator summarises what they have heard. They then go on to describe linkages and patterns in what they have heard. This can be very powerful. The person doing the graphic work has been able to listen throughout the presentation process and will have been struck by strong messages, emotions and images as they have arisen. The story and meaning of what is happening in the situation may become a little clearer at this point. Typical links may be ‘mirrored emotions’ strong themes such as loss and separation issues, or repeated processes such as actions triggering rejection. This step provides an excellent grounding for the next process of deepening understanding. What alternative strategies/interventions are open to be used? Brainstormed and recorded. ’Either/ors’ need to be avoided at this time also. This needs to be a shared session in which the family member who is presenting the concern contributes as much as anyone. Care is needed to ensure that this person is not overloaded with other people’s strategies. The final selection of strategy or strategies from the brainstormed list is the problem presenter’s choice. Strategies might include: a special time for the young person, a meeting with the child’s parents to explore how she is being managed at home and to share tactics, a home-school diary, counselling, or an agreed action plan that all are aware of, agreed sanctions and rewards and so forth. Strategies may productively involve processes of restitution and restoration, when ‘sorry’ is not enough. Making it right, rather than punishments or rewards, may then becomes the focus. First Steps. The problem presenter is finally asked to agree one or two first steps which they can carry out over the next 3-7 days. It can help to assign a ‘coach’ who will check in with them to ensure they have carried out the action they have named. This is a time to be very specific. Steps should be small and achievable. The person is just ‘making a start’. A phone call, or making an agreement with a key other person not present at the meeting would be ideal examples. Final reflections. Sometimes referred to as a ‘round of words’ help with closure for all involved. Reflections are on the process not the problem. In large families this is best done standing in a circle. In smaller groups all can remain sitting. Passing around a ‘listening stick’ or something similar such as a stone or light heighten the significance of the process ending and improve listening. Finally the problem presenter is handed the ‘Graphic’ this is their record of the meeting and can be rolled and presented ceremoniously by the facilitators for maximum effect! If you liked this course you may well like: Parent Solutions
PUPIL PARTICIPATION: LISTENING TO THE POWERFUL VOICE OF YOUNG PEOPLE
By Inclusive Solutions
Local authorities are being encouraged to seek the views of young people in relation to the services they receive. Schools and the whole range of support services (e.g. behaviour support, youth offending teams, social services, CAMHS etc.) are being expected to routinely ask young people for their views. This goes beyond involving young people in plans that concern them e.g care plans, individual education plans, pastoral support plans etc. Online Course now available via Teachable Platform – Ask the Children Learn at your own pace… lots of text and video support Course Category Peer Support Description Local authorities are being encouraged to seek the views of young people in relation to the services they receive. Schools and the whole range of support services (e.g. behaviour support, youth offending teams, social services, CAMHS etc.) are being expected to routinely ask young people for their views. This goes beyond involving young people in plans that concern them e.g care plans, individual education plans, pastoral support plans etc. This training will focus on how young people can be effectively engaged in giving their views and will present a model for use in evaluating services to young people based on the concept of resilience. This model enables young people to be clear about what has helped and hindered them in being able to overcome difficulties. It also provides a framework for evaluating the extent to which services are reducing risk and increasing protective factors to enable young people to develop the resilience. Testimonials ‘Yet again inspiring and opening more doors than I can go through’? ‘This opened a lot of avenues for thought and reflection. It will help me to help colleagues to see where they can improve practice to create a more inclusive environment within the whole school.’ ‘Some great ideas and restored my self belief! Fantastic’ Learning Objectives Strategies for engaging young people Knowledge and Understanding of resilience In relation to system and environmental factors Strategies for reducing risk and increasing protective factors In relation to Individual young people and services Evaluation framework for services to young people Who Is It For ? Youth offending teams Social services CAMHS Primary and secondary teachers Heads and Deputies SENCOs Learning Support and Guidance staff Advanced Skills Teachers Parents Local Authority Support Services Community Development workers Early Years and School based Practitioners Social work staff Health Services Course Content The course answers the questions : How can we truly involve pupils? Practically how do we go about listening to pupils views? What if we do not like what they tell us? How can we involve our most disaffected young people? Key themes Tools for engaging young people and gaining their views The concept of resilience System and environmental risk and protective factors that impact on young people’s resilience Reducing risk and Increasing protective factors Resilience planning for Individuals and services Evaluating services to young people If you liked this course you may well like: CIRCLES OF FRIENDS
