- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
224 Communication Skills courses in Watford
Security+ training course description A hands on course aimed at getting delegates successfully through the CompTia Security+ examination. What will you learn Explain general security concepts. Describe the security concepts in communications. Describe how to secure an infrastructure. Recognise the role of cryptography. Describe operational/organisational security. Security+ training course details Who will benefit: Those wishing to pass the Security+ exam. Prerequisites: TCP/IP foundation for engineers Duration 5 days Security+ training course contents General security concepts Non-essential services and protocols. Access control: MAC, DAC, RBAC. Security attacks: DOS, DDOS, back doors, spoofing, man in the middle, replay, hijacking, weak keys, social engineering, mathematical, password guessing, brute force, dictionary, software exploitation. Authentication: Kerberos, CHAP, certificates, usernames/ passwords, tokens, biometrics. Malicious code: Viruses, trojan horses, logic bombs, worms. Auditing, logging, scanning. Communication security Remote access: 802.1x, VPNs, L2TP, PPTP, IPsec, RADIUS, TACACS, SSH. Email: S/MIME, PGP, spam, hoaxes. Internet: SSL, TLS, HTTPS, IM, packet sniffing, privacy, Javascript, ActiveX, buffer overflows, cookies, signed applets, CGI, SMTP relay. LDAP. sftp, anon ftp, file sharing, sniffing, 8.3 names. Wireless: WTLS, 802.11, 802.11x, WEP/WAP. Infrastructure security Firewalls, routers, switches, wireless, modems, RAS, PBX, VPN, IDS, networking monitoring, workstations, servers, mobile devices. Media security: Coax, UTP, STP, fibre. Removable media. Topologies: Security zones, DMZ, Intranet, Extranet, VLANs, NAT, Tunnelling. IDS: Active/ passive, network/host based, honey pots, incident response. Security baselines: Hardening OS/NOS, networks and applications. Cryptography basics Integrity, confidentiality, access control, authentication, non-repudiation. Standards and protocols. Hashing, symmetric, asymmetric. PKI: Certificates, policies, practice statements, revocation, trust models. Key management and certificate lifecycles. Storage: h/w, s/w, private key protection. Escrow, expiration, revocation, suspension, recovery, destruction, key usage. Operational/Organisation security Physical security: Access control, social engineering, environment. Disaster recovery: Backups, secure disaster recovery plans. Business continuity: Utilities, high availability, backups. Security policies: AU, due care, privacy, separation of duties, need to know, password management, SLAs, disposal, destruction, HR policies. Incident response policy. Privilege management: Users, groups, roles, single sign on, centralised/decentralised. Auditing. Forensics: Chain of custody, preserving and collecting evidence. Identifying risks: Assets, risks, threats, vulnerabilities. Role of education/training. Security documentation.

Essential 5G training course description This course is designed to give delegates an explanation of the technologies and interworking requirements of the next generation of cellular communications. It is not a definitive set of descriptions but a possibility of the final deployment. we will investigate the 10 pillars for 5G which will include various Radio Access Technologies that are required to interwork smoothly. We will look at the 4G Pro features and other RATs. What will you learn List the ten pillars of 5G deployment. Describe the 5G Internet. Explain virtualization and RAT virtulization. Describe Software Defined Networks (SDN). Explain carrier aggregation. Describe the mobile cloud. Explain an overall picture of 5G architecture. Essential 5G training course details Who will benefit: Anyone looking for an understanding of the technologies and interworking requirements of the next generation of cellular communications. Prerequisites: None. Duration 3 days Essential 5G training course contents Drivers for 5G 5G Road Map, 10 Pillars of 5G, evolving RATs, oSON, MTCm, mm-wave, backhaul, EE, new spectrum, spectrum sharing, RAN virtualisation. 4G LTE Advanced MIMO technology in release 8, Downlink & uplink MIMO R8, MIMO technology in LTE advanced, Downlink 8-layer SU-MIMO, Downlink MU-MIMO, Uplink MU-MIMO, Uplink transmit diversity, Coordinated multi-point operation (CoMP), Independent eNB & remote base station configurations, Downlink CoMP. ICIC & eICIC ICIC, Homogeneous to heterogeneous network evolution, Introduction to eICIC, Macro-pico scenario, Macro-femto scenario, Time orthogonal frequencies. Almost Blank Subframe (ABS). Carrier aggregation Component carriers (CC), CC aggregation deployments, Intra-band contiguous solutions, Intra-band non-contiguous solutions, Inter-band non-contiguous solutions, CA bandwidth classes, Aggregated transmission bandwidth configurations (ATBC), Possible carrier aggregation configs. eIMTA TDD UL-DL reconfig. for traffic adaptation, Reconfig. mechanisms, Interference mitigation schemes, Dynamic & flexible resource allocation. 5G architectures 5G in Europe, horizon 2020 framework, 5G infrastructure PPP, METIS project, 5G in North America, academy research, company R&D, 5G specifications. The 5G internet High-level view of Cloud Services, The Internet of Things & context awareness, Network reconfiguration & virtualization support, server proliferation, how VMs fix underutilised server problem, enter the hypervisor, why are VM such a big deal? SDN, evolution of the data centre network, high availability, low latency, scalability, security, cost model explodes, service-oriented API. OpenFlow switches, OpenFlow controllers, how SDN works. The big picture, pulling it all together, why the network had to change, how SDN & NFV tie together. Evolutionary approach to the internet, architectures for distributed mobility management, MEDIEVAL & MEDIVO projects, a clean slate approach, mobility first architecture. VNet, INM, NetInf, ForMux, MEEM. Generic Path (GP) & anchorless mobility (AM), Quality of Service support, network resource provisioning, resourcing inside a network. IntServ, RSVP, DiffServ, CoS. Emerging approach for resource over- provisioning, example use case architecture for scalable resource control scenarios in the 5G internet. Integrating SDN/NFV for efficient resource over-reservation control, control information repository, service admission control policies, network resource provisioning, control enforcement functions, network configurations & operations. Small cells for 5G Average spectral efficiency evolution, WiFi & Femto cells, Capacity limits. Achievable gains with densifications, multi-antenna techniques, small cells. Mobile data demand, approach & methodology, subscriber density and traffic demand projections to 2020. Demand versus capacity, global mobile data traffic increase modelling, country level backhaul traffic projections, Small cell challenges, backhaul, spectrum, automation. Cooperation for next gen wireless networks Diversity & relaying strategies, cooperation & network coding, ARQ & MAC protocols, NCCARQ & PRCSMA packet exchange, Physical layer impact on MAC protocol analysis, NCCARQ overview, PHY layer impact, Case study on NCCARQ. Mobile clouds Mobile cloud, Mobile cloud enablers, mobile user domain, wireless technologies, WWAN WLAN and WPAN range, Bluetooth, IEEE.802.15.4 & software stacks, infrared, near field communications (NFC). Network coding, store & forward vs compute & forward, linear network coding, random linear coding. Security for 5G communications Potential 5G communication systems architectures, Security issues & challenges. Mobile malware attacks targeting the UE, 5G mobile botnets, access networks, attacks on 4G networks, C-RNTI & packet sequence number based UE location tracking, false buffer status reports attacks, message insertion attacks, HeNB attacks, physical attacks, credential attacks, configuration and protocol attacks, attacks on MON, user data & identity attacks, mobile operator's core network, DDoS attacks targeting MON, signalling amplification, HSS saturation, external IP networks.

Facilitation Skills Training Course (£1450 total for this 2-day course for a group of 4-10 participants)
By Buon Consultancy
Facilitation Skills Training

Satellite comms training course description A theory based course providing a foundation in how satellite communication systems work and the terminology used in the field. What will you learn Describe the satellite communications architecture. Recognise where to use satellite communication systems. Explain how satellite communications systems work. Satellite comms training course details Who will benefit: Anyone working with satellite systems. Prerequisites: None. Duration 2 days Satellite comms training course contents Satellite systems architecture Suppliers, bearers, teleports, subscribers, components, how satellite communications works. Terminals Antenna, VSAT, circulators, filters, LNA, HPA, up/ down converters, modems. Satellites Satellite components, payloads, satellite types: GEO and non-GEO. Satellite transmission Satellite C and Ku bands, Modulation, AM, FM, PSK, QPSK, FDMA, CDMA. Satellite services Regulatory issues; DVB and video distribution via satellite; how reporters uplink news, Internet services over DVB; broadband services; multicast internet services via satellite; multimedia meshed networking using VSATs; military small terminal satcoms. Satellite engineering Link budgets, Spectrum analysis, Power meter

Foundations of Immunisation and Vaccines
By Guardian Angels Training
Gain a comprehensive understanding of immunisation and vaccines with our "Foundations of Immunisation and Vaccines" course. Designed for healthcare professionals, public health workers, and individuals interested in immunisation, this course covers vaccine development, administration, safety, and the role of vaccines in preventing infectious diseases.
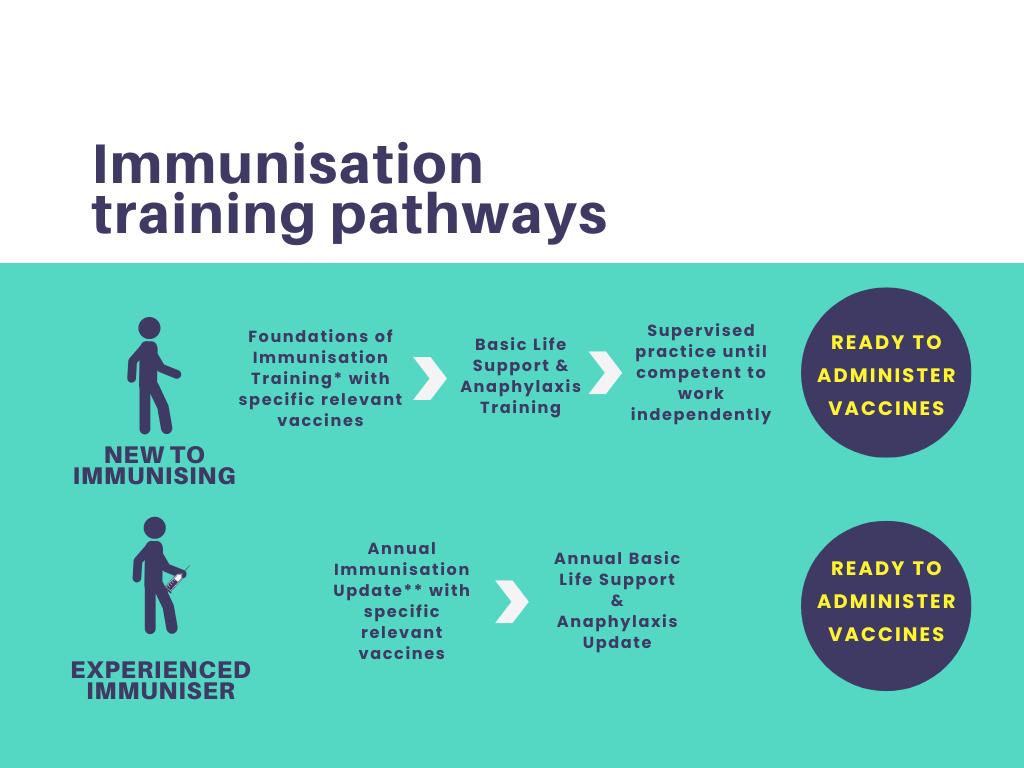
Promoting Best Practice in Asthma and Anaphylaxis Training (Train the Trainer)
By Guardian Angels Training
Gain comprehensive knowledge and practical skills in asthma and anaphylaxis management with our evidence-based training course. Ideal for healthcare professionals, educators, and patient care providers. Optimise patient outcomes with effective emergency response protocols, prevention strategies, and patient education.

Promoting Best Practice in Basic Life Support Instruction
By Guardian Angels Training
Learn to teach basic life support effectively with our "Promoting Best Practice in Basic Life Support Instruction" course. Ideal for healthcare professionals, educators, and individuals interested in life-saving interventions.

Responding to Behaviours that Challenge
By Prima Cura Training
This course provides learners with the knowledge they need to respond appropriately to behaviours that may challenge, including how to communicate effectively, understand why individuals may display behaviours, and problem solve with the individual.

SIA Instructor Course London
By London Construction College
Take The SIA Instructor Course This Will Take You 7 Days To Complete. Enroll Now On To The Course! What is the SIA Instructor Course? SIA Instructor Course is a comprehensive training program designed to empower individuals with the knowledge and skills necessary to become certified instructors in the security industry. With a blend of classroom instruction and hands-on training, this program equips you to educate and guide aspiring security professionals in obtaining their SIA licenses. SIA Trainer Instructor Course LEVEL 3: SIA Trainer / Instructor Combined 7-Day Course – £1250 Embark on the SIA Trainer/Instructor course covering Security Guarding, Door Supervision, CCTV, and Conflict Management. This comprehensive 7-day program equips you to teach various SIA courses. The course is conducted weekly, concluding with a thorough examination. Combined Course Options SIA Combined AET + Conflict Management + Physical Intervention Level 3 – £1250 AET (Award in Education Training) + Conflict Management Delivery – £850 Conflict Management Delivery + Physical Intervention Delivery Level 3 – £950 SIA Instructor Course Road Map Becoming an SIA instructor is a rewarding career path that not only allows you to contribute to the growth and development of the security industry but also opens up new opportunities for personal and professional growth. Here are some compelling reasons to consider our SIA Instructor Course: 01 Make A Difference As an SIA instructor, you have the power to shape the future of security professionals. Your expertise and guidance will directly impact the knowledge and skills of individuals entering the security industry, ultimately enhancing the safety and security of our communities. 02 Professional Growth Becoming a certified SIA instructor is a mark of excellence in your career. It not only validates your expertise but also opens doors to a wide range of teaching and training opportunities in the security sector. 03 Rewarding Career Being an SIA instructor is not just a job; it’s a rewarding career where you get to see your students grow and succeed in the security industry. The satisfaction of knowing you’ve played a role in their success is immeasurable. Embark On A Fulfilling Career As An SIA-Certified Instructor Enrolling in our SIA Instructor Course is the first step toward a fulfilling career as an SIA-certified instructor. Whether you’re a seasoned security professional or just beginning your journey in the industry, this course equips you with the knowledge and skills needed to guide the next generation of security personnel. To enroll in our SIA Instructor Course or to obtain more information, please contact us at [Insert Contact Information]. We are committed to assisting you in your journey to become an SIA-certified instructor and contribute to the development of skilled security professionals. Why Choose SIA Instructor Course? Instructional Techniques You’ll learn effective instructional methods and techniques to deliver training content in a clear and engaging manner. Whether you’re teaching new security personnel or conducting refresher courses, you’ll have the tools to make learning effective and enjoyable. Adult Learning Principles Understanding how adults learn is crucial for effective teaching. Our course equips you with the principles of adult learning, enabling you to tailor your teaching to the needs of your students. Effective Communication Communication is at the heart of successful teaching. You’ll gain insight into effective communication strategies, ensuring that your students understand and retain the material you present. SIA Training Content As an SIA instructor, you’ll be responsible for delivering specific training content to prepare security personnel for their roles. Our course covers the core content required for SIA licensing, giving you a deep understanding of the subject matter.

Getting paid - telephone tactics for debt collection (In-House)
By The In House Training Company
How to protect your cash flow In the current economic climate more and more companies are finding that their customers are taking longer to pay - or are not even paying at all. As cash flow is key to the survival of any business, effective debt collection tactics are vital for all businesses. This workshop concentrates on the telephone skills and techniques you can use to achieve the most positive outcome in any debt collection situation - payment of money owed, as soon as possible, whilst keeping the collection cost as low as possible. The course will help you: Understand your debtors and communicate with them accordingly Develop a strategy for more effective debt collection Make every call count Handle difficult calls Reduce the amount of time you need to spend on chasing payment Increase your collection rates 1 The debt collection process Understanding the reasons behind payment default Looking at the debt situation from the customer's point of view Developing a strategy for effective debt collection 2 Advanced telephone communication skills Techniques for speaking to the person responsible for paying the debt How to gain the customer's trust when discussing debt Telephone collection skills best practice Key phrases that keep the conversation positive and open 3 Questioning and listening skills for gathering information Different types of question Using high-gain questions to uncover key information Active listening that will help you understand what customers are really saying Leading with examples and high-impact questions Summarising and restating 4 Overcoming objections and excuses Identifying objections Preparing suitable responses Probing objections and ways to overcome them 5 Gaining commitment and ending the call Learn how to negotiate an agreement to suit both parties Summarising actions for you and the customer Ending the call professionally 6 Dealing with difficult and challenging situations Understand different personality types The correct way to respond to an upset customer Ways to calm angry customers (and handle verbal attacks) 7 Action plans Course summary and presentation of action plans

Search By Location
- Communication Skills Courses in London
- Communication Skills Courses in Birmingham
- Communication Skills Courses in Glasgow
- Communication Skills Courses in Liverpool
- Communication Skills Courses in Bristol
- Communication Skills Courses in Manchester
- Communication Skills Courses in Sheffield
- Communication Skills Courses in Leeds
- Communication Skills Courses in Edinburgh
- Communication Skills Courses in Leicester
- Communication Skills Courses in Coventry
- Communication Skills Courses in Bradford
- Communication Skills Courses in Cardiff
- Communication Skills Courses in Belfast
- Communication Skills Courses in Nottingham