- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Certified Data Science Practitioner
By Mpi Learning - Professional Learning And Development Provider
This course will enable you to bring value to the business by putting data science concepts into practice. Data is crucial for understanding where the business is and where it's headed. Not only can data reveal insights, but it can also inform - by guiding decisions and influencing day-to-day operations.

Estate Agent
By Lead Academy
This course will help you to gain the skills needed to thrive in the competitive field of Estate Agent. You will learn the art of property valuation, effective marketing strategies and the ins and outs of property law and regulations. This Course At A Glance Accredited by CPD UK Endorsed by Quality Licence Scheme Get an introduction to estate agents Learn to explore the career prospects of estate agents Understand the classification of estate agents Get acquainted with the types of contractual agreements Recognise the code of practice for estate agents Understand the property valuation process Get to know about the process of negotiating in an estate agency Learn about letting & renting Understand the process of selling a property Learn how to buy through an estate agent Recognise the importance of technology in the domain Estate Agent Course Overview This estate agent course online will help you understand the roles and responsibilities of an estate agent and also help you know how to explore career prospects in the same domain. You will also learn about the different types of estate agents and understand how to make a career selection accordingly. This estate agent course online will also help you get a better understanding of the different types of contractual agreements, the code of practice for estate agents and the property valuation process. You will also know how to negotiate in an estate agency, the process of selling properties and buying through an estate agent by taking this popular online course. By the end of the course, you will get a thorough understanding of the classification of estate agents and the responsibilities carried out by them. After finishing this flexible online course, you will also gain the skills and knowledge required to become a professional estate agent. Who should take this course? This comprehensive estate agent course is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of estate agent. Entry Requirement There are no academic entry requirements for this estate agent course, and it is open to students of all academic backgrounds. However, you are required to have a laptop/desktop/tablet or smartphone and a good internet connection. Assessment Method This estate agent course assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner can grasp from each section. In the assessment pass mark is 60%. Course Curriculum Module 1: Introduction to Estate Agents Introduction to Estate Agents Module 2: Exploring Career Prospects of Estate Agents Exploring Career Prospects of Estate Agents Module 3: Classification of Estate Agents Classification of Estate Agents Module 4: Types of Contractual Agreements Types of Contractual Agreements Module 5: Code of Practice for Estate Agents Code of Practice for Estate Agents Module 6: Property Listing Property Listing Module 7: Property Valuation Process Property Valuation Process Module 8: Negotiating in Estate Agency Negotiating in Estate Agency Module 9: Letting & Renting Letting & Renting Module 10: Selling a Property Selling a Property Module 11: Buying Through an Estate Agent Buying Through an Estate Agent Module 12: Technology Technology Conclusion: Estate Agent Course Conclusion: Estate Agent Course Assessment Assessment - Estate Agent Recognised Accreditation CPD Certification Service This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. Quality Licence Scheme Endorsed The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. Certificate of Achievement Endorsed Certificate from Quality Licence Scheme After successfully passing the MCQ exam you will be eligible to order the Endorsed Certificate by Quality Licence Scheme. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. There is a Quality Licence Scheme endorsement fee to obtain an endorsed certificate which is £65. Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons. When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org

PIC Microcontroller: Practical Projects Online Training
By Lead Academy
PIC Microcontroller: Practical Projects Training Course Overview Are you looking to begin your PIC Microcontroller career or want to develop more advanced skills in PIC Microcontroller? Then this PIC Microcontroller: practical projects online training course will set you up with a solid foundation to become a confident electronic engineer and help you to develop your expertise in PIC Microcontroller. This PIC Microcontroller: practical projects online training course is accredited by the CPD UK & IPHM. CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Whether you are self-taught and you want to fill in the gaps for better efficiency and productivity, this PIC Microcontroller: practical projects online training course will set you up with a solid foundation to become a confident electronic engineer and develop more advanced skills. Gain the essential skills and knowledge you need to propel your career forward as an electronic engineer. The PIC Microcontroller: practical projects online training course will set you up with the appropriate skills and experience needed for the job and is ideal for both beginners and those currently working as electronic engineer. This comprehensive PIC Microcontroller: practical projects online training course is the perfect way to kickstart your career in the field of PIC Microcontroller. This PIC Microcontroller: practical projects online training course will give you a competitive advantage in your career, making you stand out from all other applicants and employees. If you're interested in working as an electronic engineer or want to learn more skills on PIC Microcontroller but unsure of where to start, then this PIC Microcontroller: practical projects online training course will set you up with a solid foundation to become a confident electronic engineer and develop more advanced skills. As one of the leading course providers and most renowned e-learning specialists online, we're dedicated to giving you the best educational experience possible. This PIC Microcontroller: practical projects online training course is crafted by industry expert, to enable you to learn quickly and efficiently, and at your own pace and convenience. Who should take this course? This comprehensive PIC Microcontroller: practical projects online training course is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of PIC Microcontroller. Entry Requirements There are no academic entry requirements for this PIC Microcontroller: practical projects online training course, and it is open to students of all academic backgrounds. As long as you are aged seventeen or over and have a basic grasp of English, numeracy and ICT, you will be eligible to enrol. Career path This PIC Microcontroller: practical projects online training course opens a brand new door for you to enter the relevant job market and also provides you with the chance to accumulate in-depth knowledge at the side of needed skills to become flourishing in no time. You will also be able to add your new skills to your CV, enhance your career and become more competitive in your chosen industry Course Curriculum Introduction Introduction Who we are First Project: Motion Detector First Project Goal and Components First Project Circuit First Project Code Explained First Project Simulation Burning the Code to PIC Microcontroller First Project Practical Work Second Project: RGB Multi-Color Leds Controlled by LDR Second Project Goal and Components Second Project Circuit Second Project Code Second Project Simulation Second Project Practical Work Third Project: Device Control Using Clap Signals Third Project Goal and Components Third Project Circuit Third Project Code and Simulation Third Project Practical Work End of Course End Download and Install Software Section Download and Install MikroC Software Download and Install Proteus Software Recognised Accreditation CPD Certification Service This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. Certificate of Achievement Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons. When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org
Learn RabbitMQ: Asynchronous Messaging with Java and Spring
By Packt
Learn RabbitMQ: Asynchronous Messaging with Java and Spring

Ruby and Javascript Programming Bundle
By Packt
Learn the Ruby programming language and JavaScript coding from beginner to intermediate for web development - fast!

**Be prepared for the upcoming Hiring Season by enhancing your professional skillsets with Apex Learning! Get Hard Copy + PDF Certificate + Transcript + Student ID Card as a Gift - Enrol Now** In this UK Insurance complete bundle course, we go into detail and explain all you need to know about general, commercial, liability, and life insurance in the UK. We also go into detail on the UK insurance market, insurance fraud, and other related issues. Learn how to become a well-respected and in-demand member of the UK insurance business. This dynamic business sector needs talented and motivated individuals to keep it running as a profitable market, and we can help you integrate in with ease. As an exceptional Insurance Agent, you will recognise your obligation and dedication to delivering the best brokerage for your grateful clients and consumers. You will understand the ideal schemes and contracts for each case, whether it is personal plans for houses and automobiles or a comprehensive corporate programme for a wealthy organisation. This thorough course will walk you through the many aspects of the insurance industry and offer you helpful information regardless of your level of expertise. The subject ranges from fundamental vocabulary to the many forms of insurance and the abilities required for a successful career in this industry. You'll learn about risk management, underwriting, and claims management. Methods for detecting fraud and knowing the code of conduct can help you become an excellent agent. Courses are included in this Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3? Course 01: Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3 Course 02: Insurance Agent Training Course 03: Pension UK Course 04: Law and Contracts - Level 2 Course 05: Financial Investigator Course 06: Financial Analysis Course 07: Payroll Administrator and UK Payroll System Training Course 08: Business Analysis Level 3 Course 09: Level 3 Tax Accounting Course 10: Microsoft Excel Training: Depreciation Accounting Course 11: Certificate in Anti Money Laundering (AML) Course 12: Know Your Customer (KYC) Course 13: Customer Relationship Management Course 14: Time Management Enrol and Achieve Mastery in: Recognising the significance of insurance in the UK financial industry Learning about the many forms of insurance available on the market Learning the fundamental skills required to work as an agent Dealing with the demands of high-performing enterprises Developing your capacity to manage risks in the workplace and on the job Understanding how to carry out critical activities, including claim management and underwriting Knowing how to spot examples of fraud when they occur Understanding the code of ethics and behaviour required to work as a reliable insurance broker Curriculum of UK Insurance Complete Package (General, Commercial, Liability, Life) Course 01: Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3 01: Industry 02: The UK Industry 03: Principles 04: General 05: Personal Lines 06: Commercial Lines 07: Liability 08: Life Insurance 09: Insurance Fraud 10: Underwriting Process Course 02: Insurance Agent Training 01: An Overview of the UK Insurance Industry 02: Principles 03: Types 04: Career in the Industry 05: Skills of an Agent 06: Business 07: Risk Management in 08: Underwriting Process 09: Claims Handling Process 10: Fraud Finding 11: Code of Ethics and Conduct Course 03: Pension UK 01: Overview of the UK Pension system 02: Type of Pension Schemes 03: Pension Regulation 04: Pension Fund Governance 05: Law and Regulation of Pensions in the UK 06: Key Challenges in UK Pension System Course 04: Law and Contracts - Level 2 01: Introduction to UK Laws 02: Ministry of Justice 03: Agreements and Contractual Intention 04: Considerations and Capacities of Contact Laws 05: Terms within a Contract 06: Misinterpretations and Mistakes 07: Consumer Protection 08: Privity of Contract 09: Insurance Contract Laws 10: Contracts for Employees 11: Considerations in International Trade Contracts 12: Laws and Regulations for International Trade 13: Remedies for Any Contract Breach Course 05: Financial Investigator 01: Introduction to Financial Investigator 02: Introduction to Financial Investigation 03: Characteristics of Financial Crimes 04: Categories of Financial Crimes 05: Financial Crime Response Plan 06: Collecting, Preserving and Gathering Evidence 07: Laws against Financial Fraud Course 06: Financial Analysis 1. Introduction 2. Profitability 3. Return Ratio 4. Liquidity Ratio 5.Operational Analysis 6. Detecting Manipulation Course 07: Payroll Administrator and UK Payroll System Training Module 01: Payroll System in the UK Module 02: Payroll Basics Module 03: Company Settings Module 04: Legislation Settings Module 05: Pension Scheme Basics Module 06: Pay Elements Module 07: The Processing Date Module 08: Adding Existing Employees Module 09: Adding New Employees Module 10: Payroll Processing Basics Module 11: Entering Payments Module 12: Pre-Update Reports Module 13: Updating Records Module 14: e-Submissions Basics Module 15: Process Payroll (November) Module 16: Employee Records and Reports Module 17: Editing Employee Records Module 18: Process Payroll (December) Module 19: Resetting Payments Module 20: Quick SSP Module 21: An Employee Leaves Module 22: Final Payroll Run Module 23: Reports and Historical Data Module 24: Year-End Procedures Course 08: Business Analysis Level 3 01: Introduction to Business Analysis 02: Business Processes 03: Business Analysis Planning and Monitoring 04: Strategic Analysis and Product Scope 05: Solution Evaluation 06: Investigation Techniques 07: Ratio Analysis 08: Stakeholder Analysis and Management 09: Process Improvement with Gap Analysis 10: Documenting and Managing Requirements 11: Career Prospect as a Business Analyst in the UK Course 09: Level 3 Tax Accounting 01: Tax System and Administration in the UK 02: Tax on Individuals 03: National Insurance 04: How to Submit a Self-Assessment Tax Return 05: Fundamentals of Income Tax 06: Payee, Payroll and Wages 07: Value Added Tax 08: Corporation Tax 09: Double Entry Accounting 10: Management Accounting and Financial Analysis 11: Career as a Tax Accountant in the UK Course 10: Microsoft Excel Training: Depreciation Accounting Introduction Depreciation Amortization and Related Terms Various Methods of Depreciation and Depreciation Accounting Depreciation and Taxation Master Depreciation Model Conclusion Course 11: Certificate in Anti Money Laundering (AML) 01: Introduction to Money Laundering 02: Proceeds of Crime Act 2002 03: Development of Anti-Money Laundering Regulation 04: Responsibility of the Money Laundering Reporting Office 05: Risk-based Approach 06: Customer Due Diligence 07: Record Keeping 08: Suspicious Conduct and Transactions 09: Awareness and Training Course 12: Know Your Customer (KYC) 01: Introduction to KYC 02: Customer Due Diligence 03: AML (Anti-Money Laundering) 04: KYC, AML, and Data Privacy Regulations for Businesses Operations in the United Kingdom 05: Regulations to be Complied by Industries 06: Methods for carrying out KYC and AML and the Future of KYC Compliance Course 13: Customer Relationship Management Module 01: Introduction to Customer Relationship Management (CRM) Module 02: CRM Fundamentals Module 03: CRM Strategies CRM Strategies Module 04: Data Analysis in CRM Module 05: CRM Databases Module 06: Deepening Customer Relationship Module 07: Handling Customer Complaints Module 08: Future of CRM Course 14: Time Management Identifying Goals Effective Energy Distribution Working with Your Personal Style Building Your Toolbox Establishing Your Action Plan How will I get my Certificate? After successfully completing the course you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (For The Title Course) Hard Copy Certificate: Free (For The Title Course) If you want to get hardcopy certificates for other courses, generally you have to pay £20 for each. But this Fall, Apex Learning is offering a Flat 50% discount on hard copy certificates, and you can get each for just £10! P.S. The delivery charge inside the U.K. is £3.99 and the international students have to pay £9.99. CPD 140 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Insurance agent Claims handler Corporate accounts handler Compliance Consultant Client advisor Requirements This Training Course has been designed to be fully compatible with tablets and smartphones. Career path Insurance broker (£20,000 to £65,000) Insurance account manager (£18,000 to £75,000) Insurance underwriter (£18,000 to £65,000) Financial adviser (£23,500 to £45,000) Certificates Certificate of completion Digital certificate - Included You will get the PDF Certificate for the title course (Understanding UK Insurance) absolutely Free! Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Understanding UK Insurance) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

The Complete Python Course (2024)
By Packt
Learn Python with 200+ real-world examples implemented on PyCharm. Ace functions, classes, objects, dictionary, lists, sets, and tuples. The course also covers math, statistics, and random modules. This is the ideal course for you if you want to advance your Python programming skills or switch to Python programming.

Register on the Ethereum Blockchain DApp using Solidity today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The Ethereum Blockchain DApp using Solidity is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The Ethereum Blockchain DApp using Solidity Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the Ethereum Blockchain DApp using Solidity, all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16. Course Content Section 01: What is Blockchain? Introduction to Building an Ethereum Blockchain App 00:02:00 The Beginning of Blockchain 00:05:00 Currency and Cryptocurrency 00:05:00 Why Use the Blockchain? 00:06:00 Blockchain Data and Blocks 00:06:00 Blockchain Immutability 00:03:00 Blockchain Consensus 00:02:00 Building the Blockchain Story 00:03:00 Hashes 00:06:00 What is a Chain of Blocks? 00:04:00 Finding the Nonce 00:05:00 Blockchain Mining 00:03:00 Arriving at Consensus 00:05:00 Public vs. Private Blockchains 00:03:00 Distributed Processing and Blockchain Solutions 00:06:00 Section 02: What is Ethereum? Introduction to Ethereum 00:03:00 Ethereum in Financial Services 00:07:00 Ethereum in Digital Identity Management 00:05:00 Ethereum in Industry Applications 00:06:00 Ethereum in Government 00:03:00 Ethereum Smart Contracts 00:03:00 Ether and the Initial Coin Offering (ICO) 00:06:00 Decentralized Autonomous Organization (DAO) 00:03:00 The Ethereum Ecosystem 00:06:00 Building Blockchain Apps 00:05:00 Section 03: The Ethereum Ecosystem & the Development Lifecycle Parts of the Ethereum Blockchain 00:11:00 Smart Contracts 00:05:00 Smart Contract Languages 00:04:00 What are Virtual Machines? 00:06:00 The Ethereum Virtual Machine (EVM) 00:03:00 Fueling Your Code with Gas 00:05:00 Tools for Ethereum SDLC 00:03:00 Blockchain Client 00:03:00 Writing and Testing Your Code, Part 1 00:05:00 Writing and Testing Your Code, Part 2 00:07:00 Section 04: Ethereum Development Tools Your Ethereum Development Toolbox 00:04:00 Installing Geth Lab (CLI Blockchain Client) 00:04:00 Installing Ganache Lab (Test Blockchain) 00:06:00 Installing Truffle Lab (Development Environment and Testing Framework) 00:06:00 Installing Microsoft Visual Studio Code Lab (IDE) 00:05:00 Section 05: Your Ethereum Wallet What is an Ethereum Wallet? 00:02:00 Types of Ethereum Wallets 00:06:00 Web and Desktop Wallets 00:07:00 Mobile, Hardware, and Paper Wallets 00:09:00 Installing MetaMask 00:05:00 Section 06: Building Your First Ethereum App Preparing Your First Truffle Project 00:07:00 Writing a Simple Smart Contract 00:11:00 Compiling Your Simple Smart Contract 00:10:00 Deploying Code and Invoking Functions 00:09:00 Section 07: Learning about Smart Contracts Smart Contracts Review 00:03:00 What is Supply Chain? 00:07:00 Supply Chain Challenges and Blockchain Solutions 00:07:00 Blockchain Solution Examples 00:04:00 Ethereum Tokens 00:06:00 Your Supply Chain Project 00:08:00 Exploring Solidity 00:11:00 Defining Types of Data 00:05:00 Data Types Lab 00:09:00 Solidity Data Modifiers, Part 1 00:04:00 Solidity Data Modifiers, Part 2 00:06:00 Revisiting Gas 00:06:00 Controlling Flow 00:12:00 Handling Errors 00:05:00 Section 08: Your Supply Chain Smart Contract dApp Designing Your Supply Chain App 00:04:00 What are dApps? 00:06:00 Token Smart Contract Details 00:08:00 Supply Chain Smart Contract Details 00:06:00 Smart Contract Road Map 00:02:00 Token Smart Contract Data Lab, Part 1 00:07:00 Token Smart Contract Data Lab, Part 2 00:09:00 Supply Chain Smart Contract Data Lab, Part 1 00:05:00 Supply Chain Smart Contract Data Lab, Part 2 00:03:00 Token Smart Contract Functions Lab, Part 1 00:05:00 Token Smart Contract Functions Lab, Part 2 00:04:00 Supply Chain Smart Contract Functions Lab, Part 1 00:10:00 Supply Chain Smart Contract Functions Lab, Part 2 00:09:00 Using Events 00:07:00 Implementing Events 00:05:00 More on Ownership 00:08:00 Designing for Security 00:09:00 Implementing Minimal Functionality 00:06:00 Section 09: Testing Ethereum Apps Blockchain dApp Testing 00:10:00 Deploying Your dApp to a Test Blockchain Lab 00:08:00 Writing Tests for Ethereum dApps 00:06:00 Command-Line Testing Lab, Part 1 00:04:00 Command-Line Testing Lab, Part 2 00:11:00 Command-Line Testing Lab, Part 3 00:03:00 JavaScript Testing 00:08:00 Logging and Handling Errors 00:07:00 Logging Activity in Smart Contracts 00:05:00 Fixing Bugs in a dApp 00:05:00 Section 10: Deploying and Maintaining Ethereum Apps Test Blockchains 00:08:00 The Live Blockchain (Mainnet) 00:05:00 Connecting to Multiple Blockchains and Infura Lab 00:05:00 Configuring Truffle and Infura Lab 00:06:00 Funding Your Account Lab 00:04:00 Deploying to the Live Blockchain 00:08:00 Section 11: Integrating Non-Blockchain Apps with Ethereum Blockchain and Database Storage 00:11:00 Execution and Flow in dApps and Traditional Applications 00:05:00 Blockchain Incorporation Design Goals 00:06:00 Integration Considerations for Incorporating Blockchain 00:06:00 Interface Considerations for Incorporating Blockchain 00:04:00 Resources Resources - Ethereum Blockchain DApp Using Solidity 00:00:00

PVOL304: Solar Training - Advanced PV Stand-alone System Design (Battery-Based) - Online
By Solar Energy International (SEI)
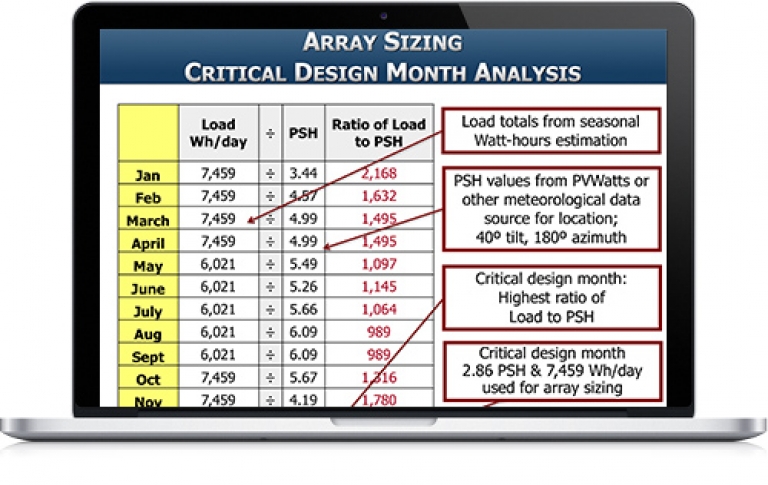
Define terms used in stand-alone systems Name common applications for stand-alone systems; describe basic component layouts Describe differences between AC and DC coupling State principle elements of a microgrid Define the importance of an accurate load analysis Review load analysis procedures; perform a load analysis based on daily data Review battery bank sizing for lead-acid and lithium-ion battery types Define array sizing variables and how they affect design for both MPPT and non-MPPT charge controllers Explain charge controller types and describe maximum power point tracking and voltage step-down Examine the calculations for PV array sizing Describe the difference between sizing for a non-MPPT and an MPPT charge controller Complete array configuration calculations for a system with a non-MPPT and an MPPT charge controller Summarize the parameters to check when selecting a charge controller Explain the purpose of DC load control and the three ways it can be implemented Identify design variables, advantages, and disadvantages of DC-only PV systems Describe how to size and integrate components for a recreational vehicle (RV) application Identify installation and maintenance considerations specific to mobile applications Identify applications and considerations for DC lighting systems Specify a battery-based inverter given electrical load and surge requirements Describe various configurations for stacking and clustering multiple inverters Examine inverter / charger size considerations Describe multiwire branch circuit wiring and concerns with single-phase supplies Describe the purpose and function of a generator Identify considerations that impact generator selection Solve for location-based performance degradation Specify a generator given electrical load, battery charging, and surge requirements Estimate approximate generator run time List generator maintenance Describe the National Electrical Code (NEC®) Articles that apply to the different parts of PV and energy storage systems (ESS) Identify NEC® requirements for workspace clearances, disconnects, and overcurrent protection devices (OCPD) that apply to PV systems Locate and apply specific requirements for storage batteries, stand-alone systems, and energy storage systems Identify labeling requirements List relevant building and fire codes Review installation considerations and best practices for stand-alone systems as related to batteries, design strategies, monitoring and metering, balance of system (BOS) equipment Review DC-coupled stand-alone residential system design Define operating modes of off-grid AC coupled PV systems Explain charge regulation of AC coupled PV inverters in a stand-alone system Discuss AC coupled PV system design strategies; evaluate equipment options for AC coupled off-grid applications Design a stand-alone microgrid system with PV (AC and DC coupled) and generator power sources Distinguish between isolated and non-isolated microgrids Compare concepts of centralized versus decentralized generation and controls Identify different types of microgrid analysis and planning software Review isolated microgrid use case examples Identify general PPE for battery system maintenance Develop a battery maintenance plan Identify methods to measure battery state of charge Identify common causes of battery problems and how to avoid them Identify PPE for lead-acid battery maintenance Develop a battery maintenance plan for lead-acid batteries Describe how to correctly add water to a flooded lead-acid (FLA) battery bank Identify methods to measure battery state of charge of FLA batteries Define when and why equalization is needed Identify common causes of battery problems and how to avoid them Note: SEI recommends working closely with a qualified person and/or taking PV 202 for more information on conductor sizing, electrical panel specification, and grounding systems. These topics will part of this course, but they are not the focus.
Ofqual Regulated Level 5 Diploma in Teaching English to Speakers of Other Languages (TESOL) (220 hrs)
5.0(5)By TEFL Wonderland - Brilliant Minds
If you want to achieve a Level-5 Ofqual UK-Government Regulated TESOL certification in the most effective, time-saving and enjoyable way, embark on a thrilling learning adventure in TEFL Wonderland. Unlike the click-and-read TEFL courses, this play-and-practice expedition will engage all your senses and keep you motivated to achieve your learning mission.
