- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Network Fundamentals and Implementing TCP/IP
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is intended for students who want to gain knowledge of basic networking components, TCP/IP, and related services Overview Upon successful completion of this course, students will be able to identify different types of networks, understand TCP/IP protocols, subnetting, name resolution, and configuring various related services This course will introduce students to different types of network environments, understand the processes involved with TCP/IP-based networking, and installing and configuring related services such as DHCP, DNS, Active Directory, and VPNs Basic Network Infrastructure Network Architecture Standards Local Area Networking Wide Area Networking Wireless Networking Connecting Network Devices OSI Model Networking Hardware Introduction to TCP/IP History of TCP/IP TCP/IP Terminology TCP/IP Components in Windows Architectural Overview of TCP/IP TCP/IP Protocol Suite Internet Layer Protocols Transport Layer Protocols IP Addressing IPv4 Addressing IPv6 Addressing Subnetting Subnetting for IPv4 Subnetting for IPv6 IP Routing IP Routing Overview IPv4 Routing Dynamic Host Configuration Protocol DHCP Overview How DHCP Works Windows-based DHCP DHCP Relay Agent Host Name Resolution TCP/IP Naming Schemes Name Resolution Process Domain Name System Overview The Domain Name System Name Resolution Name Server Roles Resource Records Zone Transfers Windows Support for DNS Active Directory Fundamentals DNS Server in Windows Active Directory Integration Windows Internet Name Service Introduction to WINS How WINS Works WINS Client and Server Configuration Virtual Private Networking Virtual Private Networking Overview VPN Protocols VPN Server Installation Troubleshooting TCP/IP Basic Steps Windows Troubleshooting Tools Troubleshooting IPv4 Additional course details: Nexus Humans Network Fundamentals and Implementing TCP/IP training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Network Fundamentals and Implementing TCP/IP course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Computer Networks Security
By Compliance Central
Are you looking to enhance your Computer Networks Security skills? If yes, then you have come to the right place. Our comprehensive course on Computer Networks Security will assist you in producing the best possible outcome by mastering the Computer Networks Security skills. The Computer Networks Security course is for those who want to be successful. In the Computer Networks Security course, you will learn the essential knowledge needed to become well versed in Computer Networks Security. Our Computer Networks Security course starts with the basics of Computer Networks Security and gradually progresses towards advanced topics. Therefore, each lesson of this Computer Networks Security course is intuitive and easy to understand. Why would you choose the Computer Networks Security course from Compliance Central: Lifetime access to Computer Networks Security course materials Full tutor support is available from Monday to Friday with the Computer Networks Security course Learn Computer Networks Security skills at your own pace from the comfort of your home Gain a complete understanding of Computer Networks Security course Accessible, informative Computer Networks Security learning modules designed by expert instructors Get 24/7 help or advice from our email and live chat teams with the Computer Networks Security bundle Study Computer Networks Security in your own time through your computer, tablet or mobile device. A 100% learning satisfaction guarantee with your Computer Networks Security Course Improve your chance of gaining in demand skills and better earning potential by completing the Computer Networks Security Computer Networks Security Curriculum Breakdown of the Computer Networks Security Course Introduction Section 01: An Introduction to Computer Networks Section 02: ISO/OSI Model Section 03: TCP/IP Protocols Section 04: Wireless Networks Section 05: Network Security Section 06: Firewalls and Honeypots Section 07: Intrusion Detection and Prevention System Section 08: Wireless Network Security Section 09: Physical Security and Incident Handling Section 10: Network Security: Conclusion CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? The Computer Networks Security course helps aspiring professionals who want to obtain the knowledge and familiarise themselves with the skillsets to pursue a career in Computer Networks Security. It is also great for professionals who are already working in Computer Networks Security and want to get promoted at work. Requirements To enrol in this Computer Networks Security course, all you need is a basic understanding of the English Language and an internet connection. Career path The Computer Networks Security course will enhance your knowledge and improve your confidence. Network Security Specialist: £40,000 to £65,000 per year Information Security Analyst: £35,000 to £55,000 per year Cybersecurity Consultant: £45,000 to £70,000 per year Penetration Tester (Ethical Hacker): £35,000 to £60,000 per year Security Operations Center (SOC) Analyst: £30,000 to £50,000 per year Certificates CPD Accredited Certificate of Completion Free Digital certificate - Included CPD Accredited PDF Certificate CPD Accredited Certificate of Completion Free Hard copy certificate - £10.79 CPD Accredited Hard Copy Certificate Delivery Charge: Inside the UK: Free Outside of the UK: £9.99 each

Diploma in Herbal Medicine Practice
By EduXpress
Our comprehensive program is meticulously crafted to equip you with the essential skills and knowledge required to thrive in your chosen field. Developed by seasoned professionals with years of industry experience, this course is ideal for those seeking to kickstart their careers or enhance their existing skill set. Featuring an engaging audio-visual presentation and easily digestible modules, our program facilitates a self-paced learning experience. Our dedicated online support team is available on weekdays to provide assistance throughout your journey. Key Learning Outcomes: Grasp the fundamentals and their practical applications. Cultivate the necessary skills for success in your field. Apply newfound knowledge to real-world scenarios. Develop effective solutions for relevant topics. Elevate your employability and career prospects. Designed to give you a competitive edge in the job market, this course offers lifetime access to materials and the flexibility to learn at your own pace, from the comfort of your home. Why Choose Us? Learn at your own pace with 24/7 online access to course materials. Benefit from full tutor support available Monday through Friday. Acquire essential skills in the convenience of your home through informative video modules. Enjoy 24/7 assistance and advice via email and live chat. Study on your preferred device - computer, tablet, or mobile. Gain a thorough understanding of the course content. Improve professional skills and earning potential upon completion. Access lifetime course materials and expert guidance. Enjoy the convenience of online learning with flexible schedules. Why Enroll in This Course? Our program provides a comprehensive introduction to the subject matter, laying a solid foundation for further study. It empowers students to acquire knowledge and skills applicable to both their professional and personal lives. Assessment: The course incorporates quizzes to evaluate your understanding and retention of the material. These quizzes pinpoint areas for further practice, allowing you to review course materials as needed. Successfully passing the final quiz qualifies you for a certificate of achievement. Career Path: Our course is meticulously designed to equip you for success in your chosen field. Upon completion, you'll have the qualifications to pursue diverse career opportunities across various industries. Course Content Diploma in Herbal Medicine Practice Module 1: Introduction to Herbal Medicine Module 2: Herbal Pharmacy and Therapeutics Module 3: Botany and Plant Identification Module 4: Herbal Materia Medica Module 5: Chemistry of Herbs Module 6: Ayurvedic Medicine Module 7: Traditional Chinese Medicine (TCM) and Herbs Module 8: Holistic Anatomy and Physiology Module 9: Aromatherapy Module 10: Herbal First Aid and Emergency Care

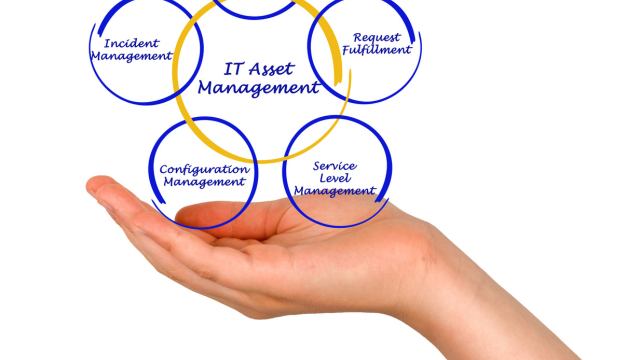
Step into the world of IT Asset Management (ITAM) and elevate your skills. From establishing ITAM programs to mastering asset security and compliance, this course offers a comprehensive guide to managing IT assets effectively. Enhance your ITAM expertise today!
CompTIA A+ 900 Certification is one of our best selling and most popular course. The CompTIA A+ 900 Certification is organised into 55 modules and includes everything you need to become successful in this profession. To make this course more accessible for you, we have designed it for both part-time and full-time students. You can study at your own pace or become an expert in just 26 hours! If you require support, our experienced tutors are always available to help you throughout the comprehensive syllabus of this course and answer all your queries through email. Why choose this course Earn an e-certificate upon successful completion. Accessible, informative modules taught by expert instructors Study in your own time, at your own pace, through your computer tablet or mobile device Benefit from instant feedback through mock exams and multiple-choice assessments Get 24/7 help or advice from our email and live chat teams Full Tutor Support on Weekdays Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Mock exams Multiple-choice assessment Certification After the successful completion of the final assessment, you will receive a CPD-accredited certificate of achievement. The PDF certificate is for £9.99, and it will be sent to you immediately after through e-mail. You can get the hard copy for £15.99, which will reach your doorsteps by post.

Register on the CompTIA A+ (220-1001) today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The CompTIA A+ (220-1001) is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The CompTIA A+ (220-1001) Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the CompTIA A+ (220-1001), all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16.

AR-CXF: ArubaOS-CX Switching Fundamentals (Delivered by Fast Lane)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Ideal candidates are IT Professionals who deploy small-to-medium scale enterprise network solutions based on Aruba products and technologies. Overview Network Fundamentals Review Aruba Switching portfolio ArubaOS-CX Network Operating System VLANs Spanning Tree Protocol VRRP Link Aggregation IP Routing Subnetting OSPFv2 - Single Area Stacking using VSF Secure Management and Maintenance Aruba NetEdit Teaches you the fundamental skills necessary to configure and manage modern, open standards-based networking solutions using Aruba's OS-CX routing & switching technologies. This course consists of approximately 60% lecture and 40% hands-on lab exercises Network Fundamentals What is a network? What is a Protocol? OSI Reference Model Encapsulation, frames, packets, segments Layer 2 to Layer 7 headers Media, cabling, Ethernet/wifi headers Binary/Hex/Decimal theory and conversion TCP/IP Stack (IP addressing & Transport Protocols TCP/UDP) Types of traffic: Unicast, Broadcast, Multicast TCP/IP Stack Overview Ethernet frames IPv4 Header TCP Header ? Three-way Handshake TCP Header ? Sequence Numbers TCP Header ? Port Numbers TCP Header UPD Header Basic Networking with Aruba Solutions Networking devices: Switches, Routers, Multilayer Switches, APs, Mobility Controllers, Firewalls, Servers (HTTP, DHCP, DNS, Telnet, FTP) 2-Tier vs 3-Tier hierarchy Switching Portfolio (AOS switches & AOS-CX switches) is this introducing both portfolio on a couple of slide and few slides on AOS-CX hardware architecture, software architecture and intro to NAE high level. Introduction to AOS-CX and feature set Port numbering Accessing Aruba OS-CX CLI Prompt modes/levels and navigation Context sensitive help Show logs, configuration, interfaces, transceivers, flash, version Hostname/interface name, enabling interfaces Link Layer Discovery Protocol ICMP and reachability testing tools: Ping and Traceroute PoE (standards one slide and what we support and one or two slide on configuration VLANs Broadcast/collision domains VLAN benefits VLAN creation DHCP server configuration in switches (optional) 802.1Q tagging Switchports vs. Routed ports MAC address table ARP table Packet Delivery part 1 Spanning Tree Protocol Redundant network L2 loops 802.1D Common Spanning Tree 802.1s 802.1w overview 802.1w load balancing 802.1w region configuration Link Aggregation Static Aggregation LACP Load Balancing IP Routing - Part 1 Default Gateway DHCP IP Helper Address IP Routing Service Inter-VLAN routing Packet Delivery Part 2 Need for layer 3 redundancy Introduction to VRF VRRP VRRP overview VRRP basic operation VRRP failover and preempt VRRP and MSTP coordination IP Routing - Part 2 Subnetting CIDR Static routes Administrative Distance Floating routes Scalability issues IP Routing - Part 3 IGP vs EGP Distance Vector vs Link State OSPF Router-ID and Hello Messages Passive interfaces States DR and BDR LSDB: LSA 1 and 2 Path selection and convergence Using cost to manipulate routes Stacking Control Plane, Management Plane, and Data Plane Introduction to Stacking technologies Stacking Benefits Centralized control and management plane Distributed Data Plane and Distributed Link Aggregation VSF VSF requirements VSF Link and member roles VSF member IDs and port numbers VSF Configuration VSF Provisioning use cases Tracing Layer 2 traffic: Unicast Tracing Layer 2 traffic: Broadcast, Multicast, and Unknown Unicast VSF Failover and OSFP Graceful-Restart VSF Link failure without MAD MAD VSX Introduction Secure Management and Maintenance OOBM port Management VRF Secure Management Protocols: AAA, SSH, HTTPS, RBAC Radius-based management auth (VSA) SNMP Web interface Configuration file management (Backup, restore, checkpoint and roll back) Operating System image management (backup and restore) Factory default/password recovery AOS-CX Management tools Intro to NetEdit NetEdit installation Basic monitoring with NetEdit AOS-CX Mobile App

Aruba OS-CX Switching Fundamentals, Rev. 20.21
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Ideal candidates are IT Professionals who deploy small-to-medium scale enterprise network solutions based on Aruba products and technologies. Overview After you successfully complete this course, expect to be able to: Explain Networking Fundamentals Describe and review the Aruba Switching portfolio with customers Install and configure devices running the ArubaOS-CX Network Operating System Describe and configure VLANs Explain, describe and configure Spanning Tree Protocol Understand when to use VRRP and how to configure it Explain and configure Link Aggregation Understand and configure IP Routing Explain IP Subnetting Understand and configure OSPFv2 - Single Area Describe and configure Switch Stacking using VSF Configuration of Aruba solutions using Secure Management and Maintenance methodologies Manage, monitor, administer and operate Aruba solutions using Aruba's NetEdit tool This course teaches you the fundamental skills necessary to configure and manage modern, open standards-based networking solutions using Aruba's OS-CX routing and switching technologies. This course consists of approximately 60% lecture and 40% hands-on lab exercises to help you learn how to implement and validate small to medium enterprise network solutions. This 5-day course prepares candidates for the Aruba Certified Switching Associate exam.In this course, participants learn about ArubaOS-CX switch technologies including multi-layer switches. You will also learn about broadcast domains and Virtual Local Area Networks (VLANs); secure management protocols such as AAA, SSH, HTTPS, and Dynamic Segmentation using Aruba's Role-Based Access Control (RBAC); availability technologies such as Multiple Spanning Tree Protocol (MSTP); link aggregation techniques including Link Aggregation Control Protocol (LACP) and switch virtualization with Aruba?s Virtual Switching Framework (VSF). Static and dynamic IP routing protocols such as Open Shortest Path First (OSPF) are also covered. Network Fundamentals What is a network? What is a Protocol? OSI Reference Model Encapsulation, frames, packets, segments Layer 2 to Layer 7 headers Media, cabling, Ethernet/wifi headers Binary/Hex/Decimal theory and conversion TCP/IP Stack (IP addressing & Transport Protocols TCP/UDP) Types of traffic: Unicast, Broadcast, Multicast TCP/IP Stack Overview Ethernet frames IPv4 Header TCP Header ? Three-way Handshake TCP Header ? Sequence Numbers TCP Header ? Port Numbers TCP Header UPD Header Basic Networking with Aruba Solutions Networking devices: Switches, Routers, Multilayer Switches, APs, Mobility Controllers, Firewalls, Servers (HTTP, DHCP, DNS, Telnet, FTP) 2-Tier vs 3-Tier hierarchy Switching Portfolio (AOS switches & AOS-CX switches) is this introducing both portfolio on a couple of slide and few slides on AOS-CX hardware architecture, software architecture and intro to NAE high level. Introduction to AOS-CX and feature set Port numbering Accessing Aruba OS-CX CLI Prompt modes/levels and navigation Context sensitive help Show logs, configuration, interfaces, transceivers, flash, version Hostname/interface name, enabling interfaces Link Layer Discovery Protocol ICMP and reachability testing tools: Ping and Traceroute PoE (standards one slide and what we support and one or two slide on configuration and verifications.) VLANs Broadcast/collision domains VLAN benefits VLAN creation DHCP server configuration in switches (optional) 802.1Q tagging Switchports vs. Routed ports MAC address table ARP table Packet Delivery part 1 Spanning Tree Protocol Redundant network L2 loops 802.1D Common Spanning Tree 802.1s 802.1w overview 802.1w load balancing 802.1w region configuration Link Aggregation Static Aggregation LACP Load Balancing IP Routing - Part 1 Default Gateway DHCP IP Helper Address IP Routing Service Inter-VLAN routing Packet Delivery Part 2 Need for layer 3 redundancy Introduction to VRF VRRP VRRP overview VRRP basic operation VRRP failover and preempt VRRP and MSTP coordination IP Routing - Part 2 Subnetting CIDR Static routes Administrative Distance Floating routes Scalability issues IP Routing - Part 3 IGP vs EGP Distance Vector vs Link State OSPF Router-ID and Hello Messages Passive interfaces States DR and BDR LSDB: LSA 1 and 2 Path selection and convergence Using cost to manipulate routes Stacking Control Plane, Management Plane, and Data Plane Introduction to Stacking technologies Stacking Benefits Centralized control and management plane Distributed Data Plane and Distributed Link Aggregation VSF VSF requirements VSF Link and member roles VSF member IDs and port numbers VSF Configuration VSF Provisioning use cases Tracing Layer 2 traffic: Unicast Tracing Layer 2 traffic: Broadcast, Multicast, and Unknown Unicast VSF Failover and OSFP Graceful-Restart VSF Link failure without MAD MAD VSX Introduction Secure Management and Maintenance OOBM port Management VRF Secure Management Protocols: AAA, SSH, HTTPS, RBAC Radius-based management auth (VSA) SNMP Web interface Configuration file management (Backup, restore, checkpoint and roll back) Operating System image management (backup and restore) Factory default/password recovery AOS-CX Management tools Intro to NetEdit NetEdit installation Basic monitoring with NetEdit AOS-CX Mobile App Additional course details: Nexus Humans Aruba OS-CX Switching Fundamentals, Rev. 20.21 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Aruba OS-CX Switching Fundamentals, Rev. 20.21 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Certified Professional Ethical Hacker
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is targeted towards the information technology (IT) professional that has a minimum 1 year IT Security and Networking experience. This course would be ideal for Information System Owners, Security Officers, Ethical Hackers, Information Owners, Penetration Testers, System Owner and Managers as well as Cyber Security Engineers. Overview Upon completion, the Certified Professional Ethical Hacker candidate will be able to competently take the CPEH exam. The CPEH certification training enables students to understand the importance of vulnerability assessments and how to implement counter response along with preventative measures when it comes to a network hack. Security Fundamentals Overview The Growth of Environments and Security Our Motivation? The Goal: Protecting Information! CIA Triad in Detail Approach Security Holistically Security Definitions Definitions Relationships Method: Ping The TCP/IP Stack Which Services Use Which Ports? TCP 3-Way Handshake TCP Flags Malware Types of Malware Types of Malware Cont... Types of Viruses More Malware: Spyware Trojan Horses Back Doors DoS DDoS Packet Sniffers Passive Sniffing Active Sniffing Firewalls, IDS and IPS Firewall ? First Line of Defense IDS ? Second Line of Defense IPS ? Last Line of Defense? Firewalls Firewall Types: (1) Packet Filtering Firewall Types: (2) Proxy Firewalls Firewall Types ? Circuit-Level Proxy Firewall Type of Circuit- Level Proxy ? SOCKS Firewall Types ? Application-Layer Proxy Firewall Types: (3) Stateful Firewall Types: (4) Dynamic Packet-Filtering Firewall Types: (5) Kernel Proxies Firewall Placement Firewall Architecture Types ? Screened Host Multi- or Dual-Homed Screened Subnet Wi-Fi Network Types Wi-Fi Network Types Widely Deployed Standards Standards Comparison 802.11n - MIMO Overview of Database Server Review Access Controls Overview Role of Access Control Definitions More Definitions Categories of Access Controls Physical Controls Logical Controls ?Soft? Controls Security Roles Steps to Granting Access Access Criteria Physical Access Control Mechanisms Biometric System Types Synchronous Token Asynchronous Token Device Memory Cards Smart Card Cryptographic Keys Logical Access Controls OS Access Controls Linux Access Controls Accounts and Groups Password & Shadow File Formats Accounts and Groups Linux and UNIX Permissions Set UID Programs Trust Relationships Review Protocols Protocols Overview OSI ? Application Layer OSI ? Presentation Layer OSI ? Session Layer Transport Layer OSI ? Network Layer OSI ? Data Link OSI ? Physical Layer Protocols at Each OSI Model Layer TCP/IP Suite Port and Protocol Relationship Conceptual Use of Ports UDP versus TCP Protocols ? ARP Protocols ? ICMP Network Service ? DNS SSH Security Protocol SSH Protocols ? SNMP Protocols ? SMTP Packet Sniffers Example Packet Sniffers Review Cryptography Overview Introduction Encryption Cryptographic Definitions Encryption Algorithm Implementation Symmetric Encryption Symmetric Downfalls Symmetric Algorithms Crack Times Asymmetric Encryption Public Key Cryptography Advantages Asymmetric Algorithm Disadvantages Asymmetric Algorithm Examples Key Exchange Symmetric versus Asymmetric Using the Algorithm Types Together Instructor Demonstration Hashing Common Hash Algorithms Birthday Attack Example of a Birthday Attack Generic Hash Demo Instructor Demonstration Security Issues in Hashing Hash Collisions MD5 Collision Creates Rogue Certificate Authority Hybrid Encryption Digital Signatures SSL/TLS SSL Connection Setup SSL Hybrid Encryption SSH IPSec - Network Layer Protection IPSec IPSec Public Key Infrastructure Quantum Cryptography Attack Vectors Network Attacks More Attacks (Cryptanalysis) Review Why Vulnerability Assessments? Overview What is a Vulnerability Assessment? Vulnerability Assessment Benefits of a Vulnerability Assessment What are Vulnerabilities? Security Vulnerability Life Cycle Compliance and Project Scoping The Project Overview Statement Project Overview Statement Assessing Current Network Concerns Vulnerabilities in Networks More Concerns Network Vulnerability Assessment Methodology Network Vulnerability Assessment Methodology Phase I: Data Collection Phase II: Interviews, Information Reviews, and Hands-On Investigation Phase III: Analysis Analysis cont. Risk Management Why Is Risk Management Difficult? Risk Analysis Objectives Putting Together the Team and Components What Is the Value of an Asset? Examples of Some Vulnerabilities that Are Not Always Obvious Categorizing Risks Some Examples of Types of Losses Different Approaches to Analysis Who Uses What? Qualitative Analysis Steps Quantitative Analysis ALE Values Uses ALE Example ARO Values and Their Meaning ALE Calculation Can a Purely Quantitative Analysis Be Accomplished? Comparing Cost and Benefit Countermeasure Criteria Calculating Cost/Benefit Cost of a Countermeasure Can You Get Rid of All Risk? Management?s Response to Identified Risks Liability of Actions Policy Review (Top-Down) Methodology Definitions Policy Types Policies with Different Goals Industry Best Practice Standards Components that Support the Security Policy Policy Contents When Critiquing a Policy Technical (Bottom-Up) Methodology Review Vulnerability Tools of the Trade Vulnerability Scanners Nessus SAINT ? Sample Report Tool: Retina Qualys Guard http://www.qualys.com/products/overview/ Tool: LANguard Microsoft Baseline Analyzer MBSA Scan Report Dealing with Assessment Results Patch Management Options Review Output Analysis and Reports Overview Staying Abreast: Security Alerts Vulnerability Research Sites Nessus SAINT SAINT Reports GFI Languard GFI Reports MBSA MBSA Reports Review Reconnaissance, Enumeration & Scanning Reconnaissance Overview Step One in the Hacking ?Life-Cycle? What Information is Gathered by the Hacker? Passive vs. Active Reconnaissance Footprinting Defined Social Access Social Engineering Techniques Social Networking Sites People Search Engines Internet Archive: The WayBack Machine Footprinting Tools Overview Maltego GUI Johnny.Ihackstuff.com Google (cont.) Domain Name Registration WHOIS Output DNS Databases Using Nslookup Traceroute Operation Web Server Info Tool: Netcraft Introduction to Port Scanning Which Services use Which Ports? Port Scan Tips Port Scans Shou

