- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
7895 Systems courses
Thinking about a career in Business Analysis? The BCS Practitioner Certificate in Business Analysis has been designed to provide valuable learning for those in roles such as business analyst, business architect, business systems analyst, data analyst, enterprise analyst, management consultant, process analyst, product manager, product owner, project manager, and systems analyst.

Level 1 Award in Motor Vehicle Studies - OFQUAL Accredited (RQF)
By Evo Education and Training Centre
The Level 1 Award in Motor Vehicle Studies is designed to encourage and enable learners who have an interest in this area of study to acquire knowledge and skills to aid progression to further study or employment.

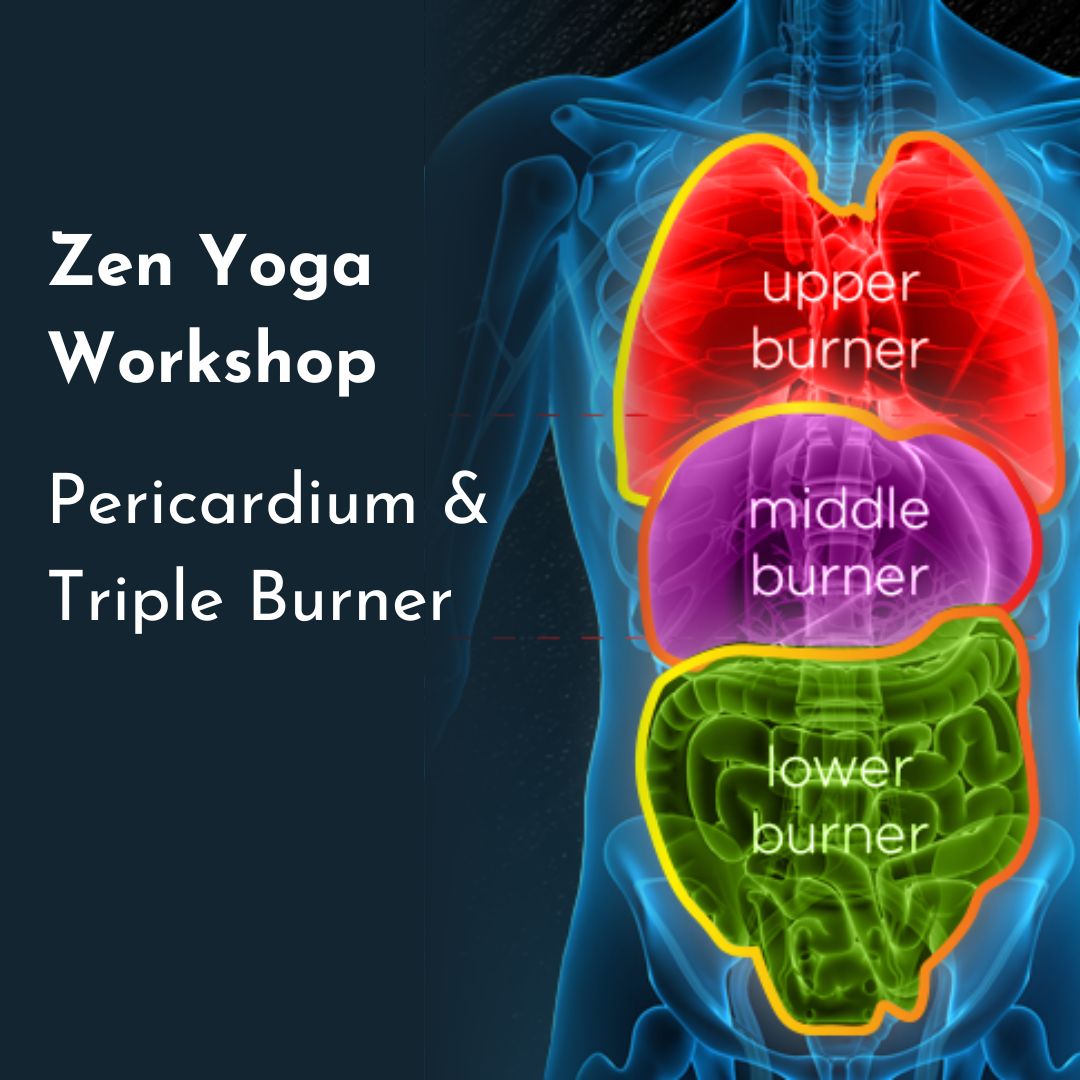
Zen Yoga Workshop - The Pericardium and Triple Heater
By Mark Westmoquette
Zen Yoga workshop exploring the paired energy systems of the Pericardium and Triple Heater. Learn about these organs from both a Western and Eastern perspective, and practice a sequence designed to enliven both systems.
3ds Max Basic to Intermediate Training
By London Design Training Courses
Why Choose 3ds Max Basic to Intermediate Training Course? Course info Looking to take your 3D modelling and animation skills to the next level then Our Intermediate 3DS Max course is designed to help you do just that! A bespoke course ideal for anyone who has a solid understanding of modelling in the 3D environment for films & games. Duration: 20 hrs Method: 1-on-1, Personalized attention. Schedule: Tailor your own schedule and hours of your choice, available from Mon to Sat between 9 am and 7 pm. Why Opt for Our 3ds Max Basic to Intermediate Course? Elevate your 3D modeling and animation skills with our tailored Intermediate 3DS Max course, perfect for those proficient in 3D modeling for films and games. 3ds Max Interface: Familiarize yourself with essential interface areas, tool names, and shortcuts. Master the Scene Explorer for comprehensive scene control. Learn initial software settings for an efficient workflow. Organize your project folder for streamlined work management. Enhance workflow through scene navigation shortcuts and visual styles setup. Understand scene unit configuration for precision. Foundations of 3D Modeling: Acquire industry-standard 3D modeling techniques. Implement compositing modeling with procedural geometry. Utilize non-destructive methods via Modifiers to enhance base geometries. Create 3D models using Splines and modifiers like Extrude, Sweep, and Lathe. Explore Boolean operations for complex shape creation. Delve into Mesh Modeling, enabling manual mesh editing for customized objects. Mesh Modeling: Navigate mesh modeling tools in 3ds Max. Model hard surface objects using mesh modeling and other techniques. Unleash creativity in modeling various objects. Material Creation and Application: Understand material basics and texture application. Create, apply, and resize materials on models. Utilize pictures as references for modeling. Apply multiple materials to one object. Incorporate transparency, reflection, and self-illuminating textures. Utilize images with transparency for intricate texture designs. Camera Control Techniques: Learn camera creation and viewpoint adjustment. Modify camera focal length and lock settings for stability. Adjust camera exposure for desired image brightness. Explore cameras with and without targets, understanding their differences. Lighting: Create realistic lighting using daylight systems. Fine-tune daylight settings based on geographical location. Optimize render settings for high-quality output. Utilize various light types for interior illumination. Master light distribution and apply color filters and textures. Implement HDRI environment images for realistic lighting effects. Animation Essentials: Gain a basic understanding of animation principles. Animate objects manually through keyframing. Create walkthrough animations using cameras and paths. Construct efficient camera rigs for path-based animations. Render animations as video output. Advanced Rendering Techniques: Explore rendering with V-Ray Simulate daylight systems and interior lighting in V-Ray Set up studio lighting configurations in both V-Ray advanced rendering. Course Requirements: A computer with 3ds Max and Vray installed (trial versions available on Autodesk and Chaos Group websites) Basic familiarity with 3D modeling concepts is beneficial but not mandatory Enthusiasm for learning 3ds Max and Vray to create impressive 3D models, visualizations, and animations

This Level 4 Diploma in Cyber Security qualification (Accredited by Qualifi, UK) has been created to develop those learners who are looking to choose, or already have chosen, a career in a business-related sector. It is envisaged that this programme will encourage both academic and professional development so that your learners move forward to realise not just their own potential but also that of organisations across a broad range of sectors. The Level 4 Diploma in Cyber Security rationale of the programme is to provide a career path for learners who wish to develop their core capabilities within the cyber security and risk management sector. The outcome of the Diploma, which is a recognised UK qualification, is for learners to develop the cyber security skills required by organisations globally. In doing so, the qualification looks to develop the cyber security team leaders, managers and leaders of the future through the creation and delivery of learning appropriate for that industry. Key Highlights of this Level 4 Diploma in Cyber Security qualification are: Program Duration: 9 Months (Fast track 6 months duration mode Available) Program Credits: 120 Designed for working Professionals Format: Online No Written Exam. The Assessment is done via Submission of Assignment Tutor Assist available Dedicated Student Success Manager Timely Doubt Resolution Regular Networking Events with Industry Professionals Become eligible to gain direct entry into relevant Undergraduate degree programme. Alumni Status No Cost EMI Option Requirements This Level 4 Diploma in Cyber Security (Accredited by Qualifi, UK) qualifications has been designed to be accessible without artificial barriers that restrict access and progression. Entry to the qualification will be through centre interview and learners will be expected to hold the following: Qualifications at Level 3 OR A Level 4 qualification in another discipline and want to develop their careers in Cyber Security or Information Technology. Career path Learners after completing this course progress to: Level 5 Diploma in Cyber Security, Diploma in Information Technology level - 5 (fast track) , BEng (Hons) in Software Engineering Degree, BSc (Hons) in Business Computing and Information Systems, Level 5 Diploma in Business Enterprise (fast track), The Second Year of Undergraduate study, Directly into employment in an associated profession. Certificates Certificate of Achievement Hard copy certificate - Included Qualifi courses: Once you complete the course, you would be receiving a Physical hard copy of your Diploma along with its Transcript which we would Courier to your address via DHL or Royal Mail without any additional charge

Sale Ends Today Automotive Engineering & Design Masterclass Admission Gifts FREE PDF & Hard Copy Certificate| PDF Transcripts| FREE Student ID| Assessment| Lifetime Access| Enrolment Letter Are you a professional feeling stuck in your career, or perhaps you're a beginner, unsure of where to start or how to break into your desired field? Whichever stage you're in, our exclusive Basic Automotive Engineering & Design Masterclass Bundle provides unique insights and tools that can help you achieve your goals. So, get ready to accelerate your career and become a leader in automotive engineering in the UK automotive sector, which is rapidly evolving with the advent of electric and hybrid technologies. The Automotive Engineering & Design Masterclass spans a wide array of critical subjects to mold you into a highly skilled automotive professional. Starting with essentials such as Automotive Engineering: Onboard Diagnostics and progressing to complex areas like Electric and Hybrid Vehicles Engineering, this course ensures a deep understanding of both foundational and advanced concepts. It also focuses on topics like Car Mechanic and Repair Training, while specialised modules like Electric Vehicle Battery Management System and Turbocharging equip you with niche skills that are highly valued in the industry. Courses Are Included In this Bundle: Course 01: Automotive Engineering: Onboard Diagnostics Course 02: Automotive Design Course 03: Automotive Engineering: Electric and Hybrid Vehicles Engineering Course 04: Automotive Engineering: Car Mechanic and Repair Training Course 05: Automotive Engineering: Supercharger Automobile Engineering Course 06: Automotive Engineering: Engine Lubrication Systems Online Course Course 07: A complete course on Turbocharging Course 08: Car Maintenance and Safety Training Course 09: Motorbike Maintenance & Servicing Course 10: Electric Vehicle Battery Management System Course 11: Vehicle Routing Problem with Spreadsheet Course 12: Power Electronics for Electrical Engineering Course 13: MATLAB Simulink for Electrical Power Engineering Course 14: Large Goods Vehicle (LGV)/HGV Course 15: Hybrid Vehicle Expert Training Course 16: MET Technician Course 17: Energy Saving in Electric Motors Course 18: Mechanical Engineering Course 19: Engineering Mechanics Course for Beginners Course 20: Electrical Machines for Electrical Engineering Course 21: Electrical Engineering - Light Current System Course 22: Heating Ventilation and Air Conditioning (HVAC) Technician Course 23: Electrical Engineering With Electric Circuits Course 24: Electronic Device Maintenance and Troubleshooting Course Course 25: Trigonometry for Electrical Engineering Course 26: Robotics - Sensors Course 27: Manual Handling Course 28: Workshop Technology: Machine Shop Theory Course 29: Good Manufacturing Practices (GMP) Course 30: Fire Safety Step into the future of automotive technology by mastering the skills taught in the Automotive Engineering & Design Masterclass. This comprehensive training will not only elevate your technical and design capabilities but also enhance your career prospects in a sector that is integral to technological advancement and environmental sustainability. Enrol now to transform your passion for automotive technology into a rewarding career that helps shape the future of transportation! Learning Outcomes of this Bundle: Diagnose and troubleshoot with advanced onboard diagnostics skills. Design and engineer cutting-edge electric and hybrid vehicles. Master mechanical aspects of supercharging and turbocharging technologies. Effectively maintain and repair diverse automotive systems. Develop comprehensive skills in battery management for electric vehicles. Apply modern electrical engineering principles to automotive technology. But that's not all. When you enrol in Automotive Engineering & Design Masterclass Training, you'll receive 30 CPD-Accredited PDF Certificates, Hard Copy Certificates, and our exclusive student ID card, all absolutely free. Why Prefer this Course? Get a Free CPD Accredited Certificate upon completion of the course Get a Free Student ID Card with this training program (£10 postal charge will be applicable for international delivery) The course is Affordable and Simple to understand Get Lifetime Access to the course materials The training program comes with 24/7 Tutor Support Start your learning journey straight away! The Automotive Engineering & Design Masterclass is expertly designed to ensure that you emerge as a highly proficient professional, ready to tackle the challenges of the modern automotive industry. This course will empower you with advanced onboard diagnostics skills, a foundational aspect of automotive engineering that is critical in the era of high-tech vehicles. By understanding how to diagnose and troubleshoot vehicle systems effectively, you'll be able to offer invaluable insights and solutions in difficult scenarios, significantly enhancing your employability and career advancement opportunities. Furthermore, the masterclass dives deep into the design and engineering of electric and hybrid vehicles, placing you at the forefront of automotive innovation. As the industry shifts towards sustainable and eco-friendly solutions, your ability to engineer these advanced vehicles will position you as a key player in driving the future of transportation. This expertise not only boosts your career potential but also aligns you with global trends towards green technology. Moreover, this diploma offers learners the opportunity to acquire a Recognised Qualification that is highly valued in the field of Automotive Engineering. With this Certification, graduates are better positioned to pursue career advancement and higher responsibilities within the Automotive Engineering setting. The skills and knowledge gained from this course will enable learners to make meaningful contributions to Automotive Engineering related fields impacting their Automotive Engineering experiences and long-term development. Course Curriculum Course 01: Automotive Engineering: Onboard Diagnostics Module 01: Introduction Module 02: Brief history Basic working of OBD Module 03: Onboard diagnostic apps Module 04: Exhaust gas - Diagnostics Module 05: APPS on Onboard diagnostics Module 06: Engine - Diagnostics Module 07: Diagnostics - spark plug Module 08: Diagnostics - Fuel injection Module 09: Diagnosis - Lubrication Course 02: Automotive Design Module 01: Emotion and Flow: Secrets of Car Designer Line Quality Module 02: Get Inspired: Developing Your Style and Technique with Speed Forms Module 03: Master Your Wheels: Secrets of Drawing Circles Module 04: Talk the Talk: The Vocabulary of Automotive Design Module 05: In the Beginning: Secrets of Drawing Great Side Views Module 06: Coming and Going: Secrets of Drawing Great Front and Rear Views Module 07: A View from the Top: Secrets of Drawing a Tip-Up View Module 08: Toward the Within: Introduction to Interiors Module 09: In a Brilliant Light: Understanding Light and Shadows Module 10: Shine Like it does: Understanding Reflections Course 03: Automotive Engineering: Electric and Hybrid Vehicles Engineering Module 01: Introduction Module 02: Key Motivations for HEVs Rise Module 03: What is HEV & world famous models Module 04: Architecture of Hybrid Electric vehicles Module 05: Parallel Hybrid Vehicles Module 06: Other types of Architecture Module 07: Modes of Operation Module 08: Engine & Motor Module 09: Motor Efficiency Module 10: Generator & Power Split Device Module 11: Battery storage systems Module 12: Fundamentals of Regenerative Braking =========>>>>> And 27 More Courses <<<<<========= How will I get my Certificate? After successfully completing the course, you will be able to order your Certificates as proof of your achievement. PDF Certificate: Free (Previously it was £12.99*30 = £390) CPD Hard Copy Certificate: Free (For The First Course: Previously it was £29.99) CPD 300 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone interested in learning more about the topic is advised to take this bundle. This bundle is ideal for: Aspiring automotive engineers. Current auto mechanics. Electrical engineering students. Automotive design enthusiasts. Hybrid technology professionals. Manufacturing sector employees. Requirements You will not need any prior background or expertise to enrol in this course. Career path After completing this bundle, you are to start your career or begin the next phase of your career. Automotive Engineer: $68,000 - $110,000 Mechanical Engineer: $70,000 - $100,000 Electrical Engineer: $75,000 - $105,000 Automotive Technician: $40,000 - $65,000 Systems Designer: $85,000 - $120,000 Production Manager: $60,000 - $90,000 Certificates CPD Accredited Digital certificate Digital certificate - Included CPD Accredited e-Certificate - Free Enrolment Letter - Free Student ID Card - Free CPD Accredited Hard copy certificate Hard copy certificate - Included If you are an international student, then you have to pay an additional 10 GBP for each certificate as an international delivery charge.

24 Hour Flash Deal **25-in-1 Robotics and Automation Engineering Mega Bundle** Robotics and Automation Engineering Enrolment Gifts **FREE PDF Certificate**FREE PDF Transcript ** FREE Exam** FREE Student ID ** Lifetime Access **FREE Enrolment Letter ** Take the initial steps toward a successful long-term career by studying the Robotics and Automation Engineering package online with Studyhub through our online learning platform. The Robotics and Automation Engineering bundle can help you improve your CV, wow potential employers, and differentiate yourself from the mass. This Robotics and Automation Engineering course provides complete 360-degree training on Robotics and Automation Engineering. You'll get not one, not two, not three, but twenty-five Robotics and Automation Engineering courses included in this course. Plus Studyhub's signature Forever Access is given as always, meaning these Robotics and Automation Engineering courses are yours for as long as you want them once you enrol in this course This Robotics and Automation Engineering Bundle consists the following career oriented courses: Course 01: Robotics - Sensors Course 02: Advanced Arduino for Embedded Systems Course 03: Embedded Systems with 8051 Microcontroller Course 04: Machine Learning Basics Course 05: AutoCAD VBA Programming Course 06: Solidworks Foundation Training Course 07: 3D Modeling for 3D Printing Course 08: AutoCAD Programming using VB.NET with Windows Forms Course 09: Intermediate Solidworks Course Course 10: Learn PCB Printed Circuit Board Course 11: Digital Electric Circuits & Intelligent Electrical Devices Course 12: Electronic Device and Circuits Protection Training Course 13: Electronic & Electrical Devices Maintenance & Troubleshooting Course 14: CNC (Computer Numerical Control) Programming for Machining Course 15: Data Center Training Essentials: Mechanical & Cooling Course 16: Electricity - Theory and Safety Training Course 17: Power Electronics for Electrical Engineering Course 18: Electrical Power System and High Voltage Engineering Course 19: Electrical Engineering for Electrical Substations Course 20: Electric Vehicle Battery Management System Course 21: Engine Lubrication Systems Online Course Course 22: Manual Handling Training Course 23: Mechanical Engineering Course 24: MATLAB Simulink for Electrical Power Engineering Course 25: Solidworks Drawing Tools Training: Test Preparation The Robotics and Automation Engineering course has been prepared by focusing largely on Robotics and Automation Engineering career readiness. It has been designed by our Robotics and Automation Engineering specialists in a manner that you will be likely to find yourself head and shoulders above the others. For better learning, one to one assistance will also be provided if it's required by any learners. The Robotics and Automation Engineering Bundle is one of the most prestigious training offered at StudyHub and is highly valued by employers for good reason. This Robotics and Automation Engineering bundle course has been created with twenty-five premium courses to provide our learners with the best learning experience possible to increase their understanding of their chosen field. This Robotics and Automation Engineering Course, like every one of Study Hub's courses, is meticulously developed and well researched. Every one of the topics is divided into Robotics and Automation Engineering Elementary modules, allowing our students to grasp each lesson quickly. The Robotics and Automation Engineering course is self-paced and can be taken from the comfort of your home, office, or on the go! With our Student ID card you will get discounts on things like music, food, travel and clothes etc. In this exclusive Robotics and Automation Engineering bundle, you really hit the jackpot. Here's what you get: Step by step Robotics and Automation Engineering lessons One to one assistance from Robotics and Automation Engineeringprofessionals if you need it Innovative exams to test your knowledge after the Robotics and Automation Engineeringcourse 24/7 customer support should you encounter any hiccups Top-class learning portal Unlimited lifetime access to all twenty-five Robotics and Automation Engineering courses Digital Certificate, Transcript and student ID are all included in the price PDF certificate immediately after passing Original copies of your Robotics and Automation Engineering certificate and transcript on the next working day Easily learn the Robotics and Automation Engineering skills and knowledge you want from the comfort of your home CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Robotics and Automation Engineering training is suitable for - Students Recent graduates Job Seekers Individuals who are already employed in the relevant sectors and wish to enhance their knowledge and expertise in Robotics and Automation Engineering Requirements To participate in this Robotics and Automation Engineering course, all you need is - A smart device A secure internet connection And a keen interest in Robotics and Automation Engineering Career path You will be able to kickstart your Robotics and Automation Engineering career because this course includes various courses as a bonus. This Robotics and Automation Engineering is an excellent opportunity for you to learn multiple skills from the convenience of your own home and explore Robotics and Automation Engineering career opportunities. Certificates CPD Accredited Certificate Digital certificate - Included CPD Accredited e-Certificate - Free CPD Accredited Hardcopy Certificate - Free Enrolment Letter - Free Student ID Card - Free

3D Printing Training Course for Product Designers
By ATL Autocad Training London
Who is this course for? The 3D Printing Bespoke 1-on-1 Training Course is designed for individuals seeking personalized instruction and hands-on experience in the field of 3D printing. Click here for more info: Website Training: 40 hrs, split as per your availability. When: 9 a.m. to 7 p.m., Mon-Sat. Call 02077202581 to reserve. Live online, or in-person. Option A: AutoCAD 10 hrs, Rhino 16 hrs, Vray 4 hrs, Photoshop 4 hrs, 3D Printing 6 hrs Option B: AutoCAD 12 hrs, 3ds Max 16 hrs, Vray 4 hrs, Photoshop 4 hrs, 3D Printing 4 hrs. Option A: AutoCAD, Rhino, Vray, Photoshop, 3D Printing (Total: 40 hours) AutoCAD (10 hours): Module 1: Introduction to AutoCAD (2 hours) Familiarization with AutoCAD interface and tools Creating, opening, and saving drawings Basic drawing and editing commands Module 2: Drawing and Editing (3 hours) Lines, circles, and arcs Polylines and polygons Modifying objects: Move, Copy, Rotate, and Scale Module 3: Precision Drawing (3 hours) Using coordinate systems Dimensioning and text Hatching and gradients Module 4: Advanced Tools (2 hours) Blocks and attributes Layers and object properties Creating layouts and plotting Rhino (16 hours): Module 1: Introduction to Rhino (2 hours) Navigating the Rhino interface Basic 2D and 3D modeling concepts Creating and manipulating objects Module 2: Advanced Modeling (6 hours) Modeling with curves and surfaces Editing and transforming geometry Building complex 3D structures Module 3: Visualization with Vray (4 hours) Understanding the Vray rendering engine Applying materials and textures Setting up lighting and cameras for realistic rendering Module 4: Presentation and Editing (2 hours) Exporting and sharing Rhino models Post-processing and enhancing designs Photoshop (4 hours): Module 1: Introduction to Photoshop (2 hours) Navigating Photoshop interface Image resolution and size Basic image editing tools Module 2: Image Editing and Enhancement (2 hours) Adjusting colors and tones Using layers and masks Retouching and image manipulation 3D Printing (6 hours): Module 1: Introduction to 3D Printing (2 hours) Basics of 3D printing technology Understanding file formats and requirements Module 2: Preparing 3D Models (2 hours) Model optimization for 3D printing Creating supports and rafts Ensuring successful prints Option B: AutoCAD, 3ds Max, Vray, Photoshop, 3D Printing (Total: 38 hours) AutoCAD (12 hours): Module 1: Introduction to AutoCAD (2 hours) Overview of AutoCAD interface and tools Creating, opening, and saving drawings Basic drawing and editing commands Module 2: Drawing and Editing (3 hours) Lines, circles, and arcs Polylines and polygons Modifying objects: Move, Copy, Rotate, and Scale Module 3: Precision Drawing (3 hours) Using coordinate systems Dimensioning and text Hatching and gradients Module 4: Advanced Tools (4 hours) Blocks and attributes Layers and object properties Creating layouts and plotting 3ds Max (16 hours): Module 1: Introduction to 3ds Max (2 hours) Exploring the 3ds Max interface Navigating viewports and objects Basic modeling techniques Module 2: 3D Modeling (6 hours) Creating and editing 3D objects Modifiers and deformations Working with shapes and splines Module 3: Visualization with Vray (4 hours) Setting up lights and cameras Rendering settings and options Post-production and compositing Photoshop (4 hours): Module 1: Introduction to Photoshop (2 hours) Navigating Photoshop interface Image resolution and size Basic image editing tools Module 2: Image Editing and Enhancement (2 hours) Adjusting colors and tones Using layers and masks Retouching and image manipulation 3D Printing (4 hours): Module 1: Introduction to 3D Printing (2 hours) Basics of 3D printing technology Understanding file formats and requirements Module 2: Preparing 3D Models (2 hours) Model optimization for 3D printing Creating supports and rafts Ensuring successful prints Training Duration: 40 hours Flexible Timings: Students can choose their preferred time slots based on our availability, operating from 9:00 am to 7:00 pm (Monday to Saturday). Pricing Details: Company Rate: £1200 (Plus 20% VAT) = £1440 inc VAT. Student, Self-Financed, and Live Online Rate: £1000 (Plus 20% VAT) = £1200 inc VAT. Who Should Enroll: This course caters to a wide range of individuals, including: Novices: Perfect for beginners unfamiliar with AutoCAD, 3ds Max, Adobe Photoshop, Rhino, Vray, and 3D printing, providing a solid foundational understanding. Architects and Interior Designers: Tailored insights for professionals seeking precision in enhancing their design skills, valuable for design firms. Industry Professionals: Establishes industry benchmarks, offering adaptable education applicable across sectors like interior design, architecture, and civil engineering. Learning Approach: Hands-On Practicality: Emphasizes practical, real-world skills through personalized one-on-one training, available in face-to-face or live online sessions. Step-by-Step Instruction: Experienced instructors guide you systematically through techniques using AutoDesk AutoCAD, Autodesk 3ds Max, Adobe Photoshop, and Trimble Sketchup. What You'll Receive: Certificate of Achievement: Upon completion, receive a certificate validating your expertise. Comprehensive Training Guide: Access an extensive PDF guide compatible with both Windows and MAC. Live Feedback: Connect with your tutor for real-time feedback during sessions and the option to record each session for future reference. Our Benefits: Price Assurance: Guaranteeing exceptional value for your career investment. Personalized Training: Tailored one-on-one sessions, adjusting to your learning pace and style. Flexible Scheduling: Choose your preferred training time and day, available Monday to Sunday, from 9 am to 8 pm. Lifetime Support: Ongoing email and phone support beyond the course completion. Computer Setup Assistance: We assist in configuring your computer for seamless software installation. Referral Benefits: Recommend a friend and enjoy discounts, including significant savings on group training courses. Advantages of Option A: Diverse Skill Enhancement: Acquire proficiency in AutoCAD, Rhino, Vray, Photoshop, and 3D Printing, expanding your skill repertoire. Career Opportunities: Access a wide range of career paths in design, architecture, and 3D printing fields, enhancing your professional prospects. Compelling Visualizations: Craft realistic and visually appealing 3D renderings using Vray, elevating the quality of your design presentations. Image Editing Expertise: Master the art of enhancing design projects with Photoshop, adding finesse to your creative work. Prototyping Prowess: Develop essential skills in 3D Printing, enabling you to create physical design prototypes for various applications. Advantages of Option B: Versatile Skill Mastery: Excel in AutoCAD, 3ds Max, Vray, Photoshop, and 3D Printing, gaining expertise in diverse areas of design and visualization. Career Advancement: Unlock opportunities in architecture, animation, and visualization fields, broadening your career horizons. High-Quality Renderings: Showcase your designs impressively with high-quality renderings generated through Vray, leaving a lasting impact on viewers. Image Editing Mastery: Polish your design concepts and presentations using advanced Photoshop techniques, ensuring your visuals are refined and professional. 3D Printing Expertise: Bring your digital designs to life across various industries, mastering the intricate art of 3D printing. Our training courses cater to both Mac and Windows operating systems and provide: Price Assurance: Ensuring the best value for your investment. Personalized Attention: Benefit from one-on-one training sessions tailored to your learning pace and style. Flexible Scheduling: Choose your preferred time and day for training sessions, available seven days a week from 9 am to 8 pm. Ongoing Support: Enjoy lifetime email and phone support, ensuring you're never alone on your learning journey. Technical Assistance: Receive guidance in configuring your computer for software installation, ensuring a seamless learning experience. Special Benefits: Avail special discounts when you refer a friend and significant savings on group training courses, maximizing the value of your training investment.

Online IAM Diploma D23005
By Asset Management Consulting (Asset Management Academy)
Online Asset Management Diploma course. Sit the IAM Diploma anywhere in the world

ISO 13485 Quality Management Foundation
By Training Centre
ISO 13485 Foundation training enables you to learn the basic elements to implement and manage a Medical Devices Quality Management System (MDQMS) as specified in ISO 13485. During this training course, you will be able to understand the different modules of a MDQMS, including MDQMS policy, procedures, performance measurements, management commitment, internal audit, management review and continual improvement. After completing this course, you can sit for the exam and gain "Certified ISO 13485 Foundation' Certification. This Certificate shows that you have understood the fundamental methodologies, requirements, framework and management approach. About This Course Learning Objectives Understand the elements and operations of a Medical Devices Quality Management System (MDQMS) Acknowledge the correlation between ISO 13485 and other standards and regulatory frameworks Understand the approaches, methods and techniques used for the implementation and management of a MDQMS Course Agenda Day 1: Introduction to Medical Devices Quality Management System (MDQMS) concepts as required by ISO 13485 Day 2: Medical Devices Quality Management System requirements and Certification Exam Assessment Delegates sit a combined exam, consisting of in-course quizzes and exercises, as well as a final 40 question, multiple choice exam on Day 2 of the course. The overall passing score is 70%, to be achieved within the 60 minute time allowance. Exam results are provided within 24 hours, with both a Certificate and a digital badge provided as proof of success. Prerequisites None What's Included? Certification fees are included on the exam price Training material containing over 200 pages of information and practical examples will be distributed An attestation of course completion worth 14 CPD (Continuing Professional Development) credits will be issued to the participants who have attended the training course. Who Should Attend? Individuals involved in Medical Devices Quality Management Individuals seeking to gain knowledge about the main processes of Medical Devices Quality Management Systems (MDQMS) Individuals interested to pursue a career in Medical Devices Quality Management Accreditation Provided by This course is Accredited by NACS and Administered by the IECB
Search By Location
- Systems Courses in London
- Systems Courses in Birmingham
- Systems Courses in Glasgow
- Systems Courses in Liverpool
- Systems Courses in Bristol
- Systems Courses in Manchester
- Systems Courses in Sheffield
- Systems Courses in Leeds
- Systems Courses in Edinburgh
- Systems Courses in Leicester
- Systems Courses in Coventry
- Systems Courses in Bradford
- Systems Courses in Cardiff
- Systems Courses in Belfast
- Systems Courses in Nottingham