- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Business Analysis Fundamentals
By IIL Europe Ltd
Business Analysis Fundamentals This course is part of IIL's Business Analysis Certificate Program (BACP), a program designed to help prepare individuals to pass the IIBA® Certification exam to become a Certified Business Analysis Professional (CBAP™). This course teaches participants the overall process of business analysis and where it fits in the bigger picture of the project life cycle and the business context. The course is interactive and combines discussion, active workshops, and demonstrations of techniques. The goal is bottom-line results that cut through the real-world problems facing people seeking to improve the way they operate to develop new and improved systems and products or otherwise deliver results through project performance. What you will Learn At the end of this program, you will be able to: Define the solution scope Work with the development team in the systems testing stage Ensure the solution is usable in the business environment Foundation Concepts Defining the business analyst (BA) function The role of the BA as change agent An introduction to the BABOK® Guide BA roles and relationships through the project life cycle (PLC) Business Analysis Planning and Monitoring Overview of business analysis planning and monitoring (BAP&M) Business analysis planning and monitoring - process and tools Business analysis planning and monitoring - roles and responsibilities Business analysis planning and monitoring - governance, information management, and performance improvement Elicitation and Collaboration Overview of elicitation and collaboration Elicitation and collaboration techniques Requirements Life Cycle Management Overview of requirements life cycle management Requirements life cycle management task details Strategy Analysis Overview of strategy analysis Analyze current state Define future state Assess risks Define change strategy Requirements Analysis and Design Definition Overview of requirements analysis and design definition (RA&DD) The anatomy of requirements RA&DD task descriptions RA&DD techniques Solution Evaluation Overview of solution evaluation Solution evaluation tasks Solution evaluation in development stages Underlying Competencies Overview of underlying competencies (UC) Underlying competencies

Business Analysis Fundamentals: In-House Training
By IIL Europe Ltd
Business Analysis Fundamentals: In-House Training This course is part of IIL's Business Analysis Certificate Program (BACP), a program designed to help prepare individuals to pass the IIBA® Certification exam to become a Certified Business Analysis Professional (CBAP™). This course teaches participants the overall process of business analysis and where it fits in the bigger picture of the project life cycle and the business context. The course is interactive and combines discussion, active workshops, and demonstrations of techniques. The goal is bottom-line results that cut through the real-world problems facing people seeking to improve the way they operate to develop new and improved systems and products or otherwise deliver results through project performance. What you will Learn At the end of this program, you will be able to: Define the solution scope Work with the development team in the systems testing stage Ensure the solution is usable in the business environment Foundation Concepts Defining the business analyst (BA) function The role of the BA as change agent An introduction to the BABOK® Guide BA roles and relationships through the project life cycle (PLC) Business Analysis Planning and Monitoring Overview of business analysis planning and monitoring (BAP&M) Business analysis planning and monitoring - process and tools Business analysis planning and monitoring - roles and responsibilities Business analysis planning and monitoring - governance, information management, and performance improvement Elicitation and Collaboration Overview of elicitation and collaboration Elicitation and collaboration techniques Requirements Life Cycle Management Overview of requirements life cycle management Requirements life cycle management task details Strategy Analysis Overview of strategy analysis Analyze current state Define future state Assess risks Define change strategy Requirements Analysis and Design Definition Overview of requirements analysis and design definition (RA&DD) The anatomy of requirements RA&DD task descriptions RA&DD techniques Solution Evaluation Overview of solution evaluation Solution evaluation tasks Solution evaluation in development stages Underlying Competencies Overview of underlying competencies (UC) Underlying competencies

https://www.transmedia.co.uk/course/figma-advanced This intensive two-day Advanced Figma course builds on your existing Figma knowledge. Through hands-on exercises, you will learn to use auto layout for resilient UX and component systems for scalable design. The course covers collaborating at scale with libraries, permissions, and version control for real-world workflows. Prototyping and accessibility best practices are woven throughout to help you create effective products. You will leave equipped with deep Figma knowledge to translate stunning, functional designs from concept to launch. All our Figma courses are taught by industry professionals who will share years of their industry experience with you, imparting best practice techniques as well mastery of the tools. Topics covered include Advanced auto layout, Components in depth, Using variables, Design systems in figma, Advanced prototyping techniques, Accessibility features, Improving team collaboration and Handoff to developers.

VMware training course description This five-day VMware course features intensive handson training that focuses on installing, configuring, and managing VMware vSphere 8, which includes VMware ESXi 8 and VMware vCenter 8. This course prepares you to administer a vSphere infrastructure for an organization of any size. This course is the foundation for most VMware technologies in the software-defined data center. What will you learn Install and configure ESXi hosts. Deploy and configure vCenter. Create virtual networks using standard and distributed switches. Configure VMs, templates, clones, and snapshots. Manage virtual machine resource allocation. Migrate virtual machines with vSphere vMotion and vSphere Storage vMotion. VMware training course details Who will benefit: Systems administrators and engineers. Prerequisites: Introduction to data communications & networking. Windows/Linux Administration. Duration 5 days VMware training course contents Course Introduction Introductions and course logistics. Course objectives vSphere and Virtualization Overview Explain basic virtualization concepts, Describe how vSphere fits in the software-defined data center and the cloud infrastructure, Recognize the user interfaces for accessing vSphere, Explain how vSphere interacts with CPUs, memory, networks, storage, and GPUs Installing and Configuring ESXi Install an ESXi host, Recognize ESXi user account best practices, Configure the ESXi host settings using the DCUI and VMware Host Client Deploying and Configuring vCenter Recognize ESXi hosts communication with vCenter, Deploy vCenter Server Appliance, Configure vCenter settings, Use the vSphere Client to add and manage license keys, Create and organize vCenter inventory objects, Recognize the rules for applying vCenter permissions, View vCenter logs and events Configuring vSphere Networking Configure and view standard switch configurations, Configure and view distributed switch configurations, Recognize the difference between standard switches and distributed switches, Explain how to set networking policies on standard and distributed switches Configuring vSphere Storage Recognize vSphere storage technologies, Identify types of vSphere datastores, Describe Fibre Channel components and addressing, Describe iSCSI components and addressing, Configure iSCSI storage on ESXi, Create and manage VMFS datastores, Configure and manage NFS datastores Deploying Virtual Machines Create and provision VMs, Explain the importance of VMware Tools, Identify the files that make up a VM Recognize the components of a VM, Navigate the vSphere, Client and examine VM settings and options, Modify VMs by dynamically increasing resources, Create VM templates and deploy VMs from them, Clone VMs, Create customization specifications for guest operating systems, Create local, published, and subscribed content libraries, Deploy VMs from content libraries, Manage multiple versions of VM templates in content libraries Managing Virtual Machines Recognize the types of VM migrations that you can perform within a vCenter instance and across vCenter instances, Migrate VMs using vSphere vMotion, Describe the role of Enhanced vMotion Compatibility in migrations, Migrate VMs using vSphere Storage vMotion, Take a snapshot of a VM, Manage, consolidate, and delete snapshots, Describe CPU and memory concepts in relation to a virtualized environment, Describe how VMs compete for resources Define CPU and memory shares, reservations, and limits Deploying and Configuring vSphere Clusters Create a vSphere cluster enabled for vSphere DRS and vSphere HA, View information about a vSphere cluster Explain how vSphere DRS determines VM placement on hosts in the cluster, Recognize use cases for vSphere DRS settings, Monitor a vSphere DRS cluster Describe how vSphere HA responds to various types of failures, Identify options for configuring network redundancy in a vSphere HA cluster, Recognize vSphere HA design considerations, Recognize the use cases for various vSphere HA settings, Configure a vSphere HA cluster, Recognize when to use vSphere Fault Tolerance Managing the vSphere Lifecycle Enable vSphere Lifecycle Manager in a vSphere cluster, Describe features of the vCenter Update Planner, Run vCenter upgrade prechecks and interoperability reports, Recognize features of vSphere Lifecycle Manager, Distinguish between managing hosts using baselines and managing hosts using images, Describe how to update hosts using baselines, Describe ESXi images, Validate ESXi host compliance against a cluster image and update ESXi hosts, Update ESXi hosts using vSphere Lifecycle Manager, Describe vSphere Lifecycle Manager automatic recommendations, Use vSphere Lifecycle Manager to upgrade VMware Tools and VM hardware

Artificial Lift and Real-Time Production Optimization in Digital Oilfield
By EnergyEdge - Training for a Sustainable Energy Future
About this training course Artificial lift systems are an important part of production operations for the entire lifecycle of an asset. Often, oil and gas wells require artificial lift for most of the life cycle. This 5-day training course offers a thorough treatment of artificial lift techniques including design and operation for production optimization. With the increasing need to optimize dynamic production in highly constrained cost environments, opportunities and issues related to real-time measurements and optimization techniques needs to be discussed and understood. Artificial lift selection and life cycle analysis are covered. These concepts are discussed and reinforced using case studies, quizzing tools, and exercises with software. Participants solve examples and class problems throughout the course. Animations and videos reinforce the concepts under discussion. Understanding of these important production concepts is a must have to exploit the existing assets profitably. Unique Features: Hands-on usage of SNAP Software to solve gas-lift exercises Discussion on digital oil field Machine learning applications in gas-lift optimization Training Objectives After the completion of this training course, participants will be able to: Understand the basics and advanced concepts of each form of artificial lift systems including application envelope, relative strengths, and weaknesses Easily recognize the different components from downhole to the surface and their basic structural and operational features Design and analyze different components using appropriate software tools Understand challenges facing artificial lift applications and the mitigation of these challenges during selection, design, and operation Learn about the role of digital oilfield tools and techniques and their applications in artificial lift and production optimization Learn about use cases of Machine learning and artificial intelligence in the artificial lift Target Audience This training course is suitable and will greatly benefit the following specific groups: Production, reservoir, completion, drilling and facilities engineers, analysts, and operators Anyone interested in learning about selection, design, analysis and optimum operation of artificial lift and related production systems will benefit from this course. Course Level Intermediate Advanced Training Methods The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training environment is highly stimulating, challenging, and effective because the participants will learn by case studies which will allow them to apply the material taught in their own organization. Course Duration: 5 days in total (35 hours). Training Schedule 0830 - Registration 0900 - Start of training 1030 - Morning Break 1045 - Training recommences 1230 - Lunch Break 1330 - Training recommences 1515 - Evening break 1530 - Training recommences 1700 - End of Training The maximum number of participants allowed for this training course is 20. This course is also available through our Virtual Instructor Led Training (VILT) format. Prerequisites: Understanding of petroleum production concepts. Each participant needs a laptop/PC for solving class examples using software to be provided during class. Laptop/PC needs to have a current Windows operating system and at least 500 MB free disk space. Participants should have administrator rights to install software. Trainer Your expert course leader has over 35 years' work-experience in multiphase flow, artificial lift, real-time production optimization and software development/management. His current work is focused on a variety of use cases like failure prediction, virtual flow rate determination, wellhead integrity surveillance, corrosion, equipment maintenance, DTS/DAS interpretation. He has worked for national oil companies, majors, independents, and service providers globally. He has multiple patents and has delivered a multitude of industry presentations. Twice selected as an SPE distinguished lecturer, he also volunteers on SPE committees. He holds a Bachelor's and Master's in chemical engineering from the Gujarat University and IIT-Kanpur, India; and a Ph.D. in Petroleum Engineering from the University of Tulsa, USA. Highlighted Work Experience: At Weatherford, consulted with clients as well as directed teams on digital oilfield solutions including LOWIS - a solution that was underneath the production operations of Chevron and Occidental Petroleum across the globe. Worked with and consulted on equipment's like field controllers, VSDs, downhole permanent gauges, multiphase flow meters, fibre optics-based measurements. Shepherded an enterprise-class solution that is being deployed at a major oil and gas producer for production management including artificial lift optimization using real time data and deep-learning data analytics. Developed a workshop on digital oilfield approaches for production engineers. Patents: Principal inventor: 'Smarter Slug Flow Conditioning and Control' Co-inventor: 'Technique for Production Enhancement with Downhole Monitoring of Artificially Lifted Wells' Co-inventor: 'Wellbore real-time monitoring and analysis of fracture contribution' Worldwide Experience in Training / Seminar / Workshop Deliveries: Besides delivering several SPE webinars, ALRDC and SPE trainings globally, he has taught artificial lift at Texas Tech, Missouri S&T, Louisiana State, U of Southern California, and U of Houston. He has conducted seminars, bespoke trainings / workshops globally for practicing professionals: Companies: Basra Oil Company, ConocoPhillips, Chevron, EcoPetrol, Equinor, KOC, ONGC, LukOil, PDO, PDVSA, PEMEX, Petronas, Repsol, , Saudi Aramco, Shell, Sonatrech, QP, Tatneft, YPF, and others. Countries: USA, Algeria, Argentina, Bahrain, Brazil, Canada, China, Croatia, Congo, Ghana, India, Indonesia, Iraq, Kazakhstan, Kenya, Kuwait, Libya, Malaysia, Oman, Mexico, Norway, Qatar, Romania, Russia, Serbia, Saudi Arabia, S Korea, Tanzania, Thailand, Tunisia, Turkmenistan, UAE, Ukraine, Uzbekistan, Venezuela. Virtual training provided for PetroEdge, ALRDC, School of Mines, Repsol, UEP-Pakistan, and others since pandemic. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

Essential optical transmission course description Transmission is the process of sending information along a medium of, copper, fibre or wireless. This course looks at transmission techniques for fibre networks. The course aims to demystify the technologies involved by explaining all the buzzwords used in optical transmission. What will you learn Describe various optical transmission technologies. Explain how SDH and OTN work. Explain how WDM, CWDM and DWDM work. Explain PON, GPON and GEPON. Essential optical transmission course details Who will benefit: Anyone working in telecommunications. Prerequisites: None. Duration 2 days Essential optical transmission course contents Transmission basics nsmission basics Systems, media, signals. Signal degradation, noise, distortion, attenuation. Digital, analogue. Modulation, encoding. Fibre transmission Fibre vs copper, optical transmission, fibre characteristics, fibre component parts. Multi Mode Fibre (MMF). Single Mode Fibre (SMF). Fibre connections. Lasers. Attenuations, dispersion, optical signal noise ratios (OSNR) and their effects. Channel Spacing and Signal Direction. Limiting factors to single wavelength. SDH Timing and synchronisation of digital signals, the plesiochronous digital hierarchy (PDH), the synchronous digital hierarchy (SDH), service protection with SDH. TDM. Standards, basic units, frames, STM1 frame, bit rates, STM0, STM1, STM4, STM16, STM64, STM256, SDH architecture, rings, Add drop multiplexors. SDH network topologies, structure of SDH equipment, SDH synchronisation, protection switching in SDH networks, SDH alarm structure, testing of SDH, equipment and systems, Ethernet over SDH. OTN G.709, OTN interface structure, Optical transport modules, ONNI, OCh, OUT, ODU, OPU. G.709 amendments. WDM overview Multiplexing, TDM, WDM benefits. WDM standards. CWDM vs. DWDM. Four Wave Mixing (FWM). Impact and countermeasures to FWM on WDM. DWDM ITU G.694.1, channel and spacing. Optical Terminal Multiplexers (OTM). Optical Add/Drop Multiplexers (OADM). Adding versus dropping. Optical Amplifiers. Erbium Doped Fibre Amplifiers (EDFA). Transponders and Combiners. Optical and Electrical Cross Connects (OXCs/DXCs). Cross Connect types (Transparent/Opaque). Advantages and disadvantages of various Optical cross connects. FTTx Fibre installation and air blown fibre, FTTH, FTTC, FTTN, FTTD, FFTH topologies and wavelengths, active or passive optical network. PON variants Gigabit passive optical network (GPON), Gigabit Ethernet passive optical network (GEPON), Time division PON (TDM-PON), XG-PON, Wave Division Multiplexing PON (WDM-PON), 1Gbps, 10Gbps, 40Ggps, 100Gbps FSAN (Full Service Access Network) NGA (Next Generation Access), Strategies for TDM-PON to WDM-PON migration, Architecture of NG-PON (hybrid WDM/TDM PON), Additional services than triple play.

The City & Guilds 2365 Level 3 Course is the natural progression for anyone who has completed the Level 2 Diploma 2365 course or related level 2 courses. On completion of this course you will then be able to undertake the Level 3 NVQ thus becoming recognised as a fully qualified electrical engineer within the industry with the ability to apply for JIB (Gold Card) membership upon successful completion of the AM2 Assessment. Further information on the Level 3 can be found here: C&G 2365 Level 3 Diploma in Electrical Installations — Optima Electrical Training (optima-ect.com)

Strategic Thinking
By IIL Europe Ltd
Strategic Thinking The goal of this course is to provide you with the building blocks and the motivation to develop the critical skill of strategic thinking. The participants will consider a four-part model that distinguishes strategic thinking from strategic planning and managing. With that understanding, you will investigate the critical components of strategic thinking and how to apply it effectively. What you Will Learn Define strategic thinking and distinguish it from strategic planning and management Explain a high-level approach to gaining strategic thinking skills Integrate other interpersonal skills, such as self-awareness, systems thinking, leadership, constructive conflict, and collaboration, into the fabric of strategic thinking skills Select appropriate techniques to apply strategic thinking in specific situations Recognize and emulate effective strategic thinking behaviors Getting Started Introductions Course structure Course goals and objectives Foundation Concepts Interactive event: Define Strategic Thinking (ST) Interactive event: Discuss relationship of ST with Strategic Planning, Management and Decision Making Strategic Level Framework - Tying it all together Strategic thinking attributes Strategic Thinking Critical Success Factors Strategic Thinking Critical Success Factors - 5-part model Strategic Thinking and the Organization Critical Success Factors Model applied to an organization Tools Introduction (5): Environmental, 5 Forces, SWOT, Value Proposition, Integral Theory of Worldview Video: Fog of War Strategic Thinking and the Individual Critical Success Factors Model applied to an individual Tools Introduction (5): Thinking Styles, Six Thinking Hats, Reverse Thinking, Systems Thinking, Integral Theory of Worldview Strategic Thinking at the Interpersonal and Team Levels Emotional Intelligence - Self Awareness and Working With Others Team Leadership and Trust Constructive Conflict as the Gateway to Collaboration Interactive event: Testing the Models - Challenge Perspective; What's Missing Applying the critical skill of Strategic Thinking Worldview: Team versus client Trusted Advisor Interactive event: Doing what is asked (Case study, wherein participants review the default case scenario prepared for this workshop and add specific details to make the scenario more relevant to their experiences / needs. Teams develop an action plan for applying ST concepts and techniques they have learned here to the situation, then compare and contrast results.)

Autodesk Maya Basics to Advanced Level
By London Design Training Courses
Why Learn Autodesk Maya Basics to Advanced Level Course? Course info. Autodesk Maya is one of the best tools for 3D animation and visual effects. Learn Maya with our training courses covering sectors like Architecture, Games & Films, Animation, and Media. London Design Training Courses empower you to master Maya, transforming your 3d skills.  Duration: 40 hrs Method: 1-on-1. Schedule: Tailor your own schedule by pre-booking a convenient hour of your choice, available from Mon to Sat 9 am and 7 pm. Experience advanced-level Maya training covering essential aspects such as modeling, UV mapping, texturing, lighting, camera movement, and rigging. The course is tailored to your specific requirements and work preferences. You can discuss your learning goals with our trainer, and we will suggest a syllabus that meets your needs. Flexible Training Options: Choose in-class training at one of our UK center or attend live online sessions. Certified Tutors and Authoritative: London Design Training Course has all Autodesk Authorized Trainers. Hands-on Learning Approach: The training is practical and hands-on, combining theory and step-by-step demonstrations. You'll have ample time to practice techniques on your computer with Maya, and you can keep all the files you create. Compatible with Windows and Mac: Maya training is available for both Windows and Mac users, with options to suit any recent version of Maya. Maya Basic to Advanced Course Duration: 40 hours Course Description: In this course, you will learn the fundamental and advanced skills to create complex 3D models and animations using Autodesk Maya software. You will gain knowledge of the Maya interface, tools, and workflow. You will learn the essentials of modeling, texturing, rigging, animating, and rendering 3D models. You will also learn how to create advanced special effects and understand advanced modeling techniques. I. Introduction to Maya (3 hours) Overview of Maya and its Uses Maya interface and basic tools Navigation and viewport controls Creating and saving projects II. Basic Polygon Modeling (6 hours) Polygon modeling basics Creating basic shapes and objects Editing and modifying objects Creating complex objects with extrusions and bevels Creating organic shapes with NURBS III. Intermediate Modeling (6 hours) Advanced polygon modeling techniques Creating complex models with Booleans and deformers Creating and modifying curves and surfaces Creating organic shapes with sculpting tools Creating architectural models IV. Texturing and Materials (6 hours) Introduction to texturing Creating and applying materials Texture mapping and UV unwrapping Creating realistic materials with shaders Painting textures with the 3D paint tool V. Lighting and Rendering (6 hours) Basic lighting techniques Advanced lighting techniques Creating realistic lighting environments Setting up a camera and creating a composition Rendering still images and animations Output options and file formats VI. Animation (9 hours) Introduction to animation Keyframe animation and animation curves Creating and editing animation clips Rigging and animating a simple character Creating and editing motion paths and animation layers Creating complex character rigs Creating lip sync and facial animation Creating realistic animation with dynamics and simulations Cloth Animation Ncloth VII. Rigging (4 hours) Introduction to rigging Creating joints and skeletons Binding skin to joints and creating weight maps Creating simple rigging systems and rigging a character Creating complex rigging systems VIII. Special Effects (4 hours) Particle systems and dynamics Creating and manipulating fluids and fire effects Creating and editing special effects like explosions and smoke Creating advanced simulations with nCloth and nParticles Paint effects Mash Networks and Mash Animation IX. Advanced Rendering Techniques (2 hours) Render layers and passes Global illumination and ambient occlusion Mental Ray rendering and settings X. Conclusion and Next Steps (1 hour) Review of course content Tips for further learning and resources Q&A; and feedback Note: The above course outline is just a suggestion, and the course content and duration can be adjusted according to the needs and level of the learners. Proficiency in Advanced Maya Techniques: Participants will gain advanced skills in various aspects of Maya, including modeling, UV mapping, texturing, lighting, camera movement, and rigging. Tailored Training: The course is customized to meet the specific requirements of participants, focusing on their preferred techniques and work type. Hands-On and Practical Experience: The training is practical and hands-on, allowing participants to practice techniques on their own computers with Maya. Versatility in Operating Systems: Participants will be equipped to use Maya on both Windows and Mac systems. Accredited Certification: Upon successful completion, participants will receive an e-certificate, accredited by Autodesk Certified instructor, confirming their achievement in the Maya training course. Post-Course Support: After the training, participants are entitled to 30 days of email support from their Maya trainer, ensuring assistance with any post-course questions or issues. Up-to-Date and Relevant Learning: The training can be based on any recent version of Maya, providing participants with up-to-date knowledge and skills.
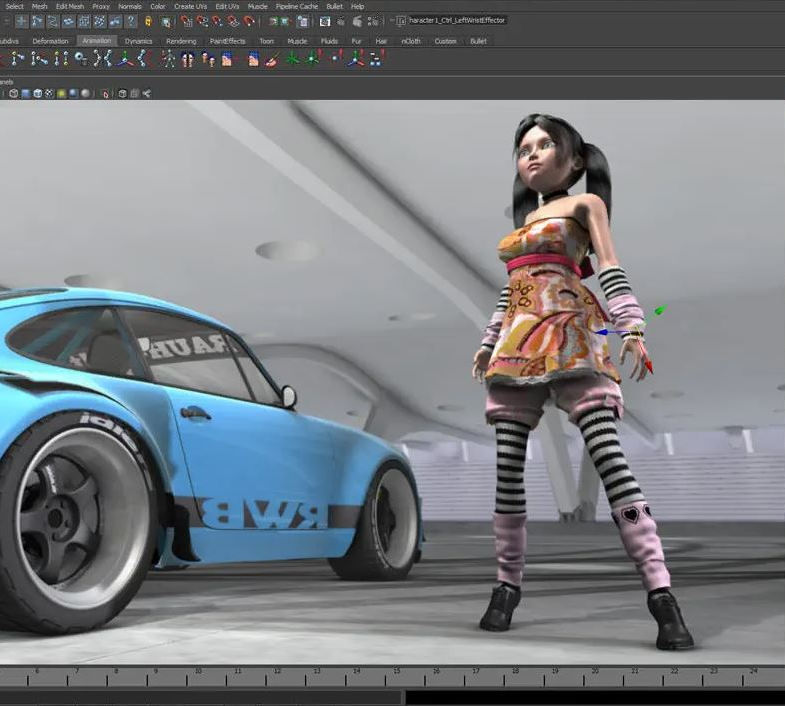
Complete Maya Beginner to Advanced Training
By ATL Autocad Training London
Why Choose Complete Maya Beginner to Advanced Training? Maya's extensive toolkit includes modeling, animation, simulation, and more, amplifying your versatility and influence in the 3D production pipeline. Click here for more info: Website Beginners or those with basic 3D knowledge. No specific digital media background is required. Duration: 40 hours Training Approach: 1-on-1 Sessions. Schedule: Customize your schedule by pre-booking a convenient hour of your choice, available Monday to Saturday between 9 am and 7 pm Course Structure: I. Introduction to Maya (3 hours) Maya Overview and Applications Interface Navigation and Basic Tools Project Creation and Management II. Basic Polygon Modeling (6 hours) Fundamentals of Polygon Modeling Creating and Editing Basic Shapes Advanced Techniques: Extrusions, Bevels, and NURBS for Organic Shapes III. Intermediate Modeling (6 hours) Advanced Polygon Modeling: Booleans, Deformers, and Surfaces Architectural Model Creation Sculpting Tools for Organic Shapes IV. Texturing and Materials (6 hours) Introduction to Texturing and Material Application Texture Mapping, UV Unwrapping, and Shaders Painting Textures with 3D Paint Tool V. Lighting and Rendering (6 hours) Basic and Advanced Lighting Techniques Realistic Lighting Environments Camera Setup, Composition, and Rendering VI. Animation (9 hours) Keyframe Animation and Animation Curves Character Rigging and Animation Complex Character Rigs, Lip Sync, Facial Animation, Dynamics, and Simulations VII. Rigging (4 hours) Skeleton Creation and Joint Binding Weight Maps and Simple to Complex Rigging Systems VIII. Special Effects (4 hours) Particle Systems, Fluid Dynamics, Fire, and Explosions Advanced Simulations with nCloth and nParticles Paint Effects and Mash Networks IX. Advanced Rendering Techniques (2 hours) Render Layers, Passes, and Global Illumination Mental Ray Rendering and Settings X. Conclusion and Next Steps (1 hour) Course Review, Tips for Further Learning Q&A Session and Feedback Please note that the course outline is flexible and can be tailored based on the learners' needs and proficiency levels. Autodesk Maya Basics to Advanced Level Course: Modeling: Surfaces, Control Vertex, Polygons, Extrusion Techniques, Subdiv Modeling, and More Deformations: Twist, Lattice, Flare, Bend Tools Shapes: Lines, Pen Tools, Surface Manipulation Techniques Animations: Keyframe Setup, Path Animations, Skeletons, IK Handles, Skinning Dynamics and Special Effects: Particle Systems, Fluid Dynamics, Lighting Effects, and Advanced Simulations Texturing and Rendering: Diffuse and Bump Mapping, Reflections, Shaders, Lights, and Camera Techniques Fluid Effects and Ncloth: 2D and 3D Containers, Collision Effects, Wind Simulations, and Gravity Control Rendering: Image and Animation Rendering, Playblast, Resolution Controls, and Output Formats. Advanced Modeling: Master intricate 3D models, including polygon, NURBS, and architectural modeling. Expert Texturing: Create realistic textures, apply shaders, and utilize the 3D paint tool. Complex Animation: Rig characters, perform lip sync, facial animation, and dynamic simulations. Special Effects Mastery: Understand particle systems, fluid dynamics, fire effects, and advanced simulations. Rendering Expertise: Grasp advanced rendering techniques, including layers, passes, and global illumination. Comprehensive Rigging: Develop joints, skeletons, and advanced rigging systems for characters and objects. Fluid Dynamics Proficiency: Manipulate 2D/3D fluid containers, create collision effects, and work with wind/gravity simulations. Advanced Lighting and Camera: Perfect lighting, shadows, and special effects. Master camera setups for diverse visual compositions. Recommended Books: "Introducing Autodesk Maya 2023" by Dariush Derakhshani and Randi L. Derakhshani "Mastering Autodesk Maya 2023" by Todd Palamar "Maya Character Creation: Modeling and Animation Controls" by Chris Maraffi "Maya Secrets of the Pros" by John Kundert-Gibbs and Dariush Derakhshani "The Art of 3D Computer Animation and Effects" by Isaac Victor Kerlow Advanced Maya Training Tailored to You: Elevate your Maya skills with specialized training covering essential areas like modeling, UV mapping, texturing, lighting, camera movement, and rigging. Your learning experience is personalized to match your unique requirements and preferences. Discuss your goals with our trainer, and we'll create a syllabus tailored just for you. Flexible Training Choices: Select between in-person sessions at our UK center or attend live online classes, offering convenience and accessibility. Certified Instructors: Benefit from expert guidance provided by Autodesk Authorized Trainers from London Design Training Course. Hands-On Learning: Our practical approach combines theory with step-by-step demonstrations, allowing ample time for hands-on practice on your computer with Maya. You'll retain all the files you create. Compatibility Across Platforms: Maya training caters to both Windows and Mac users, ensuring compatibility with various versions of Maya. Comprehensive Training Package: Participants receive an e-certificate upon successful completion, validating their Maya training. Lifetime Support: Enjoy a lifetime of email support post-training, ensuring assistance with any queries or challenges that arise. Tailored to Your Version: Training can be adapted to your preferred Maya version, ensuring you learn using the most relevant and up-to-date software features. Download Maya https://www.autodesk.co.uk Highly skilled mentors with practical experience. Cutting-edge facilities ensuring an immersive learning environment. Comprehensive courses spanning diverse design disciplines. Practical projects to enhance your portfolio. Networking avenues within the dynamic design community. Skills attuned to current industry trends. Opportunities for professional growth. Choose from flexible in-person or online classes. Internationally recognized training credentials. Engage in London's thriving art and design scene.
Search By Location
- Systems Courses in London
- Systems Courses in Birmingham
- Systems Courses in Glasgow
- Systems Courses in Liverpool
- Systems Courses in Bristol
- Systems Courses in Manchester
- Systems Courses in Sheffield
- Systems Courses in Leeds
- Systems Courses in Edinburgh
- Systems Courses in Leicester
- Systems Courses in Coventry
- Systems Courses in Bradford
- Systems Courses in Cardiff
- Systems Courses in Belfast
- Systems Courses in Nottingham