- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Advanced Game Design Course- 2D & 3D
By iStudy UK
Game Development is the creation of video games which is done by game developers. A game developer can be one person or a large company. To become a game developer, you need to learn the skills and knowledge about video games and how to make one. Many of game developers chose to become one because they are gamers themselves. To become a game development expert, you need to learn both the basics skills and special skills of game development. This course will help you to master the right skills to become successful in the growing game development industry. Course Highlights Advanced Game Design Course- 2D & 3D is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Advanced Game Design Course- 2D & 3D into 26 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 18 hours hours and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Advanced Game Design Course- 2D & 3D Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Advanced Game Design Course- 2D & 3D is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Advanced Game Design Course- 2D & 3D is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Gaming Basics Introduction 01:00:00 Understanding Consoles 01:00:00 Using Your Computer 01:00:00 Using Your Phone 01:00:00 Using the Internet 00:30:00 Where to Find Free Software 01:00:00 Understanding Accessories Dealing with Drugs 00:30:00 Wrapping Up 00:15:00 Developing Games Introduction To Game Creation 01:00:00 Essential Tools 01:00:00 2D Game Creation Software 01:00:00 3D Game Creation Software 01:00:00 3D Game Creation 00:30:00 Game Modification 01:00:00 How To Create a Game on a Social Site 00:30:00 Testing Games Introduction to Game Testing FREE 01:00:00 Two Rules of Game Testing FREE 01:00:00 How to Put a Resume Together 01:00:00 How give Examples During Job Interview 00:30:00 Contacting Game Developers 01:00:00 Use the Correct Search Keywords 01:00:00 Wrapping Up 00:15:00 Additional Study Material 2D Game 00:00:00 Game Development XNA GameStudio 00:00:00 Game QA & Testing 00:00:00 Become A Game Tester 00:00:00 Mock Exam Final Exam

Game Development Course is suitable for anyone aspiring to or already working in this field or simply want to learn deeper into game Development Course. You will be able to add this qualification to your CV by downloading your certificate instantly without any cost. To make this course more accessible for you, we have designed it for both part-time and full-time students. This course is packed into bite-size module for your convenience. You can study at your own pace or become accredited within hours! If you require support, our experienced tutors are always available to help you throughout the comprehensive syllabus of this course and answer all your queries through email. Do you want to become a Gaming Developer? Producing a game that will make people spend money on claims skills and a lot of hard work. Become a Gaming Developer with our most recommended Game Development Course by going through step by step tutorials, and develop a game. This course will provide you with an initiation to game creation, and explains you the crucial tools. Learn the basics of designing a game and grasp about complex 2D & 3D game creation software available in the market. This course will be ideal to help you in discovering how to develop your games and become a professional developer. Who is the course for? Game makers or developers who want to improve their game development skills. People who have an interest in game development and software. Entry Requirement: This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £9 and the hard copy for £15. Also, you can order both PDF and hardcopy certificates for £22. Career path This course opens a new door for you to enter the relevant job market and also gives you the opportunity to acquire extensive knowledge along with required skills to become successful. You will be able to add our qualification to your CV/resume which will help you to stand out in the competitive job industry. Course Curriculum Game Development Course - Updated Version Introduction to game logo design The first question to ask 00:02:00 My game logo design process 00:03:00 The importance of sketching 00:03:00 Basic logos Simple racing game logo design 00:12:00 Simple horror game logo design 00:17:00 Simple logo for a puzzle game 00:18:00 Complex logo designs Cute cartoon game logo design - Part 1 00:14:00 Cute cartoon game logo design - Part 2 00:18:00 Design a sci-fi logo using negative space - Part 1 00:08:00 Design a sci-fi logo using negative space - Part 2 00:16:00 Cartoon fantasy RPG game logo design -Part 1 00:15:00 Cartoon fantasy RPG game logo design -Part 2 00:14:00 Grunge zombie shooter game logo design - Part 1 00:11:00 Grunge zombie shooter game logo design - Part 2 00:19:00 Game Development Course - Old Version Introduction To Game Creation 00:30:00 Essential Tools 01:00:00 Basics of Game Design 01:00:00 2D Game Creation Software 01:00:00 3D Game Creation Software 01:00:00 3D Game Creation 00:30:00 Game Modification 01:00:00 How To Create a Game on a Social Site 00:30:00 Wrapping Up 00:15:00 Additional Supporting Materials 2D Game 00:00:00 Game Development XNA GameStudio 00:00:00 Mock Exam Mock Exam-Game Development Course 00:20:00 Final Exam Final Exam-Game Development Course 00:20:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

MySQL Database Development Mastery
By Packt
This course will help you to get familiarized with the concepts of MySQL Server and MySQL Workbench needed for database development and management. From basic SQL queries and statements to handling relationships and aggregate functions, you will learn all that you need with the help of real-time activities.

Enhance your typing skills with our 'Advanced Typing Training' course. This comprehensive program covers everything from advanced techniques and speed building strategies to specialised tasks and software tools. Ideal for professionals and individuals aiming to improve their typing speed and accuracy, this course offers personalised assessments and practical exercises. Join us to elevate your typing proficiency and efficiency in various professional contexts.

Python Data Science - QLS Machine Learning
By Kingston Open College
QLS Endorsed + CPD QS Accredited - Dual Certification | Instant Access | 24/7 Tutor Support | All-Inclusive Cost

D-Link switches training course description A hands on course covering the product specifics of D-Link switches. Installation, configuration, maintenance and troubleshooting are all covered in a practical oriented way. What will you learn Install D-Link switches. Use the command line interface and the web based interface to manage D-Link switches. Configure and troubleshoot D-Link switches. Perform software upgrades and maintain configurations using TFTP. D-Link switches training course details Who will benefit: Anyone working with D-Link switches. Particularly aimed at engineers and technicians supporting D-Link switches. Prerequisites: None. Duration 2 days D-Link switches training course content Introduction How Ethernet works with hubs, How Ethernet works with switches. Installing D-link switches. Hands on Building a network with a hub, building a network with a D-Link switch. Basic troubleshooting The D-Link switch range, LEDs, cabling issues, factory resets, default settings. Hands on Building a network with multiple D-link switches. Configuration methods Managed vs. unmanaged switches, Console port access, telnet, web based access, SNMP, saving configurations, NVRAM, switch stacks. Hands on Accessing the switch using the CLI, IP address configuration, telnet. Command line interface Users, privileges, the CLI, online help. Hands on Basic commands, user accounts, displaying the switch configuration. Web based interface Getting started, basic format. Hands on Configuring the switch using the web interface. Port configuration Common port configuration tasks, link aggregation. Hands on Configuring ports. STP configuration What is STP? 802.1D vs. 802.1W (RSTP), configuring STP. Hands on Enabling and disabling STP, changing STP versions, configuring STP. VLAN configuration What are VLANS? 802.1Q, tagged/untagged, creating VLANS, applying VLANS. Hands on Setting up VLANS, setting up 802.1Q, Inter VLAN traffic. Housekeeping TFTP, upload download, updating firmware, updating configuration files, BOOTP/DHCP for IP addresses. Hands on Using TFTP to configure a D-Link switch. SNMP Switch configuration, D-View, other NMS's. Hands on Using SNMP to manage a D-link switch putting it all together: troubleshooting.

Internet of Things training course description A concise overview course covering The Internet of Things and the technologies involved. Particular emphasis is placed on the high level architecture of IoT and the benefits achievable. What will you learn Describe the structure of the IoT List the technologies involved in IoT. Explain how IoT works. Internet of Things training course details Who will benefit: Non-technical staff working with IoT. Prerequisites: None. Duration 1 day Internet of Things training course contents What is IoT The Internet, what is IoT? IoT and M2M, IoT technologies, IoT architecture. Wired and wireless communication. IoT applications; Smart houses, smart cities, smart cars, wearable, environment, other domain specific IoTs. IoT architecture Physical objects, virtual objects, cloud computing, data capture, communications. Big data. Components Hardware, sensors, actuators, chips, firmware, embedded systems. Open source platforms. Power options: Battery, solar, PoE. IoT communication RF, ZigBee, Bluetooth, Bluetooth LE, RFID, WiFi, 802.11ah, mobile technologies. Wired. Arduino (as an example) Microcontrollers, the platform, development, Arduino software, reading from sensors, I2C, SPI. Arduino and the Internet, HTTP, WiFi, GSM. The cloud and IoT: Pachube, nimbits, ThingSpeak Security in IoT Authentication, Encryption, secure booting, firewalls.

Real-World DevOps Project From Start to Finish
By Packt
Embark on a transformative DevOps journey! This comprehensive course equips you with skills in Ansible, Docker, GitLab, backups, and more. Master the art of self-hosting your infrastructure, streamlining deployments, and boosting efficiency. Launch your DevOps career today and unleash the endless possibilities!

Do you want to prepare for your dream job but strive hard to find the right courses? Then, stop worrying, for our strategically modified Computer Programming and Data Analysis and Management bundle will keep you up to date with the relevant knowledge and most recent matters of this emerging field. So, invest your money and effort in our 33 course mega bundle that will exceed your expectations within your budget. The Computer Programming and Data Analysis and Management related fields are thriving across the UK, and recruiters are hiring the most knowledgeable and proficient candidates. It's a demanding field with magnitudes of lucrative choices. If you need more guidance to specialise in this area and need help knowing where to start, then StudyHub proposes a preparatory bundle. This comprehensive Computer Programming and Data Analysis and Management bundle will help you build a solid foundation to become a proficient worker in the sector. This Computer Programming and Data Analysis and Management Bundle consists of the following 30 CPD Accredited Premium courses - Course 01: C++ Development: The Complete Coding Guide Course 02: Basic C# Coding Course 03: Computer Vision: C++ and OpenCV with GPU support Course 04: Python Basic Programming for Absolute Beginners Course 05: Python Programming for Everybody Course 06: Intermediate Python Coding Course 07: Quick Data Science Approach from Scratch Course 08: Root Cause Analysis Course 09: Google Data Studio: Data Analytics Course 10: Microsoft Excel: Automated Dashboard Using Advanced Formula, VBA, Power Query Course 11: Business Intelligence and Data Mining Masterclass Course 12: Level 2 Microsoft Office Essentials Course 13: SQL NoSQL Big Data and Hadoop Course 14: Introduction to Data Analysis Course 15: Data Science and Visualisation with Machine Learning Course 16: Data Analytics with Tableau Course 17: R Programming for Data Science Course 18: Complete Google Analytics Course Course 19: JavaScript Promises Course 20: JavaScript Foundations for Everyone Course 21: Javascript for Data Structures Course 22: jQuery Masterclass Course: JavaScript and AJAX Coding Bible Course 23: Microsoft SQL Server Development for Everyone Course 24: SQL Programming Masterclass Course 25: Level-3 Machine Learning Course with Python Course 26: Learn to Use Python for Spatial Analysis in ArcGIS Course 27: Microsoft Azure Machine Learning Course 28: Javascript Programming for Beginners Course 29: Basic Asynchronous JavaScript Course 30: JavaScript Functions 3 Extraordinary Career Oriented courses that will assist you in reimagining your thriving techniques- Course 01: Career Development Plan Fundamentals Course 02: CV Writing and Job Searching Course 03: Interview Skills: Ace the Interview Learning Outcome This tailor-made Computer Programming and Data Analysis and Management bundle will allow you to- Uncover your skills and aptitudes to break new ground in the related fields Deep dive into the fundamental knowledge Acquire some hard and soft skills in this area Gain some transferable skills to elevate your performance Maintain good report with your clients and staff Gain necessary office skills and be tech savvy utilising relevant software Keep records of your work and make a report Know the regulations around this area Reinforce your career with specific knowledge of this field Know your legal and ethical responsibility as a professional in the related field This Computer Programming and Data Analysis and Management Bundle resources were created with the help of industry experts, and all subject-related information is kept updated on a regular basis to avoid learners from falling behind on the latest developments. Certification After studying the complete training you will be able to take the assessment. After successfully passing the assessment you will be able to claim all courses pdf certificates and 1 hardcopy certificate for the Title Course completely free. Other Hard Copy certificates need to be ordered at an additional cost of •8. CPD 330 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Ambitious learners who want to strengthen their CV for their desired job should take advantage of the Computer Programming and Data Analysis and Management bundle! This bundle is also ideal for professionals looking for career advancement. Requirements To participate in this course, all you need is - A smart device A secure internet connection And a keen interest in Computer Programming and Data Analysis and Management Career path Upon completing this essential Bundle, you will discover a new world of endless possibilities. These courses will help you to get a cut above the rest and allow you to be more efficient in the relevant fields.

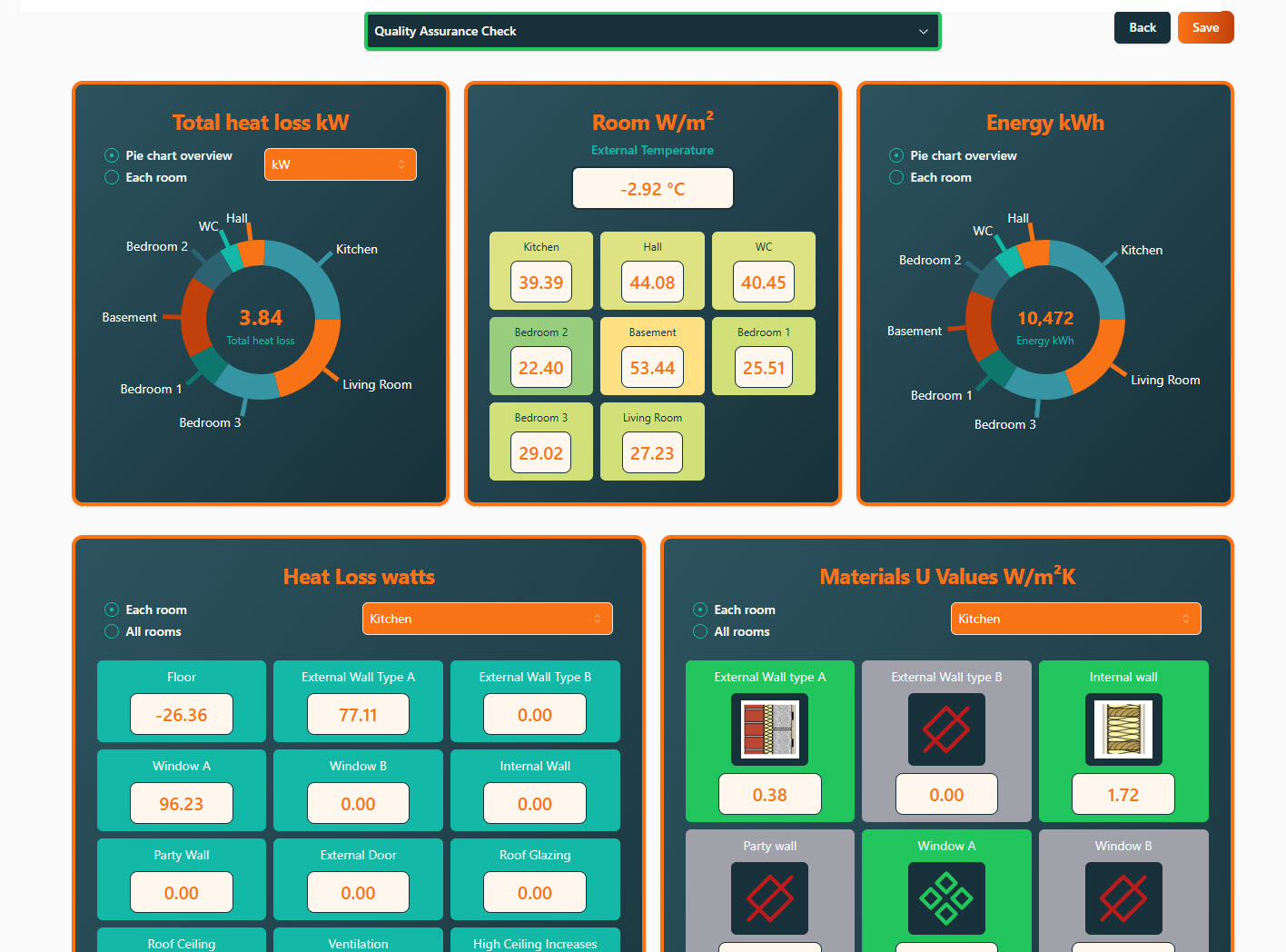
For new users and the curious. Hello, For new users and the curious. IMPORTANT: Firstly, once you are signed up, send us your requests on what you would like to see within the demonstration and learn on the course. We will then cater for your needs and answer them during the session. This is designed to be an introduction into how to start a room by room survey using the Heat Engineer app, then sending this survey to the online dashboard. We will then go through the different steps to complete this heat loss report. Optional pages will also be worked through and shown. Examples of how to select the flow temperature and the heat source (heat pumps and boilers) will be presented once the heat loss result is completed.