- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Build the Game of Life Using JavaScript
By Packt
In this course, we'll build a one-page app using HTML, CSS, and JavaScript called the Game of Life. This course is a great way to practice programming in JavaScript by creating an interactive and dynamic application right in your browser. For this course, you need basic knowledge of HTML, CSS, and JavaScript programming skills.

Jamf 400 Course
By Influential Training
Jamf 400, Jamf training course

Security+ training course description A hands on course aimed at getting delegates successfully through the CompTia Security+ examination. What will you learn Explain general security concepts. Describe the security concepts in communications. Describe how to secure an infrastructure. Recognise the role of cryptography. Describe operational/organisational security. Security+ training course details Who will benefit: Those wishing to pass the Security+ exam. Prerequisites: TCP/IP foundation for engineers Duration 5 days Security+ training course contents General security concepts Non-essential services and protocols. Access control: MAC, DAC, RBAC. Security attacks: DOS, DDOS, back doors, spoofing, man in the middle, replay, hijacking, weak keys, social engineering, mathematical, password guessing, brute force, dictionary, software exploitation. Authentication: Kerberos, CHAP, certificates, usernames/ passwords, tokens, biometrics. Malicious code: Viruses, trojan horses, logic bombs, worms. Auditing, logging, scanning. Communication security Remote access: 802.1x, VPNs, L2TP, PPTP, IPsec, RADIUS, TACACS, SSH. Email: S/MIME, PGP, spam, hoaxes. Internet: SSL, TLS, HTTPS, IM, packet sniffing, privacy, Javascript, ActiveX, buffer overflows, cookies, signed applets, CGI, SMTP relay. LDAP. sftp, anon ftp, file sharing, sniffing, 8.3 names. Wireless: WTLS, 802.11, 802.11x, WEP/WAP. Infrastructure security Firewalls, routers, switches, wireless, modems, RAS, PBX, VPN, IDS, networking monitoring, workstations, servers, mobile devices. Media security: Coax, UTP, STP, fibre. Removable media. Topologies: Security zones, DMZ, Intranet, Extranet, VLANs, NAT, Tunnelling. IDS: Active/ passive, network/host based, honey pots, incident response. Security baselines: Hardening OS/NOS, networks and applications. Cryptography basics Integrity, confidentiality, access control, authentication, non-repudiation. Standards and protocols. Hashing, symmetric, asymmetric. PKI: Certificates, policies, practice statements, revocation, trust models. Key management and certificate lifecycles. Storage: h/w, s/w, private key protection. Escrow, expiration, revocation, suspension, recovery, destruction, key usage. Operational/Organisation security Physical security: Access control, social engineering, environment. Disaster recovery: Backups, secure disaster recovery plans. Business continuity: Utilities, high availability, backups. Security policies: AU, due care, privacy, separation of duties, need to know, password management, SLAs, disposal, destruction, HR policies. Incident response policy. Privilege management: Users, groups, roles, single sign on, centralised/decentralised. Auditing. Forensics: Chain of custody, preserving and collecting evidence. Identifying risks: Assets, risks, threats, vulnerabilities. Role of education/training. Security documentation.

Modern Web Development with Blazor WebAssembly and .NET
By Packt
Writing modern web applications with a rich UI can be tedious. Blazor gives us .NET developers the chance to leverage our C# skills and build interactive web UIs. In this course, you will gain the ability to build web applications using Blazor. We will explore setting up your first Blazor application; how to work with an API; how data binding works; how to create components and integrate JavaScript components.
Python and Ruby Programming Bundle
By Packt
Python programming and Ruby coding are popular for a reason! Become a software coder, web developer, or hacker today

Shifting Left Until We Shift Right - Does It Make Sense to Test in Production?
By IIL Europe Ltd
Shifting Left Until We Shift Right - Does It Make Sense to Test in Production? Pablo Picasso famously said to learn the rules like a pro, so you can break them like an artist.' For over 20 years, the principles of agile and lean software development have been reshaping our industry with incontrovertible positive impact. However, as is so often the case with guiding principles, there are cases where the original intent has been lost and replaced by simplified patterns that sometimes prevent us from making the right decisions. In this talk, CircleCI CTO Rob Zuber will look at the guiding principles and original intent of agile practices to illustrate that the next frontier of testing in production may seem counterintuitive on the surface but, when done well, is a natural evolution of agile. Attendees will: Develop a better understanding of the principles that led to specific practices in agile development Recognize how advancement beyond planning work, such as devops and CI/CD evolved from these principles Make decisions about where and how to apply these practices in their own work Apply scenario planning to minimize cost and risk while maximizing value delivery in their own business

Modern designing techniques in the building and architectural fields include the usage of CAD (computer-aided design). Enrol in our CAD course to discover how to use computer-aided design fundamentals. To create blueprints and models, numerous industries use CAD software. It may be used to create exact measurements for 2D drawings and 3D models. Engineering, industrial design, architecture, and product design are just a few of the many sectors that regularly use CAD. Through this CAD training program, you will discover the fundamentals of Using CAD (computer-aided design), AutoCAD programming, shapes, and modelling. The curriculum will demonstrate the fundamentals of AutoCAD, T-Flex CAD, and freeCAD. Additionally, it will acquaint you with 2D and 3D forms, enhancing your viewpoint when constructing designs. The subjects of geometry and modelling, extrusion, rotation, grids, and regular polygons are all covered in this module. This Bundle Consists of the following Premium courses: Course 01: Level 5 CAD Designer Training Course 02: CAD Design Course: Assemblies, Modelling And Civil Drawings Course 03: Autocad Electrical Design Course 04: Solidworks Foundation Training Course 05: AutoCAD VBA Programming - Beginner course Course 06: AutoCAD to Excel - VBA Programming Hands-On! Course 07: Learn AutoCAD Programming using VB.NET - Hands-On! Course 08: AutoCAD Programming Using C#.NET Level 7 Course 09: Architectural Studies Course 10: Interior Design Professional Diploma Course 11:Decision Making and Critical Thinking The curriculum of CAD Training Bundle Course 01: Level 5 CAD Designer Training CAD Module 01: Introduction CAD Module 02: CAD Designer Career in the United Kingdom CAD Module 03: Basics for CAD Design - Part 1 CAD Module 04: Basics for CAD Design - Part 2 CAD Module 05: 2D Shape Using CAD CAD Module 06: 3D Shape Using CAD CAD Module 07: Geometry and Modelling CAD Module 08: Assemblies in Design CAD Module 09: Extrusion and Rotations CAD Module 10: Blending Operations CAD Module 11: Grids and Regular Polygons CAD Module 12: Parameters in Civil Drawings CAD Module 13: Introduction to AutoCAD CAD Module 14: Introduction to T-Flex CAD CAD Module 15: Introduction to SolidWorks CAD Module 16: Introduction to FreeCAD CPD 120 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this bundle. Requirements This course has been designed to be fully compatible with tablets and smartphones. Career path Successful completion of this CAD course paves the way for a series of exciting and thriving job opportunities, such as - CAD Designer Compounder Coater Technician The average salary for these positions in the UK is £25k - £45k annually. Certificates Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Level 5 CAD Designer Training) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost. Certificate of completion Digital certificate - Included

Build a Stock Market Web App with Node and JavaScript
By Packt
We'll build a cool Stock Market Portfolio app that lets you search stock ticker symbols by connecting to a third-party API to collect stock market information about your stocks!

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

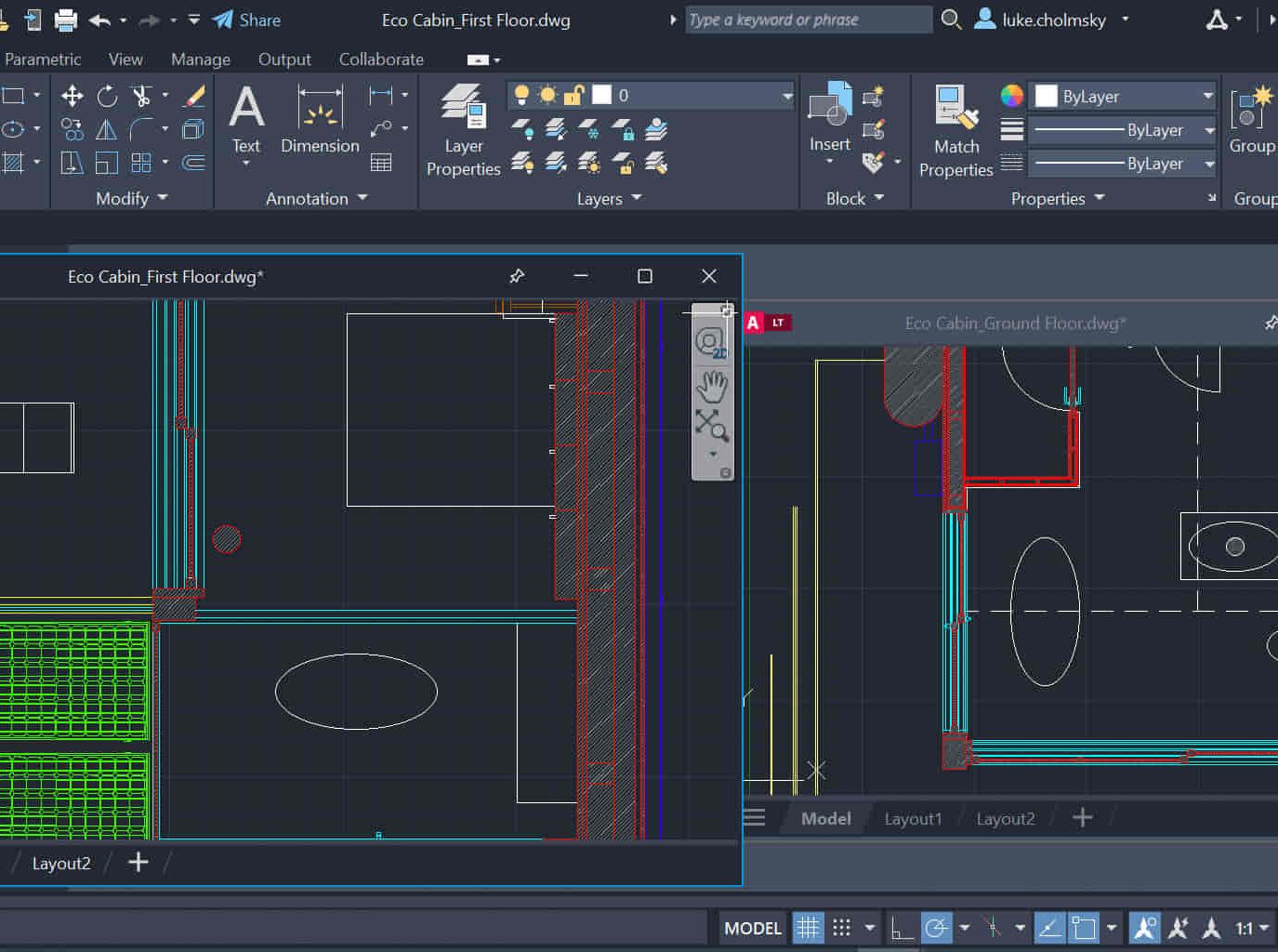
AutoCAD Night Training Course
By ATL Autocad Training London
Why AutoCAD Night Training Course? This Autodesk AutoCAD 2D Evening Course, 10 hours, is perfect for beginners aiming to create 2D plans, elevations, sections. It covers all tools in AutoCAD 2D, making it valuable for both newcomers and those aspiring to enhance their skills. Click here for more info: Website When: Personalized 1-on-1 sessions. Available from Mon to Sat 9 am to 7 pm. Book over the phone, call 02077202581 Duration: 10 hours (Split 10 hrs over as many as days you want) Method: In-person or live online training Course Content: Foundational Shape Construction Manipulating Lines, Arcs, and Polylines Optimizing Object Alignment with Grip Tools Data Management and Backup Protocols File Format Exploration and Understanding Disaster Recovery Strategies Advanced Object Creation Techniques Precision Measurement Unit Handling Dynamic Input Methods Utilizing Inquiry Commands and Measurement Tools Effective Object Visualization and Navigation Zoom, Pan, and Object Manipulation Swift Object Management Strategies Object Transformation and Alteration Techniques Functions for Trimming, Extending, and Offsetting Objects Creating Various Geometric Shapes Object Editing, Joining, and Filleting Stretching and Organizing Objects Layer Management and Customization Configuring Object Properties and Linetypes Designing Layouts and Efficient Page Configurations Scaling Drawing Views and Adding Annotations Text Creation, Styling, and Editing Dimensioning Principles and Customization Implementing Multileaders for Annotations Object Hatching and Editing Techniques Managing Reusable Content: Blocks and Symbols Utilizing Tool Palettes and Working with Groups Understanding Model Space and Paper Space Creating Layouts and Viewports Scaling Viewports and Plotting/PDF Output Managing Multiple Sheet Drawings Optimizing Plotstyles for Printing Creating Custom Drawing Templates To download AutoCAD, visit Autodesk's official website. Advantages: AutoCAD stands as the industry-leading computer-aided design (CAD) software, widely adopted for creating architectural, engineering, and construction drawings. Acquire essential skills applicable across a diverse spectrum of industries. Assessment: Evaluation will occur informally during classes, which comprehensively cover specific topics, complemented by practical drawing exercises to reinforce skills and knowledge. Additionally, we offer longer, independent drawing tasks that encompass multiple acquired skills, evaluated against professional benchmarks. Requirements: Prospective participants should possess basic computer literacy and engagement in professions where CAD is utilized. English Proficiency: Applicants are expected to demonstrate proficiency in both written and spoken English. Why Opt for This Course? Our AutoCAD course is your gateway to mastering the essential skills for creating top-notch technical drawings. Designed with beginners in mind, this course is perfect for individuals who have little to no prior experience with AutoCAD. If your work or studies involve CAD drawings, gaining a solid grasp of the program is crucial for confidence and proficiency. Upon enrollment, students gain access to a free 30 days trial. While classes are conducted using AutoCAD on PC, it's worth noting that the course is compatible with AutoCAD on Mac, albeit with slight interface variations. Who Should Attend? This course caters to those eager to acquire the skills necessary for creating and interpreting drawings produced in AutoCAD. Our diverse system hails from various industries, including engineering, architecture, landscape architecture, construction, electronics, and product design. Why Opt for CAD Training? Practical Learning Experience: Immerse yourself in hands-on training. Personalized One-to-One AutoCAD Classes: Benefit from individualized attention. Expert and Knowledgeable Instructors: Learn from skilled and experienced teachers. Online Training Recordings: Access recorded AutoCAD training sessions online. Best Price Guarantee: Enjoy competitive pricing with a satisfaction guarantee. Pre and Post-Training Support: Receive lifetime free support before and after completing your training. Flexible Schedule: Choose your class timings and dates-weekdays, weekends, or evenings. Tailored Course Content: Customize the AutoCAD course to align with your specific needs. Access Anywhere: Access AutoCAD training and support from any location.