- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1415 Software courses in Liverpool delivered Live Online
Data Analytics
By NextGen Learning
Course Overview This comprehensive Data Analytics course provides an in-depth exploration of data analysis, covering the essential principles and techniques used to extract valuable insights from data. Learners will engage with core concepts, such as data mining, statistical analysis, and visualisation, enabling them to make informed decisions and drive business outcomes. By the end of the course, participants will have the skills to analyse and interpret data, apply analytical tools effectively, and present their findings clearly. This course equips learners with the necessary tools to understand and leverage data in various professional settings, adding significant value to their career prospects. Course Description The Data Analytics course covers a wide range of topics, including the fundamentals of data analysis, statistical methods, and various data visualisation techniques. Learners will explore essential tools such as Excel and specialised software, while gaining a deep understanding of how to collect, store, and process data effectively. Emphasis is placed on developing the analytical mindset required to interpret data accurately and draw actionable insights. This course is designed to ensure learners can confidently navigate the world of data analytics and apply their knowledge in diverse industries, enhancing their problem-solving and decision-making abilities. Course Modules Module 01: Introduction to the World of Data Module 02: Basics of Data Analytics Module 03: Statistics for Data Analytics Module 04: Actions Taken in the Data Analysis Process Module 05: Gathering the Right Information Module 06: Storing Data Module 07: Data Mining Module 08: Excel for Data Analytics Module 09: Tools for Data Analytics Module 10: Data-Analytic Thinking Module 11: Data Visualisation That Clearly Describes Insights Module 12: Data Visualisation Tools (See full curriculum) Who is this course for? Individuals seeking to enhance their analytical skills for data-driven decision-making. Professionals aiming to transition into data analytics or enhance their data-related roles. Beginners with an interest in understanding data and its applications across industries. Business professionals seeking to leverage data for strategic growth. Career Path Data Analyst Business Intelligence Analyst Data Scientist Market Research Analyst Operations Analyst Financial Analyst Business Analyst Data Visualisation Specialist

VMware NSX Advanced Load Balancer: Install, Configure, Manage [V20.x]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Experienced system administrators and network administrators Overview By the end of the course, you should be able to meet the following objectives: Describe the NSX Advanced Load Balancer architecture Describe the NSX Advanced Load Balancer components and main functions Explain the NSX Advanced Load Balancer key features and benefits Deploy and configure the NSX Advanced Load Balancer infrastructure within private or public clouds using Write and No Access Cloud Connectors Explain, deploy, and configure Service Engines Explain and configure local load balancing constructors such as virtual services, pools, health monitors, and related components Understand and modify application behavior through profiles, policies, and DataScripts Configure advanced services such as global server load balancing Describe how to use NSX Advanced Load Balancer REST API interfaces and related automation capabilities Describe and configure NSX Advanced Load Balancer application and infrastructure monitoring Gather relevant information and perform basic troubleshooting of applications that use built-in NSX Advanced Load Balancer tooling This five-day, fast-paced course provides comprehensive training to install, configure, and manage a VMware NSX© Advanced Load Balancer? (Avi Networks) solution. This course covers key NSX Advanced Load Balancer (Avi Networks) features and functionality offered in the NSX Advanced Load Balancer 20.x release. Features include the overall infrastructure, virtual services and application components, global server load balancing, various cloud connectors, application troubleshooting, and solution monitoring. Hands-on labs provide access to a software-defined data center environment to reinforce the skills and concepts presented in the course. Course Introduction Introduction and course logistics Course objectives Introduction to NSX Advanced Load Balancer Introduce NSX Advanced Load Balancer Discuss NSX Advanced Load Balancer use cases and benefits Explain NSX Advanced Load Balancer architecture and components Explain the management, control, data, and consumption planes and their respective functions Virtual Services Configuration Concepts Explain Virtual Service components Explain Virtual Service types Explain and configure basic Virtual Service components such as Application Profiles, Network Profiles Profiles and Policies Explain and deep dive on Advanced Virtual Service creation Explain and deep dive on Application Profiles and Types such as L4, DNS, Syslog, and HTTP Explain and configure advanced application HTTP Profile options Deep dive on Network Profiles and Types Explain and configure SSL Profiles and Certificates Explain and Configure HTTP and DNS policies Pools Configuration Concepts Explain and deep dive on Pools configuration options Describe available Load Balancing algorithms Explain multiple Health Monitor types Explain multiple Persistence Profiles Explain and configure Pool Groups Modifying Application Behavior Design and apply application solutions leveraging application profiles Design and apply application solutions leveraging Network and HTTP Policies and DataScripts Explain DataScript fundamentals Explain and leverage NSX Advanced Load Balancer analytics to understand application behavior Describe and configure Client SSL Certificate Validation Describe and configure Virtual Service DDoS, Rate Limiting, and Throttling capabilities Modify Network Profiles properties such as TCP connection properties Design and apply application solutions leveraging Persistence Profiles NSX Advanced Load Balancer Infrastructure Architecture Deep dive on the management, control, data, and consumption planes and functions Describe Control Plane Clustering and High Availability Describe Controller Process Sharding Describe Controller Sizing Describe Service Engine CPU and NIC Architecture Explain Tenants Deep dive and configure properties of Service Engine Groups Explain Service Engine Group High Availability Modes Describe and configure Active/Standby High Availability Mode Describe and configure Elastic HA High Availability Mode (Active/Active, N+M) Explain Service Engine Failure Detection and Self-Healing Describe Service Engine as a Router Deep dive on Virtual Service scale out options, such as Layer 2 (Native), Layer 3 (BGP), and DNS-based Introduction to Cloud Connector Introduce Cloud Connectors Review Cloud Connector integration modes Introduce Cloud Connector types Install, Configure and Manage NSX Advanced Load Balancer in No-Access Cloud Explain No Access Cloud concepts Configure No Access Cloud integration Explain and Configure Linux Server Cloud Describe the Advanced Configuration options available in Bare-Metal (Linux Server Cloud) Install, Configure and Manage NSX Advanced Load Balancer in VMware Environment: Cloud Configuration Introduce VMware integration options Explain and configure VMware No Access Cloud Connector Explain and configure VMware Write Access Cloud Connector Describe VMware Write with NSX-V Access Cloud Connector Describe VMware NSX-T integration AWS Cloud Configuration Describe NSX Advanced Load Balancer Public Cloud integrations Explain and demonstrate AWS Public Cloud Integration DNS Foundations Review, discuss, and explain DNS fundamentals Describe NSX Advanced Load Balancer DNS and IPAM providers Global Server Load Balancing Introduce Global Server Load Balancing Concepts and Benefits Explain and configure NSX Advanced Load Balancer infrastructure Explain and configure DNS Virtual Service components Explain and configure GSLB Service Engine Group Describe and configure GSLB Sites Explain and configure basic GSLB Services to include pools and health monitors Describe GSLB Service Load Balancing algorithms Explain and configure Data and Control Plane-based Health Monitors Describe GSLB Health Monitor Proxy NSX Advanced Load Balancer: Troubleshooting Introduce Infrastructure and Application Troubleshooting Concepts Describe Control Plane and Data Plane-based Troubleshooting Explain Application Analytics and Logs Describe client logs analysis Explain Headers troubleshooting and Packet Capture mechanism Leverage CLI for detailed data plane troubleshooting Explain Service Engine Logs Explain Health Monitors troubleshooting Explain BGP session troubleshooting Describe Control Plane Troubleshooting, Clustering, and Cloud Connector issues Events and Alerts Describe NSX Advanced Load Balancer Events Describe and configure NSX Advanced Load Balancer Alerts Describe NSX Advanced Load Balancer monitoring capabilities, leveraging SNMP, Syslog, and Email Introduction to NSX Advanced Load Balancer Rest API Introduce NSX Advanced Load Balancer REST API interface Describe REST API Object Schema Explain and interact with REST API interface, leveraging browser and command line utility Explain Swagger-based API documentation Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware NSX Advanced Load Balancer: Install, Configure, Manage [V20.x] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware NSX Advanced Load Balancer: Install, Configure, Manage [V20.x] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware NSX Advanced Load Balancer: Install, Configure, Manage [V20.x]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
VMware vSAN: Install, Configure, Manage [V7]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Storage and virtual infrastructure consultants, solution architects, and administrators who are responsible for production support and administration of VMware vSAN. Overview By the end of the course, you should be able to meet the following objectives: Describe vSAN concepts Detail the underlying vSAN architecture and components Explain the key features and use cases for vSAN Identify requirements and planning considerations for vSAN clusters Explain the importance vSAN node hardware compatibility Describe the use of VMware vSphere Lifecycle Manager⢠to automate driver and firmware installations Describe the different vSAN deployment options Explain how to configure vSAN fault domains Detail how to define and create a VM storage policy Discuss the impact of vSAN storage policy changes Detail vSAN resilience and data availability Describe vSAN storage space efficiency Explain how vSAN encryption works Identify requirements to configure the vSAN iSCSI target Detail VMware HCI Mesh⢠technology and architecture Detail vSAN File Service architecture and configuration Explain the use cases of vSAN Direct Configuration⢠Describe how to setup a stretched and a two-node vSAN cluster Discuss vSAN cluster backup methodology Describe vSAN maintenance mode and data evacuation options Define the steps to shut down a vSAN cluster for maintenance Explain how to use proactive tests to check the integrity of a vSAN cluster Use VMware Skyline Health⢠for monitoring vSAN health During this five-day course, you will gain the knowledge, skills, and tools to plan and deploy a VMware vSAN? cluster. You will learn about managing and operating vSAN. This course focuses on building the required skills for common Day-2 vSAN administrator tasks such as vSAN node management, cluster maintenance, security operations, and advanced vSAN cluster operations. You will learn these skills through the completion of instructor-led activities and hands-on lab exercises. Course Introduction Introductions and course logistics Course objectives Introduction to vSAN Describe vSAN architecture Describe the vSAN software components: CLOM, DOM, LSOM, CMMDS, and RDT Identify vSAN objects and components Describe the advantages of object-based storage Describe the difference between All-Flash and Hybrid vSAN architecture Explain the key features and use cases for vSAN Discuss the vSAN integration and compatibility with other VMware technologies Planning a vSAN Cluster Identify requirements and planning considerations for vSAN clusters Apply vSAN cluster planning and deployment best practices Determine and plan for storage consumption by data growth and failure tolerance Design vSAN hosts for operational needs Identify vSAN networking features and requirements Describe ways of controlling traffic in a vSAN environment Recognize best practices for vSAN network configurations Deploying a vSAN Cluster Recognize the importance of hardware compatibility Ensure the compatibility of driver and firmware versioning Use tools to automate driver validation and installation Apply host hardware settings for optimum performance Use vSphere Lifecycle Manager to perform upgrades Deploy and configure a vSAN Cluster using the Cluster QuickStart wizard Manually configure a vSAN Cluster using VMware vSphere© Client? Explain and configure vSAN fault domains Using VMware vSphere© High Availability with vSAN Understand vSAN Cluster maintenance capabilities Describe the difference between implicit and explicit fault domains Create explicit fault domains vSAN Storage Policies Describe a vSAN object Describe how objects are split into components Explain the purpose of witness components Explain how vSAN stores large objects View object and component placement on the vSAN datastore Explain how storage policies work with vSAN Define and create a virtual machine storage policy Apply and modify virtual machine storage policies Change virtual machine storage policies dynamically Identify virtual machine storage policy compliance status vSAN Resilience and Data Availability Describe and configure the Object Repair Timer advanced option Plan disk replacement in a vSAN cluster Plan maintenance tasks to avoid vSAN object failures Recognize the importance of managing snapshot utilization in a vSAN cluster Configuring vSAN Storage Space Efficiency Discuss deduplication and compression techniques Understand deduplication and compression overhead Discuss compression only mode Configure erasure coding Configure swap object thin provisioning Discuss reclaiming storage space with SCSI UNMAP Configure TRIM/UNMAP vSAN Security Operations Identify differences between VM encryption and vSAN encryption Perform ongoing operations to maintain data security Describe the workflow of data-in transit encryption Identify the steps involved in replacing Key Management Server Introduction to Advanced vSAN Configurations Identify requirements to configure vSAN iSCSI target Detail VMware HCI Mesh technology and architecture Detail vSAN File Service architecture and configuration Explain the use cases of vSAN Direct Configuration vSAN Cluster Maintenance Perform typical vSAN maintenance operations Describe vSAN maintenance modes and data evacuation options Assess the impact on cluster objects of entering maintenance mode Determine the specific data actions required after exiting maintenance mode Define the steps to shut down and reboot hosts and vSAN clusters Use best practices for boot devices Replace vSAN nodes vSAN Stretched and Two Node Clusters Describe the architecture and uses case for stretched clusters Detail the deployment and replacement of a vSAN witness node Describe the architecture and uses case for two-node clusters Explain the benefits of vSphere HA and vSphere Site Recovery Manager in a vSAN stretched cluster Explain storage policies for vSAN stretched cluster vSAN Cluster Monitoring Describe how the Customer Experience Improvement Program (CEIP) enables VMware to improve products and services Use VMware Skyline Health for monitoring vSAN cluster health Manage alerts, alarms, and notifications related to vSAN in VMware vSphere© Client? Create and configure custom alarms to trigger vSAN health issues Use IOInsight metrics for monitoring vSAN performance Analyse vsantop performance metrics Use a vSAN proactive test to detect and diagnose cluster issues Additional course details:Notes Delivery by TDSynex, Exit Certified and New Horizons an VMware Authorised Training Centre (VATC) Nexus Humans VMware vSAN: Install, Configure, Manage [V7] training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the VMware vSAN: Install, Configure, Manage [V7] course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
![VMware vSAN: Install, Configure, Manage [V7]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Microsoft Office 2016 Complete Course
By NextGen Learning
Microsoft Office 2016 Complete Course Course Overview: The "Microsoft Office 2016 Complete Course" is designed to provide learners with comprehensive knowledge and essential skills in the core Microsoft Office applications. This course offers in-depth coverage of Microsoft Word, Excel, PowerPoint, Outlook, and Access, enabling participants to confidently use these programs in professional environments. By the end of the course, learners will be equipped to create, manage, and analyse documents, spreadsheets, presentations, emails, and databases with proficiency. This course is an invaluable resource for those looking to enhance their productivity and improve their digital skills, making them more competitive in the job market. Course Description: The "Microsoft Office 2016 Complete Course" delves into the key functionalities of Microsoft Office, with modules dedicated to each major application. Learners will explore the features of Word for document creation and editing, Excel for data analysis and management, PowerPoint for effective presentations, Outlook for email and calendar management, and Access for database handling. Each module is structured to help learners understand the software’s core functions and how to apply them in real-world scenarios. Upon completion, learners will have developed a strong foundation in using Office 2016, boosting their ability to operate efficiently and effectively in modern workplaces. This course is suitable for individuals seeking to increase their office productivity and streamline their daily tasks. Microsoft Office 2016 Complete Course Curriculum: Module 01: Microsoft Word 2016 Module 02: Microsoft Excel 2016 Module 03: Microsoft PowerPoint 2016 Module 04: Microsoft Outlook 2016 Module 05: Microsoft Access 2016 (See full curriculum) Who is this course for? Individuals seeking to improve their office productivity skills. Professionals aiming to advance in roles requiring Microsoft Office proficiency. Beginners with an interest in data management, communication, and office software. Those wishing to enhance their CV and increase career opportunities in administrative and support roles. Career Path: Office Administrator Executive Assistant Data Analyst Personal Assistant Administrative Support Specialist Project Coordinator

Adobe Premiere Pro CC
By NextGen Learning
Course Overview The Adobe Premiere Pro CC course is designed to provide learners with a comprehensive understanding of the software's advanced features, enabling them to create and edit professional-quality videos. Through this course, students will gain the essential skills to work efficiently with various multimedia elements, enhance their video editing techniques, and explore key tools such as colour correction, sound editing, and effects application. This course offers practical insights into working with Adobe Premiere Pro, equipping learners to create high-impact, visually appealing content. Upon completion, students will be proficient in all key aspects of video editing, ready to apply their skills in various industries such as film production, marketing, and online media. Course Description This Adobe Premiere Pro CC course takes an in-depth approach to mastering the video editing software. Learners will explore a range of topics, from setting up the workspace and understanding the interface to advanced techniques such as multi-camera editing, transitions, and colour grading. The course also covers sound editing, the use of effects, and tips for efficient workflows. Students will develop proficiency in editing both short and long-form content, ensuring that they are capable of handling a variety of editing tasks. With a focus on developing professional skills, learners will gain the confidence to use Adobe Premiere Pro CC for a wide array of video production needs. By the end of the course, learners will be well-equipped to produce polished video content for different platforms, making them highly marketable in the creative and media industries. Course Modules Module 01: Introduction to Adobe Premiere Pro CC Module 02: Setting up the Workspace and Interface Module 03: Importing and Organising Media Module 04: Basic Editing Tools and Techniques Module 05: Working with Audio Module 06: Transitions and Effects Module 07: Colour Correction and Grading Module 08: Advanced Video Editing Techniques Module 09: Multi-Camera Editing Module 10: Exporting and Rendering Video Projects Module 11: Working with Titles and Graphics Module 12: Final Project and Portfolio Development (See full curriculum) Who is this course for? Individuals seeking to enhance their video editing skills. Professionals aiming to develop expertise in video production. Beginners with an interest in video editing and media production. Creative individuals interested in improving their technical video editing abilities. Career Path Video Editor Content Creator Multimedia Specialist Film Production Assistant Digital Media Producer Marketing Video Editor Post-production Specialist

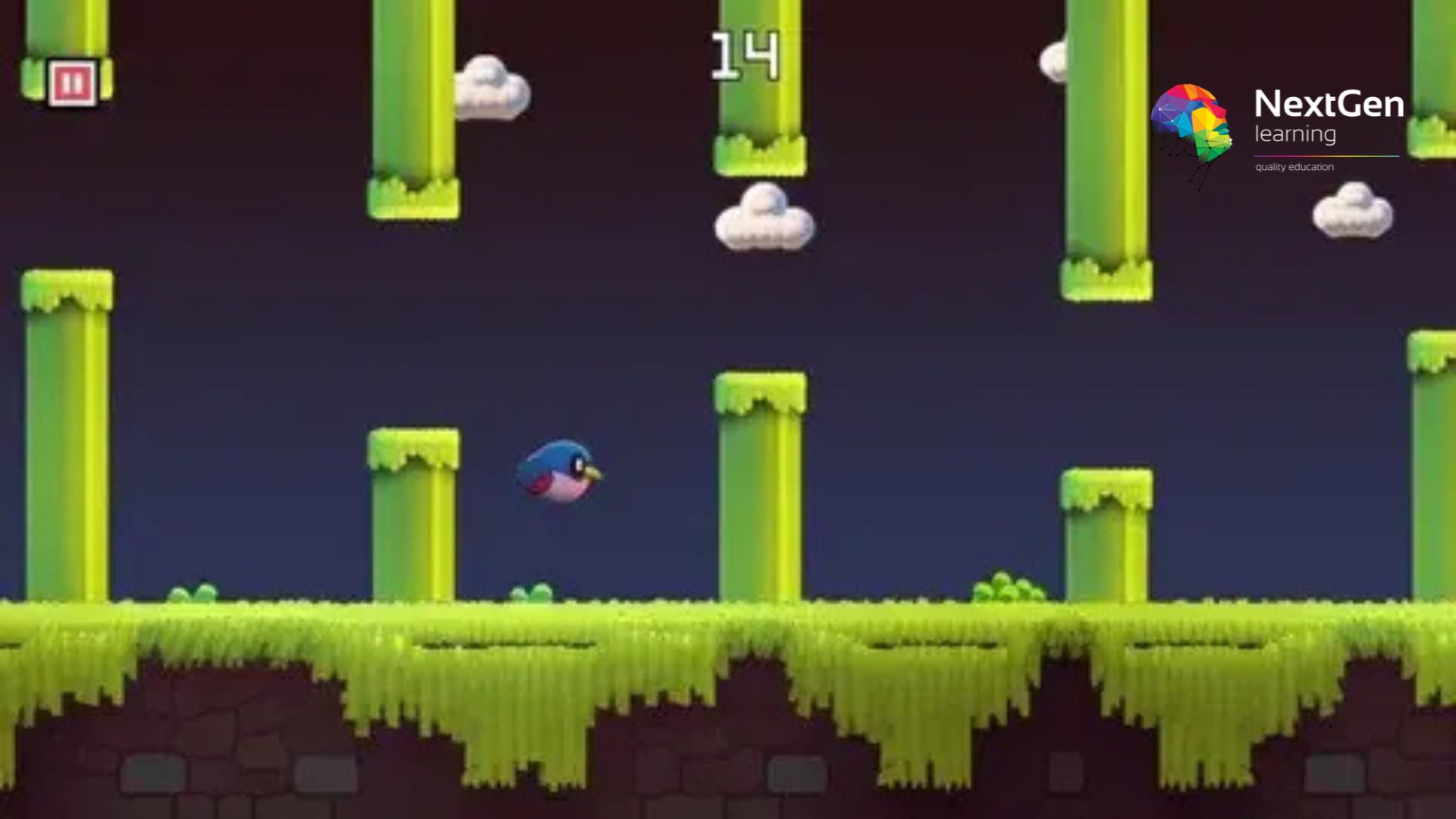
Flappy Bird Clone: Cocos2d-x C++ Game
By NextGen Learning
Flappy Bird Clone: Cocos2d-x C++ Game Course Overview: This course provides a comprehensive introduction to game development using Cocos2d-x and C++. Learners will create a fully functional Flappy Bird clone, mastering the fundamentals of game mechanics, user interface design, and game physics. The course covers essential topics in object-oriented programming, handling user input, collision detection, and scene management. By the end, learners will have the knowledge to design and develop their own 2D games, making this course an excellent starting point for anyone interested in game development. The practical value lies in learning how to implement complex game features, which can be used in future projects or professional roles. Course Description: In this course, learners will dive into the process of developing a 2D game using C++ and Cocos2d-x. Starting with the basics of game creation, the course introduces essential programming concepts including classes, object handling, and event-driven programming. Key topics include building the game environment, implementing gravity and jump mechanics, handling user inputs, and managing game scenes. Learners will also focus on game physics such as collision detection and the continuous movement of the game elements. The course encourages learners to break down complex game features into manageable components while using a leading game engine. By the end of the course, participants will be equipped with a strong foundation in game programming and the skills needed to create their own games. Flappy Bird Clone: Cocos2d-x C++ Game Curriculum: Module 01: Introduction to Cocos2d-x and C++ (See full curriculum) Who is this course for? Individuals seeking to start a career in game development Professionals aiming to enhance their programming and game design skills Beginners with an interest in learning game development Aspiring developers looking to create their own 2D games Career Path Junior Game Developer Game Programmer Game Designer Mobile Game Developer Software Developer in the gaming industry
Renewable Energy: Solar
By NextGen Learning
Course Overview: This course provides a comprehensive introduction to the field of renewable energy, focusing on solar energy systems. Learners will explore the fundamentals of solar power, including system components, design, and application. With a practical approach, the course offers insights into both off-grid and on-grid systems, solar water pumping, and system protection. The course equips learners with essential skills for designing and optimising photovoltaic (PV) systems using industry-standard software like PVSyst, MATLAB, and ETAP. Upon completion, participants will be able to contribute to renewable energy projects, enhance their career prospects in the solar energy sector, and implement solar systems with a deeper understanding of the technological and environmental impacts. Course Description: This course delves into the key aspects of solar energy systems, offering a clear overview of essential topics such as solar panel components, battery storage, system design, and optimisation. Learners will gain in-depth knowledge of off-grid and on-grid solar energy systems, solar water pumping, and system protection. The course incorporates theoretical knowledge and system design techniques using industry-standard tools, including PVSyst, MATLAB, and ETAP. Additionally, students will learn how to design and simulate PV systems, as well as the design of system diagrams using Excel. By the end of this course, learners will have acquired the skills to confidently design and optimise solar energy systems for a range of applications, contributing to the growing renewable energy sector and ensuring sustainable energy solutions. Course Modules: Module 01: Basics of Solar Energy System Module 02: Batteries in PV System Module 03: Components and Design of Off Grid Solar Energy System Module 04: Designing of ON Grid Solar Energy System Module 05: Design of PV System Using PVSyst Programme Module 06: Solar Water Pumping System Module 07: Protection of PV System Module 08: Design Using Excel Sheet Module 09: Single Line Diagram of PV System Module 10: MATLAB and ETAP PV Simulation (See full curriculum) Who is this course for? Individuals seeking to enter the renewable energy sector. Professionals aiming to develop expertise in solar energy system design. Beginners with an interest in sustainable energy solutions. Engineers or technicians looking to broaden their knowledge of solar energy applications. Career Path Solar Energy System Designer Renewable Energy Consultant Solar Power Technician Project Manager in Renewable Energy Energy Analyst Sustainability Specialist

Computer Maintenance, PAT & Cyber Security
By NextGen Learning
Course Overview The Computer Maintenance, PAT & Cyber Security course offers a comprehensive introduction to the essential components of modern IT systems, combining core knowledge in hardware setup, system troubleshooting, and security protocols. Designed to build foundational understanding as well as introduce advanced cybersecurity concepts, this course equips learners with the confidence to navigate today’s digital infrastructure. From building a computer to understanding network vulnerabilities, learners will explore a variety of modules that address both traditional and emerging technologies, including IoT and encryption. By the end of the course, students will have developed the skills to identify risks, support device performance, and understand secure systems architecture—essential for any role in technology-focused sectors. Course Description This course blends key topics across computer hardware maintenance, PAT (Portable Appliance Testing), and cyber security to prepare learners for a well-rounded understanding of IT system management. The curriculum begins with assembling and configuring computers, progressing into network security and advanced Windows troubleshooting. Learners are introduced to essential software tools and coding applications like C++ with OpenCV, and gain insights into the Internet of Things and encryption principles. Additionally, the course includes training in cyber security awareness, addressing the latest threats and preventative frameworks. With clear instructional guidance and structured content delivery, the course is suitable for learners aiming to understand technical environments and the protocols behind secure computing. It is ideal for those seeking career progression or looking to explore new opportunities in IT security, maintenance, or systems analysis. Course Modules: Module 01: Building Your Own Computer Module 02: Computer Networks Security from Scratch to Advanced Module 03: Computer Vision By Using C++ and OpenCV with GPU support Module 04: Advance Windows 10 Troubleshooting for IT HelpDesk Module 05: Portable Appliance Testing (PAT) Module 06: Internet of Things Module 07: Cyber Security Awareness Training Module 08: Encryption (See full curriculum) Who is this course for? Individuals seeking to understand IT maintenance and cybersecurity principles. Professionals aiming to broaden their knowledge of system configuration and data protection. Beginners with an interest in computer technology and digital safety. Employers looking to upskill their IT or facilities staff in security and device compliance. Career Path IT Support Specialist Systems Administrator Network Security Analyst Cyber Security Consultant Electrical Safety Compliance Officer Technical Services Coordinator

Xero Training Session (1 Hour)
By Back Office Software Support Ltd T/A Boss
Remote training session for Xero Accounting and Payroll software.

FreeAgent Training Session (1 Hour)
By Back Office Software Support Ltd T/A Boss
Remote training session for FreeAgent Accounting and Payroll software.
