- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Content Marketing Level 2
By Course Cloud
Content Marketing Level 2 Course Overview Take your digital content strategy to the next level with our Content Marketing Level 2 course — a hands-on, instructor-led training designed for learners who want to deepen their understanding of content creation, video production, SEO, email marketing, and social media management. Whether you're a budding marketer, small business owner, or creative professional, this course equips you with the practical tools and techniques needed to build authority, attract an audience, and drive conversions. From optimising blog articles for SEO to scheduling your posts using HootSuite, this course covers it all with real-time examples and actionable strategies. Learn at your own pace, develop career-ready skills, and earn a CPD-accredited certificate to showcase your growth in the competitive digital marketing space. Extra Included: Lifetime Access Free Student ID Card Learning Outcome Understand the step-by-step process of planning and outlining high-quality content Learn tools and best practices for recording professional video and audio Discover cost-effective ways to create a high-quality content background Master email marketing strategies like Soap Opera and Seinfeld sequences Optimise articles for SEO using readability tools and real-time analysis Explore content syndication through social platforms with HootSuite Get hands-on experience managing and automating your social media posts Learn how to outsource content tasks efficiently through Fiverr Why Choose This Course This course offers a well-rounded and practical learning experience in content marketing, delivered by industry professionals. Whether you're working solo or part of a team, the flexible, online structure of this course ensures you can study anywhere, anytime. With expert-led tutorials and real-world tools, you’ll build the confidence to plan, create, optimise, and distribute content that truly connects with your audience. Who is this Content Marketing Level 2 Course for? This course is ideal for digital marketers, content creators, small business owners, and aspiring freelancers looking to enhance their online presence. It’s also perfect for professionals who want to expand their content marketing skills to include SEO, email strategies, and social media automation — all within one streamlined course. Entry Requirements There are no formal entry requirements for this course. Anyone with an interest in content marketing can enrol. Accredited Certification After successfully completing the course, you can get a UK and internationally accepted certificate to share your achievement with potential employers or include it in your CV. For the PDF certificate, you’ll need to pay £9.99. You can get the hard copy for 15.99, which will reach your doorstep by post.

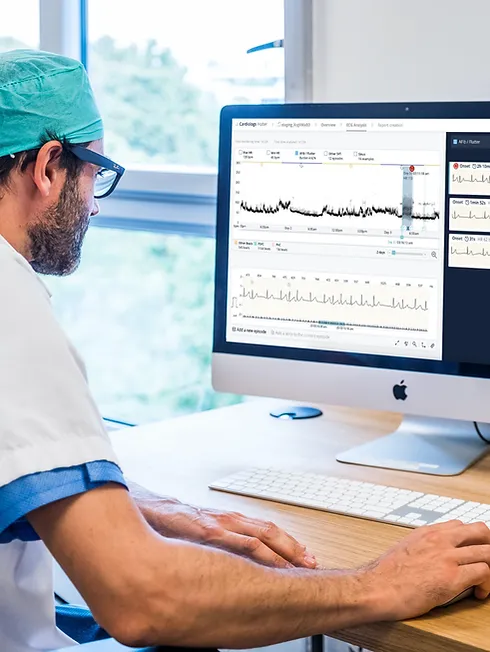
Learn how to perform and read an ECG ... Nationally Recognised Qualification OCN Accredited - Level 3 (advanced level) CPD Accredited - The CPD Certification Service Introduces you to the fundamentals of setting up and operating an ECG machine Includes patient preparation Produce a valid (error free) ECG Learn and understand ECG traces Recognise recordings that require urgent attention Basic understanding of English language required OPEN TO ALL APPLICANTS VIRTUAL CLASSROOM OPTION INCLUDES COMPREHENSIVE PRACTISE@HOME ECG TRAINING KIT Final interpretation of all ECG recordings is the responsibility of a medical professional.
SOLD OUT! 26th September Maddy Belton #Agent121. Looking for: MG, YA, CHILDREN'S NON-FICTION, ADULT FICTION
5.0(3)By I Am In Print
LOOKING FOR: MG, YA AND ADULT SCI-FI / FANTASY, CHILDREN'S NON-FICTION After graduating from St Andrews University with a degree in English Literature and Art History, Maddy followed her love of literature to an internship at non-fiction literary agency Graham Maw Christie. At GMC, Maddy worked her way up to Agent and built a list of authors who wrote for both for adults and children, spanning history, tarot, and nature writing. An avid reader of anything magical, Maddy joined Madeleine Milburn in 2022 to build a list specialising in SFF. Maddy would like to see SFF across all genres for all ages, including: grim dark, thriller, historical, romance, cosy fantasy, sci-fi, epic, YA fantasy, dark academia, contemporary fantasy, fantasy middle-grade, mythology, fairy tale and queer fantasy. Inspiring children’s non-fiction. She loves worlds to get lost in, adventures that transform what it means to be a hero, and unique magic that offers as many problems as solutions. She likes books that make her cry and books that change her mind. Above all, when she finishes a story about another world, she wants it to have taught her a lesson which helps her live in this one. She loves all fantasy, but favours richly imagined, complex worlds with a history to discover and a future to protect. Worldbuilding is one of her favourite aspects of this genre and she is always looking for a new, dense world with series potential. Think Brandon Sanderson’s Cosmere or the Marvel Cinematic Universe – the bigger the better! Maddy also likes character-driven fantasy with a diverse cast to root for (or root against) and she wants to see a range of different relationships depicted authentically. She particularly like epics that dip into big, universal themes such as grief, climate change, or war and which ask impossible questions in the vein of R.F. Kuang or N.K. Jemisin. She is also excited by authors that play with form and language in a fantasy setting. In YA, she is looking for much the same as in an adult fantasy, but with younger protagonists and a closer focus on relationships. She wants to see the tropes she knows and loves in new and exciting forms and her favourite YA books often centre around belonging and becoming. She likes a dash of romance in everything, because she is sentimental that way, but it’s particularly important in the YA space. Sci-fi is a big passion of hers, especially when it comes with a strong hook. She is a huge fan of Becky Chamber’s The Long Way to a Small Angry Planet and Michaiah Johnson’s The Space Between Worlds. She likes space as a metaphor, and would love something that explores different alien species. Please send her your space operas and sci-fi romances which combine space, magic and mayhem! In fantasy middle grade, she favours whimsy and animal companions; she would love to follow a group of kids through magic school. She tends to look for plenty of humour with a strong friendship at the centre, and she wants middle grade stories which engage with the concerns of children growing up as well as offering an all-important escape (preferably on a dragon/unicorn’s back). She is also looking for children’s non-fiction for all ages. In this space, she wants something as creative as it is informative, and thinks diverse voices are increasingly important. Maddy would like you to submit a covering letter, one page synopsis and the first three chapters (Max 5000 words) of your completed manuscript in a single word document. (In addition to the paid sessions, Maddy is kindly offering one free session for low income/under-represented writers. Please email agent121@iaminprint.co.uk to apply, outlining your case for this option which is offered at the discretion of I Am In Print). By booking you understand you need to conduct an internet connection test with I Am In Print prior to the event. You also agree to email your material in one document to reach I Am In Print by the stated submission deadline and note that I Am In Print take no responsibility for the advice received during your agent meeting. The submission deadline is: Wednesday 17th September 2025

CUSTOMS PROCEDURES & DOCUMENTATION
By Export Unlocked Limited
This course looks at the procedures required to deal with customs. It is vitally important that importers and exporters understand the information required to be submitted.

QA Level 2 Award In Food Safety For Retail (RQF) Face to Face: Full day course Virtual Classroom: Spread over 3 sessions of 2½ hr duration Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely Recommended by HSE and Environmental Health Officers (EHO's) Course Contents: The Importance of Food Safety Food Safety Laws Legal Responsibilities of Food Handlers Types of Contamination and the Associated Risks Bacteriology Food Poisoning Foodborne Illnesses An Introduction to Hazard Analysis and Critical Control Points (HACCP) Personal Hygiene Work Flow, Work Surfaces and Equipment Cleaning and Disinfection Waste Disposal Pest Control Safe Food Handling Practices including Time and Temperature Controls Preparation Cooking and Reheating Chilling Cooling Thawing Hot holding Displaying food Core temperatures Food Preservation Storage Stock Control Procedures Benefits of this course: Businesses have a duty to their customers to produce food that is safe for consumption. There are one million cases of food poisoning in the UK each year. More than 6,000 are admitted to hospital. In 2014/2015, businesses in Chesterfield were issued 344 written enforcement notices. Derby received 1,116. Doing our Ofqual regulated, nationally accredited course ensures that nothing of importance is left out. EU and UK regulations state that all food handlers must receive appropriate training in food safety practices relevant to their duties. The Food Standards Agency says that 'Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely’. Our QA Level 2 Award in Food Safety in Catering (RQF) is a nationally accredited qualification especially suitable for people working in, or planning to work in, the food retail industry, and complies with the training regulations.

QA Level 2 Award In Food Safety For Manufacturing (RQF) Face to Face: Full day course Virtual Classroom: Spread over 3 sessions of 2½hr duration Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely Recommended by HSE and Environmental Health Officers (EHO's) Course Contents: The Importance of Food Safety Food Safety Laws Legal Responsibilities of Food Handlers Types of Contamination and the Associated Risks Bacteriology Food Poisoning Foodborne Illnesses An Introduction to Hazard Analysis and Critical Control Points (HACCP) Personal Hygiene Work Flow, Work Surfaces and Equipment Cleaning and Disinfection Waste Disposal Pest Control Safe Food Handling Practices including Time and Temperature Controls Preparation Cooking and Reheating Chilling Cooling Thawing Hot holding Displaying food Core temperatures Food Preservation Storage Stock Control Procedures Benefits of this course: Businesses have a duty to their customers to produce food that is safe for consumption. There are one million cases of food poisoning in the UK each year. More than 6,000 are admitted to hospital. In 2014/2015, businesses in Chesterfield were issued 344 written enforcement notices. Derby received 1,116. Doing our Ofqual regulated, nationally accredited course ensures that nothing of importance is left out. EU and UK regulations state that all food handlers must receive appropriate training in food safety practices relevant to their duties. The Food Standards Agency says that 'Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely’. Our QA Level 2 Award in Food Safety in Catering (RQF) is a nationally accredited qualification especially suitable for people working in, or planning to work in, the food retail industry, and complies with the training regulations. Accredited, Ofqual regulated qualification: Our Food Safety For Manufacturing training course is a nationally recognised, Ofqual regulated qualification accredited by Qualsafe Awards. This means that you can be rest assured that your Food safety For Manufacturing certificate fulfils the legal requirements and is a very good way to make sure your employees are trained in Food Safety. The Ofqual Register number for this course is 603/2592/6

QA Level 2 Award In Food Safety In Catering (RQF) Face to Face: Full day course Virtual Classroom: Spread over 3 sessions of 2½ hr duration Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely Recommended by HSE and Environmental Health Officers (EHO's) Course Contents: The Importance of Food Safety Food Safety Laws Legal Responsibilities of Food Handlers Types of Contamination and the Associated Risks Bacteriology Food Poisoning Foodborne Illnesses An Introduction to Hazard Analysis and Critical Control Points (HACCP) Personal Hygiene Work Flow, Work Surfaces and Equipment Cleaning and Disinfection Waste Disposal Pest Control Safe Food Handling Practices including Time and Temperature Controls Preparation Cooking and Reheating Chilling Cooling Thawing Hot holding Displaying food Core temperatures Food Preservation Storage Stock Control Procedures Benefits of this course: Businesses have a duty to their customers to produce food that is safe for consumption. There are one million cases of food poisoning in the UK each year. More than 6,000 are admitted to hospital. In 2014/2015, businesses in Chesterfield were issued 344 written enforcement notices. Derby received 1,116. Doing our Ofqual regulated, nationally accredited course ensures that nothing of importance is left out. EU and UK regulations state that all food handlers must receive appropriate training in food safety practices relevant to their duties. The Food Standards Agency says that 'Food business operators are required by law, to ensure that food handlers receive appropriate supervision and instruction/training in food hygiene in line with their work activity and should enable them to handle food safely’. Our QA Level 2 Award in Food Safety in Catering (RQF) is a nationally accredited qualification especially suitable for people working in, or planning to work in, the food retail industry, and complies with the training regulations. Accredited, Ofqual regulated qualification Our Food Safety in Catering training course is a nationally recognised, Ofqual regulated qualification accredited by Qualsafe Awards. This means that you can be rest assured that your Food safety in Catering certificate fulfils the legal requirements and is a very good way to make sure your employees are trained in Food Safety. The Ofqual Register number for this course is 603/2594/X

Operations / Departmental Manager Level 5 apprenticeship
By Leadership Management International (LMI) UK
The Operations / Departmental Manager apprenticeship is for managers with increasing responsibility for the leading of their department or business division.


