- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Petroleum Geochemistry in Petroleum Exploration
By EnergyEdge - Training for a Sustainable Energy Future
Enhance your knowledge in petroleum geochemistry with EnergyEdge's course on petroleum exploration. Enroll now!

Spanish Language Masterclass
By The Teachers Training
Fluently express yourself in Spanish with our comprehensive Spanish Language Masterclass. Ideal for those seeking to deepen their language skills and cultural understanding.

Easily learn the skills and knowledge you desire in MS Office with our Microsoft Office for Admin, you get an unparalleled learning experience with us and you get a digital certificate, transcript and a student ID card all included with the course price. What makes us the go to choice for people who want to learn about MS Office is our dedication and commitment to providing you with the best service possible. You will get unlimited access to the Microsoft Office for Admin, no matter where you are in the world you will be able to access your Microsoft Office for Admin any time you want. Should you have any questions while studying this Microsoft Office for Admin, our experienced tutors and mentors will answer them via email and live chat. With the original certificate you get after completing your Microsoft Office for Admin you will gain the CPD qualifications that will help you succeed out in the world and in your career. With our Student ID card you will get discounts on things like music, food, travel and clothes etc. Enrol in our Microsoft Office for Admin today and start learning. Why buy this Microsoft Office for Admin? Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Microsoft Office for Admin you will be able to take the MCQ test that will assess your knowledge. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This Microsoft Office for Admin does not require you to have any prior qualifications or experience. You can just enrol and start learning. Prerequisites This Microsoft Office for Admin was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This Microsoft Office for Admin is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Microsoft Word 2016 Modify User Information 00:15:00 Share a Document 00:30:00 Work with Comments 00:15:00 Compare Document Changes 00:15:00 Review a Document 00:15:00 Merge Document Changes 00:15:00 Coauthor Documents 00:15:00 Add Captions 00:15:00 Add Cross-References 00:15:00 Add Bookmarks 00:15:00 Add Hyperlinks 00:15:00 Insert Footnotes and Endnotes 00:15:00 Add Citations 00:30:00 Insert a Bibliography 00:15:00 Insert Blank and Cover Pages 00:15:00 Insert an Index 00:30:00 Insert a Table of Contents 00:30:00 Insert an Ancillary Table 00:15:00 Manage Outlines 00:30:00 Create a Master Document 00:30:00 Suppress Information 00:30:00 Set Editing Restrictions 00:30:00 Add a Digital Signature to a Document 00:15:00 Restrict Document Access 00:15:00 Create Forms 00:30:00 Manipulate Forms 00:15:00 Form Data Conversion 00:15:00 Create a New Document Version 00:30:00 Compare Document Versions 00:15:00 Merge Document Versions 00:15:00 Activities - Microsoft Word 2016 Advanced 00:00:00 Microsoft Excel 2016 Update Workbook Properties 00:15:00 Activity-Update Workbook Properties 00:05:00 Create and Edit a Macro 00:15:00 Activity-Create and Edit a Macro 00:05:00 Apply Conditional Formatting 00:30:00 Activity-Apply Conditional Formatting 00:05:00 Add Data Validation Criteria 00:15:00 Activity-Add Data Validation Criteriaty 00:05:00 Trace Cells 00:15:00 Activity-Trace Cells 00:05:00 Troubleshoot Invalid Data and Formula Errors 00:15:00 Activity-Troubleshoot Invalid Data and Formula Errors 00:05:00 Watch and Evaluate Formulas 00:15:00 Activity-Watch and Evaluate Formulas 00:05:00 Create a Data List Outline 00:15:00 Activity-Create a Data List Outline1 00:05:00 Create Sparklines 00:15:00 Activity_Create Sparklines 00:05:00 Create Scenarios 00:15:00 Activity-Create Scenarios 00:05:00 Perform a What-If Analysis 00:15:00 Activity-Perform a What-If Analysis 00:05:00 Perform a Statistical Analysis with the Analysis ToolPak 00:15:00 Activity-Perform a Statistical Analysis with the Analysis ToolPak 00:05:00 Create Interactive Data with Power View 00:15:00 Activity-Create Interactive Data with Power View1 00:05:00 Consolidate Data 00:15:00 Activity-Consolidate Data 00:05:00 Link Cells in Different Workbooks 00:15:00 Activity-Link Cells in Different Workbooks 00:05:00 Merge Workbooks 00:15:00 Activity-Merge Workbooks 00:05:00 Export Excel Data 00:15:00 Activity-Export Excel Data 00:05:00 Import a Delimited Text File 00:14:00 Activity- Import a Delimited Text File 00:05:00 Integrate Excel Data with the Web 00:15:00 Activity-Integrate Excel Data with the Web 00:05:00 Create a Web Query 00:15:00 Activity-Create a Web Query 00:05:00 Import and Export XML Data 00:15:00 Activity-Import and Export XML Data 00:05:00 Activities - Microsoft Excel 2016 Advanced 00:00:00 Microsoft PowerPoint 2016 Customize the User Interface 01:30:00 Set PowerPoint 2016 Options 00:45:00 Create and Manage Sections 01:00:00 Modify Slide Masters and Slide Layouts 01:15:00 Add Headers and Footers 00:30:00 Modify the Notes Master and the Handout Master 00:45:00 Create SmartArt 00:45:00 Modify SmartArt 01:00:00 Add Audio to a Presentation 00:45:00 Add Video to a Presentatio 01:00:00 Customize Animations and Transitions 01:00:00 Add Comments to a Presentation 00:45:00 Review a Presentation 00:45:00 Store and Share Presentations on the Web 01:30:00 Annotate a Presentation 00:45:00 Set Up a Slide Show 00:45:00 Create a Custom Slide Show 00:30:00 Add Hyperlinks and Action Buttons 00:45:00 Record a Presentation 00:15:00 Secure a Presentation 01:30:00 Present a Slide Show Online 01:00:00 Create a Video or a CD 00:45:00 Activities - Microsoft PowerPoint 2016 Advanced 00:00:00 Microsoft Outlook 2016 Insert Advanced Characters and Objects 01:30:00 Modify Message Settings, Properties, and Options 01:30:00 Use Automatic Replies 01:30:00 Sort Messages 00:45:00 Filter Messages 01:00:00 Organize Messages 02:00:00 Search Messages 01:30:00 Manage Junk Mail 01:00:00 Manage Your Mailbox 02:00:00 Manage Advanced Calendar Options1 00:45:00 Manage Additional Calendars 01:00:00 Manage Meeting Responses 00:45:00 Assign and Manage Tasks 01:00:00 Edit an Electronic Business Card 01:00:00 Manage Advanced Contact Options 01:30:00 Forward Contacts 00:30:00 Export Contacts 01:00:00 Delegate Access to Mail Folders 01:00:00 Share Your Calendar 00:30:00 Share Your Contacts 00:15:00 Back Up Outlook Items 00:45:00 Change Data File Settings 00:45:00 Configure E-mail Message Security Settings 00:30:00 Activities - Microsoft Outlook 2016 Advanced 00:00:00 Microsoft Access 2016 Add Controls to Forms 01:00:00 Set Form Controls 01:00:00 Create Subforms 00:30:00 Organize Information with Tab Pages 00:30:00 Enhance Navigation with Forms 00:30:00 Format a Form 01:00:00 Apply Conditional Formatting 00:30:00 Field Validation 00:30:00 Form and Record Validation 00:30:00 Create a Macro 01:00:00 Restrict Records Using a Condition 00:30:00 Validate Data Using a Macro 00:30:00 Automate Data Entry Using a Macro 00:30:00 Convert a Macro to VBA 00:30:00 Link Tables to External Data Sources 00:30:00 Manage a Database 00:30:00 Determine Object Dependency 00:30:00 Document a Database 00:30:00 Analyze the Performance of a Database1 00:30:00 Split a Database for Multiple User Access 00:30:00 Implement Security 00:30:00 Set Passwords 00:30:00 Convert an Access Database to an ACCDE File 00:30:00 Package a Database with a Digital Signature 00:30:00 Create a Database Switchboard 01:00:00 Modify a Database Switchboard 00:30:00 Set Startup Options 00:30:00 Activities - Microsoft Access 2016 Advanced 00:00:00

Cisco Implementing and Operating Cisco Security Core Technologies v1.0 (SCOR)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Security engineer Network engineer Network designer Network administrator Systems engineer Consulting systems engineer Technical solutions architect Network manager Cisco integrators and partners Overview After taking this course, you should be able to: Describe information security concepts and strategies within the network Describe common TCP/IP, network application, and endpoint attacks Describe how various network security technologies work together to guard against attacks Implement access control on Cisco ASA appliance and Cisco Firepower Next-Generation Firewall Describe and implement basic email content security features and functions provided by Cisco Email Security Appliance Describe and implement web content security features and functions provided by Cisco Web Security Appliance Describe Cisco Umbrella security capabilities, deployment models, policy management, and Investigate console Introduce VPNs and describe cryptography solutions and algorithms Describe Cisco secure site-to-site connectivity solutions and explain how to deploy Cisco Internetwork Operating System (Cisco IOS) Virtual Tunnel Interface (VTI)-based point-to-point IPsec VPNs, and point-to-point IPsec VPN on the Cisco ASA and Cisco Firepower Next-Generation Firewall (NGFW) Describe and deploy Cisco secure remote access connectivity solutions and describe how to configure 802.1X and Extensible Authentication Protocol (EAP) authentication Provide basic understanding of endpoint security and describe Advanced Malware Protection (AMP) for Endpoints architecture and basic features Examine various defenses on Cisco devices that protect the control and management plane Configure and verify Cisco IOS software Layer 2 and Layer 3 data plane controls Describe Cisco Stealthwatch Enterprise and Stealthwatch Cloud solutions Describe basics of cloud computing and common cloud attacks and how to secure cloud environment The Implementing and Operating Cisco Security Core Technologies (SCOR) v1.0 course helps you prepare for the Cisco© CCNP© Security and CCIE© Security certifications and for senior-level security roles. In this course, you will master the skills and technologies you need to implement core Cisco security solutions to provide advanced threat protection against cybersecurity attacks. You will learn security for networks, cloud and content, endpoint protection, secure network access, visibility, and enforcements. You will get extensive hands-on experience deploying Cisco Firepower© Next-Generation Firewall and Cisco Adaptive Security Appliance (ASA) Firewall; configuring access control policies, mail policies, and 802.1X Authentication; and more. You will get introductory practice on Cisco Stealthwatch© Enterprise and Cisco Stealthwatch Cloud threat detection features. This course, including the self-paced material, helps prepare you to take the exam, Implementing and Operating Cisco Security Core Technologies (350-701 SCOR), which leads to the new CCNP Security, CCIE Security, and the Cisco Certified Specialist - Security Core certifications. Describing Information Security Concepts* Information Security Overview Assets, Vulnerabilities, and Countermeasures Managing Risk Vulnerability Assessment Understanding Common Vulnerability Scoring System (CVSS) Describing Common TCP/IP Attacks* Legacy TCP/IP Vulnerabilities IP Vulnerabilities Internet Control Message Protocol (ICMP) Vulnerabilities TCP Vulnerabilities User Datagram Protocol (UDP) Vulnerabilities Attack Surface and Attack Vectors Reconnaissance Attacks Access Attacks Man-in-the-Middle Attacks Denial of Service and Distributed Denial of Service Attacks Reflection and Amplification Attacks Spoofing Attacks Dynamic Host Configuration Protocol (DHCP) Attacks Describing Common Network Application Attacks* Password Attacks Domain Name System (DNS)-Based Attacks DNS Tunneling Web-Based Attacks HTTP 302 Cushioning Command Injections SQL Injections Cross-Site Scripting and Request Forgery Email-Based Attacks Describing Common Endpoint Attacks* Buffer Overflow Malware Reconnaissance Attack Gaining Access and Control Gaining Access via Social Engineering Gaining Access via Web-Based Attacks Exploit Kits and Rootkits Privilege Escalation Post-Exploitation Phase Angler Exploit Kit Describing Network Security Technologies Defense-in-Depth Strategy Defending Across the Attack Continuum Network Segmentation and Virtualization Overview Stateful Firewall Overview Security Intelligence Overview Threat Information Standardization Network-Based Malware Protection Overview Intrusion Prevention System (IPS) Overview Next Generation Firewall Overview Email Content Security Overview Web Content Security Overview Threat Analytic Systems Overview DNS Security Overview Authentication, Authorization, and Accounting Overview Identity and Access Management Overview Virtual Private Network Technology Overview Network Security Device Form Factors Overview Deploying Cisco ASA Firewall Cisco ASA Deployment Types Cisco ASA Interface Security Levels Cisco ASA Objects and Object Groups Network Address Translation Cisco ASA Interface Access Control Lists (ACLs) Cisco ASA Global ACLs Cisco ASA Advanced Access Policies Cisco ASA High Availability Overview Deploying Cisco Firepower Next-Generation Firewall Cisco Firepower NGFW Deployments Cisco Firepower NGFW Packet Processing and Policies Cisco Firepower NGFW Objects Cisco Firepower NGFW Network Address Translation (NAT) Cisco Firepower NGFW Prefilter Policies Cisco Firepower NGFW Access Control Policies Cisco Firepower NGFW Security Intelligence Cisco Firepower NGFW Discovery Policies Cisco Firepower NGFW IPS Policies Cisco Firepower NGFW Malware and File Policies Deploying Email Content Security Cisco Email Content Security Overview Simple Mail Transfer Protocol (SMTP) Overview Email Pipeline Overview Public and Private Listeners Host Access Table Overview Recipient Access Table Overview Mail Policies Overview Protection Against Spam and Graymail Anti-virus and Anti-malware Protection Outbreak Filters Content Filters Data Loss Prevention Email Encryption Deploying Web Content Security Cisco Web Security Appliance (WSA) Overview Deployment Options Network Users Authentication Secure HTTP (HTTPS) Traffic Decryption Access Policies and Identification Profiles Acceptable Use Controls Settings Anti-Malware Protection Deploying Cisco Umbrella* Cisco Umbrella Architecture Deploying Cisco Umbrella Cisco Umbrella Roaming Client Managing Cisco Umbrella Cisco Umbrella Investigate Overview and Concepts Explaining VPN Technologies and Cryptography VPN Definition VPN Types Secure Communication and Cryptographic Services Keys in Cryptography Public Key Infrastructure Introducing Cisco Secure Site-to-Site VPN Solutions Site-to-Site VPN Topologies IPsec VPN Overview IPsec Static Crypto Maps IPsec Static Virtual Tunnel Interface Dynamic Multipoint VPN Cisco IOS FlexVPN Deploying Cisco IOS VTI-Based Point-to-Point IPsec VPNs Cisco IOS VTIs Static VTI Point-to-Point IPsec Internet Key Exchange (IKE) v2 VPN Configuration Deploying Point-to-Point IPsec VPNs on the Cisco ASA and Cisco Firepower NGFW Point-to-Point VPNs on the Cisco ASA and Cisco Firepower NGFW Cisco ASA Point-to-Point VPN Configuration Cisco Firepower NGFW Point-to-Point VPN Configuration Introducing Cisco Secure Remote Access VPN Solutions Remote Access VPN Components Remote Access VPN Technologies Secure Sockets Layer (SSL) Overview Deploying Remote Access SSL VPNs on the Cisco ASA and Cisco Firepower NGFW Remote Access Configuration Concepts Connection Profiles Group Policies Cisco ASA Remote Access VPN Configuration Cisco Firepower NGFW Remote Access VPN Configuration Explaining Cisco Secure Network Access Solutions Cisco Secure Network Access Cisco Secure Network Access Components AAA Role in Cisco Secure Network Access Solution Cisco Identity Services Engine Cisco TrustSec Describing 802.1X Authentication 802.1X and Extensible Authentication Protocol (EAP) EAP Methods Role of Remote Authentication Dial-in User Service (RADIUS) in 802.1X Communications RADIUS Change of Authorization Configuring 802.1X Authentication Cisco Catalyst© Switch 802.1X Configuration Cisco Wireless LAN Controller (WLC) 802.1X Configuration Cisco Identity Services Engine (ISE) 802.1X Configuration Supplicant 802.1x Configuration Cisco Central Web Authentication Describing Endpoint Security Technologies* Host-Based Personal Firewall Host-Based Anti-Virus Host-Based Intrusion Prevention System Application Whitelists and Blacklists Host-Based Malware Protection Sandboxing Overview File Integrity Checking Deploying Cisco Advanced Malware Protection (AMP) for Endpoints* Cisco AMP for Endpoints Architecture Cisco AMP for Endpoints Engines Retrospective Security with Cisco AMP Cisco AMP Device and File Trajectory Managing Cisco AMP for Endpoints Introducing Network Infrastructure Protection* Identifying Network Device Planes Control Plane Security Controls Management Plane Security Controls Network Telemetry Layer 2 Data Plane Security Controls Layer 3 Data Plane Security Controls Deploying Control Plane Security Controls* Infrastructure ACLs Control Plane Policing Control Plane Protection Routing Protocol Security Deploying Layer 2 Data Plane Security Controls* Overview of Layer 2 Data Plane Security Controls Virtual LAN (VLAN)-Based Attacks Mitigation Sp

The Impact of Electric Vehicles (EVs) on the Grid
By EnergyEdge - Training for a Sustainable Energy Future
About this Virtual Instructor Led Training (VILT) Electrification of the transportation sector will impact the power system in several ways. Besides the additional load, local impact on the grid needs to be managed by the grid operators. Simultaneously charging of many electric vehicles (EVs) might exceed the limits in specific locations. On the other hand, EVs can provide flexibility and other ancillary services that will help grid operators. This 3 half-day VILT course will provide a complete overview of integrating electric vehicles (EVs) into the power grid. It will cover the whole value chain from grid operations to the car battery. This includes the control room, possible grid reinforcement, demand side management and power electronics. This course will demonstrate the impact on the grid and solutions for a safe & cost-effective grid plan and operation, with examples of successful integration of EVs. The course will also provide vital knowledge about technology used for EVs such as power electronics, demand side management, communication and batteries. In this context, the focus will be on power electronics as it has the highest impact on the grid. The grid planning tool, pandapower, is introduced as an open source tool for power system modelling. The set-up of the training course allows for discussion and questions. Questions can be formulated by the participants upfront or during the training. This course is delivered in partnership with Fraunhofer IEE. Training Objectives At the end of this course, the participants will: Understand the charging options for EVs and its impact on the grid and batteries Identify system services for EVs with regards to voltage quality at the point of common coupling Discover what are the 'grid friendly' and grid supporting functions in EVs Uncover the different applications, standards and data researched on EVs Examine the application of a grid planning tool (pandapower) for power system modelling Be able to develop code snippets with pandapower Apply and execute a code example for power system modelling with pandapower Target Audience EV and grid project developers and administrators Power grid operators and planners EPC organisations involved in grid development EV/ battery manufacturers and designers EV transport planners and designers Government regulators and policy makers Training Methods The VILT will be delivered online in 3 half-day sessions comprising 4 hours per day, with 2 x 10 minutes breaks per day, including time for lectures, discussion, quizzes and short interactive exercises. Additionally, some self-study will be requested. Participants are invited but not obliged to bring a short presentation (10 mins max) on a practical problem they encountered in their work. This will then be explained and discussed during the VILT. A short test or quiz will be held at the end of every session/day. Trainer Our first course expert is Head of Department Converters and Electrical Drive Systems at Fraunhofer IEE and Professor for Electromobility and Electrical Infrastructure at Bonn-Rhein-Sieg University of Applied Sciences. He received his engineering degree in automation in 2008 by the THM Technische Hochschule Mittelhessen (FH Giessen-Friedberg). Afterwards he studied power engineering at University of Kassel and received his diploma certificate in 2010. In 2016 he received the Ph.D. (Dr.-Ing.) from the University of Hannover. The title of his dissertation is Optimized multifunctional bi-directional charger for electric vehicles. He has been a researcher at the Fraunhofer IEE in Kassel since 2010 and deals with power converters for electric vehicles, photovoltaics and wind energy. His current research interests include the bidirectional inductive power transfer, battery charger and inverter as well as new power electronic components such as SiC MOSFETs and chokes. Additionally, our key expert is Chairman of the IEEE Joint IAS/PELS/IES German Chapter and a member of the International Scientific Committee of the EPE Association. Our second course expert is deputy head of energy storage department at Fraunhofer IEE. Prior to this he was the Director of Grid Integration department at SMA Solar Technology AG, one of the world's largest manufacturers of PV power converters. Before joining SMA, our course expert was manager of the Front Office System Planning at Amprion GmbH (formerly RWE TSO), one of the four German transmission system operators. He holds a degree of electrical engineering of the University of Kassel, Germany. In 2003 he finished his Ph.D. (Dr.-Ing.) on the topic of wind power forecasting at the 'Institute of Solar Energy Supply Technology' (now Fraunhofer IEE) in Kassel. In 2004 he started his career at RWE TSO with main focus on wind power integration and congestion management. Our course expert is chairman of the IEC SC 8A 'Grid Integration of Large-capacity Renewable Energy (RE) Generation' and has published several papers about grid integration of renewable energy source and forecasting systems on books, magazines, international conferences and workshops. Our third course expert is Research Associate at Fraunhofer IEE. He is actively working on different projects related to the integration of electric vehicle charging into the electric distribution grid. The focus of this work concerns time series based simulations for grid planning and operation in order to investigate the effect of a future rollout of electric vehicles and charging infrastructure on economics e.g. costs for grid reinforcement. He completed his master degree (MSc.) in Business Administration and Engineering: Electrical Power Engineering at RWTH Aachen University, Germany. Our trainers are experts from Fraunhofer Institute for Energy Economics and Energy System Technology (Fraunhofer, IEE), Germany. The Fraunhofer IEE researches for the national and international transformation of energy supply systems POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information about post training coaching support and fees applicable for this. Accreditions And Affliations

Special Executive Master's Programme in Business Enterprise Software
4.9(261)By Metropolitan School of Business & Management UK
Special Executive Masters Programme (S.E.M.P) This programme is geared at enhancing professionals' careers. The SEMP is an encapsulated Senior Management Programmes are short certificate modules designed for anyone who would benefit from more in-depth business knowledge delivered in a short and intensive programme What makes us different? We are a world class business school located in the heart of London, Dubai, Islamabad and Lagos. We are one of the fastest growing British business schools with a stylish blended learning model that is both online and on campus. Learn more about the programme Special Executive Master's Programme in Business Enterprise Software Course Overview The MSBM Special Executive Masters Programmes (SEMP) allows you to update your skills, develop new skills, and explore and develop interests in a wide range of topics. These courses can be taken as personal or professional development and may enhance your employability. Business Enterprise Software is a professional area of practice that assists enterprises in designing solutions to achieve their current and future business objectives. While enterprise software has most often been applied to complex technology environments with high technology investments, the practice is relevant for all types and sizes of enterprises. All enterprises have business goals and objectives, and all have resources that must be aligned with those goals in an effective and efficient way. Enterprise software is a critical first step in achieving those goals. One of the most important lessons from enterprise software is the importance of design and engineering before implementation. Business Enterprise Software is a critical area today given the increasing complexity of our environment and the need for greater agility. The virtualization of work, the multinational nature of work, the increasingly semantic and personalized nature of applications, the richness of technology, the increasingly networked nature of the business, a shift from simple projects to complex projects — all speak to the need for Business Enterprise Software. Course Details Mode of Study Using Web-based technology, this program provides self-paced, individualized instruction that can be taken anywhere and anytime an individual has access to a computer and the Internet. This Programme is suitable for successful professionals or specialists in the private, public, or voluntary sectors who have new management responsibilities and need to quickly expand their management knowledge. This Programme serves as a refresher course for those who have had their Masters a long time ago and need quick reminders and professional/ academic updates while it serves as a primer for those very experienced Professionals who never made time out for their masters yet they require the academic and practical relevance of this master’s experience. It is a short executive training that runs online for 3 months. Candidates will run 2 months of active lectures and series of assignments and 1 month for their dissertation. Upon successful completion of the Programme, candidates will be awarded a Continuing Professional Development (CPD) certificate in the specific Programme they have completed. What is a CPD Course? Continuing Professional Development (CPD) is the means by which professionals maintain and enhance their knowledge and skills. The world is constantly moving at a very fast pace so undertaking CPD is essential to support a professional in his/her current role as well as helping them with career progression. CPD is all about upgrading knowledge, skills, and capabilities to remain effective and compliant. A CPD course is an investment that you make in yourself. It’s a way of planning your development that links learning directly to practice. CPD can help you keep your skills and knowledge up to date and prepare you for greater responsibilities. It can boost your confidence, strengthen your professional credibility, and help you become more creative in tackling new challenges. Is the SEMP Business Enterprise Software Programme, right for me? Many organizations are embracing the use of business software to support their business priorities and objectives, and are implementing initiatives and programs to deploy business analytics across the enterprise. For these initiatives to succeed, organizations need to understand the key drivers that will facilitate the promotion and deployment of business analytics across the enterprise. The SEMP BES online program will provide an overview of the key organizational drivers and dimensions and will explore how business software should be aligned to support the organization's priorities. This online Programme will also discuss the role and function of enterprise Business software centers of excellence and their types and mandates. The SEMP BES will provide a guideline for assessing your organization's maturity, and for establishing a roadmap for an Enterprise Business Software Center of Excellence at your organization. Why SEMP Business Enterprise Software? This non-credit-bearing course provides an excellent introduction to the world of business process and systems consulting, implementation, and management. It is particularly relevant both for experienced consultants that wish to gain a broader knowledge of Business enterprise and those wishing to enter business for the first time. The course enables you to rapidly gain knowledge about how modern management information systems are structured, how they are managed and the issues in integrating them to support effective business decision making. You will take away a deep understanding of how to integrate business systems and the processes underlying them. You will gain not only knowledge of specific aspects of business enterprise, but also gain an appreciation for how a large enterprise attempts to pull together different business processes through a coherent enterprise system, and the challenges facing the elite consulting companies in implementing such systems. Who should enrol in this online Certificate Program? This online certificate program in Information System benefits professionals at all levels who want to contribute to their organization’s performance. Here are some of the people who will benefit from the online Programme: Cross-functional teams from within an organization can take the program, as that accelerates the impact and engenders a common language and understanding in the organization I.T Managers Business owners in the I.T Industry IT Trainers Accreditation The content of this course has been independently certified as conforming to universally accepted Continuous Professional Development (CPD) guidelines. Entry Requirements There are no strict entry requirements for this course. Work experience will be added advantage to understanding the content of the course. Workshops This is a self-study programme with unlimited tutor support. You will never be more than a message or phone call away from our tutors.

UNCONSCIOUS BIAS TOWARDS RACISM
By Inclusive Solutions
Unconscious biases are social stereotypes about certain groups of people that individuals form outside their own conscious awareness. Course Category Relationships Racial bias Description Unconscious biases are social stereotypes about certain groups of people that individuals form outside their own conscious awareness. Everyone holds unconscious beliefs about various social and identity groups and these biases stem from one’s tendency to organise social worlds by categorising. So join us on a reflective, engaging day where we tackle real life issues in depth and create action plans for future practice. Learning Objectives Increased confidence and understanding regarding Unconscious Bias Action planning New skills and processes to strengthen the inclusion of diverse groups Opportunity to reflect and understand more deeply on what might be happening due to unconscious bias’ Who Is It For? Any professional, carer or parent Course Content We will explore what is known about:Restorative JusticeDiversityAttitudes and ValuesProfessional dutiesReflective practice

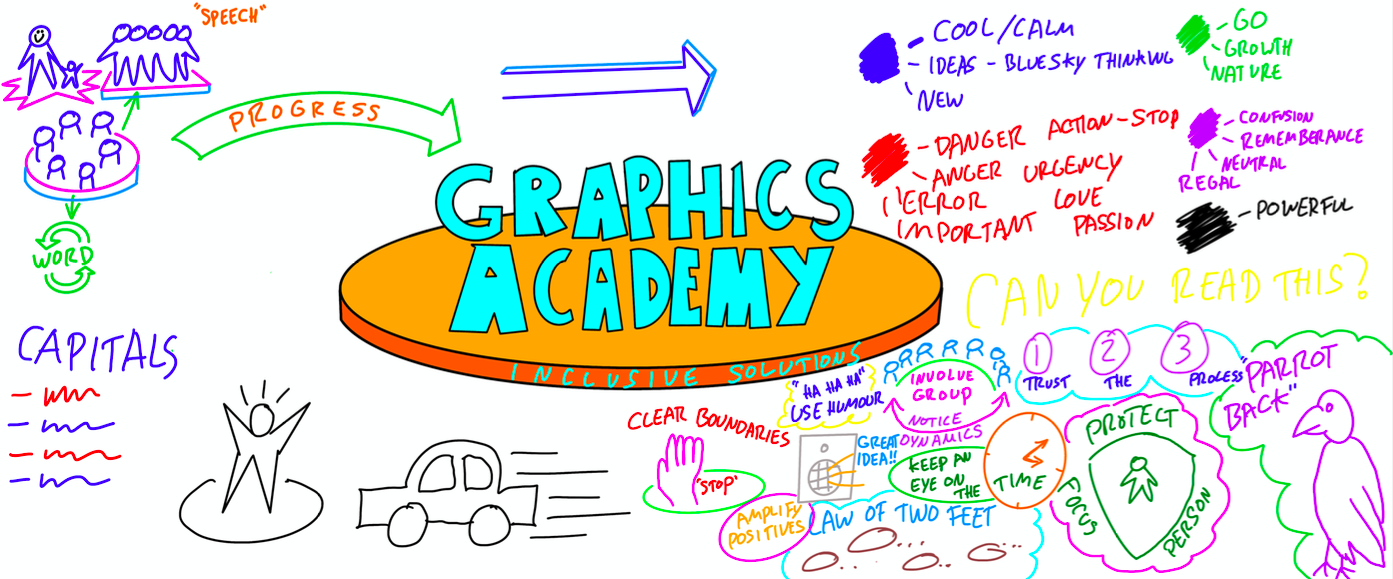
GRAPHIC FACILITATION – AN INTRODUCTION
By Inclusive Solutions
This day will introduce you to the basic techniques and skills involved in doing graphic facilitation. Learn how to use a BIG piece of paper and a handful of pens to create a memorable summary of your training day, team meeting or your work with young people and families. Learn how to harvest the essence of an event in a visual representation. This is a ‘hands on’ interactive day built around demonstrations of graphic facilitation, coaching and the chance to try things out. Ideal for teams who can then go on together to practice, practice, practice. Learning Objectives To introduce you to the basic skills of graphic facilitation – no previous experience is needed To develop your capacity to ‘listen under the words’ and draw out the deeper messages To help you suspend your self-doubt – “I can’t draw!” and rediscover your capacity to create an effective visual representation of a meeting/training day/conversation etc Course Content The day will introduce you to the fundamentals of graphic facilitation and will include the following topics: Pens, Pastels and Paper – what you will need to get started The basic ‘grammar’ of graphic facilitation; the essential shapes, using colour, images, lettering, words, creating connection How to listen for the essence of what is being said and translate this into visual language A chance to do it live – with coaching
MOVEMENT DIFFERENCES
By Inclusive Solutions
In this workshop we explore how to understand movement differences of those with ADHD/Autism, Tourettes or Cerebral Palsy in a non-medical way. Online course coming soon Online Course now available via Teachable Platform – Understanding Movement Differences Learn at your own pace… lots of text and video support Course Category Inclusion Autism and Communication Behaviour and Relationships Description In this workshop we explore how to understand movement differences of those with ADHD/Autism, Tourettes or Cerebral Palsy in a non-medical way. Learning Objectives To understand movement differences using a respectful model that helps us all empathise For participants to understand the underlying rationale and ethos of this way of working To explore ways of maximising an individual’s inclusion and connection with the wider community through useful strategies around their movement challenges To explore ways of helping with movement accommodations Who Is It For? Anyone interested in mobilising the community to make it more inclusive around disabled or challenging individuals. Course Content • Understanding movement differences: stopping/starting/executing/switching and combining • Inclusion strategies • Building relationships • Frameworks of support

Keys To Inclusion
By Inclusive Solutions
How can we interrupt the isolation of disabled, challenging and other ‘different’ children and adults? This is our lead workshop/training day and is both a values primer and a practical guide to successful strategies for developing inclusive practice in educational and non educational settings for children and young people of all ages. This is practical plus being a ‘hearts and minds’ day. What does inclusion mean? Can we imagine what an inclusive school look like? What do we have to do? The day gives those present opportunities to reflect on their attitudes and practice in relation to the inclusion of children and adults who are different or challenging. The Keys can be presented as a powerful interactive Keynote for large conferences. A great way to launch a conference as the first key is ‘welcome’. Learning Objectives Increased confidence regarding developing inclusive practice in mainstream schools and other settings Access to a wider range of practical strategies to impact on behaviour problems Deeper understanding of core values surrounding inclusion of disabled and challenging children and adults Opportunity to reflect on professional attitudes and behaviour towards parents and pupils New skills and processes to make inclusion successful Course Content The course answers the questions : Why inclusion? What is inclusion? How do we go about including high profile children or young people? What does inclusion have to do with me? Best delivered over the course of a full day, ‘Keys to Inclusion’ introduces participants to 6 guiding Ideas that underpin inclusive practice. The importance of WELCOME Inclusion is about Adults’ learning Taking the Long View Giftedness as a new paradigm for understanding disability and difference The Intentional Building of Relationships – ‘Circle of Friends’ work as an example of this Not doing it alone – the importance of Teams in developing inclusive practice.
