- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1823 Manager courses in Strabane delivered Live Online
SC-900T00 Microsoft Security Compliance and Identity Fundamentals
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for The audience for this course is looking to familiarize themselves with the fundamentals of security, compliance, and identity (SCI) across cloud-based and related Microsoft services. The content for this course aligns to the SC-900 exam objective domain. Candidates should be familiar with Microsoft Azure and Microsoft 365 and understand how Microsoft security, compliance, and identity solutions can span across these solution areas to provide a holistic and end-to-end solution. Before attending this course, students must have: General understanding of networking and cloud computing concepts. General IT knowledge or any general experience working in an IT environment. General understanding of Microsoft Azure and Microsoft 365. This course provides foundational level knowledge on security, compliance, and identity concepts and related cloud-based Microsoft solutions. Prerequisites General understanding of networking and cloud computing concepts. General IT knowledge or any general experience working in an IT environment. General understanding of Microsoft Azure and Microsoft 365. 1 - Describe security and compliance concepts Describe the shared responsibility model Describe defense in depth Describe the Zero Trust model Describe governance, risk, and compliance (GRC) concepts 2 - Describe identity concepts Define authentication and authorization Define identity as the primary security perimeter Describe the role of the identity provider Describe the concept of directory services and Active Directory Describe the concept of federation 3 - Describe the function and identity types of Microsoft Entra ID Describe Microsoft Entra ID Describe types of identities Describe hybrid identity Describe external identities 4 - Describe the authentication capabilities of Microsoft Entra ID Describe authentication methods Describe multifactor authentication Describe self-service password reset Describe password protection and management capabilities 5 - Describe access management capabilities of Microsoft Entra ID Describe Conditional Access Describe Microsoft Entra roles and role-based access control (RBAC) 6 - Describe the identity protection and governance capabilities of Azure AD Describe Microsoft Entra ID Governance Describe access reviews Describe entitlement management Describe the capabilities of Privileged identity Management Describe Microsoft Entra ID Protection Describe Microsoft Entra Permissions Management Describe Microsoft Entra Verified ID 7 - Describe core infrastructure security services in Azure Describe Azure DDoS protection Describe Azure Firewall Describe Web Application Firewall Describe network segmentation in Azure Describe Azure Network Security Groups Describe Azure Bastion Describe Azure Key Vault 8 - Describe the security management capabilities in Azure Describe Microsoft Defender for Cloud Describe how security policies and initiatives improve cloud security posture Describe Cloud security posture management Describe the enhanced security of Microsoft Defender for Cloud Describe DevOps security management 9 - Describe security capabilities of Microsoft Sentinel Describe threat detection and mitigation capabilities in Microsoft Sentinel Describe Microsoft Security Copilot 10 - Describe threat protection with Microsoft Defender XDR Describe Microsoft Defender XDR services Describe Microsoft Defender for Office 365 Describe Microsoft Defender for Endpoint Describe Microsoft Defender for Cloud Apps Describe Microsoft Defender for Identity Describe Microsoft Defender Vulnerability Management Describe Microsoft Defender Threat Intelligence Describe the Microsoft Defender portal 11 - Describe Microsoft?s Service Trust portal and privacy capabilities Describe the offerings of the Service Trust portal Describe Microsoft's privacy principles Describe Microsoft Priva 12 - Describe the compliance management capabilities in Microsoft Purview Describe the Microsoft Purview compliance portal Describe Compliance Manager Describe use and benefits of compliance score 13 - Describe information protection, data lifecycle management, and data governance capabilities in Microsoft Purview Know your data, protect your data, and govern your data Describe the data classification capabilities of the compliance portal Describe sensitivity labels and policies Describe data loss prevention Describe retention policies and retention labels Describe records management Describe the Microsoft Purview unified data governance solution 14 - Describe the insider risk capabilities in Microsoft Purview Describe insider risk management Describe communication compliance 15 - Describe the eDiscovery and Audit capabilities in Microsoft Purview Describe the eDiscovery solutions in Microsoft Purview Describe the audit solutions in Microsoft Purview

Better Business Cases Foundation & Practitioner: In-House
By IIL Europe Ltd
Better Business Cases™ Foundation and Practitioner: In-House Training Using this best-practice approach will allow organizations to reduce unnecessary spending and improve the decision-making process which gives you a greater chance of securing necessary funding and support for initiatives. The goal of the combined foundation and practitioner course is to develop a candidate's ability to deliver a comprehensive business case through encouraging expanded knowledge to guide the practical application of theoretical foundations. Upon the completion of this course, a candidate will be able to start applying the model to a real business case development project. The outline presented in the course overview will be addressed in the first 2 days, with the Foundation exam conducted on the morning of Day 3. Then the topics will be revisited at a deeper level, for 2 more days, with the Practitioner exam conducted on the afternoon of Day 5. What you will Learn At the end of this program, you will be able to: Develop the lifecycle of a business case and establish the relationships between the five cases Apply the steps in the business case development framework, in order to support the production of a business case, using the Five Case Model, for a given scenario. Overview of Better Business Cases Alignment with the strategic planning process Importance of the Business Case using the Five Case Model Overview of the Five Case Model Purpose of the key stages in the development of a spending proposal Purpose of a Business Justification Case Business Case Development Process Purpose of project / programme assurance and assurance reviews Responsibility for producing the Business Case Determining the Strategic Context and Undertaking the Strategic Assessment Scoping the Scheme and Preparing the Strategic Outline Case Planning the Scheme and Preparing the Outline Business Case Procuring the Solution and Preparing the Full Business Case Implementation and monitoring Evaluation and feedback Making the Case for Change Agree on the strategic context Determine spending objectives, existing arrangements, and business needs Determine potential business scope and key service requirements Determine benefits, risks, constraints, and dependencies Exploring the Preferred Way Forward Agree on critical success factors Determine long list options and SWOT analysis Recommend a preferred way forward Determining Potential Value for Money Revisit the short list Prepare the economic appraisal for short-listed options Undertake benefits appraisal Undertake risk appraisal Select preferred option and undertake sensitivity analysis Preparing for the Potential Deal Determine the procurement strategy Determine service streams and required outputs Outline potential risk apportionment Outline potential payment mechanisms Ascertain contractual issues and accountancy treatment Ascertaining Affordability and Funding Requirement Prepare the financial model Prepare the financial appraisals Planning for Successful Delivery Plan programme / project management Plan change and contract management Plan benefits realization Plan risk management Plan programme / project assurance and post-project evaluation Procuring the Value for Money Solution Revisit the case for change Revisit the OBC options Detail procurement process and evaluation of best and final offers (BAFOs) Contracting for the Deal Set out the negotiated deal and contractual arrangements Set out the financial implications of the deal Ensuring Successful Delivery Finalize project management arrangements and plans Finalize change management arrangements and plans Finalize benefits realization arrangements and plans Finalize risk management arrangements and plans Finalize contract management arrangements and plans Finalize post-project evaluation arrangements and plans

Corporate Peak Performance Program
By Netwomen
This highly interactive workshop will give your management team the skills and the tools necessary to understand relationships and behavioral styles of employees, improve performance and efficiency, and adopt solutions and strategies to increase your competitive edge. Optimised for tailored audiences Built for groups of 20+ Led by experienced and certified professionals Specialised to address issues around inclusivity and equity in all industries Program Details Peak Performance Part I: Observation, Assessment and Determination The final objective of this workshop is a full understanding of how managers can assess their employees for optimal behavioral team communication and assignments. Peak Performance Part II: High Efficiency Teams The final objective of this workshop is a full understanding of how managers can create High Efficiency teams taking into accounts skills and behaviors. Peak Performance Part III: Self-Learning Teams The Final objective of this workshop is KPIs agreed upon and commonly shared by employees and managers to allow employees to self-manage their learning and measure their progress monitored by managers. Investment Fee: £50,000 25 participants max per 12-week cohort TRAINING FORMAT : 12 - Week Cohorts Delivered in 1-hour sessions Virtually Facilitated Sessions Corporate Peak Performance Program One Pager

Project Requirements Management: Virtual In-House Training
By IIL Europe Ltd
Project Requirements Management: Virtual In-House Training Poor requirements definition and lack of adequate change control procedures to requirements and scope are the primary contributors to project difficulty and failure. This workshop will provide you with the knowledge, tools, and techniques required to minimize or avoid these pitfalls.

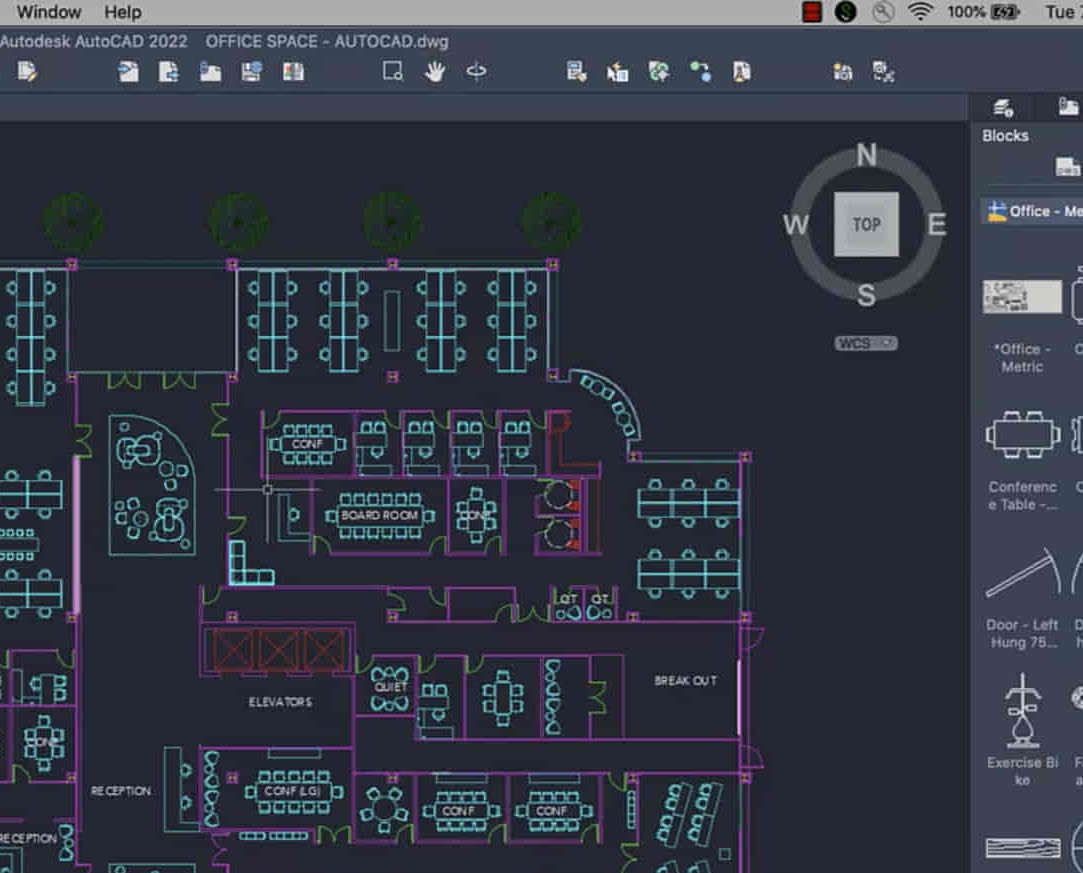
AutoCAD-Mac Introduction to Advanced Training Course
By ATL Autocad Training London
AutoCAD-Mac Introduction to Advanced Training Course This project-based course is tailored for AutoCAD Mac users, architecture and interior design students and professionals. Click here for more info: Website When Can I Book This Training Course? Personalized experience with 1-on-1 sessions designed to fit your unique needs. Available from Monday to Saturday, 9 am to 7 am Or Call to Book 02077202581. Duration of Training: 16 hours. Training Method: 1-on-1, providing the option for in-person sessions or live online training. Course Content Section 1: Introduction Course Overview Section 2: Basic Concepts Status Bar and The Units Drawing Commands Control Points - Vertex or Verteces Modifying Commands Snap Settings Drawing An Outline Section 3: Dimensions and Customization Adding Dimensions and Dimension Style Manager Importing Dimension Styles Customizing Shortcuts Section 4: Advanced Techniques Adding Walls Thickness with Offset Command Adding interior layout Cleaning Layout lines with Trim Section 5: Text and Styling Text Editing and Importing Text Styles Main File Formats in AutoCAD Section 6: Design Elements Creating Openings in the Floor Plan Adding Openings - Part 2 Adding Openings - Part 3 Drawing Doors & Windows Using Line Types & Linetype Scale Group and Ungroup Commands Using Blocks Using Blocks Library & Dynamic Blocks Section 7: Layers and Furnishing Layers - Part 2 Layers - Part 3 Furnishing Bedrooms & Bathrooms - Part 1 Adding Furniture, Fixtures, and Equipments | part 2 Adding Furniture, Fixtures, and Equipments | part 3 Drawing the Kitchen Drawing the Living Room Drawing Dining Room & Adding Casework Adding Steps and Railings Using Stretch Command Finishing Steps and patio areas Hatch command Hatch Customization Adding Plants & Finishing Floor Plan Section 8: Layout and Printing Paper Space & Page Setup Manager Working with Viewport & Using Print Command Scale & Using Multiple Viewports Locking Viewport Scale Drawing A Titleblock - Part 1 Drawing A Titleblock - Part 2 Copying the Titleblock Using Titleblock with Attributes Section 9: Roof Plan and Organization Drawing The Roof Plan Placing Roof Plan on Sheet Organizing Project Drawings & Using Layer Freeze AutoCAD Crashing And What To Do Section 10: Elevations Exterior elevations - Drawing the Outline Exterior elevations - Drawing the Openings Elevations - Detailing - Part 1 Elevations - Detailing - Part 2 Elevations - Repeating the workflow Elevations - Finishing 3rd Elevation Elevations - Drawing the final elevation Section 11: Sections Sections: Drawing Cut Lines & the Outline Sections: Placing 1st Section on Sheet Sections: Drawing Section #2 - Different Technique Sections: Adding Final Detail Section 12: Interior Elevations Interior Elevations: Drawing the Outline Interior Elevations: Placing on Sheet Interior Elevations: Using Block Clip Interior Elevations: Final Drawing Section 13: Conclusion Putting the Final Set Together Proficient AutoCAD Skills: Master essential tools for efficient drawing creation and manipulation. Accurate 2D Designs: Create precise and high-quality layouts with attention to detail. Effective Object Handling: Excel in selecting, moving, copying, and scaling objects. File Management: Organize drawings efficiently and understand different file formats. Precise Measurements: Utilize inquiry commands for accurate design analysis. Annotations and Hatching: Apply text, dimensions, and hatching to enhance drawings. Object Organization: Manage layers and object properties for organized designs. Reusable Content: Efficiently use blocks, tool palettes, and groups for productivity. Layout Optimization: Create layouts with viewports for optimal design presentation. Professional Output: Generate professional plots and PDF output for polished results. Enhanced Productivity: Explore AutoCAD toolsets and web/mobile apps for streamlined workflow. Course Overview: Learn versatile AutoCAD for Mac drawing techniques, applicable across all industries, enabling you to excel in the application. Our trainers incorporate exercises from various disciplines. Who Should Attend: Ideal for newcomers to AutoCAD for Mac, self-taught users seeking correct techniques, and those transitioning from other CAD tools. Requirements: A solid Mac OS understanding is essential, while prior CAD knowledge is not required. Pre-course preparation guidance is provided for new AutoCAD users. Highlights: Perfect for AutoCAD for Mac beginners. Gain skills for precise 2D layouts and designs. Versatile drawing techniques for all industries. Choose between in-class or live online training. Autodesk Certified Tutors: AutoCAD 1-2-1 courses. Hands-on learning with expert trainers. Lifetime post-course email support. Tailored on-request training available. Certificate: Digital certificate included. Tailored Mac Training: Excel in AutoCAD with specialized Mac training, leveraging its distinct features and interface for heightened efficiency. Comprehensive Skill Enhancement: Advance from fundamental to intermediate AutoCAD Mac proficiency, creating precise and professional 2D drawings. Industry-Relevant Expertise: Attain in-demand skills valued by employers in architecture, engineering, and design sectors. Hands-On Project Exposure: Immerse yourself in practical exercises mirroring real-world design scenarios, fostering practical competence. Lesson Recordings for Review: Access recorded lessons for reinforcement and deeper AutoCAD Mac comprehension. Ongoing Email Support: Benefit from lifetime email support, ensuring assistance beyond course completion."
Women in Leadership Program
By Netwomen
Give women managers and employees the skills they need to climb the corporate ladder within your organisation. Optimised for tailored audiences Built for groups of 20+ Led by experienced and certified professionals Specialised to address issues around inclusivity and equity in all industries Program Details For Upper Management Teams: Strategies for Upward Mobility Module 1 – Theories and Realities: Female Leadership 15 Principles Module 2 – Communicating Clearly Module 3 – Management Revelations: Relationship vs. Task Management Module 4 – Set Your Path: Empowerment Techniques For Middle Management & Staff Teams Module 1 – What the Data Tells Us Module 2 – What Are Your Leadership Skills?: Personal Skill Inventory Module 3 – What Does Good Company Culture Look Like? Module 4 – Taking On Your Performance Investment Fee: £50,000 25 participants max per 12-week cohort TRAINING FORMAT : 12 - Week Cohorts Delivered in 1-hour sessions Virtually Facilitated Sessions Women in Leadership Program One Pager

REVIT ADVANCED ONE-TO-ONE COURSE
By Real Animation Works
Vray face to face training customised and bespoke.



