- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
751 Link courses in Cardiff delivered Live Online
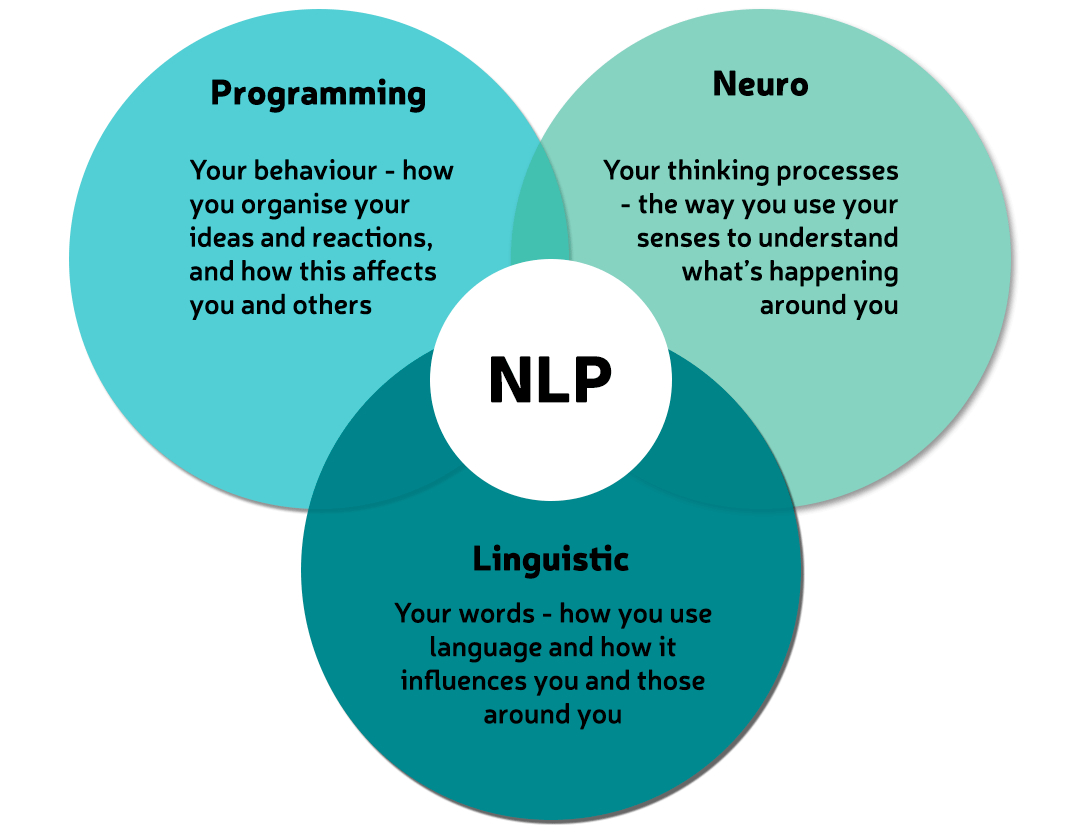
What is NLP?
By Proactive NLP Ltd
What is NLP? Join proactivenlp.com on this virtual workshop and find out how NLP can start changing your life by saying goodbye to the negatives and welcoming in all the positives you want.
Adobe After Effects Basic to Fundamentals Training Course (Live Online Only)
By London Design Training Courses
Training duration: 10 hrs Course info Method: 1-2-1, Personalized attention, Tailored content, Flexible pace, Individual support. Schedule: Personalized training experience with our flexible 1-2-1 sessions. Tailor your own schedule by pre-booking a convenient hour of your choice, available from Monday to Saturday between 9 am and 7 pm. Unlock visual effects and motion graphics skills with our 3ds Max and After Effects Course. Certified tutors guide you through seamless integration of 3D models and animations. Live online format, recorded lessons, and lifetime email support provided. Enroll now and explore exciting career opportunities in visual effects, animation, and motion graphics. Course Outline: Adobe After Effects Fundamentals. Getting Started Overview of the workspace and interface. Importing and organizing assets for seamless workflow. Understanding projects and compositions for effective project management. Working with layers to create complex compositions. Applying Effects (FX) Introduction to applying effects in After Effects. Fixed and applied FX for enhancing visual appeal. Understanding animation principles for smooth motion. Modifying motion paths to control animation trajectories. Mastering keyframes for precise animation control. Exploring the basics of the graph editor for advanced animation adjustments. Text Animation Creating and animating text in After Effects. Enhancing text with layer styles for engaging visuals. Utilizing animation options for dynamic text effects. Implementing motion blur for realistic motion. Shape Layers Introduction to shape layers and their versatility. Creating shapes from Illustrator files for flexible designs. Working with paths and their applications in animations. Utilizing animation options to breathe life into shapes. Exporting and Finalizing Projects Effective project management and organization techniques. Understanding export options for optimal rendering. Exporting projects through Media Encoder for various platforms. Utilizing dynamic link to Premiere Pro for seamless integration. Masks and Chroma-keying Creating and animating masks for selective visual effects. Utilizing tracking masks for precise adjustments. Limiting effects to specific areas using track mattes and property links. Mastering green-screen chroma-keying with Keylight 1.2. Additional Effects Exploring additional effects such as Warp Stabilizer, Camera Tracker, Motion Tracker, and Puppet Pin tool. Implementing these effects to enhance motion graphics and visual effects. Creative applications and hands-on practice with each effect. By the end of this fast-paced and practical Adobe After Effects training course, participants will achieve the following learning outcomes: Key Skills in After Effects: Gain proficiency in essential After Effects skills to transform video projects effectively. Professional Techniques: Master a range of professional techniques and processes invaluable for film makers, motion designers, and animators. Project Planning: Learn how to plan projects, prepare assets, and set compositions for seamless video production. Animation and Effects: Acquire the ability to apply and animate various transformations and effects on images, videos, and text elements. Masking and Compositing: Develop skills in masking and compositing to create visually stunning and cohesive compositions. Rendering Videos: Understand the video rendering process to produce high-quality final outputs.

Goldwork embroidery, Exquisite rose: Live Zoom class
By Ecole Saint Clare
Learn goldwork with this intricate rose

TRAINING FOR FILM & GAME DESIGNERS One to One Online or Face to Face
By Real Animation Works
Film and VFX face to face training customised and bespoke. One to One Online or Face to Face

InDesign Evening Training
By London Design Training Courses
Why Choose InDesign Evening Training Course? Course Link. If you aim to enhance your design abilities, acquire proficiency in a new software, or pursue a career in graphic design, an InDesign course is highly beneficial. Tailored for individuals with foundational knowledge of Adobe InDesign, this training is designed to further develop your existing skills. Duration: 10 hrs Method: 1-on-1, Personalized attention Schedule: Tailor your own hours of your choice, available from Mon to Sat between 9 am and 7 pm InDesign Evening Course Outline (10 hours) Introduction Getting Started with Adobe InDesign CC Advanced Course Adjusting Workspace for Maximum Efficiency Customizing Default Font Size for New Documents Utilizing Special Features for Typekit & Open Type Fonts Exploring Sources for Free Fonts in InDesign Mastering Fonts in Adobe InDesign CC Identifying Fonts with Font Guess Selecting Beautiful Font Pairings Incorporating Free Icons from Adobe Market Using the Color Theme Tool Understanding Colour Modes Importing and Setting Default Colors Finding Great Colors with Adobe Color Managing Appearance of Black & Proofing Colors Creating Multiple Shapes with Gridify Live Distribute Drawing Arrows in InDesign CC Designing Complex Flowers in InDesign CC Utilizing Auto Size for Auto-Expanding Text Boxes Exploring Placeholder Text Alternatives Adding Paragraph Borders & Shading Understanding Paragraph vs Single Line Composer Making Paragraphs Span 2 Columns Mastering Justification & Hyphenation Options Aligning Optical Margins Harnessing the Power of Keep Options Working with Advanced Anchored Objects Using Conditional Text Creating Pie Charts & Bar Graphs Pros & Cons of Interactive Types Creating Interactive PDFs Adding Interactive Page Transitions Adding Navigation to Interactive PDFs Understanding Publish Online in InDesign CC Publishing Adobe InDesign Documents Online Adding Video to InDesign Documents Creating Button-Triggered Animations Making Multi-State Objects Incorporating Adobe Animate CC to InDesign Files Adding Maps & Calendars to Interactive Documents Generating QR Codes in InDesign CC Exploring Essential Keyboard Shortcuts Automatically Placing Text on Multiple Pages Creating Cross References & Index Adding Document Name Automatically with Text Variables Utilizing Adobe InDesign CC Book Feature Changing Preferences for Advanced Users Speeding Up Workflow for Advanced Users Using Character Styles Advanced Paragraph Styles Mapping Word Styles with InDesign Styles Creating Nested Styles & Grep Styles Using Next Style Mastering Object Styles Best Practices for Working Across Multiple Documents Utilizing Adobe Stock with InDesign CC Cropping Images Inside Text Making InDesign Layouts with Adobe Comp CC Advanced Use of CC Libraries Integrating Photoshop & Illustrator in InDesign CC Creating PDF Forms in InDesign CC Advanced Use of the Pages Panel Placing InDesign Documents Inside Each Other Installing and Using Scripts in InDesign CC Improving InDesign Performance Advanced Exporting & Printing Tricks Bonus: Software Updates Adobe InDesign https://adobe.com › indesign › get-started Installing for the first time or on a new computer? Click Get InDesign below to begin downloading. Follow the onscreen instructions to sign-in and install.

PRIVATE - May 2025 Cohort ONLY - Group Supervision
By EMDR Consultancy
PRIVATE - FOR CURRENT TRAINEES ONLY - DO NOT BOOK IF YOU ARE NOT PART OF THIS COHORT Please join one of the supervision groups listed. The Zoom link for your group will be sent prior to the session date.

Lumion 3d Realtime Rendering Training
By London Design Training Courses
Why Choose Lumion 3d Realtime Rendering Training Course? Course Link Our Lumion Course is best for materials, lighting, and animation skills. Learn high-quality rendering using Lumion's asset library. In-person or live online sessions with lifetime access to recordings and email support. Unleash Lumion's potential for immersive architectural visualizations. Duration: 10 hrs Method: 1-on-1, Personalized attention Schedule: Tailor your own hours of your choice, available from Mon to Sat between 9 am and 7 pm What is Lumion? Lumion is specialized 3D rendering software designed for architects and designers. With Lumion, you can quickly bring your 3D design models to life, add materials, furnish interiors and exteriors, and showcase the impact of lighting and shadows without the need for specialized training. Objectives of the Course The course aims to teach you how to start Lumion projects, add environments, cameras, illuminations, populate scenes with various elements, create terrains, and produce animations. Lumion 3D Course Outline Module 1: Introduction to Lumion 3D Discovering Lumion 3D's capabilities and interface navigation. Learning shortcut keys for efficient workflow. Customizing settings for optimal performance. Module 2: 3D Models and Materials Importing 3D models in various formats. Applying and tweaking materials. Creating procedural materials and glass effects. Troubleshooting common issues. Module 3: Creating a Project in Lumion Building scenes and sculpting terrain. Enhancing realism with alpha and height maps. Module 4: 3D World Managing multiple 3D objects and their properties. Implementing grass and scattering elements. Module 5: Lighting in Lumion 3D Utilizing weather settings for dynamic scenes. Understanding Lumion lights and interior/exterior illumination. Creating 3D reflections and spotlights. Module 6: Realistic Visualizations Incorporating special effects like fire, smoke, and fog. Achieving realism with camera effects and shadows. Rendering still images and animations. Module 7: NPR Visualizations Creating non-photorealistic visualizations with artistic effects. Implementing unique styles for enhanced visuals. Module 8: Artistic Effects in Lumion 3D Exploring conceptual visualizations with painting and sketch effects. Creating cartoon effects and understanding perspectives. Module 9: Animation in Lumion 3D Timing and working with cameras for dynamic shots. Composing animation clips and adding effects. Utilizing layers and control objects for precise control. Module 10: Advanced Features Import and output formats in Lumion. Expanding assets with the 3D model library. Adding animated characters and sound effects. Utilizing the advanced material library. Controlling environment and weather for dynamic scenes. Scene management and movie editing within Lumion 3D. Lumion for Students | Unleash Your Creativity https://lumion.com› product › students Unlock the full potential of your designs with Lumion for students. Request your free 1-year Student license now and bring your visions to life!

Photoshop Basics to Essentials Training
By London Design Training Courses
Why Choose Photoshop Basics to Essentials Training Course? Course Link Mastering Photoshop is crucial for securing positions in creative fields such as graphic design, digital design, and user interface (UI) design. Acquiring this skill serves as a foundation to excel in various design programs essential for creative professionals. Duration: 16 hrs. Method: 1-on-1, Personalized attention. Schedule: Tailor your own hours of your choice, available from Monday to Saturday between 9 am and 7 pm. Photoshop Course: Total 16 hrs Module 1: Keyboard and Toolbar Shortcuts Customize toolbars and keyboard shortcuts for efficient workflow Learn essential keyboard shortcuts for faster navigation Module 2: Advanced Layer Management Filter, search, and color code layers for better organization Group and merge layers to streamline your design process Explore Blending Modes for creative effects Module 3: Blending Modes Understand Blending Modes and their usage within layers and effects Apply Blending Modes to enhance your designs Module 4: Layer Comps Discover Layer Comps and their benefits in managing complex designs Create, edit, and update Layer Comps for different design versions Export Layer Comps to PSD, PDF, and JPEG formats Module 5: Drawing Vectors Work with Vector images using shapes and the Pen Tool Use the Direct Selection Tool for precise editing Apply colors and create Clipping Masks with vectors Module 6: Advanced Type Techniques Convert text into Shapes and utilize font style changes with the Pen Tool Use text as a Clipping Mask and create text Outlines Design 3D text for impactful typography Module 7: Advanced Adjustment Layers Master advanced adjustments like Curves, Levels, and Black and White Utilize Selective Color and Gradient Maps for creative color control Module 8: Advanced Selection Techniques Use Smart Radius and Select and Mask for precise selections Learn to select complex objects like hair using Color Range and the Pen Tool Save and manage selections using the Path Panel Module 9: Colorizing Black and White Images Module 10: Displacement Maps Module 11: Advanced Filters Create Trees, Frames, Clouds, and Fire with filters Use Polarized, Wave, and Extrusion for artistic effects like "Japanese Sun" Explore Vanishing Point Filter, Camera RAW, Blur for depth of field, and Filter Gallery Combine 3D text with Vanishing Point for stunning designs Use Liquify for image manipulation Module 12: Introduction to Actions Automate tasks using Photoshop's preset Actions Create your own Actions to save time and effort Module 13: Creating an Animated GIF Learn frame by frame animation Utilize the Timeline to create engaging animated GIFs Learning Outcomes: Master advanced selection techniques, including the Path and Pen Tool, for precise editing. Gain proficiency in advanced layer management and utilize Layer Comps for efficient design organization. Enhance your designs with a deeper understanding and application of Blending Modes. Create visually appealing 3D text and text outlines to add depth and impact to your artwork. Explore advanced Filters like Displacement Maps, Blurs, and Distortion for creative effects. Automate tasks with actions and batch processing, streamlining your workflow. Craft engaging animated GIFs to add dynamic elements to your designs. Skillfully set project requirements by identifying the purpose, target audience, copyright considerations, and project management tasks for successful project execution.

Vectorworks Basics to Intermediate Training
By London Design Training Courses
Why learn Vectorworks Basics to Intermediate Training Course? Course Link Vectorworks skills with our course! Led by certified expert tutors, this course takes you from basics to intermediate level, enabling you to create plans and sections. The course will cover 2D and 3D modeling, rendering, and visualization. Duration: 16 hrs. Method: 1-on-1, Personalized attention. Schedule: Tailor your own schedule by pre-booking a convenient hour of your choice, available from Mon to Sat between 9 am and 7 pm. At London Design Training Course, we offer a range of Vectorworks training options to meet your specific needs and those of your business. Explore the links below for detailed information about the various training types and their content. On-Site Training: London Design Training Course comes to your location, eliminating the need for you to travel. This approach allows us to fully understand your business culture and requirements. Training can be conducted in your studio or conference room, with scheduling flexibility tailored to your preferences. In-House Training: Our studio in London SW96DE, hosts In-House Vectorworks training for both individuals and groups. During the sessions, we provide the necessary software and hardware to ensure a seamless learning experience. Vectorworks Basic to Intermediate Course Course Duration: 16 hours The Vectorworks Basic to Intermediate Course is tailored for individuals with basic Vectorworks knowledge, aiming to master advanced 2D and 3D techniques, including modeling and rendering. Participants will customize Vectorworks to their needs, create custom tools, and automate tasks with scripting. I. Review of Basic Concepts (1 hour) - Vectorworks interface and navigation - Creating and editing 2D and 3D geometry - Working with layers and classes - Utilizing views and viewports II. Advanced 2D Drawing Techniques (2 hours) - Creating complex geometry using advanced drawing tools - Editing and modifying intricate geometry - Customizing line types and hatches - Utilizing advanced annotation tools III. Advanced 3D Modeling (3 hours) - Creating 3D forms and custom 3D objects - Exploring advanced 3D tools such as Solid Modeling - Converting 2D plans into 3D models IV. Visualization and Rendering (3 hours) - Setting up cameras and lights for visualization purposes - Utilizing the Renderworks engine for rendering - Enhancing visuals with the visualization palette - Creating and editing textures and materials V. Customizing Vectorworks (3 hours) - Personalizing the interface to suit specific preferences - Creating custom tools and automating tasks using the scripting language - Developing custom object styles and resources - Creating custom plug-ins and scripts VI. Collaboration and Sharing (2 hours) - Importing and exporting data from other software - Collaborating with others on the same project - Utilizing cloud-based collaboration tools VII. Conclusion and Next Steps (1 hour) - Review of course content and key skills learned - Tips for further learning and available resources - Q&A and feedback session Free 30-day, BIM & CAD Software Trial Request | Vectorworks https://www.vectorworks.net/trial Vectorworks Trial Version Request. Please fill out the following form. We will provide you with an evaluation serial number to activate your trial copy. Learning Outcomes of the Vectorworks Basics to Intermediate Training Course: Proficiency in Vectorworks interface, tools, and navigation. Master 2D drafting and 3D modeling skills. Efficiently manage workflows using layers, classes, and views. Spotlighting techniques for lighting design and stage productions. Advanced object manipulation with solid modeling and Boolean operations. Utilize the symbol library for enhanced productivity. Create professional presentation drawings using viewports and annotations. Integrate with other software and CAD/BIM workflows. Apply skills to real-world projects for practical application. Upon completing the course, participants will have essential skills to effectively use Vectorworks, advancing their proficiency to an intermediate level.

Adobe InDesign Advanced Training
By London Design Training Courses
Why Learn Adobe InDesign Advanced Training Course? Master Adobe InDesign for efficient page layouts with our advanced course. Learn document setup, text formatting, and special effects. Suitable for beginners and advanced users. London Design Training Course provides top InDesign course with Adobe Certified Instructors. Course Link Duration: 10 hrs Method: 1-on-1, Personalized attention Schedule: Tailor your own schedule by pre-booking hours of your choice, available from Mon to Sat between 9 am and 7 pm Flexible Learning Options: Choose between in-class training at our London center or participate online. Both options provide hands-on, practical learning with step-by-step demonstrations and ample opportunities for questions. Introduction to InDesign: Exploring InDesign Basics Customizing Preferences and Workspace Navigating Panels and Windows Setting Up Toolbar and Properties Panel Document Management: New Document, Pages, and Order Quick Navigation Techniques with Shortcuts Smart Layout: Organizing Layouts with Guides and Grids Understanding Bleed, Slug, and Margins Utilizing Smart Guides for Precision Typography: Mastering the Type Tool Adding Text to Pages and Using Placeholder Text Text Formatting with Character and Paragraph Controls Editing Text Frames and Justifying Text Multi-column Setup and Styling with Character/Paragraph Styles Working with Bullet Points and Numbering Working with Images: Creating Frames and Placing Images Content Fitting Options: Proportional Fit, Content-Aware Fit, Auto-Fit Manipulating Frame Properties: Fill, Stroke, Effects Utilizing Object Styles for Consistent Frames Advanced Techniques: Image Frame Grids, Merging Frames, Text Wrap Options Understanding Image Formats and Resolution Tabs and Alignment: Mastering Tab Palette and Alignment Options Adding Leaders for Enhanced Formatting Color Theory and Editing: Basics of Color Theory and Color Modes Creating Color Themes with the Color Theme Tool Swatches, Color Libraries, and Gradients Editing Gradient Fills and Colors Advanced Interactive Actions: Adding Animation Effects with Animation Panel Fine-tuning Animations with Timing Panel Creating Complex Object States and Action Buttons Adding and Testing Hyperlinks, Page Transitions Parent Page Basics: Understanding Parent Pages Page Numbering, Order, Headers, and Footers Inserting Text Variables for Dynamic Content Advanced Object Styles and Effects: Opacity Control and Blending Modes Black and White Conversion, Color Blending Modes Adding Dimension with Bevel and Emboss Effects Advanced Text Frame Options: Auto-sizing Text Frames and Balancing Column Height Inset Spacing and Fill Colors for Text Boxes Hot Corner Resizing Shortcuts and Anchor Objects Footnotes: Purpose and Usage of Footnotes Adding, Editing Footnotes with Footnote Options By the end of this Adobe InDesign training, participants will: Understand InDesign basics and its interface. Create effective page layouts with text formatting and image placement. Work with layers, apply special effects, and manage tables. Ensure error-free and print-ready documents through preflighting. Receive a practical training guide and an e-certificate upon completion.
