- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2874 Learning courses in Cardiff delivered Live Online
SOLUTION CIRCLES
By Inclusive Solutions
A Solution Circle is a 30 minute creative Problem Solving Process for getting unstuck…Ideal for busy people! lt was designed by Marsha Forest & Jack Pearpoint. This is a short and powerful tool. It is effective in getting “unstuck” from a problem in life or work. Solution Circles are tools of “community capacity”. It assumes and demonstrates that nearby people – in any community or work place have the capacity to help – if asked. It requires a person to ASK – not an easy thing in our culture of privacy and “do it alone”. This tool puts all the values we espouse into practice and demonstrates that TOGETHER WE’RE BETTER. Course Category Problem Solving Description A Solution Circle is a 30 minute creative Problem Solving Process for getting unstuck…Ideal for busy people! lt was designed by Marsha Forest & Jack Pearpoint. This is a short and powerful tool. It is effective in getting “unstuck” from a problem in life or work. Solution Circles are tools of “community capacity”. It assumes and demonstrates that nearby people – in any community or work place have the capacity to help – if asked. It requires a person to ASK – not an easy thing in our culture of privacy and “do it alone”. This tool puts all the values we espouse into practice and demonstrates that TOGETHER WE’RE BETTER. In this training you will learn how to set up and facilitate Solution Circles Learning Objectives For participants to learn how to facilitate a Solution Circle For participants to understand the underlying rationale and ethos of this way of working For participants to learn the power of team work and problem solving when including challenging individuals Who Is It For? Team Around the Child agencies Parents and Professional working together Families Multi Agency Teams Social workers CAMHS teams Year Managers Primary and secondary staff teams Early Years and School based Practitioners Heads and Deputies SENDCOs Advanced Skills Teachers Primary and secondary teachers Local Authority Support Services Course Content This can be introduced in a twilight, half day or even a full day workshop with individualised coaching. We will provide background context for this approach and will directly model the process with real live issues facing participants. So bring your most challenging concerns to this training. The course answers the questions: What to when you are stuck Can we find an alternative to permanent exclusion or special unit or school placement? Struggling with a child for whom praise is ineffective? Feeling isolated in your responses to a child’s needs? Worried about where your instinctive reactions are leading you? Cannot seem to get any consensus view of a young person’s behaviour/needs amongst all the family and professionals involved – is everyone pulling in different directions? We will cover: Setting the tone Background and detailed teaching of process Inclusion values underpinning this work Graphic and process facilitation skills Processes modelled and opportunities to try process out with coaching Practical setting up of insights and solutions circles Lessons learned

PARENT SOLUTIONS CIRCLE
By Inclusive Solutions
In this course we explore how we have attempted to build inclusive circles of support around individuals and contrast this with a radical approach to problem solving with parents – the Parent Solutions Circle. Parent Solutions is a brand new approach to problem solving with parents based on our live group work in schools. A focus on challenging behaviour brings interest, energy and commitment. Course Category Inclusion Peer Support Parents and Carers Behaviour and relationships Description In this course we explore how we have attempted to build inclusive circles of support around individuals and contrast this with a radical approach to problem solving with parents – the Parent Solutions Circle Parent Solutions is a brand new approach to problem solving with parents based on our live group work in schools. A focus on challenging behaviour brings interest, energy and commitment. Essentially the approach involves gathering a group of parents and carers together who recognise how challenging their own children are and would like some help to figure out how to be with them or how to manage an aspect of their behaviour. The process is facilitated but majors on the parents offering each other their wisdom and ideas. The directness that only peers can provide to each other makes the work both powerful and effective. Mobilising the wisdom and experiences of parents in a safe way is a delicate art. In this training we will explore how this can best be done. Parents who have been on all the courses and had all the professional advice in world love this way of working because they get to offer each other their experience, ideas and wisdom. The approach is capacity focused, person centred approach to working with parents rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for parents. We work with rather than do things to a group of parents. This training can be modelled with a group of parents or can be demonstrated with a group of professionals. We prefer mixed groups. Learning Objectives For participants to learn how to set up a Parent Solutions Circle For participants to understand the underlying rationale and ethos of this way of working To learn the facilitation process and stages of the Circle process Who Is It For? Anyone interested in working with parents and carers in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. School leaders and managers Social Care teams Community organisers Psychologists Course Content True parent empowerment Facilitating groups Problem solving process Handling group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Creating natural circles of support that can provide peer support and mutual problem solving If you liked this course you may well like: Creating Community Circles

WORKING WITH PARENTS AND CARERS
By Inclusive Solutions
In this practical and engaging workshop there is input on building an effective team around a child, problem solving as a team, improving communication and handling conflict. Communication with parents, problem solving and collaborating is explored. Empathy with parents who are ‘labelled’ is encouraged. Course Category Parents and Carers Description In this practical and engaging workshop there is input on building an effective team around a child, problem solving as a team, improving communication and handling conflict. Communication with parents, problem solving and collaborating is explored. Empathy with parents who are ‘labelled’ is encouraged. A key aspect of this day is ‘reframing’ how we think about the most difficult, hard to work with parents who attract many labels. Participants soon discover that they are more similar than they realise to those labelled ‘others’. The day gives those present opportunities to reflect on their attitudes and practice in relation to parents who are different. Practical ideas for joint problem solving and active engagement are fully explored. Testimonials “Made me more aware of how to approach parents and carers” “It (the conference) couldn’t have been improved. All the speakers were good” “I’ll have a more positive approach to welcoming people” “It will encourage us as practitioners to listen and think a little more. Learning Objectives Increased confidence in working with parents Access to a wider range of practical and thoughtful strategies when collaborating with parents and carers Deeper understanding of core values surrounding inclusion of disabled children in collaboration with parents and carers Opportunity to reflect on professional attitudes and behaviour towards parents with a focus on labelling and stigmatisation New skills and processes to make joint work successful Who Is It For ? Early Years and School based Practitioners Children Centre Staff Heads and Deputies SENCOs Advanced Skills Teachers Primary and secondary teachers Local Authority Support Services Social Workers Health Workers Course Content The course answers the questions: Why is this parent impossible to work with? Where do I begin to communicate with some parents? How can I collaborate with parents and carers to include high profile children or young people? Best delivered over the course of a full day we will cover: The importance of WELCOME Labelling and reframing: Setting the tone: Reframing language to describe parents Providing parents with insights about children’s behaviour using stories Circle of Courage as applied to parents Circles of Support The Intentional Building of Relationships Not doing it alone – The Importance of Teams in developing inclusive practice Problem solving: Circles of Adults/Solution Circles Community Guides If you liked this you may like: COMMUNITY CIRCLES
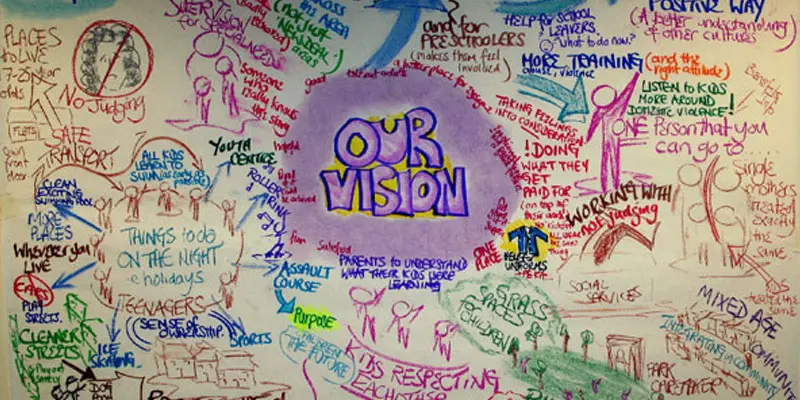
PERSON CENTRED THINKING – EXTREME
By Inclusive Solutions
The Extreme Person Centred Thinking Tools are a set of tools to support dreams, build relationships and connections and promote capacity thinking. The aim of the extreme person centred thinking tools training is not to teach people how to facilitate plans, instead it is about sharing tools that can be used to listen and reflect and creatively involve people in planning their own lives. Online Course now available via Teachable Platform – Person Centred Mindset Learn at your own pace… lots of text and video support Course Category Person Centred Planning Description The Extreme Person Centred Thinking Tools are a set of tools to support dreams, build relationships and connections and promote capacity thinking. The aim of the extreme person centred thinking tools training is not to teach people how to facilitate plans, instead it is about sharing tools that can be used to listen and reflect and creatively involve people in planning their own lives. Many of these tools have been taken from MAPS and PATH, and parts also build on the person centred thinking tools. Testimonials Be the first… Learning Objectives This course will provide participants with an understanding of how to use a range of extreme person centred thinking tools to; Use graphics to facilitate creative conversations Learn from people’s stories and histories Listen to and facilitate dreams and nightmares Think about what is positive and possible Connect people with their communities Facilitate inclusion Who Is It For? Person Centred Planning Facilitators Support Workers / Day Centre Officers / Residential Workers Personal Assistants / Teaching Assistants Families Self Advocates Social Workers CAMHS teams Primary and secondary staff teams SENCOs Local Authority Support Services Course Content The course will introduce participants to a range of tools focused around supporting relationships, realising dreams, connecting people with their communities and capacity thinking. Participants will be coached in using the tools and given the opportunity to practice the tools and their graphic facilitation skills in a safe environment. The course will answer the following questions: How can we use ideas from MAP and PATH in our day to day work? How can I use graphics to facilitate conversations? How can we learn more about the people we support? How can we start to think about connecting people to their communities? If you liked this course you may well like: PERSON CENTRED PLANNING USING PATH AND MAPS
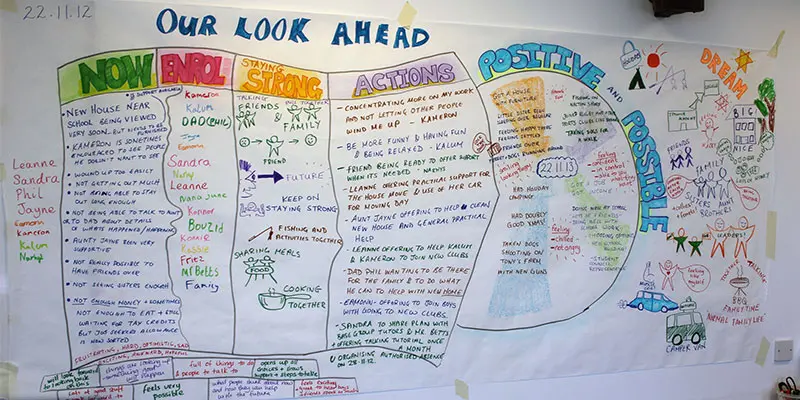
LNG Terminal Operations & Safety
By EnergyEdge - Training for a Sustainable Energy Future
Elevate your expertise in LNG terminal operations safety through our classroom training course. Energyedge provides industry-leading expertise and guidance.

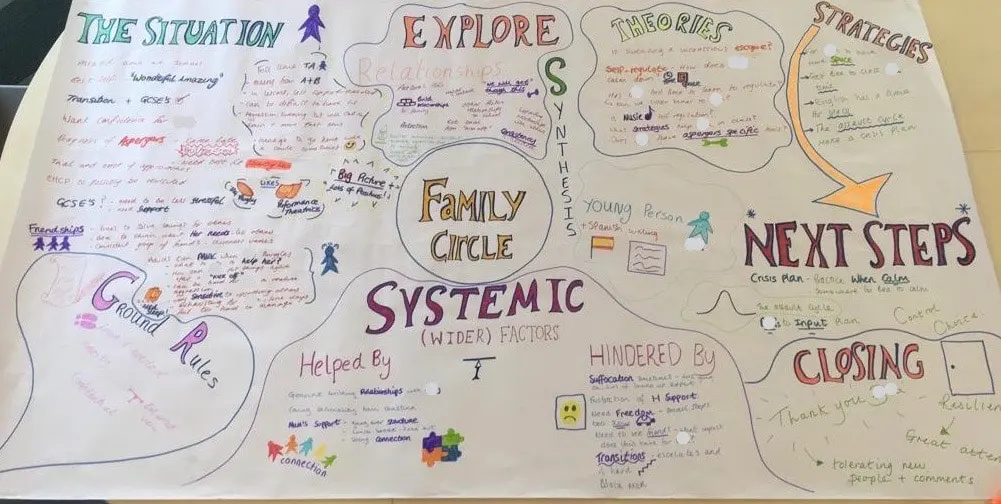
FAMILY CIRCLES
By Inclusive Solutions
Click to read more about this training, in which we demonstrate a live problem solving approach which is based on the active participation of family members. Course Category Inclusion Parents and Carers Behaviour and relationships Problem Solving Description In this training we demonstrate a live problem solving approach which is based on the active participation of family members. ‘Family Circles’ is an evolving new approach to problem solving with families and is based on our years of family work and the development and use of the Circle of Adults process. Inspired by our own Parent Solutions work and the Circle of Adults process as well as Family Group Conferencing and other Restorative Interventions we bring you Family Circles. Essentially the approach involves gathering a family together for a process that is facilitated but majors on the family members offering each other their wisdom and ideas. The approach is capacity focused, person centred approach to working with families rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for or doing things to families. This training can be modelled with a group of professionals or better still with a family. In our work with families we develop the importance of naming stories or theories and seeking linkages and synthesis between what is found out and explored about the family situation and its history. We like participants to sit with the uncertainty, to reflect on the question ‘why’ but without judgement of each other. Deeper reflections may span a whole range of perspectives from ‘within person’ considerations, to situational or systemic possibilities. Health or emotional issues can be reflected on alongside organisational or transactional aspects of what is going on for the family. The better the shared understanding the better the strategy or actions which emerge from these meetings. Quality hypotheses with a close fit to reality lead to more effective implementation in the real world. We encourage ‘loose’ thinking, a search for connections, deeper listening, an ‘open mind’, speculation and exploration without moral judgements. From this stance self-reflection as well as reflection on the situation can produce remarkable insights. The quality of theories or new stories generated is directly influenced by family members’ experiences and the models of learning, behaviour and emotion, systems, educational development, change and so on that they have been exposed to. Learning Objectives To provide opportunities for: Shared problem solving in a safe exploratory climate in which the family will find its own solutions. Individuals to reflect on their own actions and strategies An exploration of whole-family processes and their impact Emotional support and shared understandings of issues at a child, parent, family, school and community level. Feed back to each other on issues, ideas and strategies that are agreed to be worth sharing with them. Who Is It For? Anyone interested in working with families in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. Social Care teams School staff Community organisers Educational Psychologists Course Content True family empowerment Deepening shared stories and understandings Facilitating groups Problem solving process Handling family group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Process: Family members are welcomed: Introductions are carried out, ground rules and aims clarified whilst coffee is drunk. A recap from the last session is carried out: To follow up developments and reflections after the last meeting. One issue is selected for the main focus Issue presentation: The family member who raised the concern is asked questions to tell the ‘story’ of the issue or problem. Additional questions/information from the group about the problem are gathered: Ground rules may need to be observed carefully here. Individual participants need to be kept focused and prevented from leaping to premature conclusions or to making ‘helpful’ suggestions about strategy. Relationship aspects to the problem are explored. Metaphors and analogies are invited. How would a fly on the wall see your relationship? If you were alone together on a desert island, what would it be like? Impact of previous relationships/spillage from one relationship to another are explored. Eg what situation they are reminded of? For instance, does this situation remind you of any of those angry but helpless feelings you had with your other son when he was an adolescent? This provides opportunities to reflect on how emotions rub off on other people. The parent feels really frustrated, and on reflection we can see that so does the child System/Organisation factors (Family system/school and community systems and so on): What aspects help or hinder the problem? For instance, does the pastoral system of the local school provide space, or time and skilled personnel able to counsel this young person and work actively with their parents? Synthesis. At this stage the Graphic facilitator summarises what they have heard. They then go on to describe linkages and patterns in what they have heard. This can be very powerful. The person doing the graphic work has been able to listen throughout the presentation process and will have been struck by strong messages, emotions and images as they have arisen. The story and meaning of what is happening in the situation may become a little clearer at this point. Typical links may be ‘mirrored emotions’ strong themes such as loss and separation issues, or repeated processes such as actions triggering rejection. This step provides an excellent grounding for the next process of deepening understanding. What alternative strategies/interventions are open to be used? Brainstormed and recorded. ’Either/ors’ need to be avoided at this time also. This needs to be a shared session in which the family member who is presenting the concern contributes as much as anyone. Care is needed to ensure that this person is not overloaded with other people’s strategies. The final selection of strategy or strategies from the brainstormed list is the problem presenter’s choice. Strategies might include: a special time for the young person, a meeting with the child’s parents to explore how she is being managed at home and to share tactics, a home-school diary, counselling, or an agreed action plan that all are aware of, agreed sanctions and rewards and so forth. Strategies may productively involve processes of restitution and restoration, when ‘sorry’ is not enough. Making it right, rather than punishments or rewards, may then becomes the focus. First Steps. The problem presenter is finally asked to agree one or two first steps which they can carry out over the next 3-7 days. It can help to assign a ‘coach’ who will check in with them to ensure they have carried out the action they have named. This is a time to be very specific. Steps should be small and achievable. The person is just ‘making a start’. A phone call, or making an agreement with a key other person not present at the meeting would be ideal examples. Final reflections. Sometimes referred to as a ‘round of words’ help with closure for all involved. Reflections are on the process not the problem. In large families this is best done standing in a circle. In smaller groups all can remain sitting. Passing around a ‘listening stick’ or something similar such as a stone or light heighten the significance of the process ending and improve listening. Finally the problem presenter is handed the ‘Graphic’ this is their record of the meeting and can be rolled and presented ceremoniously by the facilitators for maximum effect! If you liked this course you may well like: Parent Solutions
RACISM – ACKNOWLEDGING AND UNDERSTANDING
By Inclusive Solutions
In this course we deepen participants understanding of systemic racism and the spectrum of privilege. It challenges the participants to examine their behaviours and take close looks at some of the views they have held since a very young age, e.g. this area is a “bad” area, because it has a high proportion of black/brown people living in it, or that young black men in tracksuits are “thugs”. We think about where these messages come from and how people are indoctrinated by the media. Course Category Inclusion Team Building Leadership Emotional needs Description In this course we deepen participants understanding of systemic racism and the spectrum of privilege. It challenges the participants to examine their behaviours and take close looks at some of the views they have held since a very young age, e.g. this area is a “bad” area, because it has a high proportion of black/brown people living in it, or that young black men in tracksuits are “thugs”. We think about where these messages come from and how people are indoctrinated by the media. We explore the reasons why white people are so defensive when it comes to talking about race. We discuss having racial biases and the implications of them, such as unconsciously insulting people around us in the workplace. When we become aware of how our behaviours can affect people, we then look for solutions. The course is designed for groups of professionals to come together as a team to try and take responsibility for the racism that goes on in their workplace – empowering the leadership to have difficult conversations with team members and create a paradigm shift across the entire organisation. Please come with an open mind, and you might be surprised at what you find out. We are striving for a world where racism is an open conversation and not a topic that we shy away from. Testimonials “That was a really insightful session and thought provoking. I would love to attend more sessions on racism. Thank you for the engaging questions and delivery” “Lots of things to reflect on!” Learning Objectives Participants will: Confront their own racism and unconscious biases Become aware of the ways they treat people differently based on race Think about practical changes they can make in their workplaces Who Is It For? Leadership teams seeking guidance and reflection Educators who want to get it right People who have had not had much contact with people outside their own race People who believe they are “not racist” Course Content Background – brief history of systemic racism Racism as a binary – the problem with thinking only “bad” people can be racist Trust – how do we feel around people we don’t trust? Difference – how do we act when we feel different? What do Good Manners look like around people of different cultures? What does Good Allyship look like in the workplace? Why don’t we talk about race? What does your race mean to you? Examining our privilege – activity Interracial friendship video Visioning – what does the ideal workplace look like? Setting Actions – what achievable actions can we set to bring us closer to our dream future?

Dashboard design
By Fire Plus Algebra
Data dashboards provide key information to stakeholders so that they can make informed decisions. While there are plenty of software solutions for building these essential data products, there is much less guidance on how to design dashboards to meet the diverse needs of users. This course is for anyone who is building or implementing dashboards, and wants to know more about design principles and best practice. You could be using business intelligence software (such as Power BI or Tableau), or implementing bespoke solutions. The course will give your team the ability to evaluate user needs and levels of understanding, make informed decisions about chart selections, and make effective use of interactivity dynamic data. We’ll work with you before the course to ensure that we understand your organisation and what you’re hoping to achieve. Sample learning content Session 1: Data with a purpose Understanding the different types of dashboard. Information overload and other common dashboard pitfalls. Assessing user needs and levels of data fluency. Session 2: Planning a dashboard Assessing diverse user needs and levels of data fluency. Taking a User Experience (UX) approach to design and navigation. Applying an interative and collaborative approach to onboarding. Session 3: Graphs, charts and dials Understanding how graphical perception informs chart choices. Making intelligent design choices to help users explore. Design principles for layout and navigation. Session 4: Using interactivity Making effective use of filters to slice and dice data sets. Using layers of information to enable drilldown data exploration. Complenting dashboards with automated alerts and queries. Delivery We deliver our courses over Zoom, to maximise flexibility. The training can be delivered in a single day, or across multiple sessions. All of our courses are live and interactive – every session includes a mix of formal tuition and hands-on exercises. To ensure this is possible, the number of attendees is capped at 16 people. Tutor Alan Rutter is the founder of Fire Plus Algebra. He is a specialist in communicating complex subjects through data visualisation, writing and design. He teaches for General Assembly and runs in-house training for public sector clients including the Home Office, the Department of Transport, the Biotechnology and Biological Sciences Research Council, the Health Foundation, and numerous local government and emergency services teams. He previously worked with Guardian Masterclasses on curating and delivering new course strands, including developing and teaching their B2B data visualisation courses. He oversaw the iPad edition launches of Wired, GQ, Vanity Fair and Vogue in the UK, and has worked with Condé Nast International as product owner on a bespoke digital asset management system for their 11 global markets. Testimonial “Alan was great to work with, he took us through the concepts behind data visualisation which means our team is now equipped for the future. He has a wide range of experience across the topic that is delivered in a clear, concise and friendly manner. We look forward to working with Alan again in the future.” John Masterson | Chief Product Officer | ImproveWell
Communicating complexity
By Fire Plus Algebra
Successful communications are all about making the message as simple as possible – but this can be difficult when the subjects we're talking about are inherently complicated. Academic institutions, tech companies, health organisations, charities and many others have complex ideas, processes and systems at the heart of what they do. This course is for anybody who needs to distill information down into key messages for important stakeholders, funders and investors, decision makers and members of the public. You’ll learn proven techniques for grabbing attention and changing minds through presentations and public speaking, infographics and data visualisations, and written reports and online posts. We’ll work with you before the course to ensure that we understand your organisation and what you’re hoping to achieve. Sample learning content Session 1: Understanding your audience Matching your objectives to your audience's motivations. Identifying the right tone and language. Understanding how, where and when your audience wants to be spoken to. Session 2: Refining your objectives Breaking down strategic aims into tactical steps Metrics and milestones: defining and measuring progress and success. Rapidly building a brief for your communications. Session 3: Telling the story Using metaphors, visuals, comparisons to frame your narrative. From slide decks to online campaigns - choosing the right formats for delivering your message. Selecting communications channels to maximise reach and impact. Session 4: Keeping it going Processes and systems for launching and maintaining communications campaigns. Building social proof – creating and curating content. Troubleshooting and preparing for common challenges. Delivery We deliver our courses over Zoom, to maximise flexibility. The training can be delivered in a single day, or across multiple sessions. All of our courses are live and interactive – every session includes a mix of formal tuition and hands-on exercises. To ensure this is possible, the number of attendees is capped at 16 people. Tutor Alan Rutter is the founder of Fire Plus Algebra. He is a specialist in communicating complex subjects through data visualisation, writing and design. He teaches for General Assembly and runs in-house training for public sector clients including the Home Office, the Department of Transport, the Biotechnology and Biological Sciences Research Council, the Health Foundation, and numerous local government and emergency services teams. He previously worked with Guardian Masterclasses on curating and delivering new course strands, including developing and teaching their B2B data visualisation courses. He oversaw the iPad edition launches of Wired, GQ, Vanity Fair and Vogue in the UK, and has worked with Condé Nast International as product owner on a bespoke digital asset management system for their 11 global markets. Testimonial “We’ve now worked with Alan for almost 3 years, and during that time he has continued to deliver the highest quality training for our clients and delegates. Alan’s passionate delivery style has continued to deliver innovative training solutions to over 1500 delegates across the public, private and voluntary sector. Each of our courses with him has always delivered exceptional feedback and satisfaction levels.” Joe Barlow | Head of Programme, Understanding ModernGov

Presenting with Impact
By Fire Plus Algebra
To drive actions and get decisions made, you need to be able to present effectively to customers, clients, senior managers or colleagues. The perfect presentation is a potent combination of content, design and delivery You need to distill down complex concepts, large data sets, intricate processes and innovative ideas. You need to make the right design choices to ensure your slide decks communicate quickly (as well as looking great). And you need the confidence and storytelling techniques to lead your audience through the content. This course is for anyone who regularly needs to create and deliver presentations for different stakeholders. It will cover how to plan, design and deliver brilliant presentations. Sample learning content Session 1: Planning a presentation Assessing the needs and level of understanding of your audience. Frameworks for building a logical and compelling narrative. Emphasising key messages, while allowing for deep dives and questions. Session 2: Presenting data and processes Understand graphical perception and how people absorb visual information. Effective charts for different types of data stories. How to display processes, timelines and organisational structures. Session 3: Design tricks Using colours to add emphasis and meaning. Creating hierarchies of information to help your audience. Building templates and style guides. Session 4: Delivery techniques Perfecting your performance in-person or online. Dealing with difficult questions and hostile audiences. Refining the beginning, middle and end of your narrative. Delivery We deliver our courses over Zoom, to maximise flexibility. The training can be delivered in a single day, or across multiple sessions. All of our courses are live and interactive – every session includes a mix of formal tuition and hands-on exercises. To ensure this is possible, the number of attendees is capped at 16 people. Tutor Alan Rutter is the founder of Fire Plus Algebra. He is a specialist in communicating complex subjects through data visualisation, writing and design. He teaches for General Assembly and runs in-house training for public sector clients including the Home Office, the Department of Transport, the Biotechnology and Biological Sciences Research Council, the Health Foundation, and numerous local government and emergency services teams. He previously worked with Guardian Masterclasses on curating and delivering new course strands, including developing and teaching their B2B data visualisation courses. He oversaw the iPad edition launches of Wired, GQ, Vanity Fair and Vogue in the UK, and has worked with Condé Nast International as product owner on a bespoke digital asset management system for their 11 global markets. Testimonial "We’ve now worked with Alan for almost 3 years, and during that time he has continued to deliver the highest quality training for our clients and delegates. Alan’s passionate delivery style has continued to deliver innovative training solutions to over 1500 delegates across the public, private and voluntary sector. Each of our courses with him has always delivered exceptional feedback and satisfaction levels." Joe Barlow | Head of Programme, Understanding ModernGov
