- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1313 Integration courses in Leicester delivered Online
M&A Beyond Day One: What They Don't Teach You
By IIL Europe Ltd
M&A Beyond Day One: What They Don't Teach You When merging and acquiring organizations there are many factors to consider - not all aspects of M&A activity are reserved for senior executive leadership teams, private equity companies and legal teams. There are the obvious aspects that require blending from both companies; from finances, people/teams to the corporate image and company culture. Consider all of the aspects of an organization that exist just to run the normal course of business. Then consider all of the similar aspects of another organization that is being merged into another organization! It can be a daunting task that requires skillful organization and consideration of aspects of M&A that 'they don't teach you about'. Ben Chodor, President, Intrado Digital Media shares his personal journey of excitement and freedom from selling his first company to the experience of 'now what!?' post-sale and how he was able to navigate the big changes, build company culture, shift roles from owner to employee and take on the 'new normal' at the new organization. M&A is much more than just a financial decision People and culture cannot be overlooked Successful integration is not just HR, Finance and facilities

AZ-104T00 Microsoft Azure Administrator
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for Azure Administrators. The Azure Administrator implements, manages, and monitors identity, governance, storage, compute, and virtual networks in a cloud environment. The Azure Administrator will provision, size, monitor, and adjust resources as appropriate. This course teaches IT Professionals how to manage their Azure subscriptions, secure identities, administer the infrastructure, configure virtual networking, connect Azure and on-premises sites, manage network traffic, implement storage solutions, create and scale virtual machines, implement web apps and containers, back up and share data, and monitor your solution. Prerequisites Successful Azure Administrators start this role with experience in virtualization, networking, identity, and storage. Understanding of on-premises virtualization technologies, including: VMs, virtual networking, and virtual hard disks. Understanding of network configurations, including TCP/IP, Domain Name System (DNS), virtual private networks (VPNs), firewalls, and encryption technologies. Understanding of Active Directory concepts, including users, groups, and role-based access control. Understanding of resilience and disaster recovery, including backup and restore operations. 1 - Configure Microsoft Entra ID Describe Microsoft Entra ID benefits and features Describe Microsoft Entra concepts Compare Active Directory Domain Services to Microsoft Entra ID Select Microsoft Entra editions Implement Microsoft Entra join Implement Microsoft Entra self-service password reset 2 - Configure user and group accounts Create user accounts Manage user accounts Create bulk user accounts Create group accounts Create administrative units 3 - Configure subscriptions Identify Azure regions Implement Azure subscriptions Obtain an Azure subscription Identify Azure subscription usage Implement Microsoft Cost Management Apply resource tagging Apply cost savings 4 - Configure Azure Policy Create management groups Implement Azure policies Create Azure policies Create policy definitions Create an initiative definition Scope the initiative definition Determine compliance 5 - Configure role-based access control Implement role-based access control Create a role definition Create a role assignment Compare Azure roles to Microsoft Entra roles Apply role-based access control Review fundamental Azure RBAC roles 6 - Configure Azure resources with tools Use the Azure portal Use Azure Cloud Shell Use Azure PowerShell Use Azure CLI 7 - Use Azure Resource Manager Review Azure Resource Manager benefits Review Azure resource terminology Create resource groups Create Azure Resource Manager locks Reorganize Azure resources Remove resources and resource groups Determine resource limits 8 - Configure resources with Azure Resource Manager templates Review Azure Resource Manager template advantages Explore the Azure Resource Manager template schema Explore the Azure Resource Manager template parameters Consider Bicep templates Review QuickStart templates 9 - Configure virtual networks Plan virtual networks Create subnets Create virtual networks Plan IP addressing Create public IP addressing Associate public IP addresses Allocate or assign private IP addresses 10 - Configure network security groups Implement network security groups Determine network security group rules Determine network security group effective rules Create network security group rules Implement application security groups 11 - Configure Azure DNS Identify domains and custom domains Verify custom domain names Create Azure DNS zones Delegate DNS domains Add DNS record sets Plan for Azure Private DNS zones Review Azure Private DNS zone scenarios 12 - Configure Azure Virtual Network peering Determine Azure Virtual Network peering uses Determine gateway transit and connectivity Create virtual network peering Extend peering with user-defined routes and service chaining 13 - Configure network routing and endpoints Review system routes Identify user-defined routes Determine service endpoint uses Determine service endpoint services Identify private link uses 14 - Configure Azure Load Balancer Determine Azure Load Balancer uses Implement a public load balancer Implement an internal load balancer Determine load balancer SKUs Create back-end pools Create health probes Create load balancer rules 15 - Configure Azure Application Gateway Implement Azure Application Gateway Determine Azure Application Gateway routing Configure Azure Application Gateway components 16 - Configure storage accounts Implement Azure Storage Explore Azure Storage services Determine storage account types Determine replication strategies Access storage Secure storage endpoints 17 - Configure Azure Blob Storage Implement Azure Blob Storage Create blob containers Assign blob access tiers Add blob lifecycle management rules Determine blob object replication Upload blobs Determine Blob Storage pricing 18 - Configure Azure Storage security Review Azure Storage security strategies Create shared access signatures Identify URI and SAS parameters Determine Azure Storage encryption Create customer-managed keys Apply Azure Storage security best practices 19 - Configure Azure Files and Azure File Sync Compare storage for file shares and blob data Manage Azure file shares Create file share snapshots Implement Azure File Sync Identify Azure File Sync components Deploy Azure File Sync 20 - Configure Azure Storage with tools Use Azure Storage Explorer Use the Azure Import/Export service Use the WAImportExport tool Use the AzCopy tool 21 - Configure virtual machines Review cloud services responsibilities Plan virtual machines Determine virtual machine sizing Determine virtual machine storage Create virtual machines in the Azure portal Connect to virtual machines 22 - Configure virtual machine availability Plan for maintenance and downtime Create availability sets Review update domains and fault domains Review availability zones Compare vertical and horizontal scaling Implement Azure Virtual Machine Scale Sets Create Virtual Machine Scale Sets Implement autoscale Configure autoscale 23 - Configure Azure App Service plans Implement Azure App Service plans Determine Azure App Service plan pricing Scale up and scale out Azure App Service Configure Azure App Service autoscale 24 - Configure Azure App Service Implement Azure App Service Create an app with App Service Explore continuous integration and deployment Create deployment slots Add deployment slots Secure your App Service app Create custom domain names Back up and restore your App Service app Use Azure Application Insights 25 - Configure Azure Container Instances Compare containers to virtual machines Review Azure Container Instances Implement container groups Review the Docker platform 26 - Configure file and folder backups Describe Azure Backup benefits Implement Backup Center for Azure Backup Configure Azure Recovery Services vault backup options Use the Microsoft Azure Recovery Services (MARS) agent Configure on-premises file and folder backups 27 - Configure virtual machine backups Explore options to protect virtual machine data Create virtual machine snapshots in Azure Backup Set up Azure Recovery Services vault backup options Back up your virtual machines Restore your virtual machines Implement System Center DPM and Azure Backup Server Compare the MARS agent and Azure Backup Server Implement soft delete for your virtual machines Implement Azure Site Recovery 28 - Configure Azure Monitor Describe Azure Monitor key capabilities Describe Azure Monitor components Define metrics and logs Identify monitoring data and tiers Describe activity log events Query the activity log 29 - Configure Azure alerts Describe Azure Monitor alerts Manage Azure Monitor alerts Create alert rules Create action groups 30 - Configure Log Analytics Determine Log Analytics uses Create a Log Analytics workspace Create Kusto (KQL) queries Structure Log Analytics queries 31 - Configure Network Watcher Describe Azure Network Watcher features Review IP flow verify diagnostics Review next hop diagnostics Visualize the network topology

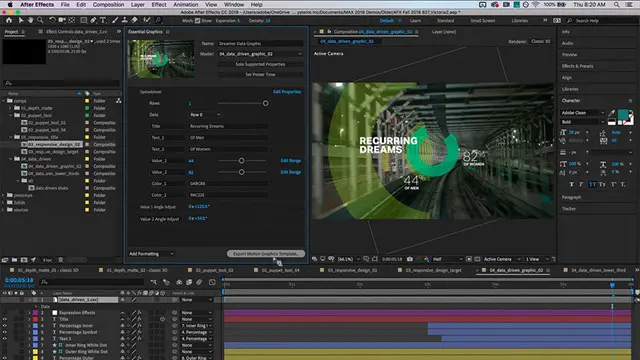
Adobe After Effects Basic to Advanced level training course 1-2-1
By Real Animation Works
AFTEREFFECTS face to face training customised and bespoke.
Overview 2 day course on scorecards, rating agency frameworks, regulation and integration and quantification of Environmental, Social and Governance (ESG) analysis into equity and credit investing / lending for / to corporates, banks and other financial institutions, applied to many case study companies and industries Who the course is for Investors and analysts – equity and credit; public and private Bank loan officers M&A advisors Restructuring advisors Course Content To learn more about the day by day course content please click here To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now

MB-800T00 Microsoft Dynamics 365 Business Central Functional Consultant
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for A Dynamics 365 Business Central core Functional Consultant is responsible for implementing core application setup processes for small and medium businesses. Overview Understand use cases for Business Central modules Set up Business Central Configure Financials Configure Sales and Purchasing Configure Operations Understand Integrationa nd Automation scenarios Built and optimized for small and medium businesses, Dynamics 365 Business Central is an application for companies that have outgrown their entry-level business applications. Growing businesses often outgrow their basic accounting software or legacy enterprise resource planning (ERP) systems that are unable to handle increased inventory and transactions, lack integration with other line-of-business systems, and have reporting limitations. Businesses are also challenged with the logistics of providing services that have more scalability, increased mobility, and availability in the cloud. With Business Central, you can manage your financials, automate and secure your supply chain, sell smarter, improve customer service and project performance, and optimize your operations. Introduction to Business Central Modules Introduction to Business Central Technology overview Navigate the user interface Master data for the Sales and Purchase process Application Setup Create and configure a new company Migrate data to Business Central Manage Security Set up core app functionality Set up dimensions Configure Financials Set up Finance Management Set up the Chart of Accounts Set up posting groups General Journals Set up Cash Management Set up Accounts Payables Set up Accounts Receivables Configure Sales and Purchasing Set up Inventory Configure prices and discounts Operations Purchase items Sell items Process financial transactions Inventory costing Integration and Automation Set up and use approvals with workflows Connect Power Apps Connect Power Automate Connect Power BI

Adobe Photoshop CC Intermediate
By iStudy UK
This Adobe Photoshop CC Intermediate builds on skills gained either in the workplace or on the Photoshop CC Introduction Training. Once you've gotten comfortable with the basic techniques of Adobe Photoshop, you're ready to sharpen your skills with this intermediate level course. Learn how to give your projects more definition, clarity and style. Take your Photoshop skills to the next level with this course. Learn how to colour correct, work with advanced layer options and make masks for image editing. You'll also create and manipulate everything from filters, gradients, patterns, type and shape layers and paths. In addition, you will work with advanced special effects, including blur and distort filters, stylizing effects, liquefy and smart filters, and work with Smart Objects. You will understand and work with RAW images. Finally, you will automate tasks using Actions, create Droplets, HDR images, and a panoramic image, explore integration with other Adobe software, and understand colour management. What Will I Learn? Paint and Use Brushes Use Vector Tools Use Advanced Special Effects Work with RAW Images Review Retouching Basics Automate Tasks Integrate with Other Adobe Software Explore Color Management Requirements Recommended pre-requisites: Adobe Photoshop CC Introduction Who is the target audience? Students who wish to learn some of the more advanced features of Photoshop CC. Start Here Introduction FREE 00:03:00 Painting and Using Brushes Painting with Brushes 00:09:00 Using the Brushes Panel 00:06:00 Defining Custom Brushes 00:04:00 Saving Tool Presets 00:02:00 Using the History Brush 00:03:00 Using Vector Tools Working with Vector Shapes 00:10:00 Creating Custom Shapes 00:02:00 Using the Pen Tool 00:07:00 Discovering Paths 00:04:00 Understanding Vector Masks 00:03:00 Using Vector Objects and Spot Colors 00:06:00 Using Libraries What is the CC Library 00:02:00 Adding and Deleting Assets in the Library 00:03:00 Sharing Assets 00:02:00 Creating New Libraries 00:03:00 Sharing a Library 00:02:00 Advanced Special Effects Using the Blur Filters 00:06:00 Applying the Distort Filters 00:03:00 Creating a Pixelated Look 00:02:00 Stylizing Effects 00:02:00 Using Liquify 00:05:00 Using Smart Filters 00:04:00 Working with Smart Objects 00:03:00 Loading a Texture into Type 00:04:00 Working with RAW Images What is a Raw Image 00:05:00 Processing Raw Images 00:12:00 Opening a JPEG File in Raw 00:06:00 Retouching Basics Developing a Strategy for Retouching 00:04:00 Using Retouching Tools 00:10:00 Using the Dust and Scratches Filter 00:04:00 Applying Sharpening 00:08:00 Working with Face Aware Liquify 00:06:00 Automating Tasks Using Actions 00:03:00 Using Droplets 00:05:00 Creating an HDR Image 00:07:00 Creating a Panoramic Image 00:07:00 Integration with other Adobe Software Using PSD Files in InDesign 00:04:00 Using PSD Files in Illustrator 00:03:00 Using PSD Files in Dreamweaver 00:04:00 Understanding Color Management Why Color Management 00:03:00 Calibrating a Monitor 00:04:00 Calibrating a Printer 00:03:00 Loading Profiles into PSDs 00:02:00 Conclusion Course Recap 00:01:00 Course Certification

VMware Cloud Director: Advanced Networking with NSX-T Data Center [v10.2]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Cloud architects, systems engineers, datacenter administrators, and cloud administrators with experience in managed services or managing a service provider environment. Overview By the end of the course, you should be able to meet the following objectives: Understanding NSX-T Data Center and VMware Cloud Director fundamentals List the various NSX-T Data Center components List the use cases and topologies of VMware Cloud Director networks Discuss the VMware Cloud Director provider networking configurations Discuss the VMware Cloud Director tenant networking configurations Discuss NSX Advanced Load Balancer and its components Discuss NSX Advanced Load Balancer configuration and integration with VMware Cloud Director Enable a layer 2 stretched network that spans across multiple VMware Cloud organization VDCs Showcase the importance of the VMware Cloud Director migration tool and its functionality Manage resources from the VMWare Cloud Director console and use VMware vRealize Operations Manager⢠In this five-day course, you focus on designing, integrating, configuring, and managing VMware Cloud Director? 10.x with VMware NSX-T© Data Center and VMware NSX© Advanced Load Balancer?. You learn about creating Network Pools and Edge Cluster management. You also learn about creating and managing an external network and creating and managing the organization of VDC, vApp, and data center group networks. Course Introduction Introductions and course logistics Course objectives VMware Cloud Director Data Center Fundamentals Explain NSX-T Data Center and its architecture Discuss various NSX-T Data Center components Describe NSX-T Data Center objects and their creation methods List the various requirement and maximum configuration details Explain NSX-T Data Center and its architecture Discuss various NSX-T Data Center components Describe NSX-T Data Center objects and their creation methods Explain VMware Cloud Director and its architecture List the various requirement and maximum configuration details Discuss VMware Cloud Director pre-requisites and deployment Discuss the use cases and features of VMware Cloud Director List the various requirement and maximum configuration details Discuss the design best practices Provider Configuration Discuss the integration of VMware vCenter Server© with VMware Cloud Director Discuss the integration of NSX-T Data Center with VMware Cloud Director Explain the provider side networking concepts and features Tenant Configuration Discuss the various types of organization VDC networks that can be created using NSX-T Data Center Explain the edge services available under each type of Organization VDC networks Explain what vApp network is Discuss various types of vApp networks Cross VDC networking with NSX-T Explain data center groups Configure cross-VDC networking and L2 stretched networks Configure a distributed firewall for a Data Center Group NSX Advanced Load Balancer Describe the NSX Advanced Load Balancer components and main functions Explain the NSX Advanced Load Balancer key features and benefits Understand and apply a Global Server Load Balancing design framework VMware NSX Migration for VMware Cloud Director Understand the main usage and purpose of the NSX migration for VMware Cloud Director List the supported topology and compatibility matrix List the supported features Understand the environmental prerequisites and how to prepare the edge cluster for bridging Know the logs and error handling exceptions Monitoring VMware Cloud Director Networking Discuss the methods to manage and monitor networking objects from VMware Cloud Director portals Understand the vRealize Operations Manager and vRealize Operations Manager Tenant App overview Discuss how to monitor VMware Cloud Director networking objects using vRealize Operations Manager and vRealize Operations Manager Tenant App Create views and reports Describe the use of vCloud Usage Meter with VMware Cloud Director
![VMware Cloud Director: Advanced Networking with NSX-T Data Center [v10.2]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Cisco Securing the Web with Cisco Web Security Applicance v3.0 (SWSA)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Security architects System designers Network administrators Operations engineers Network managers, network or security technicians, and security engineers and managers responsible for web security Cisco integrators and partners Overview After taking this course, you should be able to: Describe Cisco WSA Deploy proxy services Utilize authentication Describe decryption policies to control HTTPS traffic Understand differentiated traffic access policies and identification profiles Enforce acceptable use control settings Defend against malware Describe data security and data loss prevention Perform administration and troubleshooting This course shows you how to implement, use, and maintain Cisco© Web Security Appliance (WSA), powered by Cisco Talos, to provide advanced protection for business email and control against web security threats. Through a combination of expert instruction and hands-on practice, you?ll learn how to deploy proxy services, use authentication, implement policies to control HTTPS traffic and access, implement use control settings and policies, use the solution?s anti-malware features, implement data security and data loss prevention, perform administration of Cisco WSA solution, and more.This course helps you prepare to take the exam, Securing the Web with Cisco Web Security Appliance (300-725 SWSA). Describing Cisco WSA Technology Use Case Cisco WSA Solution Cisco WSA Features Cisco WSA Architecture Proxy Service Integrated Layer 4 Traffic Monitor Data Loss Prevention Cisco Cognitive Intelligence Management Tools Cisco Advanced Web Security Reporting (AWSR) and Third-Party Integration Cisco Content Security Management Appliance (SMA) Deploying Proxy Services Explicit Forward Mode vs. Transparent Mode Transparent Mode Traffic Redirection Web Cache Control Protocol Web Cache Communication Protocol (WCCP) Upstream and Downstream Flow Proxy Bypass Proxy Caching Proxy Auto-Config (PAC) Files FTP Proxy Socket Secure (SOCKS) Proxy Proxy Access Log and HTTP Headers Customizing Error Notifications with End User Notification (EUN) Pages Utilizing Authentication Authentication Protocols Authentication Realms Tracking User Credentials Explicit (Forward) and Transparent Proxy Mode Bypassing Authentication with Problematic Agents Reporting and Authentication Re-Authentication FTP Proxy Authentication Troubleshooting Joining Domains and Test Authentication Integration with Cisco Identity Services Engine (ISE) Creating Decryption Policies to Control HTTPS Traffic Transport Layer Security (TLS)/Secure Sockets Layer (SSL) Inspection Overview Certificate Overview Overview of HTTPS Decryption Policies Activating HTTPS Proxy Function Access Control List (ACL) Tags for HTTPS Inspection Access Log Examples Understanding Differentiated Traffic Access Policies and Identification Profiles Overview of Access Policies Access Policy Groups Overview of Identification Profiles Identification Profiles and Authentication Access Policy and Identification Profiles Processing Order Other Policy Types Access Log Examples ACL Decision Tags and Policy Groups Enforcing Time-Based and Traffic Volume Acceptable Use Policies, and End User Notifications Defending Against Malware Web Reputation Filters Anti-Malware Scanning Scanning Outbound Traffic Anti-Malware and Reputation in Policies File Reputation Filtering and File Analysis Cisco Advanced Malware Protection File Reputation and Analysis Features Integration with Cisco Cognitive Intelligence Enforcing Acceptable Use Control Settings Controlling Web Usage URL Filtering URL Category Solutions Dynamic Content Analysis Engine Web Application Visibility and Control Enforcing Media Bandwidth Limits Software as a Service (SaaS) Access Control Filtering Adult Content Data Security and Data Loss Prevention Data Security Cisco Data Security Solution Data Security Policy Definitions Data Security Logs Performing Administration and Troubleshooting Monitor the Cisco Web Security Appliance Cisco WSA Reports Monitoring System Activity Through Logs System Administration Tasks Troubleshooting Command Line Interface

META-Health Foundation Course
By EFT Tapping Training Institute
Uncovering Emotional Root Causes of Health Challenges Instructor Craig Weiner, DC, Licensed MetaHealth Foundation Trainer, EFT Master Trainer of Trainers. Learn to apply a method of analysis that effectively guides the application and integration of EFT, Matrix Reimprinting and other alternative healing modalities you may already currently use for yourself and on your clients. Discover how symptoms and disease are actually an intelligent process that is the body’s attempt to heal stress and trauma. With this knowledge, fear can be greatly reduced and a therapeutic intervention can then be utilized in a more precise way. You and your clients will achieve results faster and will be amazed at the insights, connections and progress they make in their healing journey. META-Health is the science, practice and art of Body-Mind-Social Health with a focus on how specific stress triggers, emotions and beliefs affect specific organ symptoms. META-Health is a methodology based on Integrative Medicine and Prevention and is practiced by all types of health professionals interested in a precise and effective Body-Mind-Social analysis and approach towards most effectively supporting individuals working to find emotional and physical healing. Your trainer for this Foundation weekend will be Craig Weiner, who has worked in the complementary health care field for over 30 years. He brings his professional clinical experience, his years as an educator and certified trainer in the Emotional Freedom Techqniques and Matrix Reimprinting and as a licensed META-Health Foundation Trainer. In the Foundation Course you will get the overview of the META-Health concepts and its implications for self-healing, assistance in transforming disease, and achieving sustainable health and resilience, including: Rhythms of life, and the organism’s self-regulating intelligence How the bio-logical needs change your perception and create life strategies How to decode the language of your organs Recognize the key points and phases of the healing process Experience the powerful META-Analytics questions Use the 8 milestones of META-Health to address the whole system and its soil Find META-meanings to create resilience Demonstrations and practical exercises will lead you to deeply integrate the wisdom of your body, and inspire you to actively claim and support your health. You will understand the natural, dynamic path of healing, and be empowered to lift your – and others’ – consciousness to make use of our potential! During this weekend we will spend time reviewing the core META-Health Principles: Our body-mind is highly intelligent Bio-logical survival and stress strategies, regeneration and resilience are at play in our brain, nervous system and hormonal system Significant emotional experiences shape our beliefs, personality and lifestyle Specific individual stress triggers influence typical organ tissues and functions The cycle of stress, regeneration and learning goes through distinct points and phases Awareness and imagination are capabilities of our brain which can recreate meaning and reprogram body-mind’s reactions There is no pre-requisite to taking this weekend course. Anyone who is interested can participate in the META-Health Foundation Training. The Foundation Training is the first step in becoming a certified META-Health Practitioner. Times: The course is a 12 hours training and will be held from 9:00 to 4:00 Seattle/Pacific time on both Friday and Saturday with a 60 minute lunch break held at approximately 12:30pm.

Power BI Masterclass 8 -Python, Finance, and Advanced DAX
By Packt
This comprehensive training program covers many concepts in Microsoft Power BI. From beginner to advanced levels, learn data visualization, advanced DAX expression, Python integration, custom visuals, data preparation, and collaboration in Power BI service. Develop expertise in Power BI and position yourself for a successful career in data analytics.
