- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
12269 Guide courses
Introduction to Immigration Law
By Immigration Advice Service
Our Introduction to Immigration Law course is a full-day course designed for those who are interested in a career in immigration law. About the course Our introduction to UK Immigration Law course is aimed at those looking to venture into the increasingly popular and relevant world of immigration law. This exciting course will give you an overview of the various UK visa routes as well as looking into a “day in the life” of an immigration caseworker, with the opportunity to work through a real visa application form. During this course we’ll also guide you on the path to accreditation, providing valuable insights into the requirements and steps to become a recognised immigration professional. Course joining links, materials and instructions are sent out 24hours before the course starts. Course information Course: Introduction to Immigration Law Duration: 1 day Delivery Method: Online Trainer: Expert Immigration Trainer CPD: 6 Points Career Path: Immigration Advisor Entry Requirements: None Why Study with Immigration Advice Service. Immigration Advice Service has been providing professional immigration services for over 10 years in the public, private and corporate sectors. Our Introduction to Immigration Law course will give you an insight into UK Law, covering key fundamentals as well as how to become an accredited advisor. Our qualified and OISC regulated trainer will guide you through the process and ensure you are competent with elements covered within the course. Content covered in the course: General knowledge of immigration law A look at common visa routes:Entry clearanceFamily visasVisit visasPBS How to take instructions from a client Drafting letters for clients How to work through a visa application form How to become accredited

Deep Learning using OpenPose - Learn Pose Estimation Models and Build 5 AI Apps
By Packt
The complete guide to creating your own Pose Estimation apps: Learn the full workflow and get up to speed with developing 5 AI apps
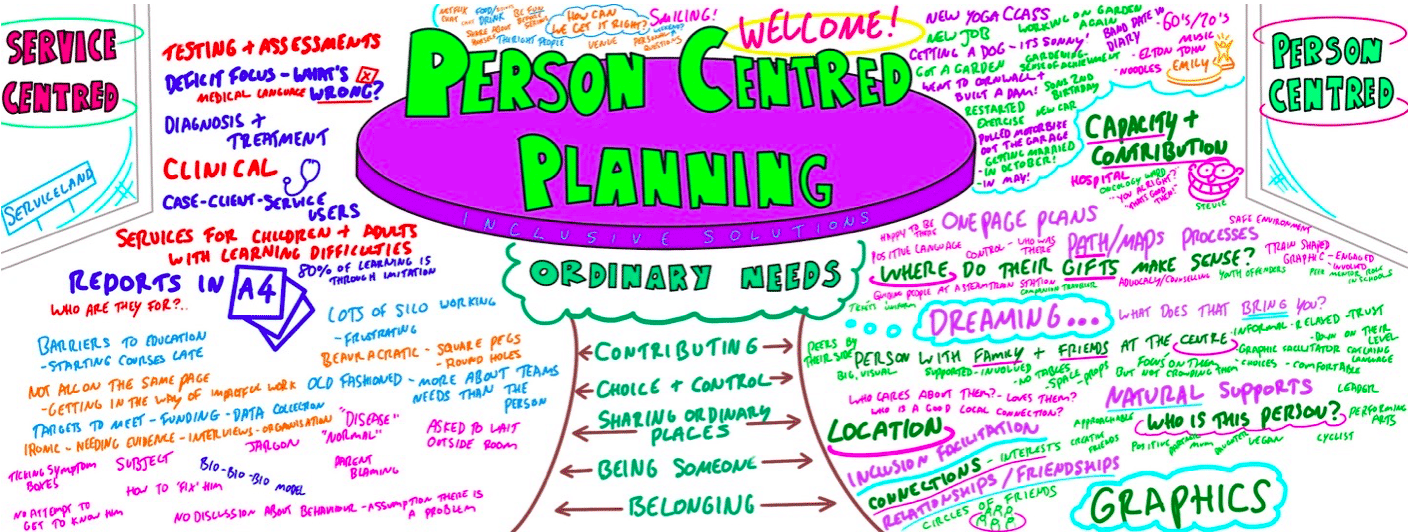
Person Centred Planning using PATH and MAPs
By Inclusive Solutions
What is Person Centred Planning? How is it different to any other kind of meeting or planning? On this day all will become clear… Give your team the opportunity to pause and reflect on what matters most to them about the work they do. The act of listening to each other creates relationship and strengthens trust and inclusion within the team – in creating a shared vision, groups of people build a sense of commitment together. They develop images of ‘the future we want to create together’, along with the values that will be important in getting there and the goals they want to see achieved along the way. Unfortunately, many people still think ’vision’ is the top leader’s job. In schools, the ‘vision task’ usually falls to the Headteacher and/or the governors or it comes in a glossy document from the local authority or the DfES. But visions based on authority are not sustainable. Making inclusive action plans using full participation and graphic facilitation Drawing on the planning tools MAPS and PATH (Pearpoint, Forest and O’Brien 1997) and other facilitation sources we use both process and graphic facilitation to enable the group to build their picture of what they would love to see happening within their organisation/community in the future and we encourage this to be a positive naming, not just a list of the things they want to avoid. Jack Pearpoint, Marsha Forest and John O’Brien developed these innovative approaches in North America and they are being used successfully in many parts of the UK. The planning can focus on an individual, group or organisation and provides a powerful problem solving opportunity, which is flexible and robust enough for many occasions. Tell the story, find the dream, touch the nightmare, and explore who you are, what are the gifts and strengths of the person or group, what are the needs of those present and what is the action plan for the future? Learning objectives Participants understand Person Centred Planning and its values and applications Participants have skills and confidence to facilitate PATH/MAP processes Participants learn graphic as well as process facilitation skills Strengthens practitioners inclusive practice Provides additional tools for those involved in inclusive work in schools and the community Further develop problem solving and planning skills Course Content The course answers the questions: Need to find new ways to bring Pathway Planning alive? Bored with annual reviews, transition plans and review meetings? Want to find a way of making meetings and planning feel more real and engaging? Need an approach, which engages a young person respectfully together with his or her family and friends? Want the ultimate visual record of the process of a meeting, which will help everyone, keep track? Want to problem solve and plan for the future of a small or large group, service or organisation up to the size of an LA? Inclusive Solutions offer an introductory day to person centred planning or a 3 – 10 session course which is practical as well as values based. Participants will receive direct individualised coaching and training. We will cover: The person being at the centre Family members and friends being full partners Planning reflecting the person’s capacities, what is important to the person and specifying the support they require to make a full contribution to their community Planning building a shared commitment to action that will uphold the person’s rights Planning leading to continual listening, learning and action and helping the person get what they want out of life. Essential Lifestyle Planning, PATH MAPS Personal Futures Planning.
The “ISO 20387 Lead Assessor Course” is a comprehensive program designed to equip individuals with the knowledge and skills needed to assess and evaluate biobanking systems in accordance with ISO 20387:2018. This course focuses on the principles of assessment, audit methodologies, and the specific requirements of ISO 20387. Participants will learn how to lead and conduct assessments of biobanking facilities and organizations to ensure compliance with the standard.

3 Day First Aid Description: The full 3-day First Aid at Work Qualification is nationally recognised. It meets the standards required to help comply with Health and Safety (First aid) regulations. This qualification is valid for three year, after which delegates need to complete a 2-day refresher course. Cardio Pulmonary Resuscitation and care of the unconscious requires physical effort. Learners should be capable of working with casualties at floor level. Learners receive a First Aid at Work guide book, a training dressing and a CPR barrier protection device. The HSE strongly recommend that all First Aiders undertake annual refresher training of at least 3 hours per year. Syllabus Care of the unconscious casualty Method of resuscitation Asphyxia Wound & bleeding Bandaging/slings Head and chest injuries Fractures Poisons Burns and scalds Epilepsy Diabetes Heart conditions Contents of a first aid box Accident reporting Other work related accidents/illnesses Scenarios AED (defibrillation) training Cost: £306.25 + VAT

Assuring Quality Through Acceptance Testing - Making Sure that the Business Problem is Solved: On-Demand
By IIL Europe Ltd
Assuring Quality Through Acceptance Testing - Making Sure that the Business Problem is Solved: On-Demand It is the business analyst's job to define the business problem to be solved by IT. It is also the business analyst's responsibility to confirm that the resulting solution developed by IT does, in fact, solve the defined problem. This is done first through testing, especially acceptance testing, and then through monitoring of the installed solution in the user community. The business analyst is not only concerned with the testing itself, but also with the management and monitoring of the users doing the acceptance testing, and recording, analyzing, and evaluating the results. What You Will Learn Upon completion of this course, participants will be able to: Create a set of acceptance test cases Manage and monitor an acceptance test stage where users perform the testing Work with the development team in the systems testing stage Assess the solution once it is in the business environment Foundation Concepts The role of the business analyst An introduction to the BABOK® Guide BA roles and relationships through the project life cycle Introduction to assuring software quality through acceptance testing The Scope of IT Testing Overview of testing stages The testing process Testing documentation Pre-Acceptance Testing The BA's role in testing Early development testing stages (unit and integration) Late development testing stage (system) The Acceptance Test Stage - Part I (Planning, Design, and Development) Overview of user acceptance testing Acceptance test planning Designing user acceptance tests Developing individual user acceptance test cases Building effective user acceptance test scenarios The Acceptance Test Stage - Part II (Execution and Reporting) Operating guidelines Execution Reporting Post-Acceptance Testing Overview Project implementation Project transition (project closure) Production through retirement Testing Commercial Off-the-Shelf (COTS) Software Overview Selecting the software Implementing the software Summary What did we learn and how can we implement this in our work environments?

Microsoft Project Orange Belt 2013: Virtual In-House Training
By IIL Europe Ltd
Microsoft Project Orange Belt® 2013: Virtual In-House Training This workshop gives participants a full insight into creating effective schedules using Microsoft® Project 2013, allowing you to estimate, coordinate, budget, staff, and control projects and support other users. This workshop gives participants a full insight into creating effective schedules using Microsoft® Project 2013, allowing you to estimate, coordinate, budget, staff, and control projects and support other users. This workshop provides the eBook Dynamic Scheduling with Microsoft® Project 2013, and is kept up to date with the framework of knowledge outlined by the Project Management Institute's PMBOK® Guide and the Practice Standard for Scheduling. What you Will Learn You'll learn how to: Understand what's new in Project 2013 Explain where Project 2013 fits in the Microsoft® EPM solution Initialize Project 2013 to start project planning Create a well-formed project schedule Understand task types and the schedule formula Assign resources and costs to tasks Analyze resource utilization and optimize the schedule Set a baseline and track progress Create and manage project reports Customize views and fields Apply Earned Value Management Understand the basics of managing multiple projects Getting Started Introductions Course structure Course goals and objectives Enterprise Project Management Concepts and Framework Getting Started with Project 2013 Project 2013: What's New and General Overview Setting Up a New Project Schedule (templates, options, save, etc.) Setting the Project Calendar Entering Tasks The Planning Processes Importing Tasks (Word, Excel, SharePoint) Synchronizing with SharePoint Tasks List Creating and managing the WBS (include tasks, manually scheduled tasks, summary tasks and milestones, as well as custom WBS coding) Entering Estimates Tendencies in Estimating The Rolling Wave Approach Entering Duration and Work Estimates Types of Tasks Entering Dependencies The Principle of Dynamic Scheduling Choosing the Right Type of Dependency Entering Dependencies in Project 2013 Different Applications of Dependencies Entering Deadlines, Constraints, and Task Calendars Use of Deadlines and Constraints Entering Deadlines and Constraints in Project 2013 Entering Resources and Costs Types of Resources Entering Resources in Project 2013 Calendars and Resources Entering Costs in Project 2013 Entering Assignments Assignments in a Schedule Assignments and Task Types Entering Assignments in Project 2013 Assignments, Budgets, and Costs Optimizing the Schedule The Critical Path Method and the Resource Critical Path Resource Leveling Optimizing Time, Cost, and Resources in Project 2013 Updating the Schedule The Baseline Updating Strategies and Situations Prepare the Status and Forecast Report in Project 2013 Reporting Using Reports Using Visual Reports Formatting and Printing in Project 2013 Customizing Fields in Project 2013 Earned Value Management (EVM) Overview of EVM Applying EVM with Project 2013 Evaluating the Project Evaluating the Project Performance Project Benefits and Results Templates for Future Projects Summary Tools and Checklist Best Practices Checklist Consolidated Schedules Creating Consolidated Schedules Using a Resource Pool Links across Projects Solving common problems Analyzing the Critical Path across Projects

Module 9 Part 2 Inner Child Hypnotherapy Workshop
5.0(22)By The Northern College Of Clinical Hypnotherapy
Learn how to deliver an interactive workshop based on the work of John Bradshaw and his inner child work. Inner child work is a way to address the needs that haven't been met as children and heal the attachment wounds we've developed. You'll learn how to offer this work in groups and one to one.

Search By Location
- Guide Courses in London
- Guide Courses in Birmingham
- Guide Courses in Glasgow
- Guide Courses in Liverpool
- Guide Courses in Bristol
- Guide Courses in Manchester
- Guide Courses in Sheffield
- Guide Courses in Leeds
- Guide Courses in Edinburgh
- Guide Courses in Leicester
- Guide Courses in Coventry
- Guide Courses in Bradford
- Guide Courses in Cardiff
- Guide Courses in Belfast
- Guide Courses in Nottingham

