- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
8733 ET courses in Nottingham delivered Online
Dynamic QDRs (Improvers)
By Floorwork Academy
What you get The pillars of Movement Our different tutorials take you through an in-depth study of technical concepts – efficiency, momentum, transitioning, weight management, spirals of motion, techniques of improvisation – to improve your flow. An extensive library of moves All my tutorials have been regrouped in one membership. Hundreds of videos to increase your movement vocabulary and lay the foundations for sequencing and freestyling, as well as dozens of sequences to integrate them and dozens of drills to learn to improve your flow. Develop a well-rounded softness The strength, mobility and body awareness you will develop through this course can be used to sustain a standalone practice or complement your own, whether it is dance, movement, yoga, pole dance or aerials.

Preliminary Electronic Security Course
By Hi-Tech Training
The Preliminary Electronic Security Course is an introductory (or revision) course designed to provide participants who have no previous Electrical or Electronics experience with the background skills required to attend the CCTV Installation Course, Access Control Course or Fire Alarm Foundation Course. The course gives both an introduction to electronics and electronic security and shows how the two fields merge together. Ideal for a beginner wishing to learn more about this fascinating area. A large practical content is guaranteed. The day will be an excellent learning experience with a skilled instructor. It is a great introduction to the other courses we provide.
IT System Support Course
By Hi-Tech Training
The IT System Support Technician (Online Virtual Classroom) Course will equip candidates with the skills and knowledge to competently carry out routine customer support to a range of Computer users, communicate effectively with support managers, supporting colleagues and external clients.

Get Hard Copy + PDF Certificate + Transcript + Student ID Card as a Gift - Enrol Now Tired of browsing and searching for the course you are looking for? Can't find the complete package that fulfils all your needs? Then don't worry as you have just found the solution. Take a minute and look through this 14-in-1 extensive bundle that has everything you need to succeed in Building Quantity Surveying & Construction Estimation and other relevant fields! After surveying thousands of learners just like you and considering their valuable feedback, this all in one Building Quantity Surveying & Construction Estimation bundle has been designed by industry experts. We prioritised what learners were looking for in a complete package and developed this in-demand Building Quantity Surveying & Construction Estimation course that will enhance your skills and prepare you for the competitive job market. Also, our Building Quantity Surveying & Construction Estimation experts are available for answering your queries and help you along your learning journey. Advanced audiovisual learning modules of these courses are broken down into little chunks so that you can learn at your own pace without being overwhelmed by too much material at once. Furthermore, to help you showcase your expertise in Building Quantity Surveying & Construction Estimation, we have prepared a special gift of 1 hardcopy certificate and 1 PDF certificate for the title course completely free of cost. These certificates will enhance your credibility and encourage possible employers to pick you over the rest. This Building Quantity Surveying & Construction Estimation Bundle Consists of the following Premium courses: Course 01: Building Quantity Surveying Training Level 3 Course 02: Building Surveyor Course 03: Construction Cost Estimation Diploma Course 04: Construction Estimation using RSMeans Course 05: Construction Cost Estimation Using Xactimate Course 06: Land Surveying Course 07: Architectural Studies Course 08: Property Law and Legislation Course 09: Construction Industry Scheme (CIS) Course 10: WELL Building Standard Course 11: LEED V4: Building Design and Construction Course 12: AutoCAD VBA Programming - Beginner course Course 13: PUWER Course 14: Construction Safety Benefits you'll get choosing Apex Learning for this Bundle: Pay once and get lifetime access to 14 CPD courses Certificates, student ID for the title course included in a one-time fee Free up your time - don't waste time and money travelling for classes Accessible, informative modules designed by expert instructors Learn at your ease - anytime, from anywhere Study the course from your computer, tablet or mobile device CPD accredited course - improve the chance of gaining professional skills How will I get my Certificate? After successfully completing the course you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (For The Title Course) Hard Copy Certificate: Free (For The Title Course) Curriculum Course 01: Building Quantity Surveying Training Level 3 Building Law Principles Building Procurement and Contract Administration Building Technology Cost Estimation Elements and Factors influencing Cost Estimation Cost Management Management of Material for construction Building Pathology Building Adaption Report Writing Legal Aspects Course 02: Building Surveyor An Introduction The Procedure of Building Survey and Surveys of Historic Buildings Beginning of the Survey: Foundation and In-depth Survey in Walls Ground Level Investigation: Floors and Investigation Above the Ground: Roofs and Chimneys Inspection of Joinery and Woodwork Services Inspection Understanding Work Breakdown Structure Report Writing Legal Aspects And Much More... Course 03: Construction Cost Estimation Diploma Introduction to Construction Management Cost Estimation Role of Cost Estimator and New Aspects of Cost Estimation Elements and Factors influencing Cost Estimation Cost Estimation in Construction Industry Cost Management Management of Material for construction Course 04: Construction Estimation using RSMeans Introduction Quantity Take Off Cost Estimation using RSMeans Course 05: Construction Cost Estimation Using Xactimate Introduction to Xactimate Foundation Cost Estimation on Xactimate Wood-frame Structure Cost Estimation on Xactimate Plumbing, Electricity and HVAC Cost Estimation on Xactimate Interior Finish & Cabinetry Cost Estimation on Xactimate Windows, Doors, Roof & Exterior Siding Cost Estimation on Xactimate Course 06: Land Surveying Introduction Land Surveying Basics And Much More... Course 07: Architectural Studies Introduction to Architectural Studies Ancient Architecture Architectural Ideas and Movements Architectural Styles Art Deco Architectural Style Scandinavian Architectural Style Victorian Architectural Style Classical and Early Christian Architectural Style Gothic Architectural Style Baroque and Rococo Architectural Style Eclecticism Architectural Style Modern and Post-Modern Architectural Style Interior Designing Colour in Interior Designing Lighting in Interior Design Part One Lighting in Interior Design Part Two Course 08: Property Law and Legislation Introduction to Property Law Land Law Principles- Rights and Interests Registered and Unregistered Land Ownership and Possession of the Property Co-Ownership in Property Leases and Bailment Property Law: License The Mortgage Law Insurance for Property Maintenance Proprietary Estoppel (Property Rights) Security Interests in Property Course 09: Construction Industry Scheme (CIS) Construction Industry Scheme (CIS) Coverage of the Scheme Contractors and Registration for the Scheme Verification Process The CIS Returns Record Keeping and CIS Certificates Penalties Involved in CIS Miscellaneous Information Course 10: WELL Building Standard Introduction Air Water Nourishment Light Fitness Comfort Mind Course 11: LEED V4: Building Design and Construction Introduction Integrative Process Location & Transportation Sustainable Sites Water Efficiency Energy & Atmosphere Materials & Resources Indoor Environment Quality Innovation Regional Priority Completion Course 12: AutoCAD VBA Programming - Beginner course Introduction VBA Integrated Development Environment (IDE) Understanding AutoCAD Object Model in VBA Using Variables in VBA User Forms and Controls Conditionals and Decisions in VBA Looping and Iterations in VBA Drawings Objects in VBA Code Debugging in VBA Error Handling in VBA Conclusion Course 13: PUWER Provision and Use of Work Equipment Regulations Selection and Conformity of Work Equipment Safe Functionality of Work Equipment Monitoring and Evaluation of Work Equipment Maintenance of Work Equipment Course 14: Construction Safety Managing Health and Safety Risk Assessment and Common Risks Health and Safety Guidelines and Legislations Reporting Accidents at Work General Site Issues Working at Height Excavation Work and Confined spaces Work Equipments Manual and Mechanical Handling Chemical and Biological Health Hazards and Control Electrical Hazards and Control Fire Hazards and Control CPD 140 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this bundle. Persons with similar professions can also refresh or strengthen their skills by enrolling in this course. Students can take this course to gather professional knowledge besides their study or for the future. Requirements Our bundle is fully compatible with PC's, Mac's, laptops, tablets and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so that you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course; it can be studied in your own time at your own pace. Certificates Certificate of completion Digital certificate - Included You will get the PDF Certificate for the title course (Building Quantity Surveying Training Level 3) absolutely Free! Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Building Quantity Surveying Training Level 3) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

CCTV Installation Course
By Hi-Tech Training
Hi-Tech Training Closed Circuit Television (CCTV) Installation Course is designed to give participants a practical knowledge of the operation and installation of CCTV systems at a foundation level.

**Be prepared for the upcoming Hiring Season by enhancing your professional skillsets with Apex Learning! Get Hard Copy + PDF Certificate + Transcript + Student ID Card as a Gift - Enrol Now** In this UK Insurance complete bundle course, we go into detail and explain all you need to know about general, commercial, liability, and life insurance in the UK. We also go into detail on the UK insurance market, insurance fraud, and other related issues. Learn how to become a well-respected and in-demand member of the UK insurance business. This dynamic business sector needs talented and motivated individuals to keep it running as a profitable market, and we can help you integrate in with ease. As an exceptional Insurance Agent, you will recognise your obligation and dedication to delivering the best brokerage for your grateful clients and consumers. You will understand the ideal schemes and contracts for each case, whether it is personal plans for houses and automobiles or a comprehensive corporate programme for a wealthy organisation. This thorough course will walk you through the many aspects of the insurance industry and offer you helpful information regardless of your level of expertise. The subject ranges from fundamental vocabulary to the many forms of insurance and the abilities required for a successful career in this industry. You'll learn about risk management, underwriting, and claims management. Methods for detecting fraud and knowing the code of conduct can help you become an excellent agent. Courses are included in this Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3? Course 01: Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3 Course 02: Insurance Agent Training Course 03: Pension UK Course 04: Law and Contracts - Level 2 Course 05: Financial Investigator Course 06: Financial Analysis Course 07: Payroll Administrator and UK Payroll System Training Course 08: Business Analysis Level 3 Course 09: Level 3 Tax Accounting Course 10: Microsoft Excel Training: Depreciation Accounting Course 11: Certificate in Anti Money Laundering (AML) Course 12: Know Your Customer (KYC) Course 13: Customer Relationship Management Course 14: Time Management Enrol and Achieve Mastery in: Recognising the significance of insurance in the UK financial industry Learning about the many forms of insurance available on the market Learning the fundamental skills required to work as an agent Dealing with the demands of high-performing enterprises Developing your capacity to manage risks in the workplace and on the job Understanding how to carry out critical activities, including claim management and underwriting Knowing how to spot examples of fraud when they occur Understanding the code of ethics and behaviour required to work as a reliable insurance broker Curriculum of UK Insurance Complete Package (General, Commercial, Liability, Life) Course 01: Understanding UK Insurance (General, Commercial, Liability, Life) - Level 3 01: Industry 02: The UK Industry 03: Principles 04: General 05: Personal Lines 06: Commercial Lines 07: Liability 08: Life Insurance 09: Insurance Fraud 10: Underwriting Process Course 02: Insurance Agent Training 01: An Overview of the UK Insurance Industry 02: Principles 03: Types 04: Career in the Industry 05: Skills of an Agent 06: Business 07: Risk Management in 08: Underwriting Process 09: Claims Handling Process 10: Fraud Finding 11: Code of Ethics and Conduct Course 03: Pension UK 01: Overview of the UK Pension system 02: Type of Pension Schemes 03: Pension Regulation 04: Pension Fund Governance 05: Law and Regulation of Pensions in the UK 06: Key Challenges in UK Pension System Course 04: Law and Contracts - Level 2 01: Introduction to UK Laws 02: Ministry of Justice 03: Agreements and Contractual Intention 04: Considerations and Capacities of Contact Laws 05: Terms within a Contract 06: Misinterpretations and Mistakes 07: Consumer Protection 08: Privity of Contract 09: Insurance Contract Laws 10: Contracts for Employees 11: Considerations in International Trade Contracts 12: Laws and Regulations for International Trade 13: Remedies for Any Contract Breach Course 05: Financial Investigator 01: Introduction to Financial Investigator 02: Introduction to Financial Investigation 03: Characteristics of Financial Crimes 04: Categories of Financial Crimes 05: Financial Crime Response Plan 06: Collecting, Preserving and Gathering Evidence 07: Laws against Financial Fraud Course 06: Financial Analysis 1. Introduction 2. Profitability 3. Return Ratio 4. Liquidity Ratio 5.Operational Analysis 6. Detecting Manipulation Course 07: Payroll Administrator and UK Payroll System Training Module 01: Payroll System in the UK Module 02: Payroll Basics Module 03: Company Settings Module 04: Legislation Settings Module 05: Pension Scheme Basics Module 06: Pay Elements Module 07: The Processing Date Module 08: Adding Existing Employees Module 09: Adding New Employees Module 10: Payroll Processing Basics Module 11: Entering Payments Module 12: Pre-Update Reports Module 13: Updating Records Module 14: e-Submissions Basics Module 15: Process Payroll (November) Module 16: Employee Records and Reports Module 17: Editing Employee Records Module 18: Process Payroll (December) Module 19: Resetting Payments Module 20: Quick SSP Module 21: An Employee Leaves Module 22: Final Payroll Run Module 23: Reports and Historical Data Module 24: Year-End Procedures Course 08: Business Analysis Level 3 01: Introduction to Business Analysis 02: Business Processes 03: Business Analysis Planning and Monitoring 04: Strategic Analysis and Product Scope 05: Solution Evaluation 06: Investigation Techniques 07: Ratio Analysis 08: Stakeholder Analysis and Management 09: Process Improvement with Gap Analysis 10: Documenting and Managing Requirements 11: Career Prospect as a Business Analyst in the UK Course 09: Level 3 Tax Accounting 01: Tax System and Administration in the UK 02: Tax on Individuals 03: National Insurance 04: How to Submit a Self-Assessment Tax Return 05: Fundamentals of Income Tax 06: Payee, Payroll and Wages 07: Value Added Tax 08: Corporation Tax 09: Double Entry Accounting 10: Management Accounting and Financial Analysis 11: Career as a Tax Accountant in the UK Course 10: Microsoft Excel Training: Depreciation Accounting Introduction Depreciation Amortization and Related Terms Various Methods of Depreciation and Depreciation Accounting Depreciation and Taxation Master Depreciation Model Conclusion Course 11: Certificate in Anti Money Laundering (AML) 01: Introduction to Money Laundering 02: Proceeds of Crime Act 2002 03: Development of Anti-Money Laundering Regulation 04: Responsibility of the Money Laundering Reporting Office 05: Risk-based Approach 06: Customer Due Diligence 07: Record Keeping 08: Suspicious Conduct and Transactions 09: Awareness and Training Course 12: Know Your Customer (KYC) 01: Introduction to KYC 02: Customer Due Diligence 03: AML (Anti-Money Laundering) 04: KYC, AML, and Data Privacy Regulations for Businesses Operations in the United Kingdom 05: Regulations to be Complied by Industries 06: Methods for carrying out KYC and AML and the Future of KYC Compliance Course 13: Customer Relationship Management Module 01: Introduction to Customer Relationship Management (CRM) Module 02: CRM Fundamentals Module 03: CRM Strategies CRM Strategies Module 04: Data Analysis in CRM Module 05: CRM Databases Module 06: Deepening Customer Relationship Module 07: Handling Customer Complaints Module 08: Future of CRM Course 14: Time Management Identifying Goals Effective Energy Distribution Working with Your Personal Style Building Your Toolbox Establishing Your Action Plan How will I get my Certificate? After successfully completing the course you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (For The Title Course) Hard Copy Certificate: Free (For The Title Course) If you want to get hardcopy certificates for other courses, generally you have to pay £20 for each. But this Fall, Apex Learning is offering a Flat 50% discount on hard copy certificates, and you can get each for just £10! P.S. The delivery charge inside the U.K. is £3.99 and the international students have to pay £9.99. CPD 140 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Insurance agent Claims handler Corporate accounts handler Compliance Consultant Client advisor Requirements This Training Course has been designed to be fully compatible with tablets and smartphones. Career path Insurance broker (£20,000 to £65,000) Insurance account manager (£18,000 to £75,000) Insurance underwriter (£18,000 to £65,000) Financial adviser (£23,500 to £45,000) Certificates Certificate of completion Digital certificate - Included You will get the PDF Certificate for the title course (Understanding UK Insurance) absolutely Free! Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Understanding UK Insurance) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

Alarm Installation Course
By Hi-Tech Training
The Alarm Installation Course is designed to teach participants how to install an intruder alarm system in domestic, commercial or industrial premises. The Alarm Installation Course simulates the practical installation of many different alarm control panels. The course is designed to equip students with the skills and expertise to competently install a wide variety of Alarm systems on the market.

**Be prepared for the upcoming Hiring Season by enhancing your professional skillsets with Apex Learning! Get Hard Copy + PDF Certificate + Transcript + Student ID Card as a Gift - Enrol Now** Tired of browsing and searching for the course you are looking for? Can't find the complete package that fulfils all your needs? Then don't worry as you have just found the solution. Take a minute and look through this 14-in-1 extensive bundle that has everything you need to succeed in Financial Advisor and other relevant fields! After surveying thousands of learners just like you and considering their valuable feedback, this all in one Financial Advisor bundle has been designed by industry experts. We prioritised what learners were looking for in a complete package and developed this in-demand Financial Advisor course that will enhance your skills and prepare you for the competitive job market. Also, our Financial Advisor experts are available for answering your queries and help you along your learning journey. Advanced audiovisual learning modules of these courses are broken down into little chunks so that you can learn at your own pace without being overwhelmed by too much material at once. Furthermore, to help you showcase your expertise in Financial Advisor, we have prepared a special gift of 1 hardcopy certificate and 1 PDF certificate for the title course completely free of cost. These certificates will enhance your credibility and encourage possible employers to pick you over the rest. This Financial Advisor Bundle Consists of the following Premium courses: Course 01: Financial Advisor Course 02: Financial Management Course 03: Investment Course 04: Capital Budgeting & Investment Decision Rules Course 05: Budgeting and Forecasting Course 06: Level 3 Tax Accounting Course 07: Team Management Course 08: Intermediate Economics Level 3 Course 09: Internal Audit Training Diploma Course 10: Forex Trading Level 3 Course 11: Stock Market Investing for Beginners Course 12: Fraud Management & Anti Money Laundering Awareness Complete Diploma Course 13: Commercial Law 2021 Course 14: Level 2 Microsoft Office Essentials Benefits you'll get choosing Apex Learning: One payment, but lifetime access to 14 CPD courses Certificates, student ID for the title course included in a one-time fee Full tutor support available from Monday to Friday Free up your time - don't waste time and money travelling for classes Accessible, informative modules taught by expert instructors Learn at your ease - anytime, from anywhere Study the course from your computer, tablet or mobile device CPD accredited course - improve the chance of gaining professional skills How will I get my Certificate? After successfully completing the course you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (For The Title Course) Hard Copy Certificate: Free (For The Title Course) Curriculum of Bundle Course 01: Financial Advisor Introduction to Finance Essential Skill Financial Planning Financial Risk Management and Assessment Investment Planning Divorce Planning Google Analytics and many more.... Course 02: Financial Management Introduction to Financial Management Fundamentals of Budgeting The Balance Sheet The Income Statement The Cash Flow Statement Statement of Stockholders' Equity Analysing and Interpreting Financial Statements International Aspects of Financial Management and many more.... Course 03: Investment Introduction to Investment Types and Techniques of Investment Key Concepts in Investment Understanding the Finance Investing in Bond Market Investing in Stock Market Risk and Portfolio Management and many more.... Course 04: Capital Budgeting & Investment Decision Rules Introduction NPV Method Payback Period Method Internal Rate of Return (IRR) Evaluating Projects in Different Lives Conclusion and many more.... Course 05: Budgeting and Forecasting Introduction Why Budget and Forecasts Is budget planning a paper exercise Operational and Financial Budget Detail Budget Requirement Components - Revenue Budgets Components - Cost Budget Qualitative Aspects Process of Making Budget Process of Budgeting - Logical Steps Example we used in Class to demonstrate a broad process in budget and planning Cost Budget Process - Other aspects and many more.... Course 06: Level 3 Tax Accounting Tax System and Administration in the UK Tax on Individuals National Insurance Fundamentals of Income Tax Payee, Payroll and Wages Value Added Tax Corporation Tax Double Entry Accounting Management Accounting and Financial Analysis Career as a Tax Accountant in the UK and many more.... Course 07: Presenting Financial Information Presenting Financial Information The Hierarchy of Performance Indicators The Principle of Effective Reports Methods of Presenting Performance Data The Pareto Chart: Highlighting Priorities Exercise: The Control Chart An Example Management Report Interpreting Performance Data Supporting Colleagues by Giving Feedback Data Visualisation Part 01, Part 02, Part 03, Part 04 and many more.... Course 08: Intermediate Economics Level 3 An Introduction to Economics The Market System and the Circular Flow Model Supply, Demand and Prices Prices Elasticity Market Failures Production and Costs Money, Banking and the Financial System Measuring GDP and Economic Growth Unemployment Inflation Income Distribution and Poverty International Finance Fiscal Policy and many more.... Course 09: Internal Audit Training Diploma Auditing as a Form of Assurance Internal Audit Procedures Technology-based Internal Audit Audit Interviews Reporting Audit Outcome UK Internal Audit Standards Career as an Auditor and many more.... Course 10: Forex Trading Level 3 Introduction to Forex Trading Kinds of Foreign Exchange Market Money Management Fundamental Analysis Technical Analysis Pitfalls and Risks Managing Risk and many more.... Course 11: Stock Market Investing for Beginners Module 01: Introduction to the Course Module 02: Introduction to Stocks Module 03: Money Required for Primary Investment Module 04: Opening an Investment Account Module 05: Brokerage Account Walkthrough Module 06: Finding Winning Stocks Module 07: Earning from Dividends Module 08: Diversifying Portfolio Module 09: Investment Plan Module 10: Rebalancing Portfolio Module 11: Understanding Order Types Module 12: Investment Tax Module 13: Investment Rules: Rule-1, 2, 3, 4, 5 Module 14: Stock Market Dictionary Module 15: Setting Up the Trading Platform Course 12: Fraud Management & Anti Money Laundering Awareness Complete Diploma Introduction to Money Laundering Proceeds of Crime Act 2002 Risk-based Approach Customer Due Diligence Record Keeping Suspicious Conduct and Transactions Awareness and Training and many more.... Course 13: Commercial Law 2021 Introduction of Commercial law Sales of Goods Law Consumer Law and Protection E-Commerce Law Competition Law and many more.... Course 14: Level 2 Microsoft Office Essentials Excel 2016 Getting Started with Microsoft Office Excel 2016 Performing Calculations Modifying a Worksheet Printing Workbooks Managing Workbooks Word 2016 Getting Started with Word Working More Efficiently Managing Lists Inserting Graphic Objects Controlling Page Appearance Preparing to Publish a Document Workbooks - Microsoft Word 2016 (Beginner) PowerPoint 2016 Presentation Basics Inserting Options Working with Objects Access 2016 Introduction to Access Access Forms Working with Reports and many more.... CPD 145 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this Financial Advisor bundle. Requirements Our Financial Advisor course is fully compatible with PCs, Macs, laptops, tablets and Smartphone devices. Career path Having this Financial Advisor expertise will increase the value of your CV and open you up to multiple job sectors. Certificates Certificate of completion Digital certificate - Included You will get the PDF Certificate for the title course (Financial Advisor) absolutely Free! Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Financial Advisor) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

Reiki Level 2 Practitioner Online Course
By Margaret Driscoll Cook - Learn More About Reiki
I am a Reiki Teacher in Manchester and one of the few traditionally trained Reiki Masters in the UK who have been trained by international best-selling Reiki author Penelope Quest. My teaching methods use traditional Reiki techniques perfected over many years and you can be assured of my support during and after your course. I teach all three levels of Reiki courses, level 1 reiki. level 2 reiki and reiki master level 3

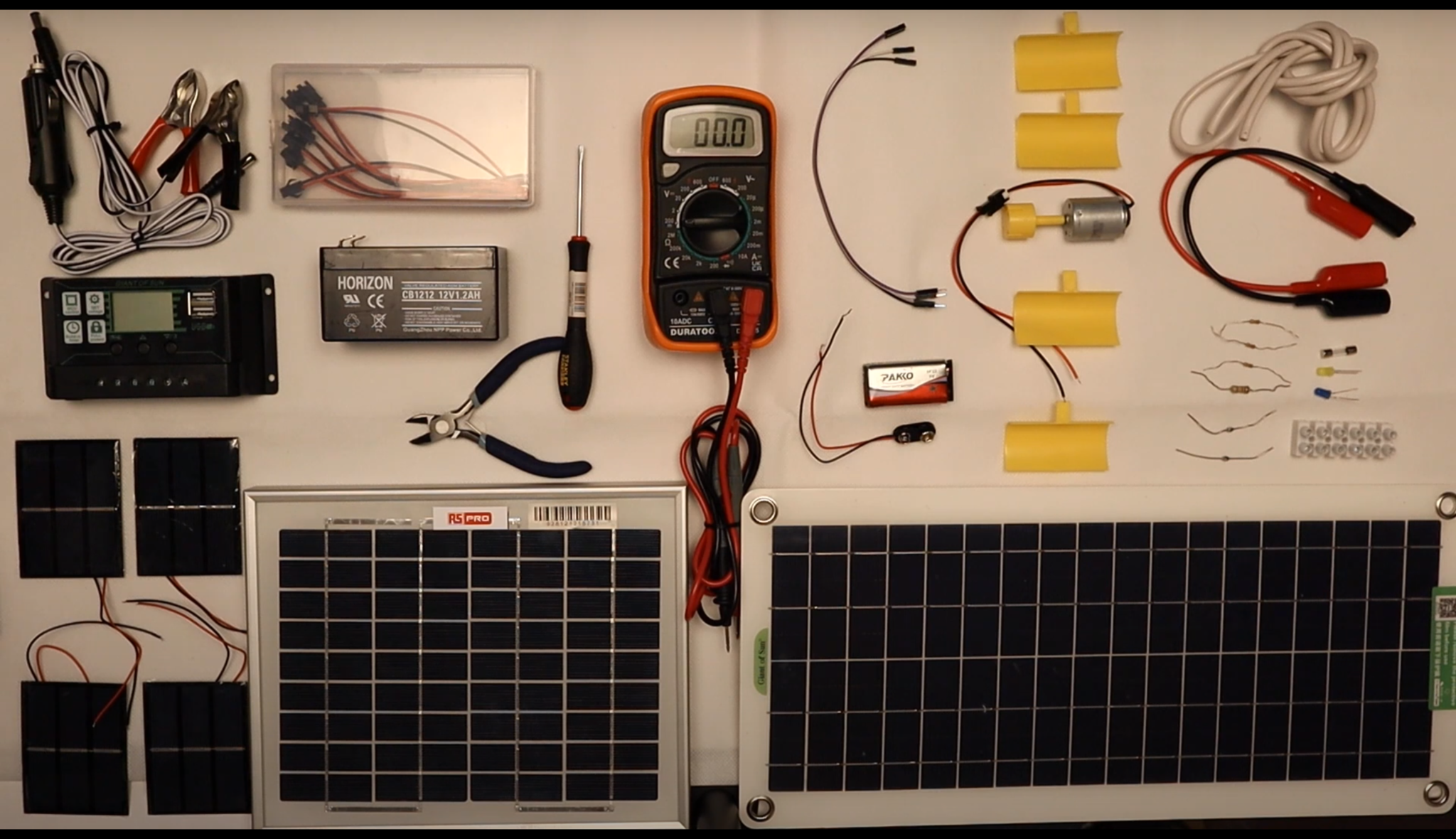
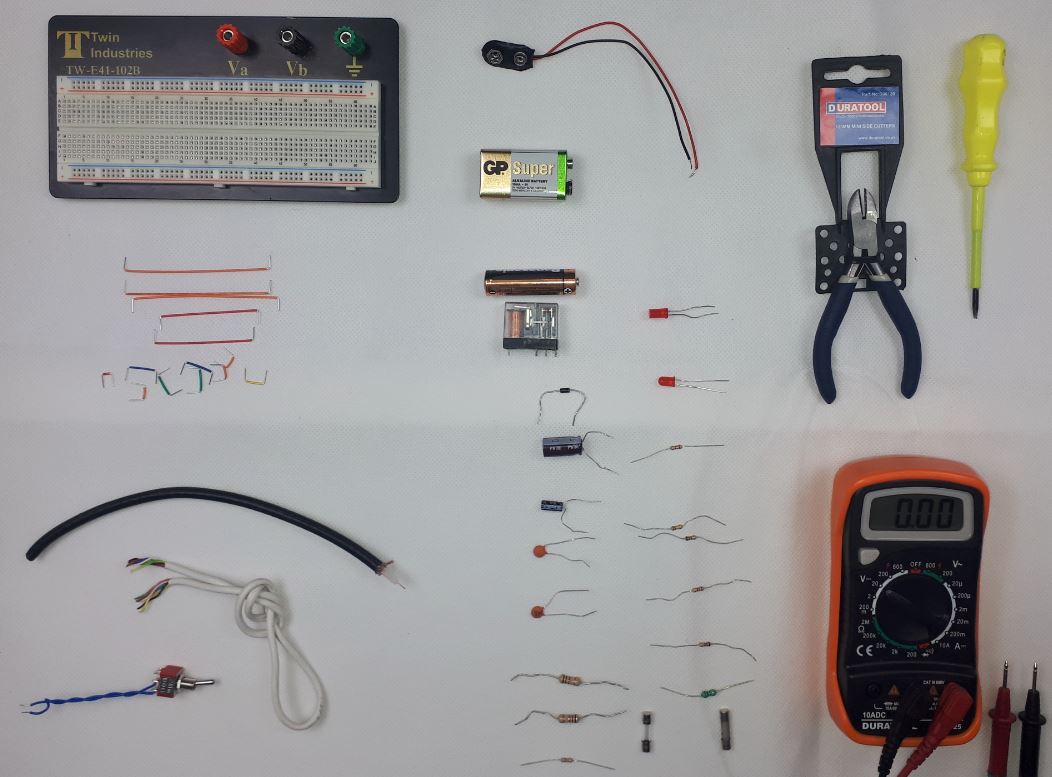
Alternative Energy Technology Course
By Hi-Tech Training
The Alternative Energy Technology Course is a practically based alternative energy course designed to give participants an understanding of alternative energy options and provide them with that practical knowledge and skills to build solar to electric and wind to electric systems at a foundation level. The course is designed to be of benefit to people either working or intending to work as:- Alternative Energy Installers or anyone just wishing to gain practical knowledge of Practical Alternative Energy Systems