- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Safety Showers & Eye Washes Training
By Compete High
ð¿ð§ Master Safety Protocols with Safety Showers & Eye Washes Training! ð¼ð©âð¬ Are you ready to ensure workplace safety and emergency preparedness? Enroll in our comprehensive Safety Showers & Eye Washes Training course today! This text-based course is meticulously designed to equip you with the essential knowledge and skills needed to handle emergency situations involving hazardous materials and chemicals. With our expert-led training, you'll gain the confidence and competence to respond effectively to emergencies, ensuring the well-being of yourself and your colleagues. Why Take Our Safety Showers & Eye Washes Training Course? ð Learn Essential Safety Protocols: Gain a thorough understanding of safety protocols and procedures related to safety showers and eye washes. From activation to decontamination, you'll learn the critical steps to take in emergency situations. ð¡ï¸ Ensure Workplace Safety: Enhance workplace safety by equipping yourself with the knowledge to effectively handle hazardous materials and chemicals. By being prepared for emergencies, you can minimize the risk of injury and promote a safer work environment. ð¼ Meet Regulatory Requirements: Our course covers regulatory requirements and industry standards related to safety showers and eye washes. By staying compliant with regulations, you can avoid fines and legal liabilities while prioritizing employee safety. ð Boost Confidence and Competence: With our expert-led training, you'll boost your confidence and competence in responding to emergency situations. Whether you're a new employee or a seasoned professional, our course provides valuable insights and practical skills. ð Who is This For? ð©âð¬ Laboratory Technicians: Laboratory technicians working with hazardous materials and chemicals can benefit from our Safety Showers & Eye Washes Training course to ensure their safety and the safety of their colleagues. ð¢ Facility Managers: Facility managers responsible for workplace safety can enhance their knowledge and skills by enrolling in our course. By understanding safety protocols related to safety showers and eye washes, they can better protect employees and comply with regulations. ð¨âð¬ Chemical Engineers: Chemical engineers working in manufacturing or research facilities can benefit from our course to ensure they are prepared to handle emergency situations involving hazardous materials. ð·âï¸ Safety Officers: Safety officers tasked with implementing safety protocols and procedures can enhance their expertise with our comprehensive training course. By staying informed and trained, they can effectively manage workplace safety initiatives. Career Path ð¬ Laboratory Safety Specialist: With advanced training and experience in safety protocols, you could pursue a career as a laboratory safety specialist, ensuring the safe handling of hazardous materials and chemicals in laboratory settings. ð Safety Manager: By demonstrating expertise in workplace safety, you could advance into a role as a safety manager overseeing safety initiatives and protocols within a company or organization. ð Regulatory Compliance Officer: With in-depth knowledge of regulatory requirements, you could pursue a career as a regulatory compliance officer, ensuring that organizations adhere to safety standards and regulations. FAQs Q: Is this course suitable for beginners? A: Yes, our Safety Showers & Eye Washes Training course is designed to accommodate learners of all levels, including beginners. Our comprehensive curriculum covers essential safety protocols and procedures, making it accessible to individuals with varying levels of experience. Q: How long does the course take to complete? A: The duration of the course may vary depending on your learning pace and schedule. On average, learners typically complete the course within a few hours to a few days, but you can progress through the material at your own pace. Q: Is there an assessment or certification upon completion? A: Yes, upon successful completion of the course, you will receive a certificate of completion, validating your knowledge and skills in safety showers and eye washes protocols. This certification can be a valuable addition to your professional portfolio. Q: Are there any prerequisites for enrolling in the course? A: There are no specific prerequisites for enrolling in our Safety Showers & Eye Washes Training course. However, a basic understanding of workplace safety concepts may be beneficial. Course Curriculum Module 1 Introduction to Safety Showers and Eye Washes Introduction to Safety Showers and Eye Washes 00:00 Module 2 Types of Safety Showers and Eye Washes Types of Safety Showers and Eye Washes 00:00 Module 3 Installation and Maintenance of Safety Showers and Eye Washes Installation and Maintenance of Safety Showers and Eye Washes 00:00 Module 4 Using Safety Showers and Eye Washes Using Safety Showers and Eye Washes 00:00 Module 5 Testing and Inspecting Safety Showers and Eye Washes Testing and Inspecting Safety Showers and Eye Washes 00:00 Module 6 Emergency Procedures Emergency Procedures 00:00 Module 7 Chemical Handling Safety Chemical Handling Safety 00:00 Module 8 Fire Safety Fire Safety 00:00

Complete Solidworks Training: Beginner to Advanced
By Compete High
ð Unlock Your Design Potential with 'Complete Solidworks Training: Beginner to Advanced' ð Are you ready to transform your engineering and design skills? Dive into the world of 3D modeling and product design with our comprehensive online course - 'Complete Solidworks Training: Beginner to Advanced.' Whether you're just starting or looking to master advanced techniques, this course is your gateway to becoming a Solidworks pro. Here's a sneak peek into what each module has in store for you: ð Module 1: Slides Get familiar with the Solidworks interface and set the stage for your learning journey. ð Module 2: Introduction Understand the core concepts of Solidworks and how it revolutionizes the design process. ð Module 3: Sketch Tools Master the art of sketching in Solidworks to lay the foundation for your 3D models. ð© Module 4: Random Part 2 Dive into creating random parts and elevate your design skills. ð Module 5: Random Screw Learn the intricacies of designing screws and fasteners for practical applications. ð Module 6: Flange Explore the Flange tool to create sheet metal components with precision. ð ï¸ Module 7: Assembly Interface Grasp the essentials of assembling parts seamlessly, a crucial skill for any designer. ï¸ Module 8: Crank Mechanism Delve into the complexities of designing a crank mechanism, enhancing your engineering prowess. ð¾ Module 9: Soda Bottle Bring your creativity to life by designing a realistic soda bottle using Solidworks. 𥤠Module 10: Soda Can Extend your beverage packaging design skills with a detailed study on soda can creation. ð© Module 11: Bearing Parts 1,2,3 Unravel the intricacies of bearing design, from individual parts to the complete assembly. ð§ Module 12: Jet Engine Parts, Casing, and Assembly Take your skills to new heights by designing jet engine components and mastering assembly techniques. ð Module 13: Rocket, Rocket Assembly Conclude your journey with a blast! Design a rocket and assemble it, showcasing your newfound Solidworks expertise. ⨠Why Choose Our Course? Comprehensive Curriculum: Covering everything from basics to advanced assemblies, ensuring no aspect is left untouched. Hands-On Projects: Apply your knowledge with real-world projects, making the learning experience practical and engaging. Expert Instruction: Learn from seasoned professionals with years of experience in Solidworks and product design. Lifetime Access: Access the course content anytime, anywhere, and revisit the material as needed. Ready to embark on your Solidworks adventure? Enroll now and revolutionize your design capabilities! ðð Course Curriculum Lecture 01 Draft Lesson 00:00 Lecture 02 Introduction 00:00 Lecture 03 Sketch Tools 00:00 Lecture 04 Random Part 2 00:00 Lecture 05 Random Screw (2) 00:00 Lecture 06 Flange 00:00 Lecture 07 Assembly Interface 00:00 Lecture 08 Crank Mechanism 00:00 Lecture 09 Soda Bottle 00:00 Lecture 10 Soda Can 00:00 Lecture 11 Bearing Parts 1 00:00 Bearing Parts 2 00:00 Bearing Assembly 00:00 Lecture 12 Jet Endgine Parts 1 00:00 Jet Engine Casing and Assembly 00:00 Lecture 13 Rocket 00:00 Rocket Assembly 00:00

Occupational Health and Safety
By Compete High
Overview ð§ Unlock a Safe and Thriving Work Environment with Our Occupational Health and Safety Course! ð Are you ready to elevate your career to new heights while ensuring the safety and well-being of your colleagues and workplace? Look no further! Our comprehensive Occupational Health and Safety Course is your ticket to mastering the essential skills and knowledge needed to create a secure and healthy work environment. ï¸ Why Occupational Health and Safety Matters ï¸ In today's fast-paced and dynamic work environments, prioritizing occupational health and safety isn't just a legal obligation-it's a moral imperative. Businesses that neglect safety protocols risk facing severe consequences, including legal liabilities, financial losses, and, most importantly, harm to employees. By investing in proper training, individuals and organizations can mitigate risks, prevent accidents, and foster a culture of safety and well-being. ð What You'll Gain from Our Course ð ð£ Frequently Asked Questions (FAQs) ð£ Q: What is Occupational Health and Safety (OHS)? A: Occupational Health and Safety (OHS) refers to the practice of ensuring the health, safety, and welfare of individuals engaged in work or employment. It involves identifying and addressing workplace hazards, implementing safety measures, and complying with relevant regulations to prevent accidents, injuries, and illnesses. Q: Why is Occupational Health and Safety important? A: Occupational Health and Safety is important for several reasons. Firstly, it helps protect the physical and mental well-being of employees, reducing the risk of work-related injuries and illnesses. Secondly, it enhances productivity and efficiency by creating a safe and conducive work environment. Lastly, it ensures compliance with legal requirements and helps organizations avoid costly penalties and liabilities associated with workplace accidents. Q: Who should take an Occupational Health and Safety course? A: Occupational Health and Safety courses are suitable for a wide range of professionals across industries, including safety officers, human resources managers, facility managers, operations supervisors, health and safety consultants, and small business owners. Anyone responsible for workplace safety or seeking to establish a career in occupational health and safety can benefit from such training. Q: What will I learn in an Occupational Health and Safety course? A: In an Occupational Health and Safety course, you will learn essential concepts, regulations, and best practices related to workplace safety. Topics typically covered include hazard identification, risk assessment, safety legislation, emergency response procedures, safety management systems, and workplace ergonomics. Q: How will completing an Occupational Health and Safety course benefit my career? A: Completing an Occupational Health and Safety course can benefit your career in several ways. It enhances your knowledge and skills in safety management, making you a valuable asset to employers. It also increases your employability and opens up opportunities for advancement in roles such as safety manager, occupational health specialist, compliance officer, and risk analyst. Q: Is certification required to work in Occupational Health and Safety? A: While certification is not always mandatory, it is highly recommended for professionals working in Occupational Health and Safety. Certification demonstrates your competence and commitment to workplace safety, increasing your credibility and marketability in the field. Many employers prefer to hire certified individuals for roles involving safety management and compliance. ð£ Frequently Asked Questions (FAQs) ð£ Q: What is Occupational Health and Safety (OHS)? A: Occupational Health and Safety (OHS) refers to the practice of ensuring the health, safety, and welfare of individuals engaged in work or employment. It involves identifying and addressing workplace hazards, implementing safety measures, and complying with relevant regulations to prevent accidents, injuries, and illnesses. Q: Why is Occupational Health and Safety important? A: Occupational Health and Safety is important for several reasons. Firstly, it helps protect the physical and mental well-being of employees, reducing the risk of work-related injuries and illnesses. Secondly, it enhances productivity and efficiency by creating a safe and conducive work environment. Lastly, it ensures compliance with legal requirements and helps organizations avoid costly penalties and liabilities associated with workplace accidents. Q: Who should take an Occupational Health and Safety course? A: Occupational Health and Safety courses are suitable for a wide range of professionals across industries, including safety officers, human resources managers, facility managers, operations supervisors, health and safety consultants, and small business owners. Anyone responsible for workplace safety or seeking to establish a career in occupational health and safety can benefit from such training. Q: What will I learn in an Occupational Health and Safety course? A: In an Occupational Health and Safety course, you will learn essential concepts, regulations, and best practices related to workplace safety. Topics typically covered include hazard identification, risk assessment, safety legislation, emergency response procedures, safety management systems, and workplace ergonomics. Q: How will completing an Occupational Health and Safety course benefit my career? A: Completing an Occupational Health and Safety course can benefit your career in several ways. It enhances your knowledge and skills in safety management, making you a valuable asset to employers. It also increases your employability and opens up opportunities for advancement in roles such as safety manager, occupational health specialist, compliance officer, and risk analyst. Q: Is certification required to work in Occupational Health and Safety? A: While certification is not always mandatory, it is highly recommended for professionals working in Occupational Health and Safety. Certification demonstrates your competence and commitment to workplace safety, increasing your credibility and marketability in the field. Many employers prefer to hire certified individuals for roles involving safety management and compliance. Course Curriculum Module 01 What is Construction Management Module 01 What is Construction Management 00:00 Module 02 Construction Operations and Job Site Management Module 02 Construction Operations and Job Site Management 00:00 Module 03 Project Performance, Quality _ Safety Module 03 Project Performance, Quality _ Safety 00:00 Module 04 Health and Safety Management Module 04 Health and Safety Management 00:00 Module 05 Engineering Safety Module 05 Engineering Safety 00:00 Module 06 Fire and Electrical Safety Module 06 Fire and Electrical Safety 00:00 Module 07 Occupational Health and Personal Protective Equipment Module 07 Occupational Health and Personal Protective Equipment 00:00

Level 3 Health and Safety in the Workplace - CPD Certified Diploma
By Compete High
ð Unlock Your Potential with Level 3 Health and Safety in the Workplace Course! ð Are you ready to elevate your career and become a safety champion in your workplace? Look no further! Our Level 3 Health and Safety in the Workplace course is designed to equip you with the essential knowledge and skills to ensure a safe and healthy working environment for yourself and your colleagues. ð Benefits of Taking Our Course ð Enhanced Safety Awareness: Gain a comprehensive understanding of occupational health and safety principles, regulations, and best practices. You'll learn how to identify and mitigate workplace hazards effectively. Reduced Risks: By mastering risk assessment techniques and emergency procedures, you'll be empowered to minimize workplace accidents and injuries, creating a safer environment for everyone. Legal Compliance: Stay ahead of the curve by staying updated on the latest health and safety legislation. Our course will ensure you understand your legal obligations as an employer or employee, helping you avoid costly penalties and legal issues. Improved Confidence: Armed with knowledge and expertise, you'll approach your work with confidence, knowing that you have the skills to handle any safety-related challenges that may arise. Career Advancement: Stand out in the job market and open doors to new opportunities. Employers highly value candidates with strong health and safety credentials, making you a desirable asset to any organization. Peace of Mind: Whether you're a seasoned professional or new to the field, our course provides you with the peace of mind that comes from knowing you're equipped to protect yourself and others in the workplace. Who is this for? ð¨âð¼ð©âð¼ Our Level 3 Health and Safety in the Workplace course is suitable for individuals across various industries and job roles, including: Managers and supervisors Human resources professionals Safety officers and representatives Health and safety consultants Workers in high-risk environments No matter your background or experience level, if you're committed to ensuring a safe and healthy workplace, this course is for you! Career Path ð¤ï¸ Completing our Level 3 Health and Safety in the Workplace course opens up a world of opportunities in the field of occupational health and safety. Here are just a few potential career paths you can pursue: Health and Safety Manager: Lead safety initiatives within organizations, develop policies and procedures, and oversee compliance efforts to ensure a safe working environment. Safety Consultant: Provide expert guidance to businesses on health and safety matters, conducting assessments, offering recommendations, and assisting with regulatory compliance. Risk Manager: Identify and assess potential risks within organizations, develop strategies to mitigate those risks, and ensure compliance with relevant safety standards and regulations. Occupational Health Specialist: Focus on preventing and managing workplace injuries and illnesses, promoting employee wellness, and advocating for safe working conditions. Safety Trainer: Educate workers on safety protocols, procedures, and best practices, empowering them to play an active role in maintaining a safe workplace culture. Don't miss out on the opportunity to take your career to new heights with our Level 3 Health and Safety in the Workplace course! Enroll today and embark on your journey towards becoming a safety leader in your industry. ð FAQ (Frequently Asked Questions) for Level 3 Health and Safety in the Workplace Q1: What is the significance of Level 3 Health and Safety in the Workplace? Level 3 Health and Safety in the Workplace course is designed to provide participants with advanced knowledge and skills necessary to ensure a safe and healthy work environment. It covers a wide range of topics including risk assessment, hazard identification, emergency procedures, and legal responsibilities. Achieving this level of certification demonstrates competence in managing workplace health and safety effectively, which is crucial for protecting employees, complying with regulations, and minimizing risks of accidents or injuries. Q2: Who should consider taking the Level 3 Health and Safety in the Workplace course? This course is suitable for individuals in various industries and roles, including managers, supervisors, health and safety representatives, and anyone responsible for overseeing health and safety practices within the workplace. It is beneficial for those seeking to enhance their understanding of health and safety regulations, improve risk management skills, and contribute to creating a safer work environment for themselves and their colleagues. Q3: What topics are covered in the Level 3 Health and Safety in the Workplace course? The course curriculum typically includes modules on risk assessment, hazard control measures, health and safety legislation, accident investigation, emergency procedures, and promoting a positive safety culture. Participants will also learn about the importance of communication, consultation, and training in maintaining effective health and safety practices within the workplace. Q4: How is the Level 3 Health and Safety in the Workplace course assessed? Assessment methods may vary depending on the training provider, but they often include a combination of written examinations, practical assessments, and/or project work. Participants are evaluated on their understanding of key concepts, ability to apply health and safety principles to real-world scenarios, and compliance with relevant regulations and best practices. Q5: What are the potential benefits of completing the Level 3 Health and Safety in the Workplace course? Earning a Level 3 Health and Safety in the Workplace certification can lead to various benefits, including improved job prospects, enhanced credibility in the field of health and safety, better risk management skills, increased awareness of legal responsibilities, and ultimately, a safer and healthier work environment for all employees. Additionally, organizations may benefit from reduced accident rates, improved compliance with regulations, and enhanced reputation for prioritizing health and safety. Course Curriculum Module 01 Health and Safety Management Health and Safety Management 00:00 Module 02 Engineering Safety Engineering Safety 00:00 Module 03 Fire and Electrical Safety Fire and Electrical Safety 00:00 Module 04 Occupational Health and Personal Protective Equipment Occupational Health and Personal Protective Equipment 00:00 Module 05 Mental Healthcare Mental Healthcare 00:00 Module 06 Public Health Public Health 00:00 Module 07 Working at Height - Hazards and Control Working at Height - Hazards and Control 00:00 Module 08 Work Equipment Hazards and Control Work Equipment Hazards and Control 00:00 Module 09 Electrical Hazards and Control Electrical Hazards and Control 00:00 Module 10 Chemical and Biological Health Hazards and Control Chemical and Biological Health Hazards and Control 00:00 Module 11 Reporting Accidents and Incidents at Work Reporting Accidents and Incidents at Work 00:00 Module 12 Legal Framework (UK) for Workplace First Aid Legal Framework (UK) for Workplace First Aid 00:00 Module 13 Practice of self-hygiene Practice of self-hygiene 00:00 Module 14 HACCP Food Safety HACCP Food Safety 00:00 Module 15 A Guide to Safe Manual Handling A Guide to Safe Manual Handling 00:00 Module 16 Work Equipment Maintenance Work Equipment Maintenance 00:00 Module 17 Occupational Diseases Occupational Diseases 00:00 Module 18 Exposure to Mutagens Biological Agents and Carcinogens Exposure to Mutagens Biological Agents and Carcinogens 00:00 Module 19 Dangerous Occurrences Dangerous Occurrences 00:00 Module 20 RIDDOR Report RIDDOR Report 00:00

An Introduction to HTC
By NJV LTD BetaTeach
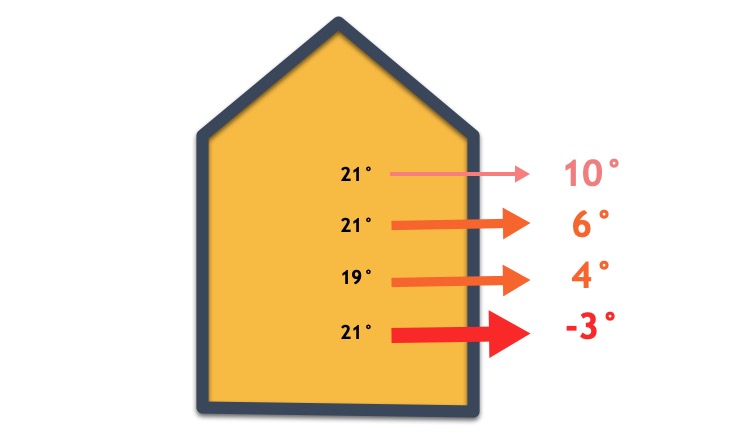
Understanding a buildings heat loss for heating engineers
COSHH Training
By Compete High
Product Overview: COSHH Training Course Course Title: COSHH Training - Control of Substances Hazardous to Health Introduction: The COSHH Training course is designed to provide comprehensive knowledge and understanding of the Control of Substances Hazardous to Health (COSHH) regulations. These regulations are vital for ensuring the safety and well-being of employees who work with or around hazardous substances. This course equips participants with the necessary skills to identify, assess, and control risks associated with hazardous substances in the workplace. Modules Overview: Module 1: Introduction to COSHH In this module, participants will gain a foundational understanding of the COSHH regulations, including its scope and legal requirements. Key topics covered include the definition of hazardous substances, responsibilities of employers and employees, and the importance of COSHH assessments. Module 2: Risk Assessment Module 2 focuses on the process of risk assessment in the context of COSHH. Participants will learn how to identify hazards, assess risks, and prioritize control measures. Practical techniques for conducting COSHH risk assessments will be discussed, along with the documentation and review processes involved. Module 3: Control Measures This module delves into the various control measures that can be implemented to minimize or eliminate exposure to hazardous substances. Participants will learn about engineering controls, administrative controls, and personal protective equipment (PPE). Case studies and real-world examples will be used to illustrate effective control measures in different workplace scenarios. Module 4: Emergency Procedures Module 4 covers the importance of emergency preparedness and response in dealing with incidents involving hazardous substances. Participants will learn how to recognize potential emergencies, evacuate safely, and implement emergency procedures. Training on the use of emergency equipment and communication protocols will also be provided. Module 5: Health Effects of Hazardous Substances The final module explores the health effects associated with exposure to hazardous substances. Participants will gain an understanding of the short-term and long-term health risks posed by different types of hazardous substances. Common symptoms of exposure and the importance of early detection and treatment will be discussed. Key Features: Interactive and engaging multimedia content. Practical exercises and case studies for hands-on learning. Quizzes and assessments to reinforce learning objectives. Expert instructors with extensive experience in occupational health and safety. Accessible anytime, anywhere via an online learning platform. Who Should Attend: The COSHH Training course is suitable for employees who work with or around hazardous substances, including but not limited to: Laboratory technicians Manufacturing workers Construction workers Healthcare professionals Facilities managers Health and safety officers Conclusion: With its comprehensive coverage of COSHH regulations and practical guidance on risk assessment, control measures, emergency procedures, and health effects, the COSHH Training course equips participants with the knowledge and skills needed to ensure a safe and healthy work environment in compliance with regulatory requirements. Course Curriculum Module 1_ Introduction to COSHH. Introduction to COSHH. 00:00 Module 2_ Risk Assessment. Risk Assessment. 00:00 Module 3_ Control Measures. Control Measures. 00:00 Module 4_ Emergency Procedures. Emergency Procedures. 00:00 Module 5_ Health Effects of Hazardous Substances. Health Effects of Hazardous Substances. 00:00

Automotive Technology and Maintenance Online Course
By Compete High
ð Unlock Your Automotive Expertise with Our Automotive Technology and Maintenance Online Course! ð ï¸ Welcome to the future of automotive education! Our comprehensive online course is meticulously designed to empower enthusiasts, aspiring mechanics, and automotive professionals with the knowledge and skills needed to thrive in the dynamic world of automotive technology and maintenance. Module 1: Introduction Embark on your journey into the automotive realm with a solid foundation. Learn about the evolution of automobiles, industry trends, and the fundamental principles that govern modern automotive technology. This module sets the stage for an in-depth exploration of the intricacies of vehicular systems. Module 2: Automotive Mechanics Dive into the heart of automotive engineering! Understand the mechanics that power vehicles, from the basic principles of engine operation to the complexities of transmission systems. Gain hands-on insights into engine components, lubrication systems, and the dynamics that make cars move efficiently. Module 3: Automotive Electrical Systems Illuminate your understanding of automotive electronics! Explore the intricacies of electrical systems in vehicles, covering topics such as batteries, alternators, and wiring diagrams. Unravel the mysteries behind dashboard electronics and learn how to diagnose and troubleshoot electrical issues like a seasoned professional. Module 4: Electrical System Delve deeper into the electrical realm by exploring advanced topics like electronic control units (ECUs), sensors, and computerized systems. Grasp the nuances of vehicle communication networks and understand how these technologies integrate to optimize performance, efficiency, and safety. Module 5: Cooling System Keep your cool with a detailed exploration of automotive cooling systems. Learn how engines maintain optimal temperatures, and gain the skills to identify and address cooling system malfunctions. From radiators to thermostats, this module equips you to keep engines running smoothly. Module 6: Fuel System Fuel your expertise in automotive fuel systems! Understand the intricacies of fuel injection, carburetion, and fuel delivery systems. Master the art of diagnosing fuel-related issues and optimizing engine performance for maximum efficiency. Module 7: Electrical System Revisit the electrical system with a focus on advanced techniques and emerging technologies. Explore topics like hybrid and electric vehicle systems, preparing yourself for the future of automotive innovation. ð Why Choose Our Course? Flexible Learning: Access modules at your own pace, anytime, anywhere. Expert Instruction: Learn from industry professionals with extensive experience. Interactive Content: Engage in hands-on activities and simulations for practical learning. Certification: Receive a recognized certificate upon course completion. Gear up for success in the automotive industry! Enroll in our Automotive Technology and Maintenance Online Course today and drive your career to new heights! ðð§ð Course Curriculum Module 1_ Introduction Introduction 00:00 Module 2_ Automotive Mechanics Automotive Mechanics 00:00 Module 3_ Automotive Electrical Systems Automotive Electrical Systems 00:00 Module 4_ Electrical System Electrical System 00:00 Module 5_ Cooling System Cooling System 00:00 Module 6_ Fuel System Fuel System 00:00 Module 7_ Electrical System Electrical System 00:00

Chemistry - CPD Certified Level 2
By Compete High
ð¬ Unlock the Secrets of Chemistry - CPD Certified Level 2 Course! ð¬ Are you ready to dive into the captivating world of chemistry and unlock a world of opportunities? Look no further! Our Chemistry - CPD Certified Level 2 Course is your gateway to understanding the fundamental principles of this fascinating science. Whether you're a budding scientist, an educator, or simply curious about the building blocks of matter, this course is designed to empower you with essential knowledge and skills. ð Why Choose Our Chemistry - CPD Certified Level 2 Course? Comprehensive Curriculum: Our course offers a well-rounded curriculum covering essential topics such as chemical reactions, atomic structure, the periodic table, and more. You'll gain a solid foundation in chemistry that will serve as a springboard for further exploration. Interactive Learning Experience: Say goodbye to dull lectures! Our course features engaging multimedia content, interactive quizzes, and practical experiments to reinforce your understanding of key concepts. Learning has never been this fun and immersive! CPD Certification: Upon successful completion of the course, you'll receive a CPD certification recognized internationally. This credential not only validates your knowledge but also enhances your credibility in the eyes of employers and peers. Flexibility and Convenience: Life is busy, but that shouldn't stand in the way of your education. Our course is designed with flexibility in mind, allowing you to learn at your own pace and on your schedule. Whether you prefer to study during lunch breaks or late at night, we've got you covered. Expert Guidance: You'll be guided every step of the way by experienced instructors who are passionate about chemistry and dedicated to your success. Have questions or need clarification? Our support team is always here to help. ð©âð¬ Who is this for? Our Chemistry - CPD Certified Level 2 Course is perfect for: Students aspiring to pursue higher education or careers in science-related fields. Educators seeking to enhance their knowledge of chemistry and improve their teaching skills. Professionals looking to expand their skillset and stay updated with the latest developments in chemistry. Anyone with a curious mind and a desire to understand the world at the molecular level. ð Career Path With a solid understanding of chemistry gained from our CPD Certified Level 2 Course, the possibilities are endless. You could embark on a rewarding career in: Pharmaceutical research and development Chemical engineering Environmental science Forensic science Food and beverage industry Teaching and academia Whether you're dreaming of curing diseases, developing innovative technologies, or simply making a positive impact on the world, a strong foundation in chemistry is your ticket to success. Don't let this opportunity pass you by! Enroll in our Chemistry - CPD Certified Level 2 Course today and take the first step towards a brighter future filled with endless possibilities. Unlock the mysteries of the universe and ignite your passion for science! ð Course Curriculum Module 1_ Basics of Chemistry Basics of Chemistry 00:00 Module 2_ Chemical Bonding and Reactions Chemical Bonding and Reactions 00:00 Module 3_ Gases and Solutions Gases and Solutions 00:00 Module 4_ Acids, Bases, and Chemical Kinetics Acids, Bases, and Chemical Kinetics 00:00 Module 5_ First and Second Law of Thermodynamics First and Second Law of Thermodynamics 00:00 Module 6_ Electrochemistry and Organic Chemistry Electrochemistry and Organic Chemistry 00:00

Biology - A Complete Guide
By Compete High
ð¿ Unlock the Wonders of Life with 'Biology - A Complete Guide' Online Course! 𧬠Are you fascinated by the intricacies of life, eager to unravel the mysteries of the natural world? Dive into the captivating realm of biology with our comprehensive online course - 'Biology - A Complete Guide.' Whether you're a student striving for academic excellence, a curious mind seeking knowledge, or a professional looking to broaden your understanding, this course is your gateway to a profound exploration of life sciences. ð What's Inside? Explore the Ten Enlightening Modules: Module 1: Introduction to Basic Biology ð± Lay the foundation with an overview of the fundamental principles and concepts in biology. Understand the language of life and its basic building blocks. Module 2: Biological Molecules 𧪠Dive into the microscopic world of biological molecules, exploring the essential components that form the basis of life. Uncover the secrets hidden within DNA, RNA, proteins, and more. Module 3: Taxonomy of Organisms ð¦ Embark on a journey through the diverse kingdoms of life. Learn the art and science of classifying organisms, understanding their relationships and significance in the grand tapestry of life. Module 4: Cell and Tissue of Organism ð¬ Explore the fundamental unit of life - the cell. Understand cellular structures, functions, and the intricate world of tissues that form the foundation of all living organisms. Module 5: Transport System in Organisms ð¨ Investigate the fascinating mechanisms that enable organisms to transport essential substances. From simple diffusion to complex circulatory systems, grasp the intricate network of life's transportation. Module 6: Bioenergetics Unravel the mysteries of energy flow in living organisms. Dive into the principles of metabolism, photosynthesis, and cellular respiration that power the vibrant dance of life. Module 7: Food, Nutrition, and Digestion ð Delve into the science of sustenance. Explore the processes of digestion, absorption, and nutrient utilization, understanding how organisms fuel their life processes. Module 8: Genetics and Evolution 𧬠Peer into the blueprint of life itself. Uncover the secrets of heredity, genetic variation, and the driving force behind the diversity of life - evolution. Module 9: Ecology ð Explore the delicate balance of ecosystems, understanding the interdependence of living organisms with their environment. Grasp the concepts of biodiversity, conservation, and sustainable living. Module 10: Biotechnology 𧫠Step into the future with biotechnology. Discover how scientific advancements are shaping the world, from genetic engineering to the ethical considerations surrounding modern biotech. ð Why Choose 'Biology - A Complete Guide'? ð Expertly Crafted Content: Developed by seasoned biologists and educators. ð» Convenient Online Learning: Study at your own pace, anytime, anywhere. ð Comprehensive Resources: Access a wealth of materials, quizzes, and interactive content. ð Join a Community: Connect with fellow learners, share insights, and enhance your understanding. ð Embark on Your Biology Journey Today! Enroll in 'Biology - A Complete Guide' and Unlock the Secrets of Life! ð Course Curriculum Module 1 Introduction to Basic Biology Introduction to Basic Biology 00:00 Module 2 Biological Molecules Biological Molecules 00:00 Module 3 Taxonomy of Organisms Taxonomy of Organisms 00:00 Module 4 Cell and Tissue of Organism Cell and Tissue of Organism 00:00 Module 5 Transport system in organisms Transport system in organisms 00:00 Module 6 Bioenergetics Bioenergetics 00:00 Module 7 Food, Nutrition and Digestion Food, Nutrition and Digestion 00:00 Module 8 Genetics and Evolution Module 8 Genetics and Evolution 00:00 Module 9 Ecology Ecology 00:00 Module 10 Biotechnology Biotechnology 00:00

Geology
By Compete High
Uncover Earth's Secrets with Our Geology Course ð Are you ready to embark on an exciting journey deep into the heart of our planet? Look no further than our comprehensive Geology course! ðï¸ Delve into the mysteries of Earth's formation, its dynamic processes, and the incredible forces that shape our world every day. Why Choose Our Geology Course? ð Explore the Wonders of the Earth: Geology isn't just about rocks and minerals-it's a captivating study of the Earth's history, its landscapes, and the fascinating stories written in its layers. ð Discover Hidden Treasures: Uncover the secrets hidden beneath the surface as you learn about the forces of erosion, tectonic plate movements, volcanic activity, and so much more. ð Expert Guidance: Our course is crafted by seasoned geologists and educators who are passionate about sharing their knowledge and expertise with you. Get ready for an immersive learning experience! ð Hands-on Learning: From field trips to virtual simulations, our course offers hands-on experiences that bring geology to life. Whether you're studying the formation of mountains or examining fossils, you'll have the opportunity to get up close and personal with Earth's wonders. ð¡ Practical Applications: Geology isn't just an academic pursuit-it's a field with real-world applications. Gain insights into how geological knowledge is used in industries such as mining, environmental conservation, and natural resource management. Who is this for? Our Geology course is perfect for: Students: Whether you're studying earth sciences, geography, or simply have a passion for understanding the world around you, our course will deepen your understanding of the Earth's processes. Professionals: Are you working in fields such as environmental science, civil engineering, or resource exploration? Our Geology course provides valuable insights that can enhance your expertise and career prospects. Curious Minds: If you've ever looked at a mountain or a rock formation and wondered about its story, this course is for you! Geology is a fascinating subject that appeals to anyone with a sense of curiosity about the natural world. Career Path A Geology course opens doors to a wide range of exciting career opportunities, including: ðï¸ Environmental Consultant: Help businesses and organizations navigate environmental regulations and assess the impact of human activities on natural landscapes. ï¸ Geologist: Work in fields such as mineral exploration, oil and gas extraction, or geological surveys, contributing to our understanding of Earth's resources and structures. ð¿ Environmental Scientist: Study the interactions between human activities and the natural environment, working to protect ecosystems and promote sustainability. ð Park Ranger: Combine your love of the outdoors with your knowledge of geology by working in national parks or protected areas, educating visitors and preserving natural landscapes. ð Data Analyst: Analyze geological data to identify patterns, trends, and potential risks, contributing to informed decision-making in various industries. FAQ Q: Is this course suitable for beginners? A: Absolutely! Our Geology course is designed to accommodate learners of all levels, from beginners to advanced students. Our instructors provide clear explanations and support to help you grasp the fundamentals of geology. Q: What materials do I need for this course? A: All you need is a curious mind and a passion for exploring the natural world! While specific materials may vary depending on the course format, we'll provide you with everything you need to succeed, whether it's textbooks, online resources, or field trip equipment. Q: Can I take this course online? A: Yes! Our Geology course offers both in-person and online learning options to accommodate your schedule and preferences. Experience the thrill of discovery from the comfort of your own home or join us in the field for hands-on exploration-it's up to you! Q: Will this course help me find a job in the field of geology? A: While completion of our Geology course is not a guarantee of employment, it provides valuable knowledge and skills that can enhance your career prospects in geology-related fields. Networking opportunities, practical experience, and a solid understanding of geological principles can help you stand out to potential employers. Enroll Today and Uncover the Secrets of the Earth! Don't miss out on the opportunity to explore the wonders of geology and gain a deeper appreciation for the world beneath your feet. Enroll in our Geology course today and embark on a journey of discovery that will expand your horizons and ignite your passion for the natural world! ð Course Curriculum Module 1 Introduction to Geology. Introduction to Geology. 00:00 Module 2 Earths Structure and Plate Tectonics. Earth_s Structure and Plate Tectonics. 00:00 Module 3 Surface Processes and Landscape Evolution. Surface Processes and Landscape Evolution. 00:00 Module 4 Earths Interior and Geophysical Processes. Earth_s Interior and Geophysical Processes. 00:00 Module 5 Earth Materials and Minerals. Earth Materials and Minerals. 00:00 Module 6 Geological Time and Earth_s History. Geological Time and Earth_s History. 00:00
