- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Golf Cart Safety (Misc) Online Training
By Compete High
â³ Drive Safely, Drive Smart: Golf Cart Safety (Misc) Online Training! ðï¸âï¸ Are you ready to ensure safety on the golf course? Enroll in our Golf Cart Safety (Misc) Online Training, a comprehensive program designed to equip you with the knowledge and skills needed to navigate golf carts safely and responsibly. Join us on a journey where golfing meets safety, turning your time on the course into a secure and enjoyable experience. ð Module 1: Introduction to Golf Cart Safety Procedures Commence your training with Module 1, offering a comprehensive introduction to golf cart safety procedures. Learn the fundamentals of safe cart operation, etiquette, and rules to ensure a secure environment for golfers and staff alike. ð Module 2: Advanced Golf Cart Safety Preparedness and First Aid Elevate your safety preparedness with Module 2, focusing on advanced safety measures and first aid. Gain insights into responding to emergencies, understanding first aid for golf-related incidents, and ensuring a quick and effective response when needed. ð§ Module 3: Golf Cart Maintenance Considerations for Safe Practices Optimize your golf cart's performance with Module 3, dedicated to maintenance considerations for safe practices. Learn to conduct routine checks, identify potential issues, and establish a proactive approach to keeping golf carts in optimal condition. ð¦ï¸ Module 4: Golf Cart Safety in Weather Conditions and Accident Response Navigate varying conditions with Module 4, focusing on golf cart safety in different weather conditions and accident response. Explore strategies for safe operation during adverse weather, and understand the proper response to accidents to minimize risks. ð Module 5: Safe Storage Training and Awareness Ensure safe storage practices with Module 5, where you'll receive training and awareness regarding the proper storage of golf carts. Explore best practices for securing carts, preventing unauthorized use, and promoting a secure storage environment. ð Module 6: Golf Cart Maintenance for Refresher and Final Assessment Cap off your training with Module 6, offering a refresher on golf cart maintenance. Review key concepts, solidify your understanding, and undertake a final assessment to ensure mastery of golf cart safety procedures. ð Why Choose Our Golf Cart Safety (Misc) Online Training? Expert-Led Training: Learn from experienced golf safety professionals with expertise in golf cart operation and safety. Interactive Learning: Engage in practical simulations, real-world scenarios, and interactive exercises to apply theoretical knowledge. Customizable Training: Tailor the course to suit the specific needs of golf courses or organizations, ensuring maximum relevance. Compliance Assurance: Align with industry standards and regulations, promoting a culture of safety and responsibility. Don't let golf cart operation be a hazard on the course! Enroll now in the Golf Cart Safety (Misc) Online Training and empower yourself with the knowledge and skills needed to navigate golf carts safely and responsibly. Your journey to safer and more enjoyable golfing begins here! â³â¨ð Course Curriculum Module 1 Introduction to Golf Cart Safety Procedures Introduction to Golf Cart Safety Procedures 00:00 Module 2 Advanced Golf Cart Safety Preparedness and First Aid Advanced Golf Cart Safety Preparedness and First Aid 00:00 Module 3 Golf Cart Maintenance Considerations for Safe Practices Golf Cart Maintenance Considerations for Safe Practices 00:00 Module 4 Golf Cart Safety in Weather Conditions and Accident Response Golf Cart Safety in Weather Conditions and Accident Response 00:00 Module 5 Safe Storage Training and Awareness Safe Storage Training and Awareness 00:00 Module 6 Golf Cart Maintenance for Refresher and Final Assessment Golf Cart Maintenance for Refresher and Final Assessment 00:00

Business Writing
By Nexus Human
Duration 1 Days 6 CPD hours Writing is a key method of communication for most people, and it?s one that many people struggle with. This workshop will give participants a refresher on basic writing concepts (such as spelling, grammar, and punctuation), and an overview of the most common business documents (such as proposals, reports, and agendas), giving you that extra edge in the workplace. 1 - Getting Started Workshop Objectives Pre-Assignment Review 2 - Working with Words Spelling Grammar Creating a Cheat Sheet 3 - Constructing Sentences Parts of a Sentence Punctuation Types of Sentences 4 - Creating Paragraphs The Basic Parts Organization Methods 5 - Writing Meeting Agendas The Basic Structure Choosing a Format Writing the Agenda 6 - Writing E-mails Addressing Your Message Grammar and Acronyms 7 - Writing Business Letters The Basic Structure Choosing a Format Writing the Letter 8 - Writing Proposals The Basic Structure Choosing a Format Writing the Proposal 9 - Writing Reports The Basic Structure Choosing a Format Writing the Report 10 - Other Types of Documents Requests for Proposals Projections Executive Summaries Business Cases 11 - Proofreading and Finishing A Proofreading Primer How Peer Review Can Help Printing and Publishing 12 - Wrapping Up Words from the Wise Additional course details: Nexus Humans Business Writing training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Business Writing course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

This course aims to provide a gentle introduction to the expectations of the Early Years Foundation Stage and it can also act as a refresher for those wanting to update their knowledge. It will introduce you to some of the key documents and legislation that relate to Early Years providers, the process for registering with Ofsted and the various policies and procedures that need to be in place. It also covers learning and development requirements, how to observe and assess the progress of children in your care and the safeguarding and welfare requirements laid out in the EYFS Framework.

Food Hygiene Awareness
By Prima Cura Training
This course will provide all staff with an awareness of food hygiene. It also covers the recommended yearly refresher in Food Hygiene.

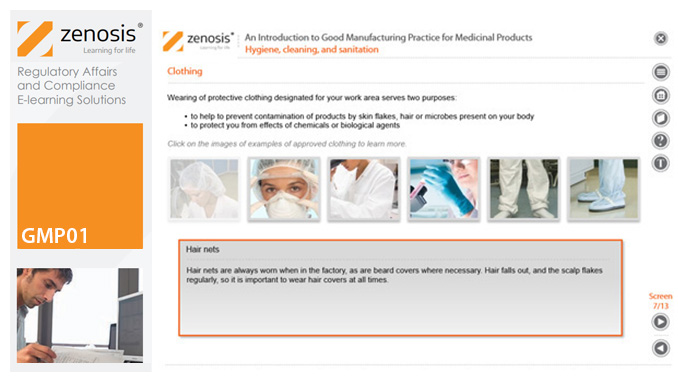
GMP01: An Introduction to Good Manufacturing Practice for Medicinal Products
By Zenosis
Good Manufacturing Practice (GMP) is a set of rules for medicines manufacturers to follow so that their products are safe, effective, and of good quality. The rules may be written into law or set out in guidance documents from regulatory authorities. Regulators will not allow medicinal products to be placed, or to remain, on the market in their country unless the products can be shown to be manufactured in compliance with GMP. To this end, they carry out inspections of manufacturing plants. Companies that persistently commit serious breaches of GMP requirements have suffered huge fines.
Computer Science and Programming Diploma
By iStudy UK
The Computer Science and Programming Diploma course covers the fundamental theories of Algorithm Analysis. If you want to explore the concepts and methods that make a good programmer, then the course is designed for you. Programming is all about how to solve a problem. Programming theory is not confined to a single language; rather it applies to all programming languages. By understanding the right programming theory, you will be able to analyse a problem and also able to find out the probable solution. The course teaches you these Programming theories covering Algorithm analysis, Binary Number System, Arrays and their Advantages, the process of analysing a problem, Nodes and their Importance, various sorting algorithms and their comparisons, and more. Upon completion, you will be able to understand the core theories of computer science. What Will I Learn? Understand the Fundamental Theories of Algorithm Analysis Be able to Compare Various Algorithms Understand When to use Different Data Structures and Algorithms Understand the Fundamentals of Computer Science theory Requirements A Willingness to Learn New Topics! No Prior Experience or Knowledge is Needed! Module: 01 Kurt Anderson - 1 Introduction FREE 00:01:00 Kurt Anderson - 2 Binary System FREE 00:11:00 Kurt Anderson - 3 Complexity Introduction 00:02:00 Kurt Anderson - 4 Math Refresher Logarithmic Functions 00:11:00 Kurt Anderson - 5 Math Refresher Factorial Functions.TS 007 00:03:00 Kurt Anderson - 6 Math Refresher Algebraic Expressions.TS 00:03:00 Kurt Anderson - 7 n-notation 00:19:00 Kurt Anderson - 8 Big O 00:13:00 Kurt Anderson - 9 Big O Real World Example 00:10:00 Module: 02 Kurt Anderson - 10 How is Data Stored 00:09:00 Kurt Anderson - 11 Fixed Arrays 00:20:00 Kurt Anderson - 12 Circular Arrays 00:08:00 Kurt Anderson - 13 Dynamic Arrays 00:16:00 Kurt Anderson - 14 Array Review 00:08:00 Kurt Anderson - 15 Array Real World Examples 00:06:00 Kurt Anderson - 16 Linked List 00:12:00 Kurt Anderson - 16 Nodes 00:04:00 Kurt Anderson - 17 Linked List Run Times 00:15:00 Kurt Anderson - 18 Doubly Linked Lists 00:08:00 Kurt Anderson - 19 Tail Pointer 00:05:00 Module: 03 Kurt Anderson - 20 Linked List Real World Examples 00:03:00 Kurt Anderson - 20 Stack Example 00:11:00 Kurt Anderson - 21 Linked List Review 00:04:00 Kurt Anderson - 22 Stacks 00:10:00 Kurt Anderson - 23 Queues 00:09:00 Kurt Anderson - 24 Queue Examples 00:10:00 Kurt Anderson - 25 Queue and Stack Run Times 00:06:00 Kurt Anderson - 26 Stack and Queues Real World Examples 00:07:00 Kurt Anderson - 27 Sorting Algorithm Introdcution 00:02:00 Kurt Anderson - 28 Bubble Sort 00:10:00 Kurt Anderson - 29 Selection Sort 00:10:00 Module: 04 Kurt Anderson - 30 Insertion Sort 00:09:00 Kurt Anderson - 31 Quick Sort 00:15:00 Kurt Anderson - 32 Quick Sort Run Times 00:10:00 Kurt Anderson - 33 Merge Sort 00:12:00 Kurt Anderson - 34 Merge Sort Run Times 00:08:00 Kurt Anderson - 35 Stable vs Nonstable 00:07:00 Kurt Anderson - 36 Sorting Algorithm Real World Examples 00:04:00 Kurt Anderson - 37 Basics of Trees 00:08:00 Kurt Anderson - 38 Binary Search Tree 00:09:00 Kurt Anderson - 39 BST Run Times 00:08:00 Module: 05 Kurt Anderson - 40 Tree Traversals 00:13:00 Kurt Anderson - 41 Tree Real World Examples 00:05:00 Kurt Anderson - 42 Heap Introduction 00:04:00 Kurt Anderson - 43 Heap Step by Step 00:12:00 Kurt Anderson - 44 Heap Real World Examples 00:07:00 Kurt Anderson - 45 Thank You 00:01:00

Network design training course description This course provides you with the knowledge needed to perform the design of a network infrastructure that supports desired network solutions to achieve effective performance, scalability, and availability. We recognise that the role of design does not normally require hands on skills but hands on sessions are used to reinforce the theory not to teach configuration or troubleshooting. What will you learn Create HA enterprise network designs. Develop optimum Layer 3 designs. Design effective modern WAN and data center networks. Develop effective migration approaches to IPv6. Create effective network security designs. Network design training course details Who will benefit: Anyone involved with network design. Prerequisites: TCP/IP Foundation for engineers Duration 5 days Network design training course contents Part I Reliable, resilient enterprise L2/3 network designOptimal Enterprise Campus Design:Enterprise campus design principles, hierarchy, modularity, flexibility, resiliency.EIGRP design:EIGRP Design, Should you use EIGRP?OSPF design: OSPF scalability designs, OSPF area design, OSPF Full-Mesh Design, OSPF Hub-and-Spoke Design, OSPF convergence design and optimization techniques. IS-IS Design:The protocol, IS-IS hierarchical architecture, IS-IS vs OSPF, IS-IS Deep Dive, IS-IS Design Considerations. BGP design:BGP overview, Designing Scalable iBGP Networks, BGP Route Reflector Design, Enhancing the Design of BGP Policies with BGP Communities, Case Study: Designing Enterprise wide BGP Policies Using BGP Communities, BGP Load-Sharing Design.Part II Enterprise IPv6 Design ConsiderationsIPv6 Design Considerations in the Enterprise: IPv6 Deployment and Design Considerations, Considerations for Migration to IPv6 Design, IPv6 Transition Mechanisms, Final Thoughts on IPv6 Transition Mechanisms. Challenges of the Transition to IPv6: IPv6 Services, Link Layer Security Considerations. Part III Modern Enterprise Wide-Area Networks DesignService Provider-Managed VPNs:Choosing Your WAN Connection, Layer 3 MPLS VPNs, Case Study: MPLS VPN Routing Propagation, Layer 2 MPLS VPN Services. Enterprise-Managed WANs: Enterprise-Managed VPNs, GRE, Multipoint GRE, Point-to-Point and Multipoint GRE, IPsec, IPsec and dynamic VTI, DMVPN, Case Study: EIGRP DMVPN, DMVPN and Redundancy, Case Study: MPLS/VPN over GRE/DMVPN, SSL VPN. Enterprise WAN Resiliency Design: WAN Remote-Site Overview, MPLS L3 WAN Design Models, Common L2 WAN Design Models, Common VPN WAN Design Models, 3G/4G VPN Design Models, Remote Site Using Local Internet, Remote-Site LAN, Case Study: Redundancy and Connectivity, NGWAN, SDWAN, and IWAN Solution Overview, IWAN Design Overview, Enterprise WAN and Access Management. Part IV Enterprise Data Center DesignsMultitier Data Center Designs: Case Study: Small Data Centers (Connecting Servers to an Enterprise LAN), Case Study: Two-Tier Data Center Network Architecture, Case Study: Three-Tier Data Center Network Architecture.Trends and Techniques to Design Modern Data Centers: The Need for a New Network Architecture, Limitations of Current Networking Technology, Modern Data Center Design Techniques and Architectures, Multitenant Data Center. SDN:SDN characteristics, How SDN addresses current Networking Limitations, SDN Architecture Components, SDN Network Virtualization overlays. Data Center Connections:Data Center Traffic Flows, The Need for DCI, IP Address Mobility, Case Study: Dark Fiber DCI, Pseudowire DCI. Part V Design QoS for Optimized User ExperienceQoS Overview:QoS Overview, IntServ versus DiffServ, Classification and Marking, Policers and Shapers, Policing Tools: Single-Rate Three-Color Marker, Policing Tools: TwoRate Three-Color Marker, Queuing Tools, Dropping Tools. QoS design principles and best practices: QoS overview, classification and marking design principles, policing and remarking design principles, queuing design principles, dropping design principles, Per-Hop behavior queue design principles, RFC 4594 QoS Recommendation, QoS Strategy Models. Campus QoS, WAN QoS, Data Center QoS.MPLS VPN QoS Design: The Need for QoS in MPLS VPN, Layer 2 Private WAN QoS Administration, Fully Meshed MPLS VPN QoS Administration, MPLS DiffServ Tunneling Modes, Sample MPLS VPN QoS Roles. IPsec VPN QoS Design: The Need for QoS in IPsec VPN, VPN Use Cases and Their QoS Models, IPsec Refresher, Encryption and Classification: Order of Operations, MTU Considerations, DMVPN QoS Considerations. Part VI IP Multicast DesignEnterprise IP Multicast Design: How Does IP Multicast Work? Multicast Protocols, Multicast Forwarding and RPF Check, Multicast Protocol Basics, PIM-SM Overview, Multicast Routing Table, Basic SSM Concepts, Bidirectional PIM. RP discovery, Anycast RP Features, MSDP. Part VII Designing Optimum Enterprise Network SecurityDesigning Security Services and Infrastructure Protection Network Security Zoning, Designing Infrastructure Protection.Designing firewall & IPS solutions: Firewall architectures, virtualized firewalls. Case Study: Application Tier separation, Case Study: Firewalls in a Data Center, Case Study: Firewall High Availability, IPS Architectures, Case Study: Secure Campus Edge Design (Internet and Extranet Connectivity). IP Multicast Security: Multicast Security Challenges, Multicast Network Security Considerations. Designing Network Access Control Solutions:IEEE 802.1X, EAP, 802.1X supplicants, 802.1X phased deployment, Case Study: Authorization Options. Part VIII Design scenariosDesign Case Studies: 1: Enterprise Connectivity, 2: Enterprise BGP with Internet Connectivity, 3: IPv6, 4: Data Center Connectivity, 5: Resilient Enterprise WAN, 6: Secure Enterprise Network, 7: QoS in the Enterprise Network.

Let's Master British English Pronunciation
By Course Cloud
If you are tired of the stumbling blocks in pronunciation, want to perfect your English, or need a little refresher, this course is for you. Our British English expert will take you through several techniques which will be incredibly useful in perfecting your English pronunciation. We'll work through lots of different practice exercises together to develop your confidence, and discover some common misconceptions along the way. This comprehensive course is suitable for beginners through to advanced English speakers and designed to harness your English pronunciation so that you can become a confident speaker. After this course, you will have improved your English pronunciation, you'll be speaking naturally and freely, and you will have gained the skills you need to communicate effectively. So let's begin!

Principles of the Role of a Fire Marshal
By Security Cpd Global Ltd
Fire warden and Fire Safety

Yoga Module 1 - Shadow Yoga Prelude (1:1)
By Tim Cummins Yoga
Online courses in the shadow yoga preludes with recognised shadow yoga teacher
