- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
792 Courses in Nottingham delivered Live Online
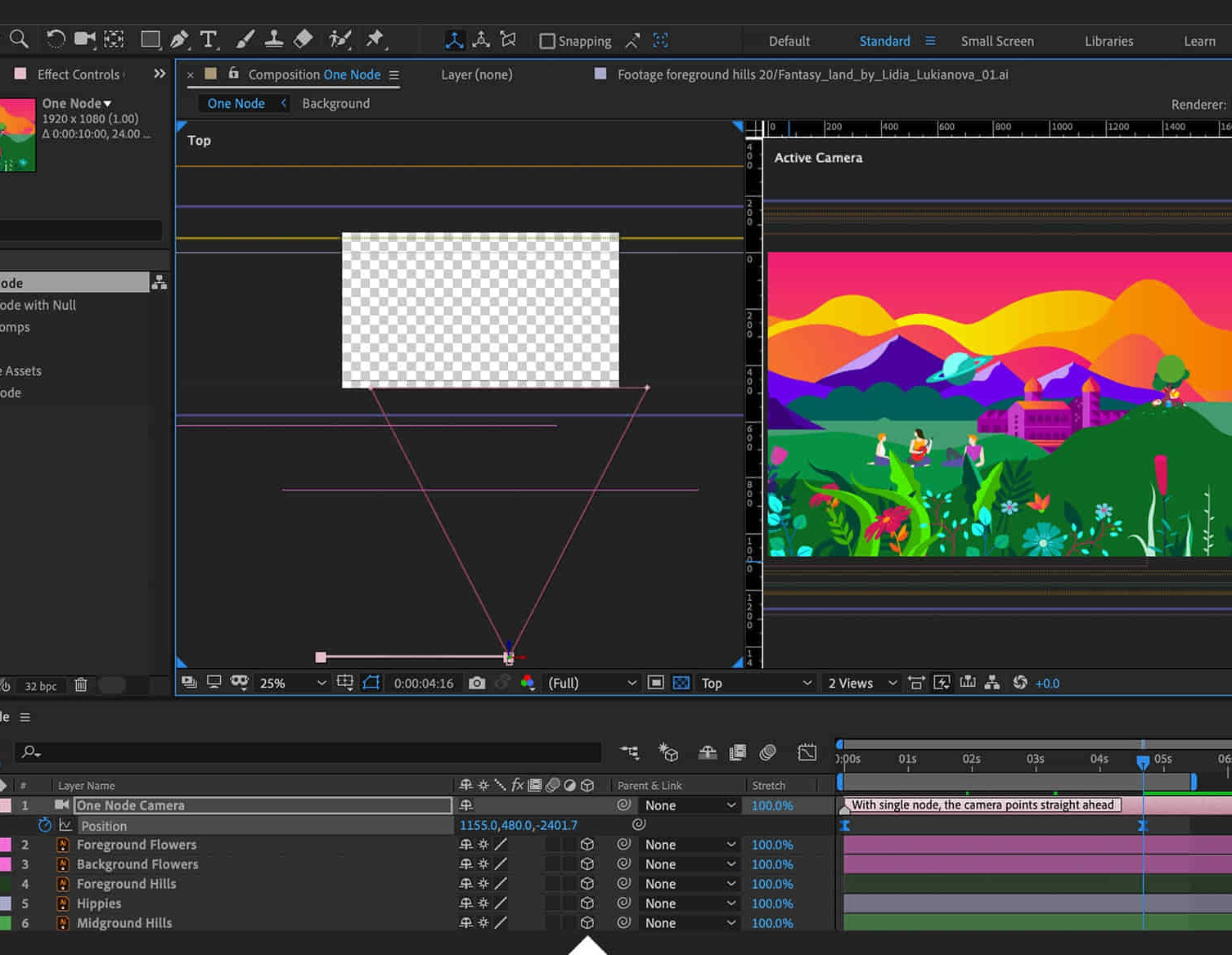
Adobe After Effects Beginners to Advanced Course
By ATL Autocad Training London
Adobe After Effects Beginners to Advanced Course Tailored for motion graphics designers basic to expert level. Explore advanced topics including motion tracking, green screen compositing, text animation, and techniques like expressions. Learn animations based on geometric proportions in our Advanced Motion Methods module. Click here for more info: Website Duration: 40 hours Approach: 1-on1 sessions and Customized content. Schedule: Choose your own day and time. Mon to Sat between 9 am and 5 pm. Module 1: Introduction to After Effects Exploring Adobe After Effects Navigating the Interface Configuring Preferences Utilizing Auto-Save Feature Module 2: Projects and Compositions Creating New Projects/Compositions Importing and Organizing Assets Working with Layers Module 3: Animation Techniques Keyframe Essentials Motion Paths and Modifications Graph Editor Insights Motion Control Tools Module 4: Layer Management Organizing and Navigating Layers Layer Visibility and Locking Switches and Modes in Detail Module 5: Shape Manipulation Shape Layers Fundamentals Creating and Animating Shapes Anchor Point Adjustment Module 6: Effects Mastery Applying and Customizing Effects Exploring Various Effects Examples Module 7: Masks and Track Mattes Mask Creation and Animation Track Matte Techniques Module 8: Text and Typography Animation Working with Text Layers Text Animation Presets Layer Styles for Typography Module 9: Exporting Your Creations Export Options Overview Direct Export from After Effects Utilizing Media Encoder After Effects https://www.adobe.com By the end of this 40-hour After Effects training, you will: Master Essentials: Understand fundamental and advanced After Effects features for diverse projects. Create Impactful Visuals: Craft compelling motion graphics, animations, and visual effects. Expert Animation Skills: Perfect keyframing, motion paths, and dynamic animations. Streamlined Workflow: Organize projects efficiently, ensuring smooth project execution. Creative Expression: Manipulate shapes, animate text, apply effects, and create masks creatively. Professional Exporting: Master export techniques for various platforms and media. Confidence and Expertise: Solve challenges confidently, applying skills in real-world projects. Industry-Ready: Gain skills applicable in filmmaking, animation, marketing, and creative sectors. Ongoing Support: Access post-training support for continued assistance. Certification: Receive a recognized certification, enhancing your professional profile. Course Title: Adobe After Effects Comprehensive Training Key Details: Duration: 40 hours Learning Approach: Personalized Training: Tailored content with 1-2-1 sessions. Flexible Schedule: Choose hours between 9 am and 7 pm, Monday to Saturday. Method: Hands-on learning with step-by-step demonstrations. Course Highlights: Master Essential Tools: From basics to advanced features for motion graphics and visual effects. Expert Guidance: Certified trainers provide personalized attention. Creative Animation: Learn advanced animation techniques, motion paths, and effects application. Efficient Workflow: Optimize project organization, layer management, and export techniques. Real-World Projects: Apply skills in filmmaking, animation, marketing, and more. Post-Training Support: Lifetime access to email and phone assistance for continued guidance. Certification: Receive a recognized certificate upon course completion. Benefits: Industry-Relevant Skills: Gain expertise for diverse creative sectors. Unleash Creativity: Craft compelling motion graphics, animations, and visual effects. Confidence in Execution: Solve challenges confidently with real-world application. Professional Recognition: Enhance your profile with a certified After Effects proficiency. Course Materials and Certification: Upon enrollment, you will receive a valuable After Effects training guide in PDF format, serving as a useful resource during and after the course. Additionally, upon successful completion, you'll be awarded an e-certificate, validating your achievement in the Adobe After Effects training program. Post-Course Support: Rest assured, you'll have access to lifetime email support from your dedicated After Effects trainer, providing assistance for any inquiries or challenges arising after the course. Prerequisites and Software Version: No prior After Effects knowledge is required for enrollment. The training is tailored for After Effects 2023, with techniques applicable to recent software releases. Whether you're a Windows or Mac user, the training suits your needs. Our Guarantees: We prioritize your satisfaction with our double guarantee - a price assurance ensuring the best value for your investment and a training guarantee ensuring you master essential concepts and skills.
Age of the Coach Series
By Mpi Learning - Professional Learning And Development Provider
This virtual modular programme develops the coaching skills of managers and leaders. This programme is delivered virtually over zoom, 4 x 180 Minute Sessions over 4 Days.

Artificial Lift and Real-Time Production Optimization in Digital Oilfield
By EnergyEdge - Training for a Sustainable Energy Future
About this training course Artificial lift systems are an important part of production operations for the entire lifecycle of an asset. Often, oil and gas wells require artificial lift for most of the life cycle. This 5-day training course offers a thorough treatment of artificial lift techniques including design and operation for production optimization. With the increasing need to optimize dynamic production in highly constrained cost environments, opportunities and issues related to real-time measurements and optimization techniques needs to be discussed and understood. Artificial lift selection and life cycle analysis are covered. These concepts are discussed and reinforced using case studies, quizzing tools, and exercises with software. Participants solve examples and class problems throughout the course. Animations and videos reinforce the concepts under discussion. Understanding of these important production concepts is a must have to exploit the existing assets profitably. Unique Features: Hands-on usage of SNAP Software to solve gas-lift exercises Discussion on digital oil field Machine learning applications in gas-lift optimization Training Objectives After the completion of this training course, participants will be able to: Understand the basics and advanced concepts of each form of artificial lift systems including application envelope, relative strengths, and weaknesses Easily recognize the different components from downhole to the surface and their basic structural and operational features Design and analyze different components using appropriate software tools Understand challenges facing artificial lift applications and the mitigation of these challenges during selection, design, and operation Learn about the role of digital oilfield tools and techniques and their applications in artificial lift and production optimization Learn about use cases of Machine learning and artificial intelligence in the artificial lift Target Audience This training course is suitable and will greatly benefit the following specific groups: Production, reservoir, completion, drilling and facilities engineers, analysts, and operators Anyone interested in learning about selection, design, analysis and optimum operation of artificial lift and related production systems will benefit from this course. Course Level Intermediate Advanced Training Methods The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training environment is highly stimulating, challenging, and effective because the participants will learn by case studies which will allow them to apply the material taught in their own organization. Course Duration: 5 days in total (35 hours). Training Schedule 0830 - Registration 0900 - Start of training 1030 - Morning Break 1045 - Training recommences 1230 - Lunch Break 1330 - Training recommences 1515 - Evening break 1530 - Training recommences 1700 - End of Training The maximum number of participants allowed for this training course is 20. This course is also available through our Virtual Instructor Led Training (VILT) format. Prerequisites: Understanding of petroleum production concepts. Each participant needs a laptop/PC for solving class examples using software to be provided during class. Laptop/PC needs to have a current Windows operating system and at least 500 MB free disk space. Participants should have administrator rights to install software. Trainer Your expert course leader has over 35 years' work-experience in multiphase flow, artificial lift, real-time production optimization and software development/management. His current work is focused on a variety of use cases like failure prediction, virtual flow rate determination, wellhead integrity surveillance, corrosion, equipment maintenance, DTS/DAS interpretation. He has worked for national oil companies, majors, independents, and service providers globally. He has multiple patents and has delivered a multitude of industry presentations. Twice selected as an SPE distinguished lecturer, he also volunteers on SPE committees. He holds a Bachelor's and Master's in chemical engineering from the Gujarat University and IIT-Kanpur, India; and a Ph.D. in Petroleum Engineering from the University of Tulsa, USA. Highlighted Work Experience: At Weatherford, consulted with clients as well as directed teams on digital oilfield solutions including LOWIS - a solution that was underneath the production operations of Chevron and Occidental Petroleum across the globe. Worked with and consulted on equipment's like field controllers, VSDs, downhole permanent gauges, multiphase flow meters, fibre optics-based measurements. Shepherded an enterprise-class solution that is being deployed at a major oil and gas producer for production management including artificial lift optimization using real time data and deep-learning data analytics. Developed a workshop on digital oilfield approaches for production engineers. Patents: Principal inventor: 'Smarter Slug Flow Conditioning and Control' Co-inventor: 'Technique for Production Enhancement with Downhole Monitoring of Artificially Lifted Wells' Co-inventor: 'Wellbore real-time monitoring and analysis of fracture contribution' Worldwide Experience in Training / Seminar / Workshop Deliveries: Besides delivering several SPE webinars, ALRDC and SPE trainings globally, he has taught artificial lift at Texas Tech, Missouri S&T, Louisiana State, U of Southern California, and U of Houston. He has conducted seminars, bespoke trainings / workshops globally for practicing professionals: Companies: Basra Oil Company, ConocoPhillips, Chevron, EcoPetrol, Equinor, KOC, ONGC, LukOil, PDO, PDVSA, PEMEX, Petronas, Repsol, , Saudi Aramco, Shell, Sonatrech, QP, Tatneft, YPF, and others. Countries: USA, Algeria, Argentina, Bahrain, Brazil, Canada, China, Croatia, Congo, Ghana, India, Indonesia, Iraq, Kazakhstan, Kenya, Kuwait, Libya, Malaysia, Oman, Mexico, Norway, Qatar, Romania, Russia, Serbia, Saudi Arabia, S Korea, Tanzania, Thailand, Tunisia, Turkmenistan, UAE, Ukraine, Uzbekistan, Venezuela. Virtual training provided for PetroEdge, ALRDC, School of Mines, Repsol, UEP-Pakistan, and others since pandemic. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

A day of Data Governance, support, networking, and answering your questions. Join me for my 1 Day Data Governance Mastermind where you get allocated time to get specific advice on your current Data Governance challenges and get the chance to network with others in similar situations.

Managing Multiple Projects: Virtual In-House Training
By IIL Europe Ltd
Managing Multiple Projects: Virtual In-House Training Succeeding in today's competitive marketplace often requires cycle time reduction - reducing the duration of projects and getting results faster. This workshop will address managing multiple projects within the context of program or product management. Are your projects taking longer and longer to complete? Are results less than optimal because of time pressures on resources? Would you like to increase project 'throughout'? Succeeding in today's competitive marketplace often requires cycle time reduction - reducing the duration of projects and getting results faster. This workshop will address managing multiple projects within the context of program or product management. Planning and managing individual projects is challenging. When introducing the real-life limitation of resources and other outside influences into the multi-project environment, those challenges are magnified, and new challenges are introduced. This interactive workshop will position you for immediate action. The goal of this course is to equip you with the necessary knowledge, skills, and techniques so that you can effectively and productively manage multiple projects. What you Will Learn You'll learn how to: Manage stakeholder relationships and expectations Prioritize and sequence multiple projects Manage time and stress within a multiple project environment Effectively manage logical dependencies among projects Optimize the use of resources across multiple projects using concepts from Critical Chain methods Manage risk and communications in a multiple project environment Getting Started Introductions Course structure Course goals and objectives Foundation Concepts Portfolio, program, and project management principles The multiple project environment The MMP Process Model Developing the Multiple Project List Multiple project portfolio management Project selection Project categories and types The multiple project list Multiple Project Logical Dependencies Project dependencies Types of multiple project portfolios Categories of logical dependencies across multiple projects Project priorities in the multiple project schedule Multiple Project Resource Management Multiple project resources and resource management concepts Multiple project resource loading Resource pool and resource database Multiple project resource issues and outsourcing Critical chain resource management, including drum resources and multi-tasking Managing Risk Across Multiple Projects Multiple project risk management process Identifying, assessing, and responding to multiple project risks Critical chain and multiple project risks Risk interrelationship management methods Creating and Executing the Multiple Project Plan The multiple project plan Multiple project scheduling Multiple project budgeting Executing and maintaining the multiple project plan Controlling in the multiple project environment Tools in multiple project management Multiple Project Communications Effective communication in the multiple project environment Common communication barriers Multiple project communications plan Resolving multiple project conflicts Summary and Next Steps What did we learn, and how can we implement this in our work environments?

Certified Cloud Security Professional (CCSP)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The CCSP is ideal for IT and information security leaders responsible for applying best practices to cloud security architecture, design, operations and service orchestration. Overview Upon completing this course, the participants will gain valuable knowledge and skills including the ability to: - Successfully pass the CCSP exam. - Understand the fundamentals of the cloud computing architecture framework. - Understand security challenges associated with different types of cloud services. - Identify and evaluate security risks for their organization?s cloud environments. - Select and implement appropriate controls to ensure secure implementation of cloud services. - Thoroughly understand the 6 essential core domains of the CCSP common body of knowledge: 1. Architectural Concepts & Design Requirements 2. Cloud Data Security 3. Cloud Platform & Infrastructure Security 4. Cloud Application Security 5. Operations 6. Legal & Compliance The goal of the course is to prepare professionals for the challenging CCSP exam by covering the objectives of the exam based on the six domains as defined in the (ISC)2 CCSP common body of knowledge. 1 - Architectural Concepts and Design Requirements Cloud Computing Concepts Cloud Reference Architecture Cloud Computing Security Concepts Design Principles of Secure Cloud Computing Trusted Cloud Services 2 - Cloud Data Security CSA (Cloud Security Alliance) Cloud Data Lifecycle Cloud Data Storage Architectures Data Security Strategies Data Discovery and Classification Technologies Protecting Privacy and PII (Personally Identifiable Information) Data Rights Management Data Retention, Deletion, and Archiving Policies Auditability, Traceability, and Accountability of Data Events 3 - Cloud Platform and Infrastructure Security Cloud Infrastructure Components Cloud Infrastructure Risks Designing and Planning Security Controls Disaster Recovery and Business Continuity Management 4 - Cloud Application Security The Need for Security Awareness and Training in application Security Cloud Software Assurance and Validation Verified Secure Software SDLC (Software Development Life Cycle) Process Secure SDLC Specifics of Cloud Application Architecture Secure IAM (Identity and Access Management) Solutions 5 - Operations Planning Process for the Data Center Design Installation and Configuration of Physical Infrastructure for Cloud Environment Running Physical Infrastructure for Cloud Environment Managing Physical Infrastructure for Cloud Environment Installation and Configuration of Logical Infrastructure for Cloud Environment Running Logical Infrastructure for Cloud Environment Managing Logical Infrastructure for Cloud Environment Compliance with Regulations and Controls Risk Assessment for Logical and Physical Infrastructure Collection, Acquisition, and Preservation of Digital Evidence Managing Communication with Stakeholders 6 - Legal and Compliance Legal Requirements and Unique Risks within the Cloud Environment Relevant Privacy and PII Laws and Regulations Audit Process, Methodologies, and Required Adaptions for a Cloud Environment Implications of Cloud to Enterprise Risk Management Outsourcing and Cloud Contract Design Vendor Management

Coal Power Plant Life Cycle Management and Flexible Operations in Energy Transition - Decommissioning, Preservation, Repurposing and Recommissioning
By EnergyEdge - Training for a Sustainable Energy Future
Enhance your knowledge in coal power plant life cycle management and flexible operations with EnergyEdge. Learn about decommissioning, preservation, repurposing, and recommissioning.

EC-Council Computer Hacking Forensic Investigator (CHFI) v10.0
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The CHFI course will benefit: Police and other laws enforcement personnel Defense and Military personnel e-Business Security professionals Systems administrators Legal professionals Banking, Insurance and other professionals Government agencies Overview At the end of this course, you will possess the skills needed to: Understand the fundamentals of computer forensics Understand the computer forensic investigation process Describe in detail different types of hard disks and file systems Understand data acquisition and duplication Counteract anti-forensic techniques Leverage forensic skills in Windows, Linux, and Mac Investigate web attacks Understand dark web forensics Deploy forensic techniques for databases, cloud, and networks Investigate email crimes including malware Perform forensics in mobile and IoT environments Every crime leaves a digital footprint, and you need the skills to track those footprints. In this course, students will learn to unravel these pieces of evidence, decode them and report them. From decoding a hack to taking legal action against the perpetrators, they will become an active respondent in times of cyber-breaches. Computer Forensics in Today?s World 1.1. Understand the Fundamentals of Computer Forensics 1.2. Understand Cybercrimes and their Investigation Procedures 1.3. Understand Digital Evidence 1.4. Understand Forensic Readiness, Incident Response and the Role of SOC (Security Operations Center) in Computer Forensics 1.5. Identify the Roles and Responsibilities of a Forensic Investigator 1.6. Understand the Challenges Faced in Investigating Cybercrimes 1.7. Understand Legal Compliance in Computer Forensics Computer Forensics Investigation Process 2.1. Understand the Forensic Investigation Process and its Importance 2.2. Understand the Pre-investigation Phase 2.3. Understand First Response 2.4. Understand the Investigation Phase 2.5. Understand the Post-investigation Phase Understanding Hard Disks and File Systems 3.1. Describe Different Types of Disk Drives and their Characteristics 3.2. Explain the Logical Structure of a Disk 3.3. Understand Booting Process of Windows, Linux and Mac Operating Systems 3.4. Understand Various File Systems of Windows, Linux and Mac Operating Systems 3.5. Examine File System Using Autopsy and The Sleuth Kit Tools 3.6 Understand Storage Systems 3.7. Understand Encoding Standards and Hex Editors 3.8. Analyze Popular File Formats Using Hex Editor Data Acquisition and Duplication 4.1. Understand Data Acquisition Fundamentals 4.2. Understand Data Acquisition Methodology 4.3. Prepare an Image File for Examination Defeating Anti-forensics Techniques 5.1. Understand Anti-forensics Techniques 5.2. Discuss Data Deletion and Recycle Bin Forensics 5.3. Illustrate File Carving Techniques and Ways to Recover Evidence from Deleted Partitions 5.4. Explore Password Cracking/Bypassing Techniques 5.5. Detect Steganography, Hidden Data in File System Structures, Trail Obfuscation, and File Extension Mismatch 5.6. Understand Techniques of Artifact Wiping, Overwritten Data/Metadata Detection, and Encryption 5.7. Detect Program Packers and Footprint Minimizing Techniques 5.8. Understand Anti-forensics Countermeasures Windows Forensics 6.1. Collect Volatile and Non-volatile Information 6.2. Perform Windows Memory and Registry Analysis 6.3. Examine the Cache, Cookie and History Recorded in Web Browsers 6.4. Examine Windows Files and Metadata 6.5. Understand ShellBags, LNK Files, and Jump Lists 6.6. Understand Text-based Logs and Windows Event Logs Linux and Mac Forensics 7.1. Understand Volatile and Non-volatile Data in Linux 7.2. Analyze Filesystem Images Using The Sleuth Kit 7.3. Demonstrate Memory Forensics Using Volatility & PhotoRec 7.4. Understand Mac Forensics Network Forensics 8.1. Understand Network Forensics 8.2. Explain Logging Fundamentals and Network Forensic Readiness 8.3. Summarize Event Correlation Concepts 8.4. Identify Indicators of Compromise (IoCs) from Network Logs 8.5. Investigate Network Traffic 8.6. Perform Incident Detection and Examination with SIEM Tools 8.7. Monitor and Detect Wireless Network Attacks Investigating Web Attacks 9.1. Understand Web Application Forensics 9.2. Understand Internet Information Services (IIS) Logs 9.3. Understand Apache Web Server Logs 9.4. Understand the Functionality of Intrusion Detection System (IDS) 9.5. Understand the Functionality of Web Application Firewall (WAF) 9.6. Investigate Web Attacks on Windows-based Servers 9.7. Detect and Investigate Various Attacks on Web Applications Dark Web Forensics 10.1. Understand the Dark Web 10.2. Determine How to Identify the Traces of Tor Browser during Investigation 10.3. Perform Tor Browser Forensics Database Forensics 11.1. Understand Database Forensics and its Importance 11.2. Determine Data Storage and Database Evidence Repositories in MSSQL Server 11.3. Collect Evidence Files on MSSQL Server 11.4. Perform MSSQL Forensics 11.5. Understand Internal Architecture of MySQL and Structure of Data Directory 11.6. Understand Information Schema and List MySQL Utilities for Performing Forensic Analysis 11.7. Perform MySQL Forensics on WordPress Web Application Database Cloud Forensics 12.1. Understand the Basic Cloud Computing Concepts 12.2. Understand Cloud Forensics 12.3. Understand the Fundamentals of Amazon Web Services (AWS) 12.4. Determine How to Investigate Security Incidents in AWS 12.5. Understand the Fundamentals of Microsoft Azure 12.6. Determine How to Investigate Security Incidents in Azure 12.7. Understand Forensic Methodologies for Containers and Microservices Investigating Email Crimes 13.1. Understand Email Basics 13.2. Understand Email Crime Investigation and its Steps 13.3. U.S. Laws Against Email Crime Malware Forensics 14.1. Define Malware and Identify the Common Techniques Attackers Use to Spread Malware 14.2. Understand Malware Forensics Fundamentals and Recognize Types of Malware Analysis 14.3. Understand and Perform Static Analysis of Malware 14.4. Analyze Suspicious Word and PDF Documents 14.5. Understand Dynamic Malware Analysis Fundamentals and Approaches 14.6. Analyze Malware Behavior on System Properties in Real-time 14.7. Analyze Malware Behavior on Network in Real-time 14.8. Describe Fileless Malware Attacks and How they Happen 14.9. Perform Fileless Malware Analysis - Emotet Mobile Forensics 15.1. Understand the Importance of Mobile Device Forensics 15.2. Illustrate Architectural Layers and Boot Processes of Android and iOS Devices 15.3. Explain the Steps Involved in Mobile Forensics Process 15.4. Investigate Cellular Network Data 15.5. Understand SIM File System and its Data Acquisition Method 15.6. Illustrate Phone Locks and Discuss Rooting of Android and Jailbreaking of iOS Devices 15.7. Perform Logical Acquisition on Android and iOS Devices 15.8. Perform Physical Acquisition on Android and iOS Devices 15.9. Discuss Mobile Forensics Challenges and Prepare Investigation Report IoT Forensics 16.1. Understand IoT and IoT Security Problems 16.2. Recognize Different Types of IoT Threats 16.3. Understand IoT Forensics 16.4. Perform Forensics on IoT Devices

M.D.D PRIVATE OCCUPATIONAL THERAPY LONDON PACKAGE (SELF IMPROVEMENT)
4.9(27)By Miss Date Doctor Dating Coach London, Couples Therapy
Introducing Private Occupational Therapy London Package: Personalized Support for Your Unique Needs Are you looking for private occupational therapy services in London that prioritize your individual needs and goals? Miss Date Doctor’s Private Occupational Therapy London Package offers you dedicated one-on-one support and personalized interventions to help you overcome challenges and improve your quality of life. Private occupational therapy provides a focused and tailored approach, ensuring that you receive the highest level of care and attention. Our experienced occupational therapists in London are committed to understanding your specific needs and providing effective solutions to enhance your daily functioning and well-being. Here’s how the Private Occupational Therapy London Package can support you: Personalized Assessment: Our private occupational therapists will conduct a thorough and individualized assessment to gain a comprehensive understanding of your unique challenges, strengths, and goals. Tailored Treatment Plan: Based on the assessment, we’ll develop a customized treatment plan designed to address your specific needs and aspirations. This plan will focus on enhancing your functional abilities and promoting independence. Focused Attention: Private occupational therapy sessions offer you dedicated one-on-one attention, ensuring that you receive the most effective and personalized interventions. Individual Progress: Our therapists will closely monitor your progress throughout the therapy process, making adjustments to the treatment plan as needed to maximize your outcomes. Convenient Scheduling: Private occupational therapy allows for flexible scheduling options to accommodate your busy lifestyle and ensure that you have access to the support you need when it’s most convenient for you. Personal Empowerment: We believe in empowering you to take an active role in your therapy journey. Our therapists will collaborate with you, providing guidance and support as you work towards your goals. Confidentiality and Privacy: Private occupational therapy sessions offer a confidential and private environment where you can freely discuss your challenges and experiences. The Private Occupational Therapy London Package at Miss Date Doctor is committed to providing you with the highest level of personalized care and support. Our expert occupational therapists will work closely with you to help you overcome obstacles, regain independence, and enhance your daily living skills. Invest in your well-being and experience the benefits of private occupational therapy. Take the first step towards a more fulfilling and empowered life with the Private Occupational Therapy London Package. Let our skilled therapists guide you towards greater independence, improved functionality, and a more enriched quality of life. 3 x1 hour https://relationshipsmdd.com/product/private-occupational-therapy-london-package/

