- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
77 Courses in Liverpool delivered Live Online
VMware Horizon 8: Troubleshooting Bootcamp
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for New or junior administrators and operators; system managers accountable for staffing and training Horizon operators and administrators. Experienced system operators, administrators, and integrators responsible for managing and maintaining VMware Horizon solutions Overview By the end of the course, you should be able to meet the following objectives: Implement a structured approach to troubleshooting Resolve common issues that occur in a VMware Horizon environment Troubleshoot issues with linked and instant clones Configure the Windows client Identify the correct log level for gathering logs Optimize protocols for best end-user experience Discuss Horizon Connection Server advanced configurations List troubleshooting techniques for Horizon Connection Server common issues Interpret Horizon 8 Connection Server logs Identify Unified Access Gateway configuration and certificate issues List troubleshooting steps for Unified Access Gateway common issues Describe BLAST configuration verification using logs and settings Describe BLAST optimization recommendations for different use cases Describe Horizon 8 Connections and how to troubleshoot related issues Describe Horizon 8 certificates List troubleshooting steps for common issues with Horizon 8 certificates Leverage Horizon infrastructure troubleshooting steps to resolve issues This five-day course builds your skills in resolving common issues that occur in a VMware Horizon© environment. You engage in a series of lab exercises to bring existing environment issues to resolution. The exercises mirror real-world troubleshooting use cases. These exercises equip learners with the knowledge and practical skills to manage typical challenges faced by virtual desktop administrators and operators and provides you with the advanced knowledge, skills, and abilities to troubleshoot VMware Horizon© 8 infrastructure related issues. This workshop teaches the required skill and competence for troubleshooting VMware Horizon© Connection Server?, VMware Unified Access Gateway?, protocols, connections, and certificates Course Introduction Introductions and course logistics Course objectives Overview of Virtual Desktop Troubleshooting Structured approach to troubleshooting configuration and operational problems Applying troubleshooting methods Documenting the steps to resolving the problem Command-Line Tools and Backup Options Using command-line tools Backing-up and restoring VMware Horizon databases Troubleshooting Horizon Linked Clone Desktops Only applicable for Horizon 7.x environments Describe the components that make up a VMware Horizon desktop Explain how the View Agent Direct-Connection plug-In is useful for diagnosing problems Highlight the best practice for optimizing a VMware Horizon desktop Troubleshoot common problems with VMware Horizon desktops Troubleshooting Instant Clones Discuss how instant clones are created Discuss what gets logged when an instant clone is created Discuss the keywords to look for in the logs when troubleshooting instant clones Discuss how to troubleshoot problems with instant clones Windows Client Correctly configure the Windows Client Identify the correct log level for gathering logs Enable the required SSL configuration level for the environment Ports and Protocols Discuss the key ports on a Horizon Environment Discuss protocols used in the Horizon Environment Understand the benefit of optimizing Blast Become familiar with the optimization features for Blast Implement GPO changes for Blast Become familiar with the causes for Black Screens Discuss how to troubleshoot Black Screen problems Identify problems encountered when applying GPOs Discuss how to troubleshoot GPO-related problems Horizon Connection Server Troubleshooting Discuss Horizon Connection Server general troubleshooting techniques Identity Horizon Connection Server common issues through logs Describe AD LDS replication Discuss Horizon Connection Server replication common issues Review and Interpret Horizon Connection Server logs Compare successful and unsuccessful logs from everyday infrastructure administration tasks Unified Access Gateway Troubleshooting List and identify common Unified Access Gateway deployment issues Monitor the Unified Access Gateway deployment to identify health and issues Identify and troubleshoot Unified Access Gateway certificate issues Monitor, test, and troubleshoot network problems Discuss general Unified Access Gateway troubleshooting processes BLAST Configuration Verification Discuss BLAST Codecs and Encoder Switch settings. Describe how to verify BLAST configuration using logs and settings BLAST Optimization List general BLAST optimization recommendations Summarize BLAST tuning recommendations that apply to WAN connections Summarize BLAST tuning recommendations that apply to work-from-home and home-office-to-cloud use cases Describe recommended tuning options to increase display protocol quality for all use cases and applications. VMware Horizon Connections Troubleshooting Explain Horizon connections Describe the role of Primary and Secondary protocols in Horizon connections Describe HTML client access connections Describe Horizon connections load balancing Describe timeout settings, supported health monitoring string, and suitable load balancer persistence values Identify troubleshooting steps for failing Horizon load balancer connections List troubleshooting steps for Horizon connections VMware Horizon Certificates Troubleshooting List Horizon certificate functions Describe Horizon certificates scenarios. Discuss potential challenges related to certificates in Horizon Describe the troubleshooting approach to Horizon certificate issues VMware Horizon Challenge Lab Leverage Horizon infrastructure troubleshooting steps to resolve issues

One to One deep-dive into your intuitive knowing: Sleeping Beauty: Awaken to more of who you are
4.9(8)By The Soul Shed
This is an opportunity to go gently into the world of forest story and to explore your intuitive creativity as a wisdom stream you can connect with. Your inner world and neurodiversity is celebrated.

Microsoft Lync training course description This course teaches IT staff how to plan, design, deploy, configure, and administer a Microsoft Lync Server solution. The course emphasizes Lync Server Enterprise Unified Communications features focussing particularly on coexisting with and migrating from legacy communication services. The labs in this course create a solution that includes IM and Presence, Conferencing, and Persistent Chat. This course helps prepare for Exam 70-336. What will you learn Describe the Lync Server architecture. Install and deploy Lync Server. Use Lync Server management interfaces. Deploy and manage clients. Manage and administer dial-in conferencing. Design audio and video for web conferencing. Plan for instant message and presence Federation. Deploy and configure persistent chat in Lync. Configure archiving and monitoring services. Troubleshoot Lync Server. Describe the required daily, weekly, and monthly maintenance tasks. Use SIP commands and analyze SIP logs. Configure high availability features in Lync. Design load balancing in Lync Server. Backup and restore Lync Server data. Microsoft Lync training course details Who will benefit: Technical staff working with Microsoft Lync. Prerequisites: Supporting Windows 2008 or 2012. Duration 5 days Microsoft Lync training course contents Microsoft Lync Server architecture Lync Server architecture, Lync core capabilities, Lync design process, assessing infrastructure requirements and updating the design, planning for all Microsoft solutions framework phases. Designing a Lync Server topology Infrastructure requirements for Lync Server, using the planning tool, using topology builder, server infrastructure, documentation. Hands on Environment preparation and Lync Server pools. Users and rights in Microsoft Lync Server Managing Lync Server, role based access control. Hands on Using the management shell, configuring role-based access control. Client/device deployment and management Deploy and manage clients, prepare for device deployment, IP phones. Hands on Clients. Conferencing in Lync Server Introduction to conferencing in Lync Server, designing for audio\video and web conferencing, dial-in conferencing in Lync Server, managing and administering conferencing. Hands on Conferencing in Microsoft Lync. Designing and deploying external access Conferencing and external capabilities of Lync Server, planning for IM and presence federation, designing edge services. Hands on Deploying Edge Server and Configuring Remote Access, Validating the Edge Server. Deploying Lync Server persistent chat Overview of persistent chat architecture in Lync Server, designing persistent chat, deploying and persistent chat. Hands on persistent chat server. Monitoring and archiving The archiving service, the monitoring service, configuring archiving and monitoring. Hands on Archiving and monitoring in Lync Server. Administration and maintenance of Lync Lync Server troubleshooting tools, Lync Server operational tasks, Lync Server troubleshooting techniques. Hands on Lync administration tools, centralized logging service, analysing Lync Server logs and traces. High Availability in Lync Server High availability in Lync Server, configuring high availability in Lync Server, planning for load balancing, designing load balancing. Hands on Configuring database mirroring, experiencing a scheduled SQL Server outage, experiencing an unscheduled SQL Server outage. Disaster recovery in Lync Server Disaster recovery in Lync Server, tools for backing up and restoring Lync Server, critical Lync Server data to back up and restore, critical data to export and import, designing branch site resiliency. Hands on Configure pool pairing, experiencing a pool failure or outage. Planning a migration to Lync Server Coexistence and migration, migration steps, planning for clients and devices. Designing a client migration and device migration strategy. Hands on Creating a migration plan, documenting the migration phases.

Advanced HP switches training course description A hands on course covering advanced features of HP switches. The focus of the course is on Layer 3 switching advanced features. Delegates will benefit the most from this course if they can supply us with their own configurations before the course. These configurations can then be used by the trainer in the course. What will you learn Configure and troubleshoot HP layer 3 switching. Configure and troubleshoot OSPF Harden HP switches. Explain the majority of their own configurations (if configurations are supplied to us before the course). Advanced HP switches training course details Who will benefit: Technical staff working with HP switches. Prerequisites: HP switches for engineers. Duration 2 days Advanced HP switches training course content Introduction VLAN review. Tagged and untagged ports. MSTP, PVST, UDLD, BPDU guard. Hands on VLANs, diagnostic tools debug, LLDP, remote port mirroring. L3 switching What are L3 switches? L3 lite, IPv4 and IPv6, routing protocols, routing tables. IP address on VLAN, no ip address on VLAN, connected interfaces, RIP. Hands on Routing between VLANs. Configuring and troubleshooting RIP. VRRP Default gateways, dead router detection, resilience. Hands on Configuring and troubleshooting VRRP. Static routes Why use static routes? Configuring static routes, default routes. OSPF Link state protocols, operation. Router types, LSA types, area 0. Hands on Configuring and troubleshooting OSPF. QoS Layer 2 QoS, 802.1Q, priorities, dscp mapping, rate limiting. Access lists Filtering traffic through the switch, controlling access to the switch, enabling and disabling ACLs, standard ACLs, extended ACLs Security DHCP snooping, ARP protection, STP guards, switch hardening. Summary Walkthrough of delegate configurations.

Security Engineering on AWS
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for security engineers, security architects, and information security professionals. Overview Identify security benefits and responsibilities of using the AWS Cloud Build secure application infrastructures Protect applications and data from common security threats Perform and automate security checks Configure authentication and permissions for applications and resources Monitor AWS resources and respond to incidents Capture and process logs Create and configure automated and repeatable deployments with tools such as AMIs and AWS CloudFormation This course demonstrates how to efficiently use AWS security services to stay secure in the AWS Cloud. The course focuses on the security practices that AWS recommends for enhancing the security of your data and systems in the cloud. The course highlights the security features of AWS key services including compute, storage, networking, and database services. You will also learn how to leverage AWS services and tools for automation, continuous monitoring and logging, and responding to security incidents. Prerequisites We recommend that attendees of this course have: Working knowledge of IT security practices and infrastructure concepts Familiarity with cloud computing concepts Completed AWS Security Essentials and Architecting on AWS courses 1 - Security on AWS Security in the AWS cloud AWS Shared Responsibility Model Incident response overview DevOps with Security Engineering 2 - Identifying Entry Points on AWS Identify the different ways to access the AWS platform Understanding IAM policies IAM Permissions Boundary IAM Access Analyzer Multi-factor authentication AWS CloudTrail 3 - Security Considerations: Web Application Environments Threats in a three-tier architecture Common threats: user access Common threats: data access AWS Trusted Advisor 4 - Application Security Amazon Machine Images Amazon Inspector AWS Systems Manager 5 - Data Security Data protection strategies Encryption on AWS Protecting data at rest with Amazon S3, Amazon RDS, Amazon DynamoDB Protecting archived data with Amazon S3 Glacier Amazon S3 Access Analyzer Amazon S3 Access Points 6 - Securing Network Communications Amazon VPC security considerations Amazon VPC Traffic Mirroring Responding to compromised instances Elastic Load Balancing AWS Certificate Manager 7 - Monitoring and Collecting Logs on AWS Amazon CloudWatch and CloudWatch Logs AWS Config Amazon Macie Amazon VPC Flow Logs Amazon S3 Server Access Logs ELB Access Logs 8 - Processing Logs on AWS Amazon Kinesis Amazon Athena 9 - Security Considerations: Hybrid Environments AWS Site-to-Site and Client VPN connections AWS Direct Connect AWS Transit Gateway 10 - Out-Of-Region Protection Amazon Route 53 AWS WAF Amazon CloudFront AWS Shield AWS Firewall Manager DDoS mitigation on AWS 11 - Security Considerations: Serverless Environments Amazon Cognito Amazon API Gateway AWS Lambda 12 - Threat Detection and Investigation Amazon GuardDuty AWS Security Hub Amazon Detective 13 - Secrets Management on AWS AWS KMS AWS CloudHSM AWS Secrets Manager 14 - Automation and Security by Design AWS CloudFormation AWS Service Catalog 15 - Account Management and Provisioning on AWS AWS Organizations AWS Control Tower AWS SSO AWS Directory Service

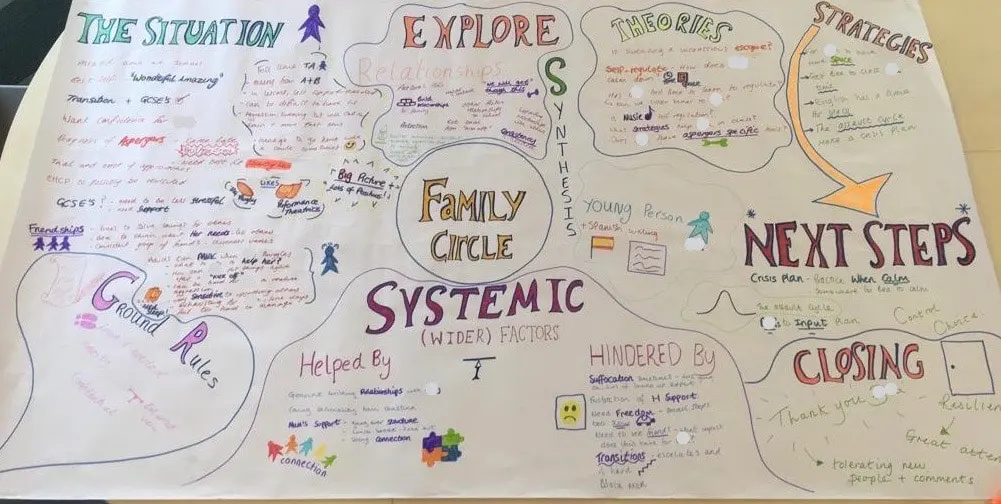
FAMILY CIRCLES
By Inclusive Solutions
Click to read more about this training, in which we demonstrate a live problem solving approach which is based on the active participation of family members. Course Category Inclusion Parents and Carers Behaviour and relationships Problem Solving Description In this training we demonstrate a live problem solving approach which is based on the active participation of family members. ‘Family Circles’ is an evolving new approach to problem solving with families and is based on our years of family work and the development and use of the Circle of Adults process. Inspired by our own Parent Solutions work and the Circle of Adults process as well as Family Group Conferencing and other Restorative Interventions we bring you Family Circles. Essentially the approach involves gathering a family together for a process that is facilitated but majors on the family members offering each other their wisdom and ideas. The approach is capacity focused, person centred approach to working with families rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for or doing things to families. This training can be modelled with a group of professionals or better still with a family. In our work with families we develop the importance of naming stories or theories and seeking linkages and synthesis between what is found out and explored about the family situation and its history. We like participants to sit with the uncertainty, to reflect on the question ‘why’ but without judgement of each other. Deeper reflections may span a whole range of perspectives from ‘within person’ considerations, to situational or systemic possibilities. Health or emotional issues can be reflected on alongside organisational or transactional aspects of what is going on for the family. The better the shared understanding the better the strategy or actions which emerge from these meetings. Quality hypotheses with a close fit to reality lead to more effective implementation in the real world. We encourage ‘loose’ thinking, a search for connections, deeper listening, an ‘open mind’, speculation and exploration without moral judgements. From this stance self-reflection as well as reflection on the situation can produce remarkable insights. The quality of theories or new stories generated is directly influenced by family members’ experiences and the models of learning, behaviour and emotion, systems, educational development, change and so on that they have been exposed to. Learning Objectives To provide opportunities for: Shared problem solving in a safe exploratory climate in which the family will find its own solutions. Individuals to reflect on their own actions and strategies An exploration of whole-family processes and their impact Emotional support and shared understandings of issues at a child, parent, family, school and community level. Feed back to each other on issues, ideas and strategies that are agreed to be worth sharing with them. Who Is It For? Anyone interested in working with families in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. Social Care teams School staff Community organisers Educational Psychologists Course Content True family empowerment Deepening shared stories and understandings Facilitating groups Problem solving process Handling family group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Process: Family members are welcomed: Introductions are carried out, ground rules and aims clarified whilst coffee is drunk. A recap from the last session is carried out: To follow up developments and reflections after the last meeting. One issue is selected for the main focus Issue presentation: The family member who raised the concern is asked questions to tell the ‘story’ of the issue or problem. Additional questions/information from the group about the problem are gathered: Ground rules may need to be observed carefully here. Individual participants need to be kept focused and prevented from leaping to premature conclusions or to making ‘helpful’ suggestions about strategy. Relationship aspects to the problem are explored. Metaphors and analogies are invited. How would a fly on the wall see your relationship? If you were alone together on a desert island, what would it be like? Impact of previous relationships/spillage from one relationship to another are explored. Eg what situation they are reminded of? For instance, does this situation remind you of any of those angry but helpless feelings you had with your other son when he was an adolescent? This provides opportunities to reflect on how emotions rub off on other people. The parent feels really frustrated, and on reflection we can see that so does the child System/Organisation factors (Family system/school and community systems and so on): What aspects help or hinder the problem? For instance, does the pastoral system of the local school provide space, or time and skilled personnel able to counsel this young person and work actively with their parents? Synthesis. At this stage the Graphic facilitator summarises what they have heard. They then go on to describe linkages and patterns in what they have heard. This can be very powerful. The person doing the graphic work has been able to listen throughout the presentation process and will have been struck by strong messages, emotions and images as they have arisen. The story and meaning of what is happening in the situation may become a little clearer at this point. Typical links may be ‘mirrored emotions’ strong themes such as loss and separation issues, or repeated processes such as actions triggering rejection. This step provides an excellent grounding for the next process of deepening understanding. What alternative strategies/interventions are open to be used? Brainstormed and recorded. ’Either/ors’ need to be avoided at this time also. This needs to be a shared session in which the family member who is presenting the concern contributes as much as anyone. Care is needed to ensure that this person is not overloaded with other people’s strategies. The final selection of strategy or strategies from the brainstormed list is the problem presenter’s choice. Strategies might include: a special time for the young person, a meeting with the child’s parents to explore how she is being managed at home and to share tactics, a home-school diary, counselling, or an agreed action plan that all are aware of, agreed sanctions and rewards and so forth. Strategies may productively involve processes of restitution and restoration, when ‘sorry’ is not enough. Making it right, rather than punishments or rewards, may then becomes the focus. First Steps. The problem presenter is finally asked to agree one or two first steps which they can carry out over the next 3-7 days. It can help to assign a ‘coach’ who will check in with them to ensure they have carried out the action they have named. This is a time to be very specific. Steps should be small and achievable. The person is just ‘making a start’. A phone call, or making an agreement with a key other person not present at the meeting would be ideal examples. Final reflections. Sometimes referred to as a ‘round of words’ help with closure for all involved. Reflections are on the process not the problem. In large families this is best done standing in a circle. In smaller groups all can remain sitting. Passing around a ‘listening stick’ or something similar such as a stone or light heighten the significance of the process ending and improve listening. Finally the problem presenter is handed the ‘Graphic’ this is their record of the meeting and can be rolled and presented ceremoniously by the facilitators for maximum effect! If you liked this course you may well like: Parent Solutions
Advanced Ethernet switching training course description An advanced hands on switching course for those already familiar with the basics such as STP and VLANs. The course starts with advanced diagnostics and network monitoring moving onto switch protocols. A large part of the second day is spent implementing QoS and security such as 802.1x. What will you learn Troubleshoot switching. Explain how a number of switch protocols work, including: UDLD LLDP LACP DTP VTP/MVRP Design redundancy into switched networks. Implement QoS on switches. Harden switches. Advanced Ethernet switching training course details Who will benefit: Technical staff working with Ethernet switches. Prerequisites: None Duration 2 days Advanced Ethernet switching training course contents Switches Switch review, troubleshooting, diagnostics, L2 traceroute, UDLD, message logging, Wireshark, port mirroring, Hands on: Troubleshooting. Network management SNMP, SNMPv3, RMON, Netflow, Sflow. System logging. Hands on: Managing switches with SNMP. Syslogd. Switches and automatic configuration Auto-MDIX, LLDP, CDP, Link aggregation, LACP, Link state tracking, VLANS and tags, DTP. Hands on: Discovery, dynamic configuration. RSTP 802.1w, new port roles and states, new BPDUs, rapid convergence, topology changes, compatibility issues. L3 redundancy, VRRP, GLBP. Design issues. Hands on: RSTP, VRRP. VLANS: Registration protocols Why VTP? VTP modes, how VTP works, VTP pruning. GVRP, MVRP. Hands on: Dynamic VLANs STP variations and alternatives 802.1s (multiple spanning tree), regions, rings, L2MP, TRILL. Hands on: 802.1s Multicasting What is multicasting, Static configuration, IGMP snooping, CGMP, MVR. IPv6 MLD snooping. Hands on: Multicast through switches QoS Storm control, DSCP, 802.1Q, 802.1p, mapping, classification, policy, Ingress queues, Egress queues. Dropping frames, limiting bandwidth. Hands on: Voice through switches. More VLANS Native VLANs, Voice VLANs Security Static MAC addresses, AAA, RADIUS, Port based authentication, 802.1x, Guest VLANs, L2 attacks, SSH, HTTPS. Hands on: Hardening switches. Miscellaneous NTP, managing the MAC address table, managing system resources, SDN

Mastering Unity 3D Intermediate Level Training Course
By ATL Autocad Training London
Who is this Course for? Mastering Unity 3D Intermediate Level Training Course Our Unity 3D training programs are tailored for individuals aspiring to become game developers, creative minds, & enthusiasts keen to explore the realm of game development. Learn 3D & 2D games or looking to master Unity's cross-platform features. Click here for more info: Website Duration: 20 hours Approach: 1-on-1 Individualized Attention & Customized Content Timetable: Scheduling any hour between 9 am and 7 pm, from Mon to Sat Course Overview: Sessions 1-2: Introduction to Unity Familiarize yourself with Unity's interface and workspace Create a new Unity project and set up the initial scene and navigation Sessions 3-4: Asset Management Explore and download free assets Import various asset types into Unity and understand their applications Sessions 5-6: Environmental Design Utilize Unity's terrain tools for environment creation Enhance scenes with textures, materials, and environmental objects Sessions 7-8: Character Development Design 3D character models Rig, animate, and import characters into Unity Sessions 9-10: Player Interaction Set up player controls and script basic movements Implement camera controls for seamless gameplay experiences Sessions 11-12: Physics and Realism Understand and implement physics in Unity Configure collisions, gravity, force, and torque for realistic interactions Sessions 13-14: Audio Enhancement Master audio implementation with sound effects and background music Fine-tune volume and pitch for immersive gameplay Sessions 15-16: Lighting and Visual Effects Employ advanced lighting techniques, including dynamic day-night cycles Enhance visuals with lens flares and particle systems Sessions 17-18: User Interface Design Construct user interfaces using Unity's canvas system Integrate interactive elements such as buttons and menus, ensuring smooth functionality Sessions 19-20: Optimization and Performance Implement optimization techniques and utilize the profiler for performance analysis Improve frame rates and reduce memory usage for seamless gameplay Session 21-22: Multiplayer Integration Explore multiplayer implementation and set up local multiplayer games Session 23-24: Mobile Game Development Discover mobile game development in Unity Build, deploy, and optimize games for mobile devices, focusing on performance and controls Session 25: Advanced Topics Delve into advanced scripting techniques, including coroutines, delegates, and events Explore shader programming and visual effects, and venture into VR development with Unity and Oculus Quest Final Project: Create a Comprehensive Game Test the game thoroughly, identify and resolve bugs Make necessary adjustments and improvements for a polished final product Experience the Real-Time Development Platform: Unleash your creativity and create 3D, 2D, VR, and AR experiences across various industries, including games, automotive, AEC, film, and more. Unity Pro offers a complete solution to develop better, iterate faster, and grow your business. Enjoy amazing games and immersive experiences with multi-platform support. Get started today: Unity Pro. Learning Outcomes: Participants will gain expertise in Unity 3D, mastering asset management, environmental design, character animation, player interaction, physics, audio, lighting, UI, optimization, and advanced scripting. They will develop a complete game, honing skills in debugging and project completion. Career Opportunities: Graduates can pursue roles as Game Developers, Mobile Game Developers, VR/AR Developers, Game Designers, UI/UX Designers, Game Testers, Indie Game Developers, Educational Game Developers, Freelance Developers, or Game Development Instructors, leveraging their Unity 3D skills for diverse and exciting career paths in the gaming industry. Skills Acquired: Participants in the Mastering Unity 3D Intermediate Level Training Course will gain advanced proficiency in Unity 3D game development, including: Advanced 3D Game Development Techniques Real-time Physics and Animation Skills Multiplatform Game Deployment Expertise Job Opportunities: Upon completion, individuals can pursue roles such as: Game Developer Unity 3D Programmer AR/VR Developer Interactive Simulation Designer This course equips participants with the expertise required for exciting opportunities in game development studios, AR/VR companies, and interactive media agencies, setting the stage for a successful career in the gaming and simulation industry. Course Advantages: Comprehensive Unity Mastery: Develop expertise in various Unity aspects, including game design, scripting, animation, and optimization. Hands-On Project Experience: Engage in practical projects mirroring real-world game development, enhancing your skills and portfolio. Interactive Live Instruction: Learn from experienced instructors in real-time, encouraging interactive discussions, Q&A sessions, and personalized guidance. Flexible Learning Paths: Opt for in-person or online classes, ensuring accessible and convenient learning tailored to your needs. Lesson Revisions: Access recorded lessons, allowing flexible review and reinforcement of concepts at your own pace. Lifetime Email Support: Benefit from ongoing support via email, where experts are available to assist with any questions or challenges, even after the course concludes.


