- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
10239 Concept courses in Nottingham delivered Online
Medical Secretary & Receptionist
By Training Tale
A medical secretary is responsible for ensuring that a doctor's office runs smoothly so that patients receive the best possible care. A medical secretary must understand office organisation and standard procedures to provide this secretarial support. They should also be able to use medical terminologies fluently. This coursewill teach you about the medical secretarial profession and the skills needed to do the job successfully. This coursewill teach you about the roles and responsibilities of a medical secretary. You will also learn various medical secretary skills, including an effective filing system, medical transcription, medical writing, maintaining medical records, an appointment system, and more. Furthermore, this comprehensive Medical Secretary & Receptionist will teach you the critical concepts of patient confidentiality and other legal aspects of the healthcare industry. Learning Outcomes After completing this course, learner will be able to: Understand the fundamentals of the National Health Service. Understand the roles and responsibilities of a medical secretary. Know how to organise schedules and manage appointment systems. Gain a clear understanding of the Law, Ethics and Medicine. Gain a thorough understanding of the effective filing system in medical offices. Familiarise yourself with the concept of patient confidentiality and its dos and don'ts. Become skilled at controlling and ordering stocks and supplies. Gain in-depth knowledge of Medical Terminology and Clinical Aspects. Know the importance of health and safety in the healthcare sector. Have a solid understanding of Complementary Medicine Why Choose Diploma in Medical Receptionist and Secretary from Us Self-paced course, access available from anywhere. Easy to understand, high-quality study materials. Medical Secretary & Receptionist Course developed by industry experts. MCQ quiz after each module to assess your learning. Automated and instant assessment results. 24/7 support via live chat, phone call or email. Free PDF certificate as soon as completing this Course. **Courses are included in this Medical Secretary & Receptionist Bundle Course Course 01: Medical Secretary & Receptionist Course 02: Dealing With Difficult People Course 03: Communication Skills Course Course 04: Level 5 Proofreading & Copy Editing Course 05: Level 2 Customer Service Course 06: Level 1 Certificate in Well-being Course 07: Mental Health Support Worker Course 08: Workplace Stress Management Course 09: Level 2 Award in Job Search and Interview Skills Course 10: Anger Management ***Others Included of this Bundle Course Free 10 PDF Certificate Access to Content - Lifetime Exam Fee - Totally Free Free Retake Exam [ Note: Free PDF certificate as soon as completing the course ] Detailed course curriculum of the Medical Secretary & Receptionist: Module 1: The National Health Service History Structure of the NHS The NHS Plan Resource Allocation Delivering Care Mental Health Services Public Health The NHS, the Regions and Devolution Module 2: Patient (Customer) Care The Medical Receptionist Putting Patient First Complaints Within the Health Service The Complaints Procedure Patient and Public Involvement Patient's Rights Access to Health Care Total Quality in Medical Practice Customer Care: Involving Patients and the Public Module 3: Communication Report Writing Electronic Mail & Mobile Phones: Text Messages Telephone Skills People Skills - Face to Face Meeting Performance Review & Counselling The Practice Leaflet & Hospital Information Leaflets Networking Module 4: Law, Ethics and Medicine Medical Ethics and Etiquette Doctor's Duties Patient's Right The Regulatory Bodies and Their Role Legal Aspects Certification Health and Safety at Work Module 5: Health & Safety in a Clinical Environment First Aid at Work Hazardous Substances The NHS National Patient Safety Agency (NPSA) Hepatitis & AIDS Fire Precautions Clinical Risk Management Coping With Aggression & Violence Module 6: Practical Reception Skills in General Practice Record Keeping and General Administration Information Technology Module 7: The Hospital Service The Patient's Route Through the Hospital Outpatient Appointments Admissions from the Waiting List Accident and Emergency Admissions Home From Hospital Support Day Cases and Ward Attendees Hospital Team Clinical Audit Star Ratings What is a Medical Record? Cases Notes Master Index Filing Room or Records Library Medical Records Procedure for Departments Retention of Records Destruction of Medical Records The Role of the Secretary in the Hospital Module 8: Private Medicine Private Clinic or Hospital The Secretary In Private Practice Module 9: Forms, Fees and Finances in General Practises Contracting Finance Practice Income Scotland Wales Northern Ireland Module 10: Using Information Technology Computers in General Practice Electronic Medicine Computers in Hospitals Maintaining Security Module 11: Medical Terminology and Clinical Aspects Pathology and X-ray Examinations Prescribing and Drugs Nurse Prescribing New Developments in Pharmacy Module 12: Audit, Health Economics and Ensuring Quality for the Medical Receptionist and Secretary Audit Health Economics and Cost-effective Medicine Private Finance Initiative Clinical Governance National Institute for Clinical Excellence (NICE) National Clinical Assessment Service (NCAS) National Service Framework (NSF) Patient Surveys Module 13: Complementary Medicine Acupuncture Alexander Technique Aromatherapy Chiropractic Homoeopathy Hydrotherapy Hypnotherapy Osteopathy Reflexology ------------------- ***Communication Skills Course*** Module 01: Introduction to Communication Module 02: The Communication Skills Module 03: Different Types of Communication Module 04: Different Methods of Communication Module 05: Styles of Communication Module 06: Barriers to Communication Module 07: Assessing Communication Competence: Relevant Criteria Module 08: Seven Actions for Effective Communication Module 09: Do's and Don'ts of Effective Communication ------------------- ***Level 1 Certificate in Well-being*** Module 01: Introduction to Stress and Stress Management Module 02: Develop an Awareness of Mental Health Module 03: Develop an Awareness of Substance Misuse Module 04: Introductory Awareness of the Importance of Healthy Eating and Drinking for Adults Module 05: Dementia Awareness ------------------- ***Level 5 Proofreading & Copy Editing*** Module 01: An Overview of Proofreading Module 02: Use of the Style Guide Module 03: Spelling and Grammar Module 04: Paper-based Proofreading Module 05: On the Screen Proofreading Module 06: Basics of Copy Editing Module 07: Copy Editing - the Use of Language Module 08: Copy Editing - Checking Accuracy and Facts Module 09: Copy Editing - Legal Checks Module 10: Career Development ------------------- ***Dealing With Difficult People*** Module 01: Difficult People and Their Difficult Behaviour Module 02: Communicating With Difficult People Module 03: Standing Up to Difficult People Module 04: A Quick Guide to the Seven Classically Difficult Types Module 05: Dealing with Bosses Who Drive You Barmy Module 06: Colleagues to Throttle Module 07: Dealing With Impossible People Module 08: The Temper Tantrum Type ------------------- ***Level 2 Award in Job Search and Interview Skills*** Module 01: Preparing to Achieve Own Job Goals Module 02: Promoting Yourself and Preparing for a Job Interview ------------------- ***Level 2 Customer Service*** Module 1: Introduction to Customer Service Module 2: Understanding the Organisation Module 3: Prepare to Deliver Excellent Customer Service Module 4: Communication in the Customer Service Role Module 5: Understand Customers ------------------- ***Mental Health Support Worker*** Module 01: An Overview of Mental Health Module 02: Mental Health Support Worker Module 03: Understanding Childhood and Adolescent Psychiatric Disorders Module 04: Understanding Stress and Anxiety Disorders Module 05: Understanding Schizophrenia Module 06: Understanding Personality Disorders Module 07: Understanding Mood Disorders Module 08: Understanding Eating & Sleeping Disorders Module 09: Understanding Self-Harm and Suicide Module 10: Treating Mental Illness with Medication and Therapy Module 11: Laws Related to Mental Health Module 12: Mental Health System Module 13: The Participation of the Service User ------------------- ***Workplace Stress Management*** Module 01: Workplace Stress Module 02: Rational and Irrational Beliefs Module 03: The ABC Framework of REBT Module 04: Cognitive Therapy (CT) Module 05: Cognitive Behavioural Therapy (CBT) in the Workplace Module 06: Conclusion ------------------- ***Anger Management*** Module 01: Introduction to Anger Module 02: The Process in Anger Module 03: Effect of Anger on Our Thinking Module 04: How to Manage Anger ------------------- Assessment Method After completing each module of the Medical Secretary & Receptionist, you will find automated MCQ quizzes. To unlock the next module, you need to complete the quiz task and get at least 60% marks. Once you complete all the modules in this manner, you will be qualified to request your certification. Certification After completing the MCQ/Assignment assessment for this Medical Secretary & Receptionist, you will be entitled to a Certificate of Completion from Training Tale. It will act as proof of your extensive professional development. The certificate is in PDF format, which is completely free to download. A printed version is also available upon request. It will also be sent to you through a courier for £13.99. Who is this course for? Medical Secretary & Receptionist is ideal for Health Care Professionals who work and will be working in healthcare settings such as hospitals, clinics, and healthcare facilities. Requirements Students who intend to enrol in this course must meet the following requirements: Good command of the English language Must be vivacious and self-driven Basic computer knowledge A minimum of 16 years of age is required Career path After completing this Medical Secretary & Receptionist, you will have developed a set of skills necessary for career advancement and will be able to pursue a variety of job opportunities, including - Medical Receptionist Medical Secretary Healthcare Administrator GP Receptionist Patient Coordinator Certificates Certificate of completion Digital certificate - Included

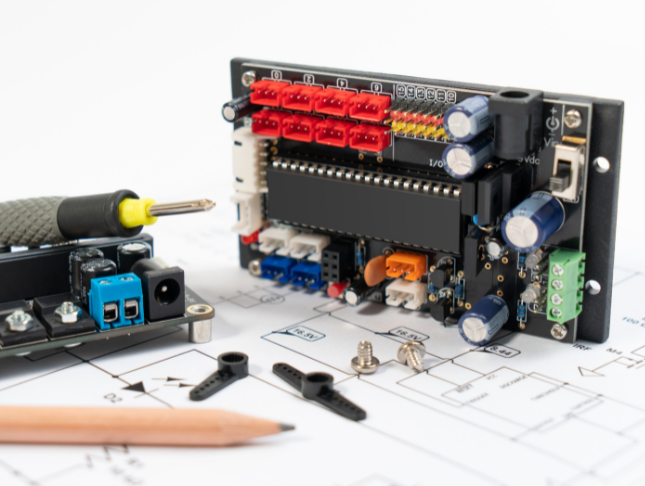
Join us on a thought-provoking trip into the core of technology with our 'Embedded Systems with 8051 Microcontroller' course. Picture yourself unraveling the mysteries of embedded systems and delving into the intricacies of the 8051 microcontroller. This course is not just a series of modules; it's an odyssey into the world of programming, interfacing, and innovation. From the foundational concepts of embedded systems to the nitty-gritty of program creation for the 8051, each module is a stepping stone towards mastery. Imagine crafting projects that involve LED alternations, switch interfacing, and even the precise control of DC motors and relays. Join us, and let the 8051 microcontroller be your passport to unlocking a realm where circuits come to life, timers dictate precision, and serial communication is your language of control. As you progress through units on LCD and ADC interfacing, envision yourself creating schematics, writing code, and connecting with the essence of each concept. This course transcends theoretical knowledge, offering hands-on experience in program downloading using Nuvoton ICSP programmer and FlashMagic. The journey concludes not just with a module on conclusions but with a sense of empowerment, equipped with the skills to conquer the intricate world of embedded systems. Learning Outcomes Master the fundamentals of embedded systems, from the basics to the intricate workings of the 8051 microcontroller. Acquire proficiency in software installation, including the setup of the Keil IDE and the creation of initial projects. Develop expertise in input and output interfacing, covering LED concepts, for loops, and switch interfacing with the 8051. Explore advanced concepts, such as DC motor and relay interfacing, LCD concepts, and serial communication principles. Gain hands-on experience in timer concepts, timer as a counter, and analog-to-digital conversion with the LM35 temperature sensor, along with the practical skills of program downloading. Why choose this Embedded Systems with 8051 Microcontroller course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this Embedded Systems with 8051 Microcontroller course for? Electronics enthusiasts eager to delve into embedded systems and microcontroller programming. Students and beginners seeking a comprehensive understanding of 8051 microcontroller applications. Hobbyists with a keen interest in hands-on projects involving LEDs, switches, motors, and more. Aspiring engineers looking to enhance their skills in the field of embedded systems. DIY enthusiasts interested in crafting innovative projects with practical applications. Career path Embedded Systems Engineer: £40,000 - £60,000 Electronics Design Engineer: £35,000 - £55,000 Control Systems Engineer: £40,000 - £65,000 Microcontroller Programmer: £30,000 - £50,000 Hardware Development Engineer: £35,000 - £60,000 Automation Specialist: £45,000 - £70,000 Prerequisites This Embedded Systems with 8051 Microcontroller does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Embedded Systems with 8051 Microcontroller was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Unit 01: Introduction Module 01: Introduction to the Course 00:03:00 Module 02: Introduction to Embedded Systems 00:20:00 Module 03: Introduction to 8051 Controller 00:15:00 Module 04: Program for 8051 00:13:00 Unit 02: Software Installation Module 01: Installation of Keil IDE 00:05:00 Module 02: First Project creation on Keil 00:05:00 Unit 03: Input And Output Interfacing Module 01: Concepts on LED 00:12:00 Module 02: Project based on Led Alternate on off 00:04:00 Module 03: Using For Loop 00:05:00 Unit 04: 8051 Interfaces Module 01: Switch Interfacing with 8051 00:13:00 Unit 05: Interfacing With DC Motor And Relay Module 01: Relay Interfacing 00:11:00 Module 02: Relay Interfacing Part 2 00:03:00 Module 03: Introduction to DC Motor 00:09:00 Module 04: DC Motor Interfacing Part 2 00:07:00 Unit 06: Concepts On LCD Module 01: Introduction to LCD 00:09:00 Module 02: Creating Schematics for LCD 00:07:00 Module 03: First Program on LCD 00:07:00 Module 04: LCD Interfacing - 4 00:08:00 Unit 07: Concepts On Serial Module 01: Serial Part-01 00:07:00 Module 02: Serial Part-02 00:13:00 Module 03: Serial Part-03 00:08:00 Module 04: Serial Part-04 00:08:00 Unit 08: Timer Concepts Module 01: Timer Part-01 00:08:00 Module 02: Timer Part-02 00:07:00 Module 03: Timer Part-03 00:06:00 Unit 09: Timer As Counter Module 01: Timer as Counter 00:08:00 Unit 10: ADC With LM35 Module 01: Analog to Digital Converter with 8051 - Part 1 00:10:00 Module 02: Analog to Digital Converter with 8051 - Part 2 00:07:00 Module 03: Analog to Digital Converter with 8051 - Part 3 00:10:00 Module 04: Analog to Digital Converter with 8051 use LM35 Temperature Sensor 00:11:00 Unit 11: Stepper Motor And Program For Stepper Motor Module 01: Concepts around Stepper Motor [34] 00:15:00 Unit 12: Program Downloading Module 01: Program Downloading Using Nuvoton ICSP Programmer 00:09:00 Module 02: Program (Hex File) Downloading using FlashMagic to P89v51RD2 Controller 00:16:00 Unit 13: Conclusion Conclusion 00:01:00
ArcGIS Desktop for Spatial Analysis: Go from Basic to Pro
By Packt
Gain proficiency in the mastery of Geographic Information Systems (GIS) via ArcGIS Desktop

Mental Health with Positive Psychology
By IOMH - Institute of Mental Health
Join our Mental Health with Positive Psychology course and discover your hidden skills, setting you on a path to success in this area. Get ready to improve your skills and achieve your biggest goals. The Mental Health with Positive Psychology course has everything you need to get a great start in this sector. Improving and moving forward is key to getting ahead personally. The Mental Health with Positive Psychology course is designed to teach you the important stuff quickly and well, helping you to get off to a great start in the field. So, what are you looking for? Enrol now! You will Learn The Following Things: Learn strategies to boost your workplace efficiency. Hone your skills to help you advance your career. Acquire a comprehensive understanding of various topics and tips. Learn in-demand skills that are in high demand among UK employers This course covers the topic you must know to stand against the tough competition. The future is truly yours to seize with this Mental Health with Positive Psychology. Enrol today and complete the course to achieve a certificate that can change your career forever. Details Perks of Learning with IOMH One-to-one support from a dedicated tutor throughout your course. Study online - whenever and wherever you want. Instant Digital/ PDF certificate 100% money back guarantee 12 months access Process of Evaluation After studying the course, an MCQ exam or assignment will test your skills and knowledge. You have to get a score of 60% to pass the test and get your certificate. Certificate of Achievement After completing the Mental Health with Positive Psychology course, you will receive your CPD-accredited Digital/PDF Certificate for £5.99. To get the hardcopy certificate for £12.99, you must also pay the shipping charge of just £3.99 (UK) and £10.99 (International). Who Is This Course for? This Mental Health with Positive Psychology is suitable for anyone aspiring to start a career in relevant field; even if you are new to this and have no prior knowledge, this course is going to be very easy for you to understand. On the other hand, if you are already working in this sector, this course will be a great source of knowledge for you to improve your existing skills and take them to the next level. This course has been developed with maximum flexibility and accessibility, making it ideal for people who don't have the time to devote to traditional education. Requirements There is no prerequisite to enrol in this course. You don't need any educational qualification or experience to enrol in the Mental Health with Positive Psychology course. Do note: you must be at least 16 years old to enrol. Any internet-connected device, such as a computer, tablet, or smartphone, can access this online course. Career Path The certification and skills you get from this Mental Health with Positive Psychology Course can help you advance your career and gain expertise in several fields, allowing you to apply for high-paying jobs in related sectors. Course Curriculum Section 01: Models of Positive Psychology Introduction to Positive Psychology 00:02:00 Overview of the Course 00:02:00 What is Positive Psychology? 00:09:00 Health Model 00:03:00 IAC Model 00:09:00 Uncovering Automatic Thoughts 00:04:00 Understanding Feedback Loops 00:04:00 Learned Optimisation 00:24:00 Positive Thinking 00:19:00 Limited Thinking Patterns 00:24:00 Positive Attitude New 00:13:00 Self-Image Selection New 00:01:00 Section 02: Healthy Self Esteem Concept of Self Image 00:05:00 Experience Changes Self Image 00:03:00 Synthetic Experience 00:08:00 Experiences Prove 00:01:00 Self-Consistency & Association 00:05:00 Power of Suggestion 00:07:00 Perception Reality 00:05:00 Goal Striving Beings 00:04:00 Let the Dog Sleep 00:04:00 Habit of Happiness 00:05:00 Success Mechanism 00:04:00 Failure Mechanism 00:03:00 Unlock Real Personality 00:05:00 Mind Room 00:02:00 Becoming Alive 00:06:00 Getting the Winning Feeling 00:02:00 For Past 00:03:00 For Present 00:02:00 For Future 00:01:00 Other Areas and Role Playing 00:03:00 Section 03: Sleep Better Introduction 00:06:00 Understanding Sleep 00:28:00 Drive for Deep Sleep 00:08:00 Sleep Schedule 00:06:00 Quite Your Mind 00:09:00 Buffer Zone 00:12:00 Relaxation Exercises 00:02:00 Abdominal Breathing 00:05:00 PMR 00:06:00 Cue Controlled Relaxation 00:02:00 Visualization 00:04:00 Think like a Good Sleeper 00:09:00 Focus on Day 00:12:00 Section 04: Bonus Essentialism 02:47:00 Section 05: Conclusion Conclusion 00:01:00

Geomechanics at Well and Field Scale
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course Geomechanical evaluations are about the assessment of deformations and failure in the subsurface due to oil & gas production, geothermal operations, CO2 storage and other operations. All geomechanical evaluations include four types of modelling assumptions, which will be systematically addressed in this training, namely: 1. Geometrical modelling assumption: Impact of structural styles on initial stress and stress redistribution due to operations 2. Formation (or constitutive) behaviour: Linear elastic and non-linear behaviour, associated models and their parameters, and methods how to constrain these using 3. Initial stress: Relation with structural setting and methods to quantify the in-situ stress condition 4. Loading conditions: Changes in pore pressure and temperature on wellbore and field scale This 5 full-day course starts with the determination of the stresses in the earth, the impact of different structural styles, salt bodies, faulting and folding on the orientation of the three main principal stress components. Different (field) data sources will be discussed to constrain their magnitude, while exercises will be made to gain hands-on experience. Subsequently, the concepts of stress and strain will be discussed, linear elasticity, total and effective stress and poro-elasticity in 1D, 2D and 3D, as well as thermal expansion. Participants will be able to construct and interpret a Mohr-circles. Also, different failure mechanisms and associated models (plastic, viscous) will be discussed. All these concepts apply on a material point level. Next, geomechanics on the wellbore scale is addressed, starting with the stress distribution around the wellbore (Kirsch equations). The impact of mudweight on shear and tensile failure (fracturing) will be calculated, and participants will be able to determine the mudweight window stable drilling operations, while considering well deviation and the use of oil-based and water-based muds (pore pressure penetration). Fracturing conditions and fracture propagation will be addressed. Field-scale geomechanics is addressed on the fourth day, focussing on building a 3D geomechanical model that is fit-for-purpose (focussing on the risks that need evaluation). Here, geological interpretation (layering), initial stress and formation property estimation (from petrophysical logs and lab experiments) as well as determining the loading conditions come together. The course is concluded with interpretation of the field-wide geomechanical response to reservoir depletion with special attention to reservoir compaction & subsidence, well failure and fault reactivation & induced seismicity. Special attention is paid to uncertainties and formulating advice that impacts decision-making during development and production stages of a project. This course can also be offered through Virtual Instructor Led Training (VILT) format. Training Objectives Upon completing of this course, the participants will be able to: Identify potential project risks that may need a geomechanical evaluation Construct a pressure-depth plot based on available field data (density logs, (X)LOT, FIT, RFT) Employ log-based correlation function to estimate mechanical properties Produce a simplified, but appropriate geometrical (layered, upscaled) model that honours contrasts in initial stress, formation properties and loading conditions, including Construct and interpret a Mohr-circle for shear and tensile failure Calculate the mud weight that leads to shear and tensile failure (fracturing conditions) Identify potential lab experiments to measure required formation properties Describe the workflow and data to develop a field-wide fit-for-purpose geomechanical model Discuss the qualitative impact of pressure and temperature change on the risk related to compaction, well failure, top-seal integrity and fault reactivation Target Audience This course is intended for Drilling Engineers, Well Engineers, Production Technologists, Completion Engineers, Well Superintendents, Directional Drillers, Wellsite Supervisors and others, who wish to further their understanding of rock mechanics and its application to drilling and completion. There is no specific formal pre-requisite for this course. However, the participants are requested to have been exposed to drilling, completions and production operations in their positions and to have a recommended minimum of 3 years of field experience. Course Level Intermediate Trainer Your expert course leader has over 30 years of experience in the Oil & Gas industry, covering all geomechanical issues in the petroleum industry for Shell. Some of his projects included doing research and providing operational advice in wellbore stability, sand failure prediction, and oil-shale retortion among others. He guided multi-disciplinary teams in compaction & subsidence, top-seal integrity, fault reactivation, induced-seismicity and containment. He was also involved in projects related to Carbon Capture Storage (CCS). He is the founding father of various innovations and assessment tools, and developed new insights into the root causes seismicity induced by Oil & Gas production. Furthermore, he was the regional coordinator for technology deployment in Africa, and Smart Fields (DOFF, iField) design advisor for Shell globally. He was responsible for the Geomechanical competence framework, and associated virtual and classroom training programme in Shell for the last 10 years. He served as one of the Subject Matter Expert (SME) on geomechanics, provided Technical Assurance to many risk assessments, and is a co-author of Shell's global minimun standard on top-seal integry and containment. He has a MSc and PhD in Civil Engineering and computational mechanics from Delft University of Technology, The Netherlands. Training experience: Developed and delivered the following (between 2010 and 2020): The competence framework for the global geomechanical discipline in Shell Online Geomechanical training programs for petroleum engineers (post-doc level) The global minimum standard for top-seal integrity assessment in Shell Over 50 learning nuggets with Subject Matter Experts Various Shell virtual Geomechanical training courses covering all subjects Developed Advanced Geomechanical training program for experienced staff in Shell Coaching of KPC staff on Geomechanics and containment issues on an internship at Shell in The Netherlands, Q4 2014 Lectured at the Utrecht University summer school (The Netherlands, 2020) on induced seismicity among renowned earthquake experts (Prof. Mark Zoback, Prof. Jean-Philippe Avouac, Prof. Jean-Pierre Ampuero and Prof. Torsten Dahm) (https://www.nwo.nl/onderzoeksprogrammas/deepnl/bijeenkomsten/6-10-juli-2020-deepnl-webinar-series-induced-seismicity) Lectured at the Danish Technical University summer school (Copenhagen, 2021) summer school on Carbon Capture and Storage (https://www.oilgas.dtu.dk/english/Events/DHRTC-Summer-School) Virtual Carbon Capture and Storage (CCS): Project Risks & How to Manage Them training course (October and November 2021) POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

Diploma in Visual Effects for Film and Television Animation
By ATL Autocad Training London
Who is this course for? The Diploma in Visual Effects for Film and Television Animation is tailored for individuals aspiring to work in the Visual Effects, TV, Film, and 3D animation industry. Gain essential skills necessary for a successful career in these fields. Click here for more info: Website Duration: 120 hours of 1-on-1 Training. When can I book: 9 am - 4 pm (Choose your preferred day and time once a week). Monday to Saturday: 9 am - 7 pm (Flexible timing with advance booking). Course Overview for a 120-Hour Diploma Program in Game Design and Development Term 1: Introduction to Game Design and 3D Modeling (40 hours) Module 1: Introduction to Game Design (1 hour) Understanding the game development industry and current trends Exploring game mechanics and fundamental design principles Introduction to the game engines and tools utilized in the program Module 2: 3D Modeling with 3ds Max (25 hours) Familiarization with 3ds Max and its user interface Mastering basic modeling techniques like box modeling and extrusion Advanced modeling skills including subdivision and topology Texturing and shading techniques tailored for game development Module 3: Character Design and Animation (10 hours) Introduction to character design and its developmental process Creating and rigging characters specifically for games Keyframe animation techniques for character movement Term 2: Game Development and Unity 3D (40 hours) Module 4: Unity 3D Basics (20 hours) Navigating Unity 3D and understanding its interface Grasping fundamental game development concepts within Unity Creating game objects, writing scripts, and designing scenes Introduction to scripting using C# Module 5: Advanced Game Development with Unity 3D (10 hours) Constructing game mechanics including UI, scoring, and game states Working with physics and collision systems in Unity Crafting intricate game environments and level designs Module 6: Game Assets with Photoshop (10 hours) Exploring Photoshop tools and features for game asset creation Crafting game elements such as textures, sprites, and icons Optimizing assets for seamless integration into game development Term 3: Advanced Game Design and Portfolio Development (40 hours) Module 7: Advanced Game Design (20 hours) Delving into advanced game design concepts like balancing and difficulty curves Understanding player psychology and methods for engaging audiences Implementing game analytics and user testing for refinement Module 8: Portfolio Development (24 hours) Building a comprehensive portfolio showcasing acquired skills Effective presentation techniques for showcasing work Establishing a professional online presence and networking strategies Final Project: Creating and presenting a collection of best works in collaboration with tutors and fellow students Please note: Any missed sessions or absence without a 48-hour notice will result in session loss and a full class fee charge due to the personalized one-to-one nature of the sessions. Students can request pauses or extended breaks by providing written notice via email. What can you do after this course: Software Proficiency: Master industry-standard design tools for architectural and interior projects. Design Expertise: Develop a deep understanding of design principles and spatial concepts. Visualization Skills: Acquire advanced 2D/3D rendering and virtual reality skills for realistic design representation. Communication and Collaboration: Enhance communication skills and learn to collaborate effectively in design teams. Problem-Solving: Develop creative problem-solving abilities for real-world design challenges. Jobs and Career Opportunities: Architectural Visualizer Interior Designer CAD Technician Virtual Reality Developer 3D Modeler Project Coordinator Freelance Designer Visualization Consultant Students can pursue these roles, applying their expertise in architectural and interior design across various professional opportunities. Course Expectations: Maintain a dedicated notebook to compile your study notes. Schedule makeup sessions for any missed coursework, subject to available time slots. Keep meticulous notes and maintain a design folder to track your progress and nurture creative ideas. Allocate specific time for independent practice and project work. Attain certification from the esteemed professional design team. Post-Course Proficiencies: Upon successful course completion, you will achieve the following: Develop confidence in your software proficiency and a solid grasp of underlying principles. Demonstrate the ability to produce top-tier visuals for architectural and interior design projects. Feel well-prepared to pursue positions, armed with the assurance of your software expertise. Continued Support: We are pleased to offer lifetime, complimentary email and phone support to promptly assist you with any inquiries or challenges that may arise. Software Accessibility: Access to the required software is available through either downloading it from the developer's website or acquiring it at favorable student rates. It is important to note that student software should be exclusively utilized for non-commercial projects. Payment Options: To accommodate your preferences, we provide a range of payment options, including internet bank transfers, credit cards, debit cards, and PayPal. Moreover, we offer installment plans tailored to the needs of our students. Course Type: Certification. Course Level: Basic to Advanced. Time: 09:00 or 4 pm (You can choose your own day and time once a week) (Monday to Friday, 09 am to 7 pm, you can choose anytime by advance booking. Weekends can only be 3 to 4 hrs due to heavy demand on those days). Tutor: Industry Experts. Total Hours: 120 Price for Companies: £3500.00 (With VAT = £4200) For Companies. Price for Students: £3000.00 (With VAT = £3600) For Students.

Cryptocurrency Online Course
By Compete High
Overview Bitcoin, Ethereum, NFT - these cryptocurrencies and blockchain-based concepts have become buzzwords lately that everybody talks about all the time when hardly anybody can explain the terms clearly. Whether we understand them properly or not, blockchain and cryptocurrency will soon dominate the whole world financially and technologically. Jobs related to these concepts are at an all-time high in demand too. So, it's your choice if you want to get left behind, or you want to stand out from the crowd by learning about blockchain & cryptocurrency inside out. Compete High assures you a complete online course on cryptocurrency that'll teach you everything from scratch. This carefully-crafted online training packs all the required relevant information complied into one place so you don't have to elsewhere or waste your time in finding the right resources. The course materials of this online course on Cryptocurrency have been prepared with consultation from the relevant experts. The information available on Cryptocurrency is kept up to date regularly so that learners don't get left behind on the current trends/updates. The following key topics have been covered in the learning materials of this cryptocurrency training: The concept of money & basics of cryptocurrency Types & categories of cryptocurrency Investing in cryptocurrency (dividends, decentralization etc.) Risk assessment & management in crypto Basics of blockchain Blockchain terminologies essential for cryptocurrency Exchanging/buying-selling crypto Cryptocurrency wallet Identifying potential crypto investment ICO Mining Technical analysis in crypto investment Trading strategies Taxation in crypto investment NFT DEFI The self-paced online learning methodology from Compete High helps you learn whenever or however you wish - keeping in mind the busy schedule of the learners or the possible inconveniences that come with physical classes. The bite-sized lessons are proven to be most effective in memorising and learning them by heart. On top of that, you have the option to receive a certificate of accomplishment after successfully completing the course! So, instead of searching for hours, enrol right away on this Cryptocurrency course from Compete High and accelerate your career on the right path with expert-outlined lessons and a guarantee of success in the long run. Who is this course for? While it's clear that we don't discourage anyone or impose restrictions on enrolling and learning something new from this Cryptocurrency course, people falling under any of the following criteria will benefit the most: Anyone looking for the basics of Cryptocurrency, People aiming to start trading/investing in Cryptocurrency, Jobseekers in the field of Cryptocurrency/Blockchain/NFT, Anyone looking for a certificate of completion on doing an online training on Cryptocurrency, Anyone with a general interest/curiosity in this topic. Career Path The earning potential is endless if you start investing/trading cryptocurrency after completing this course. Apart from that, this course is the perfect gateway for a rewarding career ahead in the emerging tech industries dealing with cryptocurrency/blockchain/NFT. Cryptocurrency is the future, and this course holds the key to opening up the doorway of limitless opportunities for you in that future. Course Curriculum Module 1 - Introduction to Cryptocurrency Introduction to Cryptocurrency 00:00 Module 2 - Types of Cryptocurrencies Types of Cryptocurrencies 00:00 Module 3 - Why Invest in Cryptocurrencies Why Invest in Cryptocurrencies 00:00 Module 4 - Recognizing the Risks Upfront Recognizing the Risks Upfront 00:00 Module 5 - Basics of Blockchain Technology Basics of Blockchain Technology 00:00 Module 6 - How Cryptocurrencies Use Blockchain Technology How Cryptocurrencies Use Blockchain Technology 00:00 Module 7 - Cryptocurrency Exchanges and Brokers Cryptocurrency Exchanges and Brokers 00:00 Module 8 - How to Use Cryptocurrency Wallets How to Use Cryptocurrency Wallets 00:00 Module 9 - Identifying Top Performing Cryptos Identifying Top Performing Cryptos 00:00 Module 10 - Investing in ICOs Investing in ICOs 00:00 Module 11 - Cryptocurrency Mining Cryptocurrency Mining 00:00 Module 12 - Dealing with Dollars and Other Fiat Currencies Dealing with Dollars and Other Fiat Currencies 00:00 Module 13 - Using Technical Analysis in Crypto Investment Using Technical Analysis in Crypto Investment 00:00 Module 14 - Short Term vs. Long Term Trading Strategies Short Term vs. Long Term Trading Strategies 00:00 Module 15 - Cryptocurrency Taxes Cryptocurrency Taxes 00:00 Module 16 - Ultimate Tips to Kickstart Cryptocurrency Investing Ultimate Tips to Kickstart Cryptocurrency Investing 00:00 Module 17 - NFTs or Non-Fungible Tokens NFTs or Non-Fungible Tokens 00:00 Module 18 - DEFI (Decentralized Finance) DEFI (Decentralized Finance) 00:00

Structural Design Patterns in Modern C++
By Packt
Discover the power of modern C++ design patterns, including adapter, façade, and composite. This course provides a comprehensive understanding of each pattern, complete with real-world examples to help you confidently implement them in your projects and build efficient, scalable software like a pro.

Digital Marketing Course - E-Commerce Store
By Lead Academy
Quality Guarantee: Promising training excellence, satisfaction gurantee Accredited by CPD UK & Quality License Scheme Tutor Support Unlimited support via email, till you complete the course Recognised Certification: Accepted by thousands of professional bodies Start Anytime With 1 year access to the course materials Online Learning Learn from anywhere, whenever you want In this course, you will learn the tactics to drive targeted traffic, optimise conversions and boost sales in the world of online retail. From SEO to Email marketing and social media strategies you will master the skills of promoting your E-commerce store effectively. This course at a glance Accredited by CPD UK Endorsed by Quality Licence Scheme Learn the concepts of email marketing, e-commerce and digital marketing Understand the rules for email marketing Recognise types of email marketing campaigns you should already be using Get acquainted with the 10 email marketing terms every marketer should know Learn the tips for building responsive email marketing lists Know the importance of lead capture pages in email marketing Learn to acquire leads from Facebook Discover the importance of a sales funnel in email marketing Recognise the 10 ways to make people actually read your emails and much more Why Digital Marketing Course right for you? This online digital marketing e-commerce store course will provide you with a comprehensive understanding of e-commerce and digital marketing and how digital marketing can be beneficial for e-commerce stores. You will also learn the concept of email marketing and various other marketing strategies to elevate the marketing campaign of the e-commerce store. This extensive online digital marketing e-commerce store course will also help you recognise the importance of list cleaning and segmentation tags. You will also understand how to get leads from Facebook and some great email marketing campaigns. By the end of the course, you will acquire the understanding and knowledge required to run a successful email campaign for an e-commerce store. You will also develop the necessary skills to become a successful email marketer. Digital Marketing Course Details Accredited by CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. Course Curriculum Introduction Review of Course Introduction The Concepts of Email Marketing Rules of Email Marketing Types of Email Marketing Campaigns You Should Already be Using 10 Email Marketing Terms Every Marketer Should Know The Importance of List Cleaning and Segmentation Tags Tips for Building Responsive Email Marketing Lists Using Capture Pages and Funnels for Leads The Importance of Lead Capture Pages in Email Marketing The Importance of a Sales Funnel in Email Marketing Getting Leads from Facebook Types of Landing Pages and How to Use Them Types Of Online Sales Funnels That Work Really Well Creating Email Lists What Makes an Email List Valuable? What is a Double Opt-in Email List and Why is It Important? How eBooks Help Generate Leads and Fill Sales Pipelines How to Generate More Leads with Your Video Marketing Easy Ideas for Lead-Generating Content Marketing to Build Your Lists Email Copywriting Email Copy-writing Tips to Write Engaging Content Subscribers Want to Read 10 Ways to Make People Actually Read Your Emails 9 Ways to Make Your Emails More Engaging 6 Psychological Triggers to Turn Email Marketing Prospects into Loyal Customers 17 Tips for Writing Email Marketing Copy that Converts Email Deliverability 7 Best Practices for Email Deliverability How to Improve Your Email Deliverability (Step-by-Step) Blueprints for Email Copywriting 7 Ways to Improve Your Email Deliverability How to Test Your Email Deliverability? A Step-by-Step Guide Email Automation What is Email Automation & How Can Your Business Use it? What is an Email Marketing Autoresponder? 16 Awesome Email Marketing Campaigns & How to Run Your Own 9 Simple (But Powerful) Automated Email Sequences For Service Businesses Using Tags to Gaining Useful Insights From Email Segmentation Using Tags to Gaining Useful Insights From Email Segmentation Who should take this course? This comprehensive digital marketing - e-commerce store course is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of email marketing. Entry Requirements There are no academic entry requirements for this digital marketing - e-commerce store course, and it is open to students of all academic backgrounds. However, you are required to have a laptop/desktop/tablet or smartphone and a good internet connection. Assessment Method This digital marketing e-commerce store course assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner could grasp from each section. In the assessment pass mark is 60%. Certification Endorsed Certificate from Quality Licence Scheme After successfully passing the MCQ exam you will be eligible to order the Endorsed Certificate by Quality Licence Scheme. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. There is a Quality Licence Scheme endorsement fee to obtain an endorsed certificate which is £65. Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs Is CPD a recognised qualification in the UK? CPD is globally recognised by employers, professional organisations and academic intuitions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD-certified certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Are QLS courses recognised? Although QLS courses are not subject to Ofqual regulation, they must adhere to an extremely high level that is set and regulated independently across the globe. A course that has been approved by the Quality Licence Scheme simply indicates that it has been examined and evaluated in terms of quality and fulfils the predetermined quality standards. When will I receive my certificate? For CPD accredited PDF certificate it will take 24 hours, however for the hardcopy CPD certificate takes 5-7 business days and for the Quality License Scheme certificate it will take 7-9 business days. Can I pay by invoice? Yes, you can pay via Invoice or Purchase Order, please contact us at info@lead-academy.org for invoice payment. Can I pay via instalment? Yes, you can pay via instalments at checkout. How to take online classes from home? Our platform provides easy and comfortable access for all learners; all you need is a stable internet connection and a device such as a laptop, desktop PC, tablet, or mobile phone. The learning site is accessible 24/7, allowing you to take the course at your own pace while relaxing in the privacy of your home or workplace. Does age matter in online learning? No, there is no age limit for online learning. Online learning is accessible to people of all ages and requires no age-specific criteria to pursue a course of interest. As opposed to degrees pursued at university, online courses are designed to break the barriers of age limitation that aim to limit the learner's ability to learn new things, diversify their skills, and expand their horizons. When I will get the login details for my course? After successfully purchasing the course, you will receive an email within 24 hours with the login details of your course. Kindly check your inbox, junk or spam folder, or you can contact our client success team via info@lead-academy.org

Advanced Xero Training Course
By Lead Academy
This advanced course is designed for those who want to enhance their expertise in using zero software and want to excel in this field. With a focus on advanced concepts, intricate problem solving and practical application, you will go beyond the basics and solve complex calculations. This Course At A Glance Accredited by CPD UK Endorsed by Quality Licence Scheme Learn how to use Xero confidently Recognise the advanced features of Xero Learn Xero basic and advanced aspects of accounting and bookkeeping Learn about the chart of accounts Know how to import data using Xero Understand what are the tracking categories and how to track inventory Learn how to deal with multi-currency bills Know how to handle expense claims, multi-currency sales, billable expenses and much more. Get a comprehensive understanding of fixed assets and depreciation Advanced Xero Training Course Overview This online Advanced Xero Training course will provide you with a comprehensive understanding of Xero and its fundamental aspects. You will also learn Xero's advanced strategies and concepts you should implement to become a successful bookkeeper or accountant. This career advancement online Xero Training course UK will help you understand what are the tracking categories and how to track inventory. You will also learn Xero's basic and advanced aspects of accounting and bookkeeping by taking this popular online course. By the end of the course, you will obtain the knowledge required to boost your accounting and bookkeeping skills and master Xero. You will also understand the process of handling expense claims, multi-currency sales, billable expenses and much more. This course is endorsed by the Quality Licence Scheme for its high-quality, non-regulated provision and training programmes. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. This course and/or training programme is not regulated by Ofqual and is not an accredited qualification. Your training provider will be able to advise you on any further recognition, for example, progression routes into further and/or higher education. For further information, please visit the Learner FAQs on the Quality Licence Scheme website. Who should take this course? This comprehensive Advanced Xero training course UK is suitable for anyone looking to improve their job prospects or aspiring to accelerate their career in this sector and want to gain in-depth knowledge of Xero accounting and bookkeeping. Entry Requirement There are no academic entry requirements for this Xero advanced course, and it is open to students of all academic backgrounds. However, you are required to have a laptop/desktop/tablet or smartphone and a good internet connection. Assessment Method This advanced Xero certification course UK assesses learners through multiple-choice questions (MCQs). Upon successful completion of the modules, learners must answer MCQs to complete the assessment procedure. Through the MCQs, it is measured how much a learner could grasp from each section. In the assessment pass mark is 60%. Check out our Accounting, Finance and Payroll Management Online Training Bundle and gain the skills and knowledge you need to succeed in today's competitive job market. Our comprehensive courses are designed to provide practical, real-world training that will help you advance your career. Course Curriculum Introduction Introduction Importing Data Part 1 Importing Data Part 1 Importing Data Part 2 Importing Data Part 2 Tracked Inventory Part 1 Tracked Inventory Part 1 Tracked Inventory Part 2 Tracked Inventory Part 2 Tracked Inventory Part 3 Tracked Inventory Part 3 Tracking Categories Part 1 Tracking Categories Part 1 Tracking Categories Part 2 Tracking Categories Part 2 Projects Part 1 Projects Part 1 Projects Part 2 Projects Part 2 Projects Part 3 Projects Part 3 Expenses Claims Part 1 Expenses Claims Part 1 Expenses Claims Part 2 Expenses Claims Part 2 Multi Currency Intro Multi Currency Intro Multi Currency Bills Multi Currency Bills Multi Currency Bank Rec Multi Currency Bank Rec Multi Currency Sales Invs Multi Currency Sales Invs Billable Expenses Billable Expenses Fixed Assets and Dreciation Fixed Assets and Dreciation Depreciation Part 2 Depreciation Part 2 Find and Recode Find and Recode Conclusions Conclusions Assessment Assessment - Xero Advanced Course Recognised Accreditation CPD Certification Service This course is accredited by continuing professional development (CPD). CPD UK is globally recognised by employers, professional organisations, and academic institutions, thus a certificate from CPD Certification Service creates value towards your professional goal and achievement. CPD certificates are accepted by thousands of professional bodies and government regulators here in the UK and around the world. Many organisations look for employees with CPD requirements, which means, that by doing this course, you would be a potential candidate in your respective field. Quality Licence Scheme Endorsed The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. Certificate of Achievement Endorsed Certificate from Quality Licence Scheme After successfully passing the MCQ exam you will be eligible to order the Endorsed Certificate by Quality Licence Scheme. The Quality Licence Scheme is a brand of the Skills and Education Group, a leading national awarding organisation for providing high-quality vocational qualifications across a wide range of industries. It will give you a competitive advantage in your career, making you stand out from all other applicants and employees. There is a Quality Licence Scheme endorsement fee to obtain an endorsed certificate which is £65. Certificate of Achievement from Lead Academy After successfully passing the MCQ exam you will be eligible to order your certificate of achievement as proof of your new skill. The certificate of achievement is an official credential that confirms that you successfully finished a course with Lead Academy. Certificate can be obtained in PDF version at a cost of £12, and there is an additional fee to obtain a printed copy certificate which is £35. FAQs How is the advanced Xero training course different from the introductory Xero course? The introductory Xero course will introduce you to the concept of Xero, including how it works, what it is and more, but the advanced Xero course will make you an expert on using it to solve accounting issues. It will uncover all the features related to the Xero software. How will I get access to the course Materials? You will get access to the course materials once you purchase the course. After gaining access permission via an email account, you can access the course and materials simultaneously. What is the lifetime access facility about? Lead Academy provides lifetime access facilities to its learners. It means that once learners purchase any course, they can access the course material for a lifetime, even after completing it. Is Xero popular in the UK and the world? Xero is known as the most used software for business organisations in the UK and the world. Over 180 countries depend on and use this application. What does Xero use for? Companies use Xero accounting software to manage their entire accounting process and record accounting transactions. What Is Xero? It is a cloud-based accounting software platform for small and medium-sized enterprises which includes capabilities for invoicing, bank reconciliation, inventory management, payroll, financial reporting etc. It allows users to access their financial data from any location and collaborate with their accountant or bookkeeper in real time. What are the benefits of using Xero? There are several benefits, including faster payment processing, time savings, accessibility from anywhere at any time, data security, automatic updates and backups, improved business efficiency etc. What is the benefit of doing an accredited course? You will only realize the benefit of having a CPD-accredited certificate once you face the corporate world. As employees, job places, and more value the CPD-accredited certificate, you must own this certificate by doing the course with us. What do you mean by a CPD course? CPD refers to Continuing Professional Development, and the CPD-accredited course is developed for individuals who want to improve and update their skills within their professional field continuously. This certificate claims that the certificate holder's knowledge is up-to-date in their work area.
