- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
5681 Computing & IT courses delivered Online
NSE 4 Bundle
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Networking and security professionals involved in the management, configuration, administration, and monitoring of FortiGate devices used to secure their organizations' networks. Overview In interactive labs, you will explore firewall policies, user authentication, basic VPNs, explicit proxy, virus detection, web filtering, application control and more. These administrative fundamentals will provide you with a solid understanding of how to integrate and maintain basic network security. In the last three days you will review topics including features commonly used in complex or larger enterprise/MSSP networks, such as advanced routing, transparent mode, redundant infrastructure, security-as-a-service (SaaS), advanced IPsec VPN, IPS, SSO, certificates, data leak prevention, diagnostics, and fine-tuning performance. The Fortinet NSE 4 Bundle is a 5-day event that provides the basic configuration and administration of the most commonly used features of FortiGate appliances and a selection of advanced FortiGate networking and security features. The Fortinet NSE 4 Bundle is a 5-day event that provides the basic configuration and administration of the most commonly used features of FortiGate appliances and a selection of advanced FortiGate networking and security features. Additional course details: Nexus Humans NSE 4 Bundle training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the NSE 4 Bundle course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

AN30 IBM Power Systems for AIX - Virtualization I - Implementing Virtualization
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This advanced course is appropriate for System Administrators, Technical Support Personnel, and Business Partners responsible for implementing LPARs on IBM Power Systems with AIX servers. Overview Discuss the advantages or value of PowerVM edition's featuresDefine micro-partitioning and shared processor LPARsDiscuss the benefits of simultaneous multithreadingDiscuss and configure the Integrated Virtual Ethernet (IVE)Install and configure the Virtual I/O ServerConfigure virtual network devices, such as virtual Ethernet and shared Ethernet adaptersConfigure virtual SCSI and virtual Fibre Channel storage adaptersConfigure virtual SCSI target devices on a virtual SCSI adapterDefine file-backed storage pools and file-backed virtual optical devicesIdentify single points of failure in virtualized environmentsConfigure multiple VIO servers for high availabilityConfigure advanced virtual networking optionsConfigure the shared Ethernet adapter failover featureConfigure advanced virtual SCSI optionsConfigure MPIO in a VIO server's client partitionManage the service events, configure call home, add, exchange FRUs, and discuss FSP failoverPerform PowerVM (VIOS) Maintenance This course explains the new features and benefits of virtualization including processor virtualization, Virtual I/O Server, and virtual devices, such as virtual Ethernet, virtual SCSI, and virtual Fibre Channel adapters. Course Outline Unit 1: Introduction to partitioning Exercise 1: Power Systems documentation overview Unit 2: HMC V8 enhancements Exercise 2: HMC enhanced interface Unit 3: Processor virtualization Exercise 3: Processor virtualization configuration Unit 4: Virtual Ethernet Exercise 4: Virtual Ethernet adapter configuration Unit 5: Virtual I/O Server and Shared Ethernet Adapter Exercise 5: Virtual I/O Server configuration Unit 6: Virtual SCSI devices Exercise 6: Client partition configuration Unit 7: Virtual network configuration with dual VIOS Exercise 7: SEA failover setup Unit 8: Virtual SCSI configurations with dual VIOS Exercise 8: Dual VIO server configuration with MPIO in the client partition Unit 9: Virtual Fibre Channel devices Exercise 9: Virtual Fibre Channel adapter configuration Unit 10: HMC Service Management Exercise 10: Manage service events Unit 11: PowerVM advanced systems maintenance Exercise 11: PowerVM system maintenance Exercise 12: (Optional) File-backed virtual SCSI devices Additional course details: Nexus Humans AN30 IBM Power Systems for AIX - Virtualization I - Implementing Virtualization training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AN30 IBM Power Systems for AIX - Virtualization I - Implementing Virtualization course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

55244 JavaScript for Developers
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is intended for both novice and experienced programmers. Some experience in C++, C# or Java is helpful. Overview After completing this course, you will be able to: Write and test JavaScript code in modern browsers. Understand and work with the browser's Document Object Model (DOM). Work DOM objects and write code to respond to events. Add jQuery to their projects and use jQuery to manipulate the DOM and to make Ajax calls. Understand Ajax and Web Services, including HTTP Verbs and asynchronous Ajax calls. Work with XML and JSON data formats. Understand and use RESTful Web Services including ODATA queries. Work with Anonymous Functions, Self-Invoking Functions and Closures. Understand the role of the Window and Navigator objects. Describe and understand variables, 'variable hoisting', and JavaScript objects. This course is an in depth hands-on study of JavaScript. The course includes detailed hands-on labs and Q&A labs. The labs include multiple projects that update an existing web site. This course is similar to the retired Course 20480: Programming in HTML5 with JavaScript and CSS3. Module 1: Basic Scripting JavaScript Basics JavaScript or ECMAScript? Which Version of JavaScript am I Using? Shims, Shivs, and Polyfills Writing and Testing JavaScript Editors and the F12 Tools Key Parts of a Script Module 2: The Document Object Model The DOM Accessing Objects from the DOM Responding to Events Adding Elements to the DOM Module 3: Introduction to jQuery jQuery Downloading the jQuery Library jQuery Versions Linking to the Library Selecting Elements using jQuery Working with the Data Returned by jQuery Setting CSS Properties Running a Function Against the jQuery Return Set Module 4: Ajax and Web Services Web Services HTTP Verbs Data Formats ? XML and JSON Ajax RESTful Web Services OData OData Queries OData Updates Module 5: Diving in Deeper Is JavaScript Compiled? Data Types and Objects Extending Data Types Variables, Scopes and Hoisting Functions The ?this? Keyword Errors Recursion

Introduction to Reactive Spring (TT3355 )
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This in an intermediate-level Java development course geared for students experienced with Java and Spring programming essentials. This course does not cover Java or Spring development basics. Overview Working within in an engaging, hands-on learning environment, guided by our expert team, attendees will: Understand the ReactiveX specification Understand the basics of Reactive Programming Discuss the advantages and limitations of Observables Write a client application capable of handling Reactive events Apply operators to event streams to filter, modify and combine the objects emitted by event publishers Select the appropriate type of Event Source Use both Cold and Hot Observables Deal with backpressure problems in reactive programming Develop a reactive web application using Spring WebFlux Define application flows of a WebFlux application Use the WebClient API to work with both synchronous and streaming APIs Develop Unit and Integration tests to test WebFlux endpoints Creating a reactive REST endpoint Become familiar with the basics of WebSockets Create a WebSocket endpoint using Spring Create a WebSocket client Understand the basics of NoSQL Become familiar with the basics of MongoDB Understand how the data in MongoDB can be retrieved using a Reactive API Define Spring Data MongoDB repositories Query the MongoDB using Spring Data Define a reactive repository using MongoDB Explore the Spring Data R2DBC API to perform reactive CRUD operations against a relational database Spring Data reative allow us to implement database operations relying on Reative Programming APIs. While the Spring R2DBC initiative aims to bring reactive programming to relational databaes, several NoSQL databases already provide this possibility. After an introduction to NoSQL and the MongoDB, this courses covers the APIs available to communicate with this NoSQL database using both blocking and reactive APIs.Introdcution to Reactive Spring is a comprehensive Java training workshop geared for experienced developers who wish to explore concurrent, asynchronous and reactive programming APIs and techniques using Spring. After an introduction to reactive programming, Reactive Streams and the Project Reactor APIs, this course will show how this APIs are integrated into Spring. Spring 5 includes Spring WebFlux, providing a reactive programming model for web applications, including support for Reactive REST APIs. Spring WebSocket assists in the creation of web applications which provide a full-duplex, two-way communication between client and server. Introduction to Reactive Programming Reactive Manifesto Introduce ReactiveX ReactiveX implementations The Observer, Iterator pattern and functional programming Discuss hot and cold publishers Reactive Streams API Introduce the Reactive Streams specification Publisher and Subscribers java.util.concurrent.Flow Transformation of Messages (Processor) Controlling messages Tutorial: Setup Eclipse for Using Maven Introduction Introduce the Reactor Building blocks Flux and Mono Creating observables Subscribing to a stream Testing Event Sources (introduction) Testing reactive implementations StepVerifier : test sequence of emitted items Defining expectations TestPublisher: produce test data to test downstream operators Reactive Operators Introduce Operators Show the use of marble diagrams Explain some commonly used operators Callback operators Schedulers (Multithreading) Thread usage of subscriber and consumer Using the subscribeOn method Introduce the Scheduler interface Using the observeOn method Backpressure Strategies for dealing with Backpressure ?reactive pull? backpressure Exception Handling Handling errors in onError Exception handling strategies Using onErrorReturn or onErrorNext operators Using the retry operators The Global Error Handler Spring Data Review Quick review of Spring Data repositories Query return types Defining Query methods Pagination and sorting R2DBC Reactive Relational Database Connectivity DatabaseClient Performing CRUD operations Reactive Query annotated methods Spring WebFlux: Introduction Annotated Controllers Functional Endpoints WebFlux configuration Creating a reactive REST endpoint Defining flows Defining the application flow Actions Defining decision Navigating flows RouterFunction View Technologies View technologies Using Thymeleaf to create the view View Configuration Spring WebClient: Introduction to WebClient Working with asynchronous and streaming APIs Making requests Handling the response Lab: WebClient WebTestClient Testing WebFlux server endpoints Testing controllers or functions Define integration tests Introduction to Spring Reactive WebSockets Be familiar with the basics of WebSockets Understand the HTTP handshake and upgrade Name some of the advantages of WebSockets Defining the WebSocket WebSocket Message Handling WebSocketSession Implementing the WebSockethandler Creating a Browser WebSocket Client WebSocket STOMP Streaming (or Simple) text-orientated messaging protocol Introduce SockJS Connecting to the STOMP endpoint Configuring the message broker STOMP destinations Reactive WebSocket Reactive WebSocket support Implement the reactive WebSocketHandler BigData Introduce Big Data Explain the need for enhanced data storage Introduction to MongoDB JavaScript Object Notation Overview Introduce Binary JSON (BSON) Starting the database Creating Collections and Documents Executing ?simple? database commands Introduce the ObjectID Searching for documents using query operators Updating and deleting documents MongoDB Compass Spring and MongoDB MongoDB Support in Spring Data MongoClient and MongoTemplate Spring Data MongoDB configuration @EnableMongoRepositories Adding documents to the database The @Document and @Field annotations Polymorphism and the _class property The Criteria object Spring Data MongoDB MongoRepository Field naming strategy Using JSON queries to find documents The @PersistenceConstructor annotation Reactive Repositories with MongoDB Using reactive repositories ReactiveMongoTemplate RxJava or Reactor Additional course details: Nexus Humans Introduction to Reactive Spring (TT3355 ) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Introduction to Reactive Spring (TT3355 ) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Information Security Manager
By Compliance Central
Are you looking to enhance your Information Security Manager skills? If yes, then you have come to the right place. Our comprehensive course on Information Security Manager will assist you in producing the best possible outcome by mastering the Information Security Manager skills. The Information Security Manager course is for those who want to be successful. In the Information Security Manager course, you will learn the essential knowledge needed to become well versed in Information Security Manager. Our Information Security Manager course starts with the basics of Information Security Manager and gradually progresses towards advanced topics. Why would you choose the Information Security Manager course from Compliance Central: Lifetime access to Information Security Manager course materials Full tutor support is available from Monday to Friday with the Information Security Manager course Learn Information Security Manager skills at your own pace from the comfort of your home Gain a complete understanding of Information Security Manager course Accessible, informative Information Security Manager learning modules designed by experts Get 24/7 help or advice from our email and live chat teams with the Information Security Manager Curriculum Breakdown of the Information Security Manager Course Course Outline: Module 01: Introduction Module 02: Organisational Security Management Module 03: Risk Analysis and Risk Reduction Module 04: Physical and Information Security Protection Module 05: Business Resilience and Crisis Management Module 06: Cyber Security and Fraud Prevention Module 07: Security Investigations and Threat Awareness Module 08: Laws and Regulations CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? The Information Security Manager course helps aspiring professionals who want to obtain the knowledge and familiarise themselves with the skillsets to pursue a career in Information Security Manager. Requirements To enrol in this Information Security Manager course, all you need is a basic understanding of the English Language and an internet connection. Career path Information Security Analyst: £40,000 to £70,000 per year Cybersecurity Consultant: £45,000 to £80,000 per year IT Risk Manager: £50,000 to £90,000 per year Security Operations Center (SOC) Analyst: £35,000 to £60,000 per year Penetration Tester (Ethical Hacker): £40,000 to £75,000 per year Chief Information Security Officer (CISO): £70,000 to £150,000 per year Certificates CPD Accredited PDF Certificate Digital certificate - Included CPD Accredited PDF Certificate CPD Accredited Hard Copy Certificate Hard copy certificate - £10.79 CPD Accredited Hard Copy Certificate Delivery Charge: Inside the UK: Free Outside of the UK: £9.99 each

SFBT - Solution-Focused Brief Therapy Training
By Course Cloud
Solution-Focused Brief Therapy (SFBT) is an evidence-based approach that focuses on the present and future rather than the past. It helps clients identify and achieve their desired goals in a short time by using their own resources and strengths. SFBT is based on the assumption that clients are experts on their own lives and have the ability to change. This course is your gateway to mastering the art of SFBT-an approach that focuses on strengths, solutions, and client empowerment. It's about creating an environment where individuals can discover their own paths to positive change. Enroll now and be the change your clients are searching for.

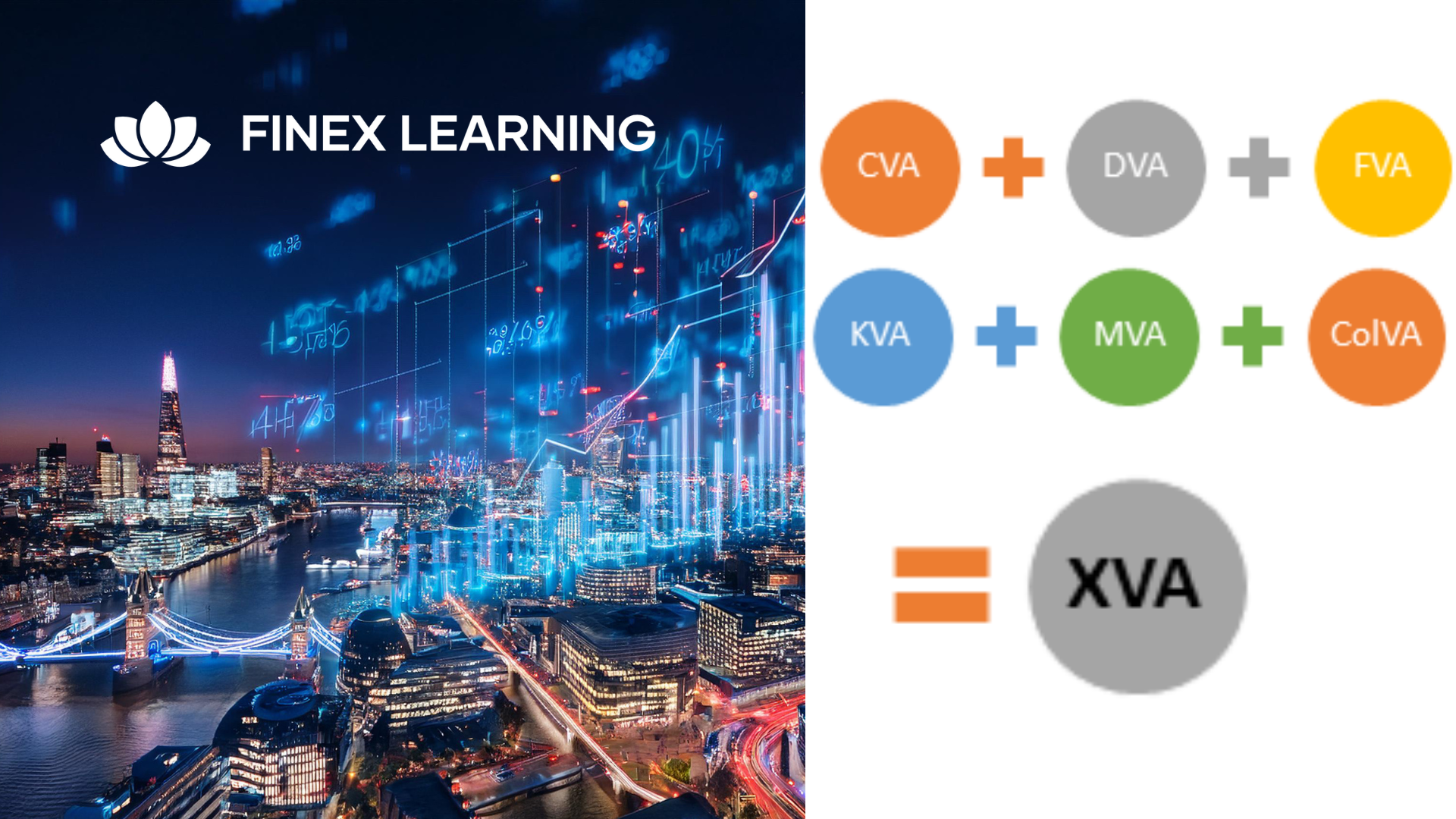
Overview This 1 day course focus on comprehensive review of the current state of the art in quantifying and pricing counterparty credit risk. Learn how to calculate each xVA through real-world, practical examples Understand essential metrics such as Expected Exposure (EE), Potential Future Exposure (PFE), and Expected Positive Exposure (EPE) Explore the ISDA Master Agreement, Credit Support Annexes (CSAs), and collateral management. Gain insights into hedging strategies for CVA. Gain a comprehensive understanding of other valuation adjustments such as Funding Valuation Adjustment (FVA), Capital Valuation Adjustment (KVA), and Margin Valuation Adjustment (MVA). Who the course is for Derivatives traders, structurers and salespeople xVA desks Treasury Regulatory capital and reporting Risk managers (market and credit) IT, product control and legal Quantitative researchers Portfolio managers Operations / Collateral management Consultants, software providers and other third parties Course Content To learn more about the day by day course content please click here To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now
Overview This comprehensive course on Information Management will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This Information Management comes with accredited certification which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is this course for? There is no experience or previous qualifications required for enrolment on this Information Management. It is available to all students, of all academic backgrounds. Requirements Our Information Management is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible on tablets and smartphones so you can access your course on wifi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career path Having these various qualifications will increase the value in your CV and open you up to multiple sectors such as Business & Management, Admin, Accountancy & Finance, Secretarial & PA, Teaching & Mentoring etc. Course Curriculum 7 sections • 7 lectures • 02:17:00 total length •Introduction to Information Management: 00:32:00 •Information Management Strategy: 00:17:00 •Databases and Information Management: 00:29:00 •Management Information Systems (MIS): 00:16:00 •Auditing Information Systems: 00:16:00 •Ethical and Social Issues and Data Protection: 00:27:00 •Assignment - Information Management: 00:00:00


