- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
55232 Writing Analytical Queries for Business Intelligence
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for information workers and data science professionals who seek to use database reporting and analysis tools such as Microsoft SQL Server Reporting Services, Excel, Power BI, R, SAS and other business intelligence tools, and wish to use TSQL queries to efficiently retrieve data sets from Microsoft SQL Server relational databases for use with these tools. Overview After completing this course, students will be able to: - Identify independent and dependent variables and measurement levels in their own analytical work scenarios. - Identify variables of interest in relational database tables. - Choose a data aggregation level and data set design appropriate for the intended analysis and tool. - Use TSQL SELECT queries to produce ready-to-use data sets for analysis in tools such as PowerBI, SQL Server Reporting Services, Excel, R, SAS, SPSS, and others. - Create stored procedures, views, and functions to modularize data retrieval code. This course is about writing TSQL queries for the purpose of database reporting, analysis, and business intelligence. 1 - INTRODUCTION TO TSQL FOR BUSINESS INTELLIGENCE Two Approaches to SQL Programming TSQL Data Retrieval in an Analytics / Business Intelligence Environment The Database Engine SQL Server Management Studio and the CarDeal Sample Database Identifying Variables in Tables SQL is a Declarative Language Introduction to the SELECT Query Lab 1: Introduction to TSQL for Business Intelligence 2 - TURNING TABLE COLUMNS INTO VARIABLES FOR ANALYSIS: SELECT LIST EXPRESSIONS, WHERE, AND ORDER BY Turning Columns into Variables for Analysis Column Expressions, Data Types, and Built-in Functions Column aliases Data type conversions Built-in Scalar Functions Table Aliases The WHERE clause ORDER BY Lab 1: Write queries 3 - COMBINING COLUMNS FROM MULTIPLE TABLES INTO A SINGLE DATASET: THE JOIN OPERATORS Primary Keys, Foreign Keys, and Joins Understanding Joins, Part 1: CROSS JOIN and the Full Cartesian Product Understanding Joins, Part 2: The INNER JOIN Understanding Joins, Part 3: The OUTER JOINS Understanding Joins, Part 4: Joining more than two tables Understanding Joins, Part 5: Combining INNER and OUTER JOINs Combining JOIN Operations with WHERE and ORDER BY Lab 1: Write SELECT queries 4 - CREATING AN APPROPRIATE AGGREGATION LEVEL USING GROUP BY Identifying required aggregation level and granularity Aggregate Functions GROUP BY HAVING Order of operations in SELECT queries Lab 1: Write queries 5 - SUBQUERIES, DERIVED TABLES AND COMMON TABLE EXPRESSIONS Non-correlated and correlated subqueries Derived tables Common table expressions Lab 1: Write queries 6 - ENCAPSULATING DATA RETRIEVAL LOGIC Views Table-valued functions Stored procedures Creating objects for read-access users Creating database accounts for analytical client tools Lab 1: Encapsulating Data Retrieval Logic 7 - GETTING YOUR DATASET TO THE CLIENT Connecting to SQL Server and Submitting Queries from Client Tools Connecting and running SELECT queries from: Excel PowerBI RStudio Exporting datasets to files using Results pane from SSMS The bcp utility The Import/Export Wizard Lab 1: Getting Your Dataset to the Client Additional course details: Nexus Humans 55232 Writing Analytical Queries for Business Intelligence training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55232 Writing Analytical Queries for Business Intelligence course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

PMI-RMP Exam Prep: In-House Training
By IIL Europe Ltd
PMI-RMP® Exam Prep: In-House Training This course is aimed at preparing the participant to pass the PMI-RMP® (Risk Management Professional) exam. The course will also provide practical tips and tools that can be used in any organization's project management risk practices. In this expanded session, you will also have time to practice your exam taking skills with coaching from a credentialed instructor. The course includes the tool RMP-IQ, with sample exam questions to practice for the exam and allow participants to see their knowledge level in the various domains. What You Will Learn At the end of this course, participants will be able to: Explain the value and benefits of the PMI-RMP® credential Perform a self-assessment of your knowledge and skills Prepare a study plan that will allow you to pass the exam Foundation Concepts The Risk Management Professional (PMI-RMP®) Exam PMI's Standard for Risk Management Portfolios, Programs and Projects Key risk definitions Risk management life cycle Levels of Risk Management Enterprise Risk Management Portfolio Risk Management Program Risk Management Project Risk Management Risk Strategy and Planning: Part 1 Task 1: Perform a preliminary document analysis Task 2: Assess project environment for threats and opportunities Task 3: Confirm risk thresholds based on risk appetites Risk Strategy and Planning: Part 2 Task 4: Establish risk management strategy Task 5: Document the risk management plan Task 6: Plan and lead risk management activities with stakeholders Agile, programs, and portfolio aspects of risk strategy and planning Risk Identification: Part 1 Objectivity and bias Task 1: Conduct risk identification exercises Risk Identification: Part 2 Task 2: Examine assumption and constraint analysis Task 3: Document risk triggers and thresholds based on context / environment Task 4: Develop risk register Agile, programs, and portfolio aspects of risk identification Risk Analysis: Part 1 Task 1: Perform qualitative analysis Risk analysis in an agile environment Risk Analysis: Part 2 Task 2: Perform quantitative analysis Task 3: Identify threats and opportunities Program and portfolio aspects of risk analysis Risk Response Task 1: Plan risk responses Agile, programs, and portfolio aspects of risk response planning Task 2: Implement risk responses Monitor and Close Risks: Part 1 Task 1: Gather and analyze performance data Monitor and Close Risks: Part 2 Task 2: Monitor residual and secondary risks Task 4: Monitor project risk levels Task 3: Provide information required to update relevant project documents Agile, programs, and portfolio aspects of monitoring and closing risks

An information security manager takes responsibility for overseeing and controlling all aspects of computer security in a business. The job entails planning and carrying out security measures that will protect a business’s data and information from deliberate attack, unauthorized access, corruption and theft.” Randstad.co.uk Learning outcomes: How to ensure essential guidelines are in place for adhering to industry rules and regulations. How to conduct internal audits and reviews to ensure compliance (SOX, etc). How to carry-out gap analysis using ISO27001, ISO27002, ISO27005, NIST CSF etc. How to review companies’ policies, procedures, and guidelines. How to carry-out risk assessment and ensuring the right treatment is selected. How to identify vulnerabilities and patch the weaknesses How to compliance to regulatory requirements (UK Data Privacy, GDPR, HIPAA, etc). How to ensure employees are thoroughly updated about the organization’s policies, regulations, and processes. How to ensure employees are guided and made aware of information security risks the legal implication. Who is the course for? Managers Accountant Engineers Business Analysts Healthcare Professionals. Teachers and Academics. Students and professions with transferable skills. E-mail: info@prefortconsult.com Website: www.prefortconsult.com Mobile: +447455884242 Attending this will enable you to access some paid courses and training for free. HURRY NOW and book your place before the opportunity closes. Note: All sessions/classes will take place online via Zoom. You are also required to attend group discussions to improve your skills like presentation, communication, analysis, etc.

APM Project Fundamentals Qualification (PFQ): In-House Training
By IIL Europe Ltd
APM Project Fundamentals Qualification (PFQ): In-House Training This practical course gives Participants a solid introduction to the fundamentals of project management and to prepare them for the one-hour, multiple-choice exam held at the end of the course. The APM Project Fundamentals Qualification (PFQ) is an entry-level qualification suitable for those who are new to project management and working in a project team, and who wish to understand the standard terminology. The goal of this course is to prepare you to successfully pass the exam. What you will Learn You'll learn how to: Identify project management terminology and context Identify project management processes Identify the roles involved in project management Describe project success criteria and benefits Prepare project documentation Acquire the level of understanding needed to pass the APM PFQ examination Getting Started Introductions Course structure Course goals and objective Project Context Project characteristics Project management processes Business and project context Organizational roles Project Lifecycle Programme and portfolio management Project Concept Phase Stakeholder management Project success and benefits management Business case Benefits People in Projects Leadership and teamwork Communication Project Definition Phase Project management plan Quality management Risk management Scope management Scheduling Resource management Estimating Procurement Project Implementation Phase Change control and configuration management Issue management Information management Project Hand-over and Close-out Phase Hand-over and close-out Post-project review Revision and Exam Revision and practice questions APM PFQ examination

Portfolio, Programs, & Project Offices Practitioner: In-House
By IIL Europe Ltd
Portfolio, Programme, and Project Offices (P3O®) Practitioner: In-House Training P3O® is the AXELOS standard for the design of decision-making processes regarding changes in organizations. P3O provides a guideline for the design of portfolio, programme, and project offices in organizations. The P3O Practitioner Course is an interactive learning experience. The P3O Practitioner-level content provides you with sufficient knowledge and understanding of the P3O guidance to design, implement, manage or work within any component office of a P3O model. It enables participants to successfully complete the associated P30 Practitioner exam and achieve the qualification. In this course, you will be prepared to successfully attempt the P3O Practitioner exam and learn how to implement or re-energize a P3O model in their own organization. What you will Learn At the end of the P3O Practitioner course, you will be able to: Define a business case to get senior management approval for P3O Build a right P3O model to adapt to the organization's needs, taking account of the organization's size and portfolio, programme and project management maturity Identify the elements, roles, and functions deployed in a generalized P3O model Use tools and techniques in running the P3O and advising those who shape the portfolio of programmes and projects Introduction to P3O What is the purpose of P3O? Definitions What are P3Os? Portfolio, programme, and project lifecycles Governance and the P3O Designing a P3O Model Factors that affect the design Design considerations What functions and services should the P3O offer? Roles and responsibilities Sizing and tailoring of the P3O model Why have a P3O? How a P3O adds value Maximizing that value Getting investment for the P3O Overcoming common barriers Timescales Why have a P3O (Extension)? The P3O Business Case The P3O Model Blueprint Vision Statement Demonstrating the Value KPIs The Benefits of Claimed Capabilities Benefit Realisation and Strategic Objectives Benefit Profile How to Implement or Re-Energize a P3O Implementation lifecycle for a permanent P3O Identify Define Deliver Close Implementation lifecycle for a temporary programme or project office Organizational context Definition and implementation Running Closing Recycling How to operate a P3O Overview of tools and techniques Benefits of using standard tools and techniques Critical success factors P3O tools P3O techniques

PRINCE2 Practitioner: In-House Training
By IIL Europe Ltd
PRINCE2® Practitioner : In-House Training Projects fail for a variety of reasons including poor planning, lack of defined quality criteria, poor understanding of the business drivers, inadequate control, and lack of senior management involvement in other words, lack of a structured best practice approach to project delivery. PRINCE2® (6th Edition is the current version) is a structured, process-based approach for project management providing a methodology which can be easily tailored and scaled to suit all types of projects. It is the de facto standard for project management in the UK Government and is also used extensively in more than 150 countries worldwide with in excess of 20,000 organizations already benefitting from its powerful approach. It can be used easily in combination with PMI®'s PMBOK® Guide to provide a robust project methodology, or to augment an existing PMBOK®-based methodology with additional rigor around areas such as Quality, Organization, and Benefits Realization. The goals of this course are to take participants to the next level of understanding and application of the PRINCE2® methodology and to prepare them to sit the Practitioner exam. Using APMG provided sample exam papers and additional project case studies, participants will learn how to apply what they learned during the Foundation course and how to approach the OTE Practitioner exam, which is aimed at testing their ability to apply PRINCE2® in an actual project environment simulated via a case study provided as part of the exam. What you will Learn You'll learn how to: Tailor and apply the principles, themes, process structure, techniques, and management products of PRINCE2® within a work environment, via carefully selected case studies Define the PRINCE2® 6th Edition method at the Practitioner level Prepare for and take the Practitioner exam Getting Started Introductions Course structure Course goals and objectives Tailoring PRINCE2® Tailoring PRINCE2® Adopting PRINCE2® Tailoring PRINCE2® to suit different projects Adopting PRINCE2® in an organizational environment Controlled Start Recap management products Study business case and risk Study activities and responsibilities in: Starting up a project Initiating a project Controlled Progress Study management products and risk Study activities and responsibilities in: Getting work done Monitoring and reporting Issues and escalation Controlled Close Study Activities and Responsibilities in Closing a Project Activities and roles Roles and Responsibilities Principles Exercise Product-basedPlanning Producing a product breakdown structure (PBS) Producing a product flow diagram (PFD) Linking product breakdown structures and product flow diagrams to product descriptions

Portfolio, Programs, and Project Offices Foundation: In-House
By IIL Europe Ltd
Portfolio, Programme, and Project Offices (P3O®) Foundation: In-House Training P3O® is the AXELOS standard for the design of decision-making processes regarding changes in organizations. P3O provides a guideline for the design of portfolio, programme, and project offices in organizations. The P3O Foundation course is an interactive learning experience. The P3O Foundation-level content provides you with sufficient knowledge and understanding of the P3O guidance to interact effectively with, or act as an informed member of, an office within a P3O model. It enables you to successfully complete the associated P30 Foundation exam and achieve the qualification. In this course, you will be prepared to successfully attempt the P3O Foundation exam and learn how to implement or re-energize a P3O model in their own organization. What you will Learn Individuals certified at the P3O Foundation level will be able to: Define a high-level P3O model and its component offices List the component offices in a P3O model Differentiate between Portfolio, Programme, and Project Management List the key functions and services of a P3O List the reasons for establishing a P3O model Compare different types of P3O models List the factors that influence selection of the most appropriate P3O model for an organization Define the processes to implement or re-energize a P3O Benefits: Fast-track programme for those who want to achieve P3O Foundation qualification Practical case study and scenarios Attractive slides and course book Introduction to P3O What is the purpose of P3O? Definitions What are P3Os? Portfolio, programme, and project lifecycles Governance and the P3O Designing a P3O Model Factors that affect the design Design considerations What functions and services should the P3O offer? Roles and responsibilities Sizing and tailoring of the P3O model Introduction to P3O What is the purpose of P3O? Definitions What are P3Os? Portfolio, programme, and project lifecycles Governance and the P3O Designing a P3O Model Factors that affect the design Design considerations What functions and services should the P3O offer? Roles and responsibilities Sizing and tailoring of the P3O model Why Have a P3O? How a P3O adds value Maximizing that value Getting investment for the P3O Overcoming common barriers Timescales How to Implement or Re-Energize a P3O Implementation lifecycle for a permanent P3O Identify Define Deliver Close Implementation lifecycle for a temporary programme or project office Organizational context Definition and implementation Running Closing Recycling How to Operate a P3O Overview of tools and techniques Benefits of using standard tools and techniques Critical success factors P3O tools P3O techniques

PRINCE2 Foundation: In-House Training
By IIL Europe Ltd
PRINCE2® Foundation: In-House Training Projects fail for a variety of reasons including poor planning, lack of defined quality criteria, poor understanding of the business drivers, inadequate control, and lack of senior management involvement in other words, lack of a structured best practice approach to project delivery. PRINCE2® (6th Edition is the current version) is a structured, process-based approach to project management providing a methodology which can be easily tailored and scaled to suit all types of projects. It is the de facto standard for project management in the UK Government and is used extensively in more than 150 countries worldwide with in excess of 20,000 organizations already benefiting from its powerful approach. It can be used easily in combination with PMI®'s PMBOK® Guideto provide a robust project management methodology, or to augment an existing PMBOK®-based methodology with additional rigor around areas such as Quality, Organization, and Benefits Realization. The goals of this course are to provide participants with a thorough grounding in PRINCE2® and its benefits and to prepare them to sit the Foundation exam. What you will Learn You'll learn how to: Identify the benefits and principles underlying a structured approach to project management Define the PRINCE2® method in depth, including the principles, themes, and processes Prepare and practice for the Foundation exam Getting Started Introductions Course structure Course goals and objectives Overview of the PRINCE2® Foundation exam PRINCE2® Introduction Introducing PRINCE2® The structure of PRINCE2® What PRINCE2® does not provide What makes a project a 'PRINCE2® project'? Project Management with PRINCE2® Defining a project Managing a project Controlling the variables The Project Manager's work PRINCE2 Principles PRINCE2® Principles The Seven Principles Tailoring and Adopting PRINCE2® Defining tailoring Defining embedding What can be tailored? Who is responsible for tailoring? Introduction to the PRINCE2® Themes What is a PRINCE2® Theme? What are the PRINCE2® Themes? Tailoring the themes Format of the theme chapters Business Case Need for a business case Elements of a business case How a business case is developed Managing Benefits Organization Need for a special type of organization PRINCE2® organization structure Roles in a PRINCE2® project Combining roles Quality Relevance of quality to project work Quality, quality control, and quality assurance Quality management approach and the quality register Who is responsible for quality? Plans Need for plans and their hierarchy Approach to planning Content of a PRINCE2® plan Product-based planning Risk The need to manage risks What is a risk? Risk and continued business justification A risk management option Change Change is inevitable Different types of change Baselines and configuration management Issue and change control in PRINCE2® Progress Controlling a PRINCE2® project The application of tolerance Types of control Raising exceptions Introduction to Processes Processes and the project lifecycle The PRINCE2® journey Structure of the process chapters Tailoring the processes Starting up a Project Appointing people to the PRINCE2® roles Establishing some baselines Should we go further with this work? Planning for initiation Directing a Project Should we start / continue the project? Responding to internal / external influences Should we close this project? Initiating a Project Establishing the project's approaches Creating the project plan Refining the business case Assembling the PID Controlling a Stage Authorizing and reviewing work Monitoring and reporting Handling non-planned situations Triggering the next process Managing Product Delivery Accepting work from the Project Manager Getting the work done by the team Routine and non-routine reporting Handing back the completed work Managing a Stage Boundary Taking stock of what we have done Updating the PID Consider the options for continuing / stopping Producing exception plans Closing a Project PRINCE2® at the end of a project Transition of product to operational use How well did we do? Tying up all the loose ends

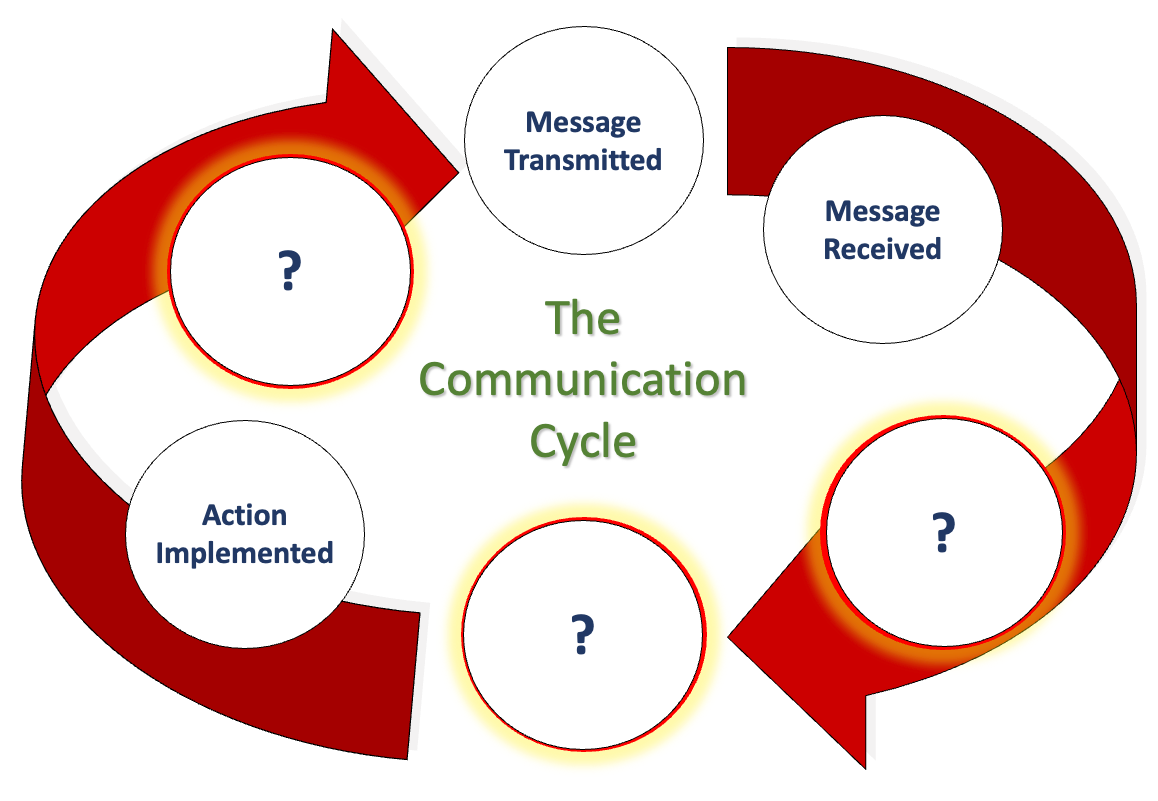
We communicate daily in many ways, including email, phone, text, Zoom, Teams, Google Meets, Slack, and even that old-fashioned thing, what was it now... oh yes, talking face-to-face. But, when we look at communication closely and really drill down into what we are doing in conjunction with how our brain works (neuroscience), how internal, organisational, and social politics control what we believe we can say, how hierarchical positioning impacts our honesty and how the lack of psychological safety means we say what we know others want to hear rather than what they need to hear…. It is oh so complicated! This workshop not only explores the concept of excellent communication, but we also want to hear what you believe it is too. We also delve into how organisational culture influences our perception of speaking up. Factors that hinder open and honest communication, and we work collaboratively towards removing these barriers to achieve a communication style that fosters trust and transparency, creating psychological safety. This workshop is particularly relevant to our Emotional Intelligence workshop (EI and Me). We firmly believe that developing emotional intelligence is the key to unlocking Clean Communication, a skill that is crucial for all of us, regardless of our roles and responsibilities, so that we thrive in our professional environment. If you want to see if we are correct, why not have us facilitate a workshop for you and see what you get by the end of it? LENGTH - Normally, one day. But please contact us to discuss your specific needs, or we can offer advice. NEXT WORKSHOP START - Please ask for more information as we deliver bespoke closed events for your people at your location or a mutually suitable location. WORKSHOP DELIVERY - The best environment for this workshop is face-to-face, but we can facilitate this workshop online. Suitability - Who should attend? Who Should Attend and Why? Who? - Perhaps think of this another way… who shouldn’t attend to ensure we can attain Clean Communication? There’s your answer. Why? - Every person needs to understand what we are saying above about how we get trapped in this organisational formatting which changes how we communicate and how it prevents us from communicating cleanly. EVERY organisation has this, despite what our values profess. And 'Values', that’s a whole other story. Workshop Content Using the 'Moccasin Approach'® to clean our personal and organisational communication LaPD’s Communication Cycle and what we must consider. (Can you work out what the ? represent above? Accountability and Responsibility raises its head in Communication. It has to. Bias, unconscious bias and its impacts on our communication. The conundrum of communicating with others and their styles (The TRAP). How would my perfect Manager/Leader communicate with me? Nonverbal communication (body language), rapport, Clean Communication. Negative communication can go viral (Self-Fulfilling Prophecy). Reflections, findings and goals (individual and team). Meeting our workshop objectives by listing five areas for development. Workshop delivery and venue This workshop is usually one day in duration, and it focuses solely on how we communicate with each other. It can also be a two-day event incorporating aspects of Emotional Intelligence (EI) with group, and individual activities to allow discussions about the various communication we need in your organisation. When you consider the content we deliver, we are sure you will understand why we always prefer to deliver our workshops, courses and programmes face-to-face. Face-to-face workshops and courses can be held at a location of your choice or, if you wish, a central UK location, such as the Macdonald Burlington Hotel in Birmingham, located directly across from the Birmingham New Street train station. We can deliver our workshops, courses and programmes online, although this will mean splitting elements into manageable learning events to suit the online environment.
Helping people become more efficient in how they manage and prioritise their working day, and for leaders and managers, how they can work efficiently by collaborating effectively with their people.
