- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
459 Cisco courses
RADIUS training course description A fast paced hands-on introduction to RADIUS. Moves from installation and configuration through to packet analysis and accounting. Practical exercises are spread throughout the course to maintain student interest. What will you learn Configure PPP and PAP/CHAP. Install and configure RADIUS servers. Describe how RADIUS works. Setup RADIUS accounting. Analyse RADIUS packets. Troubleshoot RADIUS installations. RADIUS training course details Who will benefit: Network Administrators. Support personnel. Anyone who will be working with RADIUS. Prerequisites: Knowledge of the TCP/IP protocols would be advantageous. Duration 2 days RADIUS training course contents What is RADIUS? AAA services, Authentication, Authorisation, Accounting, local AAA services, remote AAA services, What is RADIUS? RADIUS as a protocol, RADIUS as an architecture, RADIUS as a standard. Installing RADIUS RADIUS platforms, RADIUS servers, client server communications, services, daemons. Hands on Installing RADIUS and testing with NTRadPing. Server configuration Configuring clients on the server, shared secrets, usernames and passwords. IP address pools. Hands on Configuring a server and testing with NTRadPing. Client configuration Example clients, client configuration steps, enabling RADIUS, pointing clients to the server, shared secrets, example Cisco authentication, example Cisco authorization. Hands on Configuring clients for RADIUS. How RADIUS works RADIUS architecture, RADIUS and authentication, PPP, PAP, CHAP, RADIUS SUCCESS, RADIUS FAILURE, the RADIUS protocol stack, the RADIUS protocol, the RADIUS header, RADIUS codes, RADIUS attributes, ACCESS-REQUEST example, ACCESS-ACCECPT example, CHAP example, proprietary attributes, using unassigned type codes, RADIUS attribute 26, Cisco specific attributes. Hands on Analysing RADIUS packets, configuring PPP CHAP to work with RADIUS. RADIUS accounting Simplified operation, Accounting codes, Accounting attributes, client and server configuration for accounting. Hands on Configuring RADIUS accounting. RADIUS architectures Traditional architecture, multiple RADIUS servers for resilience, Proxy RADIUS servers, Realms, RADIUS in VPNs, RADIUS with 802.1x. Hands on Using multiple RADIUS servers, Proxies. Troubleshooting RADIUS General problem solving, basic tools, RADIUS troubleshooting, Common configuration errors, log files, RADIUS design and performance. Hands on Fixing RADIUS problems.

SN71 IBM Storage Area Networking Fundamentals
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for personnel who are assessing and planning to deploy a storage area network. Overview Summarize the storage infrastructure challenges and the various storage architectures such as DAS, SAN and NASClassify SAN terminology including trunking, zoning, multipathing and fabric mergingRecognize b-type Data Center Management tools such as Data Center Fabric Manager and Network Advisor (NA)Classify the various tabs in the Network Advisor ToolRecall the Cisco MDS management toolsRecognize the importance of Converged Enhanced EthernetCompare the features of iSCSI and FCoE This course provides an overview of storage network and data center networking technology. Day 1 Welcome Unit 1 - Evolution of storage area networks Unit 2 - Fibre Channel Day 2 Unit 3 - Fibre Channel switches and directors: Brocade (b-type) Unit 4 - Brocade DCFM and Network Advisor Day 3 Exercise 0 - Lab setup and preliminary instructions Exercise 1 - Brocade switch 2109: Initial configuration Exercise 2 - Management software installation Exercise 3 - Brocade Fabric Manager Exercise 4 - Brocade switch: Zoning configuration Exercise 5 - V3700 storage provisioning using iSCSI Exercise 6 - Brocade VDX fabric merging Unit 5 - Fibre Channel switches and directors: Cisco MDS Day 4 Unit 6 - Converged Enhanced Ethernet Unit 7 - Fibre Channel over Ethernet Unit 8 - iSCSI Exercise 7 - Basic configuration Exercise 8 - Management tools installation Exercise 9 - VSAN creation Exercise 10 - Zoning configuration on Cisco Exercise 11 - Configuring the DS3500 storage subsystem Additional course details: Nexus Humans SN71 IBM Storage Area Networking Fundamentals training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SN71 IBM Storage Area Networking Fundamentals course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

IT Security: Cyber Security & CompTIA Network+ (AWS, Cisco ASA Firewall) - CPD Certified
4.8(9)By Skill Up
5 STAR Rated | CPD Certified Diploma | 22-in-1 Premium Bundle | 22 Free PDF+ Transcript Certificate | Lifetime Access

Definitive Nagios training course description Nagios is an open source application designed to provide system and network monitoring. This hands on course gives a comprehensive coverage of using Nagios to provide monitoring of Linux, Windows and network devices. The course is based on Nagios core but contact us if you would like Nagios XI. What will you learn Install Nagios. Configure Nagios. Monitor Windows, Linux and Cisco (and other network equipment) using Nagios. Configure notifications Definitive Nagios training course details Who will benefit: Technical staff working with Nagios. Prerequisites: None. Duration 2 days Definitive Nagios for engineers Nagios architecture Downloading Nagios, Installing Nagios, Nagios core, plugins, frontends, addons. Nagios XI. Nagios Fusion. Hands on Installing Nagios. Getting started with Nagios Nagios files, nagios.cfg, minimal.cfg. Starting and stopping Nagios. Hands on Controlling Nagios. Using Nagios Nagios web interface. Maps, Hosts, host groups, services, service groups, problems. Reports. Configuration. Hands on Using the web interface. Monitoring Linux systems SSH, NRPE. Hands on Monitoring Linux system health. Monitoring Windows systems Installing NSClient++, Configuring NSClient++, check_nt plugin, monitoring uptime, CPU, memory, disks, services, processes. Hands on Monitoring Windows system health. Monitoring network devices SNMP architecture, MIBs. Polling. Hands on Configuring Nagios for SNMP. Agents Configuring Cisco devices for SNMP support, communities, traps, syslog. Hands on Monitoring network devices. Nagios alerts and notifications SNMP traps. Email notifications, SMS alerts other messaging

**Don't Spend More; Spend Smarter** Boost Your Career with Apex Learning and Get Noticed By Recruiters in this Hiring Season! Get Hard Copy + PDF Certificates + Transcript + Student ID Card worth £160 as a Gift - Enrol Now Give a compliment to your career and take it to the next level. This Internet of Things (IoT) will provide you with the essential knowledge to shine in your professional career. Whether you want to develop skills for your next job or elevate skills for your next promotion, this Internet of Things (IoT) will help you keep ahead of the pack. The Internet of Things (IoT) incorporates basic to advanced level skills to shed some light on your way and boost your career. Hence, you can strengthen your expertise and essential knowledge, which will assist you in reaching your goal. Further, this Internet of Things (IoT) will add extra value to your resume to stand out to potential employers. Throughout the programme, it stresses how to improve your competency as a person in your chosen field while also outlining essential career insights in this job sector. Consequently, you'll sharpen your knowledge and skills; on the other hand, see a clearer picture of your career growth in future. By the end of the Internet of Things (IoT), you can equip yourself with the essentials to keep you afloat in the competition. Along with this Internet of Things (IoT) course, you will get 10 premium courses, an original Hardcopy, 11 PDF Certificates (Main Course + Additional Courses) Student ID card as gifts. This Internet of Things (IoT) Bundle Consists of the following Premium courses: Course 01: Internet of Things Course 02: Internet of Things Hacking Course 03: Automation Course 04: Learning Computers and Internet Level 2 Course 05: AWS Essentials Course 06: Encryption Course 07: Cloud Computing / CompTIA Cloud+ (CV0-002) Course 08: CompTIA Networking - Level 4 Course 09: Network Security Level 2 Course 10: Cyber Security Incident Handling and Incident Response Course 11: Data Center Training Essentials: General Introduction So, enrol now to advance your career! Benefits you'll get choosing Apex Learning for this Internet of Things (IoT): Pay once and get lifetime access to 11 CPD courses Free e-Learning App for engaging reading materials & helpful assistance Certificates, student ID for the title course included in a one-time fee Free up your time - don't waste time and money travelling for classes Accessible, informative modules designed by expert instructors Learn at your ease - anytime, from anywhere Study the course from your computer, tablet or mobile device CPD accredited course - improve the chance of gaining professional skills How will I get my Certificate? After successfully completing the course you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (Previously it was £6*11 = £66) Hard Copy Certificate: Free (For The Title Course: Previously it was £10) Curriculum of Internet of Things (IoT) Bundle Course 01: Internet of Things Course Agenda Unit 01: Introduction Unit 02: Raspberry Pi Installation Unit 03: Getting Around Raspberry Pi Unit 04: Raspberry Pi GPIO Output Unit 05: Output from Raspberry Pi Unit 06: Inputs to Raspberry Pi Unit 07: Sensor Interfacing Unit 08: Interfacing of I2C Based BMP180 Sensor with Raspberry Pi Unit 09: Internet of Things with Microsoft Azure Unit 10: IoT with Thingspeak Unit 11: Learn a new platform, Adafruit IO Unit 12: IOT Security Course 02: Internet of Things Hacking Module 01: IoT Part 1 Module 02: IoT Part 2 Module 03: IoT Hacking Tools and Technique Module 04: IoT Hacking Tools and Technique Part 2 Module 05: IoT Scenario Part 1 Module 06: IoT Scenario Part 2 Module 07: Smart Devices Module 08: AWS Basics Course 03: Automation Module 01: Introduction Module 02: Overview of Automation Concepts and Tools Module 03: Common Automation Workflows and Campaigns Module 04: Build Your First Workflow from Scratch Course 04: Cloud Computing / CompTIA Cloud+ (CV0-002) Section 01: What You Need to Know Section 02: Introducing the Cloud Section 03: System Requirements for Cloud Deployments Section 04: Cloud Storage Section 05: Cloud Compute Section 06: Cloud Networking Section 07: Cloud Security Section 08: Migrating to the Cloud Section 09: Maintaining Cloud Solutions Section 10: Troubleshooting Cloud Solutions Course 05: AWS Essentials Section 01: AWS Foundations and Services Section 02: AWS Security and Costs Course 06: Encryption Section 01: Introduction Section 02: Basics of Common Encryption Section 03: Technical Aspects of Encryption Section 04: AES Basic Tech Demo Section 05: File and System Encryption Section 06: Conclusion Course 07: Basics Blockchain Section 01: Introduction Section 02: Underlying technologies of Blockchain Section 03: Advantages of Blockchain Section 04: How Blockchain works Section 05: Types of blockchain and bitcoin Section 06: Libra [Facebook's cryptocurrency] Section 07: Ethereum [The revolution in Blockchain technology] Section 08: Forming Blockchain Solutions Course 08: Cisco ASA Firewall Training Lecture 01: Common Network Security Terms Lecture 02: Confidentiality, Integrity, Availability. Lecture 03: Security Concepts & Terms Lecture 04: Intro to Firewall Technologies Lecture 05: About Cisco ASA Firewall Lecture 06: Install Cisco ASAv Firewall in GNS3 Lecture 07: Install ASA 9 Cluster, Security Context enable in GNS3. Lecture 08: Install Cisco ASAv Firewall on EVE-NG Lecture 09: Install Cisco ASAv Firewall on VMWare Workstation. Lecture 10: Cisco ASA Firewall Basic Configuration Commands. Lecture 11: Device Management Cisco ASA Console Lecture 12: Device Management Cisco ASA Telnet Lecture 13: Device Management Cisco ASA SSH Lecture 14: Device Management Cisco ASA ASDM Lecture 15: Device Management Cisco ASA TFTP Lecture 16: Device Management Cisco ASA FTP Lecture 17: Security Levels and Zoning in Cisco ASA Lecture 18: Introduction to Routing & Static Routing Lecture 19: Network Route Configuration in Cisco ASA Lecture 20: Host Route Configuration in Cisco ASA Lecture 21: Default Route Configuration in Cisco ASA Lecture 22: Floating Static Route Configuration in ASA Lecture 23: IP SLA (Service Level Agreement) in ASA Lecture 24: Dynamic Routing Protocol RIP version 2 Lecture 25: Dynamic Routing Protocol EIGRP Configuration Lecture 26: Dynamic Routing Protocol OSPF Configuration Lecture 27: Routing Protocols Redistribution Lecture 28: Implement Access Control Lists in ASA Lecture 29: Configure & Verify Extended ACLs in ASA Lecture 30: Configure & Verify Infrastructure ACLs Lecture 31: Configure & Verify Time-Based ACLs Lecture 32: Configure & Verify Standard ACLs Lecture 33: Configure & Verify Object Groups ACLs Lecture 34: Configure & Verify DHCP Server in ASA Lecture 35: Configure & Verify DHCP Relay in ASA Lecture 36: Introduction & Theory of NAT and PAT ASA Lecture 37: Creating Lab Topology for NAT & PAT Lecture 38: Static NAT in Cisco ASA Lecture 39: Static PAT in Cisco ASA Lecture 40: Dynamic NAT in Cisco ASA Lecture 41: Dynamic PAT in Cisco ASA Lecture 42: Identity NAT in Cisco ASA Lecture 43: Policy NAT in Cisco ASA Lecture 44: Modular Policy Framework (MPF) Lecture 45: Transparent Firewall Lecture 46: ASDM Walkthrough Lecture 47: Security Contexts (Multi-Contexts) Lecture 48: Redundancy, HA, Active/Standby Failover Lecture 49: Packet Capture in Cisco ASA Firewall Lecture 50: Packet Tracer in Cisco ASA Firewall Lecture 51: Syslog Logging in Cisco ASA Firewall Lecture 52: Introduction and Concept of Cryptography & Terminologies Lecture 53: Introduction & Concept of Symmetric & Asymmetric Encryption Lecture 54: Introduction and Concept of Cryptography Hash (SHA, MD5) Lecture 55: Introduction and Concept of Virtual Private Network VPN Lecture 56: Introduction and Concept of IPSec Protocols Features Lecture 57: Introduction and Concept of Diffie-Hellman (DH) And Much More... Course 09: Network Security Level 2 Security and Risk Management Asset Security Security Engineering Communication and Network Security Identity and Access Management Security Assessment and Testing Security Operations Software Development Security Course 10: Cyber Security Level 3 Module 01: Getting Started Module 02: Cyber security Fundamentals Module 03:Types of Malware Module 04: Cyber Security Breaches Module 05: Types of Cyber Attacks Module 06: Prevention Tips Module 07: Mobile Protection Module 08: Social Network Security Module 09: Prevention Software Module 10: Critical Cyber Threats Module 11: Defense Against Hackers Module 12: Closing Course 11: Data Center Training Essentials: General Introduction Module 01: Data Center Introduction Module 02: Data Center Reliability Module 03: Data Center Equipment Module 04: Data Center White Space Module 05: Data Center Support Spaces Module 06: Data Center Security, Safety, Networks and IT CPD 120 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this Internet of Things (IoT) bundle. Persons with similar professions can also refresh or strengthen their skills by enrolling in this course. Students can take this course to gather professional knowledge besides their study or for the future. Requirements Our Internet of Things (IoT) is fully compatible with PC's, Mac's, laptops, tablets and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones, so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course; it can be studied in your own time at your own pace. Career path Having this various expertise will increase the value of your CV and open you up to multiple job sectors. Certificates Certificate of completion Digital certificate - Included Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Internet of Things) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

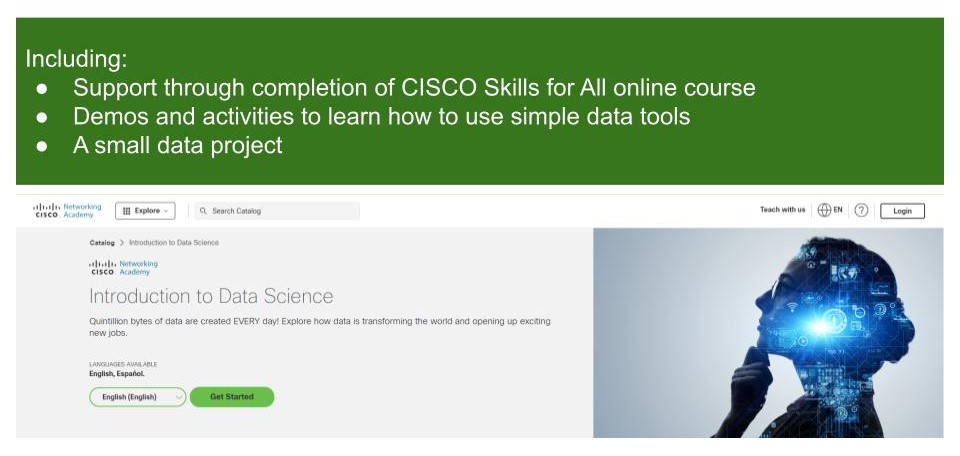
Introduction to Data Science
By futureCoders SE
Learn the basics of Data Science, combining a supported #CISCO Skills for All online course with practical learning and a project to help consolidate the learning.
CVPD Scripting - Part 1
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Application Developers; Programmers, Sales and Pre Sales, Technical Support, Project Managers, Cisco customers, partners and employees involved in UCCE/CVP or CVP stand alone deployments Overview Upon completing this course, the learner will be able to meet these overall objectives: Introduction to the Java API, its capabilities and limitations - Practice - This course is applicable for any version of CVP and Studio. Introduction to Voice Elements and their complexity - creating every different Java component to extend Studio (see below) Overview of a UCCE with CVP Comprehensive Call Flow Module 1 Overview of a UCCE with CVP Comprehensive Call Flow Module 2 ICM routing scripts to route calls to CVP VXML Server applications Passing data (e.g., global variables) Parsing and evaluating data returned Queueing Assigning data to send to Finesse. Module 3 Writing Call Studio scripts (applications) Prompting Callers ? using pre-recorded audio; TTS text-to-speech; Say it Smart to format audio as digits, date, time, currency; input error reprompting Menus Collecting and confirming caller input, such as account numbers, dates of birth, etc Working with variables ? Session data, Element data, Call data, Local data (CVP11) Introduction to retrieving data from back end systems: SQL Database interaction ? using the Studio Database element to select data Web service interaction- Studio Web Services element for SOAP-web services and calling a simple REST web service Playing audio to callers during back-end data retrieval Catch events Working with counters, decisions, math Introduction to javascript for substrings and string length Setting VoiceXML properties affecting the gateway Multi-Language applications Module 4 Working with Version Control Module 5 ÿImplementing a Post Call Survey Module 6 Using the Studio Debugger to test applications within Studio Module 7 CVP Reporting Server and CVP CUIC Reports Best practices regarding naming elements and variables Configuring data to pass to the Reporting Server using OAMP Understanding Reporting Server tables Understanding the Application Summary CUIC reports Module 8 Administration covered throughout the course OAMP Operations Console to deploy applications to VXML Server Using Studio Documenter to print Visio-like diagrams of the application Configuring log file properties Using logs for debugging applications Administrative scripts for graceful updates or suspensions of the server Important log, debug, administration files Module 9 Cisco Courtesy Callback Detailed discussion of the CCB Call flow, the ICM script, and the 5 Studio scripts used for Courtesy Callback.

Telephone Training - Cisco
By Telephone Trainers Ltd
78, 79, 88 and 99 series Handsets & Voicemail Cisco Call Manager (CCM) & Self Care Portal Jabber WebEx Meetings WebEx Training Centre WebEx Events Centre Attendant Console Standard and Advanced Console (ARC) UCCX/UCCE and Finesse Agent & Supervisor CUIC Reporting

------------------------NEW YEAR SALE ENDS TODAY------------------------ Boost Your Career with Apex Learning and Get Noticed By Recruiters in this Hiring Season! Get Hard Copy + PDF Certificates + Transcript + Student ID Card worth £180 as a Gift - Enrol Now The demand for cybersecurity pros in the UK is at an all-time high. Start and grow your career in IT cybersecurity with our Cloud Computing. These skill sets will help you show that you have the knowledge and expertise in the field. Employers hire individuals with expertise in higher-salaried positions. So, become a proven problem solver by enrolling in our Exclusive Cloud Computing Engineering Bundle. Throughout the Cloud Computing Engineering programme, it stresses how to improve your competency as a person in your chosen field while also outlining essential career insights in this job sector. Consequently, you'll sharpen your knowledge and skills; on the other hand, see a clearer picture of your career growth in future. By the end of the Cloud Computing Engineering bundle, you can equip yourself with the essentials to keep you afloat in the competition. Along with this Cloud Computing course, you will get 10 premium courses, an original hardcopy, 11 PDF Certificates (Main Course + Additional Courses) Student ID card as gifts. This Cloud Computing Engineering Bundle Consists of the following Premium courses: Course 01: Cloud Computing / CompTIA Cloud+ (CV0-002) Course 02: CompTIA Network+ Certification Course 03: CompTIA IT Fundamentals ITF+ (FCO-U61) Course 04: CompTIA A+ (220-1001) Course 05: CompTIA A+ (220-1002) Course 06: CompTIA Security+ (SY0-601) Course 07: CompTIA PenTest+ (Ethical Hacking) Course 08: CompTIA CySA+ Cybersecurity Analyst (CS0-002) Course 09: Cisco ASA Firewall Training Course 10: Linux for Absolute Beginners! Course 11: GDPR Data Protection Level 5 So, enrol in this bundle now to advance your career! Benefits you'll get choosing Apex Learning: Pay once and get lifetime access to 11 CPD courses Free e-Learning App for engaging reading materials & helpful assistance Certificates, student ID for the title course included in a one-time fee Free up your time - don't waste time and money travelling for classes Accessible, informative modules designed by expert instructors Learn at your ease - anytime, from anywhere Study the course from your computer, tablet or mobile device CPD accredited course - improve the chance of gaining professional skills Gain valuable knowledge without leaving your home Curriculum of the Cloud Computing Engineering Bundle: Course 01: Cloud Computing / CompTIA Cloud+ (CV0-002) What You Need to Know Introducing the Cloud System Requirements for Cloud Deployments Cloud Storage Cloud Compute Cloud Networking And Much More... Course 02: CompTIA Network+ Certification Networking Fundamentals Network Models and Topologies Network Components and Services Becoming a Network Professional Introducing Networking Standards Planning for Network Security Network Safety Fundamentals Network Operations And Much More... Course 03: CompTIA IT Fundamentals ITF+ (FCO-U61) How People Use Computers System Hardware Device Ports and Peripherals Data Storage and Sharing Understanding Operating Systems Setting Up and Configuring a PC Setting Up and Configuring a Mobile Device Managing Files And Much More... Course 04: CompTIA A+ (220-1001) All about the CompTIA A+ Safety and Professionalism The Visible Computer CPUs RAM Firmware Motherboards Power Supplies Mass Storage Technologies Implementing Mass Storage Essential Peripherals Building a PC And Much More... Course 05: CompTIA A+ (220-1002) All About the CompTIA A+ 2019 Core 2 Exam Safety and Professionalism The Visible Computer CPUs RAM Power Supply Implementing Mass Storage Building a PC Windows under the Hood Users, Groups, and Permissions Maintaining and Optimizing Operating Systems And Much More... Course 06: CompTIA Security+ (SY0-601) Introduction Risk Management Cryptography Identity and Account Management Tools of the Trade Securing Individual Systems The Basic LAN Securing Wireless LANs And Much More... Course 07: CompTIA PenTest+ (Ethical Hacking) Introduction Planning and Scoping Surveying the Target Select Your Attack Vector Selecting Pen Testing Tools Reporting and Communication Course 08: CompTIA CySA+ Cybersecurity Analyst (CS0-002) Introduction The Importance of Threat Data and Intelligence Threat Intelligence in Support of Organizational Security Vulnerability Assessment Tools Threats and Vulnerabilities Associated with Specialized Technology Threats and Vulnerabilities Associated with Specialized Technology Threats and Vulnerabilities Associated with Operating in the Cloud Mitigating Controls for Attacks and Software Vulnerabilities Security Solutions for Infrastructure Management Software Assurance Best Practices Hardware Assurance Best Practices And Much More... Course 09: Cisco ASA Firewall Training Common Network Security Terms Confidentiality, Integrity, Availability. Security Concepts & Terms Intro to Firewall Technologies About Cisco ASA Firewall Install Cisco ASAv Firewall in GNS3 Install ASA 9 Cluster, Security Context enable in GNS3. Install Cisco ASAv Firewall on EVE-NG Install Cisco ASAv Firewall on VMWare Workstation. Cisco ASA Firewall Basic Configuration Commands. Device Management Cisco ASA Console Device Management Cisco ASA Telnet Device Management Cisco ASA SSH And Much More... Course 10: Linux for Absolute Beginners! Introduction to Linux Linux Installation Linux Command Line Interface (CLI) Essentials Advanced CLI Usage Linux Development Tools Web Development Project Web Server Setup, Host Cofiguration and App Deployment And Much More... Course 11: GDPR Data Protection Level 5 GDPR Basics GDPR Explained Lawful Basis for Preparation Rights and Breaches Responsibilities and Obligations How will I get my Certificate? After successfully completing the Cloud Computing Engineering bundle, you will be able to order your CPD Accredited Certificates (PDF + Hard Copy) as proof of your achievement. PDF Certificate: Free (Previously it was £10 * 11 = £110) Hard Copy Certificate: Free (For The Title Course) If you want to get hardcopy certificates for other courses, generally you have to pay £20 for each. But with this special offer, Apex Learning is offering a Flat 50% discount on hard copy certificates, and you can get each for just £10! PS The delivery charge inside the UK is £3.99, and the international students have to pay £9.99. CPD 140 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this Cloud Computing Engineering bundle. Requirements No Requirements to enrol this Cloud Computing Engineering bundle. Career path Cloud Computing Engineering: Network administrator IT consultant Network field engineer Computer technician Help desk technician System engineer Network support specialist Network analyst And much more! Certificates Certificate of completion Digital certificate - Included Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (CompTIA Network+ Certification) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost.

World of Computer Networking: Your CCNA start
By Packt
This course will help you to prepare for the Cisco Certified Network Associate (CCNA) certification exam. The course covers all the major topics of computer networking and network devices, such as Internet Protocol (IP) addressing, routing, switching, Transmission Control Protocol/Internet Protocol (TCP/IP), Network Address Translation (NAT), Dynamic Host Configuration Protocol (DHCP), and Domain Name System (DNS).

Search By Location
- Cisco Courses in London
- Cisco Courses in Birmingham
- Cisco Courses in Glasgow
- Cisco Courses in Liverpool
- Cisco Courses in Bristol
- Cisco Courses in Manchester
- Cisco Courses in Sheffield
- Cisco Courses in Leeds
- Cisco Courses in Edinburgh
- Cisco Courses in Leicester
- Cisco Courses in Coventry
- Cisco Courses in Bradford
- Cisco Courses in Cardiff
- Cisco Courses in Belfast
- Cisco Courses in Nottingham