- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1963 A2 courses
Once Upon A Project - Stories and Their Influence on Project Performance
By IIL Europe Ltd
Once Upon A Project - Stories and Their Influence on Project Performance What are the stories people share about your project? Do the stories promote success or failure? Do they indicate engagement and respect, or disappointment and exclusion? Every project is a story, and the story can unfold as one of great success or crushing failure. The most effective projects use storylines that promote integration and excellence. The most successful project leaders are able to harness the power of stories to build and maintain a strong team, focus on core values, ensure effective reviews, and openly address risk. This session will consider the use of stories for project success, and suggest the most effective leaders are skilled at the art of story. This and other IIL Learning in Minutes presentations qualify for PDUs. Some titles, such as Agile-related topics may qualify for other continuing education credits such as SEUs, or CEUs. Each professional development activity yields one PDU for one hour spent engaged in the activity. Some limitations apply and can be found in the Ways to Earn PDUs section that discusses PDU activities and associated policies. Fractions of PDUs may also be reported. The smallest increment of a PDU that can be reported is 0.25. This means that if you spent 15 minutes participating in a qualifying PDU activity, you may report 0.25 PDU. If you spend 30 minutes in a qualifying PDU activity, you may report 0.50 PDU.

Things to Consider to Ensure a Successful Minimum Viable Product (MVP)
By IIL Europe Ltd
Things to Consider to Ensure a Successful Minimum Viable Product (MVP) This presentation will look at some remarkably successful companies that started with an idea, built a Minimum Viable Product, and never looked back. Learn the patterns and approaches they applied that led to their success and that keep them innovative in a competitive market space. We will examine several case studies from Dropbox, AirBnB, Groupon, Twitter, and Spotify. Then we will define what a MVP is and how the approach can be applied using tools like the Lean Canvas. We will look at 10 MVP patterns and approaches that can be applied to validate your product with your market. Just to keep it real the presentation will close with some reasons why MVPs fail. This and other IIL Learning in Minutes presentations qualify for PDUs. Some titles, such as Agile-related topics may qualify for other continuing education credits such as SEUs, or CEUs. Each professional development activity yields one PDU for one hour spent engaged in the activity. Some limitations apply and can be found in the Ways to Earn PDUs section that discusses PDU activities and associated policies. Fractions of PDUs may also be reported. The smallest increment of a PDU that can be reported is 0.25. This means that if you spent 15 minutes participating in a qualifying PDU activity, you may report 0.25 PDU. If you spend 30 minutes in a qualifying PDU activity, you may report 0.50 PDU.

Once Upon A Project - Stories and Their Influence on Project Performance
By IIL Europe Ltd
Once Upon A Project - Stories and Their Influence on Project Performance What are the stories people share about your project? Do the stories promote success or failure? Do they indicate engagement and respect, or disappointment and exclusion? Every project is a story, and the story can unfold as one of great success or crushing failure. The most effective projects use storylines that promote integration and excellence. The most successful project leaders are able to harness the power of stories to build and maintain a strong team, focus on core values, ensure effective reviews, and openly address risk. This session will consider the use of stories for project success, and suggest the most effective leaders are skilled at the art of story. This and other IIL Learning in Minutes presentations qualify for PDUs. Some titles, such as Agile-related topics may qualify for other continuing education credits such as SEUs, or CEUs. Each professional development activity yields one PDU for one hour spent engaged in the activity. Some limitations apply and can be found in the Ways to Earn PDUs section that discusses PDU activities and associated policies. Fractions of PDUs may also be reported. The smallest increment of a PDU that can be reported is 0.25. This means that if you spent 15 minutes participating in a qualifying PDU activity, you may report 0.25 PDU. If you spend 30 minutes in a qualifying PDU activity, you may report 0.50 PDU.

This course is intended to give you an overview of the common types and symptoms of dementia as well as going into how it can affect the brain in different ways. It also covers strategies to use with clients with dementia and dealing with challenging behaviour. The course is intended for anyone who works with or around people that may be living with dementia.

This Introduction to the Safe Handling of Medicines course will start by explaining the key terminology used when handling medicines. It then goes into detail about the roles of the people involved, some of the different groups of medicines, providing different levels of support to patients, infection control, label interpretation and much more.

A duty of care is the requirement that all health and social care professionals, and organisations providing health and care services, must put the interests of service users first. This course will give you an introduction to the concept of duty of care, cover how duty of care affects your work, what to do if you come across a duty of care dilemma and where to go for support or advice along with some practical examples of duty of care situations.

This course aims to provide a gentle introduction to the expectations of the Early Years Foundation Stage and it can also act as a refresher for those wanting to update their knowledge. It will introduce you to some of the key documents and legislation that relate to Early Years providers, the process for registering with Ofsted and the various policies and procedures that need to be in place. It also covers learning and development requirements, how to observe and assess the progress of children in your care and the safeguarding and welfare requirements laid out in the EYFS Framework.

Learn how to identify the different types of fire extinguishers that might be installed within your workplace and what situations they might be used in. At the end of the final module you will be presented with a simulation that will test what you’ve learnt.

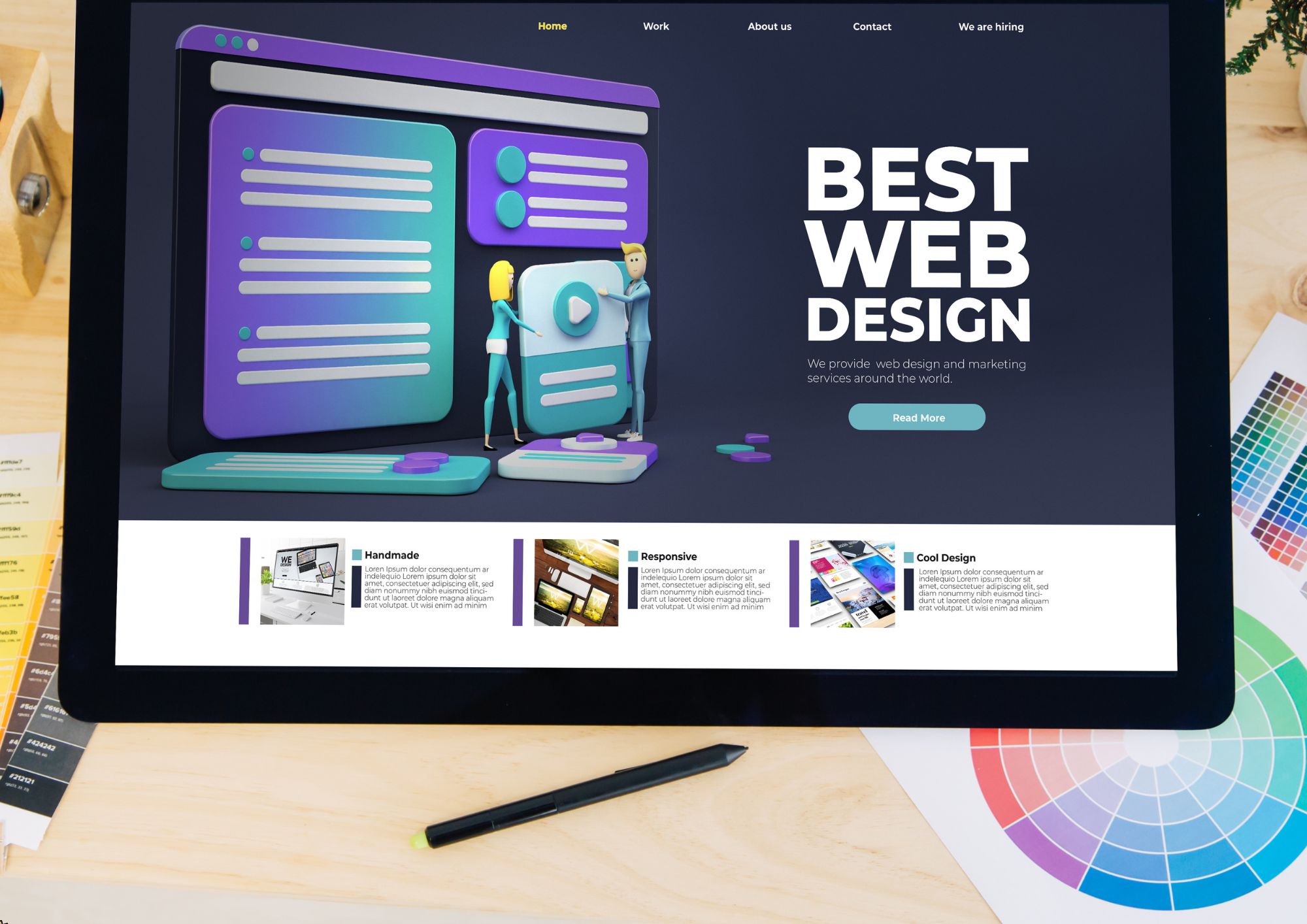
Web Design for Non-Designers A Practical Guide
By Compete High
Overview: 'Web Design for Non-Designers: A Practical Guide' Are you a non-designer looking to create stunning websites? Look no further! Our comprehensive course, 'Web Design for Non-Designers: A Practical Guide,' is tailored just for you. With six meticulously crafted modules, this course will empower you to master the art of web design and create visually captivating websites that leave a lasting impression. Module 1: Introduction to Web Design Dive into the fundamentals of web design, understanding its importance, principles, and basic terminology. Learn how to conceptualize your website and lay a solid foundation for your design journey. Module 2: User Experience (UX) Design Discover the key elements of user experience design and how they impact the effectiveness of your website. From navigation to usability, learn how to create seamless experiences that keep your visitors engaged and satisfied. Module 3: Layout and Composition Unlock the secrets of effective layout and composition in web design. Explore different grid systems, balance, and hierarchy to create visually appealing and organized layouts that enhance user engagement. Module 4: Color Theory and Psychology Delve into the fascinating world of color theory and psychology. Understand the impact of color on emotions and behaviors, and learn how to choose the perfect color palette to evoke the desired response from your audience. Module 5: Typography in Web Design Master the art of typography and its role in web design. Explore different font types, sizes, and styles, and learn how to use typography to enhance readability, convey hierarchy, and create a unique brand identity. Module 6: Visual Elements in Web Design Explore the use of visual elements such as images, icons, and illustrations to enhance the visual appeal of your website. Learn how to choose and manipulate visuals effectively to convey your message and engage your audience. With a perfect blend of theory and hands-on practical exercises, 'Web Design for Non-Designers: A Practical Guide' equips you with the knowledge and skills needed to create professional-looking websites with confidence. Whether you're a business owner, marketer, or aspiring web designer, this course is your gateway to unlocking the secrets of successful web design. Enroll now and unleash your creativity on the digital canvas! Course Curriculum Module 1_ Introduction to Web Design Introduction to Web Design 00:00 Module 2_ User Experience (UX) Design User Experience (UX) Design 00:00 Module 3_ Layout and Composition Layout and Composition 00:00 Module 4_ Color Theory and Psychology Color Theory and Psychology 00:00 Module 5_ Typography in Web Design Typography in Web Design 00:00 Module 6_ Visual Elements in Web Design Visual Elements in Web Design 00:00
Search By Location
- A2 Courses in London
- A2 Courses in Birmingham
- A2 Courses in Glasgow
- A2 Courses in Liverpool
- A2 Courses in Bristol
- A2 Courses in Manchester
- A2 Courses in Sheffield
- A2 Courses in Leeds
- A2 Courses in Edinburgh
- A2 Courses in Leicester
- A2 Courses in Coventry
- A2 Courses in Bradford
- A2 Courses in Cardiff
- A2 Courses in Belfast
- A2 Courses in Nottingham
