- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1137 Courses
Adobe Illustrator Basic to Intermediate Training
By London Design Training Courses
Why Learn Adobe Illustrator Basic to Intermediate Training Course? Course Link With our Illustrator Intermediate Course take your vector graphics to the next level and bring your designs to life with advanced techniques and tools. Gain hands-on skills in creating shapes, patterns, and logos, and learn how to edit images with precision. Duration: 6 hrs. Method: 1-on-1 - Personalized attention Schedule: Schedule by pre-booking a convenient hour of your choice, available from Mon to Sat between 9 am and 7 pm. This course covers fundamental tools and features of Adobe Illustrator, aimed at beginners, to enable them to create and edit vector graphics efficiently and effectively. Adobe Illustrator is the industry-leading vector graphic software for working with vector graphics, providing a comprehensive set of tools for producing exceptional graphics for various media, including print, video, web, and mobile devices. Course Title: Adobe Illustrator Course Outline: Mastering Advanced Drawing Techniques In-Depth Curvature Tool Mastery Advanced Pen Tool Usage: Drawing Complex Paths Understanding Path, Anchor Points, and Handles Precision Editing with Direct Selection Tool Slicing and Dividing Paths using Scissors and Knife Tools Exploring Advanced Stroke and Path Options Custom Width Profiles with the Width Tool Diverse Brushes Exploration in Brush Library Creating Scattered Objects with Scatter Brushes Applying Patterns along Paths with Pattern Brushes Crafting Custom Pattern Brushes Understanding Graphic Styles Efficient Usage of Graphic Style Libraries Creating, Deleting, and Saving Graphic Styles with Graphic Style Panel Leveraging the Power of Graphic Styles Mastering Pattern Manipulation Techniques Creating and Editing Patterns using Pattern Mode Modifying Pattern Elements with Precision Adjusting Spacing and Resizing Patterns using the Tile Tool Rectifying Background Errors with Overlap Options Saving and Exporting Custom Patterns Exploring Advanced Gradient Options Gradient Styles Exploration Fine-Tuning Gradients with the Gradient Annotator Creating Free Transform Gradient Points and Lines Applying Single Gradient across Multiple Objects Gradient and Transparency Integration Creative Applications and Practical Projects Applying Advanced Techniques to Real-World Projects Creative Problem-Solving Strategies Q&A Session and Feedback Gathering Note: Each section includes practical exercises and hands-on projects to reinforce learning. The course emphasizes practical application, ensuring participants leave with tangible skills and a deep understanding of advanced Adobe Illustrator concepts. Q: What will I learn in the London Design Training Course in Adobe Illustrator? A: In this course, you'll learn essential techniques for creating and editing vector graphics using Adobe Illustrator. The training covers drawing tools, shapes, layers, effects, styles, logo design, Image Trace, Live Paint, and integration into your design workflow. Q: What can I expect to achieve after completing the Illustrator training course? A: By the end of the course, you'll be proficient in Illustrator tools, create graphics for print, web, and mobile, design logos with special effects, and manipulate images. You'll receive an accredited Illustrator training certification and post-course support. Q: Is any prior knowledge of Illustrator required to attend the course? A: No, the course is designed for beginners, and no prior knowledge of Illustrator is necessary. Q: Which version of Illustrator will the training be based on? A: The training is primarily based on Illustrator 2023, but the techniques apply to recent releases. Q: Can I attend the course on either a Windows or Mac computer? A: Yes, Illustrator works identically on both Windows and Mac. Our training centers offer both platforms for your convenience.

Unlock the essentials of auditing with our course, "Business Auditor: Basic Auditing Techniques." Gain expertise in types of audits, planning, internal control, and more. Delve into UK audit standards, technology integration, and explore lucrative career prospects. Elevate your skills and become a proficient auditor today!

Master the intricacies of the UK tax system with our 'UK Self Assessment Tax Return: Comprehensive Guide' course. From understanding the fundamentals to advanced topics like income tax, expenses, and capital gains, gain the skills to confidently complete your self-assessment tax return. Ensure compliance, maximize deductions, and optimize your tax position with expert insights. Empower yourself financially and navigate tax complexities with ease. Enroll now for a comprehensive journey through the world of UK taxation.

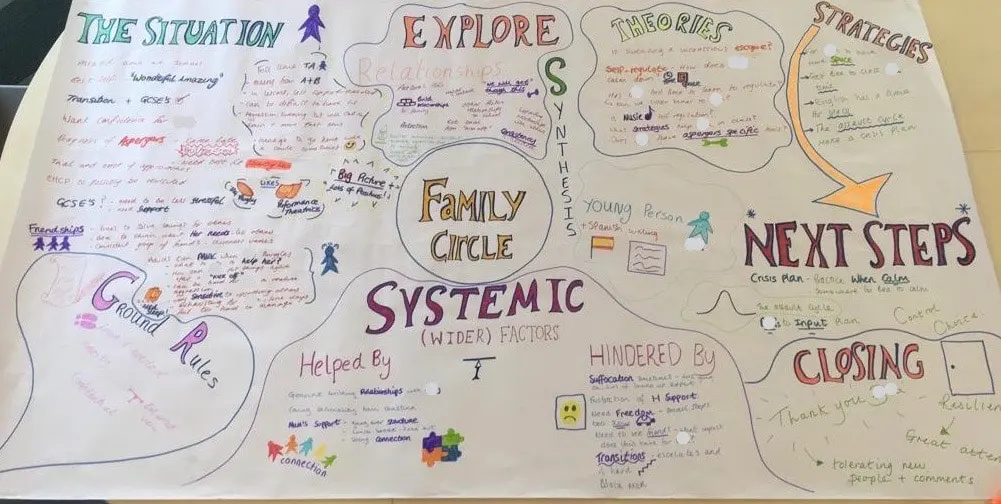
FAMILY CIRCLES
By Inclusive Solutions
Click to read more about this training, in which we demonstrate a live problem solving approach which is based on the active participation of family members. Course Category Inclusion Parents and Carers Behaviour and relationships Problem Solving Description In this training we demonstrate a live problem solving approach which is based on the active participation of family members. ‘Family Circles’ is an evolving new approach to problem solving with families and is based on our years of family work and the development and use of the Circle of Adults process. Inspired by our own Parent Solutions work and the Circle of Adults process as well as Family Group Conferencing and other Restorative Interventions we bring you Family Circles. Essentially the approach involves gathering a family together for a process that is facilitated but majors on the family members offering each other their wisdom and ideas. The approach is capacity focused, person centred approach to working with families rather than the dominant deficit oriented and ‘medical model’ of viewing and planning for or doing things to families. This training can be modelled with a group of professionals or better still with a family. In our work with families we develop the importance of naming stories or theories and seeking linkages and synthesis between what is found out and explored about the family situation and its history. We like participants to sit with the uncertainty, to reflect on the question ‘why’ but without judgement of each other. Deeper reflections may span a whole range of perspectives from ‘within person’ considerations, to situational or systemic possibilities. Health or emotional issues can be reflected on alongside organisational or transactional aspects of what is going on for the family. The better the shared understanding the better the strategy or actions which emerge from these meetings. Quality hypotheses with a close fit to reality lead to more effective implementation in the real world. We encourage ‘loose’ thinking, a search for connections, deeper listening, an ‘open mind’, speculation and exploration without moral judgements. From this stance self-reflection as well as reflection on the situation can produce remarkable insights. The quality of theories or new stories generated is directly influenced by family members’ experiences and the models of learning, behaviour and emotion, systems, educational development, change and so on that they have been exposed to. Learning Objectives To provide opportunities for: Shared problem solving in a safe exploratory climate in which the family will find its own solutions. Individuals to reflect on their own actions and strategies An exploration of whole-family processes and their impact Emotional support and shared understandings of issues at a child, parent, family, school and community level. Feed back to each other on issues, ideas and strategies that are agreed to be worth sharing with them. Who Is It For? Anyone interested in working with families in a way that builds and makes use of their capacities rather than focus on their challenges and difficulties. Social Care teams School staff Community organisers Educational Psychologists Course Content True family empowerment Deepening shared stories and understandings Facilitating groups Problem solving process Handling family group communication Allowing direct feedback and challenge between participants in a safe way Building relationships Process: Family members are welcomed: Introductions are carried out, ground rules and aims clarified whilst coffee is drunk. A recap from the last session is carried out: To follow up developments and reflections after the last meeting. One issue is selected for the main focus Issue presentation: The family member who raised the concern is asked questions to tell the ‘story’ of the issue or problem. Additional questions/information from the group about the problem are gathered: Ground rules may need to be observed carefully here. Individual participants need to be kept focused and prevented from leaping to premature conclusions or to making ‘helpful’ suggestions about strategy. Relationship aspects to the problem are explored. Metaphors and analogies are invited. How would a fly on the wall see your relationship? If you were alone together on a desert island, what would it be like? Impact of previous relationships/spillage from one relationship to another are explored. Eg what situation they are reminded of? For instance, does this situation remind you of any of those angry but helpless feelings you had with your other son when he was an adolescent? This provides opportunities to reflect on how emotions rub off on other people. The parent feels really frustrated, and on reflection we can see that so does the child System/Organisation factors (Family system/school and community systems and so on): What aspects help or hinder the problem? For instance, does the pastoral system of the local school provide space, or time and skilled personnel able to counsel this young person and work actively with their parents? Synthesis. At this stage the Graphic facilitator summarises what they have heard. They then go on to describe linkages and patterns in what they have heard. This can be very powerful. The person doing the graphic work has been able to listen throughout the presentation process and will have been struck by strong messages, emotions and images as they have arisen. The story and meaning of what is happening in the situation may become a little clearer at this point. Typical links may be ‘mirrored emotions’ strong themes such as loss and separation issues, or repeated processes such as actions triggering rejection. This step provides an excellent grounding for the next process of deepening understanding. What alternative strategies/interventions are open to be used? Brainstormed and recorded. ’Either/ors’ need to be avoided at this time also. This needs to be a shared session in which the family member who is presenting the concern contributes as much as anyone. Care is needed to ensure that this person is not overloaded with other people’s strategies. The final selection of strategy or strategies from the brainstormed list is the problem presenter’s choice. Strategies might include: a special time for the young person, a meeting with the child’s parents to explore how she is being managed at home and to share tactics, a home-school diary, counselling, or an agreed action plan that all are aware of, agreed sanctions and rewards and so forth. Strategies may productively involve processes of restitution and restoration, when ‘sorry’ is not enough. Making it right, rather than punishments or rewards, may then becomes the focus. First Steps. The problem presenter is finally asked to agree one or two first steps which they can carry out over the next 3-7 days. It can help to assign a ‘coach’ who will check in with them to ensure they have carried out the action they have named. This is a time to be very specific. Steps should be small and achievable. The person is just ‘making a start’. A phone call, or making an agreement with a key other person not present at the meeting would be ideal examples. Final reflections. Sometimes referred to as a ‘round of words’ help with closure for all involved. Reflections are on the process not the problem. In large families this is best done standing in a circle. In smaller groups all can remain sitting. Passing around a ‘listening stick’ or something similar such as a stone or light heighten the significance of the process ending and improve listening. Finally the problem presenter is handed the ‘Graphic’ this is their record of the meeting and can be rolled and presented ceremoniously by the facilitators for maximum effect! If you liked this course you may well like: Parent Solutions
Financial Investigator
By Compliance Central
Financial Investigator Training Course is Now The Most Demanding Course to Advance Your Career! Financial Investigator Course is for those who want to advance in this field. Throughout this course, you will learn the essential skills and gain the knowledge needed to become well versed in Personal Finance. Our course starts with the basics of Financial Investigator training and gradually progresses towards advanced topics. Therefore, each lesson of this course is intuitive and easy to understand. Financial Investigator Course Basic Learning Outcomes: Upon successful completion of this highly appreciated this Financial Investigator training Course, you'll be a skilled professional, besides- You can provide services related to Financial Investigator with complete knowledge and confidence. You'll be competent and proficient enough to explore Financial Investigator related job fields on your own. Furthermore, you can train up others and grow an efficient peer community in your locality and serve people. It will enhance your portfolio, you can use the certificate as proof of your efficiency to the employer. It will boost up your productivity, you can use the skill and credentials, and become more competent in your vocation with increased earning! So, stand out in the job market by completing the course. Get an accredited certificate and add it to your resume to impress your employers. Along with the Financial Investigator training course, you also get: Lifetime Access Unlimited Retake Exam & Tutor Support Easy Accessibility to the Course Materials- Anytime, Anywhere - From Any Smart Device (Laptop, Tablet, Smartphone Etc.) 100% Learning Satisfaction Guarantee Learn at your own pace from the comfort of your home, as the rich learning materials of this course are accessible from any place at any time. The curriculums are divided into tiny, bite-sized modules by industry specialists. And you will get answers to all your queries from our experts. Curriculum Breakdown of the Financial Investigator Course: Module 1: Introduction Module 2: Characteristics of Financial Crimes Module 3: Categories of Financial Crimes Module 4: Financial Crime Response Plan Module 5: Collecting, Preserving and Gathering Evidence Module 6: Laws against Financial Fraud CPD 10 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this course. Requirements To enrol in this course, all you need is a basic understanding of the English Language and an internet connection. Career path After completing this course, you can explore trendy and in-demand jobs related to this course.

C)PEH - Certified Professional Ethical Hacker
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for IS Security Owners Security Officers Ethical Hackers Information Owners Penetration Testers System Owners and Managers Cyber Security Engineers Overview Upon completion, the Certified Professional Ethical Hacker candidate will be able to competently take the C)PEH exam. To protect an information system you need to be able to see that system through the eyes of the attacker.ÿThe Certified Professional Ethical Hackerÿcertification course is the foundational training to Mile2?s line of penetration testing courses because it teaches you to think like a hacker.ÿ Therefore, you can set up dynamic defenses to prevent intrusion. First, you will learn the value of vulnerability assessments.ÿ Then, you will discover how to use those assessments to make powerful changes in an information system?s security. Additionally, you will learn how malware and destructive viruses function and how to implement counter response and preventative measures when it comes to a network hack. Course Introduction Introduction to Ethical Hacking Linux Fundamentals Protocols Cryptography Password Cracking Malware Security Devices Information Gathering ? Passive Reconnaissance Social Engineering Active Reconnaissance Vulnerability Assessment Network Attacks Hacking Servers Hacking Web Technologies Hacking Wireless Technologies Maintaining Access and Covering Tracks

Embark on a riveting expedition into the realm of website security with our course, 'Website Hacking From Scratch.' Delve deep into the labyrinth of potential vulnerabilities, from SQL injections to XSS vulnerabilities, equipping yourself with the prowess to identify and safeguard against digital threats. By course end, learners are not only conversant with the anatomy of website vulnerabilities but are also adept at leveraging tools like Owasp ZAP for holistic website fortification. Learning Outcomes Gain comprehensive insights into the foundation of website vulnerabilities and their exploitation. Understand and identify risks associated with file uploads, code executions, and session management. Acquire proficiency in detecting and safeguarding against SQL and XSS vulnerabilities. Master the use of automated tools, such as Owasp ZAP, in vulnerability detection. Develop strategies for effective post-exploitation management. Why choose this Website Hacking From Scratch course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments are designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Website Hacking From Scratch Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Who is this Website Hacking From Scratch course for? Aspiring cybersecurity enthusiasts eager to delve into website security. Web developers keen to fortify their sites against potential breaches. IT professionals aiming to enhance their repertoire with security expertise. Entrepreneurs looking to ensure the robustness of their online platforms. Individuals curious about ethical hacking and its applications. Career path Ethical Hacker: £25,000 - £70,000 Penetration Tester: £30,000 - £60,000 Cybersecurity Analyst: £28,000 - £55,000 IT Security Consultant: £35,000 - £75,000 Web Security Manager: £40,000 - £80,000 Information Security Officer: £45,000 - £85,000 Prerequisites This Website Hacking From Scratch does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Website Hacking From Scratch was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Course Introduction Course Introduction 00:02:00 Preparation - Creating a Penetration Testing Lab Lab Overview & Needed Software 00:08:00 Installing Kali 2019 As a Virtual Machine Using a Ready Image 00:10:00 Installing Kali 2019 As a Virtual Machine 00:10:00 Installing Metasploitable As a Virtual Machine 00:04:00 Preparation - Linux Basics Basic Overview of Kali Linux 00:05:00 The Linux Terminal & Basic Linux Commands 00:11:00 Configuring Metasploitable & Lab Network Settings 00:06:00 Website Basics What is a Website? 00:04:00 How To Hack a Website? 00:04:00 Information Gathering Gathering Information Using Whois Lookup 00:05:00 Discovering Technologies Used On The Website 00:06:00 Gathering Comprehensive DNS Information 00:10:00 Discovering Websites On The Same Server 00:04:00 Discovering Subdomains 00:12:00 Discovering Sensitive Files 00:07:00 Analysing Discovered Files 00:04:00 Maltego - Discovering Servers, Domains & Files 00:08:00 Maltego - Discovering Websites, Hosting Provider & Emails 00:05:00 File Upload Vulnerabilities What are they? And How To Discover & Exploit Basic File Upload Vulnerabilities 00:07:00 HTTP Requests - GET & POST 00:04:00 Intercepting HTTP Requests 00:07:00 Exploiting More Advanced File Upload Vulnerabilities 00:04:00 Exploiting More Advanced File Upload Vulnerabilities 00:04:00 [Security] Fixing File Upload Vulnerabilities 00:06:00 Code Execution Vulnerabilities What are they? & How To Discover & Exploit Basic Code Execution Vulnerabilities 00:07:00 Exploiting Advanced Code Execution Vulnerabilities 00:06:00 [Security] - Fixing Code Execution Vulnerabilities 00:06:00 Local File Inclusion Vulnerabilities (LFI) What are they? And How To Discover & Exploit Them 00:06:00 Gaining Shell Access From LFI Vulnerabilities - Method 1 00:07:00 Gaining Shell Access From LFI Vulnerabilities - Method 2 00:11:00 Remote File Inclusion Vulnerabilities (RFI) Remote File Inclusion Vulnerabilities - Configuring PHP Settings 00:04:00 Remote File Inclusion Vulnerabilities - Discovery & Exploitation 00:06:00 Exploiting Advanced Remote File Inclusion Vulnerabilities 00:03:00 [Security] Fixing File Inclusion Vulnerabilities 00:06:00 SQL Injection Vulnerabilities What is SQL 00:06:00 Dangers of SQL Injections 00:03:00 SQL Injection Vulnerabilities - SQLi In Login Pages Discovering SQL Injections In POST 00:08:00 Bypassing Logins Using SQL Injection Vulnerability 00:05:00 Bypassing More Secure Logins Using SQL Injections 00:06:00 [Security] Preventing SQL Injections In Login Pages 00:08:00 SQL Injection Vulnerabilities - Extracting Data From The Database Discovering SQL Injections in GET 00:07:00 Reading Database Information 00:05:00 Finding Database Tables 00:04:00 Extracting Sensitive Data Such As Passwords 00:04:00 SQL Injection Vulnerabilities - Advanced Exploitation Discovering & Exploiting Blind SQL Injections 00:06:00 Discovering a More Complicated SQL Injection 00:07:00 Extracting Data (passwords) By Exploiting a More Difficult SQL Injection 00:05:00 Bypassing Filters 00:05:00 Bypassing Security & Accessing All Records 00:09:00 [Security] Quick Fix To Prevent SQL Injections 00:07:00 Reading & Writing Files On The Server Using SQL Injection Vulnerability 00:06:00 Getting A Reverse Shell Access & Gaining Full Control Over The Target Web Server 00:08:00 Discovering SQL Injections & Extracting Data Using SQLmap 00:07:00 [Security] - The Right Way To Prevent SQL Injection 00:05:00 XSS Vulnerabilities Introduction - What is XSS or Cross Site Scripting? 00:03:00 Discovering Basic Reflected XSS 00:04:00 Discovering Advanced Reflected XSS 00:05:00 Discovering An Even More Advanced Reflected XSS 00:07:00 Discovering Stored XSS 00:03:00 Discovering Advanced Stored XSS 00:04:00 XSS Vulnerabilities - Exploitation Hooking Victims To BeEF Using Reflected XSS 00:06:00 Hooking Victims To BeEF Using Stored XSS 00:04:00 BeEF - Interacting With Hooked Victims 00:04:00 BeEF - Running Basic Commands On Victims 00:04:00 BeEF - Stealing Credentials/Passwords Using A Fake Login Prompt 00:02:00 Bonus - Installing Veil 3.1 00:06:00 Bonus - Veil Overview & Payloads Basics 00:07:00 Bonus - Generating An Undetectable Backdoor Using Veil 3 00:10:00 Bonus - Listening For Incoming Connections 00:07:00 Bonus - Using A Basic Delivery Method To Test The Backdoor & Hack Windows 10 00:07:00 BeEF - Gaining Full Control Over Windows Target 00:04:00 [Security] Fixing XSS Vulnerabilities 00:07:00 Insecure Session Management Logging In As Admin Without a Password By Manipulating Cookies 00:06:00 Discovering Cross Site Request Forgery Vulnerabilities (CSRF) 00:07:00 Exploiting CSRF Vulnerabilities To Change Admin Password Using a HTML File 00:07:00 Exploiting CSRF Vulnerabilities To Change Admin Password Using Link (Preview) 00:06:00 [Security] The Right Way To Prevent CSRF Vulnerabilities 00:09:00 Brute Force & Dictionary Attacks What Are Brute Force & Dictionary Attacks? 00:04:00 Creating a Wordlist 00:07:00 Launching a Wordlist Attack & Guessing Login Password Using Hydra 00:14:00 Discovering Vulnerabilities Automatically Using Owasp ZAP Scanning Target Website For Vulnerabilities 00:04:00 Analysing Scan Results 00:04:00 Post Exploitation Post Exploitation Introduction 00:04:00 Interacting With The Reverse Shell Access Obtained In Previous Lectures 00:07:00 Escalating Reverse Shell Access To Weevely Shell 00:08:00 Weevely Basics - Accessing Other Websites, Running Shell Commands etc 00:07:00 Bypassing Limited Privileges & Executing Shell Commands 00:05:00 Downloading Files From Target Webserver 00:05:00 Uploading Files To Target Webserver 00:08:00 Getting a Reverse Connection From Weevely 00:08:00 Accessing The Database 00:09:00 Resources Resources - Website Hacking From Scratch 00:00:00 Assignment Assignment - Website Hacking From Scratch 00:00:00

To succeed in any business or manage any work properly, understanding finance is crucial. Learn how you can conduct a financial investigation for any task or project from this Financial Investigator course and boost your financial skills. This course will help you to understand financial management and the investigation process properly. This comprehensive Financial Investigator course is developed by industry experts with the utmost care and thorough research. All the topics are broken down into simply digestible bite-sized modules, allowing our students to understand each lesson quickly. After completing the Financial Investigator course, you will build up accurate knowledge and skills with proper confidence to enrich yourself. These skills will brighten up your career in the relevant job market. Our Financial Investigator course is the most effective way to obtain a thorough understanding of this subject. You will receive an e-certificate immediately after completing the Financial Investigator course, which will help you find work in the sector and will boost your CV. Enrol in this Financial Investigator course from Course Gate if you want to learn more about this skill and become competent in this area. Learning Objectives Understand the purpose of financial investigation Be able to understand the steps of financial investigation Manage your finance better Learn how financial documentation works Be able to sort and analyse your data properly Help your organisation grow using proper financial management Learn about the roles and responsibilities of a financial investigator Who is this Course for? This introductory Financial Investigator course is ideal for aspiring Financial Investigators who wish to gain the relevant skills and knowledge to fast track their careers. It is for those who have little or no knowledge of the principles of Financial Investigation or those who are new to the field and want to test their skills and knowledge. There are no entry requirements for this course; however, an eye for detail and a creative mind is essential. Entry Requirement This course is available to all learners of all academic backgrounds. A good understanding of the English language, numeracy and ICT are required to attend this course. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £4.99 and the hard copy for £9.99. Also, you can order both PDF and hardcopy certificates for £12.99. Career path On successful completion of the Financial Investigator course, learners can progress to a more advanced program from our course list. Career opportunities in this field include freelancing or working in-house, within a range of professional settings, with the opportunity to earn a high salary. Related professions in this industry include: Financial Managers Finance Advisors Financial Investigators Managers Accountants Bookkeepers Course Curriculum Module 1: Introduction to Financial Investigator Introduction to Financial Investigator 00:21:00 Module 2: Introduction to Financial Investigation Introduction to Financial Investigation 00:12:00 Module 3: Characteristics of Financial Crimes Characteristics of Financial Crimes 00:13:00 Module 4: Categories of Financial Crimes Categories of Financial Crimes 00:20:00 Module 5: Financial Crime Response Plan Financial Crime Response Plan 00:18:00 Module 6: Collecting, Preserving and Gathering Evidence Collecting, Preserving and Gathering Evidence 00:13:00 Module 7: Laws against Financial Fraud Laws against Financial Fraud 00:18:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

Gather Information from Summaries - Creative Entrepreneurship
By Compete High
ð Unlock Your Creative Entrepreneurial Potential with 'Gather Information from Summaries' Online Course! ð Are you an aspiring creative entrepreneur looking to harness the power of information to fuel your success? Welcome to our transformative online course tailored just for you! Introducing 'Gather Information from Summaries - Creative Entrepreneurship' - your gateway to mastering the art of extracting valuable insights from summaries to supercharge your entrepreneurial journey. In this dynamic course, you'll learn: ð Strategies to Efficiently Extract Key Information: Discover proven techniques to swiftly gather essential insights from summaries, enabling you to stay ahead of trends and opportunities in your industry. ð§ Cognitive Amplification Techniques: Sharpen your cognitive skills to absorb, retain, and apply information effectively, giving you a competitive edge in decision-making and innovation. ð Empower Your Entrepreneurial Vision: Learn how to translate distilled knowledge into actionable steps that fuel your creative endeavors, fostering growth and success in your ventures. ð¡ Transform Information Overload into Strategic Advantage: Master the art of sifting through vast amounts of data, transforming it into a strategic asset rather than a hurdle. ð¤ Networking and Collaboration: Explore ways to leverage your newfound expertise in information gathering to build meaningful connections and collaborations within your industry. Taught by industry experts with a passion for entrepreneurial creativity, this course offers: ð Comprehensive Modules: Dive into a structured curriculum crafted to deliver maximum learning and skill enhancement. ð» Engaging Multimedia Content: Access video lectures, interactive exercises, and downloadable resources for a well-rounded learning experience. ð Practical Applications: Apply your knowledge immediately with real-world exercises and case studies, ensuring you're equipped to implement these skills in your entrepreneurial endeavors. Join a vibrant community of like-minded creative entrepreneurs, exchange ideas, and embark on a transformative journey together! Whether you're an aspiring entrepreneur or a seasoned professional seeking to revitalize your approach, 'Gather Information from Summaries - Creative Entrepreneurship' will equip you with the tools and insights to thrive in today's fast-paced business landscape. Don't miss this opportunity to elevate your entrepreneurial game! Enroll now and unleash your potential with the power of information! Course Curriculum

------------------------NEW YEAR SALE ENDS TODAY------------------------ Give a compliment to your career and take it to the next level. This Fraud Management & Anti Money Laundering Awareness Complete Diploma bundle will provide you with the essential knowledge to shine in your professional career. Whether you want to develop skills for your next job or elevate your skills for your next promotion, this Fraud Management & Anti Money Laundering Awareness Complete Diploma bundle will help you stay ahead of the pack. Throughout the Fraud Management & Anti Money Laundering Awareness Complete Diploma programme, it stresses how to improve your competency as a person in your chosen field while also outlining essential career insights in the relevant job sector. Along with this Fraud Management & Anti Money Laundering Awareness Complete Diploma course, you will get 10 premium courses, an originalhardcopy, 11 PDF certificates (Main Course + Additional Courses) Student ID card as gifts. This Fraud Management & Anti Money Laundering Awareness Complete Diploma Bundle Consists of the following Premium courses: Course 01:Fraud Management & Anti Money Laundering Awareness Complete Diploma Course 02:Financial Investigator Course 03:Financial Analysis Course 04:Team Management Course 05:Internal Audit Training Diploma Course 06:Training of Compliance Officer Level 3 Course 07:Level 3 Tax Accounting Course 08:GDPR Data Protection Level 5 Course 09:English Law and Legal System Level 3 Course 10:Workplace Confidentiality Course 11:Human Rights Enrol now in Fraud Management & Anti Money Laundering Awareness Complete Diploma to advance your career, and use the premium study materials from Apex Learning. Certificate: PDF Certificate: Free (Previously it was £6*11 = £66) Hard Copy Certificate: Free (For The Title Course: Previously it was £10) The bundle incorporates basic to advanced level skills to shed some light on your way and boost your career. Hence, you can strengthen your Fraud Management & Anti Money Laundering Awareness Complete Diploma expertise and essential knowledge, which will assist you in reaching your goal. Moreover, you can learn from any place in your own time without travelling for classes. Curriculum Course 01: Fraud Management & Anti Money Laundering Awareness Complete Diploma Module 01: Introduction to Money Laundering Module 02: Proceeds of Crime Act 2002 Module 03: Development of Anti-Money Laundering Regulation Module 04: Responsibility of the Money Laundering Reporting Office Module 05: Risk-based Approach Module 06: Customer Due Diligence Module 07: Record Keeping Module 08: Suspicious Conduct and Transactions Module 09: Awareness and Training Course 02: Financial Investigator Module 01: Introduction to Financial Investigator Module 02: Introduction to Financial Investigation Module 03: Characteristics of Financial Crimes Module 04: Categories of Financial Crimes Module 05: Financial Crime Response Plan Module 06: Collecting, Preserving and Gathering Evidence Module 07: Laws against Financial Fraud Course 03: Financial Analysis Section-1. Introduction Section-2. Profitability Section-3. Return Ratio Section-4. Liqudity Ratio Section-5.Operational Analysis Section-6. Detecting Manipulation And Much More... CPD 110 CPD hours / points Accredited by CPD Quality Standards Who is this course for? Anyone from any background can enrol in this Fraud Management & Anti Money Laundering Awareness Complete Diploma bundle. Requirements This Fraud Management & Anti Money Laundering Awareness Complete Diploma course has been designed to be fully compatible with tablets and smartphones. Career path Having this expertise will increase the value of your CV and open you up to multiple job sectors. Certificates Certificate of completion Digital certificate - Included Certificate of completion Hard copy certificate - Included You will get the Hard Copy certificate for the title course (Fraud Management & Anti Money Laundering Awareness Complete Diploma) absolutely Free! Other Hard Copy certificates are available for £10 each. Please Note: The delivery charge inside the UK is £3.99, and the international students must pay a £9.99 shipping cost

Search By Location
- gathering Courses in London
- gathering Courses in Birmingham
- gathering Courses in Glasgow
- gathering Courses in Liverpool
- gathering Courses in Bristol
- gathering Courses in Manchester
- gathering Courses in Sheffield
- gathering Courses in Leeds
- gathering Courses in Edinburgh
- gathering Courses in Leicester
- gathering Courses in Coventry
- gathering Courses in Bradford
- gathering Courses in Cardiff
- gathering Courses in Belfast
- gathering Courses in Nottingham