- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
6659 Courses
Description Register on the Master JavaScript with Data Visualization today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get a certificate as proof of your course completion. The Master JavaScript with Data Visualization course is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablets, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With This Course Receive a digital certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Certificate of Achievement After the successful completion of the final assessment, you will receive a CPD-accredited certificate of achievement. The PDF certificate is for 9.99, and it will be sent to you immediately after through e-mail. You can get the hard copy for 15.99, which will reach your doorsteps by post. Method of Assessment You need to attend an assessment right after the completion of this course to evaluate your progression. For passing the assessment, you need to score at least 60%. After submitting your assessment, you will get feedback from our experts immediately. Who Is This Course For The course is ideal for those who already work in this sector or are aspiring professionals. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Course Content Introduction Getting Started Introduction to Getting Started 00:02:00 Course Curriculum 00:05:00 How to Get Pre-Requisites 00:02:00 Getting Started on Windows, Linux or Mac 00:01:00 How to ask a Great Questions 00:02:00 FAQ's 00:01:00 Setting Up Local Development Environment What is JavaScript 00:09:00 Choosing Code Editor 00:03:00 Installing Code Editor (Sublime Text) 00:04:00 Installing Code Editor(Visual Studio Code) 00:07:00 Hello World Program 00:14:00 Getting Output 00:11:00 Summary 00:02:00 JavaScript Fundamentals Introduction 00:02:00 Internal JavaScript 00:13:00 External JavaScript 00:09:00 Inline JavaScript 00:04:00 Async and defer 00:06:00 Variables 00:13:00 Data Types 00:10:00 Numbers 00:06:00 Boolean 00:04:00 Arrays() 00:12:00 Objects 00:06:00 Comments 00:05:00 Summary 00:01:00 JavaScript Strings Introduction 00:02:00 Strings 00:06:00 String Formatting 00:05:00 String Methods 00:12:00 Summary 00:02:00 JavaScript Operators Introduction 00:02:00 Arithmetic operators 00:07:00 Assignment operators 00:03:00 Comparison operators 00:06:00 Logical operators 00:08:00 Summary 00:02:00 JavaScript Conditional Statements Introduction 00:02:00 If statement 00:04:00 If-else statement 00:05:00 If-else-if statement 00:04:00 Switch-case statement 00:09:00 Summary 00:01:00 JavaScript Control Flow Statements Introduction 00:02:00 While loop 00:09:00 Do-while loop 00:03:00 For loop 00:08:00 Break 00:02:00 Continue 00:03:00 Coding Exercise 00:02:00 Solution for Coding Exercise 00:02:00 Summary 00:02:00 JavaScript Functions Introduction 00:02:00 Creating a Function 00:07:00 Function Call() 00:07:00 Function with parameters 00:05:00 Function Bind() 00:06:00 Summary 00:01:00 Data Visualization (Google Chart) Introduction 00:01:00 How to Use Google chart script 00:04:00 Line Graph chart 00:14:00 Scatter plots chart 00:02:00 Bar chart 00:04:00 Pie chart 00:02:00 3D Pie chart 00:02:00 Summary 00:01:00 JavaScript Error Handling Introduction 00:01:00 Try-catch 00:05:00 Try-catch-finally 00:17:00 Summary 00:01:00 JavaScript Client-Side Validations Introduction 00:01:00 On Submit Validation 00:09:00 Input Numeric Validation 00:12:00 Login Form Validation 00:05:00 Password Strength Check Validation 00:04:00 Summary 00:01:00 Order your Certificates & Transcripts Order your Certificates & Transcripts 00:00:00 Frequently Asked Questions Are there any prerequisites for taking the course? There are no specific prerequisites for this course, nor are there any formal entry requirements. All you need is an internet connection, a good understanding of English and a passion for learning for this course. Can I access the course at any time, or is there a set schedule? You have the flexibility to access the course at any time that suits your schedule. Our courses are self-paced, allowing you to study at your own pace and convenience. How long will I have access to the course? For this course, you will have access to the course materials for 1 year only. This means you can review the content as often as you like within the year, even after you've completed the course. However, if you buy Lifetime Access for the course, you will be able to access the course for a lifetime. Is there a certificate of completion provided after completing the course? Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate can be a valuable addition to your professional portfolio and can be shared on your various social networks. Can I switch courses or get a refund if I'm not satisfied with the course? We want you to have a positive learning experience. If you're not satisfied with the course, you can request a course transfer or refund within 14 days of the initial purchase. How do I track my progress in the course? Our platform provides tracking tools and progress indicators for each course. You can monitor your progress, completed lessons, and assessments through your learner dashboard for the course. What if I have technical issues or difficulties with the course? If you encounter technical issues or content-related difficulties with the course, our support team is available to assist you. You can reach out to them for prompt resolution.

Register on the JavaScript Masterclass: ES6 Modern Development today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The JavaScript Masterclass: ES6 Modern Development is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The JavaScript Masterclass: ES6 Modern Development Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the JavaScript Masterclass: ES6 Modern Development, all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16. Course Content Section 01: Introduction Introduction To This Course 00:02:00 Setup on Windows 00:06:00 Setup on Mac OS X 00:05:00 Setup on Linux 00:08:00 Online Code IDE 00:02:00 Section 02: Basics Comments 00:05:00 Noscript Tag 00:02:00 Strict Mode 00:03:00 Console Output 00:02:00 Variables 00:04:00 Prompt 00:02:00 Functions 00:09:00 Arithmetic Operators 00:08:00 Comparison Operators 00:07:00 Logical Operators 00:04:00 Bitwise Operators 00:04:00 Assignment Operators 00:05:00 Conditional Operators 00:03:00 Type of Operator 00:02:00 Conditional Statements 00:06:00 Switch Statement 00:05:00 For Loop 00:05:00 For In Loop 00:03:00 While Loop 00:02:00 Do While Loop 00:03:00 Loops Advanced 00:03:00 Events 00:03:00 Cookies 00:05:00 Redirect Page 00:03:00 Dialog Box 00:04:00 Void Operator 00:03:00 Printing the Page 00:02:00 Section 03: Objects Number 00:04:00 Boolean 00:03:00 String 00:04:00 Date 00:05:00 Regular Expressions 00:04:00 Arrays 00:15:00 Math 00:04:00 HTML DOM 00:05:00 Section 04: Classes Simple Class Example 00:04:00 Variables 00:03:00 Functions 00:02:00 Static Functions 00:02:00 Instance of Operator 00:02:00 Class Inheritance 00:04:00 Method Overriding 00:03:00 Super Keyword 00:02:00 Section 05: Advanced Error Handling 00:03:00 Validation 00:05:00 Animation 00:10:00 Multimedia Controls 00:03:00 Image Map 00:03:00 Browser Navigator 00:04:00 Modules 00:04:00 Promises 00:06:00 Block Scope 00:04:00 Loop Labels 00:03:00 Variable Hoisting 00:02:00 Function Hoisting 00:01:00 Anonymous Functions 00:02:00 Arrow & Lambda Functions 00:02:00 Function Constructor 00:03:00 Generator Functions 00:06:00 Immediately Invoked Function Expressions 00:05:00 JavaScript URI 00:02:00 Template Literals 00:04:00 Map Collection 00:07:00 Set Collection 00:03:00 AJAX 00:08:00 Section 06: Resource Resource 00:00:00 Frequently Asked Questions Are there any prerequisites for taking the course? There are no specific prerequisites for this course, nor are there any formal entry requirements. All you need is an internet connection, a good understanding of English and a passion for learning for this course. Can I access the course at any time, or is there a set schedule? You have the flexibility to access the course at any time that suits your schedule. Our courses are self-paced, allowing you to study at your own pace and convenience. How long will I have access to the course? For this course, you will have access to the course materials for 1 year only. This means you can review the content as often as you like within the year, even after you've completed the course. However, if you buy Lifetime Access for the course, you will be able to access the course for a lifetime. Is there a certificate of completion provided after completing the course? Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate can be a valuable addition to your professional portfolio and can be shared on your various social networks. Can I switch courses or get a refund if I'm not satisfied with the course? We want you to have a positive learning experience. If you're not satisfied with the course, you can request a course transfer or refund within 14 days of the initial purchase. How do I track my progress in the course? Our platform provides tracking tools and progress indicators for each course. You can monitor your progress, completed lessons, and assessments through your learner dashboard for the course. What if I have technical issues or difficulties with the course? If you encounter technical issues or content-related difficulties with the course, our support team is available to assist you. You can reach out to them for prompt resolution.

Register on the Kotlin Masterclass Programming Course: Android Coding Bible today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The Kotlin Masterclass Programming Course: Android Coding Bible is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The Kotlin Masterclass Programming Course: Android Coding Bible Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the Kotlin Masterclass Programming Course: Android Coding Bible, all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16. Course Content Section 01: Introduction & Setup Introduction To This Course 00:02:00 Windows Setup 00:13:00 Mac Setup 00:11:00 Linux Setup 00:12:00 Online Code Editor 00:02:00 Section 02: Basics Variables 00:06:00 Data Types 00:06:00 String 00:05:00 Array 00:07:00 Data Type Conversion 00:05:00 Comments 00:04:00 Arithmetic Operators 00:07:00 Relational Operators 00:06:00 Assignment Operators 00:06:00 Unary Operators 00:05:00 Bitwise Operators 00:09:00 Logical Operators 00:04:00 Input & Output 00:03:00 Section 03: Control Statements Conditional if Statement 00:05:00 when Statement 00:07:00 For Loop 00:04:00 while Loop 00:04:00 do while Loop 00:04:00 Break Statement 00:04:00 Continue Statement 00:04:00 Section 04: Functions Basic Functions 00:03:00 Function Parameters 00:04:00 Return Values 00:04:00 Recursion 00:04:00 Default & Named Arguments 00:06:00 Lambda Function 00:04:00 Higher Order Function 00:05:00 Inline Function 00:02:00 Section 05: Error/Exception Handling Try Catch Block 00:04:00 Try Catch Expression 00:05:00 Multiple Catch Block77 00:05:00 Nested Try Catch Block 00:05:00 Finally Block 00:02:00 Throw Keyword 00:02:00 Section 06: NULL Safety Nullable & Non Nullable Types 00:03:00 Smart Cast 00:02:00 Unsafe and Safe Cast 00:03:00 Elvis Operator 00:04:00 Section 07: Collections List: listOf Function 00:06:00 List: mutableListOf Function 00:05:00 List: arrayListOf Function 00:06:00 Map: mapOf Function 00:07:00 Map: HashMap 00:08:00 Map: hashMapOf Function 00:05:00 Map: mutableMapOf Function 00:04:00 Set: setOf Function 00:04:00 Set: mutableSetOf Function 00:04:00 Set: HashSet 00:04:00 Section 08: Classes & Objects Basic Example 00:07:00 Nested and Inner Class 00:06:00 Constructors 00:05:00 Visibility Modifiers 00:06:00 Inheritance 00:05:00 Method Overriding 00:04:00 Property Overriding 00:02:00 Abstract Class 00:03:00 Superclass 00:03:00 Data Class 00:05:00 Multiple Class Inheritance & Interfaces 00:03:00 Sealed Class 00:03:00 Extension Function 00:03:00 Generics 00:05:00 Section 09: Extras Integer Type Range 00:05:00 Regex 00:04:00 Call Java from Kotlin 00:03:00 Call Kotlin from Java 00:02:00 Section 10: Resource Resource 00:00:00 Frequently Asked Questions Are there any prerequisites for taking the course? There are no specific prerequisites for this course, nor are there any formal entry requirements. All you need is an internet connection, a good understanding of English and a passion for learning for this course. Can I access the course at any time, or is there a set schedule? You have the flexibility to access the course at any time that suits your schedule. Our courses are self-paced, allowing you to study at your own pace and convenience. How long will I have access to the course? For this course, you will have access to the course materials for 1 year only. This means you can review the content as often as you like within the year, even after you've completed the course. However, if you buy Lifetime Access for the course, you will be able to access the course for a lifetime. Is there a certificate of completion provided after completing the course? Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate can be a valuable addition to your professional portfolio and can be shared on your various social networks. Can I switch courses or get a refund if I'm not satisfied with the course? We want you to have a positive learning experience. If you're not satisfied with the course, you can request a course transfer or refund within 14 days of the initial purchase. How do I track my progress in the course? Our platform provides tracking tools and progress indicators for each course. You can monitor your progress, completed lessons, and assessments through your learner dashboard for the course. What if I have technical issues or difficulties with the course? If you encounter technical issues or content-related difficulties with the course, our support team is available to assist you. You can reach out to them for prompt resolution.

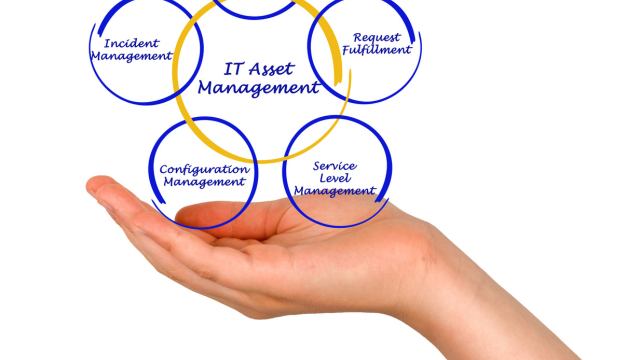
Step into the world of IT Asset Management (ITAM) and elevate your skills. From establishing ITAM programs to mastering asset security and compliance, this course offers a comprehensive guide to managing IT assets effectively. Enhance your ITAM expertise today!
Register on the Food and Beverage Manager today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The Food and Beverage Manager is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The Food and Beverage Manager Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the Food and Beverage Manager, all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16.

Register on the CompTIA A+ (220-1002) today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get an e-certificate as proof of your course completion. The CompTIA A+ (220-1002) is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablet, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With The CompTIA A+ (220-1002) Receive a e-certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Course Design The course is delivered through our online learning platform, accessible through any internet-connected device. There are no formal deadlines or teaching schedules, meaning you are free to study the course at your own pace. You are taught through a combination of Video lessons Online study materials Certification Upon successful completion of the course, you will be able to obtain your course completion e-certificate free of cost. Print copy by post is also available at an additional cost of £9.99 and PDF Certificate at £4.99. Who Is This Course For: The course is ideal for those who already work in this sector or are an aspiring professional. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Requirements: The online training is open to all students and has no formal entry requirements. To study the CompTIA A+ (220-1002), all your need is a passion for learning, a good understanding of English, numeracy, and IT skills. You must also be over the age of 16.

Master the strategies of handing medicine efficiently and safely with the Safe Handling of Medication course. Medicine should be handled carefully as human lives depend on it. Medicine is prepared to make you well, but if you do not use it properly, you may sick and even it may cause death. The purpose of the course is to aware you how to handle medicine safely. The course presents a general overview of the legislation and guidelines regarding the management of medication management settings. The principal legal aspects of handling medicines will be covered in the course. Therefore, you will gain all the essential skills for Health's UK Core Skills Training Framework (CSTF), the Care Quality Commission (CQC) recommendations for health care and social care providers. The course guides you to know the procedures for ordering, receiving, administering, storing and disposing of medicines safely. You will explore the steps of obtaining and receiving supplies. You will also learn how drugs are administered and how problems may occur. Upon completion, you will be able to know the techniques for storing and disposing of the drugs safely and securely. Who is this course for? Safe Handling of Medication is suitable for anyone who want to gain extensive knowledge, potential experience and professional skills in the related field. This course is CPD accredited so you don't have to worry about the quality. Requirements Our Safe Handling of Medication is open to all from all academic backgrounds and there is no specific requirements to attend this course. It is compatible and accessible from any device including Windows, Mac, Android, iOS, Tablets etc. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £9 and the hard copy for £15. Also, you can order both PDF and hardcopy certificates for £22. Career path This course opens a new door for you to enter the relevant job market and also gives you the opportunity to acquire extensive knowledge along with required skills to become successful. You will be able to add our qualification to your CV/resume which will help you to stand out in the competitive job industry. Course Curriculum Diploma in Safe Handling of Medication Introduction to Safe Handling of Medicines 00:30:00 Legislation and guidance of medication management 00:30:00 Principles of Safe and Appropriate Handling of Medicines 00:45:00 Medication Risk Assessment Guidance 00:30:00 Consent to Treatment 00:30:00 Handling Medicines in Social Care Settings 01:00:00 Requirements for Specific Services 00:45:00 Levels of Care and Support 00:15:00 Procedure for Handling Medication 00:30:00 The Six Rights of Medication Administration 00:30:00 Covert Administration of Medication 00:30:00 Recording Procedures 00:15:00 Storage of Medication 00:15:00 Transfer and Disposal of Medication 00:30:00 Drug Formulation and Ways of Taking It 01:00:00 Mock Exam Mock Exam - Safe Handling of Medication 00:20:00 Final Exam Final Exam - Safe Handling of Medication 00:20:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

Improve your accounting skills to perform a wide range of finance-related tasks by taking this Accountancy course. Through this course, you'll get a glimpse of how to perform your duties as an accountant, such as preparing financial statements and maintaining business records. The Accountancy course will thoroughly introduce you to the roles and responsibilities of a successful accountant. Here, you will gain valuable insights on accounting concepts and standards, double-entry bookkeeping, balance sheet, income statement, and financial statements. In addition, you'll learn to prepare cash flow statements and acquire knowledge of financial planning and budgeting. Finally, you'll learn the steps to a successful audit for error-free accounting processes. Learning Objectives Familiarise yourself with the roles and responsibilities of a successful accountant Learn about double-entry bookkeeping Enrich your knowledge of trial balance Learn to prepare income statements, financial statements and cash flow statements Gain the essential skills in financial budgeting and planning Know about the types of audits Who is this Course for? This introductory course is ideal for aspiring professionals who wish to gain the relevant skills and knowledge to fast track their careers. It is for those who have little or no accounting knowledge or those who are new to the field and want to test their skills and knowledge. There are no entry requirements for this course. However, an eye for detail and a creative mind is essential. Entry Requirement This course is available to all learners of all academic backgrounds. Good understanding of English language, numeracy and ICT are required to attend this course. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £4.99 and the hard copy for £9.99. Also, you can order both PDF and hardcopy certificates for £12.99. Career path On successful completion of the Accountancy course, learners can progress to a more advanced program from our course list. Career opportunities in this field include freelancing or working in-house, within a range of professional settings, with the opportunity to earn a high salary. Related professions in this industry include: Accounts Assistant Accounts Payable & Expenses Supervisor Accounts Payable Clerk Audit Trainee Payroll Administrator / Supervisor Tax Assistant / Accountant. Accounting Clerk Auditing Clerk Accounts Receivable Clerk Course Curriculum Module 01: Introduction to Accounting Introduction to Accounting 00:15:00 Module 02: The Role of an Accountant The Role of an Accountant 00:16:00 Module 03: Accounting Concepts and Standards Accounting Concepts and Standards 00:22:00 Module 04: Double-Entry Bookkeeping Double-Entry Bookkeeping 00:23:00 Module 05: Balance Sheet Balance Sheet 00:21:00 Module 06: Income statement Income statement 00:19:00 Module 07: Financial statements Financial statements 00:27:00 Module 08: Cash Flow Statements Cash Flow Statements 00:17:00 Module 09: Understanding Profit and Loss Statement Understanding Profit and Loss Statement 00:17:00 Module 10: Financial Budgeting and Planning Financial Budgeting and Planning 00:28:00 Module 11: Auditing Auditing 00:17:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

Description Enrol the Adobe InDesign CC Beginner course and learn Adobe InDesign CC in simple and easy steps. The course is designed for the novice people or people who have little or no knowledge about the desktop publishing software application Adobe InDesign CC. Using the application, you will be able to create incredible graphical works such as posters, flyers, brochures, magazines, newspapers, presentations, books and ebooks. The course covers the basic features and functions of the application. You will be familiar with the user interface of the software and learn the basic InDesign documents. Adobe InDesign is also a vector program like Adobe Illustrator. You will learn how to modify the text, modify the layout, format the text, modify graphics and use effects. Additionally, the course shows you how to play with the colors to create an amazing output. You will explore the procedures of working with tables, adding and transforming shapes, managing pages, layers, and objects, and more. By the end of the course, you will gain all the essential functions of the software. Assessment: This course does not involve any MCQ test. Students need to answer assignment questions to complete the course, the answers will be in the form of written work in pdf or word. Students can write the answers in their own time. Once the answers are submitted, the instructor will check and assess the work. Certification: After completing and passing the course successfully, you will be able to obtain an Accredited Certificate of Achievement. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. Who is this Course for? Adobe InDesign CC Beginner is certified by CPD Qualifications Standards and CiQ. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic background. Requirements Our Adobe InDesign CC Beginner is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path After completing this course you will be able to build up accurate knowledge and skills with proper confidence to enrich yourself and brighten up your career in the relevant job market. Introduction Introduction FREE 00:01:00 Building a Basic InDesign Document Overview of InDesign 00:03:00 Touring the InDesign Interface 00:10:00 Customizing Preferences 00:09:00 Building a document 00:09:00 Advanced Document Settings 00:09:00 Adding Graphics 00:06:00 Adding Text 00:03:00 Customizing the Workspace Using Panels and Workspace Presets 00:10:00 Document Views 00:08:00 Understanding the Control Panel 00:04:00 Managing Pages Adding, Moving, and Deleting Pages 00:06:00 Using Master Pages 00:10:00 Modifying Text Selecting Text 00:03:00 Understanding Text Frame Options 00:09:00 Importing Text 00:06:00 Threading Text 00:05:00 Using Special Characters 00:10:00 Using Spell Check 00:07:00 Using the Story Editor 00:04:00 Modifying Graphics Defining Graphic Types 00:07:00 Placing Multiple Graphics 00:04:00 Selecting Graphics 00:05:00 Fitting Options 00:07:00 Updating Graphics 00:07:00 Placing Photoshop and Illustrator Files 00:05:00 Working with Color Basics of Color 00:06:00 Working with Swatches 00:08:00 Creating Swatches 00:08:00 Making Spot Color Swatches 00:03:00 Working with the Color Panel 00:05:00 Creating and Using Gradients 00:08:00 Using Effects Using the Effects Panel 00:08:00 Using the Blend Modes 00:04:00 Adding and Removing Effects 00:03:00 Adding and Transforming Shapes Adding Vector Shapes 00:08:00 Drawing Vector Lines 00:08:00 Selecting and Moving Frames 00:07:00 Scaling Arrowheads 00:05:00 Managing Objects and Layers Managing Layers 00:10:00 Aligning and Grouping Objects 00:06:00 Wrapping Text around an Object 00:07:00 Formatting Text Character Formatting 00:11:00 Advanced Character Formatting 00:10:00 Paragraph Formatting 00:10:00 Using Styles Basics of Styles 00:01:00 Managing Paragraph Styles 00:10:00 Managing Character Styles 00:05:00 Using Object Styles 00:08:00 Working with Tables Creating Tables 00:10:00 Formatting Tables and Cells 00:08:00 Using Table and Cell Styles 00:08:00 Exporting the Document to Other Formats Preflighting your document 00:09:00 Packaging your Document 00:10:00 Printing your Document 00:09:00 Converting to PDF 00:06:00 Conclusion Course Recap 00:01:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Search By Location
- Steps Courses in London
- Steps Courses in Birmingham
- Steps Courses in Glasgow
- Steps Courses in Liverpool
- Steps Courses in Bristol
- Steps Courses in Manchester
- Steps Courses in Sheffield
- Steps Courses in Leeds
- Steps Courses in Edinburgh
- Steps Courses in Leicester
- Steps Courses in Coventry
- Steps Courses in Bradford
- Steps Courses in Cardiff
- Steps Courses in Belfast
- Steps Courses in Nottingham
