- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
3013 Courses
PMP Certification Training
By Packt
The PMP course covers the latest trends, emerging practices, and core competencies that are required by a project management professional. Learners will also get an understanding of real-world scenarios through the case studies that are developed by the industry PMP-certified veterans.

Be on the Inside: Decode the Jargon of Project Management
By OnlinePMCourses
Understand the Terminology of Modern Project Management with this Handy Guide and Glossary
Effective Leadership Development
By Leadership Management International (LMI) UK
Everyone has what it takes to become an effective leader, but first you must learn the skills needed to succeed in a position of responsibility. Our program will help people nurture the talent within and allow managers to lead confidently. Sometimes, working longer hours isn’t the right approach, as you risk burning out and abandoning the task at hand. Instead, effective leadership teaches you how to organise your workload, practice better time management and learn the power of delegation.

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - Introduction to Ethical Hacking Information Security Overview Cyber Kill Chain Concepts Hacking Concepts Ethical Hacking Concepts Information Security Controls Information Security Laws and Standards 2 - 2 - Foot-printing and Reconnaissance Footprinting Concepts Footprinting through Search Engines Footprinting through Web Services Footprinting through Social Networking Sites Website Footprinting Email Footprinting Who is Footprinting DNS Footprinting Network Footprinting Footprinting through Social Engineering Footprinting Tools Footprinting Countermeasures 3 - Scanning Networks Network Scanning Concepts Scanning Tools Host Discovery Port and Service Discovery OS Discovery (Banner Grabbing/OS Fingerprinting) Scanning Beyond IDS and Firewall Draw Network Diagrams 4 - Enumeration Enumeration Concepts NetBIOS Enumeration SNMP Enumeration LDAP Enumeration NTP and NFS Enumeration SMTP and DNS Enumeration Other Enumeration Techniques Enumeration Countermeasures 5 - Vulnerability Analysis Vulnerability Assessment Concepts Vulnerability Classification and Assessment Types Vulnerability Assessment Solutions and Tools Vulnerability Assessment Reports 6 - System Hacking System Hacking Concepts Gaining Access Escalating Privileges Maintaining Access Clearing Logs 7 - Malware Threats Malware Concepts APT Concepts Trojan Concepts Virus and Worm Concepts Fileless Malware Concepts Malware Analysis Countermeasures Anti-Malware Software 8 - Sniffing Sniffing Concepts Sniffing Technique: MAC Attacks Sniffing Technique: DHCP Attacks Sniffing Technique: ARP Poisoning Sniffing Technique: Spoofing Attacks Sniffing Technique: DNS Poisoning Sniffing Tools Countermeasures Sniffing Detection Techniques 9 - Social Engineering Social Engineering Concepts Social Engineering Techniques Insider Threats Impersonation on Social Networking Sites Identity Theft Countermeasures 10 - Denial-of-Service DoS/DDoS Concepts DoS/DDoS Attack Techniques BotnetsDDoS Case Study DoS/DDoS Attack Tools Countermeasures DoS/DDoS Protection Tools 11 - Session Hijacking Session Hijacking Concepts Application Level Session Hijacking Network Level Session Hijacking Session Hijacking Tools Countermeasures 12 - Evading IDS, Firewalls, and Honeypots IDS, IPS, Firewall, and Honeypot Concepts IDS, IPS, Firewall, and Honeypot Solutions Evading IDS Evading Firewalls IDS/Firewall Evading Tools Detecting Honeypots IDS/Firewall Evasion Countermeasures 13 - Hacking Web Servers Web Server Concepts Web Server Attacks Web Server Attack Methodology Web Server Attack Tools Countermeasures Patch Management Web Server Security Tools 14 - Hacking Web Applications Web Application Concepts Web Application Threats Web Application Hacking Methodology Web API, Webhooks, and Web Shell Web Application Security 15 - SQL Injection SQL Injection Concepts Types of SQL Injection SQL Injection Methodology SQL Injection Tools Evasion Techniques Countermeasures 16 - Hacking Wireless Networks Wireless Concepts Wireless Encryption Wireless Threats Wireless Hacking Methodology Wireless Hacking Tools Bluetooth Hacking Countermeasures Wireless Security Tools 17 - Hacking Mobile Platforms Mobile Platform Attack Vectors Hacking Android OS Hacking iOS Mobile Device Management Mobile Security Guidelines and Tools 18 - IoT and OT Hacking IoT Hacking IoT Concepts IoT Attacks IoT Hacking Methodology IoT Hacking Tools Countermeasures OT Hacking OT Concepts OT Attacks OT Hacking Methodology OT Hacking Tools Countermeasures 19 - Cloud Computing Cloud Computing Concepts Container Technology Serverless Computing Cloud Computing Threats Cloud Hacking Cloud Security 20 - Cryptography Cryptography Concepts Encryption Algorithms Cryptography Tools Public Key Infrastructure (PKI) Email Encryption Disk Encryption Cryptanalysis Countermeasures Additional course details: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

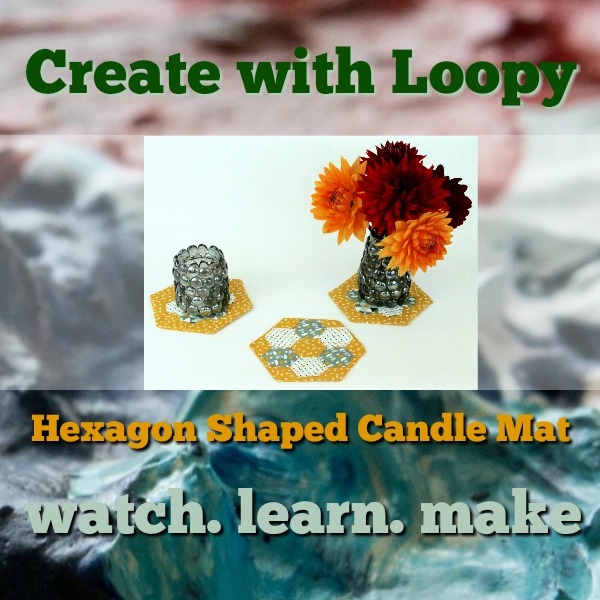
Sew a Hexagon Shaped Candle Mat
By Loopy's Place
A sewing class to create a hexagon shaped candle mat using a mixture of hand and machine sewing.
Embark on a transformative journey into the realm of AutoLISP programming with our comprehensive course titled 'Complete AutoLISP Programming.' Crafted with precision and expertise, this course is not just a curriculum; it's a key to unlocking a world of possibilities within AutoCAD customization. Imagine seamlessly creating macros for essential commands, mastering AutoLISP rules, variables, math functions, list functions, user input functions, object handling functions, selection sets, conditionals, and delving into the intricacies of AutoCAD objects and data models. Authored by industry experts, this course goes beyond the basics, providing a Quick Win Demo and hands-on projects that reinforce your newfound skills. Learning Outcomes Develop a deep understanding of AutoLISP programming rules, enabling you to create efficient and customized AutoCAD commands. Master the application of AutoLISP variables in real-world programming scenarios, honing your skills through practical exercises. Acquire proficiency in AutoLISP math functions, empowering you to perform complex mathematical operations seamlessly within AutoCAD. Unlock the potential of AutoLISP's list functions, gaining the ability to manipulate lists for enhanced program functionality. Explore AutoLISP's user input functions, object handling functions, and delve into the intricacies of conditionals and equality functions. Why choose this Complete AutoLISP Programming course? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards and CIQ after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Unlock career resources for CV improvement, interview readiness, and job success. Who is this The Complete AutoLISP Programming course for? CAD enthusiasts and draftsmen seeking to elevate their AutoCAD customization skills. Architects aiming to streamline and enhance their design processes. Engineers looking to automate repetitive tasks and boost productivity. Students and professionals in the fields of architecture, engineering, and design. Anyone with a passion for programming and a desire to delve into the world of AutoCAD customization. Career path AutoCAD Programmer: £35,000 - £45,000 CAD Automation Specialist: £40,000 - £50,000 Architectural Technologist: £30,000 - £40,000 Engineering Design Consultant: £35,000 - £45,000 BIM Specialist: £40,000 - £50,000 Project Manager (CAD): £45,000 - £55,000 Prerequisites This Complete AutoLISP Programming does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Complete AutoLISP Programming was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Unit 01: Introduction Module 01: Introduction 00:01:00 Module 02: Course Outline 00:05:00 Module 03: Introduction to AutoLISP 00:02:00 Module 04: Who is this Course for? 00:02:00 Module 05: What will I Learn? 00:01:00 Module 06: About the Author 00:02:00 Module 07: Why Learn AutoLISP? 00:02:00 Module 08: Tools 00:04:00 Unit 02: Quick Win Demo Module 01: Create Zoom Command Macros 00:13:00 Module 02: Create Layer Command Macros 00:10:00 Module 03: Create Insert Command Macros 00:07:00 Module 04: Create Audit Commands 00:06:00 Unit 03: AutoLISP Rules Module 01: AutoLISP Rules 00:05:00 Unit 04: AutoLISP Variables Module 01: Understanding AutoLISP Variables 00:05:00 Module 02: Using Variables in a Real World Program - Part 1 00:08:00 Module 03: Using Variables in a Real World Program - Part 2 00:08:00 Module 04: Using Variables in a Real World Program - Part 3 00:05:00 Module 05: Using Variables in a Real World Program - Part 4 00:07:00 Unit 05: AutoLISP Math Functions Module 01: Math Functions in Theory 00:06:00 Module 02: Math Functions by Example 00:15:00 Unit 06: AutoLISP's List Functions Module 01: List Functions Theory - Part 1 00:06:00 Module 02: CAR Function - Demo 00:02:00 Module 03: CDR Function - Demo 00:02:00 Module 04: CADR Function - Demo 00:02:00 Module 05: CADDR Function - Demo 00:02:00 Module 06: CAAR Function - Demo 00:02:00 Module 07: CDDR Function - Demo 00:01:00 Module 08: List Functions Theory - Part 2 00:05:00 Module 09: list Function - Demo 00:01:00 Module 10: cons Function - Demo 00:02:00 Module 11: nth Function - Demo 00:01:00 Module 12: Foreach Function - Demo 00:04:00 Module 13: List Functions Theory - Part 3 00:05:00 Module 14: Assoc Function - Demo 00:04:00 Module 15: Subst Function - Demo 00:06:00 Module 16: Last Function - Demo 00:02:00 Module 17: Reverse Function - Demo 00:02:00 Unit 07: AutoLISP's User Input Functions Module 01: User Input Functions Theory - Part 1 00:05:00 Module 02: User Input Functions Theory - Part 2 00:04:00 Module 03: GetPoint Function - Demo 00:02:00 Module 04: GetInt Function - Demo 00:03:00 Module 05: GetString Function - Demo 00:04:00 Module 06: GetReal Function - Demo 00:02:00 Module 07: GetDist Function - Demo 00:04:00 Module 08: GetCorner Function - Demo 00:04:00 Module 09: GetAngle Function - Demo 00:10:00 Module 10: GetKword Function - Demo 00:05:00 Unit 08: Object Handling Functions Module 01: Object Handling Functions - Theory 00:04:00 Module 02: Entsel Function - Demo 00:03:00 Module 03: Entnext Function - Demo 00:03:00 Module 04: Entlast Function - Demo 00:02:00 Module 05: Entget Function - Demo 00:04:00 Module 06: Object Handling Functions - Exercises 00:02:00 Module 07: Object Handling Functions - Solutions to Exercises 00:06:00 Unit 09: AutoLISP's Selection Sets Module 01: Selection Sets - Theory 00:08:00 Module 02: Ssget Function - Demo 00:11:00 Module 03: Ssadd Function - Demo 00:05:00 Module 04: Ssdel Function - Demo 00:03:00 Module 05: Ssmemb Function - Demo 00:03:00 Module 06: Ssname Function - Demo 00:03:00 Module 07: Sslength Function - Demo 00:05:00 Module 08: Selection Sets - Exercises 00:04:00 Module 09: Selection Sets - Solutions to Exercises 00:13:00 Unit 10: Conditionals And Equality Functions Module 01: Using If and Progn Statements 00:05:00 Module 02: Using While and EQ Functions 00:05:00 Module 03: Using Cond and And Functions 00:04:00 Unit 11: AutoCAD Objects - Data Model Module 01: AutoCAD Objects: Re-examined (Part 1) 00:04:00 Module 02: AutoCAD Objects: Re-examined (Part 2) 00:05:00 Module 03: Line Object: Re-examined (Demo) 00:05:00 Module 04: Circle Object: Re-examined (Demo) 00:04:00 Module 05: Text Object: Re-examined (Demo) 00:08:00 Module 06: Dimension Object: Re-examined (Demo) 00:11:00 Module 07: Block/Attribute Object: Re-examined (Demo) 00:28:00 Unit 12: Symbol Table And Dictionary Handling Functions Module 01: Symbol Table and Dictionary-Handling Functions - Theory 00:05:00 Module 02: Tblsearch - Demo 00:13:00 Module 03: Tblnext - Demo 00:09:00 Unit 13: Hands-On Projects Module 01: CDIM - Project 00:12:00 Module 02: CHSTYLE - Project 00:16:00 Module 03: EXTATTR - Hands-On Project 00:26:00 Unit 14: Conclusion Module 01: Conclusion Message and Thank you! 00:01:00

Project Management Checklists
By OnlinePMCourses
Make Rapid Progress with a Comprehensive Set of Project Management Templates

Description Register on the Complete AutoLISP Programming today and build the experience, skills and knowledge you need to enhance your professional development and work towards your dream job. Study this course through online learning and take the first steps towards a long-term career. The course consists of a number of easy to digest, in-depth modules, designed to provide you with a detailed, expert level of knowledge. Learn through a mixture of instructional video lessons and online study materials. Receive online tutor support as you study the course, to ensure you are supported every step of the way. Get a certificate as proof of your course completion. The Complete AutoLISP Programming course is incredibly great value and allows you to study at your own pace. Access the course modules from any internet-enabled device, including computers, tablets, and smartphones. The course is designed to increase your employability and equip you with everything you need to be a success. Enrol on the now and start learning instantly! What You Get With This Course Receive a digital certificate upon successful completion of the course Get taught by experienced, professional instructors Study at a time and pace that suits your learning style Get instant feedback on assessments 24/7 help and advice via email or live chat Get full tutor support on weekdays (Monday to Friday) Certificate of Achievement After the successful completion of the final assessment, you will receive a CPD-accredited certificate of achievement. The PDF certificate is for 9.99, and it will be sent to you immediately after through e-mail. You can get the hard copy for 15.99, which will reach your doorsteps by post. Method of Assessment You need to attend an assessment right after the completion of this course to evaluate your progression. For passing the assessment, you need to score at least 60%. After submitting your assessment, you will get feedback from our experts immediately. Who Is This Course For The course is ideal for those who already work in this sector or are aspiring professionals. This course is designed to enhance your expertise and boost your CV. Learn key skills and gain a professional qualification to prove your newly-acquired knowledge. Course Content Unit 01: Introduction Module 01: Introduction 00:01:00 Module 02: Course Outline 00:05:00 Module 03: Introduction to AutoLISP 00:02:00 Module 04: Who is this Course for? 00:02:00 Module 05: What will I Learn? 00:01:00 Module 06: About the Author 00:02:00 Module 07: Why Learn AutoLISP? 00:02:00 Module 08: Tools 00:04:00 Unit 02: Quick Win Demo Module 01: Create Zoom Command Macros 00:13:00 Module 02: Create Layer Command Macros 00:10:00 Module 03: Create Insert Command Macros 00:07:00 Module 04: Create Audit Commands 00:06:00 Unit 03: AutoLISP Rules Module 01: AutoLISP Rules 00:05:00 Unit 04: AutoLISP Variables Module 01: Understanding AutoLISP Variables 00:05:00 Module 02: Using Variables in a Real World Program - Part 1 00:08:00 Module 03: Using Variables in a Real World Program - Part 2 00:08:00 Module 04: Using Variables in a Real World Program - Part 3 00:05:00 Module 05: Using Variables in a Real World Program - Part 4 00:07:00 Unit 05: AutoLISP Math Functions Module 01: Math Functions in Theory 00:06:00 Module 02: Math Functions by Example 00:15:00 Unit 06: AutoLISP's List Functions Module 01: List Functions Theory - Part 1 00:06:00 Module 02: CAR Function - Demo 00:02:00 Module 03: CDR Function - Demo 00:02:00 Module 04: CADR Function - Demo 00:02:00 Module 05: CADDR Function - Demo 00:02:00 Module 06: CAAR Function - Demo 00:02:00 Module 07: CDDR Function - Demo 00:01:00 Module 08: List Functions Theory - Part 2 00:05:00 Module 09: list Function - Demo 00:01:00 Module 10: cons Function - Demo 00:02:00 Module 11: nth Function - Demo 00:01:00 Module 12: Foreach Function - Demo 00:04:00 Module 13: List Functions Theory - Part 3 00:05:00 Module 14: Assoc Function - Demo 00:04:00 Module 15: Subst Function - Demo 00:06:00 Module 16: Last Function - Demo 00:02:00 Module 17: Reverse Function - Demo 00:02:00 Unit 07: AutoLISP's User Input Functions Module 01: User Input Functions Theory - Part 1 00:05:00 Module 02: User Input Functions Theory - Part 2 00:04:00 Module 03: GetPoint Function - Demo 02:00:00 Module 04: GetInt Function - Demo 00:03:00 Module 05: GetString Function - Demo 00:04:00 Module 06: GetReal Function - Demo 00:02:00 Module 07: GetDist Function - Demo 00:04:00 Module 08: GetCorner Function - Demo 00:04:00 Module 09: GetAngle Function - Demo 00:10:00 Module 10: GetKword Function - Demo 00:05:00 Unit 08: Object Handling Functions Module 01: Object Handling Functions - Theory 00:04:00 Module 02: Entsel Function - Demo 00:03:00 Module 03: Entnext Function - Demo 00:03:00 Module 04: Entlast Function - Demo 00:02:00 Module 05: Entget Function - Demo 00:04:00 Module 06: Object Handling Functions - Exercises 00:02:00 Module 07: Object Handling Functions - Solutions to Exercises 00:06:00 Unit 09: AutoLISP's Selection Sets Module 01: Selection Sets - Theory 00:08:00 Module 02: Ssget Function - Demo 00:11:00 Module 03: Ssadd Function - Demo 00:05:00 Module 04: Ssdel Function - Demo 00:03:00 Module 05: Ssmemb Function - Demo 00:03:00 Module 06: Ssname Function - Demo 00:03:00 Module 07: Sslength Function - Demo 00:05:00 Module 08: Selection Sets - Exercises 00:04:00 Module 09: Selection Sets - Solutions to Exercises 00:13:00 Unit 10: Conditionals and Equality Functions Module 01: Using If and Progn Statements 00:05:00 Module 02: Using While and EQ Functions 00:05:00 Module 03: Using Cond and And Functions 00:04:00 Unit 11: AutoCAD Objects - Data Model Module 01: AutoCAD Objects: Re-examined (Part 1) 00:04:00 Module 02: AutoCAD Objects: Re-examined (Part 2) 00:05:00 Module 03: Line Object: Re-examined (Demo) 00:05:00 Module 04: Circle Object: Re-examined (Demo) 00:04:00 Module 05: Text Object: Re-examined (Demo) 00:08:00 Module 06: Dimension Object: Re-examined (Demo) 00:11:00 Module 07: Block/Attribute Object: Re-examined (Demo) 00:28:00 Unit 12: Symbol Table and Dictionary Handling Functions Module 01: Symbol Table and Dictionary-Handling Functions - Theory 00:05:00 Module 02: Tblsearch - Demo 00:13:00 Module 03: Tblnext - Demo 00:09:00 Unit 13: Hands-On Projects Module 01: CDIM - Project 00:12:00 Module 02: CHSTYLE - Project 00:16:00 Module 03: EXTATTR - Hands-On Project 00:26:00 Unit 14: Conclusion Module 01: Conclusion Message and Thank you! 00:01:00 Assignment Assignment - Complete AutoLISP Programming 00:00:00 Frequently Asked Questions Are there any prerequisites for taking the course? There are no specific prerequisites for this course, nor are there any formal entry requirements. All you need is an internet connection, a good understanding of English and a passion for learning for this course. Can I access the course at any time, or is there a set schedule? You have the flexibility to access the course at any time that suits your schedule. Our courses are self-paced, allowing you to study at your own pace and convenience. How long will I have access to the course? For this course, you will have access to the course materials for 1 year only. This means you can review the content as often as you like within the year, even after you've completed the course. However, if you buy Lifetime Access for the course, you will be able to access the course for a lifetime. Is there a certificate of completion provided after completing the course? Yes, upon successfully completing the course, you will receive a certificate of completion. This certificate can be a valuable addition to your professional portfolio and can be shared on your various social networks. Can I switch courses or get a refund if I'm not satisfied with the course? We want you to have a positive learning experience. If you're not satisfied with the course, you can request a course transfer or refund within 14 days of the initial purchase. How do I track my progress in the course? Our platform provides tracking tools and progress indicators for each course. You can monitor your progress, completed lessons, and assessments through your learner dashboard for the course. What if I have technical issues or difficulties with the course? If you encounter technical issues or content-related difficulties with the course, our support team is available to assist you. You can reach out to them for prompt resolution.

CO2 Sequestration and Enhanced Oil Recovery
By EnergyEdge - Training for a Sustainable Energy Future
Learn about CO2 sequestration and enhanced oil recovery in our EnergyEdge course. Gain valuable insights and practical knowledge. Enroll now.

A Practical Approach to Timeseries Forecasting Using Python
By Packt
Gain a thorough grasp of time series analysis and its effects, as well as practical tips on how to apply machine learning methods and build RNNs. Learn to train RNNs efficiently while taking crucial concepts such as overfitting and underfitting into account. The course offers a useful, hands-on manner for learning Python methods and principles.

Search By Location
- author Courses in London
- author Courses in Birmingham
- author Courses in Glasgow
- author Courses in Liverpool
- author Courses in Bristol
- author Courses in Manchester
- author Courses in Sheffield
- author Courses in Leeds
- author Courses in Edinburgh
- author Courses in Leicester
- author Courses in Coventry
- author Courses in Bradford
- author Courses in Cardiff
- author Courses in Belfast
- author Courses in Nottingham