- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
7883 Systems courses
IP security training course description Connection to the Internet is becoming an essential business tool. This course looks at firewalls, digital certificates, encryption and other essential topics for e-commerce sites. A generic course that looks at firewalls and VPNs. Hands on sessions include using hacking tools and configuring firewalls. What will you learn Describe: Basic security attacks RADIUS SSL IPSec VPNs Implement digital certificates Deploy firewalls to protect Web servers and users. Secure Web servers and clients. IP security training course details Who will benefit: Network administrators. Network operators. Security auditors Prerequisites: TCP/IP foundation for engineers Duration 2 days IP security training course contents TCP/IP review Brief overview of the relevant headers. Hands on Download software for course, use analyser to capture passwords on the wire. Security review Policies, Types of security breach, denial of service, data manipulation, data theft, data destruction, security checklists, incident response. Security exploits The Internet worm, IP spoofing, SYN attack, hijacking, Ping o' Death⦠keeping up to date with new threats. Hands on Use a port scanning tool, use a 'hacking' tool. Firewalls Products, Packet filtering, DMZ, content filtering, stateful packet inspection, Proxies, firewall architectures, Intrusion Detection Systems, Viruses. Hands on Set up a firewall and prevent attacks. NAT NAT and PAT, Why use NAT, NAT-ALG, RSIP. Encryption Encryption keys, Encryption strengths, Secret key vs Public key, algorithms, systems, SSL, SSH, Public Key Infrastructures. Hands on Run a password-cracking program. Authentication Types of authentication, Securid, Biometrics, PGP, Digital certificates, X.509 v3, Certificate authorities, CRLs, PPP authentication, RADIUS. Hands on Using certificates. Web client and server security Cookies, browser certificates, censorship, PICS. Operating system security, Web server user authentication, Restricting access, Logging, Securing CGI scripts. Hands on Browser security. VPNs and IPSec What is a VPN, tunnelling, L2F, PPTP, L2TP, IPSec, AH, ESP, transport mode, tunnel mode.

Artificial Lift and Real-Time Production Optimization in Digital Oilfield
By EnergyEdge - Training for a Sustainable Energy Future
About this training course Artificial lift systems are an important part of production operations for the entire lifecycle of an asset. Often, oil and gas wells require artificial lift for most of the life cycle. This 5-day training course offers a thorough treatment of artificial lift techniques including design and operation for production optimization. With the increasing need to optimize dynamic production in highly constrained cost environments, opportunities and issues related to real-time measurements and optimization techniques needs to be discussed and understood. Artificial lift selection and life cycle analysis are covered. These concepts are discussed and reinforced using case studies, quizzing tools, and exercises with software. Participants solve examples and class problems throughout the course. Animations and videos reinforce the concepts under discussion. Understanding of these important production concepts is a must have to exploit the existing assets profitably. Unique Features: Hands-on usage of SNAP Software to solve gas-lift exercises Discussion on digital oil field Machine learning applications in gas-lift optimization Training Objectives After the completion of this training course, participants will be able to: Understand the basics and advanced concepts of each form of artificial lift systems including application envelope, relative strengths, and weaknesses Easily recognize the different components from downhole to the surface and their basic structural and operational features Design and analyze different components using appropriate software tools Understand challenges facing artificial lift applications and the mitigation of these challenges during selection, design, and operation Learn about the role of digital oilfield tools and techniques and their applications in artificial lift and production optimization Learn about use cases of Machine learning and artificial intelligence in the artificial lift Target Audience This training course is suitable and will greatly benefit the following specific groups: Production, reservoir, completion, drilling and facilities engineers, analysts, and operators Anyone interested in learning about selection, design, analysis and optimum operation of artificial lift and related production systems will benefit from this course. Course Level Intermediate Advanced Training Methods The training instructor relies on a highly interactive training method to enhance the learning process. This method ensures that all participants gain a complete understanding of all the topics covered. The training environment is highly stimulating, challenging, and effective because the participants will learn by case studies which will allow them to apply the material taught in their own organization. Course Duration: 5 days in total (35 hours). Training Schedule 0830 - Registration 0900 - Start of training 1030 - Morning Break 1045 - Training recommences 1230 - Lunch Break 1330 - Training recommences 1515 - Evening break 1530 - Training recommences 1700 - End of Training The maximum number of participants allowed for this training course is 20. This course is also available through our Virtual Instructor Led Training (VILT) format. Prerequisites: Understanding of petroleum production concepts. Each participant needs a laptop/PC for solving class examples using software to be provided during class. Laptop/PC needs to have a current Windows operating system and at least 500 MB free disk space. Participants should have administrator rights to install software. Trainer Your expert course leader has over 35 years' work-experience in multiphase flow, artificial lift, real-time production optimization and software development/management. His current work is focused on a variety of use cases like failure prediction, virtual flow rate determination, wellhead integrity surveillance, corrosion, equipment maintenance, DTS/DAS interpretation. He has worked for national oil companies, majors, independents, and service providers globally. He has multiple patents and has delivered a multitude of industry presentations. Twice selected as an SPE distinguished lecturer, he also volunteers on SPE committees. He holds a Bachelor's and Master's in chemical engineering from the Gujarat University and IIT-Kanpur, India; and a Ph.D. in Petroleum Engineering from the University of Tulsa, USA. Highlighted Work Experience: At Weatherford, consulted with clients as well as directed teams on digital oilfield solutions including LOWIS - a solution that was underneath the production operations of Chevron and Occidental Petroleum across the globe. Worked with and consulted on equipment's like field controllers, VSDs, downhole permanent gauges, multiphase flow meters, fibre optics-based measurements. Shepherded an enterprise-class solution that is being deployed at a major oil and gas producer for production management including artificial lift optimization using real time data and deep-learning data analytics. Developed a workshop on digital oilfield approaches for production engineers. Patents: Principal inventor: 'Smarter Slug Flow Conditioning and Control' Co-inventor: 'Technique for Production Enhancement with Downhole Monitoring of Artificially Lifted Wells' Co-inventor: 'Wellbore real-time monitoring and analysis of fracture contribution' Worldwide Experience in Training / Seminar / Workshop Deliveries: Besides delivering several SPE webinars, ALRDC and SPE trainings globally, he has taught artificial lift at Texas Tech, Missouri S&T, Louisiana State, U of Southern California, and U of Houston. He has conducted seminars, bespoke trainings / workshops globally for practicing professionals: Companies: Basra Oil Company, ConocoPhillips, Chevron, EcoPetrol, Equinor, KOC, ONGC, LukOil, PDO, PDVSA, PEMEX, Petronas, Repsol, , Saudi Aramco, Shell, Sonatrech, QP, Tatneft, YPF, and others. Countries: USA, Algeria, Argentina, Bahrain, Brazil, Canada, China, Croatia, Congo, Ghana, India, Indonesia, Iraq, Kazakhstan, Kenya, Kuwait, Libya, Malaysia, Oman, Mexico, Norway, Qatar, Romania, Russia, Serbia, Saudi Arabia, S Korea, Tanzania, Thailand, Tunisia, Turkmenistan, UAE, Ukraine, Uzbekistan, Venezuela. Virtual training provided for PetroEdge, ALRDC, School of Mines, Repsol, UEP-Pakistan, and others since pandemic. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

The 'Linux Shell Scripting' course offers comprehensive training in shell scripting for Linux environments. From creating a local Linux shell scripting environment to network scripting and automation, learners will develop practical skills to automate tasks, process data, and improve efficiency using shell scripts. Learning Outcomes: Set up a local Linux shell scripting environment for practical learning. Create shell scripts for user and account management, including password generation and handling shell script arguments. Apply Linux programming conventions to maintain clear and efficient code. Develop shell scripts that parse command-line options for flexible user interaction. Utilize shell scripting for data processing, transformation, and reporting tasks. Automate network scripting and distributed systems for enhanced efficiency. Summarize the key concepts and techniques learned throughout the course. Access additional course extras and resources for further exploration and practice. Why buy this Linux Shell Scripting? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Linux Shell Scripting there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This Linux Shell Scripting course is ideal for Students Recent graduates Job Seekers Anyone interested in this topic People already working in the relevant fields and want to polish their knowledge and skill. Prerequisites This Linux Shell Scripting does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Linux Shell Scripting was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path As this course comes with multiple courses included as bonus, you will be able to pursue multiple occupations. This Linux Shell Scripting is a great way for you to gain multiple skills from the comfort of your home. Course Curriculum Unit 01: Course Introduction Introduction and Course Overview 00:02:00 Course Downloads 00:03:00 Unit 02: Creating a Local Linux Shell Scripting Environment Creating a Local Lab Environment Using Vagrant and VirtualBox - Background 00:16:00 Exercise 1 Instructions - Creating a Local Linux Shell Scripting Lab Environment 00:28:00 Exercise 1 - Walkthrough - Part I - Windows Users Only 00:04:00 Exercise 1 - Walkthrough - Part I - Mac Users Only 00:02:00 Exercise 1 - Walkthrough - Part I - Linux (CentOS/RHEL) Users Only 00:03:00 Exercise 1 - Walkthrough - Part II - All Users 00:23:00 Unit 03: User and Account Creation - Shell Scripting Project 1 Section Introduction 00:03:00 Getting Started with Shell Scripting: Naming, Permissions, Variables, Builtins. 00:35:00 Special Variables, Pseudocode, Command Substitution, if Statement, Conditionals. 00:23:00 Exit Statuses, Return Codes, String Test Conditionals, More Special Variables. 00:18:00 Reading Standard Input, Creating Accounts, Username Conventions, More Quoting. 00:23:00 Exercise 2 - Instructions 00:12:00 Exercise 2 - Walkthrough 00:21:00 Unit 04: Password Generation and Shell Script Arguments - Shell Scripting Project 2 Random Data, Cryptographic Hash Functions, Text and String Manipulation. 00:31:00 Positional Parameters, Arguments, for Loops, Special Parameters 00:30:00 The while Loop, Infinite Loops, Shifting, Sleeping 00:16:00 Exercise 3 - Instructions 00:12:00 Exercise 3 - Walkthrough 00:20:00 Unit 05: Linux Programming Conventions - Shell Scripting Project 3 Advanced Standard Input, Standard Output, and Standard Error - Part I 00:13:00 Advanced Standard Input, Standard Output, and Standard Error - Part II 00:26:00 Exercise 4 - Instructions 00:05:00 Exercise 4 - Walkthrough 00:12:00 Unit 06: Parsing Command Line Options - Shell Scripting Project 4 Case Statements 00:20:00 Functions 00:33:00 Parsing Command Line Options with getopts, Part 1 00:20:00 Parsing Command Line Options with getopts, Part 2 00:18:00 Deleting and Disabling Linux Accounts, Part 1 of 4 (Finding Files) 00:11:00 Deleting and Disabling Linux Accounts, Part 2 of 4 (The userdel command) 00:05:00 Deleting and Disabling Linux Accounts, Part 3 of 4 (Archives with tar) 00:14:00 Deleting and Disabling Linux Accounts, Part 4 of 4 (Disabling Accounts) 00:08:00 Deleting Users - Exercise 5 - Instructions 00:14:00 Deleting Users - Exercise 5 - Walkthrough 00:33:00 Unit 07: Transforming Data / Data Processing / Reporting - Shell Scripting Project 5 Cut and Awk 00:22:00 Cut and Awk Demonstration Script: Open Network Ports 00:10:00 Sort and Uniq 00:18:00 Parsing Log Files - Exercise 6 - Walkthrough 00:15:00 Sed 00:29:00 Unit 08: Network Scripting & Automation of Distributed Systems: Shell Scripting Project 6 Configuring a Mini Network and Scripting for Remote Systems 00:30:00 Scripting Remote Commands - Walkthrough - Part 1 00:26:00 Scripting Remote Commands - Exercise - Instructions 00:12:00 Scripting Remote Commands - Walkthrough - Part 2 00:13:00 Unit 09: Course Summary Summary 00:08:00 Unit 10: Course Extras What Shell Scripting Is and Why You Should Learn It 00:10:00 Resources Resources - Linux Shell Scripting 00:00:00 Assignment Assignment - Linux Shell Scripting 00:00:00

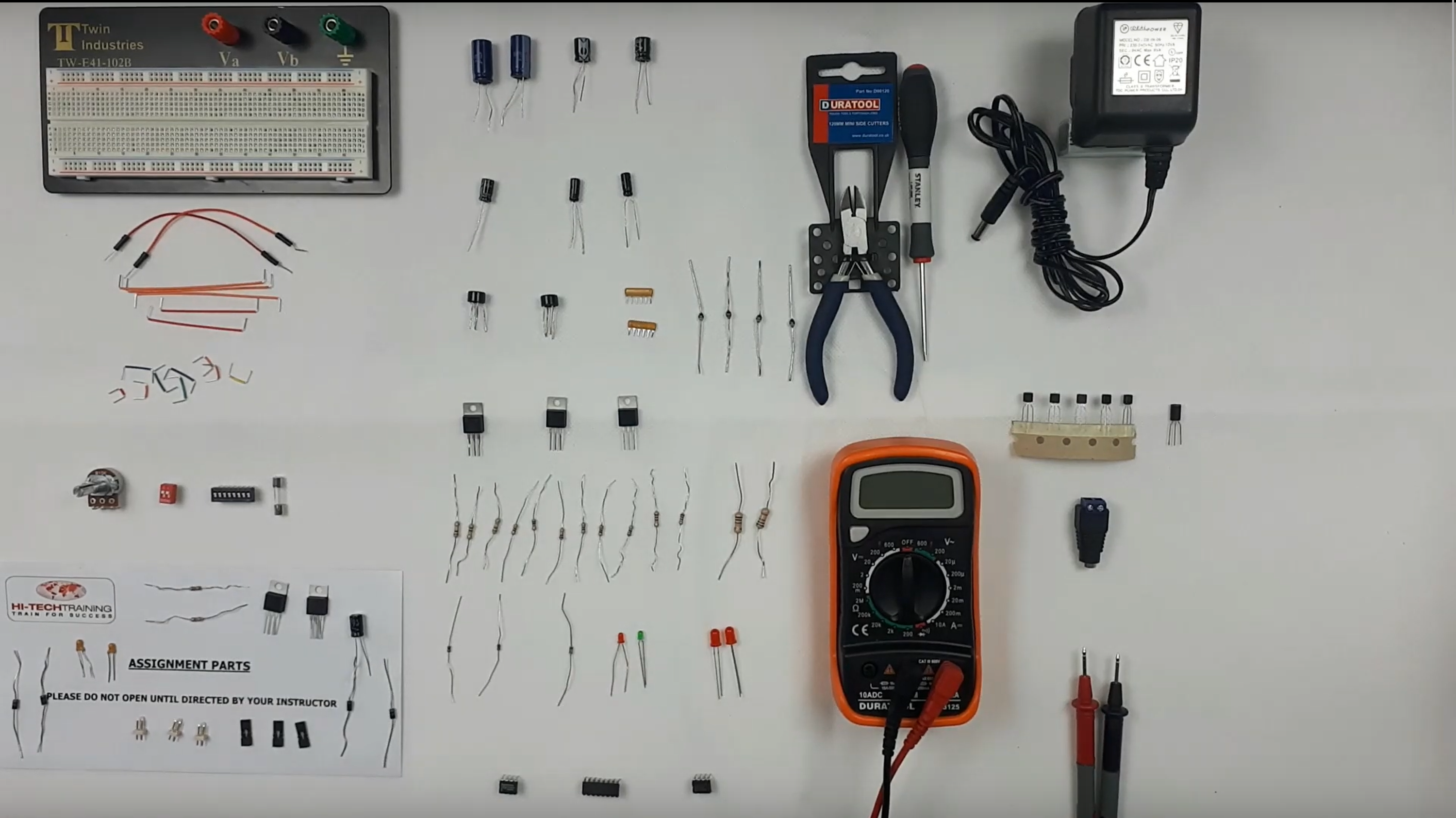
Electronics Repair 2 Course
By Hi-Tech Training
Electronics Equipment Repair 2 (Online Virtual Classroom) is a follow on course to Electronics Equipment Repair 1. This course builds on the skills gained and enables participants to build, test and fault-find more complex Analogue Electronic circuits
CertNexus Certified CyberSec First Responder (CFR-410)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed primarily for cybersecurity practitioners preparing for or who currently perform job functions related to protecting information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. It is ideal for those roles within federal contracting companies and private sector firms whose mission or strategic objectives require the execution of Defensive Cyber Operations (DCO) or DoD Information Network (DoDIN) operation and incident handling. This course focuses on the knowledge, ability, and skills necessary to provide for the defense of those information systems in a cybersecurity context, including protection, detection, analysis, investigation, and response processes. Overview In this course, you will identify, assess, respond to, and protect against security threats and operate a system and network security analysis platform. You will: Assess cybersecurity risks to the organization. Analyze the threat landscape. Analyze various reconnaissance threats to computing and network environments. Analyze various attacks on computing and network environments. Analyze various post-attack techniques. Assess the organization's security posture through auditing, vulnerability management, and penetration testing. Collect cybersecurity intelligence from various network-based and host-based sources. Analyze log data to reveal evidence of threats and incidents. Perform active asset and network analysis to detect incidents. Respond to cybersecurity incidents using containment, mitigation, and recovery tactics. Investigate cybersecurity incidents using forensic analysis techniques. This course covers network defense and incident response methods, tactics, and procedures that are in alignment with industry frameworks such as NIST 800-61r2 (Computer Security Incident Handling Guide), US-CERT's National Cyber Incident Response Plan (NCIRP), and Presidential Policy Directive (PPD)-41 on Cyber Incident Coordination. It is ideal for candidates who have been tasked with the responsibility of monitoring and detecting security incidents in information systems and networks, and for executing standardized responses to such incidents. The course introduces tools, tactics, and procedures to manage cybersecurity risks, defend cybersecurity assets, identify various types of common threats, evaluate the organization's security, collect and analyze cybersecurity intelligence, and remediate and report incidents as they occur. This course provides a comprehensive methodology for individuals responsible for defending the cybersecurity of their organization. This course is designed to assist students in preparing for the CertNexus CyberSec First Responder (Exam CFR-410) certification examination. What you learn and practice in this course can be a significant part of your preparation. In addition, this course and subsequent certification (CFR-410) meet all requirements for personnel requiring DoD directive 8570.01-M position certification baselines: CSSP Analyst CSSP Infrastructure Support CSSP Incident Responder CSSP Auditor The course and certification also meet all criteria for the following Cybersecurity Maturity Model Certification (CMMC) domains: Incident Response (IR) Audit and Accountability (AU) Risk Management (RM) Lesson 1: Assessing Cybersecurity Risk Topic A: Identify the Importance of Risk Management Topic B: Assess Risk Topic C: Mitigate Risk Topic D: Integrate Documentation into Risk Management Lesson 2: Analyzing the Threat Landscape Topic A: Classify Threats Topic B: Analyze Trends Affecting Security Posture Lesson 3: Analyzing Reconnaissance Threats to Computing and Network Environments Topic A: Implement Threat Modeling Topic B: Assess the Impact of Reconnaissance Topic C: Assess the Impact of Social Engineering Lesson 4: Analyzing Attacks on Computing and Network Environments Topic A: Assess the Impact of System Hacking Attacks Topic B: Assess the Impact of Web-Based Attacks Topic C: Assess the Impact of Malware Topic D: Assess the Impact of Hijacking and Impersonation Attacks Topic E: Assess the Impact of DoS Incidents Topic F: Assess the Impact of Threats to Mobile Security Topic G: Assess the Impact of Threats to Cloud Security Lesson 5: Analyzing Post-Attack Techniques Topic A: Assess Command and Control Techniques Topic B: Assess Persistence Techniques Topic C: Assess Lateral Movement and Pivoting Techniques Topic D: Assess Data Exfiltration Techniques Topic E: Assess Anti-Forensics Techniques Lesson 6: Assessing the Organization's Security Posture Topic A: Implement Cybersecurity Auditing Topic B: Implement a Vulnerability Management Plan Topic C: Assess Vulnerabilities Topic D: Conduct Penetration Testing Lesson 7: Collecting Cybersecurity Intelligence Topic A: Deploy a Security Intelligence Collection and Analysis Platform Topic B: Collect Data from Network-Based Intelligence Sources Topic C: Collect Data from Host-Based Intelligence Sources Lesson 8: Analyzing Log Data Topic A: Use Common Tools to Analyze Logs Topic B: Use SIEM Tools for Analysis Lesson 9: Performing Active Asset and Network Analysis Topic A: Analyze Incidents with Windows-Based Tools Topic B: Analyze Incidents with Linux-Based Tools Topic C: Analyze Indicators of Compromise Lesson 10: Responding to Cybersecurity Incidents Topic A: Deploy an Incident Handling and Response Architecture Topic B: Mitigate Incidents Topic C: Hand Over Incident Information to a Forensic Investigation Lesson 11: Investigating Cybersecurity Incidents Topic A: Apply a Forensic Investigation Plan Topic B: Securely Collect and Analyze Electronic Evidence Topic C: Follow Up on the Results of an Investigation Additional course details: Nexus Humans CertNexus Certified CyberSec First Responder (CFR-410) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CertNexus Certified CyberSec First Responder (CFR-410) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

55348 Administering Microsoft Endpoint Configuration Manager
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is for experienced information technology (IT) professionals, typically described as Enterprise Desktop Administrators (EDAs). These EDAs deploy, manage, and maintain PCs, devices, and applications across medium, large, and enterprise organizations. A significant portion of this audience uses, or intends to use, the latest release of Configuration Manager to manage and deploy PCs, devices, and applications. Overview Describe the features Configuration Manager and Intune include, and explain how you can use these features to manage PCs and mobile devices in an enterprise environment. Analyze data by using queries and reports. Prepare a management infrastructure, including configuring boundaries, boundary groups, and resource discovery, and integrating mobile-device management with Intune. Deploy and manage the Configuration Manager client. Configure, manage, and monitor hardware and software inventory, and use Asset Intelligence and software metering. Identify and configure the most appropriate method to distribute and manage content used for deployments. Distribute, deploy, and monitor applications for managed users and systems. Maintain software updates for PCs that Configuration Manager manages. Implement Endpoint Protection for managed PCs. Configure an operating-system deployment strategy by using Configuration Manager. Manage and maintain a Configuration Manager site. This five-day course describes how to use Configuration Manager and its associated site systems to efficiently manage network resources. In this five-day course, you will learn day-to-day management tasks, including how to manage applications, client health, hardware and software inventory, operating system deployment, and software updates by using Configuration Manager. You also will learn how to optimize Endpoint Protection, manage compliance, and create management queries and reports. Although this course and the associated labs are written for Microsoft Endpoint Configuration Manager and Windows 11, the skills taught will also be backwards compatible with previous editions of System Center Configuration Manager and Windows 10. Prerequisites Networking fundamentals, including common networking protocols, topologies, hardware, media, routing, switching, and addressing. Active Directory Domain Services (AD DS) principles and fundamentals of AD DS management. Installation, configuration, and troubleshooting for Windows-based personal computers. Basic concepts of public key infrastructure (PKI) security. Basic understanding of scripting and Windows PowerShell syntax. Basic understanding of Windows Server roles and services. Basic understanding of the configuration options for iOS and Android Mobile device platforms. 1 - Managing computers and mobile devices in the enterprise Overview of systems management by using enterprise management solutions Overview of the Configuration Manager architecture Overview of the Configuration Manager administrative tools Tools for monitoring and troubleshooting a Configuration Manager site 2 - Analyzing data using queries, reports, and CMPivot Introduction to queries Configuring SQL Server Reporting Services Analyzing the real-time state of a device by using CMPivot 3 - Preparing the Configuration Manager management infrastructure Configuring site boundaries and boundary groups Configuring resource discovery Organizing resources using device and user collections 4 - Deploying and managing the Configuration Manager client Overview of the Configuration Manager client Deploying the Configuration Manager client Configuring and monitoring client status Managing client settings and performing management operations 5 - Managing inventory for PCs and applications Overview of inventory collection Configuring hardware and software inventory Managing inventory collection Configuring software metering Configuring and managing Asset Intelligence 6 - Distributing and managing content used for deployments Preparing the infrastructure for content management Distributing and managing content on distribution points 7 - Deploying and managing applications Overview of application management Creating applications Deploying applications Managing applications Deploying and managing Windows apps 8 - Maintaining software updates for managed PCs The software updates process Preparing a Configuration Manager site for software updates Managing software updates Configuring automatic deployment rules Monitoring and troubleshooting software updates Enabling third-party updates 9 - Implementing Defender Protection for managed PCs Overview of Endpoint Protection in Configuration Manager Configuring, deploying, and monitoring Endpoint Protection policies Configuring and deploying advanced threat policies 10 - Managing compliance and secure data access Overview of Compliance Settings Configuring compliance settings Viewing compliance results Managing resource and data access 11 - Managing operating system deployment An overview of operating system deployment Preparing a site for operating system deployment Deploying an operating system Managing Windows as a service 12 - Managing and maintaining a Configuration Manager site Configuring role-based administration Configuring Remote Tools Overview of Configuration Manager site maintenance and Management Insights Backing up and recovering a Configuration Manager site Updating the Configuration Manager infrastructure 13 - What?s new in Microsoft Endpoint Configuration Manager Whats new in Microsoft Endpoint Manager covering each semi annual release Additional course details: Nexus Humans 55348: Administering Microsoft Endpoint Configuration Manager training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55348: Administering Microsoft Endpoint Configuration Manager course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

VMware training course description This five-day VMware course features intensive handson training that focuses on installing, configuring, and managing VMware vSphere 8, which includes VMware ESXi 8 and VMware vCenter 8. This course prepares you to administer a vSphere infrastructure for an organization of any size. This course is the foundation for most VMware technologies in the software-defined data center. What will you learn Install and configure ESXi hosts. Deploy and configure vCenter. Create virtual networks using standard and distributed switches. Configure VMs, templates, clones, and snapshots. Manage virtual machine resource allocation. Migrate virtual machines with vSphere vMotion and vSphere Storage vMotion. VMware training course details Who will benefit: Systems administrators and engineers. Prerequisites: Introduction to data communications & networking. Windows/Linux Administration. Duration 5 days VMware training course contents Course Introduction Introductions and course logistics. Course objectives vSphere and Virtualization Overview Explain basic virtualization concepts, Describe how vSphere fits in the software-defined data center and the cloud infrastructure, Recognize the user interfaces for accessing vSphere, Explain how vSphere interacts with CPUs, memory, networks, storage, and GPUs Installing and Configuring ESXi Install an ESXi host, Recognize ESXi user account best practices, Configure the ESXi host settings using the DCUI and VMware Host Client Deploying and Configuring vCenter Recognize ESXi hosts communication with vCenter, Deploy vCenter Server Appliance, Configure vCenter settings, Use the vSphere Client to add and manage license keys, Create and organize vCenter inventory objects, Recognize the rules for applying vCenter permissions, View vCenter logs and events Configuring vSphere Networking Configure and view standard switch configurations, Configure and view distributed switch configurations, Recognize the difference between standard switches and distributed switches, Explain how to set networking policies on standard and distributed switches Configuring vSphere Storage Recognize vSphere storage technologies, Identify types of vSphere datastores, Describe Fibre Channel components and addressing, Describe iSCSI components and addressing, Configure iSCSI storage on ESXi, Create and manage VMFS datastores, Configure and manage NFS datastores Deploying Virtual Machines Create and provision VMs, Explain the importance of VMware Tools, Identify the files that make up a VM Recognize the components of a VM, Navigate the vSphere, Client and examine VM settings and options, Modify VMs by dynamically increasing resources, Create VM templates and deploy VMs from them, Clone VMs, Create customization specifications for guest operating systems, Create local, published, and subscribed content libraries, Deploy VMs from content libraries, Manage multiple versions of VM templates in content libraries Managing Virtual Machines Recognize the types of VM migrations that you can perform within a vCenter instance and across vCenter instances, Migrate VMs using vSphere vMotion, Describe the role of Enhanced vMotion Compatibility in migrations, Migrate VMs using vSphere Storage vMotion, Take a snapshot of a VM, Manage, consolidate, and delete snapshots, Describe CPU and memory concepts in relation to a virtualized environment, Describe how VMs compete for resources Define CPU and memory shares, reservations, and limits Deploying and Configuring vSphere Clusters Create a vSphere cluster enabled for vSphere DRS and vSphere HA, View information about a vSphere cluster Explain how vSphere DRS determines VM placement on hosts in the cluster, Recognize use cases for vSphere DRS settings, Monitor a vSphere DRS cluster Describe how vSphere HA responds to various types of failures, Identify options for configuring network redundancy in a vSphere HA cluster, Recognize vSphere HA design considerations, Recognize the use cases for various vSphere HA settings, Configure a vSphere HA cluster, Recognize when to use vSphere Fault Tolerance Managing the vSphere Lifecycle Enable vSphere Lifecycle Manager in a vSphere cluster, Describe features of the vCenter Update Planner, Run vCenter upgrade prechecks and interoperability reports, Recognize features of vSphere Lifecycle Manager, Distinguish between managing hosts using baselines and managing hosts using images, Describe how to update hosts using baselines, Describe ESXi images, Validate ESXi host compliance against a cluster image and update ESXi hosts, Update ESXi hosts using vSphere Lifecycle Manager, Describe vSphere Lifecycle Manager automatic recommendations, Use vSphere Lifecycle Manager to upgrade VMware Tools and VM hardware

Is your gas inspection due soon? We offer training packages that are designed to build your confidence in preparation for your gas inspection Please bare in mind that this training is not a guarantee that you will pass your inspection.

CompTIA PenTest+ (PenTest)
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for IT professionals who want to develop penetration testing skills to enable them to identify information-system vulnerabilities and effective remediation techniques for those vulnerabilities. Target students who also need to offer practical recommendations for action to properly protect information systems and their contents will derive those skills from this course. This course is also designed for individuals who are preparing to take the CompTIA PenTest+ certification exam PT0-002, or who plan to use PenTest+ as the foundation for more advanced security certifications or career roles. Individuals seeking this certification should have three to four years of hands-on experience performing penetration tests, vulnerability assessments, and vulnerability management. Overview After completing this course, you will be able to plan, conduct, analyze, and report on penetration tests, including the ability to: Plan and scope penetration tests. Conduct passive reconnaissance. Perform non-technical tests to gather information. Conductive active reconnaissance. Analyze vulnerabilities. Penetrate networks. Exploit host-based vulnerabilities. Test applications. Complete post-exploit tasks. Analyze and report pen test results. Security remains one of the hottest topics in IT and other industries. It seems that each week brings news of some new breach of privacy or security. As organizations scramble to protect themselves and their customers, the ability to conduct penetration testing is an emerging skill set that is becoming ever more valuable to the organizations seeking protection, and ever more lucrative for those who possess these skills. In this course, you will be introduced to some general concepts and methodologies related to pen testing, and you will work your way through a simulated pen test for a fictitious company. 1 - Outline Lesson 1: Scoping Organization/Customer Requirements Lesson 2: Defining the Rules of Engagement Lesson 3: Footprinting and Gathering Intelligence Lesson 4: Evaluating Human and Physical Vulnerabilities Lesson 5: Preparing the Vulnerability Scan Lesson 6: Scanning Logical Vulnerabilities Lesson 7: Analyzing Scanning Results Lesson 8: Avoiding Detection and Covering Tracks Lesson 9: Exploiting the LAN and Cloud Lesson 10: Testing Wireless Networks Lesson 11: Targeting Mobile Devices Lesson 12: Attacking Specialized Systems Lesson 13: Web Application-Based Attacks Lesson 14: Performing System Hacking Lesson 15: Scripting and Software Development Lesson 16: Leveraging the Attack: Pivot and Penetrate Lesson 17: Communicating During the PenTesting Process Lesson 18: Summarizing Report Components Lesson 19: Recommending Remediation Lesson 20: Performing Post-Report Delivery Activities Additional course details: Nexus Humans CompTIA Penetration Testing Certification (PenTest Plus) - (Exam PT0-002) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CompTIA Penetration Testing Certification (PenTest Plus) - (Exam PT0-002) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Search By Location
- Systems Courses in London
- Systems Courses in Birmingham
- Systems Courses in Glasgow
- Systems Courses in Liverpool
- Systems Courses in Bristol
- Systems Courses in Manchester
- Systems Courses in Sheffield
- Systems Courses in Leeds
- Systems Courses in Edinburgh
- Systems Courses in Leicester
- Systems Courses in Coventry
- Systems Courses in Bradford
- Systems Courses in Cardiff
- Systems Courses in Belfast
- Systems Courses in Nottingham