- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
6152 Software courses
Python Data Science - QLS Machine Learning
By Kingston Open College
QLS Endorsed + CPD QS Accredited - Dual Certification | Instant Access | 24/7 Tutor Support | All-Inclusive Cost

Advanced Game Design Course- 2D & 3D
By iStudy UK
Game Development is the creation of video games which is done by game developers. A game developer can be one person or a large company. To become a game developer, you need to learn the skills and knowledge about video games and how to make one. Many of game developers chose to become one because they are gamers themselves. To become a game development expert, you need to learn both the basics skills and special skills of game development. This course will help you to master the right skills to become successful in the growing game development industry. Course Highlights Advanced Game Design Course- 2D & 3D is an award winning and the best selling course that has been given the CPD Certification & IAO accreditation. It is the most suitable course anyone looking to work in this or relevant sector. It is considered one of the perfect courses in the UK that can help students/learners to get familiar with the topic and gain necessary skills to perform well in this field. We have packed Advanced Game Design Course- 2D & 3D into 26 modules for teaching you everything you need to become successful in this profession. To provide you ease of access, this course is designed for both part-time and full-time students. You can become accredited in just 18 hours hours and it is also possible to study at your own pace. We have experienced tutors who will help you throughout the comprehensive syllabus of this course and answer all your queries through email. For further clarification, you will be able to recognize your qualification by checking the validity from our dedicated website. Why You Should Choose Advanced Game Design Course- 2D & 3D Lifetime access to the course No hidden fees or exam charges CPD Accredited certification on successful completion Full Tutor support on weekdays (Monday - Friday) Efficient exam system, assessment and instant results Download Printable PDF certificate immediately after completion Obtain the original print copy of your certificate, dispatch the next working day for as little as £9. Improve your chance of gaining professional skills and better earning potential. Who is this Course for? Advanced Game Design Course- 2D & 3D is CPD certified and IAO accredited. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic backgrounds. Requirements Our Advanced Game Design Course- 2D & 3D is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path You will be ready to enter the relevant job market after completing this course. You will be able to gain necessary knowledge and skills required to succeed in this sector. All our Diplomas' are CPD and IAO accredited so you will be able to stand out in the crowd by adding our qualifications to your CV and Resume. Gaming Basics Introduction 01:00:00 Understanding Consoles 01:00:00 Using Your Computer 01:00:00 Using Your Phone 01:00:00 Using the Internet 00:30:00 Where to Find Free Software 01:00:00 Understanding Accessories Dealing with Drugs 00:30:00 Wrapping Up 00:15:00 Developing Games Introduction To Game Creation 01:00:00 Essential Tools 01:00:00 2D Game Creation Software 01:00:00 3D Game Creation Software 01:00:00 3D Game Creation 00:30:00 Game Modification 01:00:00 How To Create a Game on a Social Site 00:30:00 Testing Games Introduction to Game Testing FREE 01:00:00 Two Rules of Game Testing FREE 01:00:00 How to Put a Resume Together 01:00:00 How give Examples During Job Interview 00:30:00 Contacting Game Developers 01:00:00 Use the Correct Search Keywords 01:00:00 Wrapping Up 00:15:00 Additional Study Material 2D Game 00:00:00 Game Development XNA GameStudio 00:00:00 Game QA & Testing 00:00:00 Become A Game Tester 00:00:00 Mock Exam Final Exam

Netgear switches training course description A hands on course covering the product specifics of Netgear switches. Installation, configuration, maintenance and troubleshooting are all covered in a practical oriented way. What will you learn Install Netgear switches. Use the command line interface and the web based interface to manage Netgear switches. Configure and troubleshoot Netgear switches. Perform software upgrades. Netgear switches training course details Who will benefit: Anyone working with Netgear switches. Particularly aimed at engineers and technicians supporting Netgear switches. Prerequisites: None. Duration 2 days Netgear switches training course content Introduction How Ethernet works with hubs, How Ethernet works with switches. Installing Netgear switches. Hands on Building a network with a hub, building a network with a Netgear switch. Basic troubleshooting The Netgear switch range, LEDs, cabling issues, factory resets, default settings. Hands on Building a network with multiple Netgear switches. Configuration methods Managed vs. unmanaged switches, Console port access, telnet, web based access, SNMP, saving configurations, NVRAM, switch stacks, stacking ports. Hands on Accessing the switch using the console, IP address configuration, telnet. Console interface Password protection, the menus, menu options. Hands on Setting a password, displaying the switch configuration. Web based interface Getting started, basic format. Hands on Configuring the switch using the web interface. Port configuration Common port configuration tasks, port trunking. Hands on Configuring ports. STP configuration What is STP? Configuring STP. Hands on Enabling and disabling STP, configuring STP VLAN configuration What are VLANS? 802.1Q, tagged/untagged, creating VLANS, applying VLANS. Hands on Setting up VLANS, setting up 802.1Q, Inter VLAN traffic. Housekeeping TFTP, upgrades Hands on Boot from net. SNMP SNMP configuration, NMS's. Hands on Using SNMP to manage a Netgear switch, putting it all together: troubleshooting.

Vectorworks 2d | 3d and Spotlight training
By London Design Training Courses
Why Learn Vectorworks 2d | 3d and Spotlight training Course? Course info Led by experts, this comprehensive program equips you with skills in 2D drafting, immersive 3D modeling, and dynamic lighting design. Master Vectorworks' powerful features, including the Spotlight module tailored for entertainment and events. Duration: 16 hrs Method: 1-on-1, Personalized attention. Schedule: Tailor your own hours, available from Mon to Sat between 9 am and 7 pm. Or Call 02077202581 or WhatsApp 07970325184. Course Details: Format: 1-on-1 Training Schedule: Flexible, Any Day, Anytime (Monday to Saturday), 9 AM to 7 PM Duration: Customizable to Individual Learning Pace Content: Comprehensive training in Vectorworks, focusing on 2D Drafting, Immersive 3D Modeling, and Dynamic Lighting Design. Specialization: Spotlight Module for Entertainment and Events Instructors: Expert-led sessions ensuring personalized attention and effective learning. Outcome: Mastery of Vectorworks' Powerful Features, Proficiency in 2D and 3D Design, and Expertise in Dynamic Lighting Design for Entertainment Purposes. Note: Schedule and course duration are flexible to accommodate individual preferences and learning needs. Course Details: Format: 1-on-1 Training Schedule: Flexible, Any Day, Anytime (Monday to Saturday), 9 AM to 7 PM Duration: Customizable to Individual Learning Pace Content: Comprehensive training in Vectorworks, focusing on 2D Drafting, Immersive 3D Modeling, and Dynamic Lighting Design. Specialization: Spotlight Module for Entertainment and Events Instructors: Expert-led sessions ensuring personalized attention and effective learning. Outcome: Mastery of Vectorworks' Powerful Features, Proficiency in 2D and 3D Design, and Expertise in Dynamic Lighting Design for Entertainment Purposes. Note: Schedule and course duration are flexible to accommodate individual preferences and learning needs. Vectorworks 2D | 3D and Spotlight Training Course Course Duration: 16 hours Course Description: I. Introduction to Vectorworks (1 hour) Overview of Vectorworks software and its applications Familiarization with the user interface and navigation Customizing preferences and settings for optimal workflow II. 2D Drawing Tools (2 hours) Using basic drawing tools for creating lines, rectangles, circles, and polygons Utilizing text and dimension tools for annotations Applying modify tools for editing and transforming objects Organizing elements with layers and classes III. 3D Modeling Tools (3 hours) Introduction to extrude, revolve, sweep, and loft tools for 3D modeling Creating 3D objects from 2D shapes for spatial representation Modifying and refining 3D models Exploring the 3D modeling environment IV. Advanced 3D Modeling Tools (2 hours) Utilizing solid modeling tools for complex geometry creation Performing Boolean operations to combine or subtract shapes Creating and utilizing symbols for efficient workflow V. Introduction to Spotlight (1 hour) Overview of the Spotlight workspace and its features Adding and configuring lighting devices for stage and event design Creating and modifying lighting positions for accurate placement VI. Spotlight Tools and Techniques (3 hours) Creating and editing lighting instruments for customized setups Using visualization tools for lighting simulations Creating and applying labels and legends for documentation Generating worksheets and reports for lighting analysis VII. Advanced Spotlight Techniques (2 hours) Utilizing video and projection tools for multimedia presentations Incorporating audio and sound systems for immersive experiences Understanding rigging and hoisting for stage setup Managing paperwork and documentation for effective planning VIII. Integration with Other Software (1 hour) Importing and exporting files to collaborate with other software Utilizing Vectorworks in CAD and BIM workflows for interoperability Exploring plugins and add-ons for expanded functionality IX. Project-based Exercises (1 hour) Applying learned techniques to real-world scenarios Creating a lighting plan for a concert or theater production Designing a 3D model of a building or interior space Free 30-day, BIM & CAD Software Trial Request | Vectorworks https://www.vectorworks.net/trial Vectorworks Trial Version Request. Please fill out the following form. We will provide you with an evaluation serial number to activate your trial copy. Learning Outcomes of Vectorworks 2D | 3D and Spotlight Training Course: Master Vectorworks with 2D and 3D design skills. Create precise 2D drawings and detailed 3D models. Learn specialized tools for lighting and event planning in Spotlight. Optimize workflows and improve project coordination. Produce realistic renderings and visualizations. Apply skills to real-world projects in architecture and events.

Start Your Journey to Becoming a coder Today, and Make Up to •100,000 yearly The Future is Coding. The world is changing. The way we work is changing. And the skills we need to succeed are changing. In the future, coding will be essential. Whether you want to work in tech, business, or any other field, coding skills will give you a competitive edge. That's why we created the Coding Training - Career Mentoring & Support with Job Opportunity program. This program will teach you the skills you need to become a successful software developer. But it's not just about the coding. We also offer career mentoring and support. We'll help you develop your career goals, build your CV, and land your dream job. So what are you waiting for? The future is coding. And the future starts with us. Enrol Today! Our mission is simple: to be your trusted partner and assist you every step of the way until you land the job of your dreams. Why Choose Us Here's what makes our Coding Training Program stand out from the crowd: Personalised Job Search Assistance: We're in this together! Our dedicated team will work tirelessly to support your entire job searching process. From crafting a standout resume to submitting it to top companies, we'll ensure you have a compelling application that gets noticed. Expertly Crafted CV: Your resume is your ticket to the interview room. Our professional resume writers will create a customised CV highlighting your unique skills and experiences. This will maximise your chances of standing out among the competition. Strategic Placement: We understand the power of casting a wide net. We'll strategically submit your CV to various platforms and networks, expanding your reach and connecting you with valuable opportunities that align with your career goals. One-On-One Consultation Sessions with Industry Experts: Gain invaluable insights and guidance from seasoned professionals who have thrived in the Coding field. Our consultation sessions provide you with insider tips, tricks, and advice, empowering you to navigate the industry with confidence and finesse. Comprehensive Skill Development: Our program is designed to equip you with the most sought-after skills in the coding sector. From mastering cutting-edge tools to honing your coding prowess, we'll ensure you have the knowledge and expertise to excel in any coding-driven environment. Ongoing Support: We understand that the journey to landing your dream job doesn't end with placement. That's why our commitment to your success extends well beyond your initial training. Our support team will be available to answer your questions, provide guidance, and assist you as you progress in your career. Here are the 6 courses we will provide once you enrol in the program: Course 01: Python 3 Programming Course 02: Coding with Scratch Course 03: Basic C# Coding Course 04: C++ Coding Masterclass Course 05: Introduction to Data Analysis Course 06: HTML and CSS Coding for Beginners and Kids These courses will help you to develop your knowledge and skills to become a successful coder. The Program is completed in 5 easy steps: Step 1 - Enrol in the program and start learning from the courses we provide After you enrol in this Coding Training Program, you will get lifetime access to 6 premium courses related to coding. These courses will teach you the knowledge and skills required to become a successful coding expert. Our customer service team will help you and keep in contact with you every step of the way. Step 2 - Complete your courses and get certifications After learning from the courses, you must obtain certificates for each course. There will be exams for every course, and you have to pass them to get your certificate. To pass successfully, you must get 90% marks for the first course and 80% for the rest relevant courses. Once you pass the exams, you will receive hardcopy certificates. These certificates will prove that you're an expert in the subject. Step 3 - Get a consultation session from a professional coder Take your coding skills to new heights with a one-on-one consultation session led by a seasoned professional. Gain invaluable insights, expert tips, and tailored advice that will propel your career forward. Step 4 - Complete the CV and attend the interview Once you've successfully obtained the certifications, our team of professionals will build you a compelling CV and LinkedIn profile. With these powerful tools in hand, you'll be fully prepared to tackle job interviews confidently. Kickstart your coding career with a starting salary ranging from •30,000 to •50,000 annually. Step into the coding industry with the assurance of a promising future. Step 5 - We will not leave you until you find a job Our commitment to your success goes above and beyond. We won't stop until you land that dream job. With personalised support, expert guidance, and unwavering dedication, we'll be by your side until you secure the perfect opportunity. Your job search becomes our mission, ensuring you have the best chance at a successful career in coding. Don't let your dream career as a coder remain out of reach. You just have to learn and gain knowledge and skills. Finding a job is our task! We will remove most of your worries and help you focus on only developing your skills. So join our Coding Training Program today, and let us be your trusted partner on your journey to success. CPD 100 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This Coding Training program is ideal for the following: Aspiring Coders: Individuals who have a passion for coding and are eager to embark on a career in the tech industry. Career Changers: Professionals from diverse backgrounds looking to transition into the world of coding and explore new opportunities. Recent Graduates: Graduates who want to enhance their job prospects and develop in-demand coding skills to kick-start their careers. Job Seekers: Individuals actively searching for employment in the tech sector and seeking the necessary training and support to secure a job. Tech Enthusiasts: Individuals with a strong interest in technology who want to expand their knowledge and skills in coding for personal or professional growth. NCFE LEVEL 3 CERTIFICATE IN CODING PRACTICES Requirements No experience required. Just enrol & start learning. Career path Our program paves the way for a successful career in coding. From beginner to professional, you'll gain essential skills, receive personalised mentoring, build a standout CV, and access exclusive job opportunities. Let us guide you towards a fulfilling and lucrative path in the ever-expanding tech industry. Certificates CPD Accredited e-Certificate Digital certificate - Included CPD Accredited Framed (Hardcopy) Certificate Hard copy certificate - Included Enrolment Letter Digital certificate - Included Student ID Card Digital certificate - Included

Game Development Course is suitable for anyone aspiring to or already working in this field or simply want to learn deeper into game Development Course. You will be able to add this qualification to your CV by downloading your certificate instantly without any cost. To make this course more accessible for you, we have designed it for both part-time and full-time students. This course is packed into bite-size module for your convenience. You can study at your own pace or become accredited within hours! If you require support, our experienced tutors are always available to help you throughout the comprehensive syllabus of this course and answer all your queries through email. Do you want to become a Gaming Developer? Producing a game that will make people spend money on claims skills and a lot of hard work. Become a Gaming Developer with our most recommended Game Development Course by going through step by step tutorials, and develop a game. This course will provide you with an initiation to game creation, and explains you the crucial tools. Learn the basics of designing a game and grasp about complex 2D & 3D game creation software available in the market. This course will be ideal to help you in discovering how to develop your games and become a professional developer. Who is the course for? Game makers or developers who want to improve their game development skills. People who have an interest in game development and software. Entry Requirement: This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £9 and the hard copy for £15. Also, you can order both PDF and hardcopy certificates for £22. Career path This course opens a new door for you to enter the relevant job market and also gives you the opportunity to acquire extensive knowledge along with required skills to become successful. You will be able to add our qualification to your CV/resume which will help you to stand out in the competitive job industry. Course Curriculum Game Development Course - Updated Version Introduction to game logo design The first question to ask 00:02:00 My game logo design process 00:03:00 The importance of sketching 00:03:00 Basic logos Simple racing game logo design 00:12:00 Simple horror game logo design 00:17:00 Simple logo for a puzzle game 00:18:00 Complex logo designs Cute cartoon game logo design - Part 1 00:14:00 Cute cartoon game logo design - Part 2 00:18:00 Design a sci-fi logo using negative space - Part 1 00:08:00 Design a sci-fi logo using negative space - Part 2 00:16:00 Cartoon fantasy RPG game logo design -Part 1 00:15:00 Cartoon fantasy RPG game logo design -Part 2 00:14:00 Grunge zombie shooter game logo design - Part 1 00:11:00 Grunge zombie shooter game logo design - Part 2 00:19:00 Game Development Course - Old Version Introduction To Game Creation 00:30:00 Essential Tools 01:00:00 Basics of Game Design 01:00:00 2D Game Creation Software 01:00:00 3D Game Creation Software 01:00:00 3D Game Creation 00:30:00 Game Modification 01:00:00 How To Create a Game on a Social Site 00:30:00 Wrapping Up 00:15:00 Additional Supporting Materials 2D Game 00:00:00 Game Development XNA GameStudio 00:00:00 Mock Exam Mock Exam-Game Development Course 00:20:00 Final Exam Final Exam-Game Development Course 00:20:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

Real-World DevOps Project From Start to Finish
By Packt
Embark on a transformative DevOps journey! This comprehensive course equips you with skills in Ansible, Docker, GitLab, backups, and more. Master the art of self-hosting your infrastructure, streamlining deployments, and boosting efficiency. Launch your DevOps career today and unleash the endless possibilities!

Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu
By Course Cloud
Course Overview Learn how to Install and configure NGINX on Ubuntu step-by-step. Includes MySQL, PHP, PhpMyAdmin, WordPress & SSL integration. NGINX is one of the most powerful Web Server technologies in the world. In this course, you will learn how to install NGINX on a DigitalOcean droplet or any virtual server of your choice, with complete step-by-step guidance. It also covers key topics such as the differences between Apache & NGINX, configuring DNS one files, and creating a database for WordPress. This practical training course is a great introduction to NGINX and other open source software, ideal for students interested in web development and web design. There are no specific entry requirements for this course, which can be studied on a part-time or full-time basis. This best selling Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu has been developed by industry professionals and has already been completed by hundreds of satisfied students. This in-depth Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu is suitable for anyone who wants to build their professional skill set and improve their expert knowledge. The Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu is CPD-accredited, so you can be confident you're completing a quality training course will boost your CV and enhance your career potential. The Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu is made up of several information-packed modules which break down each topic into bite-sized chunks to ensure you understand and retain everything you learn. After successfully completing the Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu, you will be awarded a certificate of completion as proof of your new skills. If you are looking to pursue a new career and want to build your professional skills to excel in your chosen field, the certificate of completion from the Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu will help you stand out from the crowd. You can also validate your certification on our website. We know that you are busy and that time is precious, so we have designed the Install NGINX, PHP, MySQL, SSL & WordPress on Ubuntu to be completed at your own pace, whether that's part-time or full-time. Get full course access upon registration and access the course materials from anywhere in the world, at any time, from any internet-enabled device. Our experienced tutors are here to support you through the entire learning process and answer any queries you may have via email.

Modern PHP Web Development with MySQL, GitHub and Heroku
By Packt
This course covers all the essential topics of PHP web development, such as syntaxes, loops, conditional statements, Bootstrap, GitHub, Heroku, XAMPP, and MySQL that every PHP developer needs to know. You will learn all these concepts by building and deploying a data-driven web application into the production.

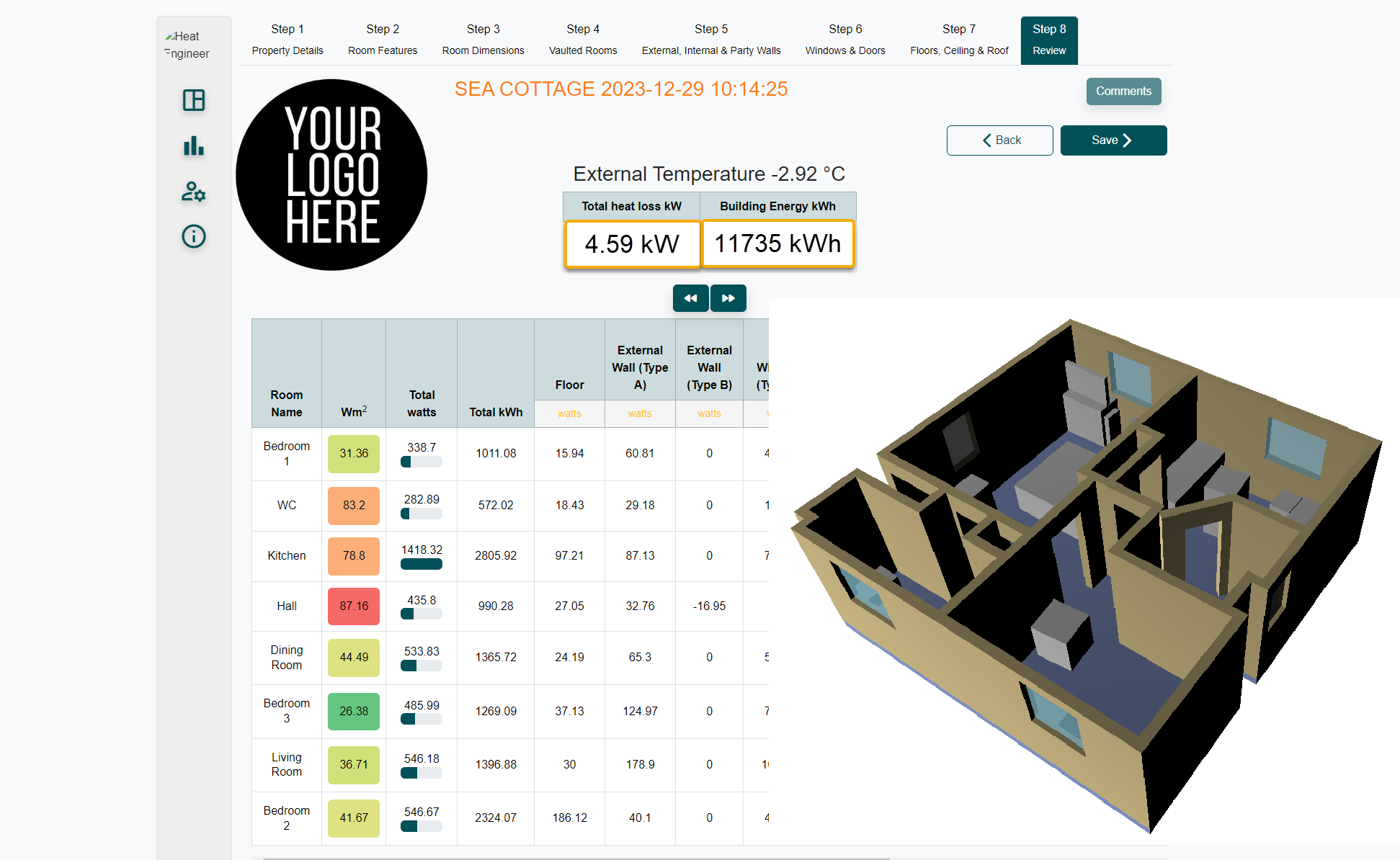
This is designed to be an introduction into how to start a room by room survey using the new CAD Heat Engineer feature, using the online dashboard. We will then go through the different steps to complete this heat loss report. Optional pages will also be worked through and shown. Examples of how to select the flow temperature and the heat source (heat pumps and boilers) will be presented once the heat loss result is completed.
Search By Location
- Software Courses in London
- Software Courses in Birmingham
- Software Courses in Glasgow
- Software Courses in Liverpool
- Software Courses in Bristol
- Software Courses in Manchester
- Software Courses in Sheffield
- Software Courses in Leeds
- Software Courses in Edinburgh
- Software Courses in Leicester
- Software Courses in Coventry
- Software Courses in Bradford
- Software Courses in Cardiff
- Software Courses in Belfast
- Software Courses in Nottingham