- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
Overview Objective Understand the requirement of Information Security Concepts and Definitions of Information Security Management Systems Deeply Analysing the policies, Standards and procedures How to deliver a balanced ISMS and following its security procedures Analysing the Information risk management Evaluating the organisational responsibilities Understanding the Information security controls Scrutinising Legal framework Techniques of Cryptographic models

Cyber Secure Coder
By Mpi Learning - Professional Learning And Development Provider
This course presents an approach for dealing with security and privacy throughout the entire software development lifecycle. You will learn about vulnerabilities that undermine security, and how to identify and remediate them in your own projects.

Penetration testing training course description An advanced technical hands on course focusing on hacking and counter hacking. The course revolves around a series of exercises based on "hacking" into a network (pen testing the network) and then defending against the hacks. What will you learn Perform penetration tests. Explain the technical workings of various penetration tests. Produce reports on results of penetration tests. Defend against hackers. Penetration testing training course details Who will benefit: Technical support staff, auditors and security professionals. Staff who are responsible for network infrastructure integrity. Prerequisites: IP Security IP VPNs Duration 5 days Penetration testing training course contents Introduction Hacking concepts, phases, types of attacks, 'White hacking', What is penetration testing? Why use pen testing, black box vs. white box testing, equipment and tools, security lifecycles, counter hacking, pen testing reports, methodologies, legal issues. Physical security and social engineering Testing access controls, perimeter reviews, location reviews, alarm response testing. Request testing, guided suggestions, trust testing. Social engineering concepts, techniques, counter measures, Identity theft, Impersonation on social media, Footprints through social engineering Reconnaissance (discovery) Footprinting methodologies, concepts, threats and countermeasures, WHOIS footprinting, Gaining contacts and addresses, DNS queries, NIC queries, ICMP ping sweeping, system and server trails from the target network, information leaks, competitive intelligence. Scanning pen testing. Gaining access Getting past passwords, password grinding, spoofed tokens, replays, remaining anonymous. Scanning (enumeration) Gaining OS info, platform info, open port info, application info. Routes used, proxies, firewalking, Port scanning, stealth port scanning, vulnerability scanning, FIN scanning, Xmas tree scanning, Null scanning, spoofed scanning, Scanning beyond IDS. Enumeration concepts, counter measures and enumeration pen testing. Hacking Hacking webservers, web applications, Wireless networks and mobile platforms. Concepts, threats, methodology, hacking tools and countermeasures. Trojan, Backdoors, Sniffers, Viruses and Worms Detection, concepts, countermeasures, Pen testing Trojans, backdoors, sniffers and viruses. MAC attacks, DHCP attacks, ARP poisoning, DNS poisoning Anti-Trojan software, Malware analysis Sniffing tools. Exploiting (testing) vulnerabilities Buffer overflows,, simple exploits, brute force methods, UNIX based, Windows based, specific application vulnerabilities. DoS/DDoS Concepts, techniques, attack tools, Botnet, countermeasures, protection tools, DoS attack pen testing. SQL Injection Types and testing, Blind SQL Injection, Injection tools, evasion and countermeasures. Securing networks 'Hurdles', firewalls, DMZ, stopping port scans, IDS, Honeypots, Router testing, firewall testing, IDS testing, Buffer Overflow. Cryptography PKI, Encryption algorithms, tools, Email and Disk Encryption. Information security Document grinding, privacy.

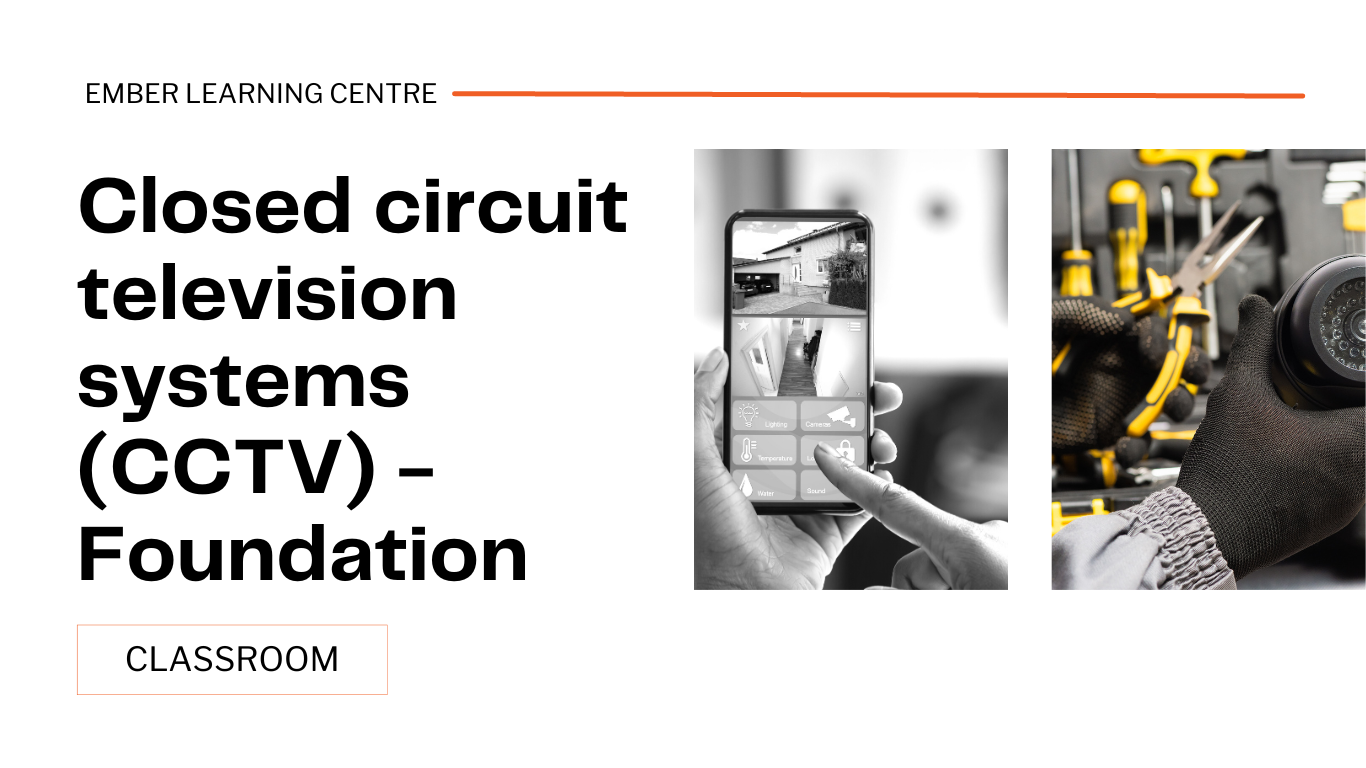
This course provides the basic requirements for auditing I&HAS to PD 6662, EN 50131, BS 8243, and access control / CCTV systems to certification bodies' standards. The course enables certified contractors to conduct objective auditing of their own systems.

Kerberos for engineers training course description This hands on course covers the details of Kerberos, from installation and administration through to how it all works including the protocols. What will you learn Describe what Kerberos is. Explain how Kerberos works. Install Kerberos. Configure Kerberos. Troubleshoot Kerberos. Kerberos for engineers training course details Who will benefit: Engineers interested in security. Prerequisites: TCP/IP foundation for engineers Duration 2 days Kerberos for engineers training course contents What is Kerberos? Single Sign On, The protocol, the standard, history, v4, v5, RFCs, Linux, Windows. Kerberos concepts and technology AAA, Authentication, Authorization, Accounting. Kerberos vs LDAP and directories. Privacy, integrity. Kerberos realms, principles, instances. Keys, salts, passwords. Key Distribution Centre, Authentication server, ticket granting server. Tickets. Installation and administration of Kerberos Installing Kerberos, creating realms, testing. DNS and Kerberos, Kerberos clients. Hands on Windows and Linux Kerberos. Kerberos protocols The Needham-Schroeder protocol, Kerberos v4. Authentication server, ticket granting server, Kerberos v5, encryption options, ticket options, other protocol features and extensions. Related protocols: GSSAPI, SPNEGO. Hands on Using Wireshark to 'see' Kerberos. Troubleshooting Kerberos Approach, debugging tools, errors and solutions. Hands on Kerberos troubleshooting. Kerberos security concerns Kerberos attacks, protocol security issues. Dictionary attacks, brute force attacks, replay attacks, MITM attacks, security solutions, protecting the KDC, firewalls, NAT and Kerberos. Hands on Kerberos logging. Software which uses Kerberos Kerberos logins, Kerberos and web based applications, Directory services. Advanced Kerberos issues Cross realm authentication, Windows issues, Windows and UNIX interoperability, Hands on Using a Windows DC for UNIX clients.

Firewalls training course description A technical hands on training course covering firewall technologies. This focuses on the whys and hows of firewall technology rather than looking at manufacturer specific issues. What will you learn Design secure firewall protected networks. Test firewalls. Evaluate firewalls Configure firewalls Firewalls training course details Who will benefit: Technical staff wanting to learn about Filrewalls including: Technical network staff. Technical security staff. Prerequisites: IP security foundation for engineers Duration 2 days Firewalls training course contents Firewall introduction Security review, what is a firewall? What do firewalls do? Firewall benefits, concepts. Hands on Configuring the network to be used in later labs, launching various attacks on a target. Firewall types Packet filtering, SPI, Proxy, Personal. Software firewalls, hardware firewalls, blade based firewalls, personal firewalls, which firewall should you use? Firewall products. Hands on Configuring a simple firewall. Packet filtering firewalls Things to filter in the IP header, stateless vs. stateful filtering. ACLs. Advantages of packet filtering. Hands on Configuring packet filtering firewalls. Stateful packet filtering Stateful algorithms, packet-by-packet inspection, application content filtering, tracks, special handling (fragments, IP options), sessions with TCP and UDP. Firewall hacking detection: SYN attacks, SSL, SSH interception. Hands on Stateful packet inspection firewalls. Proxy firewalls Circuit level, application level, SOCKS. Proxy firewall advantages and disadvantages. Hands on Proxy firewalls. Personal firewalls The role of personal firewalls, Windows XP, Zonealarm. Hands on Configuring a personal firewall. Firewall architectures Home based, small office, enterprise, service provider, what is a DMZ? DMZ architectures, bastion hosts, multi DMZ. Virtual firewalls, transparent firewalls. Dual firewall design, high availability, load balancing, VRRP. Hands on Resilient firewall architecture. Securing communications VPNs, IPsec. Firewall configuration of VPNs, integration of dedicated VPN devices and firewalls. Hands on IPSec VPN configuration. Testing firewalls Configuration checklist, testing procedure, monitoring firewalls, logging, syslog. Hands on Testing firewalls.

RESILIA Foundation: In-House Training
By IIL Europe Ltd
RESILIA™ Foundation: In-House Training AXELOS RESILIA™: Cyber Resilience Best Practice is designed to help commercial and government organizations around the world prevent, detect, and correct any impact cyber attacks will have on the information required to do business. Adding RESILIA to the existing AXELOS global best practice portfolio, including ITIL® and PRINCE2®, brings a common cyber resilience best practice for security, IT service management, and business. Active cyber resilience is achieved through people, process, and technology. The RESILIA™ Foundation course starts with the purpose, key terms, the distinction between resilience and security, and the benefits of implementing cyber resilience. It introduces risk management and the key activities needed to address risks and opportunities. Further, it explains the relevance of common management standards and best practice frameworks to achieve cyber resilience. Subsequently, it identifies the cyber resilience processes, the associated control objectives, interactions, and activities that should be aligned with corresponding ITSM activities. In the final part of the course, it describes the segregation of duties and dual controls related to cyber resilience roles and responsibilities. What you will Learn At the end of this course, you will be able to: Demonstrate your knowledge of the purpose, benefits, and key terms of cyber resilience Demonstrate your knowledge of the risk management and the key activities needed to address risks and opportunities Demonstrate your knowledge of the purpose of a management system and how best practices and standards can contribute Demonstrate your knowledge of the cyber resilience strategy, the associated control objectives, and their interactions with ITSM activities Demonstrate your knowledge of cyber resilience design, the associated control objectives, and their interactions with ITSM activities Demonstrate your knowledge of cyber resilience transition, the associated control objectives, and their interactions with ITSM activities Demonstrate your knowledge of cyber resilience operation, the associated control objectives, and their interactions with ITSM activities Demonstrate your knowledge of cyber resilience continual improvement, the associated control objectives, and their interactions with ITSM activities Demonstrate your knowledge of the purpose and benefits of segregation of duties and dual controls Course Introduction Course Learning Objectives Course Agenda Activities Course Book Structure RESILIA Certification Introduction to Cyber Resilience What is Cyber Resilience? Defining Cyber Resilience Balancing in Cyber Resilience Characteristics of Cyber Resilience Risk Management Understanding Risk Management: Discussion Defining Risk Management Addressing Risks and Opportunities Managing Cyber Resilience Why and What of Management Systems? Management Systems Common Management Standards and Frameworks Cyber Resilience Strategy What is Strategy? Cyber Resilience Strategy and Activities Security Controls at Cyber Resilience Strategy Interaction Between ITSM Processes and Cyber Resilience Cyber Resilience Design Why Cyber Resilience Design? Cyber Resilience Design Activities Security Controls at Cyber Resilience Design Aligning ITSM Processes with Cyber Resilience Processes Cyber Resilience Transition Why Cyber Resilience Transition? Basics of Cyber Resilience Transition Cyber Resilience Transition: Controls Interaction Between ITSM Processes and Cyber Resilience Cyber Resilience Operation The Purpose of Cyber Resilience Operation Security Controls in Cyber Resilience Operation Interaction Between IT Processes and Cyber Resilience Interaction Between ITSM Functions and Cyber Resilience Cyber Resilience Continual Improvement Continual or Continuous Improvement Maturity Models Continual Improvement Controls The Seven-Step Improvement Process The ITIL CSI Approach Cyber Resilience Roles & Responsibilities Segregating Duties Dual Controls

Search By Location
- Security Courses in London
- Security Courses in Birmingham
- Security Courses in Glasgow
- Security Courses in Liverpool
- Security Courses in Bristol
- Security Courses in Manchester
- Security Courses in Sheffield
- Security Courses in Leeds
- Security Courses in Edinburgh
- Security Courses in Leicester
- Security Courses in Coventry
- Security Courses in Bradford
- Security Courses in Cardiff
- Security Courses in Belfast
- Security Courses in Nottingham