- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
CompTIA IT Fundamentals ITF+ (FCO-U61) Exam Prep Course
By Packt
This video course will prepare you to take and pass the CompTIA IT Fundamentals (ITF+) certification (FC0-U61) exam confidently by helping you get to grips with all the major domains covered in the certification and enabling you to develop the skills required to set up, configure, and secure desktop PC, mobile, and networking devices.

Securing Cisco Networks with Open Source Snort (SSFSNORT) v2.1
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for The primary audience for this course is as follows: Security administrators Security consultants Network administrators System engineers Technical support personnel Channel partners and resellers Overview Upon completing this course, the learner will be able to meet these overall objectives: Define the use and placement IDS/IPS components. Identify Snort features and requirements. Compile and install Snort. Define and use different modes of Snort. Install and utilize Snort supporting software. Securing Cisco Networks with Open Source Snort (SSFSNORT) v3.0 is a 4-day course that shows you how to deploy Snort© in small to enterprise-scale implementations. You will learn how to install, configure, and operate Snort in Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) modes. You?ll practice installing and configuring Snort, utilize additional software tools and define rules to configure and improve the Snort environment, and more. The course qualifies for 32 Cisco Continuing Education credits (CE) towards recertification.This course will help you:Learning how to implement Snort, an open-source, rule-based, intrusion detection and prevention system. Gain leading-edge skills for high-demand responsibilities focused on security. Module 1: Detecting Intrusions with Snort 3.0 History of Snort IDS IPS IDS vs. IPS Examining Attack Vectors Application vs. Service Recognition Module 2: Sniffing the Network Protocol Analyzers Configuring Global Preferences Capture and Display Filters Capturing Packets Decrypting Secure Sockets Layer (SSL) Encrypted Packets Module 3: Architecting Nextgen Detection Snort 3.0 Design Modular Design Support Plug Holes with Plugins Process Packets Detect Interesting Traffic with Rules Output Data Module 4: Choosing a Snort Platform Provisioning and Placing Snort Installing Snort on Linux Module 5: Operating Snort 3.0 Start Snort Monitor the System for Intrusion Attempts Define Traffic to Monitor Log Intrusion Attempts Actions to Take When Snort Detects an Intrusion Attempt License Snort and Subscriptions Module 6: Examining Snort 3.0 Configuration Introducing Key Features Configure Sensors Lua Configuration Wizard Module 7: Managing Snort Pulled Pork Barnyard2 Elasticsearch, Logstash, and Kibana (ELK) Module 8: Analyzing Rule Syntax and Usage Anatomy of Snort Rules Understand Rule Headers Apply Rule Options Shared Object Rules Optimize Rules Analyze Statistics Module 9: Use Distributed Snort 3.0 Design a Distributed Snort System Sensor Placement Sensor Hardware Requirements Necessary Software Snort Configuration Monitor with Snort Module 10: Examining Lua Introduction to Lua Get Started with Lua

CCTE Check Point Troubleshooting Expert
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This course is designed for security experts and Check Point resellers who desire to obtain the necessary knowledge required to perform more advanced troubleshooting skills while managing their security environments. Overview Understand how to use Check Point diagnostic tools to determine the status of a network. Understand how to use network packet analyzers and packet capturing tools to evaluate network traffic.Become familiar with more advanced Linux system commands. Obtain a deeper knowledge of the Security Management architecture. Understand how the Management database is structured and how objects are represented in the database. Understand key Security Management Server processes and their debugs. Understand how GuiDBedit operates. Understand how the kernel handles traffic and how to troubleshoot issues with chain modules. Understand how to use the two main procedures for debugging the Firewall kernel and how they differ. Recognize User mode processes and how to interpret their debugs. Discuss how to enable and use core dumps. Understand the processes and components used for policy installs and processing packets in Access Control policies. Understand how to troubleshoot and debug issues that may occur with App Control and URLF. Understand how to debug HTTPS Inspection-related issues. Understand how to troubleshoot and debug Content Awareness issues. Understand how IPS works and how to manage performance issues. Understand how to troubleshoot Anti-Bot and Antivirus. Recognize how to troubleshoot and debug Site-to-Site VPN related issues. Understand how to troubleshoot and debug Remote Access VPNs. Understand how troubleshoot Mobile Access VPN issues. Recognize how to use SecureXL features and commands to enable and disable accelerated traffic. Understand how the server hardware and operating system affects the performance of Security Gateways. Understand how to evaluate hardware configurations for optimal performance. Provide advanced troubleshooting skills to investigate and resolve more complex issues that may occur while managing your Check Point Security environment. Course Outline Advanced Troubleshooting Management Database and Processes Advanced Kernel Debugging User Mode Troubleshooting Advanced Access Control Understanding Threat Prevention Advanced VPN Troubleshooting Acceleration and Performance Tuning Additional course details: Nexus Humans CCTE Check Point Troubleshooting Expert training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the CCTE Check Point Troubleshooting Expert course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Description: This Certified Professional Ethical Hacker (CPEH) - Complete Video Training covers everything you need to know about becoming a certified professional ethical hacker. In this course you will learn about security fundamentals, access controls, protocols, cryptography, vulnerability assessments, vulnerability tools of the trade, output analysis and reports, reconnaissance, enumeration and scanning, gaining access, maintaining access, covering tracks, malware, buffer overflows, and password cracking. This course is designed to introduce you to up-to-date penetrating testing, plus certification. This course will enable you to understand the importance of vulnerability assessments by providing industry knowledge and skills in Vulnerability Assessments. In doing so, you will be able to understand how malware and destructive viruses function. In addition, the CPEH course helps you to learn how to implement counter response and preventative measures when it comes to a network hack. Assessment: At the end of the course, you will be required to sit for an online MCQ test. Your test will be assessed automatically and immediately. You will instantly know whether you have been successful or not. Before sitting for your final exam you will have the opportunity to test your proficiency with a mock exam. Certification: After completing and passing the course successfully, you will be able to obtain an Accredited Certificate of Achievement. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. Who is this Course for? Certified Professional Ethical Hacker (CPEH) - Complete Video Training is certified by CPD Qualifications Standards and CiQ. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic background. Requirements Our Certified Professional Ethical Hacker (CPEH) - Complete Video Training is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path After completing this course you will be able to build up accurate knowledge and skills with proper confidence to enrich yourself and brighten up your career in the relevant job market. Security Fundamentals Security Fundamentals FREE 00:51:00 Access Controls Access Controls 00:33:00 Protocols Protocols 00:36:00 Cryptography Cryptography 00:52:00 Why Vulnerability Assessments? Why Vulnerability Assessments? 00:36:00 Vulnerability Tools of the Trade Vulnerability Tools of the Trade 00:10:00 Output Analysis and Reports Output Analysis and Reports 00:13:00 Reconnaisance, Enumeration and Scanning Reconnaisance, Enumeration and Scanning 00:51:00 Gaining Access Gaining Access 00:31:00 Maintaining Access Maintaining Access 00:17:00 Covering Tracks Covering Tracks 00:18:00 Malware Malware 00:28:00 Buffer Overflows Buffer Overflows 00:22:00 Password Cracking Password Cracking 00:33:00 Mock Exam Mock Exam- Certified Professional Ethical Hacker (CPEH) - Complete Video Training 00:20:00 Final Exam Final Exam- Certified Professional Ethical Hacker (CPEH) - Complete Video Training 00:20:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Attacking and Securing Java / JEE Web Applications (TT8320-J)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This is an intermediate -level programming course, designed for experienced Java developers who wish to get up and running on developing well defended software applications. Familiarity with Java and JEE is required and real world programming experience is highly recommended. Ideally students should have approximately 6 months to a year of Java and JEE working knowledge. Overview Students who attend Attacking and Securing Java Web Applications will leave the course armed with the skills required to recognize actual and potential software vulnerabilities and implement defenses for those vulnerabilities. This course begins by developing the skills required to fingerprint a web application and then scan it for vulnerabilities and bugs. Practical labs using current tools and techniques provide students with the experience needed to begin testing their own applications. Students also gain a deeper understanding of how attackers probe applications to understand the runtime environment as well as find potential weaknesses. This course the introduces developers to the most common security vulnerabilities faced by web applications today. Each vulnerability is examined from a Java/JEE perspective through a process of describing the threat and attack mechanisms, recognizing associated vulnerabilities, and, finally, designing, implementing, and testing effective defenses. Practical labs reinforce these concepts with real vulnerabilities and attacks. Students are then challenged to design and implement the layered defenses they will need in defending their own applications. There is an emphasis on the underlying vulnerability patterns since the technologies, use cases, and methods of attack as constantly changing. The patterns remain the same through all the change and flux. This 'skills-centric' course is about 50% hands-on lab and 50% lecture, designed to train attendees in secure web application development, coding and design, coupling the most current, effective techniques with the soundest industry practices. Our engaging instructors and mentors are highly experienced practitioners who bring years of current 'on-the-job' experience into every classroom. This lab-intensive course provides hands-on Java / JEE security training that offers a unique look at Java application security. Beginning with penetration testing and hunting for bugs in Java web applications, you embrace best practices for defensively coding web applications, covering all the OWASP Top Ten as well as several additional prominent vulnerabilities. You will repeatedly attack and then defend various assets associated with fully functional web applications and services, allowing you to experience the mechanics of how to secure JEE web applications in the most practical of terms. Bug Hunting Foundation Why Hunt Bugs? Safe and Appropriate Bug Hunting/Hacking Scanning Web Applications Scanning Applications Overview Moving Forward from Hunting Bugs Removing Bugs Foundation for Securing Applications Principles of Information Security Bug Stomping 101 Unvalidated Data Broken Authentication Sensitive Data Exposure XML External Entities (XXE) Broken Access Control Bug Stomping 102 Security Misconfiguration Cross Site Scripting (XSS) Deserialization/Vulnerable Components Insufficient Logging and Monitoring Spoofing, CSRF, and Redirects Moving Forward with Application Security Applications: What Next? Making Application Security Real

Explore the world of cybersecurity beyond firewalls and antivirus software in this micro-learning course. Discover the critical role employees play in safeguarding your organization's digital assets and learn about the motivations behind cybercrimes. Gain insights into the dynamic landscape of digital threats and the alarming growth of cybercrime. This course will equip you with essential knowledge to protect yourself and your company from security breaches, emphasizing the importance of vigilance and awareness. Learning Objectives Construct a dedicated and productive remote workspace, considering factors such as comfort, organization, and freedom from distractions, to enhance focus and work-life balance.;Develop effective time management skills and routines, including setting clear boundaries, prioritizing tasks, and scheduling breaks, to optimize productivity and prevent burnout in a hybrid work setting.;Enhance your communication and collaboration skills with the steps to accurately engage in virtual meetings, share ideas, and foster effective teamwork, ensuring successful interactions in the hybrid workspace.

Overview EDMS Electronic Document Management System is basically a kind of IT-based system which is developed to manage the creation, tracking, storage and disposal of all physical and digital documents and records. Through this, we can easily keep track of various documents modified by different users. With the access of one application, many different tasks can be completed that revolve around document management. It enhances the security system where we can easily define whom to have access to what part of the documents. EDRMS is known by many other different names like Enterprise content management systems or digital asset management, document mapping and so on. This course shows participants how to deal with documents in an electronic way to get rid of the paper's hard copy which takes a lot of space and time. It will also update you with the EDRMS system and changes that happen to take place with the passage of time. The advanced technology leads to Advance EDRMS systems with enhanced features.

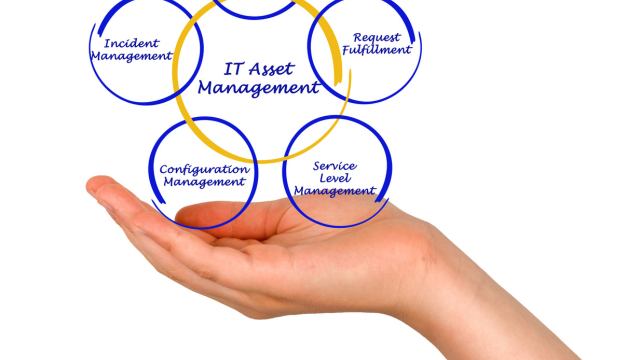
Step into the world of IT Asset Management (ITAM) and elevate your skills. From establishing ITAM programs to mastering asset security and compliance, this course offers a comprehensive guide to managing IT assets effectively. Enhance your ITAM expertise today!
Data Protection : Data Protection ( GDPR, Cyber, IT & Security)
By Training Tale
Data Protection : Data Protection If you want to learn about Data Protection: Data Protection Course and become an expert in the field, you have arrived at the right place. Industry experts designed this Data Protection: Data Protection course to enable you to learn quickly and efficiently and at your own pace and convenience. The Data Protection: Data Protection course contains all major GDPR topics in several lectures to help you learn more. This Data Protection: Data Protection also covers the UK's implementation of the General Data Protection: Data Protection Regulation Act. Data Protection: Data Protection Course aims to equip people and businesses with knowledge of the GDPR's obligations and measures. They must take to follow the regulation. The Data Protection: Data Protection Training seeks to educate individuals on their data rights and the obligations of organizations when it comes to collecting, processing, and keeping personal data. The Data Protection: Data Protection also includes best data protection: data protection, privacy practices, and advice on addressing data breaches and other problems. Main Course: GDPR Training Course Free Courses: Course 01: Security Management Diploma Course 02: Level 5 Diploma in Cyber Security Course 03: IT Security Data Protection : Data Protection Industry Experts Designed this Data Protection: Data Protection course into 09 detailed modules. Who is this course for? Data Protection : Data Protection This Data Protection: Data Protection course is open to everyone, Requirements Data Protection : Data Protection There are no specific requirements for this Data Protection : Data Protection course because it does not require any advanced knowledge or skills. Career path Data Protection : Data Protection

GDPR , Compliance & Information Management Level 3, 5 & 6 at QLS
4.7(47)By Academy for Health and Fitness
***24 Hour Limited Time Flash Sale*** GDPR , Compliance & Information Management Level 3, 5 & 6 at QLS Admission Gifts FREE PDF & Hard Copy Certificate| PDF Transcripts| FREE Student ID| Assessment| Lifetime Access| Enrolment Letter Unleash your potential in the crucial sectors of GDPR, Compliance, and Information Management with our comprehensive course bundle. Included in this unique bundle are three Quality License Scheme (QLS) endorsed courses that provide you with an in-depth understanding of GDPR basics, compliance certification, and information management. To authenticate your learning journey, you'll receive a hardcopy certificate upon completion of these QLS-endorsed courses, marking a noteworthy milestone in your professional development. But that's not all; this course bundle also incorporates five relevant Continued Professional Development (CPD) Quality Standard (QS) accredited courses. These cover important topics like Anti-Money Laundering (AML), Know Your Customer (KYC) guidelines, Cyber Security Awareness, Cyber Law, and Security Management. Equip yourself with this comprehensive GDPR, Compliance & Information Management course bundle and stay ahead in a world that increasingly values data protection and regulatory compliance. Key Features of the GDPR, Compliance & Information Management Level 3, 5 & 6 at QLS Bundle: 3 QLS-Endorsed Courses: We proudly offer 3 QLS-endorsed courses within our GDPR, Compliance & Information Management Level 3, 5 & 6 at QLS bundle, providing you with industry-recognized qualifications. Plus, you'll receive a free hardcopy certificate for each of these courses. QLS Course 01: Data Protection : GDPR Basics QLS Course 02: Certificate in Compliance QLS Course 03: Information Management 5 CPD QS Accredited Courses: Additionally, our bundle includes 5 relevant CPD QS accredited courses, ensuring that you stay up-to-date with the latest industry standards and practices. Course 01: Anti-Money Laundering (AML) Training Course 02: KYC Course 03: Cyber Security Awareness Training Course 04: Cyber Law Online Course Course 05: Security Management Diploma In Addition, you'll get Five Career Boosting Courses absolutely FREE with this Bundle. Course 01: Professional CV Writing Course 02: Job Search Skills Course 03: Self-Esteem & Confidence Building Course 04: Professional Diploma in Stress Management Course 05: Complete Communication Skills Master Class Convenient Online Learning: Our GDPR, Compliance & Information Management Level 3, 5 & 6 at QLS courses are accessible online, allowing you to learn at your own pace and from the comfort of your own home. Learning Outcomes of the GDPR, Compliance & Information Management Level 3, 5 & 6 at QLS Bundle: By the end of this GDPR, Compliance & Information Management bundle course, learners will be able to: Understand the essentials of the General Data Protection Regulation (GDPR). Gain theoretical knowledge of compliance and its significance in businesses. Learn about the intricacies of Information Management. Gain insights into Anti-Money Laundering (AML) measures. Understand the importance of Know Your Customer (KYC) guidelines. Develop awareness about Cyber Security and its importance in the digital age. Gain insights into the essentials of Cyber Law. Understand the principles of Security Management. The GDPR, Compliance & Information Management Level 3, 5 & 6 at QLS bundle offers a wide spectrum of knowledge across several key domains. It empowers you with a fundamental understanding of the GDPR, taking you through its importance in the digital era, and ensuring data protection. The bundle also includes a course on Compliance, which deepens your knowledge of maintaining organisational standards and regulations. The Information Management course provides insights into managing and utilising information effectively in a business setting. Moreover, the bundle also includes relevant CPD QS accredited courses like AML Training and KYC, offering a thorough understanding of financial regulations and customer verification processes. Further, it encompasses courses like Cyber Security Awareness Training, Cyber Law, and Security Management Diploma, amplifying your understanding of the digital security landscape. This comprehensive course bundle promises a thorough theoretical understanding, preparing you for the next steps in your career journey. CPD 250 CPD hours / points Accredited by CPD Quality Standards Who is this course for? This GDPR, Compliance & Information Management bundle course is ideal for: Individuals aspiring for a career in data protection, compliance, or information management. Professionals in the IT or finance sector seeking to enhance their theoretical knowledge. Students studying law, finance, or related fields. Anyone with a keen interest in understanding the legal and regulatory aspects of data management. Career path GDPR Compliance Officer - Salary range in the UK: £25,000 - £55,000 per year Compliance Officer - Salary range in the UK: £26,000 - £60,000 per year Information Management Specialist - Salary range in the UK: £30,000 - £70,000 per year AML Analyst - Salary range in the UK: £30,000 - £55,000 per year Cyber Security Analyst - Salary range in the UK: £30,000 - £70,000 per year Certificates Digital certificate Digital certificate - Included Hard copy certificate Hard copy certificate - Included
