- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
4560 Operations courses in Swallownest delivered Online
Embarking on a journey into the digital realm? Dive deep into the vast ocean of web development with our course: 'Start Your Career as Web Developer - Complete Training'. This comprehensive programme unfolds the mysteries of HTML, revealing its foundational to advanced layers. As you delve further, JavaScript beckons, introducing you to its core elements, from basic operations to error handling. But that's not all. PHP emerges on the horizon, offering an exploration from rudimentary concepts to intricate object-oriented programming and real-world applications. Equip yourself with the essence of web development and illuminate the pathways of the digital world. Learning Outcomes Grasp the foundational to advanced principles of HTML. Understand and apply JavaScript concepts from introductory to advanced error handling techniques. Master PHP from its fundamental aspects to advanced object-oriented programming and database integration. Develop and implement web applications integrating PHP with MySQL. Implement client-side and server-side validations using JavaScript and PHP. Why choose this Start Your Career as Web Developer - Complete Training? Unlimited access to the course for a lifetime. Opportunity to earn a certificate accredited by the CPD Quality Standards after completing this course. Structured lesson planning in line with industry standards. Immerse yourself in innovative and captivating course materials and activities. Assessments are designed to evaluate advanced cognitive abilities and skill proficiency. Flexibility to complete the Start Your Career as Web Developer - Complete Training Course at your own pace, on your own schedule. Receive full tutor support throughout the week, from Monday to Friday, to enhance your learning experience. Who is this Start Your Career as Web Developer - Complete Training for? Aspiring web developers seeking a structured pathway into the field. Current web designers looking to expand their skills into development. IT students aiming to bolster their academic understanding with applied knowledge. Entrepreneurs aiming to manage or understand their website's backend. Tech enthusiasts with a curiosity about the workings of web development. Career path Web Developer: £28,000 - £50,000 Front-End Developer: £30,000 - £50,000 Back-End Developer: £35,000 - £55,000 Full Stack Developer: £40,000 - £60,000 PHP Developer: £30,000 - £52,000 JavaScript Developer: £35,000 - £57,000 Prerequisites This Start Your Career as Web Developer - Complete Training does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Start Your Career as Web Developer - Complete Training was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Certification After studying the course materials, there will be a written assignment test which you can take at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £4.99 Original Hard Copy certificates need to be ordered at an additional cost of £8. Course Curriculum Introduction Introduction 00:03:00 How to Get Course requirements 00:02:00 Getting Started on Windows, Linux or Mac 00:02:00 How to ask Great Questions 00:01:00 FAQ's 00:01:00 HTML Introduction HTML 00:05:00 Choosing Code Editor 00:06:00 Installing Code Editor (Sublime Text) 00:04:00 Overview of a Webpage 00:05:00 Structure of a Full HTML Webpage 00:07:00 First Hello World! Webpage 00:09:00 HTML Basic Heading tags 00:09:00 Paragraph 00:08:00 Formatting Text 00:12:00 List Items Unordered 00:05:00 List Items Ordered 00:04:00 Classes 00:09:00 IDs 00:06:00 Comments 00:04:00 HTML Intermediate Images 00:12:00 Forms 00:05:00 Marquee 00:06:00 Text area 00:06:00 Tables 00:06:00 Links 00:07:00 Navbar - Menu 00:04:00 HTML Entities 00:05:00 Div tag 00:06:00 Google Maps 00:07:00 HTML Advanced HTML Audio 00:07:00 HTML Video 00:05:00 Canvas 00:06:00 Iframes 00:05:00 Input Types 00:04:00 Input Attributes 00:06:00 Registration Form 00:04:00 Contact Us Form 00:10:00 Coding Exercise 00:01:00 Solution for Coding Exercise 00:02:00 JavaScript Introduction What is JavaScript 00:09:00 Hello World Program 00:14:00 Getting Output 00:11:00 Internal JavaScript 00:13:00 External JavaScript 00:09:00 Inline JavaScript 00:04:00 Async and defer 00:06:00 JavaScript Basics Variables 00:13:00 Data Types 00:10:00 Numbers 00:06:00 Strings 00:07:00 String Formatting 00:05:00 JavaScript Operators Arithmetic operators 00:07:00 Assignment operators 00:03:00 Comparison operators 00:06:00 Logical operators 00:08:00 JavaScript Conditional Statements If-else statement 00:05:00 If-else-if statemen 00:04:00 JavaScript Control Flow Statements While loop 00:09:00 Do-while loop 00:03:00 For loop 00:08:00 Coding Exercise 00:02:00 Solution for Coding Exercise 00:02:00 JavaScript Functions Creating a Function 00:07:00 Function Call() 00:07:00 Function with parameters 00:05:00 JavaScript Error Handling Try-catch 00:05:00 Try-catch-finally 00:17:00 JavaScript Client-Side Validations On Submit Validation 00:09:00 Input Numeric Validation 00:12:00 PHP Introduction What is PHP 00:08:00 Installing XAMPP for PHP, MySQL and Apache 00:12:00 Installing Code Editor(Visual Studio Code) 00:07:00 Creating PHP Project on XAMPP 00:03:00 Hello World Program 00:06:00 PHP Basic Variables 00:16:00 Echo and Print 00:08:00 Data Types 00:11:00 Numbers 00:06:00 Boolean 00:04:00 Arrays 00:06:00 Multi-Dimensional Array 00:07:00 Sorting Arrays 00:04:00 Constants 00:05:00 PHP Strings Strings 00:04:00 String Formatting 00:05:00 String Methods 00:08:00 Coding Exercise 00:01:00 Solution for Coding Exercise 00:01:00 PHP Operators Arithmetic operators 00:03:00 Assignment operators 00:02:00 Comparison operators 00:05:00 Increment - decrement operators 00:03:00 Logical operators 00:06:00 Ternary operator 00:03:00 PHP Decision-making System If statement 00:05:00 If-else statement 00:02:00 If-else-if-else statement 00:03:00 Switch-case statement 00:05:00 PHP Control flow statements Flow Chart 00:06:00 While loop 00:09:00 Do-while loop 00:04:00 For loop 00:15:00 Foreach loop 00:04:00 Coding Exercise 00:01:00 Solution for Coding Exercise 00:01:00 PHP Functions Creating a Function 00:08:00 Function with Arguments 00:08:00 Default Argument 00:03:00 Function return values 00:06:00 Call-by-value 00:02:00 Call-by-reference 00:03:00 PHP Super globals $_POST Method 00:06:00 $_GET Method 00:02:00 PHP Advanced Form Handling 00:08:00 Date and Time 00:08:00 Include 00:06:00 Require 00:02:00 Sessions 00:08:00 File Reading 00:02:00 File Upload 00:06:00 PHP Object-oriented programming[OOPs] What is OOP 00:03:00 Class and Objects 00:11:00 Constructor 00:04:00 Destructor 00:03:00 Access Modifiers 00:10:00 Inheritance 00:12:00 Method overriding 00:06:00 Abstract Class 00:03:00 Interface 00:08:00 PHP - MySQL Application [CRUD] MySQL Basic PhpMyAdmin 00:04:00 Creating Database and Table 00:07:00 Database Connection 00:05:00 PHP Form Create records 00:16:00 PHP Form Reading records 00:11:00 PHP Form Update Data 00:15:00 PHP Form Delete record 00:04:00 PHP Real-world code forms Registration Form 00:04:00 MD5 Algorithm for Encrypting 00:03:00 Sha Algorithm 00:02:00 Login Form 00:12:00 PHP Validations On Submit Validation 00:09:00 Input Numeric Validation 00:12:00 Login Form Validation 00:05:00 Form Server-side all Data Validation 00:06:00 Form Server-side Validation 00:06:00 PHP Error handling Try-throw-catch 00:06:00 Try-throw-catch-finally 00:02:00

Cisco Securing Email with Cisco Email Security Appliance v3.1 (SESA)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for Security engineers Security administrators Security architects Operations engineers Network engineers Network administrators Network or security technicians Network managers System designers Cisco integrators and partners Overview After taking this course, you should be able to: Describe and administer the Cisco Email Security Appliance (ESA) Control sender and recipient domains Control spam with Talos SenderBase and anti-spam Use anti-virus and outbreak filters Use mail policies Use content filters Use message filters to enforce email policies Prevent data loss Perform LDAP queries Authenticate Simple Mail Transfer Protocol (SMTP) sessions Authenticate email Encrypt email Use system quarantines and delivery methods Perform centralized management using clusters Test and troubleshoot This course shows you how to deploy and use Cisco© Email Security Appliance to establish protection for your email systems against phishing, business email compromise, and ransomware, and to help streamline email security policy management. This hands-on course provides you with the knowledge and skills to implement, troubleshoot, and administer Cisco Email Security Appliance, including key capabilities such as advanced malware protection, spam blocking, anti-virus protection, outbreak filtering, encryption, quarantines, and data loss prevention. This course helps you prepare to take the exam, Securing Email with Cisco Email Security Appliance (300-720 SESA). Describing the Cisco Email Security Appliance Cisco Email Security Appliance Overview Technology Use Case Cisco Email Security Appliance Data Sheet SMTP Overview Email Pipeline Overview Installation Scenarios Initial Cisco Email Security Appliance Configuration Centralizing Services on a Cisco Administering the Cisco Email Security Appliance Distributing Administrative Tasks System Administration Managing and Monitoring Using the Command Line Interface (CLI) Other Tasks in the GUI Advanced Network Configuration Using Email Security Monitor Tracking Messages Logging Controlling Sender and Recipient Domains Public and Private Listeners Configuring the Gateway to Receive Email Host Access Table Overview Recipient Access Table Overview Configuring Routing and Delivery Features Controlling Spam with Talos SenderBase and Anti-Spam SenderBase Overview Anti-Spam Managing Graymail Protecting Against Malicious or Undesirable URLs File Reputation Filtering and File Analysis Bounce Verification Using Anti-Virus and Outbreak Filters Anti-Virus Scanning Overview Sophos Anti-Virus Filtering McAfee Anti-Virus Filtering Configuring the Appliance to Scan for Viruses Outbreak Filters How the Outbreak Filters Feature Works Managing Outbreak Filters Using Mail Policies Email Security Manager Overview Mail Policies Overview Handling Incoming and Outgoing Messages Differently Matching Users to a Mail Policy Message Splintering Configuring Mail Policies Using Content Filters Content Filters Overview Content Filter Conditions Content Filter Actions Filter Messages Based on Content Text Resources Overview Using and Testing the Content Dictionaries Filter Rules Understanding Text Resources Text Resource Management Using Text Resources Using Message Filters to Enforce Email Policies Message Filters Overview Components of a Message Filter Message Filter Processing Message Filter Rules Message Filter Actions Attachment Scanning Examples of Attachment Scanning Message Filters Using the CLI to Manage Message Filters Message Filter Examples Configuring Scan Behavior Preventing Data Loss Overview of the Data Loss Prevention (DLP) Scanning Process Setting Up Data Loss Prevention Policies for Data Loss Prevention Message Actions Updating the DLP Engine and Content Matching Classifiers Using LDAP Overview of LDAP Working with LDAP Using LDAP Queries Authenticating End-Users of the Spam Quarantine Configuring External LDAP Authentication for Users Testing Servers and Queries Using LDAP for Directory Harvest Attack Prevention Spam Quarantine Alias Consolidation Queries Validating Recipients Using an SMTP Server SMTP Session Authentication Configuring AsyncOS for SMTP Authentication Authenticating SMTP Sessions Using Client Certificates Checking the Validity of a Client Certificate Authenticating User Using LDAP Directory Authenticating SMTP Connection Over Transport Layer Security (TLS) Using a Client Certificate Establishing a TLS Connection from the Appliance Updating a List of Revoked Certificates Email Authentication Email Authentication Overview Configuring DomainKeys and DomainKeys Identified Mail (DKIM) Signing Verifying Incoming Messages Using DKIM Overview of Sender Policy Framework (SPF) and SIDF Veri?cation Domain-based Message Authentication Reporting and Conformance (DMARC) Verification Forged Email Detection Email Encryption Overview of Cisco Email Encryption Encrypting Messages Determining Which Messages to Encrypt Inserting Encryption Headers into Messages Encrypting Communication with Other Message Transfer Agents (MTAs) Working with Certificates Managing Lists of Certificate Authorities Enabling TLS on a Listener?s Host Access Table (HAT) Enabling TLS and Certi?cate Verification on Delivery Secure/Multipurpose Internet Mail Extensions (S/MIME) Security Services Using System Quarantines and Delivery Methods Describing Quarantines Spam Quarantine Setting Up the Centralized Spam Quarantine Using Safelists and Blocklists to Control Email Delivery Based on Sender Configuring Spam Management Features for End Users Managing Messages in the Spam Quarantine Policy, Virus, and Outbreak Quarantines Managing Policy, Virus, and Outbreak Quarantines Working with Messages in Policy, Virus, or Outbreak Quarantines Delivery Methods Centralized Management Using Clusters Overview of Centralized Management Using Clusters Cluster Organization Creating and Joining a Cluster Managing Clusters Cluster Communication Loading a Configuration in Clustered Appliances Best Practices Testing and Troubleshooting Debugging Mail Flow Using Test Messages: Trace Using the Listener to Test the Appliance Troubleshooting the Network Troubleshooting the Listener Troubleshooting Email Delivery Troubleshooting Performance Web Interface Appearance and Rendering Issues Responding to Alerts Troubleshooting Hardware Issues Working with Technical Support References Model Specifications for Large Enterprises Model Specifications for Midsize Enterprises and Small-to-Midsize Enterprises or Branch O?ces Cisco Email Security Appliance Model Specifications for Virtual Appliances

F5 Networks Configuring BIG-IP Advanced WAF - Web Application Firewall (formerly ASM)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is intended for security and network administrators who will be responsible for the installation, deployment, tuning, and day-to-day maintenance of the F5 Advanced Web Application Firewall. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTP-based attacks. The course includes lecture, hands-on labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. Module 1: Setting Up the BIG-IP System Introducing the BIG-IP System Initially Setting Up the BIG-IP System Archiving the BIG-IP System Configuration Leveraging F5 Support Resources and Tools Module 2: Traffic Processing with BIG-IP Identifying BIG-IP Traffic Processing Objects Overview of Network Packet Flow Understanding Profiles Overview of Local Traffic Policies Visualizing the HTTP Request Flow Module 3: Web Application Concepts Overview of Web Application Request Processing Web Application Firewall: Layer 7 Protection F5 Advanced WAF Layer 7 Security Checks Overview of Web Communication Elements Overview of the HTTP Request Structure Examining HTTP Responses How F5 Advanced WAF Parses File Types, URLs, and Parameters Using the Fiddler HTTP Proxy Module 4: Common Web Application Vulnerabilities A Taxonomy of Attacks: The Threat Landscape What Elements of Application Delivery are Targeted? Common Exploits Against Web Applications Module 5: Security Policy Deployment Defining Learning Comparing Positive and Negative Security Models The Deployment Workflow Policy Type: How Will the Policy Be Applied Policy Template: Determines the Level of Protection Policy Templates: Automatic or Manual Policy Building Assigning Policy to Virtual Server Deployment Workflow: Using Advanced Settings Selecting the Enforcement Mode The Importance of Application Language Configure Server Technologies Verify Attack Signature Staging Viewing Requests Security Checks Offered by Rapid Deployment Defining Attack Signatures Using Data Guard to Check Responses Module 6: Policy Tuning and Violations Post-Deployment Traffic Processing Defining Violations Defining False Positives How Violations are Categorized Violation Rating: A Threat Scale Defining Staging and Enforcement Defining Enforcement Mode Defining the Enforcement Readiness Period Reviewing the Definition of Learning Defining Learning Suggestions Choosing Automatic or Manual Learning Defining the Learn, Alarm and Block Settings Interpreting the Enforcement Readiness Summary Configuring the Blocking Response Page Module 7: Attack Signatures & Threat Campaigns Defining Attack Signatures Attack Signature Basics Creating User-Defined Attack Signatures Defining Simple and Advanced Edit Modes Defining Attack Signature Sets Defining Attack Signature Pools Understanding Attack Signatures and Staging Updating Attack Signatures Defining Threat Campaigns Deploying Threat Campaigns Module 8: Positive Security Policy Building Defining and Learning Security Policy Components Defining the Wildcard Defining the Entity Lifecycle Choosing the Learning Scheme How to Learn: Never (Wildcard Only) How to Learn: Always How to Learn: Selective Reviewing the Enforcement Readiness Period: Entities Viewing Learning Suggestions and Staging Status Violations Without Learning Suggestions Defining the Learning Score Defining Trusted and Untrusted IP Addresses How to Learn: Compact Module 9: Cookies and Other Headers F5 Advanced WAF Cookies: What to Enforce Defining Allowed and Enforced Cookies Configuring Security Processing on HTTP headers Module 10: Reporting and Logging Overview: Big Picture Data Reporting: Build Your Own View Reporting: Chart based on filters Brute Force and Web Scraping Statistics Viewing F5 Advanced WAF Resource Reports PCI Compliance: PCI-DSS 3.0 The Attack Expert System Viewing Traffic Learning Graphs Local Logging Facilities and Destinations How to Enable Local Logging of Security Events Viewing Logs in the Configuration Utility Exporting Requests Logging Profiles: Build What You Need Configuring Response Logging Module 11: Lab Project 1 Lab Project 1 Module 12: Advanced Parameter Handling Defining Parameter Types Defining Static Parameters Defining Dynamic Parameters Defining Dynamic Parameter Extraction Properties Defining Parameter Levels Other Parameter Considerations Module 13: Automatic Policy Building Overview of Automatic Policy Building Defining Templates Which Automate Learning Defining Policy Loosening Defining Policy Tightening Defining Learning Speed: Traffic Sampling Defining Track Site Changes Lesson 14: Web Application Vulnerability Scanner Integration Integrating Scanner Output Importing Vulnerabilities Resolving Vulnerabilities Using the Generic XML Scanner XSD file Lesson 15: Deploying Layered Policies Defining a Parent Policy Defining Inheritance Parent Policy Deployment Use Cases Lesson 16: Login Enforcement and Brute Force Mitigation Defining Login Pages for Flow Control Configuring Automatic Detection of Login Pages Defining Session Tracking Brute Force Protection Configuration Source-Based Brute Force Mitigations Defining Credentials Stuffing Mitigating Credentials Stuffing Lesson 17: Reconnaissance with Session Tracking Defining Session Tracking Configuring Actions Upon Violation Detection Lesson 18: Layer 7 DoS Mitigation Defining Denial of Service Attacks Defining the DoS Protection Profile Overview of TPS-based DoS Protection Creating a DoS Logging Profile Applying TPS Mitigations Defining Behavioral and Stress-Based Detection Lesson 19: Advanced Bot Protection Classifying Clients with the Bot Defense Profile Defining Bot Signatures Defining Proactive Bot Defense Defining Behavioral and Stress-Based Detection Defining Behavioral DoS Mitigation Lesson 20: Form Encryption using DataSafe Targeting Elements of Application Delivery Exploiting the Document Object Model Protecting Applications Using DataSafe The Order of Operations for URL Classification Lesson 21: Review and Final Labs Review and Final Labs

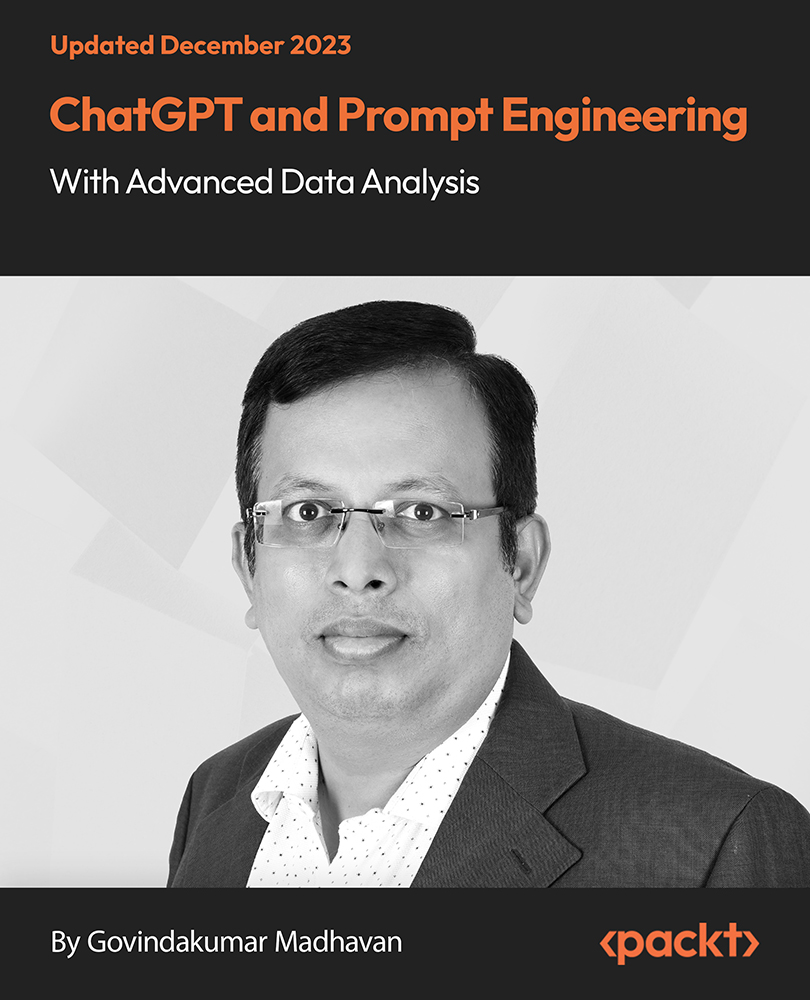
ChatGPT and Prompt Engineering With Advanced Data Analysis
By Packt
Explore ChatGPT, a cutting-edge world of AI content creation, with our comprehensive course. This meticulously curated program unravels the technology behind ChatGPT to practical applications in machine learning, social media, data analysis, and image generation. This course unveils new facets of AI to navigate this evolving landscape with prowess.
This Hotel & Hospitality Management Diploma with Holiday Representative Training will provide you with an understanding of the interrelationships between departments that drive performance in the hotel and resort industry. The course will introduce to the central philosophies of facilities and resource management, operating procedures and compliance requirements. You will focus on developing and maintaining effective teamwork and the management of staff relationships within a hospitality team. You will become proficient in developing food and beverage menus that meet cost requirements and the management of staff training processes. You'll learn about food service operations alongside a variety of academic disciplines, including foreign languages. This course covers a range of topics such as hotels, resorts, cruise ships, private / corporate owned restaurants and special catering events. You'll also be provided with cash handling, function, restaurant service, and barista skills. Who is this course for? Retail Customer Service and Visual Merchandising Training is suitable for anyone who wants to gain extensive knowledge, potential experience, and professional skills in the related field. This course is CPD accredited so you don't have to worry about the quality. Requirements Our Retail Customer Service and Visual Merchandising Training is open to all from all academic backgrounds and there is no specific requirements to attend this course. It is compatible and accessible from any device including Windows, Mac, Android, iOS, Tablets etc. CPD Certificate from Course Gate At the successful completion of the course, you can obtain your CPD certificate from us. You can order the PDF certificate for £9 and the hard copy for £15. Also, you can order both PDF and hardcopy certificates for £22. Career path This course opens a new door for you to enter the relevant job market and also gives you the opportunity to acquire extensive knowledge along with required skills to become successful. You will be able to add our qualification to your CV/resume which will help you to stand out in the competitive job industry. Course Curriculum Starting a Restaurant Are you ready for the challenge? 00:15:00 How to decide on a concept 00:30:00 Designing your restaurant 00:15:00 Friends and family 00:15:00 Writing a Business Plan 00:30:00 Insurance 00:15:00 Restaurant Organizations that you need to check out. 00:15:00 What are the best Catering Industry Trade Shows? 00:15:00 Managing a Restaurant Managing Yourself 00:30:00 Managing Others 00:30:00 Managing Your Money 00:15:00 Managing Your Food and Supplies 00:30:00 Managing Everything Else 00:30:00 Starting Food Catering Where You Work 00:15:00 Health and safety 00:15:00 Staff, Suppliers and Transport 00:00:00 Food Hygiene 01:00:00 Rules about Menus 00:15:00 Paperwork and Finances 00:15:00 Law 00:15:00 Food Business Food Business Basics 00:45:00 Put Together Your Business Concept 00:10:00 Identify Your Target Market 00:10:00 Identify Your Competition 00:10:00 Write A Mission Statement 00:10:00 Downline Basics 00:15:00 Equipment And Supplies 00:10:00 Marketing And Quality Control 00:10:00 Wrapping Up 00:05:00 Hospitality Introduction to Hospitality 00:15:00 Characteristics of the Hospitality Industry 00:15:00 Relationship Between the Hospitality Industry and Tourism 00:15:00 Types of Accommodation 00:15:00 Types of Room 00:30:00 Types of Hotel Guests 00:15:00 Hospitality Management Introduction to Hospitality Management 01:00:00 Influences Which Affect the Industry 00:05:00 The Development of the Hospitality Industry 00:05:00 Hospitality Brands 00:15:00 Accommodation 00:05:00 Food Service 00:05:00 Successful Quality Management 00:05:00 Holiday Representative Your Introduction to Becoming a Holiday Rep 00:15:00 Defining the Career of a Holiday Rep 00:30:00 Exploring the Various Types of Holiday Reps 00:30:00 Exploring the Origins and Growth of British Tourism 00:30:00 The Components of the Travel and Tourism Industry 00:15:00 Factors that Affect Your Career 00:30:00 Nailing the Teamwork Element Required to Surpass Expectations 01:00:00 The Standard Duties of Holiday Reps 00:15:00 The Legalities Holiday Reps Need to Know About 01:00:00 The Holiday Reps Role in Keeping their Guests Safe 00:30:00 Effective Handling of Customer Complaints 00:30:00 Administration Duties 00:15:00 Crushing It With Customer Services 00:30:00 Creating the Perfect Welcome Meeting 00:15:00 Guide to Selling Excursions 00:15:00 Preparing and Conducting Transfers Successfully 00:05:00 Tallying Floats and Converting Currencies 00:30:00 Mock Exam Mock Exam - Hotel & Hospitality Management Diploma with Holiday Representative Training 00:20:00 Final Exam Final Exam - Hotel & Hospitality Management Diploma with Holiday Representative Training 00:20:00 Certificate and Transcript Order Your Certificates or Transcripts 00:00:00

Step into the discreet, high-stakes world of close protection with this CPD Accredited course designed for those serious about understanding personal security operations. Whether you're navigating the roles within a protection team or decoding threat assessments, this course delivers a focused, professional insight into the structured processes behind effective close protection. Each module is methodically arranged to shed light on team dynamics, planning, route strategy, and legal considerations — without any unnecessary drama or vague promises. From vehicle drills to legislative frameworks, this course stays firmly on target. It's tailored for learners who prefer clear, intelligent content over inflated jargon. You'll explore how protection services are planned, what threat analysis involves, and why reconnaissance isn't just for spy films. And yes, all of this without needing to leap into a black SUV. This is online learning designed with a sharp suit and an even sharper sense of purpose. If you appreciate structure, precision, and a bit of dry wit along the way — you're in the right place. Still not convinced? Take a glimpse of the key benefits you'll get with - Lessons prepared in collaboration with Professionals User-friendly Learner Management System (LMS) Syllabus designed in line with the standards of the UK Education System Updated Study Materials focusing both on Knowledge and Skill based training Guidance to expand in 'a' territory and move forward with Skills and Capability Mentor profession Free Assessment to test learners' knowledge and skills Course Curriculum: Module 01: Introduction to Close Protection Module 02: The Close Protection Team Module 03: The Planning Module 04: Threat Assessment Module 05: Vehicle Drills: Embus and Debus Module 06: Route Selection and Reconnaissance Module 07: Legislation Regarding Close Protection Course Assessment You will immediately be given access to a specifically crafted MCQ test upon completing the Close Protection - CPD Accredited course. For each test, the pass mark will be set to 60%. Accredited Certificate After successfully completing this Close Protection - CPD Accredited course, you will qualify for the CPD Quality Standards (CPD QS) certified certificate from Training Express. CPD 10 CPD hours / points Accredited by The CPD Quality Standards (CPD QS) Who is this course for? The Close Protection - CPD Accredited training is ideal for highly motivated individuals or teams who want to enhance their skills and efficiently skilled employees. Requirements There are no formal entry requirements for the course, with enrollment open to anyone! Career path Learn the essential skills and knowledge you need to excel in your professional life with the help & guidance from our Close Protection - CPD Accredited training.

Mastering Management: Navigating the UK's Top Courses for Success
By Assignment help Online
Get the best management assignment help and management course guide online by Uk management experts.

Google Cloud Engineer Associate Certification Bootcamp
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Cloud Solutions Architects DevOps Engineers Individuals using Google Cloud Platform who deploy applications, monitor operations, and manage enterprise solutions Overview At course completion, you will have attained knowledge of: Fundamentals of Google Cloud Platform (GCP) Google Cloud Storage Google Compute Engine Google Cloud SQL Load Balancing (LB) Google Cloud Monitoring Auto-Scaling Virtual Private Cloud (VPC) Network Cloud Identity and Access Management (IAM) Cloud CDN and DNS Cloud VPN Google Cloud Deployment Manager Google Container Engine Cloud Run Cloud Bigtable Cloud Datastore Cloud BigQuery Cloud DataFlow Cloud DataProc Cloud Pub/Sub In this course you will attain a deep knowledge of Google Cloud Platform infrastructure and design patterns on developing applications on GCP. This course will prepare you for the Google Cloud Architect Associate Certification Exam. Fundamentals of Google Cloud Platform (GCP) Overview Regions and Zones Review of major GCP services Google Cloud Storage Fundamental APIs Consistency Cloud Storage Namespace Buckets and Objects Bucket and Object Naming Guidelines Encryption Object Versioning Object Lifecycle Management Access Control Access Control Lists Signed URL Multipart upload Resumable upload Understanding Pricing for Cloud Storage Offline Media Import/Export Architecture case study of common Use Cases of Google Cloud Storage Hands-on: Cloud Storage Lab; Creating Buckets, objects, and managing access control Google Compute Engine Compute Engine Architecture VM Instances types Persistence Disks Images Generating Custom Images IP Addresses Static IPs Ephemeral Access Control Options IAM Service Account Monitoring Instances with Google Cloud Monitoring Compute Engine Networks and Firewalls Hands-on: Hosting an Application on Compute Engine Google Cloud SQL Core advantages of Cloud SQL Cloud SQL database instance types Access Control High availability options Failover Read replica Backup options On Demand Automated Understanding Pricing of Cloud SQL Load Balancing (LB) Fundamentals of a Load Balancer Network Load balancing HTTPS Load balancing Cross region Load balancing Content Load balancing Target proxies SSL Load Balancing Internal Load Balancing Network Load Balancing Understanding Pricing for Load Balancer Google Cloud Monitoring Architecture of Cloud Monitoring Supported metrics Stackdriver Monitoring APIs Auto-Scaling Overview of Autoscaling Auto-scaling Fundamentals Instance groups Templates Policies Decisions Hands-on: Deploying a scale application on GCP using Autoscaling, Compute Engine, Cloud SQL, Load Balancers. Virtual Private Cloud (VPC) Network Salient features of Virtual Private Cloud (VPC) Network Infrastructure Virtual Private Cloud (VPC) Networking Fundamentals Subnetworks Firewall Internal DNS Network Routes Hands-on: Hosting Secure Applications in Google Cloud VPC Networks Cloud Identity and Access Management (IAM) Introduction User and Service Accounts IAM Roles Policy Hands-on: Managing Users, Policies and Granting Roles using Service Accounts Cloud CDN and DNS What is CDN Google Cloud CDN Cloud CDN Concepts Some of the Cloud CDN Edge locations Cloud DNS Cloud DNS Terminologies Supported Record Types Hands-on: Moving an Existing Domain Name to Cloud DNS Cloud VPN Cloud VPN overview Types of Cloud VPN Specifications Maintenance and Availability Google Cloud Deployment Manager Deployment Manager Deployment Manager Fundamentals Runtime Configurator Quotas Hands-on: Generating and Creating Cloud Deployment Manager Template Google Container Engine Google Container Engine Overview Docker Overview Kubernetes Terminologies Replication Controller Deployment Price and Quotas Hands-on: Deploying WordPress Cluster using Container Engine Cloud Run Overview of Cloud Run Deploy a Prebuilt Sample container Cloud Bigtable Overview of Cloud Bigtable Access Control Performance Locations Cloud Datastore Overview of Cloud Datastore Limits Storage Size Multitenancy Benefits of Multitenancy Encryption Locations Cloud BigQuery BigQuery Overview Interacting with BigQuery Datasets, Tables, and Views Partitioned Tables Query Plan Explanation Hands-on: Getting Started with BigQuery Cloud DataFlow Overview Programming Model DataFlow SDK 1.x for java Cloud Dataflow SDK 2.x Security and Permissions Advanced Access Control Cloud DataProc Overview Clusters Versioning Cloud Pub/Sub Overview of Cloud Pub/Sub Pub/Sub Concepts and Message Flow Data Model Cleanup of All Services Hands-on: Cloud Pub/Sub Lab with Background Cloud Function Additional course details: Nexus Humans Google Cloud Engineer Associate Certification Bootcamp training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Google Cloud Engineer Associate Certification Bootcamp course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

TX319 IBM Workload Scheduler 9.4 - Operations and Scheduling
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is designed for operators and schedulers who perform duties that are related to batch workload automation. Overview In this course, you learn how to perform the following tasks:Explain the production terminology used with IBM Workload Scheduler and its production planning processMonitor production batch workload processesManage production batch workloadCreate and modify scheduling objectsSchedule new workloadsForecast future workloadsMigrate workload definitions from test to production environmentsCreate and maintain reports about production workloads This course provides professional report authors an opportunity to learn report building techniques using relational data models. Demonstrations and exercises will illustrate and reinforce key concepts during this learning opportunity. IBM Workload Scheduler Introduction About Workload Automation IBM workload automation offerings IBM Workload Scheduler terminology Workload Scheduler user interfaces Getting started with Application Lab Getting started with the Dynamic Workload Console Connecting the console to Workload Scheduler Getting started with the command-line interfaces Using the Application Lab Interface Using the processes status overview page Managing processes Using other Application Lab functions Monitoring Workload Scheduler Production Monitoring Workload Scheduler production by using queries Using the Workload Dashboard Monitoring system status and health Monitoring plan objects Using the What-if Analysis interface Monitoring the plan graphically Managing Workload Scheduler Production Managing the scheduling environment Managing scheduling objects in the plan Creating Scheduling Objects Using the Workload Designer Creating scheduling objects Creating variables and variable tables Creating prompts and resources Creating calendars Defining jobs Scheduling, Forecasting, and Migrating Workloads Creating job streams Applying jobs to job streams Setting time and date restrictions Using advanced scheduling options Creating job stream definitions by using composer Creating and using event rules Forecasting and previewing future dates Exporting and importing scheduling definitions Using Workload Application Templates Reporting with Workload Scheduler Using reporting features Using Common Reporting with Workload Scheduler Using the batch reporting utility Using the preformatted text-based report utilities

Course Overview Develop the skills and expertise of Lean process and Six Sigma to set up a plier for a promising career. The Lean Process and Six Sigma Masterclass course will equip you with valuable lean and Six Sigma skills and provide you with a valuable certificate to elevate your resume. The Lean Process and Six Sigma Masterclass will provide you with an overall description of Lean and Six Sigma. You will get a peek inside the Lean culture and familiarize yourself with the five key principles of lean. From the engaging lessons, you will understand the fundamentals of value stream mapping. Within no time, you will attain the expertise required for Six Sigma. This step by step learning process will teach you the details of the define phase, measure phase, control phase and more. This Lean Process and Six Sigma Masterclass course is perfect for building a solid Lean and Six Sigma foundation. Join the course and increase your employability in the relevant sector. Learning Outcomes Understand the fundamentals of Lean and Lean culture Familiarize yourself with the five principles of Lean Enrich your knowledge and understanding of value stream mapping Learn the essential skills for Six Sigma Build an understanding of the define phase, control phase and measure phase in six Sigma Who is this course for? The Lean Process and Six Sigma Masterclass is for those who want to acquire Lean process and Six Sigma skills. Entry Requirement This course is available to all learners, of all academic backgrounds. Learners should be aged 16 or over to undertake the qualification. Good understanding of English language, numeracy and ICT are required to attend this course. Certification After you have successfully completed the course, you will be able to obtain an Accredited Certificate of Achievement. You can however also obtain a Course Completion Certificate following the course completion without sitting for the test. Certificates can be obtained either in hardcopy at the cost of £39 or in PDF format at the cost of £24. PDF certificate's turnaround time is 24 hours, and for the hardcopy certificate, it is 3-9 working days. Why choose us? Affordable, engaging & high-quality e-learning study materials; Tutorial videos/materials from the industry-leading experts; Study in a user-friendly, advanced online learning platform; Efficient exam systems for the assessment and instant result; The UK & internationally recognized accredited qualification; Access to course content on mobile, tablet or desktop from anywhere anytime; The benefit of career advancement opportunities; 24/7 student support via email. Career Path The Lean Process and Six Sigma Masterclass is a useful qualification to possess and would be beneficial for any related profession or industry such as: Lean Six Sigma Consultant Business Process Analyst Operating System Specialist Lean Process and Six Sigma Masterclass Module 1: Understanding Lean 00:24:00 Module 2: The Lean Culture 00:21:00 Module 3: The Five Principles of Lean 00:12:00 Module 4: Value and Waste 00:21:00 Module 5: Value Stream Mapping (VSM) 00:21:00 Module 6: The Principles of Flow and Pull 00:16:00 Module 7: Overview of Six Sigma 00:13:00 Module 8: The Define Phase 00:20:00 Module 9: The Measure Phase 00:23:00 Module 10: The Analyse Phase 00:24:00 Module 11: The Improve Phase 00:23:00 Module 12: The Control Phase 00:16:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00
