- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
1431 Network & Security courses delivered Online
In a world where so much of our commerce is focused online, it can be easy to forget the importance of physical security. However, physical breaches still take place and can lead to cyber-attacks, huge financial losses, damaged company reputation, and more. Cybercriminals who target businesses often look for the weak links in an organization's buildings, staff, and security protocol and are only successful if they can find them. This video outlines six different physical security protocols that you and your employees can take to ensure none of you are the weak link that may allow an attack. Learning Objectives Analyze the risks and consequences of physical security breaches, emphasizing the importance of maintaining a secure workplace environment.;Evaluate and implement best practices for physical security to reduce vulnerabilities and enhance workplace security.;Apply proactive measures to protect personal and organizational assets ensuring a stronger defense against physical security threats.

Level 7 Diploma in Cyber Security Law Online Course
By Kingston Open College
QLS Endorsed + CPD QS Accredited - Dual Certification | Instant Access | 24/7 Tutor Support | All-Inclusive Cost

Overview This comprehensive course on CompTIA A+ (220-1002) will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This CompTIA A+ (220-1002) comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this CompTIA A+ (220-1002). It is available to all students, of all academic backgrounds. Requirements Our CompTIA A+ (220-1002) is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Course Curriculum 22 sections • 106 lectures • 14:51:00 total length •CompTIA A+ 2019 Core 2 (220-1002) Course Introduction: 00:02:00 •What is the CompTIA A+: 00:02:00 •Why Get A+ Certified?: 00:03:00 •What is on the CompTIA A+ Core 2 (220-1002) Exam?: 00:04:00 •How to Pass the CompTIA A+ Exam: 00:04:00 •How to use this Video Course: 00:03:00 •Professional Communication Part 1: 00:06:00 •Professional Communication Part 2: 00:07:00 •Physical Safety: 00:07:00 •What is an Operating System?: 00:09:00 •Users and Super Users: 00:05:00 •Why Windows?: 00:08:00 •Windows Editions and Versions: 00:12:00 •Touring the macOS: 00:06:00 •Touring Linux: 00:08:00 •32-Bit vs. 64-Bit Processing: 00:12:00 •Virtual Memory: 00:06:00 •Power Protection: 00:10:00 •Understanding Partitioning: 00:04:00 •MBR Partitioning: 00:12:00 •GPT Partitioning: 00:09:00 •Understanding File Systems: 00:12:00 •Popular File Systems: 00:07:00 •Formatting in Action: 00:11:00 •Dynamic Disks: 00:09:00 •Software RAID in Storage Spaces: 00:10:00 •Encrypting Mass Storage: 00:09:00 •Boot from Everything: 00:12:00 •Installing Windows: 00:12:00 •Post-Installation Tasks: 00:12:00 •Windows Installation options: 00:07:00 •What is the Registry?: 00:11:00 •Processes: 00:07:00 •Services: 00:04:00 •Your Windows Toolset: 00:08:00 •Windows 7 Task Manager: 00:09:00 •Windows 10 Task Manager: 00:06:00 •Information and Configuration Tools: 00:11:00 •Performance Monitor: 00:12:00 •Event Viewer: 00:07:00 •Tools for Programmers: 00:08:00 •Introduction to Users and Groups: 00:06:00 •Managing Users and Groups: 00:12:00 •NTFS Permissions: 00:08:00 •Linux and macOS Permissions: 00:05:00 •File Explorer: 00:14:00 •Sharing Resources: 00:11:00 •Security Policies: 00:08:00 •Patch Management: 00:11:00 •Working with Disks: 00:06:00 •Working with Applications: 00:07:00 •System Restore: 00:05:00 •Backing up Your Files: 00:07:00 •Task Scheduler: 00:07:00 •Understanding the CLI: 00:11:00 •Navigating the CLI: 00:14:00 •Working with Folders: 00:07:00 •Working with Files: 00:11:00 •Working with Drives: 00:13:00 •Super Copy Commands: 00:09:00 •Advanced Windows Command Line: 00:08:00 •Advanced Linux Commands: 00:13:00 •Command-Line Permissions: 00:08:00 •Introduction to Scripting: 00:10:00 •Interpreted Languages: 00:12:00 •Windows Recovery Environment: 00:05:00 •Advanced Windows Startup Options: 00:07:00 •Troubleshooting Boot Problems: 00:10:00 •Troubleshooting at the GUI: 00:11:00 •Troubleshooting Applications: 00:07:00 •Kernel Panic: 00:05:00 •Resolutions and Aspect Ratios: 00:06:00 •Multiple Monitors: 00:05:00 •Network Card Troubleshooting: 00:09:00 •Working with Connections: 00:09:00 •Working with Workgroups: 00:08:00 •Working with Active Directory: 00:14:00 •Windows Sharing with Mac and LInux: 00:07:00 •Net Command: 00:04:00 •Firewall Configuration: 00:11:00 •Windows Firewall: 00:08:00 •Port Forwarding: 00:07:00 •Wireless Encryption: 00:11:00 •Enterprise Wireless: 00:16:00 •Telnet and SSH: 00:07:00 •Remote Desktop Connections: 00:06:00 •The World Wide Web: 00:09:00 •Troubleshooting Internet Connections: 00:07:00 •Power Management: 00:11:00 •Mobile Device Security: 00:08:00 •Mobile Security Troubleshooting: 00:06:00 •Mobile Device Troubleshooting: 00:10:00 •Threats: 00:10:00 •Physical Security: 00:08:00 •Passwords and Authentication: 00:14:00 •Malware: 00:14:00 •Anti-Malware: 00:11:00 •Social Engineering: 00:06:00 •Licensing: 00:10:00 •Incident Response: 00:05:00 •Environmental Controls: 00:06:00 •Documents You Need to Know: 00:09:00 •Data You Need to Know: 00:04:00 •Change Management: 00:06:00 •The Zen of Backup: 00:11:00 •Recycling and Data Destruction: 00:07:00
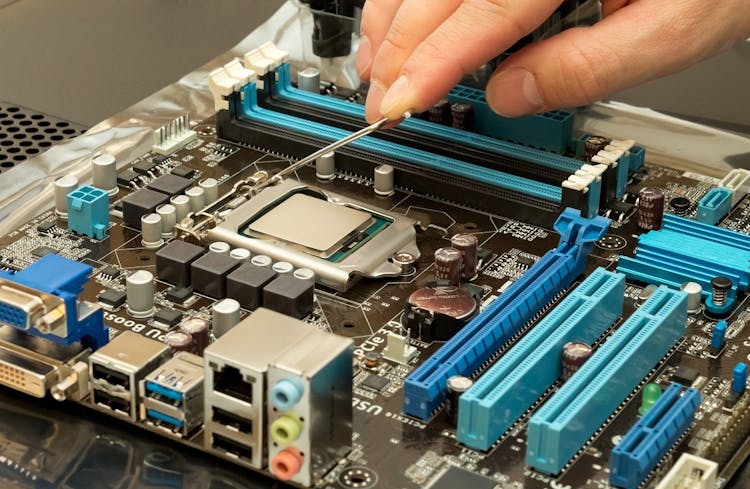
Overview Having a foundational understanding of IT components is essential. Did you know that by 2023, an estimated 2.5 million new IT positions will be available globally? The CompTIA A+ (220-1001) course offers a comprehensive dive into the world of computer technology. Designed to shape the professionals of tomorrow, this course meticulously covers the gamut of fundamental IT knowledge. Ranging from RAM technology to the vast world of cloud computing, the curriculum is structured to foster a comprehensive understanding. With modules such as 'Inside the PC' and 'Understanding Virtualization', learners will be adept at navigating the complex terrains of the modern IT environment. Ready to steer your career into the future of IT? Enrol now and become a part of the technological revolution! How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this CompTIA A+ (220-1001). It is available to all students, of all academic backgrounds. Requirements Our CompTIA A+ (220-1001) is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 24 sections • 132 lectures • 17:30:00 total length •CompTIA A+ 2019 Core 1 (220-1001) Course Introduction: 00:02:00 •What is the CompTIA A+?: 00:02:00 •Why Get A+ Certified?: 00:03:00 •What is on the CompTIA A+ Core 1 (220-1001) Exam?: 00:09:00 •How to Pass the A+ Exam: 00:04:00 •How to Use This Video Course: 00:03:00 •Tools of the Trade: 00:06:00 •Troubleshooting Theory: 00:10:00 •Primary PC Connections: 00:05:00 •External Connections: 00:11:00 •Inside the PC: 00:08:00 •What is a Computer?: 00:07:00 •What is a CPU?: 00:15:00 •CPU Speeds and Cores: 00:12:00 •Caching: 00:07:00 •CPU Sockets: 00:12:00 •Installing a CPU: 00:11:00 •Liquid Cooling: 00:04:00 •RAM Technology: 00:11:00 •RAM Capacity: 00:08:00 •RAM Features: 00:07:00 •Installing RAM: 00:07:00 •What is the BIOS?: 00:06:00 •POST: 00:09:00 •System Setup: 00:09:00 •Troubleshooting Firmware: 00:12:00 •Form Factors: 00:06:00 •Chipsets: 00:05:00 •Touring the Motherboard: 00:14:00 •Touring the Case: 00:07:00 •Installing a Motherboard: 00:09:00 •The Power Supply: 00:09:00 •Mounting a Power Supply: 00:05:00 •Choosing a Power Supply: 00:08:00 •Cooling Your PC: 00:11:00 •Troubleshooting Power Supplies: 00:09:00 •Troubleshooting Core Components: 00:14:00 •Introduction to Mass Storage: 00:13:00 •Magnetic Disk Drives: 00:08:00 •Solid State Drives: 00:08:00 •SCSI: 00:03:00 •Boot Order: 00:07:00 •New Installation - First Drive: 00:05:00 •RAID: 00:11:00 •Hardware RAID: 00:07:00 •Mass Storage Troubleshooting: 00:08:00 •Optical Media: 00:10:00 •USB Standards: 00:10:00 •Understanding USB: 00:11:00 •Configuring USB: 00:07:00 •Thunder and Lightning: 00:06:00 •Keyboards and Mice: 00:08:00 •Sight and Sound: 00:07:00 •Readers and Scanners: 00:08:00 •Using Expansion Cards: 00:08:00 •The Right PC for the Job: 00:13:00 •Monitor Technologies: 00:08:00 •LCD Breakdown: 00:04:00 •Graphics Cards and Connections: 00:13:00 •Installing a Graphics Card: 00:07:00 •Projectors: 00:05:00 •Troubleshooting Monitors: 00:06:00 •Introduction to Networking: 00:08:00 •Hubs vs. Switches: 00:05:00 •Hexadecimal: 00:07:00 •WANs and Routers: 00:09:00 •Cables and Connectors: 00:11:00 •Crimping Cables: 00:10:00 •Structured Cabling: 00:11:00 •Introduction to TCP/IP: 00:14:00 •Network IDs and Subnet Masks: 00:05:00 •Special IP Addresses: 00:09:00 •NAT: 00:07:00 •Dynamic IP Addressing: 00:10:00 •IPv6: 00:07:00 •Port Numbers: 00:12:00 •TCP, UDP, and ICMP: 00:06:00 •Understanding DNS: 00:09:00 •Working with DNS: 00:07:00 •Windows Naming: 00:08:00 •Routers: 00:12:00 •Basic Router Configuration: 00:12:00 •Advanced Router Configuration: 00:06:00 •VLANs: 00:07:00 •Network Troubleshooting: 00:05:00 •Wireless Network Hardware: 00:11:00 •Wi-Fi Standards: 00:10:00 •Basic WAP Setup: 00:11:00 •Connecting to a Wi-Fi Network: 00:09:00 •It's a Huge Mesh: 00:04:00 •Beyond Wi-Fi: 00:07:00 •Troubleshooting Wireless Connections: 00:07:00 •Beyond the LAN: 00:03:00 •Internet Tiers: 00:06:00 •Dial-up Connections: 00:08:00 •Broadband Connections: 00:10:00 •Firewalls and Servers: 00:06:00 •FTP: 00:07:00 •E-Mail: 00:08:00 •Proxy Servers: 00:06:00 •Virtual Private Networks (VPNs): 00:08:00 •Internet of Things (IoT): 00:04:00 •Understanding Virtualization: 00:10:00 •Your First Virtual Machine: 00:11:00 •Advanced Virtualization Setup: 00:10:00 •Cloud Computing: 00:08:00 •Cloud Ownership: 00:03:00 •Cloud-Based Applications: 00:06:00 •Laptop Features: 00:08:00 •Laptop Hardware Troubleshooting - The Tools: 00:05:00 •Laptop Hardware - Core Hardware: 00:04:00 •Laptop Hardware - CPU and Motherboard: 00:07:00 •Touring Your Laptop Display: 00:04:00 •What is a Mobile Device?: 00:09:00 •Mobile Connections: 00:10:00 •Touring Android: 00:10:00 •Touring iOS: 00:08:00 •Virtual Reality: 00:03:00 •Maintaining Mobile Devices: 00:11:00 •Mobile Devices and E-mail: 00:10:00 •Mobile Synchronization: 00:08:00 •Laser Printers: 00:13:00 •Inkjet Printers: 00:08:00 •Impact Printers: 00:04:00 •Thermal Printers: 00:04:00 •Installing a Local Printer: 00:14:00 •Sharing Printers: 00:08:00 •Installing Wireless and Cloud Printers: 00:10:00 •Troubleshooting Printers: 00:10:00 •3D Printing: 00:07:00 •Dealing with Threats: 00:07:00 •Assignment - CompTIA A+ (220-1001): 00:00:00
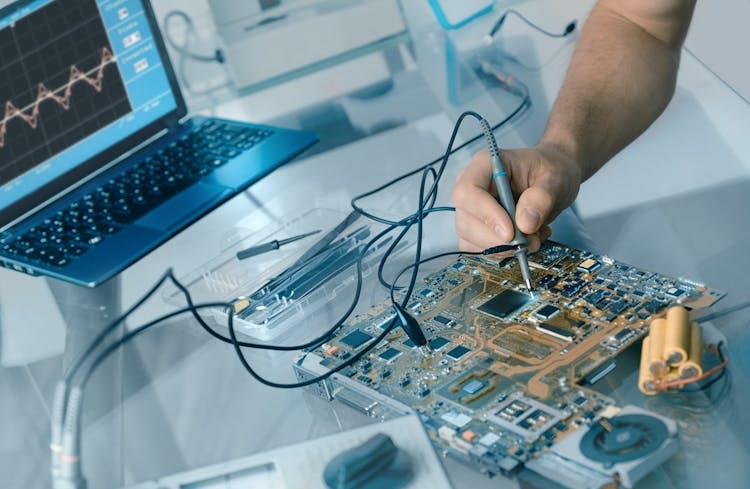
Overview This comprehensive course on CompTIA IT Fundamentals ITF+ (FCO-U61) will deepen your understanding on this topic. After successful completion of this course you can acquire the required skills in this sector. This CompTIA IT Fundamentals ITF+ (FCO-U61) comes with accredited certification from CPD, which will enhance your CV and make you worthy in the job market. So enrol in this course today to fast track your career ladder. How will I get my certificate? You may have to take a quiz or a written test online during or after the course. After successfully completing the course, you will be eligible for the certificate. Who is This course for? There is no experience or previous qualifications required for enrolment on this CompTIA IT Fundamentals ITF+ (FCO-U61). It is available to all students, of all academic backgrounds. Requirements Our CompTIA IT Fundamentals ITF+ (FCO-U61) is fully compatible with PC's, Mac's, Laptop, Tablet and Smartphone devices. This course has been designed to be fully compatible with tablets and smartphones so you can access your course on Wi-Fi, 3G or 4G. There is no time limit for completing this course, it can be studied in your own time at your own pace. Career Path Learning this new skill will help you to advance in your career. It will diversify your job options and help you develop new techniques to keep up with the fast-changing world. This skillset will help you to- Open doors of opportunities Increase your adaptability Keep you relevant Boost confidence And much more! Course Curriculum 15 sections • 64 lectures • 04:55:00 total length •Introduction to IT Fundamentals: 00:03:00 •The Case for Computer Literacy: 00:03:00 •Features Common to Every Computing Device: 00:02:00 •Common General-Purpose Computing Devices: 00:02:00 •Networks of Computing Devices: 00:04:00 •Remotely-Accessed Computer Systems: 00:04:00 •Specialized Computer Systems: 00:02:00 •Specialty I/O Devices: 00:01:00 •CPUs: 00:03:00 •Passive and Active Cooling: 00:03:00 •RAM and Active Memory: 00:05:00 •Motherboards: 00:03:00 •Power Supplies: 00:03:00 •AMA - Ask Me Anything about System Hardware: 00:07:00 •Ports and Connectors: 00:03:00 •General Use I/O Devices: 00:02:00 •AMA - Ask Me Anything about I/O, Ports and Peripherals: 00:07:00 •Basics of Binary: 00:04:00 •Storage Technologies: 00:04:00 •Mass Storage Variation: 00:03:00 •AMA - Ask Me Anything about Data Storage and Sharing: 00:07:00 •Operating System Functions: 00:04:00 •Operating System Interfaces: 00:05:00 •AMA - Ask Me Anything about Understanding OS's: 00:05:00 •Preparing the Work Area: 00:02:00 •Setting up a Desktop PC: 00:01:00 •Completing PC Setup: 00:04:00 •AMA - Ask Me Anything about Setting up and Configuring a PC: 00:09:00 •Personalizing a Tablet: 00:08:00 •AMA - Ask Me Anything about Mobile Devices Part 1: 00:07:00 •AMA - Ask Me Anything about Mobile Devices Part 2: 00:07:00 •File Management Tools: 00:02:00 •File Manipulation: 00:06:00 •Backups: 00:03:00 •AMA - Ask Me Anything about Managing Files: 00:08:00 •Walking Survey of Applications: 00:03:00 •Managing Applications: 00:03:00 •Applications and Extensions: 00:04:00 •AMA - Ask Me Anything about Working with Applications: 00:07:00 •Wi-Fi Setup: 00:06:00 •Going High Speed: 00:03:00 •Setting Up and Sharing Printers: 00:05:00 •AMA - Ask Me Anything about Networks and Internet Connectivity Part 1: 00:07:00 •AMA - Ask Me Anything about Networks and Internet Connectivity Part 2: 00:05:00 •Physical Security: 00:05:00 •Dealing with Malware: 00:03:00 •Password Management: 00:03:00 •Clickworthy: 00:03:00 •Perils of Public Internet: 00:02:00 •AMA - Ask Me Anything about IT Threat Mitigation Part 1: 00:07:00 •AMA - Ask Me Anything about IT Threat Mitigation Part 2: 00:08:00 •Power Management: 00:02:00 •Cleaning and Maintaining Computers: 00:02:00 •Trash it or Stash it?: 00:02:00 •AMA - Ask Me Anything about Computer Maintenance and Management: 00:11:00 •Troubleshooting 101: 00:03:00 •AMA - Ask Me Anything about Troubleshooting Computers Part 1: 00:10:00 •AMA - Ask Me Anything about Troubleshooting Computers Part 2: 00:11:00 •Introduction to Databases: 00:06:00 •Database Details: 00:06:00 •AMA - Ask Me Anything about Databases: 00:06:00 •Introduction to Programming: 00:04:00 •Programming with a PBJ Sandwich: 00:08:00 •AMA - Ask Me Anything about Programming: 00:04:00

Dive into the intricate world of criminal behaviour, law, and intelligence with this CPD Accredited Crime Analysis bundle. This triple-course package is designed to provide a solid grounding in the foundations of crime analysis, from understanding criminal motives to interpreting patterns in behaviour and legal frameworks. Whether you’re interested in the study of crime, looking to explore legal concepts, or fascinated by criminal psychology, this bundle offers a rich blend of content to expand your knowledge. Covering Crime Analysis, Criminal Law, and Criminal Psychology and Intelligence, each course complements the others to form a cohesive learning path. You’ll explore how crime is studied, how it’s prosecuted, and what drives offenders—building your understanding through structured, accessible lessons. The content is ideal for those looking to broaden their awareness of the criminal justice system, analytical approaches to crime, and behavioural insights, all from a distance-learning perspective. This is an excellent choice for learners who want depth, without the fluff—just focused, informative content built for curious minds. These comprehensive courses are available in this Crime Analysis - CPD Accredited 3 Courses Bundle Course 01: Crime Analysis Course 02: Criminal Law Course 03: Criminal Psychology and Intelligence ** Special Offer: Free PDF and Hard Copy Certificates** Key Benefits Get instant PDF and Hard Copy certificate Fully online courses Developed by qualified professionals Self-paced learning and laptop, tablet, and smartphone-friendly 24/7 Learning Assistance Course Curriculum: Crime Analysis Module 01: Introduction to Crime Analysis Module 02: The Criminal Justice System in England and Wales Module 03: Classification of Crime Module 04: Crime Scene Module 05: Crime Mapping Module 06: Tactical Crime Analysis Module 07: Strategic and Administrative Crime Analysis Module 08: Criminal Behaviour and Psychology Module 09: Financial and Environmental Criminology Module 10: Criminal Justice Module 11: Criminal Profiling: Science, Logic and Metacognition Module 12: Phases of Profiling Module 13: Criminal Intelligence Analysis Module 14: Technology in Criminal Intelligence Analysis Module 15: Research Method and Statistics in Crime Analysis Module 16: Policing and Cyber Security Module 17: Forecasting Future Occurrences and Prediction Course Assessment You will immediately be given access to a specifically crafted MCQ test upon completing each Crime Analysis - CPD Accredited 3 Courses Bundle bundle course. For each test, the pass mark will be set to 60%. Accredited Certificate After successfully completing this Crime Analysis - CPD Accredited 3 Courses Bundle course, you will qualify for the CPD Quality Standards (CPD QS) certified certificate from Training Express. CPD 30 CPD hours / points Accredited by The CPD Quality Standards (CPD QS) Who is this course for? The Crime Analysis - CPD Accredited 3 Courses Bundle training is ideal for highly motivated individuals or teams who want to enhance their skills and efficiently skilled employees. Requirements There are no formal entry requirements for the course, with enrollment open to anyone! Career path Learn the essential skills and knowledge you need to excel in your professional life with the help & guidance from our Crime Analysis - CPD Accredited 3 Courses Bundle training.

Dive into the layered world of criminal behaviour, legal frameworks, and analytical thinking with our CPD Accredited Criminal Intelligence Analyst – 3 Courses Bundle. This specialist programme is tailored for those with a keen interest in crime psychology, law, and intelligence, combining three distinct yet interconnected areas of study: Criminal Psychology and Intelligence, Criminal Law, and Crime Analysis. Whether you're exploring career options or broadening your understanding of the justice system, this course bundle offers a structured insight into the mechanics of criminal investigation and behavioural profiling. Each course is designed to complement the next—forming a cohesive path through the psychological motives behind crime, the legal systems that respond to it, and the analytical methods used to detect patterns and trends. From decoding criminal intent to interpreting legal responses and mapping crime data, this course bundle lays the groundwork for anyone aiming to deepen their knowledge of the criminal justice landscape. Fully online and designed for flexible learning, this is an ideal opportunity to develop analytical thinking within a focused, professional context. These comprehensive courses are available in this Criminal Intelligence Analyst - CPD Accredited 3 Courses Bundle Course 01: Criminal Psychology and Intelligence Course 02: Criminal Law Course 03: Crime Analysis ** Special Offer: Free PDF and Hard Copy Certificates** Key Benefits Get instant PDF and Hard Copy certificate Fully online courses Developed by qualified professionals Self-paced learning and laptop, tablet, and smartphone-friendly 24/7 Learning Assistance Course Curriculum: Criminal Psychology and Intelligence Module 01: Understanding Criminal Psychology Module 02: Influence of Mental Disorders Module 03: Classification of Crime Module 04: Forensic Science Module 05: Criminal Intelligence Analysis Module 06: Criminal Intelligence Analyst - Skills and Competencies Module 07: Research Methods in Crime Analysis Module 08: Decision Making in Criminal Intelligence Analysis Module 09: Criminal Profiling: Science, Logic and Metacognition Module 10: Phases of Profiling Module 11: Offender Profiling: Pragmatic Solution and Behavioural Investigative Advice Module 12: Victimology Module 13: The Criminal Justice System in England and Wales Course Assessment You will immediately be given access to a specifically crafted MCQ test upon completing each Criminal Intelligence Analyst - CPD Accredited 3 Courses Bundle bundle course. For each test, the pass mark will be set to 60%. Accredited Certificate After successfully completing this Criminal Intelligence Analyst - CPD Accredited 3 Courses Bundle course, you will qualify for the CPD Quality Standards (CPD QS) certified certificate from Training Express. CPD 30 CPD hours / points Accredited by The CPD Quality Standards (CPD QS) Who is this course for? The Criminal Intelligence Analyst - CPD Accredited 3 Courses Bundle training is ideal for highly motivated individuals or teams who want to enhance their skills and efficiently skilled employees. Requirements There are no formal entry requirements for the course, with enrollment open to anyone! Career path Learn the essential skills and knowledge you need to excel in your professional life with the help & guidance from our Criminal Intelligence Analyst - CPD Accredited 3 Courses Bundle training.

Description: The CISM certification program is developed specifically for experienced information security managers and those who have information security management responsibilities. CISM is globally recognized as the leading credential for information security managers. This Certified Information Security Manager (CISM) - Complete Video Course is designed to provide you with the knowledge and proficiency to prepare for the globally recognized CISM certification exam. The CISM certification combines the achievement of passing a comprehensive exam with recognition of work, management and educational experience, providing you with greater credibility in the marketplace. This course will immerse you into the subject, with in-depth coverage of the information covering the four domains that make up the 'Body of Knowledge' for the CISM exam and will provide you the tools to build your technical skills to manage, design, oversee and assess an enterprise's information security. Assessment: At the end of the course, you will be required to sit for an online MCQ test. Your test will be assessed automatically and immediately. You will instantly know whether you have been successful or not. Before sitting for your final exam you will have the opportunity to test your proficiency with a mock exam. Certification: After completing and passing the course successfully, you will be able to obtain an Accredited Certificate of Achievement. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. Who is this Course for? Certified Information Security Manager (CISM) - Complete Video Course is certified by CPD Qualifications Standards and CiQ. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic background. Requirements Our Certified Information Security Manager (CISM) - Complete Video Course is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path After completing this course you will be able to build up accurate knowledge and skills with proper confidence to enrich yourself and brighten up your career in the relevant job market. Information Security Governance Information Security Governance Overview FREE 00:25:00 Effective Information Security Governance 00:24:00 Information Security Concepts and Technologies 00:20:00 Information Security Manager 00:09:00 Scope and Charter of Information Security Governance 00:10:00 Information Security Governance Metrics 00:23:00 Information Security Strategy Overview 00:02:00 Creating Information Security Strategy 00:36:00 Determining Current State Of Security 00:06:00 Information Security Strategy Development 00:10:00 Strategy Resources 00:40:00 Strategy Constraints 00:07:00 Action Plan to Implement Strategy 00:20:00 Information Risk Management Risk Management Overview 00:16:00 Good Information Security Risk Management 00:15:00 Information Security Risk Management Concepts 00:13:00 Implementing Risk Management 00:17:00 Risk Assessment 00:39:00 Controls Countermeasures 00:23:00 Recovery Time Objectives 00:18:00 Risk Monitoring and Communication 00:04:00 Information Security Program Development Development of Information Security Program 00:11:00 Information Security Program Objectives 00:09:00 Information Security Program Development Concepts 00:14:00 Scope and Charter of Information Security Program Development 00:22:00 Information Security Management Framework 00:16:00 Information Security Framework Components 00:12:00 Information Security Program Resources 01:04:00 Implementing an Information Security Program 00:27:00 Information Infrastructure and Architecture 00:14:00 Information Security Program 00:14:00 Security Program Services and Operational Activities 00:45:00 Information Security Incident Management Incident Management Overview 00:28:00 Incident Response Procedures 00:29:00 Incident Management Organization 00:19:00 Incident Management Resources 00:36:00 Incident Management Objectives 00:14:00 Incident Management Metrics and Indicators 00:17:00 Current State of Incident Response Capability 00:11:00 Developing an Incident Response Plan 00:32:00 BCP DRP 00:36:00 Testing Response and Recovery Plans 00:10:00 Executing the Plan 00:27:00 Mock Exam Mock Exam- Certified Information Security Manager (CISM) - Complete Video Course 00:20:00 Final Exam Final Exam- Certified Information Security Manager (CISM) - Complete Video Course 00:20:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

Description: When a business is hit by a natural disaster, cybercrime or any other disruptive tragedy, how should the organization react? What if the network infrastructure is taken down? Will the business be able to continue operations? How much will it cost if the business is down during repairs? The answer is found in the vendor-neutral Certified Disaster Recovery Engineer (CDRE) - Complete Video Course. Disaster recovery and business continuity planning is the process of having a professional work with a business to prepare processes, policies and procedures to follow in the event of a disruption. The goal is to keep a business' critical operations running. This Certified Disaster Recovery Engineer (CDRE) - Complete Video Course covers everything you need to know about becoming a certified disaster recovery engineer. In this course you will learn about business impact analysis, risk analysis, BDP strategies, IT recovery strategies, implementation phase, testing and exercise, maintenance and updating, execution phase, cyber attacks, and pandemics. Assessment: At the end of the course, you will be required to sit for an online MCQ test. Your test will be assessed automatically and immediately. You will instantly know whether you have been successful or not. Before sitting for your final exam you will have the opportunity to test your proficiency with a mock exam. Certification: After completing and passing the course successfully, you will be able to obtain an Accredited Certificate of Achievement. Certificates can be obtained either in hard copy at a cost of £39 or in PDF format at a cost of £24. Who is this Course for? Certified Disaster Recovery Engineer (CDRE) - Complete Video Course is certified by CPD Qualifications Standards and CiQ. This makes it perfect for anyone trying to learn potential professional skills. As there is no experience and qualification required for this course, it is available for all students from any academic background. Requirements Our Certified Disaster Recovery Engineer (CDRE) - Complete Video Course is fully compatible with any kind of device. Whether you are using Windows computer, Mac, smartphones or tablets, you will get the same experience while learning. Besides that, you will be able to access the course with any kind of internet connection from anywhere at any time without any kind of limitation. Career Path After completing this course you will be able to build up accurate knowledge and skills with proper confidence to enrich yourself and brighten up your career in the relevant job market. Modules Welcome to Disaster Recovery Training FREE 00:26:00 Business Impact Analysis 00:24:00 Risk Analysis8 00:12:00 BCP Strategies 00:27:00 IT Recovery Strategies 00:27:00 Implementation Phase 00:09:00 Testing and Exercise 00:07:00 Maintenance and Updating 00:06:00 Execution Phase 00:07:00 Mock Exam Mock Exam- Certified Disaster Recovery Engineer (CDRE) - Complete Video Course 00:20:00 Final Exam Final Exam- Certified Disaster Recovery Engineer (CDRE) - Complete Video Course 00:20:00 Certificate and Transcript Order Your Certificates and Transcripts 00:00:00

CISSP®️ Certification Domain 8 - Software Development Security Video Boot Camp for 2022
By Packt
This course helps you prepare for your CISSP certification. In this course, we will be discussing CISSP? Certification Domain 8 - Software Development Security. This course focuses on how to secure software as we develop it. Domain 8 makes up 11% of the exam questions.
