- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
9683 Mode courses
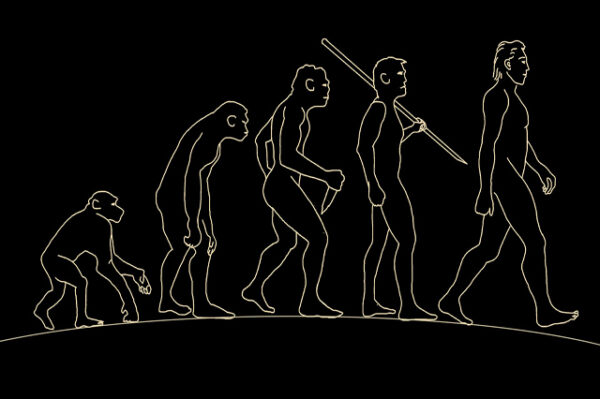
Description Anthropology Diploma The field of anthropology is a discipline concerned with how human societies originated and consequently developed over time. Experts in the field study various aspects of human life, from our primitive origins to recent developments like language and structured societies. There are five significant sub-fields under anthropology. Social anthropology, biological or physical, linguistic, applied, and archaeological anthropology. The diploma course in Anthropology offered by Elearncollege can help you gain knowledge about humans and human societies in ways you will find compelling, engaging, and comprehensive, including quizzes, detailed explanations, and so much more activities through an online mode of learning. Your adventure into the world of Anthropology can begin with the unique experience provided by the diploma course in Anthropology offered by Elearncollege. The course is adaptable to your pace of learning, and you will gain all the basic skills you require in the field. You will see how studying anthropology can enhance your understanding of various areas within the field from different viewpoints and perspectives. The Elearncollege Anthropology diploma course includes the study of human beings, human culture, and human societies and how they have developed over time. The diploma will provide you with a course that dives deep into the study of how life began for humans, the first organisations set up by humans, different societies and cultures, and the development of human languages throughout history. Experts in the domain designed every aspect of this diploma course through careful consideration and analysis. The course offers you a detailed breakdown going step-by-step through every topic in the course. After the course, you will be an expert ready to have a prosperous profession in Anthropology. Comprehensive and detailed step-by-step explanations regarding primitive human lives in tiny villages and how these have grown into different empires and states that we are today, spread all over the planet, will be available in the course. Human beings as a species started many million years ago. Through the field of Anthropology, we can explore this spectrum of evolution, how the species spread in different geographical regions, and how we have progressed over these several millions of years. We are a sophisticated, intelligent, and advanced species- a marvellous creation. One cannot help but wonder how it all happened. Could it be explained through the cause and effect of a chain of never-ending events, where one thing leads to another, and everything can be drawn back to one origin, which has been driving our developments? Are parts of our body results of evolution or creations of some supernatural being? Anthropology aims to attempt all these intriguing questions. IF, by any chance, we are creations of a supernatural being, then what is the origin of this so-called being? Anthropology is working towards understanding the internal thoughts and logic underlying societies and cultures and explaining various behaviours, paintings, arts, and societal rituals humans have had over time. The studies in this discipline aim to provide a new lens through which we can look at everyday objects with unique insight and understanding. The diploma in Anthropology offered by Elearncollege is a course open to any individual who may or may not have background training in anthropology. It wants to provide an introduction to the field that is easily understandable to all novices and beginners interested in gaining knowledge in the field without struggling to understand complicated texts. What you will learn 1: Introduction to Anthropology 2: Social Cultural Anthropology 3: Biological Anthropology 4: Archaeological Anthropology 5: Linguistic Anthropology 6: Gender and Sexuality 7: Economic Anthropology Course Outcomes After completing the course, you will receive a diploma certificate and an academic transcript from Elearn college. Assessment Each unit concludes with a multiple-choice examination. This exercise will help you recall the major aspects covered in the unit and help you ensure that you have not missed anything important in the unit. The results are readily available, which will help you see your mistakes and look at the topic once again. If the result is satisfactory, it is a green light for you to proceed to the next chapter. Accreditation Elearn College is a registered Ed-tech company under the UK Register of Learning( Ref No:10062668). After completing a course, you will be able to download the certificate and the transcript of the course from the website. For the learners who require a hard copy of the certificate and transcript, we will post it for them for an additional charge.
INTRODUCTION TO FILMMAKING
By Screen and Film School
This 10-week short course is perfect for students who are passionate about film and would like to explore different aspects of filmmaking in a fun, practical and creative manner. You will be given the opportunity to work with professional actors to shoot your first short film. Using a combination of practical workshops, presentations and film analysis, the course will provide you with experience and support in writing for the screen, producing, shooting and editing broadcast-quality moving images, and understanding screen acting techniques from both actor and director perspectives.

Master Business Networking in Just 1 Day - Join our Workshop in Plymouth
By Mangates
Business Networking 1 Day Training in Plymouth

Master Business Networking in Just 1 Day - Join our Workshop in Preston
By Mangates
Business Networking 1 Day Training in Preston

Master Business Networking in Just 1 Day - Join our Workshop in Livingston
By Mangates
Business Networking 1 Day Training in Livingston

Master Business Networking in Just 1 Day - Join our Workshop in Hinckley
By Mangates
Business Networking 1 Day Training in Hinckley

Master Business Networking in Just 1 Day - Join our Workshop in Hamilton, UK
By Mangates
Business Networking 1 Day Training in Hamilton, UK

Master Business Networking in Just 1 Day - Join our Workshop in Oxford
By Mangates
Business Networking 1 Day Training in Oxford

Master Business Networking in Just 1 Day - Join our Workshop in Newport
By Mangates
Business Networking 1 Day Training in Newport

Master Business Networking in Just 1 Day - Join our Workshop in Leeds
By Mangates
Business Networking 1 Day Training in Leeds

Search By Location
- Mode Courses in London
- Mode Courses in Birmingham
- Mode Courses in Glasgow
- Mode Courses in Liverpool
- Mode Courses in Bristol
- Mode Courses in Manchester
- Mode Courses in Sheffield
- Mode Courses in Leeds
- Mode Courses in Edinburgh
- Mode Courses in Leicester
- Mode Courses in Coventry
- Mode Courses in Bradford
- Mode Courses in Cardiff
- Mode Courses in Belfast
- Mode Courses in Nottingham