- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
221 Mac courses in Northfleet
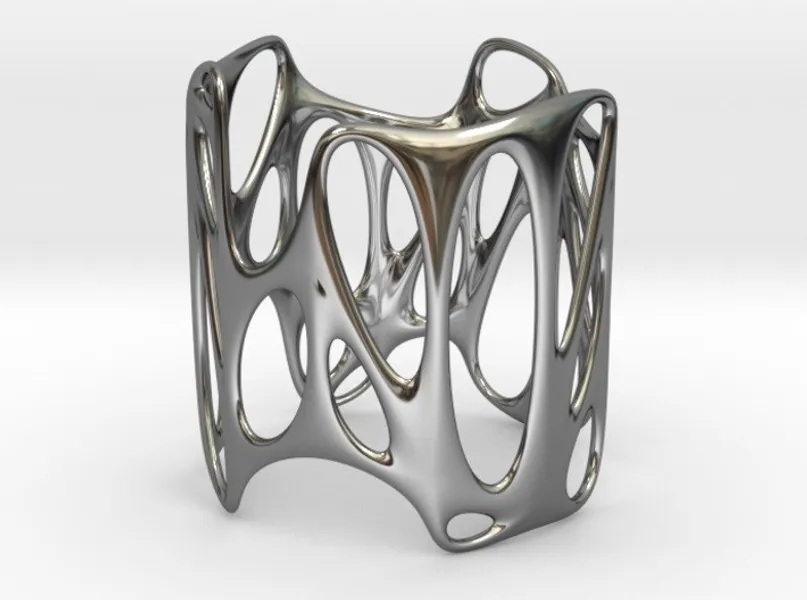
Jewellery Design Course - Create Personalised Jewellery (Blender)
By FluidDesigner
Learn to use 3D printing software to design and create your own pendants, earrings, rings and bracelets. The course is on a one-to-one basis. If you want to be in the jewellery trade as a designer and seller of modern jewellery or you simply want to create designs for yourself and your family then you should be learning how to create your own designs using apps such as Fluid Designer for 3D Printing.
LTE Architecture and Protocols course description This course provides a comprehensive tour of the LTE architecture along with services provided and the protocols used. What will you learn Describe the overall architecture of LTE. Explain the information flows through LTE. Describe the LTE security. Describe LTE mobility management. Recognise the next steps for LTE. LTE Architecture and Protocols course details Who will benefit: Anyone working with LTE. Prerequisites: Mobile communications demystified Duration 3 days LTE Architecture and Protocols course contents Introduction History, LTE key features. The 4G ITU process. The LTE 3GPP specifications. Specifications. System Architecture LTE hardware architecture. UE architecture and capabilities. E-UTRAN and eNB. EPC, MME functions, SGW, PGW and PCRF. System interfaces and protocol stacks. Example information flows. Dedicated and default bearers. EMM, ECM, RRC state diagrams. Radio transmission and reception OFDMA, SC-FDMA, MIMO antennas. Air interface protocol stack. Logical, transport and physical channels. Frame and slot structure, the resource grid. Resource element mapping of the physical channels and signals. Cell acquisition, data transmission and random access. MAC, RLC, PDCP protocols. LTE spectrum allocation. Power-on procedures Network and cell selection. RRC connection establishment. Attach procedure, including IP address allocation and default bearer activation. LTE detach procedure. Security in LTE networks LTE security features, identity confidentiality, ciphering and integrity protection. Architecture of network access security in LTE. Secure key hierarchy. Authentication and key agreement procedure. Security mode command procedure. Network domain security architecture. Security associations using IKE and IPSec. Mobility management RRC_IDLE, RRC_CONNECTED. Cell reselection, tracking area updates. Measurement reporting. X2 and S1 based handovers. Interoperation with UMTS, GSM and non-3GPP technologies such as cdma2000. QoS, policy control and charging QoS in LTE, EPS bearers, service data flows and packet flows. The architecture and signalling procedures for policy and charging control. Data transport using GPRS, differentiated services and MPLS. Offline and online charging in LTE. Delivery of voice and text messages over LTE Difficulties and solutions for Voice over LTE. Architecture and call setup procedures for circuit switched fallback. Architecture, protocols and call setup procedures in IP multimedia subsystem. Enhancements in release 9 LTE location services. Multimedia broadcast / multicast service and MBSFN. Cell selection, commercial mobile alert service. LTE Advanced and release 10 Impact of carrier aggregation on LTE air interface. Enhanced MIMO processing on uplink and downlink. Relaying. Release 11 and beyond. OAM and self organising networks Operation, administration, maintenance and provisioning for LTE. Self-configuration of base station parameters. Fractional frequency re-use, inter-cell interference co-ordination. Self-optimisation of base station procedures. Self-healing to detect and recover from faults.

Securing UNIX systems training course description This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. What will you learn Secure UNIX accounts. Secure UNIX file systems. Secure UNIX access through the network. Securing UNIX systems course details Who will benefit: Linux technical staff needing to secure their systems. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Securing UNIX systems course contents Cryptography Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. Host Security Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. Access Control Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. Network Security Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

LEATHER CRAFT AND LEATHER SEWING TECHNIQUES: WHAT IS THIS COURSE ABOUT? This is a theoretical and practical introductory group tuition during which you will be taught common, essential leather crafting and sewing techniques and understand how working with leather differs from working with vegan leather or fabric.You will be taught how to correctly use hand tools, how to sew leather by hand and understand the most common finishing and construction techniques used in bag and accessory making. You will learn about different types of leather and understand how to select the correct type of material(s) for your project. You will receive an overview of the technical aspects of working with leather and constructing bags and accessories such as inking, burninshing, marking, cutting, gluing, reinforcing, skiving, debossing and more.You will learn how to saddle stitch, select the appropriate tools for this sewing technique, and produce your own samples of work to take home with you.You will receive relevant, useful and informative handouts as well as lists of leather and tool suppliers. At the end of the lesson, you will have the choice to create a simple hand-sewn leather item, such as a simple purse or card holder, to take home with you, or to practice more techniques.This is a professional course delivered by a prototype maker and manufacturer, with the aim of providing an overview and hands-on experience on more common leather working practices. At the end of the tuition you will have: – Gained an understanding of leather types, tanning methods, leather characteristics and the best uses for specific projects. – Gained confidence in using specific tools for preparing, marking, finishing, cutting leather and fastening fittings. – Understood and practiced leather craft techniques such as inking, beveling and burnishing techniques – Understood what it means to work with different leather types and thicknesses and have the ability to source and select the correct tools and materials for your projects. – Understood how to manipulate leather using tools, reinforcement, stabilisers and stiffeners in crucial areas of bags and accessories. – Gained confidence in sewing by hand and obtained the skills to realise some simple leather items independently. WHAT WILL BE TAUGHT?Below is a list of topics covered during the classes: LEATHER, VEGAN LEATHER AND HAND TOOLS: – Understanding leather: overviews on types of leather, tanning, finishings and best use– Vegan leathers: an overview on different types and features – Understanding how to choose the right materials for your project and the appropriate tools for those materials – Leather preparing, pattern placement and marking on leather – Cutting complex shapes using a variety of tools – Using leather punches – Understanding the use of skiving, beveling and creasing – Finishing leather edges: painting vs burnishing – Using various leather glues and tapes – Understand the use of reinforcements, fusings and stabilisers to back leather – Prototyping and manufacturing leather goods: mentions of different working methods, machines and tools HAND SEWING: – To understand the different options, characteristics, and proper application of the tools used in saddle stitching – To learn the basics of saddle stitching leather and understood the different the tools and materials used in the technique CONSTRUCTION TECHNIQUES: – To create a small, simple hand stitched leather item to take home with you INCLUDED IN THE COURSE: You will be provided with useful digital and paper handouts which contain:– A list of tools and materials used during the lesson(s), including a description of what they are and how they are used– A list of recommended suppliers for both leather and fittings (physically in London and online)– A glossary containing essential key words related to the topic of the lesson– A glossary containing information about leather types and characteristics WHAT ARE THE ENTRY REQUIREMENTS?This course is suitable for total beginners, beginners with some experience and intermediate.You should be able to use measurements and understand verbal and written English instructions. ARE THERE ANY OTHER COSTS? IS THERE ANYTHING I NEED TO BRING?Materials are included.Feel free to bring a notepad, if you would like to take some notes, we will provide the rest. HOW LONG IS THIS TUITION?:This tuition will require up to 12 hours to complete. We aim to provide customised and high quality tuition services and by only allowing up to 6 students at a time, we are able to focus on each person needs and interests.As every student has a different level of ability and previous experience, this course might lead some students to complete the core aspects of the lesson in a shorter time frame than others.Students who complete the course early will be welcome to stay and use the studio facilities to exercise on the topics of the lesson.

LTE Airside training course description This course provides a concise insight into the LTE airside. Key parts of the course are detailed looks at the air interface protocol stack, cell acquisition, transmission and reception of data and of he layer 1 procedures along with layer 2 procedures. What will you learn Explain the RF optimisation flowchart. Describe the importance of Reference Signal Received Power (RSRP). List many of the 3GPP recommended KPIs. Describe the concept of APN AMBR and UE AMBR within LTE. Describe the use of planning and optimisation computer tools. LTE Airside training course details Who will benefit: Anyone working with LTE. Prerequisites: Essential LTE Duration 2 days LTE Airside training course contents Introduction and review of LTE This section describes the requirements of LTE and key technical features, and reviews the system architecture. LTE Architecture, UE, E-UTRAN and EPC. Specifications. OFDMA, SC-FDMA and MIMO antennas This section describes the techniques used in the LTE air interface, notably orthogonal frequency division multiple access (OFDMA) and multiple input multiple output (MIMO) antennas. Communication techniques for fading multipath channels. OFDMA, FFT processing and cyclic prefix insertion. SC-FDMA in the LTE uplink. Multiple antenna techniques including transmit & receive diversity and spatial multiplexing. Introduction to the air interface This section covers the operation of the air interface, the channels that it uses, and the mapping to the time and frequency domains of OFDMA and SC-FDMA. Air interface protocol stack. Logical, transport and physical channels. Frame and slot structure, the resource grid. Resource element mapping of the physical channels and physical signals. LTE spectrum allocation. Cell acquisition This is the first of three sections covering the air interface physical layer. Here, we cover mobile procedures to start low-level communications with the cell, and base station transmission of the corresponding information. Primary/secondary synchronisation signals. Downlink reference signals. The master information block. Physical control format indicator channel. Organisation and transmission of the system information. Data transmission and reception In this section, we cover procedures used for data transmission and reception on the shared channels, and describe in detail the individual steps. Data transmission and reception on the uplink and downlink. Scheduling commands and grants on the PDCCH. DL-SCH and UL-SCH. Physical channel processing of the PDSCH and PUSCH. Hybrid ARQ indicators on the PHICH. Uplink control information on the PUCCH. Uplink demodulation and sounding reference signals. Additional physical layer procedure This section concludes our discussion of the air interface physical layer, by discussing a number of procedures that support its operation. Transmission of the physical random access channel. Contention and non-contention based random access procedures. Discontinuous transmission in idle and connected modes. Uplink power control and timing advance. Air interface layer 2 This section describes the architecture and operation of layer 2 of the air interface protocol stack. MAC protocol, interactions with the physical layer, use for scheduling. RLC protocol, transparent, unacknowledged and acknowledged modes. PDCP, including header compression, security functions and recovery from handover.

LAN training course description A concise overview course covering Local Area Networks with particular emphasis on the use of Ethernet and Wireless LANS. As well as explaining buzzwords we cover how the technology works at a simple level. After defining LANs the course moves onto Ethernet and switching also covering VLANs. WiFi is then covered, with coverage of 802.11 standards and frequencies along with integrating WiFi with Ethernet. The course then covers routers and their role in connecting networks and the course finishes with a comparison of Ethernet vs WiFi and when to use them. What will you learn Describe how Ethernet works (in simple terms) and when to use Ethernet. Explain the difference between a switch and a router. Describe how WiFi works (in simple terms). Describe the role of Access points. Evaluate wireless technologies and when to use them. List the speeds of various LAN technologies. LAN training course details Who will benefit: Sales staff, managers and other non technical staff. Prerequisites: None. Duration 1 day LAN training course contents LANS What is a LAN? LAN standards, LAN choices, choosing the media, copper, UTP, cat5e, fibre, RF, bandwidth speeds, link aggregation, Full/half duplex. Ethernet What is Ethernet? 802.3, parts of Ethernet, Ethernet evolution, MAC addresses, frames, broadcasts. Ethernet switches What are switches, switches versus hubs, how switches work, ways to configure switches, Loops, STP. VLANs What are VLANs? Why have VLANs, impact of VLANs, Tagging (aka trunking), 802.1Q Wireless LANS Type of wireless LAN, RF frequencies, 2.4GHz, 5GHz, others, interference, standards, 802.11 and variants, CSMA/CA. Wireless LANS NICs, Access points, integration with Ethernet, multiple access points, mesh networks, WiFi security. Interconnecting LANs Routers, connecting networks, interconnecting VLANs, IP addressing, Layer 3 switches. Summary WiFi vs Ethernet.

Securing Linux systems training course description This course teaches you everything you need to know to build a safe Linux environment. The first section handles cryptography and authentication with certificates, openssl, mod_ssl, DNSSEC and filesystem encryption. Then Host security and hardening is covered with intrusion detection, and also user management and authentication. Filesystem Access control is then covered. Finally network security is covered with network hardening, packet filtering and VPNs. What will you learn Secure Linux accounts. Secure Linux file systems. Secure Linux access through the network. Securing Linux systems training course details Who will benefit: Linux technical staff needing to secure their systems. Prerequisites: Linux system administration (LPIC-1) Duration 5 days Securing Linux systems training course contents Cryptography Certificates and Public Key Infrastructures X.509 certificates, lifecycle, fields and certificate extensions. Trust chains and PKI. openssl. Public and private keys. Certification authority. Manage server and client certificates. Revoke certificates and CAs. Encryption, signing and authentication SSL, TLS, protocol versions. Transport layer security threats, e.g. MITM. Apache HTTPD with mod_ssl for HTTPS service, including SNI and HSTS. HTTPD with mod_ssl to authenticate users using certificates. HTTPD with mod_ssl to provide OCSP stapling. Use OpenSSL for SSL/TLS client and server tests. Encrypted File Systems Block device and file system encryption. dm-crypt with LUKS to encrypt block devices. eCryptfs to encrypt file systems, including home directories and, PAM integration, plain dm-crypt and EncFS. DNS and cryptography DNSSEC and DANE. BIND as an authoritative name server serving DNSSEC secured zones. BIND as an recursive name server that performs DNSSEC validation, KSK, ZSK, Key Tag, Key generation, key storage, key management and key rollover, Maintenance and resigning of zones, Use DANE. TSIG. Host Security Host Hardening BIOS and boot loader (GRUB 2) security. Disable useless software and services, sysctl for security related kernel configuration, particularly ASLR, Exec-Shield and IP / ICMP configuration, Exec-Shield and IP / ICMP configuration, Limit resource usage. Work with chroot environments, Security advantages of virtualization. Host Intrusion Detection The Linux Audit system, chkrootkit, rkhunter, including updates, Linux Malware Detect, Automate host scans using cron, AIDE, including rule management, OpenSCAP. User Management and Authentication NSS and PAM, Enforce password policies. Lock accounts automatically after failed login attempts, SSSD, Configure NSS and PAM for use with SSSD, SSSD authentication against Active Directory, IPA, LDAP, Kerberos and local domains, Kerberos and local domains, Kerberos tickets. FreeIPA Installation and Samba Integration FreeIPA, architecture and components. Install and manage a FreeIPA server and domain, Active Directory replication and Kerberos cross-realm trusts, sudo, autofs, SSH and SELinux integration in FreeIPA. Access Control Discretionary Access Control File ownership and permissions, SUID, SGID. Access control lists, extended attributes and attribute classes. Mandatory Access Control TE, RBAC, MAC, DAC. SELinux, AppArmor and Smack. etwork File Systems NFSv4 security issues and improvements, NFSv4 server and clients, NFSv4 authentication mechanisms (LIPKEY, SPKM, Kerberos), NFSv4 pseudo file system, NFSv4 ACLs. CIFS clients, CIFS Unix Extensions, CIFS security modes (NTLM, Kerberos), mapping and handling of CIFS ACLs and SIDs in a Linux system. Network Security Network Hardening FreeRADIUS, nmap, scan methods. Wireshark, filters and statistics. Rogue router advertisements and DHCP messages. Network Intrusion Detection ntop, Cacti, bandwidth usage monitoring, Snort, rule management, OpenVAS, NASL. Packet Filtering Firewall architectures, DMZ, netfilter, iptables and ip6tables, standard modules, tests and targets. IPv4 and IPv6 packet filtering. Connection tracking, NAT. IP sets and netfilter rules, nftables and nft. ebtables. conntrackd Virtual Private Networks OpenVPN server and clients for both bridged and routed VPN networks. IPsec server and clients for routed VPN networks using IPsec-Tools / racoon. L2TP.

Networks demystified training course description A concise overview course covering all aspects of networking with particular emphasis of use of the 7 layer model as a framework for discussing and learning new network terms enabling delegates to recognise the main buzzwords used in the industry. What will you learn Use the 7 layer model to classify networking terms. Differentiate between LANS and WANS. Recognise bandwidth measurements. List LAN and WAN technologies. Recognise cabling issues in a network. Networks demystified training course details Who will benefit: Sales staff, managers and other non-technical personnel. Technical personnel may benefit more from our Intro to data communications and networking course. Prerequisites: None. Duration 1 day Networks demystified training course contents What are networks? What is a network? Types of network, Local Area Networks (LANs), Wide Area Networks (WANs), connecting networks together with routers. The 7 layer model What is the 7 layer model? The importance of standards, using the 7 layer model to classify networking terms. Cables Copper, Fibre, Air, standards, connectors, LAN cables, WAN cables, distance limitations, hubs and repeaters, other issues. The radio spectrum. Bandwidth Bits and bytes. Bandwidth measurements, common technologies and their bandwidth, the impact of applications on bandwidth. Full and half duplex. Joining cables together to increase bandwidth (Link aggregation). LANs and WANs What is Ethernet? What is WiFi? What are Leased lines? What is MPLS? Ethernet switches Ethernet 'packets', MAC addresses, what is a switch, what is the difference between a hub and a switch. TCP/IP What is TCP/IP? What is a protocol? What is IP? What is TCP? The role of routers in joining LANS and WANS, What is the Internet? Applications Ways to use the network, clients, servers, web browsing and HTTP, Email, instant messaging, multimedia applications.

PROFESSIONAL TRAINING: MODULE 3 – INDUSTRIAL MACHINE SEWING TRAINING FOR LEATHER BAGS, ACCESSORIES, AND GARMENTS
5.0(52)By The London Leather Workshop
LEARN HOW TO SEW LEATHER USING INDUSTRIAL MACHINES FOR BAGS, ACCESSORIES, AND GARMENTS This is the third module of a series designed to provide thorough, professional training in leatherworking, sewing and accessory making. Each module has been carefully designed to equip individuals with key skills for starting a career in this sector, broadening their industry knowledge, or embarking on their own journey with solid foundational skills. During the class, you will learn how to correctly sew with the most common machines used in the leather industry and understand their differences. You will gain knowledge about threads, needles, feet, machine components, and useful sewing tricks. You will learn how to set the machine correctly to obtain suitable tension and successfully work with a variety of leather thicknesses and textures. Additionally, you will acquire skills to troubleshoot sewing issues and effectively handle challenges like sewing curves, working with multiple layers of leather, and managing stretchy, rough, or slippery surfaces. Moreover, you will receive valuable handouts, curated lists of leather and tool suppliers for future reference, and create personalised samples for your own use. By the end of the tuition, you will have: – Understood how to set and operate common leather industrial sewing machines, comprehended their differences and main features – Effectively threaded and operated a lock stitch walking foot machine, ensuring correct tension in your sewing – Utilised various tools, equipment and industry tricks proficiently in sewing – Identified thread types and needle sizes for different applications – Learned to sew leather accurately, distinguishing it from other materials, and mastered sewing thin versus thick leather – Sewn straight lines, curves, and parallel lines with confidence – Produced a variety of basic seams, seam finishes, constructions, continuous, and reinforced seams – Handled sewing multiple layers of leather -Successfully obtained fundamental knowledge to sew simple products independently Included in the course: You will receive useful paper handouts containing: – An illustrated guide providing essential information about types of sewing machines and their components. – A glossary containing information about needles, thread types and essential key words related to the topics of the lesson – A list of recommended suppliers for leather and fittings, both in London and online Find all modules here: https://the-london-leather-workshop.cademy.co.uk/

Search By Location
- Mac Courses in London
- Mac Courses in Birmingham
- Mac Courses in Glasgow
- Mac Courses in Liverpool
- Mac Courses in Bristol
- Mac Courses in Manchester
- Mac Courses in Sheffield
- Mac Courses in Leeds
- Mac Courses in Edinburgh
- Mac Courses in Leicester
- Mac Courses in Coventry
- Mac Courses in Bradford
- Mac Courses in Cardiff
- Mac Courses in Belfast
- Mac Courses in Nottingham
