- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
2892 Learning courses in Bradford delivered Live Online
Layer of Protection Analysis (LOPA)
By EnergyEdge - Training for a Sustainable Energy Future
Take your knowledge to the next level with EnergyEdge course on Layer of Protection Analysis (LOPA). Enroll now to advance your career.

This practitioner-level 4 award encourages individuals in IT and technical roles to explore the many teams, ideas, and functions within an organisation and maximise their contribution. You will achieve this by learning the key concepts and considering behaviour and response in different scenarios.

Management of Value (MoV) Practitioner: Virtual In-House Training
By IIL Europe Ltd
Management of Value (MoV®) Practitioner: Virtual In-House Training This interactive MoV® Practitioner course provides a modular and case-study-driven approach to learning Management of Value (MoV). The core knowledge is structured and comprehensive; and well-rounded modules cover the methodology and various techniques. A case study is used to help appreciate the relevance of MoV in its practical application. What you will Learn The MoV Practitioner Course prepares you for the MoV Practitioner exam. Individuals certified at the MoV Practitioner level will be able to: Apply Management of Value (MoV) principles, processes and techniques, and advocate the benefits of this application appropriately to the senior Management. Develop a plan of MoV activities for the whole lifecycle of small and large projects and programs. Plan an MoV study, tailoring it to particular projects or programs and developing practical study or workshop handbooks as required. Understand and articulate value in relation to organizational objectives. Prioritize value drivers using function analysis and use these to demonstrate how value might be improved. Quantify monetary and non-monetary value using the Value Index, Value Metrics and the Value for Money ratio. Describe and comment on the application of various techniques relevant to MoV. Monitor improvements in value realized throughout a project lifecycle and capture learning which can be transferred to future projects. Offer suggestions and guidance about embedding MoV into an organization, including policy issues, undertake a health check, assess maturity and competence, and provide guidance on typical roles and responsibilities. Understand and articulate the use of MoV within other Best Management Practice methods and its contributions to them Benefits of Taking This Course Upon successful completion of this course, you will be able to: Organise and contribute constructively to a Management of Value (MoV) Study Demonstrate a knowledge of MoV principles, processes, approach, and environment Analyse a company, programme or project to establish its organisational value includes identification and weighting of Value Drivers Pass the AXELOS Practitioner Examination Function Analysis Customer FAST Diagram Value Tree Development Weighting Attributes Paired Comparisons Developing a Value Profile Developing a Value Index Value for Money Ratio Stimulating Innovation Value Engineering Option Evaluation and Selection Evaluation Matrix Value and Value for Money Timing and Planning Teams and Stakeholders MoV in the Organization Integrating with Best Management Practice Relationship between Process and Approach

55399 Implementing and Managing Microsoft Intune
By Nexus Human
Duration 3 Days 18 CPD hours This three-day instructor-led course is aimed at modern device management professionals looking to manage their enterprise devices using Microsoft Intune. This course will cover Enrolment, Application Management, Endpoint Security and Windows Autopilot as well as Azure Active Directory Conditional Access and Identity Protection. The delegates will learn how to enroll devices, deploy applications and manage them to maximize user productivity and device security. 1: Introduction to Microsoft Intune Mobile Device Management Microsoft Intune Azure Active Directory AAD Identity Protection AAD Conditional Access 2: Microsoft Intune Device Management Enrolling Devices Device Compliance Device Profiles Device Updates 3: Microsoft Intune Application Management Application Management Deploying Applications Application Configuration Managing Applications Policy Sets and Guided Scenarios 4: Microsoft Intune Endpoint Security Security Baselines and tasks Antivirus Disk Encryption Firewall Atack Surface reduction Endpoint detection and response Account Protection 5: Deploying Windows with Windows Autopilot Windows Autopilot overview Preparing for Windows Autopilot deployment Deploying Windows 11 using Windows Autopilot 6: Microsoft Intune Additional and Premium Features Remote Help Tunnel for Mobile Application Management Endpoint Privilege Management Advanced Endpoint Analytics Additional course details: Nexus Humans 55399 Implementing and Managing Microsoft Intune training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55399 Implementing and Managing Microsoft Intune course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Level 7 Diploma In International Business Law Pathway To LLM International Business Law
4.9(261)By Metropolitan School of Business & Management UK
Level 7 Diploma In International Business Law Pathway To LLM International Business Law Level 7 Diploma in International Business Law (QCF) – 6 - 8 Months Credits: 120 Credits The objectives of the OTHM Level 7 Diploma in International Business Law qualification are to enable learners to gain knowledge and understanding of various branches of law, develop an analytical and critical approach to the application of the UK and International legal principles and understand the appropriateness of dealing with certain aspects of behaviour within the law.The qualification provides learners with an understanding of law in the context of business to equip them with the abilities needed to work with advanced issues.By the end of the qualification, learners will be able to: To understand a range of subjects in international business law. Develop an understanding of legal frameworks that govern international business transactions within the industry. Demonstrate an understanding of commercial trust law, company law, international trade law, intellectual property law, and the law of financial crimes. Develop research skills and have the ability to write on key areas in law. This programme is a Pathway programme to L.L.M Degree Accreditation All MSBM courses are accredited by the relevant partners and awarding bodies. Please refer to MSBM accreditation in about us for more details. University Progression University Top-up Upon completion of this course, students have the opportunity to complete a Master's degree programme from a range of UK universities. The top-up programme can be studied online or on campus. The top-up comprises the final 60 credits which consist of either a dissertation or a dissertation and one module. (The course tuition fee listed above does NOT include the top-up fees) University Progression Click here to see University routes and fee information for progression. Entry Requirements For entry onto the Level 7 Diploma in International Business Law leading to L.L.M qualification, learners must possess: An honours degree in a related subject or the UK level 6 diploma or equivalent overseas qualification i.e. Bachelors Degree or Higher National Diploma OR Mature learners (over 25) with at least 5 years of management experience if they do not possess the above qualification (this is reviewed on a case by case basis) Workshops Workshops are conducted by live webinars for all students. Visa Requirements There is no Visa requirement for this programme.

Level 7 Diploma In Accounting & Finance - Pathway To MSc Accounting & Finance Degree
4.9(261)By Metropolitan School of Business & Management UK
Level 7 Diploma In Accounting & Finance - Pathway To MSc Accounting & Finance Degree Level 7 Diploma in Accounting & Finance (QCF) – 6 - 8 Months Credits: 120 Credits This qualification is designed for learners who wish to pursue a career in the financial services industry, professional accountancy, banking, and finance or management. The qualification equips learners with the essential skills and knowledge needed to pursue high-level careers in all types of organizations in the public and private sector and within industry and commerce, both in the UK and abroad. The Level 7 Diploma in Accounting and Finance qualification also provides learners with the opportunity to work toward a relevant master’s programme with advanced standing. This programme is a Pathway programme to MSc Accounting & Finance Degree Course Details Assessment: Assignments Objectives: contemporary and specialized approaches to accountancy and finance key practical, theoretical and empirical issues, and academic research the complexity of the ever-changing legal framework in which the financial sector operates the latest developments in accountancy and reporting required by local, national and European governments. Accreditation All MSBM courses are accredited by the relevant partners and awarding bodies. Please refer to MSBM accreditation in about us for more details. University Progression University Top-up On completion of this course, students have the opportunity to complete a Master degree programme from a range of UK universities. The top-up programme can be studied online or on campus. The top-up comprises the final 60 credits which consist of either a dissertation or a dissertation and one module. (The course tuition fee listed above does NOT include the top-up fees) University Progression Click here to see University routes and fee information for progression. Entry Requirements For entry onto the Level 7 Diploma in Human Resource Management leading to the MA Human Resource Management qualification, learners must possess: An honours degree in related subject or UK level 6 diploma or equivalent overseas qualification i.e. Bachelors Degree or Higher National Diploma OR Mature learners (over 25) with at least 5 years of management experience if they do not possess the above qualification (this is reviewed on a case by case basis) Workshops Workshops are conducted by live webinars for all students. Visa Requirements There is no Visa requirement for this programme.

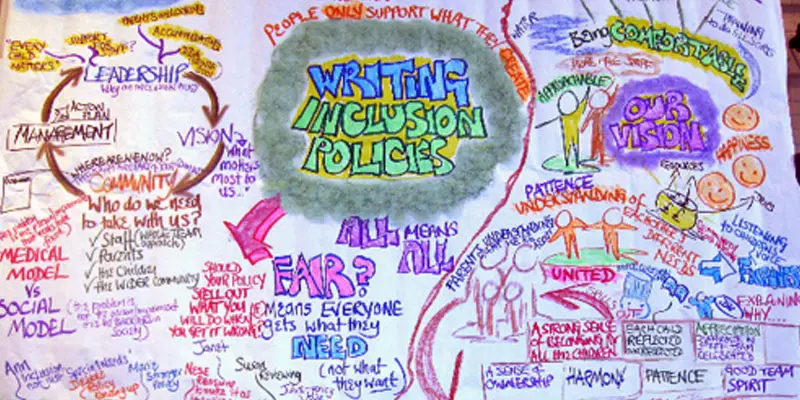
INCLUSION POLICIES
By Inclusive Solutions
This day is relevant to anyone involved in the task of developing an Inclusion Policy. How to create a real policy built around shared vision with true community commitment. Participate in this very practical workshop to take your first very real steps forward. The day gives those present opportunities to reflect on their attitudes and practice in relation to the inclusion of pupils who are different and the policy and practice which currently exist. Course Category Strategic Work Description This day is relevant to anyone involved in the task of developing an Inclusion Policy. How to create a real policy built around shared vision with true community commitment. Participate in this very practical workshop to take your first very real steps forward. The day gives those present opportunities to reflect on their attitudes and practice in relation to the inclusion of pupils who are different and the policy and practice which currently exist. Testimonials Be the first… Learning Objectives Increased confidence regarding developing an inclusion policy Understanding of essential steps to be taken to make inclusion policy a reality Deeper understanding of core values surrounding inclusion of disabled children Who Is It For? Anyone needing to create an inclusion policy Course Content The course answers the questions: Why an inclusion policy? What is the scope of an inclusion policy? How can an inclusion policy become a reality? How do I roll this out? We will cover: Legal and ethical background Local requirements Vision and Values Aims and Objectives Scope Evaluation and monitoring Complaints procedures Community involvement Consultation Implementation Practical steps If you like this you may like: KEYS TO INCLUSION
HV & MV Power System Design, Protection & Coordination - Virtual Instructor-Led Training (VILT)
By EnergyEdge - Training for a Sustainable Energy Future
Enhance your expertise in HV/MV power system design and protection coordination with EnergyEdge's virtual instructor-led training. Join now!

Petroleum Geology for Non-Geologists
By EnergyEdge - Training for a Sustainable Energy Future
About this Training Course To the non-geologist, working with Petroleum Geologists can be confusing. Petroleum geology has specific terminology and many concepts and data sources unfamiliar to the uninitiated. This course has been designed to introduce these terms and provide an insight into how oil and gas are formed, how they are found and how they are extracted. Using a holistic combination of lectures, experiments, case study and practical exercises, the course involves an introduction to fundamental geological concepts, to exploration techniques, prospecting, drilling, well logs and recovery methods. The course will also demystify the terminology surrounding petroleum geology, demonstrate the use of geological information to show the value and weakness of different datasets, and lead to better communication and decision-making between the geologists and non-geologists. It will feature world-class virtual reality field trips that incorporate activities and features unavailable in the physical field, and provide for a more integrated and flexible learning resource (also see the trainer's article on page 4 which was first published in GEO ExPro Magazine, the upstream oil and gas industry's favourite magazine). Course Highlights: Course facilitator has delivered petroleum geology training to many companies over the years Facilitator is also a professionally trained teacher and former university lecturer who is experienced in communicating with people at all levels of technical knowledge Practical exercises, experiments, examination of real rocks, a virtual reality field trip and case study are used to clarify and reinforce important concepts Training Objectives By attending this training, you will be able to acquire the following: Understand the geological methods and principles used in hydrocarbon exploration, development and production. Understand the key elements of a petroleum system, from hydrocarbon source to reservoir and seal Appreciate basin analysis, regional geology and play based exploration techniques Be aware of the different sorts of hydrocarbon trap from structural to stratigraphic Understand the technical terminology, tools and methods used in exploration geology Learn about unconventional Understand and evaluate the sources and reliability of various types of geological information Understand acquisition, processing and interpretation of seismic data Learn the technical processes and terminology involved in exploration Understand how a prospect is defined and risked Understand how seismic, existing well information and outcrop geology can be used for exploration Gain an understanding of the methods used for petroleum geology to allow a discovery to be appraised and then developed Target Audience The course is suitable to all personnel, but those that benefit most include: This course will benefit Petroleum Engineers (reservoir, drilling, production) who work with geological data, Geophysicists with little or no geological background, Project managers whose teams include petroleum geologists, Finance, Procurement, Marketing and Communications staff, and government Data Managers who handle petroleum geological data and need to understand the sources of different types of data. Trainer Your expert course leader is the Geosciences Technical Director for PetroEdge. She was previously, the manager of Robertson Petroleum Training Centre and a Senior Project Scientist at Robertson CGG. She has over 20 years of experience in teaching geology and leading field trips. Prior to her 8 years at Robertson, she was in academia as a lecturer for 6 years and a Research Fellow for 3 years. She has conducted fieldwork and led field trips in the US and many areas in the UK. In addition, she has led university regional geology day schools and has comprehensive experience in course and study programme writing. She has extensive experience in delivering courses and in Clastic and Carbonate Reservoir Geology, Deepwater Turbidites, Sandstone Reservoirs, Wireline Log Interpretation, Integrated Sequence Stratigraphy, Basin Analysis and Exploration & Appraisal workshops globally. In delivering the Exploration Team Management Workshop, she has project managed and taught key principles and modules on project planning, data collection/collation, geophysical assessment, stratigraphy and facies mapping, source rock facies and hydrocarbon generation, play fairway mapping, risking and prospect evaluation. Her knowledge and enthusiasm for instructing is reflected in consistently being rated as excellent by trainees, and clients specifically requesting her participation in courses. POST TRAINING COACHING SUPPORT (OPTIONAL) To further optimise your learning experience from our courses, we also offer individualized 'One to One' coaching support for 2 hours post training. We can help improve your competence in your chosen area of interest, based on your learning needs and available hours. This is a great opportunity to improve your capability and confidence in a particular area of expertise. It will be delivered over a secure video conference call by one of our senior trainers. They will work with you to create a tailor-made coaching program that will help you achieve your goals faster. Request for further information post training support and fees applicable Accreditions And Affliations

SC-100T00 Microsoft Cybersecurity Architect
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is for experienced cloud security engineers who have taken a previous certification in the security, compliance and identity portfolio. Specifically, students should have advanced experience and knowledge in a wide range of security engineering areas, including identity and access, platform protection, security operations, securing data, and securing applications. They should also have experience with hybrid and cloud implementations. Beginning students should instead take the course SC-900: Microsoft Security, Compliance, and Identity Fundamentals. This is an advanced, expert-level course. Although not required to attend, students are strongly encouraged to have taken and passed another associate level certification in the security, compliance and identity portfolio (such as AZ-500, SC-200 or SC-300) before attending this class. This course prepares students with the expertise to design and evaluate cybersecurity strategies in the following areas: Zero Trust, Governance Risk Compliance (GRC), security operations (SecOps), and data and applications. Students will also learn how to design and architect solutions using zero trust principles and specify security requirements for cloud infrastructure in different service models (SaaS, PaaS, IaaS). Prerequisites Highly recommended to have attended and passed one of the associate level certifications in the security, compliance and identity portfolio (such as AZ-500T00 Microsoft Azure Security Technologies, SC-200T00: Microsoft Security Operations Analyst, or SC-300T00: Microsoft Identity and Access Administrator.) Advanced experience and knowledge in identity and access, platform protection, security operations, securing data and securing applications. Experience with hybrid and cloud implementations. 1 - Introduction to Zero Trust and best practice frameworks Zero Trust initiatives Zero Trust technology pillars part 1 Zero Trust technology pillars part 2 2 - Design solutions that align with the Cloud Adoption Framework (CAF) and Well-Architected Framework (WAF) Define a security strategy Cloud Adoption Framework secure methodology Design security with Azure Landing Zones The Well-Architected Framework security pillar 3 - Design solutions that align with the Microsoft Cybersecurity Reference Architecture (MCRA) and Microsoft cloud security benchmark (MCSB) Design solutions with best practices for capabilities and controls Design solutions with best practices for attack protection 4 - Design a resiliency strategy for common cyberthreats like ransomware Common cyberthreats and attack patterns Support business resiliency Ransomware protection Configurations for secure backup and restore Security updates 5 - Case study: Design solutions that align with security best practices and priorities Case study description Case study answers Conceptual walkthrough Technical walkthrough 6 - Design solutions for regulatory compliance Translate compliance requirements into a security solution Address compliance requirements with Microsoft Purview Address privacy requirements with Microsoft Priva Address security and compliance requirements with Azure policy Evaluate infrastructure compliance with Defender for Cloud 7 - Design solutions for identity and access management Design cloud, hybrid and multicloud access strategies (including Azure AD) Design a solution for external identities Design modern authentication and authorization strategies Align conditional access and Zero Trust Specify requirements to secure Active Directory Domain Services (AD DS) Design a solution to manage secrets, keys, and certificates 8 - Design solutions for securing privileged access The enterprise access model Design identity governance solutions Design a solution to secure tenant administration Design a solution for cloud infrastructure entitlement management (CIEM) Design a solution for privileged access workstations and bastion services 9 - Design solutions for security operations Design security operations capabilities in hybrid and multicloud environments Design centralized logging and auditing Design security information and event management (SIEM) solutions Design solutions for detection and response Design a solution for security orchestration, automation, and response (SOAR) Design security workflows Design threat detection coverage 10 - Case study: Design security operations, identity and compliance capabilities Case study description Case study answers Conceptual walkthrough Technical walkthrough 11 - Design solutions for securing Microsoft 365 Evaluate security posture for collaboration and productivity workloads Design a Microsoft 365 Defender solution Design configurations and operational practices for Microsoft 365 12 - Design solutions for securing applications Design and implement standards to secure application development Evaluate security posture of existing application portfolios Evaluate application threats with threat modeling Design security lifecycle strategy for applications Secure access for workload identities Design a solution for API management and security Design a solution for secure access to applications 13 - Design solutions for securing an organization's data Design a solution for data discovery and classification using Microsoft Purview Design a solution for data protection Design data security for Azure workloads Design security for Azure Storage Design a security solution with Microsoft Defender for SQL and Microsoft Defender for Storage 14 - Case study: Design security solutions for applications and data Case study description Case study answers Conceptual walkthrough Technical walkthrough 15 - Specify requirements for securing SaaS, PaaS, and IaaS services Specify security baselines for SaaS, PaaS, and IaaS services Specify security requirements for web workloads Specify security requirements for containers and container orchestration 16 - Design solutions for security posture management in hybrid and multicloud environments Evaluate security posture by using Microsoft Cloud Security Benchmark Design integrated posture management and workload protection Evaluate security posture by using Microsoft Defender for Cloud Posture evaluation with Microsoft Defender for Cloud secure score Design cloud workload protection with Microsoft Defender for Cloud Integrate hybrid and multicloud environments with Azure Arc Design a solution for external attack surface management 17 - Design solutions for securing server and client endpoints Specify server security requirements Specify requirements for mobile devices and clients Specify internet of things (IoT) and embedded device security requirements Secure operational technology (OT) and industrial control systems (ICS) with Microsoft Defender for IoT Specify security baselines for server and client endpoints Design a solution for secure remote access 18 - Design solutions for network security Design solutions for network segmentation Design solutions for traffic filtering with network security groups Design solutions for network posture management Design solutions for network monitoring 19 - Case study: Design security solutions for infrastructure Case study description Case study answers Conceptual walkthrough Technical walkthrough Additional course details: Nexus Humans SC-100T00 Microsoft Cybersecurity Architect training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the SC-100T00 Microsoft Cybersecurity Architect course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.
