- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
45 Interpreting courses in Glasgow delivered Live Online
Business Soft Skills
By Nexus Human
Duration 1.5 Days 9 CPD hours This course is intended for This course is intended for individuals who want to gain basic knowledge communicating, etiquette, professionalism and time management for the office environment. Overview Upon successful completion of this course, students will be able to communicate, be professional and manage their time effectively in a business environment. In this course, students will learn how to communicate, act and manage time effective in a business environment. Getting Started Icebreaker Housekeeping Items The Parking Lot Workshop Objectives The Big Picture What is Communication? How Do We Communicate? Other Factors in Communication Understanding Communication Barriers An Overview of Common Barriers Language Barriers Cultural Barriers Differences in Time and Place Paraverbal Communication Skills The Power of Pitch The Truth about Tone The Strength of Speed Non-Verbal Communication Understanding the Mehrabian Study All About Body Language Interpreting Gestures Speaking like a Star S = Situation T = Task A = Action R = Result Summary Listening Skills Seven Ways to Listen Better Today Understanding Active Listening Sending Good Signals to Others Asking Good Questions Open Questions Closed Questions Probing Questions Appreciative Inquiry The Purpose of AI The Four Stages Examples and Case Studies Mastering the Art of Conversation Level One: Discussing General Topics Level Two: Sharing Ideas and Perspectives Level Three: Sharing Personal Experiences Our Top Networking Tips Advanced Communication Skills Understanding Precipitating Factors Establishing Common Ground Using ?I? Messages Wrapping Up Words from the Wise Review of Parking Lot Lessons Learned Completion of Action Plans and Evaluations Principles of Professional Behavior Always be Your Best Meeting and Greeting Sending Social Invitations to Business Associates Interview Etiquette Interviewing Before the Interview In the Waiting Room During the Interview After the Interview Job Fair Interviews Planning & Attending Business Meetings Office Meetings Meal Meetings Electronic Etiquette Voicemail Cell Phones Email Multiculture Etiquette Defining the Challenge Five Steps to Dealing with Diversity Guidelines for Managing Diverse Relationships Time Management Concepts Benefits of better time utilization Who controls your schedule? Your Job: What You Are Responsible for Accomplishing? Your job responsibilities Setting objectives Setting priorities How to Use Your Time Gathering data-the time log Analyzing the data Delegation: Working Through Others Why some people don't delegate Levels of delegation How to delegate Benefits of delegation Getting started Planning: Keys to Achievement Planning: Keys to Achievement Coping with Common Time Wasters Coping with self-generated time wasters Coping with environmental time wasters Personal Needs that Get in the Way of Effective Time Utilization Needs profile analysis Self-assessment questionnaire Applying needs assessment results Planning for Improvement Six tips for effective time management Planning for improved time utilization Follow-Up: Staying on Track Time savings progress report Time savings progress chart Time management progress survey Additional course details: Nexus Humans Business Soft Skills training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Business Soft Skills course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

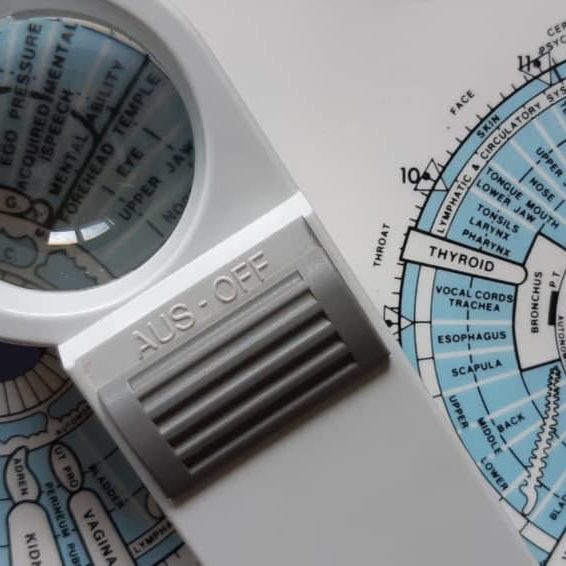
Iridology Diploma
By Plaskett International
LEARN HOW IRIDOLOGY CAN MAKE A HUGE CONTRIBUTION TO ANY COMPLEMENTARY PRACTICE A MESSAGE FROM THE AUTHOR I want to welcome you most warmly to the study of Iridology. Students of our course have taken their knowledge out into the world of practice and they have been able to see more penetratingly into the health of their patients. They have seen many truths about causes and effects in health and disease - that is what allows you to understand those extra things that make you into an even better healer. I think you are going to find this the most intriguing and absorbing study and, certainly, that is my sincere hope. As you precede, much of what you learn will amaze you and inspire wonder at the ways of the human body and mind. As you tread this very special road, I pass on to you the words that Bernard Jensen gave me years ago when I was his student, inscribed upon the inside cover of his book: “Seek the Higher Values in Life”. DR. LAWRENCE PLASKETT WHAT IS IRIDOLOGY? Iridology is the art of iris analysis. The iris is connected to the brain via the hypothalamus and can give naturopathic read outs on tissue conditions in various parts of the body. With training and practice it is possible to read signs indicative of biochemical, emotional and environmental influences that are hard to determine by other means. We can thus interpret health (and even aspects of personality) by close examination of the eyes, using suitable illumination and a magnifying glass. The close relationship between naturopathic iridology as an assessment tool and nutritional therapy and other naturopathic disciplines continues and grows closer. Now Iridology can make a huge contribution to complementary therapeutic practice and enhanced by our wonderful digital collection of eye photographs, the learning process with the Plaskett International College is a profound and exciting one. We teach Iridology quite separately from other topics and anyone who possesses, or expects to possess, a practitioner's qualification in any therapeutic discipline, may join the course. Course Duration 12 months Study Hours 200 hours Course Content 9 sections Course Fee £495 How Can Iridology Help Practitioners? Examples of how iridology can help practitioners Did you know that some iris features are so very plain that you can see them with the naked eye in ordinary social contact? You can see from two or three feet away in many cases that the person has a toxic digestive system (a strong wide dark ring around the pupil margin). You can often tell that the person has an overactive stomach (a narrow bright white ring very close to the pupil). You can tell when the skin is overlaid with toxins so that the skin's function in excreting toxins from the body is jeopardised (very narrow dark ring around the iris margin). You can tell in some people (rather advanced cases) that they suffer badly from sodium and potassium imbalance and have placed themselves at potential risk from cholesterol accumulation (the so-called corneal arcus, a white or off-white cloudy deposit, usually fairly thick, around the iris margin). Another example is the ring of spots or 'tophi' represented by the lymphatic rosary. Its mere presence tells one that there is sluggishness in the lymphatic system. When these tophi are darkly pigmented, the situation gives rise to concern for the possible generation of lymphatic illness. Using the precise positioning of iris reflex areas contained on the iris chart, one may distinguish many key points of analysis. Areas of stress and tension can be pinpointed by identifying 'contraction furrows’. Past injuries and adhesions show themselves as contortions of the normally regular and even iris fibres. You can answer questions like:- Is it the pancreas or the liver that is responsible for the trouble? Is the patient's hypertension caused by a defect of or toxic deposits in the particular brain area that is geared to control blood pressure? One of Jensen's rather dramatic illustrations is of the iris of a man who has just been shot. It shows the precise areas of tissue damage within the body and the response is very fast. The number of potential examples is almost without limit. The above may suffice to show the types of things that iridology can do for practitioners. We hope it will help you decide to study Iridology with the Plaskett International College. Course Overview The course covers the nature of iris observation, the nutritive zone, the iris chart, the chronic and acute, the intestinal and stomach zones and nerve collarette, the constitution type, respiratory system, lacunae, open lacuna, inherent weaknesses, the organs of elimination, other organs, special signs, complete diagnosis of a subject. The treatment of the topic follows the principles of Bernard Jensen in the USA. Once the basics have been learnt, the course teachings then extend considerably by bringing in the work of Dorothy Hall and of Dr Josef Deck, both of which are the subject of a special presentation during the course. The published insights of Farida Sharan and Harri Wolf, while not separately presented, also influence the presentation of the course material. Both the Australian School, (Dorothy Hall) and the German School, (Dr Deck/Harri Wolf), offer an added dimension to the study and interpretation of the constitution. PERSONALITY ASPECTS & CONSTITUTIONAL TYPES The study focuses upon the different personality aspects, which show up in different constitutional types. Dorothy Hall gives insights into what contributes to various different types of personality and their emotional and mental responses and their pre-dispositions to health or disease. Different sorts of people can have different priorities, preferences and imperatives built into their very nature from or before birth, sometimes determining the course of their entire lives and their attitudes to the world and to other people. AN EMPATHY BETWEEN PATIENT & PRACTITIONER The course teaches an understanding of these types and facilitates an empathy between patient and practitioner. It shows how people of the differing constitutional types are likely to go out of balance either mentally or emotionally and how their vulnerability to various physical ailments varies. The German School offers a very exciting and precise approach to the constitutional types, which is really quite different, but no less helpful. It highlights variations in the susceptibility to diseases of different organs and systems. THE 3 SCHOOLS OF THOUGHT It is a prime purpose of this course, not only to teach these differing positions, but also to demonstrate how it is that all three of these major schools of Iridology embody different aspects of the truth, how each is individually valuable and how a full and deep understanding of the meaning of 'constitution' can be gained through a sympathetic synthesis of the contributions from all three of these schools. BREAKDOWN OF THE COURSE SECTIONS In total there are 9 sections comprising of text, videos and iris images to study: SECTION 1 GENERAL PRACTICE AND AN ACCOUNT OF THE NUTRITIVE ZONE Areas Covered Iris colour Information that iridology can give us The structure of the eye and the iris Using the iris as an assessment tool The principle of reflex areas The Nutritive Zone Abnormality in the colon The Collarette (autonomic nerve wreath or anw) Diagnosis of the constitution based upon fibre structure Studies on images of real eyes SECTION 2 FEATURES OF THE FIBRES OUTSIDE THE COLLARETTE Areas Covered The general layout of fibres outside the collarette Inherent weaknesses First stage in further deterioration of an inherent weakness The meaning of darkness in the iris The development of discrete – open lacunae Lacunae Further notes about lightness and darkness amongst the fibres Healing lines Crypts Round the iris chart – the left iris Round the iris chart – the right iris Checking which structures and inside and which outside the collarette The organ systems The neural arc reflex SECTION 3 SPECIAL SIGNS Areas covered The corneal arcus (sodium ring, cholesterol ring, lipemic ring) The tophi (also lymphatic tophi or lymphatic rosary) Corneal Arcus The anaemia sign The catarrhal sign Acidity Grey background Scurf rim Circulatory ring Sphincter muscle (also called pupillary sphincter) Pigments (topastible or topolabile) Psoric spots Contrcation furrows Radial furrows SECTION 4 THE CONSTITUTIONS IN RELATION TO PERSONALITY TYPE AND DISEASE DISPOSITION Areas covered Very resilient Resilient average Moderately resilient Mildly resilient SECTION 5 MORE ABOUT WHITE SIGNS Areas covered Revision of distinctions between the different white signs Pictures of irises with white signs, with commentaries Further interpretation of the corneal arcus Further interpretation of the lytophi More general interpretation of the colour white SECTION 6 COLOURS IN THE IRIS AND OTHER SPECIAL SIGNS Areas Covered Yellow pigment in the iris Orange pigment Brown pigment Contraction furrows Radial furrows Psoric spots Pupillary border The “friendly fibrils” sign Summary of remedies SECTION 7 THE CONSTITUTION AND SIGNS ACCORDING TO THE GERMAN SCHOOL Areas Covered The German school of iridology Our approach to teaching the German school Introduction to the German constitutional types The lymphatic constitutions Mixed biliary constitution or biliary constitution Haematogenic (or haematogenous) constitution The way to use information on the German constitutions New signs that are specific to the German school Treatment recommendations for constitutional types SECTION 8 ADVANCED STUDIES OF THE IRIS Areas Covered Further details of the iris chart – its layout and its implications Neural arc reflex Deformation of pupil shape and position Advanced study of fibre separations, sinuosity, injuries & adhesions Lacunae of different shape and appearance The b3 bulge and the pterygium Working with genetically brown eyes SECTION 9 THE CONSULTATION & THE PRACTICALITIES Areas Covered Diagnosing pathology of individual critical organs Personality interpretations based upon the German school Conducting an iridology consultation Practical aspects of iris examination Making drawings of the iris and recording the data The uses, advantages and limitations of iris photography and its place in iridology practice Equipments and techniques of iris photography Using the computer to store and process digital images The interaction of signs Interpreting the whole iris in conjunction with the case study Pointers to treatment Carrying out case histories TESTIMONIALS Here's what students have to say about the course Emma Rubio, Health Coach Spain "As a Health Coach I decided to pursue my studies with the Plaskett College to become a Nutritional Therapist. For that, I am also studying Iridology. I am happy to have a tutor to answer my doubts and I like the flexibility that the College offers me. I love the subject of Iridology and the way it is explained, I also like having some videos of Dr Plaskett teaching Iridology as I admire him." Dr Ezequiel Lafontaine, Iridologist Puerto Rico "I LOVE IRIDOLOGY. I have over 30 iridology books, Italian, French, German, Spanish and English, plus over 4,000 photos from my own practice. I took this course for a refresher course and found the material was second to none." Mrs D. Moothy, Nutritional Therapist Mauritius “The distance learning courses have given me the opportunity to pursue my dreams through a program that was not only flexible and convenient for my schedule, but was also challenging and rewarding. I thoroughly enjoyed the readings and the assignments but most importantly, I enjoyed being able to do things at my pace. I must say that the most exciting and challenging course was the Iridology Diploma, and I am happy that I was able to do well in all the courses."
Quick Start to Mastering Prompt Engineering for Software Developers (TTAI2300)
By Nexus Human
Duration 1 Days 6 CPD hours This course is intended for To gain the most from attending this course you should possess the following incoming skills: Basic knowledge of programming concepts and syntax in Python. Familiarity with common data formats such as CSV, JSON, and XML. Experience using command-line interfaces and basic text editing tools. Understanding of basic machine learning concepts and algorithms. Overview Working in an interactive learning environment, led by our engaging expert, you will: Gain a solid understanding of prompt engineering concepts and their applications in software development and AI-driven solutions. Master the techniques for preprocessing and cleaning text data to ensure high-quality inputs for AI models like GPT-4. Develop expertise in GPT-4 tokenization, input formatting, and controlling model behavior for various tasks and requirements. Acquire the ability to design, optimize, and test prompts effectively, catering to diverse business applications and use cases. Learn advanced prompt engineering techniques, such as conditional text generation and multi-turn conversations, to create more sophisticated AI solutions. Practice creating prompts to generate, run, and test code in a chosen programming language using GPT-4 and OpenAI Codex. Understand the ethical implications and best practices in responsible AI deployment, ensuring fair and unbiased AI applications in software development. Prompt Engineering offers coders and software developers a competitive edge by empowering them to develop more effective and efficient AI-driven solutions in their projects. By harnessing the capabilities of cutting-edge AI models like GPT-4, coders can automate repetitive tasks, enhance natural language understanding, and even generate code suggestions, boosting productivity and creativity. In addition, mastering prompt engineering can contribute to improved job security, as professionals with these in-demand skills are highly sought after in the rapidly evolving tech landscape. Quick Start to Prompt Engineering for Coders and Software Developers is a one day course designed to get you quickly up and running with the prompting skills required to out AI to work for you in your development efforts. Guided by our AI expert, you?ll explore key topics such as text preprocessing, data cleansing, GPT-4 tokenization, input formatting, prompt design, and optimization, as well as ethical considerations in prompt engineering. In the hands-on labs you?ll explore tasks such as formatting inputs for GPT-4, designing and optimizing prompts for business applications, and implementing multi-turn conversations with AI. You?ll work with innovative tools like the OpenAI API, OpenAI Codex, and OpenAI Playground, enhancing your learning experience while preparing you for integrating prompt engineering into your professional toolkit. By the end of this immersive course, you?ll have the skills necessary to effectively use prompt engineering in your software development projects. You'll be able to design, optimize, and test prompts for various business tasks, integrate GPT-4 with other software platforms, and address ethical concerns in AI deployment. Introduction to Prompt Engineering Overview of prompt engineering and its importance in AI applications Major applications of prompt engineering in business Common challenges faced in prompt engineering Overview of GPT-4 and its role in prompt engineering Key terminology and concepts in prompt engineering Getting Things Ready: Text Preprocessing and Data Cleansing Importance of data preprocessing in prompt engineering Techniques for text cleaning and normalization Tokenization and n-grams Stop word removal and stemming Regular expressions and pattern matching GPT-4 Tokenization and Input Formatting GPT-4 tokenization and its role in prompt engineering Understanding and formatting GPT-4 inputs Context windows and token limits Controlling response length and quality Techniques for handling out-of-vocabulary tokens Prompt Design and Optimization Master the skills to design, optimize, and test prompts for various business tasks. Designing effective prompts for different tasks Techniques for prompt optimization GPT-4 system and user parameters for controlling behavior Importance of prompt testing and iteration Best practices for prompt engineering in business applications Advanced Techniques and Tools in Prompt Engineering Learn advanced techniques and tools for prompt engineering and their integration in business applications. Conditional text generation with GPT-4 Techniques for handling multi-turn conversations Overview of tools for prompt engineering: OpenAI API, OpenAI Codex, and OpenAI Playground Integration of GPT-4 with other software platforms and tools Monitoring and maintaining prompt performance Code Generation and Testing with Prompt Engineering Develop the skills to generate, integrate, and test AI-generated code effectively, enhancing productivity and creativity in software development projects. Introduction to code generation with AI models like GPT-4 Designing prompts for code generation across programming languages Techniques for specifying requirements and constraints in prompts Generating and interpreting code snippets using AI-driven solutions Integrating generated code into existing projects and codebases Best practices for testing and validating AI-generated code Ethics and Responsible AI Understand the ethical implications of prompt engineering and the importance of responsible AI deployment in business. Ethical considerations in prompt engineering Bias in AI systems and its impact on prompt engineering Techniques to minimize bias and ensure fairness Best practices for responsible AI deployment in business applications Monitoring and addressing ethical concerns in prompt engineering

Oracle Database 12c R2 - Backup and Recovery Workshop Ed 3
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Data Warehouse Administrator Database Administrators Support Engineer Technical Administrator Technical Consultant Overview Use Oracle Flashback Technologies to recover from human error Use Recovery Manager (RMAN) to create backups and perform recovery operations Use the Data Recovery Advisor to diagnose and repair failures Plan effective backup and recovery procedures Describe the Oracle Database architecture components related to backup and recovery operations Perform an encrypted database backup and restore Perform tablespace point-in-time recovery Configure the database for recoverability Describe Cloud Tooling for Backup and Recovery Describe Oracle Database backup methods and recovery operations that can be used to resolve database failure In this Oracle Database 12c R2: Backup and Recovery Workshop, students learn how to perform backup and recovery based on the related Oracle Database architecture components. Various backup, failure, restore, and recovery scenarios are provided so that students learn to evaluate their own recovery requirements and develop an appropriate strategy for backup and recovery procedures. This course includes an interactive workshop, with scenarios that provide participants with opportunities to diagnose and recover from several failure situations. Introduction Curriculum Context Assess your recovery requirements Categories of failures Oracle backup and recovery solutions Oracle Maximum Availability Architecture Oracle Secure Backup Benefits of using Oracle Data Guard Basic Workshop Architecture Getting Started Core Concepts of the Oracle Database, critical for Backup and Recovery Oracle DBA Tools for Backup and Recovery Connecting to Oracle Recovery Manager (RMAN) Configuring for Recoverablility RMAN commands Configuring and managing persistent settings Using the Fast Recovery Area (FRA) Control File Redo Log File Archiving Logs Using the RMAN Recovery Catalog Creating and Configuring the Recovery Catalog Managing Target Database Records in the Recovery Catalog Using RMAN Stored Scripts Maintaining and Protecting the Recovery Catalog Virtual Private Catalogs Backup Strategies and Terminology Backup Solutions Overview and Terminology Balancing Backup and Restore Requirements Backing Up Read-Only Tablespaces Data Warehouse Backup and Recovery: Best Practices Additional Backup Terminology Performing Backups RMAN Backup Types Incrementally Updated Backups Fast Incremental Backup Block Change Tracking Oracle-Suggested Backup Reporting on Backups Managing Backups Improving Your Backups Compressing Backups Using a Media Manager Backup and Restore for Very Large Files Creating RMAN Multi-section Backups, Proxy Copies, Duplexed Backup Sets and Backups of Backup Sets Creating and Managing Archival Backups Backing Up Recovery Files Backing Up the Control File to a Trace File Cataloging Additional Backup Files Using RMAN-Encrypted Backups Creating RMAN-Encrypted Backups Using Transparent-Mode Encryption Using Password-Mode Encryption Using Dual-Mode Encryption Diagnosing Failures Reducing Problem Diagnosis Time Automatic Diagnostic Repository Data Recovery Advisor Handling Block Corruption Restore and Recovery Concepts Restoring and Recovering Instance Failure and Instance/Crash Recovery Media Failure Complete Recovery (Overview) Point-in-Time Recovery (Overview) Recovery with the RESETLOGS Option Performing Recovery, Part I RMAN Recovery in NOARCHIVELOG Mode Performing Complete Recovery (of critical and noncritical data files) Restoring ASM Disk Groups Recovery with Image Files Performing Point-in-Time (PITR) or Incomplete Recovery Performing Recovery, Part II Recovery of Server Parameter File, Control File (One and All) Redo Log File Loss and Recovery Password Authentication File Re-creation Index, Read-Only Tablespace, and Temp file Recovery Restoring the Database to a New Host Disaster Recovery Restoring RMAN Encrypted Backups RMAN and Oracle Secure Backup Oracle Secure Backup Overview and Interface Options RMAN and OSB: Overview and Basic Process Flow Starting with Oracle Secure Backup Configuring Oracle Secure Backup for RMAN RMAN Backup and Restore Operations Oracle Secure Backup Jobs Displaying OSB log files and transcripts for RMAN activities Using Flashback Technologies Flashback Technology: Overview and Setup Using Flashback Technology to Query Data Flashback Table Flashback Transaction (Query and Back out) Flashback Drop and the Recycle Bin Flashback Data Archive Using Flashback Database Flashback Database Architecture Configuring Flashback Database Performing Flashback Database Best Practices for Flashback Database Transporting Data Transporting Data Across Platforms Transporting Data with Backup Sets Database Transport: Using Data Files Performing Point-in-Time Recovery When to use TSPITR TSPITR Architecture Performing RMAN TS Point-in-time Recovery Recovering Tables from Backups Duplicating a Database Using a Duplicate Database Duplicating Database with 'push' and 'pull' techniques Choosing Database Duplication Techniques Creating a Backup-up Based Duplicate Database Understanding the RMAN Duplication Operation RMAN Troubleshooting and Tuning Interpreting RMAN Message Output Tuning Principles Diagnosing Performance Bottlenecks RMAN Multiplexing Restore and Recovery Performance Best Practices Cloud Tooling for Backup and Recovery Backup Destinations Customize Backup Configuration On-Demand Backup and Recovery Oracle Backup Cloud Service Installing the Backup Module Backup and Recovery Workshop Workshop Structure and Approach Business Requirements for Database Availability and Procedures Diagnosing the Failures

F5 Networks Configuring BIG-IP Advanced WAF - Web Application Firewall (formerly ASM)
By Nexus Human
Duration 4 Days 24 CPD hours This course is intended for This course is intended for security and network administrators who will be responsible for the installation, deployment, tuning, and day-to-day maintenance of the F5 Advanced Web Application Firewall. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTP-based attacks. The course includes lecture, hands-on labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. Module 1: Setting Up the BIG-IP System Introducing the BIG-IP System Initially Setting Up the BIG-IP System Archiving the BIG-IP System Configuration Leveraging F5 Support Resources and Tools Module 2: Traffic Processing with BIG-IP Identifying BIG-IP Traffic Processing Objects Overview of Network Packet Flow Understanding Profiles Overview of Local Traffic Policies Visualizing the HTTP Request Flow Module 3: Web Application Concepts Overview of Web Application Request Processing Web Application Firewall: Layer 7 Protection F5 Advanced WAF Layer 7 Security Checks Overview of Web Communication Elements Overview of the HTTP Request Structure Examining HTTP Responses How F5 Advanced WAF Parses File Types, URLs, and Parameters Using the Fiddler HTTP Proxy Module 4: Common Web Application Vulnerabilities A Taxonomy of Attacks: The Threat Landscape What Elements of Application Delivery are Targeted? Common Exploits Against Web Applications Module 5: Security Policy Deployment Defining Learning Comparing Positive and Negative Security Models The Deployment Workflow Policy Type: How Will the Policy Be Applied Policy Template: Determines the Level of Protection Policy Templates: Automatic or Manual Policy Building Assigning Policy to Virtual Server Deployment Workflow: Using Advanced Settings Selecting the Enforcement Mode The Importance of Application Language Configure Server Technologies Verify Attack Signature Staging Viewing Requests Security Checks Offered by Rapid Deployment Defining Attack Signatures Using Data Guard to Check Responses Module 6: Policy Tuning and Violations Post-Deployment Traffic Processing Defining Violations Defining False Positives How Violations are Categorized Violation Rating: A Threat Scale Defining Staging and Enforcement Defining Enforcement Mode Defining the Enforcement Readiness Period Reviewing the Definition of Learning Defining Learning Suggestions Choosing Automatic or Manual Learning Defining the Learn, Alarm and Block Settings Interpreting the Enforcement Readiness Summary Configuring the Blocking Response Page Module 7: Attack Signatures & Threat Campaigns Defining Attack Signatures Attack Signature Basics Creating User-Defined Attack Signatures Defining Simple and Advanced Edit Modes Defining Attack Signature Sets Defining Attack Signature Pools Understanding Attack Signatures and Staging Updating Attack Signatures Defining Threat Campaigns Deploying Threat Campaigns Module 8: Positive Security Policy Building Defining and Learning Security Policy Components Defining the Wildcard Defining the Entity Lifecycle Choosing the Learning Scheme How to Learn: Never (Wildcard Only) How to Learn: Always How to Learn: Selective Reviewing the Enforcement Readiness Period: Entities Viewing Learning Suggestions and Staging Status Violations Without Learning Suggestions Defining the Learning Score Defining Trusted and Untrusted IP Addresses How to Learn: Compact Module 9: Cookies and Other Headers F5 Advanced WAF Cookies: What to Enforce Defining Allowed and Enforced Cookies Configuring Security Processing on HTTP headers Module 10: Reporting and Logging Overview: Big Picture Data Reporting: Build Your Own View Reporting: Chart based on filters Brute Force and Web Scraping Statistics Viewing F5 Advanced WAF Resource Reports PCI Compliance: PCI-DSS 3.0 The Attack Expert System Viewing Traffic Learning Graphs Local Logging Facilities and Destinations How to Enable Local Logging of Security Events Viewing Logs in the Configuration Utility Exporting Requests Logging Profiles: Build What You Need Configuring Response Logging Module 11: Lab Project 1 Lab Project 1 Module 12: Advanced Parameter Handling Defining Parameter Types Defining Static Parameters Defining Dynamic Parameters Defining Dynamic Parameter Extraction Properties Defining Parameter Levels Other Parameter Considerations Module 13: Automatic Policy Building Overview of Automatic Policy Building Defining Templates Which Automate Learning Defining Policy Loosening Defining Policy Tightening Defining Learning Speed: Traffic Sampling Defining Track Site Changes Lesson 14: Web Application Vulnerability Scanner Integration Integrating Scanner Output Importing Vulnerabilities Resolving Vulnerabilities Using the Generic XML Scanner XSD file Lesson 15: Deploying Layered Policies Defining a Parent Policy Defining Inheritance Parent Policy Deployment Use Cases Lesson 16: Login Enforcement and Brute Force Mitigation Defining Login Pages for Flow Control Configuring Automatic Detection of Login Pages Defining Session Tracking Brute Force Protection Configuration Source-Based Brute Force Mitigations Defining Credentials Stuffing Mitigating Credentials Stuffing Lesson 17: Reconnaissance with Session Tracking Defining Session Tracking Configuring Actions Upon Violation Detection Lesson 18: Layer 7 DoS Mitigation Defining Denial of Service Attacks Defining the DoS Protection Profile Overview of TPS-based DoS Protection Creating a DoS Logging Profile Applying TPS Mitigations Defining Behavioral and Stress-Based Detection Lesson 19: Advanced Bot Protection Classifying Clients with the Bot Defense Profile Defining Bot Signatures Defining Proactive Bot Defense Defining Behavioral and Stress-Based Detection Defining Behavioral DoS Mitigation Lesson 20: Form Encryption using DataSafe Targeting Elements of Application Delivery Exploiting the Document Object Model Protecting Applications Using DataSafe The Order of Operations for URL Classification Lesson 21: Review and Final Labs Review and Final Labs

Information Assurance (STIG) Overview (TT8800)
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for The intended audience for this comprehensive course on Information Assurance and STIGs includes professionals with roles such as: IT professionals - System administrators, network engineers, and security analysts who are responsible for maintaining and securing IT infrastructure and web applications. Developers - Software engineers and web developers who design, implement, and maintain web applications, and need to integrate security best practices throughout the development process. Project teams - Cross-functional teams that collaborate on application development projects, including members from development, testing, and deployment teams. Technical leads - Senior software engineers or architects who oversee technical aspects of projects and ensure the implementation of secure design and coding practices. Project managers - Professionals responsible for planning, executing, and closing projects, ensuring that security requirements are met throughout the project lifecycle. Overview Working in an interactive learning environment, guided by our application security expert, you'll explore: The concepts and terminology behind defensive coding Threat Modeling as a tool in identifying software vulnerabilities based on realistic threats against meaningful assets The entire spectrum of threats and attacks that take place against software applications in today's world The role that static code reviews and dynamic application testing to uncover vulnerabilities in applications The vulnerabilities of programming languages as well as how to harden installations The basics of Cryptography and Encryption and where they fit in the overall security picture The requirements and best practices for program management as specified in the STIGS The processes and measures associated with the Secure Software Development (SSD) The basics of security testing and planning Understand the concepts and terminology behind defensive coding Understand Threat Modeling as a tool in identifying software vulnerabilities based on realistic threats against meaningful assets Learn the entire spectrum of threats and attacks that take place against software applications in today's world Discuss the role that static code reviews and dynamic application testing to uncover vulnerabilities in applications Understand the vulnerabilities of programming language as well as how to harden installations Understand the basics of Cryptography and Encryption and where they fit in the overall security picture Understand the fundamentals of XML Digital Signature and XML Encryption as well as how they are used within the web services arena Understand the requirements and best practices for program management as specified in the STIGS Understand the processes and measures associated with the Secure Software Development (SSD) Understand the basics of security testing and planning The Information Assurance (STIG) Overview is a comprehensive two-day course that delves into the realm of Information Assurance, empowering you to enhance your cybersecurity skills, understand the essentials of STIGs, and discover cutting-edge web application security practices. This immersive experience is tailored for IT professionals, developers, project teams, technical leads, project managers, testing/QA personnel, and other key stakeholders who seek to expand their knowledge and expertise in the evolving cybersecurity landscape. The course focuses on the intricacies of best practices for design, implementation, and deployment, inspired by the diverse and powerful STIGs, ultimately helping participants become more proficient in application security.The first half of the course covers the foundations of DISA's Security Technical Implementation Guides (STIGs) and learn the ethical approach to bug hunting, while exploring the language of cybersecurity and dissecting real-life case studies. Our expert instrtors will guide you through the importance of respecting privacy, working with bug bounty programs, and avoiding common mistakes in the field.The next half delves into the core principles of information security and application protection, as you learn how to identify and mitigate authentication failures, SQL injections, and cryptographic vulnerabilities. You?ll gain experience with STIG walkthroughs and discover the crucial steps for securing web applications.Throughout the course, you'll also explore the fundamentals of application security and development, including checklists, common practices, and secure development lifecycle (SDL) processes. You?ll learn from recent incidents and acquire actionable strategies to strengthen your project teams and IT organizations. You'll also have the opportunity to explore asset analysis and design review methodologies to ensure your organization is prepared to face future cybersecurity challenges. DISA's Security Technical Implementation Guides (STIGs) The motivations behind STIGs Requirements that the various software development roles must meet Implementing STIG requirements and guidelines Why Hunt Bugs? The Language of CyberSecurity The Changing Cybersecurity Landscape AppSec Dissection of SolarWinds The Human Perimeter Interpreting the 2021 Verizon Data Breach Investigation Report First Axiom in Web Application Security Analysis First Axiom in Addressing ALL Security Concerns Lab: Case Study in Failure Safe and Appropriate Bug Hunting/Hacking Working Ethically Respecting Privacy Bug/Defect Notification Bug Bounty Programs Bug Hunting Mistakes to Avoid Principles of Information Security Secuity Is a Lifecycle Issue Minimize Attack Surface Area Layers of Defense: Tenacious D Compartmentalize Consider All Application States Do NOT Trust the Untrusted Identification and Authentication Failures Applicable STIGs Quality and Protection of Authentication Data Proper hashing of passwords Handling Passwords on Server Side Session Management HttpOnly and Security Headers Lab: STIG Walk-Throughs Injection Applicable STIGs Injection Flaws SQL Injection Attacks Evolve Drill Down on Stored Procedures Other Forms of Server-Side Injection Minimizing Injection Flaws Client-side Injection: XSS Persistent, Reflective, and DOM-Based XSS Best Practices for Untrusted Data Lab: STIG Walk-Throughs Applications: What Next? Common Vulnerabilities and Exposures CWE/SANS Top 25 Most Dangerous SW Errors Strength Training: Project Teams/Developers Strength Training: IT Organizations Cryptographic Failures Applicable STIGs Identifying Protection Needs Evolving Privacy Considerations Options for Protecting Data Transport/Message Level Security Weak Cryptographic Processing Keys and Key Management Threats of Quantum Computing Steal Now, Crack Later Threat Lab: STIG Walk-Throughs Application Security and Development Checklists Checklist Overview, Conventions, and Best Practices Leveraging Common AppSec Practices and Control Actionable Application Security Additional Tools for the Toolbox Strength Training: Project Teams/Developers Strength Training: IT Organizations Lab: Recent Incidents SDL Overview Attack Phases: Offensive Actions and Defensive Controls Secure Software Development Processes Shifting Left Actionable Items Moving Forward Lab: Design Study Review Asset Analysis Asset Analysis Process Types of Application-Related Assets Adding Risk Escalators Discovery and Recon Design Review Asset Inventory and Design Assets, Dataflows, and Trust Boundaries Risk Escalators in Designs Risk Mitigation Options

AWS Developing Serverless Solutions on AWS
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for Developers who have some familiarity with serverless and experience with development in the AWS Cloud Overview In this course, you will learn to: Apply event-driven best practices to a serverless application design using appropriate AWS services Identify the challenges and trade-offs of transitioning to serverless development, and make recommendations that suit your development organization and environment Build serverless applications using patterns that connect AWS managed services together, and account for service characteristics, including service quotas, available integrations, invocation model, error handling, and event source payload Compare and contrast available options for writing infrastructure as code, including AWS CloudFormation, AWS Amplify, AWS Serverless Application Model (AWS SAM), and AWS Cloud Development Kit (AWS CDK) Apply best practices to writing Lambda functions inclusive of error handling, logging, environment re-use, using layers, statelessness, idempotency, and configuring concurrency and memory Apply best practices for building observability and monitoring into your serverless application Apply security best practices to serverless applications Identify key scaling considerations in a serverless application, and match each consideration to the methods, tools, or best practices to manage it Use AWS SAM, AWS CDK, and AWS developer tools to configure a CI/CD workflow, and automate deployment of a serverless application Create and actively maintain a list of serverless resources that will assist in your ongoing serverless development and engagement with the serverless community This course gives developers exposure to and practice with best practices for building serverless applications using AWS Lambda and other services in the AWS serverless platform. You will use AWS frameworks to deploy a serverless application in hands-on labs that progress from simpler to more complex topics. You will use AWS documentation throughout the course to develop authentic methods for learning and problem-solving beyond the classroom. Introduction Introduction to the application you will build Access to course resources (Student Guide, Lab Guide, and Online Course Supplement) Thinking Serverless Best practices for building modern serverless applications Event-driven design AWS services that support event-driven serverless applications API-Driven Development and Synchronous Event Sources Characteristics of standard request/response API-based web applications How Amazon API Gateway fits into serverless applications Try-it-out exercise: Set up an HTTP API endpoint integrated with a Lambda function High-level comparison of API types (REST/HTTP, WebSocket, GraphQL) Introduction to Authentication, Authorization, and Access Control Authentication vs. Authorization Options for authenticating to APIs using API Gateway Amazon Cognito in serverless applications Amazon Cognito user pools vs. federated identities Serverless Deployment Frameworks Overview of imperative vs. declarative programming for infrastructure as code Comparison of CloudFormation, AWS CDK, Amplify, and AWS SAM frameworks Features of AWS SAM and the AWS SAM CLI for local emulation and testing Using Amazon EventBridge and Amazon SNS to Decouple Components Development considerations when using asynchronous event sources Features and use cases of Amazon EventBridge Try-it-out exercise: Build a custom EventBridge bus and rule Comparison of use cases for Amazon Simple Notification Service (Amazon SNS) vs. EventBridge Try-it-out exercise: Configure an Amazon SNS topic with filtering Event-Driven Development Using Queues and Streams Development considerations when using polling event sources to trigger Lambda functions Distinctions between queues and streams as event sources for Lambda Selecting appropriate configurations when using Amazon Simple Queue Service (Amazon SQS) or Amazon Kinesis Data Streams as an event source for Lambda Try-it-out exercise: Configure an Amazon SQS queue with a dead-letter queue as a Lambda event source Writing Good Lambda Functions How the Lambda lifecycle influences your function code Best practices for your Lambda functions Configuring a function Function code, versions and aliases Try-it-out exercise: Configure and test a Lambda function Lambda error handling Handling partial failures with queues and streams Step Functions for Orchestration AWS Step Functions in serverless architectures Try-it-out exercise: Step Functions states The callback pattern Standard vs. Express Workflows Step Functions direct integrations Try-it-out exercise: Troubleshooting a Standard Step Functions workflow Observability and Monitoring The three pillars of observability Amazon CloudWatch Logs and Logs Insights Writing effective log files Try-it-out exercise: Interpreting logs Using AWS X-Ray for observability Try-it-out exercise: Enable X-Ray and interpret X-Ray traces CloudWatch metrics and embedded metrics format Try-it-out exercise: Metrics and alarms Try-it-out exercise: ServiceLens Serverless Application Security Security best practices for serverless applications Applying security at all layers API Gateway and application security Lambda and application security Protecting data in your serverless data stores Auditing and traceability Handling Scale in Serverless Applications Scaling considerations for serverless applications Using API Gateway to manage scale Lambda concurrency scaling How different event sources scale with Lambda Automating the Deployment Pipeline The importance of CI/CD in serverless applications Tools in a serverless pipeline AWS SAM features for serverless deployments Best practices for automation Course wrap-up Additional course details: Nexus Humans AWS Developing Serverless Solutions on AWS training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the AWS Developing Serverless Solutions on AWS course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Primavera Risk Analysis
By Underscore Group
Discover the powerful schedule and cost risk analysis features of PRA. Course overview Duration: 2 days (13 hours) Our Primavera Risk Analysis course gives a detailed introduction to the schedule and risk analysis features of Primavera Risk Analysis. It shows the powerful features of the tool and give hands on practice throughout the course to ensure you can confidentially put your new skills into practice back in the workplace. This course is designed for new users of Primavera Risk Analysis, and no previous experience is required. You should however be familiar with risk management processes and terminology. Objectives By the end of the course you will be able to: Import schedules into PRA Add three point estimates onto plans Perform schedule and cost analysis Use templated quick risk Run risk analysis Interpret results from the Risk Histogram and Tornado graph Add task percentiles to a Gantt chart Set up a risk register Add qualitative and quantitative risks Link risk to activities in the plan Create reports Use the Distribution Analyser Content Importing schedules Importing MSP and Primavera Schedules Running import checks Checking schedule integrity Schedule risk analysis 3 point estimating Entering uncertainly Different distributions Using quick risk Updating plan Importing plans with 3 point estimates Cost/Resource uncertainty Resource loadings Creating 3 point cost estimates Resource distributions and escalations Simple cost estimates Templated quick risk Setting up and applying templated quick risk Assessing risk at WBS level Running risk analysis Running risk analysis Interpreting results on the Risk Histogram Setting analysis options Task percentiles Setting task percentile options Including task percentiles on the Gantt chart Tornado graph Creating a Tornado graph Viewing sensitivity Analysing sensitivity against activities Setting up the risk register Setting Schema levels Defining criteria and tolerances Setting up a Risk Breakdown Structure (RBS) Working with manageability and proximity Saving scoring matrices Adding custom fields Exporting data Exporting to Excel, Word and PowerPoint Qualitive risks Setting risk IDs Adding risk cause, description and effect Setting up risk details Entering mitigation actions Quantitative risks Linking risks to activities Adding schedule and cost impacts Defining how multiple risks impact Correlation Migrating your plan Adding mitigation actions to your plan as tasks Linking tasks to mitigation actions Actioning your risk register Progressing risks Importing progressed plans Linking register to progressed plans Risk history The Waterfall chart Saving and reporting Exporting the risk register Running reports Creating new reports Building and comparing risk plans Using the distribution analyser Comparing dates and cost

Dog Behaviour and Training
By NextGen Learning
Course Overview The Dog Behaviour and Training course offers a comprehensive insight into canine psychology, behaviour management, and effective training techniques. Designed to build confidence and understanding, this course equips learners with the knowledge needed to address common dog behaviours and establish positive habits. Through focused modules, participants will develop skills in interpreting dog body language, managing feeding behaviours, addressing separation anxiety, and conducting training consultations. Whether supporting pet owners or advancing towards a professional role, learners will emerge with the ability to apply behavioural theories and strategies in real-world settings. By the end of the course, participants will understand how to create positive environments for dogs and promote lasting behavioural change, making them valuable assets in both domestic and professional contexts. Course Description The Dog Behaviour and Training course delves into the fascinating world of canine behaviour, offering learners a structured exploration of topics such as food aggression, appropriate greeting methods, and separation anxiety management. Learners will gain insights into interpreting dog communication signals, answering common client questions, and guiding puppy development. The course also covers consultation practices, preparing participants to engage confidently with dog owners seeking advice. Designed to foster a deep understanding of behavioural patterns, the curriculum blends theoretical frameworks with real-world applications, ensuring that learners develop a well-rounded skill set. By completing this course, individuals will strengthen their ability to assess behavioural issues, recommend appropriate training strategies, and support the welfare and development of dogs across various settings. Course Modules Module 01: Introduction Module 02: Feeding Time - Aggression and Stealing Food Module 03: The Right Way to Greet a Dog Module 04: Separation Anxiety Module 05: Dog Language - What They're Really Saying! Module 06: The Answers To 10 Popular Dog Questions You Are Likely To Be Asked Module 07: The Answers To 10 Common Puppy Training Questions That You'll Likely To Be Asked Module 08: Dog Training Consultations With Clients (See full curriculum) Who is this course for? Individuals seeking to build a deeper understanding of dog behaviour and training techniques. Professionals aiming to expand their expertise in animal behaviour consultancy or dog training services. Beginners with an interest in canine psychology and behaviour management. Dog owners wishing to enhance their relationships and communication with their pets. Animal care workers looking to broaden their knowledge for career development. Career Path Dog Behaviour Specialist Dog Trainer Animal Welfare Officer Veterinary Assistant (Behaviour Support Role) Pet Care Consultant Animal Shelter Worker Behavioural Advisor in Animal Charities

Diploma in Data Analysis Fundamentals
By NextGen Learning
Diploma in Data Analysis Fundamentals Course Overview The Diploma in Data Analysis Fundamentals provides a comprehensive introduction to the core principles and techniques used in data analysis. Throughout this course, learners will explore various data analysis tools and methods, such as Pareto charts, histograms, and control charts, to gain insights into processes and performance. By focusing on key data analysis skills, including identifying variation and interpreting results, this course empowers learners to use data-driven approaches to improve business processes. Upon completion, learners will have the ability to assess and present data effectively, enabling informed decision-making in a wide range of industries. Course Description This course covers essential topics in data analysis, including the principles of process management, tools for data analysis, and methods to interpret and present performance data. Learners will delve into key techniques such as Pareto charts, histograms, run charts, and control charts, focusing on how to use these tools to identify patterns, variations, and areas for improvement. The course also includes a structured approach to performance measurement and provides exercises to reinforce the theoretical knowledge gained. By the end of the course, learners will be equipped with the skills to analyse data, identify trends, and contribute to process improvement initiatives within their organisations. Diploma in Data Analysis Fundamentals Curriculum Module 01: Introduction Module 02: Agenda and Principles of Process Management Module 03: The Voice of the Process Module 04: Working as One Team for Improvement Module 05: Exercise: The Voice of the Customer Module 06: Tools for Data Analysis Module 07: The Pareto Chart Module 08: The Histogram Module 09: The Run Chart Module 10: Exercise: Presenting Performance Data Module 11: Understanding Variation Module 12: The Control Chart Module 13: Control Chart Example Module 14: Control Chart Special Cases Module 15: Interpreting the Control Chart Module 16: Control Chart Exercise Module 17: Strategies to Deal with Variation Module 18: Using Data to Drive Improvement Module 19: A Structure for Performance Measurement Module 20: Data Analysis Exercise Module 21: Course Project Module 22: Test your Understanding (See full curriculum) Who is this course for? Individuals seeking to enhance their data analysis skills. Professionals aiming to improve decision-making through data insights. Beginners with an interest in process improvement and business analysis. Data enthusiasts looking to build a solid foundation in analysis techniques. Career Path Data Analyst Business Intelligence Analyst Process Improvement Specialist Operations Analyst Quality Control Analyst
