- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
NPORS Plant Loader Securer Training The NPORS plant loader securer training course is intended for delivery drivers who operate plant equipment to load on to delivery vehicles, additionally for workers who are responsible for securing the plant using various securing equipment. Unsafe loads on vehicles injure more than 1,200 people a year and cost UK businesses millions of pounds in damaged goods. There has been an increasing number of accidents involving mobile plant during loading/unloading or during transportation resulting in fatalities. In line with recommendations from the Safety of Loads on Vehicles from the Department Of Transport, the course will provide both theoretical and practical training to ensure candidates are able to carry out the duties of Plant Loader Securer. NPORS is an approved CSCS Partner Card Scheme, providing evidence that individuals working on construction sites have the appropriate training and qualifications for the plant loader securer duties. Furthermore, training criteria is based on the approved standards of the Construction Leadership Council. Visit our page; The Art Of Securing Loads Experienced operator – NPORS Plant Loader Securer Test Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Plant Loader Securer Experienced Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Plant Loader Securer Experienced Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Plant Loader Securer Test is for operators who have received some form of training in the past or alternatively has been operating the Plant Loader Securer for several years. If you are unsure if you qualify to go down the test route please contact us to discuss this in more detail. Discounts are available for multiple bookings There are two parts to the plant loader securer test, a theory section comprised of 25 questions and a practical session. Plant Loader And Securer Course Objectives Plant Loader and Securer Training covers: Legislation: All relevant health and safety and current legislation and British Standards Loading: Load or guide items of plant onto a transporter. Position items of plant on the transporter to ensure no overloading of transporter axles. Ensure integrity and security of items of plant plus attachments using a range of restraining equipment Preparations: Prepare an area for the purposes of loading and unloading construction plant. Prepare a transporter for receiving different items of construction plant, which must include tracked, wheeled and roller types. Agree and give appropriate signals to the plant operator. Check equipment prior to operations Travel: Prepare a transporter for road travel. Ensure intended route of travel is compatible with load weight, width and height. Explain the specific requirements of current legislation for equipment designed for transporting construction plant. State the requirements to be undertaken when loading and unloading plant on the public highway. Plant Loader Securer Training Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable instructors, who have a wealth of knowledge of the loading and securing and the construction industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury, however this course must be on your site. With its own purpose-built practical training area to simulate an actual working environment. Our Loader Securer training and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS Plant Loader Securer Tester to your site nationwide, to reduce the amount of time away from work Frequently Asked Questions 1. Who should take the Plant Loader Securer Training? This training is intended for delivery drivers operating plant equipment to load onto delivery vehicles and workers responsible for securing the plant using various securing equipment. 2. What does the Plant Loader Securer Training cover? The course covers legislation, load and guide items of plant, preparing areas for loading/unloading, securing equipment, preparing transporters for road travel, and ensuring compliance with safety requirements. 3. How long is the Plant Loader Securer Training? For novice operators, the training lasts 2 days. Experienced operators can take a 1-day test. 4. What certification do I receive upon completion? Participants receive an NPORS card, either the traditional card valid for 5 years or the NPORS card with CSCS logo, valid initially for 2 years. 5. Are there any prerequisites for the Plant Loader Securer Training? Candidates must have a good understanding of English. For the NPORS card with CSCS logo, a CSCS Health & Safety test must have been completed within the last two years. More courses: Polish your abilities with our dedicated Lift Supervision Training, Slinger Signaller Training, Telehandler Training, Cat & Genny Training, Plant Loader Securer, Ride-On Road Roller, Abrasive Wheel Training, Lorry Loader Training and Scissor Lift Training sessions. Learn the safe and effective operation of these vital machines, crucial for construction and maintenance tasks. Elevate your skills and career prospects by enrolling in our comprehensive courses today. For those looking for a “NPORS Plant Loader Securer Training near me,” our widespread operations make it convenient for you to access Vally Plant Trainings top-quality training no matter where you are in the UK

Forklift Truck Training The aim of the NPORS Forklift Truck Training is to provide both theoretical and practical training to ensure the safe usage of the FLT Counter Balance Forklifts. As a result of the forklift truck training you will receive the red trained operator card or the Traditional Card. Call to book your forklift course today Experienced operator – NPORS Forklift Truck Test Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Forklift Experienced Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Forklift Experienced Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Forklift Truck Test is for operators who have received some form of forklift training in the past or alternatively has been operating Forklift trucks for a period of time. If you are unsure if you qualify to go down the forklift truck test route please contact us to discuss this in more detail. There are two parts to the forklift truck course, a theory section comprised of 25 questions and a practical session. Forklift Truck Training Course: Navigating Safety and Efficiency Forklift trucks, also known as lift trucks or forklifts, are indispensable tools in various industries, facilitating the movement and handling of materials with precision and ease. However, operating a forklift requires specialised skills and knowledge to ensure safety, efficiency, and compliance with regulations. In this comprehensive course outline, we will delve into the essential content covered in a forklift truck training course, designed to equip participants with the expertise needed to operate forklifts safely and effectively in the work place. 1. Introduction to Forklift Trucks: Overview of forklift types: counterbalance, reach, pallet trucks, etc. Understanding the components and controls of a forklift Different configurations and attachments for specific tasks All health and safety regulations covered 2. Forklift Safety Procedures: Importance of safety in forklift operation Pre-operational checks and inspections Understanding load capacity and load centre Personal protective equipment (PPE) requirements Emergency procedures: evacuation, fire, and accident response 3. Forklift Operation Basics: Starting, stopping, and manoeuvring the forklift safely around obstacles Steering techniques: forward, reverse, and turning Operating on various surfaces: smooth floors, ramps, and inclines Lifting, lowering, side shifting and tilting loads using hydraulic controls 4. Load Handling Techniques: Proper load assessment: weight, size, and stability Positioning the forklift for efficient loading and unloading Securing loads with proper attachments: forks, clamps, and attachments Stacking and de-stacking loads safely and efficiently 5. Site Safety and Hazard Awareness: Identifying potential hazards in the workplace Working safely around pedestrians, other forklifts, and obstacles Recognising environmental hazards: narrow aisles, confined spaces, and overhead obstructions Understanding site-specific safety rules and regulations 6. Maintenance and Inspections: Importance of regular maintenance for forklift performance and longevity Daily, pre-shift, and post-shift inspection procedures Lubrication points and maintenance schedules Identifying and reporting mechanical issues and defects 7. Practical Hands-On Training: Practical exercises in forklift operation under supervision Manoeuvring through obstacle courses and tight spaces Load handling exercises: stacking, de-stacking, and transporting loads Emergency response drills: simulated scenarios to test response and decision-making skills 8. Assessment and Certification: Written examination to assess theoretical knowledge Practical assessment of forklift operation skills Certification upon successful completion of the course Conclusion: A forklift truck training course equips participants with the essential knowledge, skills, and confidence to operate forklifts safely and efficiently in various work environments. By covering topics such as safety procedures, operation techniques, load handling, site awareness, maintenance practices, and practical hands-on training, participants can enhance their proficiency and contribute to a safer and more productive workplace. Whether you’re a novice operator or an experienced professional, investing in forklift training is essential for ensuring compliance, reducing risks, and promoting excellence in material handling operations. Frequently Asked Questions 1. What types of forklifts are covered in the training? The training covers various forklift types, including counterbalance, reach trucks, and pallet trucks. 2. What are the course components? The course includes theoretical training, practical sessions, safety procedures, load handling techniques, site safety, maintenance, and inspections. 3. Who is the training suitable for? The training is suitable for both novice operators and experienced operators who need certification or recertification. 4. What certification will I receive? Participants will receive an NPORS card, either a red trained operator card or a traditional card, valid for 2-5 years depending on the type. 5. What are the prerequisites for the course? There are no prerequisites for novice operators, but experienced operators should have prior forklift operation experience. Forklift Truck Training Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable instructors, who have a wealth of knowledge of Forklifts and the construction industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury. With its own purpose-built practical training area to simulate an actual working environment. However, this training can only be conducted on your sites Our forklift training and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS forklift Tester to your site nationwide, to reduce the amount of time away from work Our more courses: Polish your abilities with our dedicated Lift Supervision Training, Slinger Signaller Training, Telehandler Training, Cat & Genny Training, Plant Loader Securer, Ride-On Road Roller, Abrasive Wheel Training, Lorry Loader Training and Scissor Lift Training sessions. Learn the safe and effective operation of these vital machines, crucial for construction and maintenance tasks. Elevate your skills and career prospects by enrolling in our comprehensive courses today. For those looking for a “NPORS Forklift Training near me,” our widespread operations make it convenient for you to access Vally Plant Trainings top-quality training no matter where you are in the UK

Slinger Signaller Training The aim of the NPORS Slinger Signaller Training or Slinger Signaller Course is to provide both theoretical and practical training in the safe and efficient operation of slinging and moving loads using hand signals or radios Guided by the Lift Supervisor. On successful completion of the slinger and signaller course you will be issued with the NPORS Slinger Signaller trained identity card with or without the CSCS Logo or testing can be carried out on your site nationwide or at our training centre in Gloucestershire NPORS Slinger Signaller Test Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Slinger And Signaller Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Slinger and Signaller Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Slinger Signaller Experienced Worker Test .This test is for operators who have received some form of training in the past or alternatively has been operating as a Slinger Signaller for a period of time. If you are unsure if you qualify to go down the test route please contact us to discuss this in more detail. This test is held at our test centre in Gloucestershire or at your site nationwide. Discounts are available for multiple bookings Turn your Slinger Signaller red card to blue with our hassle free NVQ, for more information CLICK HERE Slinger Signaller Course Duration Novice: 2 days, maximum of 3 candidates Experienced Worker Test: 1 day test only, maximum of 6 candidates. Location: Tewkesbury Training Centre At Our Customers Site*: Our instructors travel throughout the UK to deliver the slinger signaller training *Mileage and accommodation charges may apply Certification NPORS Traditional card – lasts for 5 years and is mainly accepted with housebuilders, utilities, port and marine as proof of competence OR NPORS card with CSCS logo – accepted by all major building contractor’s. The initial card is the RED trained operator card which lasts for 2 years and can be upgraded to BLUE competent operator card further to completion of relevant NVQ. CSCS Health & Safety Test If you require the NPORS Slingers Red operator card with the CSCS logo on then you must have completed the operatives health and safety test within the last two years. In house certificates: suitable as proof of operator competence accepted for insurance and HSE compliance. Slinger Signaller Course Contents: A Slinger Signaller course typically covers a range of topics related to the safe operation of lifting equipment and the signalling procedures involved in crane and lifting operations. While specific course contents may vary depending on the training provider and the regulations of the region, here’s a general outline of what will be included: 1. Introduction to Lifting Operations: Overview of lifting equipment and machinery. Importance of safe lifting operations. Legal and regulatory requirements for lifting operations, LOLLER, PUWER and BS 7121. 2. Roles and Responsibilities of Slinger and Signaller: Duties of the slinger signaller. Understanding the roles of other personnel involved in lifting operations (crane operator, banksman, etc.). Importance of effective communication and coordination. 3. Health and Safety: Risk assessment and hazard identification. Personal protective equipment (PPE) requirements. Safe working practices around lifting equipment and machinery. 4. Lifting Equipment and Accessories: Types of lifting equipment (cranes, hoists, slings, etc.). Inspection and maintenance requirements for lifting gear. Proper selection and use of lifting accessories. 5. Signals and Communication: Standard hand signals for crane operations. Radio communication procedures between Crane Driver & The Slinger and Signaller. Clear and effective communication techniques. 6. Load Identification and Weight Estimation: Methods for identifying loads and determining their weights. Estimating centre of gravity and load stability. 7. Slinging Techniques: Types of slings and their applications. Correct methods for attaching and securing loads. Precautions for different types of loads (e.g., fragile, hazardous). 8. Lifting Operations Planning: Pre-lift checks and planning considerations. Site-specific factors affecting lifting operations (e.g., terrain, weather). Emergency procedures and contingency planning. 9. Practical Exercises and Demonstrations: Hands-on training with lifting equipment and machinery. Practice sessions for signalling and communication. Simulation of real-world lifting scenarios. 10. Assessment and Certification: Written tests to assess theoretical knowledge. Practical assessments of signalling and slinging skills. Certification upon successful completion of the course. It’s essential for the Slinger Signaller Course to provide a balance of theoretical knowledge and practical skills to ensure that participants can effectively carry out their duties as slinger signallers in various lifting operations. Additionally, the course should emphasise the importance of safety and adherence to regulations throughout all aspects of lifting operations. Slinger Signaller Training Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable instructors, who have a wealth of knowledge of the Slinger Signaller and the construction industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury. With its own purpose-built practical training area to simulate an actual working environment as a slinger signaller Our slinger and signaller training and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS slinger Tester to your site nationwide, to reduce the amount of time away from work Other courses: Master the operation of essential machinery with our Lift Supervision Training, Telehandler Training, Cat & Genny Training, Ride-On Road Roller, Scissor Lift, Abrasive Wheel Training, Lorry Loader Training and Telehandler Training. Elevate your skills for safer and more efficient operations in construction and maintenance projects. Enrol today to advance your career prospects in these industries. Location Advantage: NPORS Slinger Signaller Training Near Me For those looking for a “NPORS Slinger Signaller Training near me,” our widespread operations make it convenient for you to access Vally Plant Trainings top-quality training no matter where you are in the UK

Lorry Loader Training The aim of the Lorry Loader Training or Clamshell Bucket Courses is to provide the candidate with the basic knowledge and practical skills involved in operating a Lorry Loader ( HIAB ) or clamshell bucket courses, and on successful completion of the practical test, you will be issued with the NPORS Identity card with or without the CSCS logo. Discounts are available for multiple bookings NPORS/CSCS Lorry loader Experienced Worker Test or Training can only be delivered on our customer’s sites nationwide, Therefore reducing downtime and disruption of works to our clients. Experienced operator – NPORS Lorry Loader Test Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Lorry Loader Experienced Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Lorry Loader Experienced Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Lorry Loader Test is for operators who have received some form of training in the past or alternatively has been operating the Lorry Loader for several years. If you are unsure if you qualify to go down the test route please contact us to discuss this in more detail. Discounts are available for multiple bookings There are two parts to the lorry loader test, a theory section comprised of 25 questions and a practical session. Lorry Loader Training Course: Safely Operating Mobile Crane Vehicles 1. Introduction to Lorry Loaders Overview of lorry loader types and configurations Understanding the components and controls of a lorry loader Different applications and lifting capacities of lorry loaders 2. Lorry Loader Safety Procedures Importance of safety in lorry loader operation Pre-operational checks and inspections Understanding load charts and load capacities Personal protective equipment (PPE) requirements Emergency procedures: shutdown, lockout/tagout, and evacuation protocols 3. Lorry Loader Operation Basics Starting, stopping, and controlling the lorry loader, include emergency stops Familiarisation with lorry loader controls: boom, remote, and outriggers Manoeuvring the lorry loader on different terrain types: roads, construction sites, etc. Lifting and lowering loads safely and accurately 4. Load Handling Techniques Proper assessment of loads: weight, size, and stability Positioning the lorry loader for efficient loading and unloading Securing loads with proper rigging techniques: slings, chains, and hooks Stacking and de-stacking loads safely and efficiently Using other professionals to complete the work. Slinger signaller to direct the load 5. Site Safety and Hazard Awareness Identifying potential hazards in the workplace Working safely around pedestrians, other vehicles, and obstacles Recognising environmental hazards: overhead obstructions, power lines, etc. Understanding site-specific safety rules and regulations 6. Maintenance and Inspections Importance of regular maintenance for lorry loader performance and reliability Daily, pre-shift, and post-shift inspection procedures Lubrication points and maintenance schedules Identifying and reporting mechanical issues and wear parts replacement 7. Practical Hands-On Training Practical exercises in lorry loader operation under supervision Manoeuvring through obstacle courses and confined spaces Load handling exercises: lifting, positioning, and placing loads Emergency response drills: simulated scenarios to test response and decision-making skills 8. Assessment and Certification Written examination to assess theoretical knowledge Practical assessment of lorry loader operation skills Certification upon successful completion of the course A lorry loader training course, by Vally Plant Training provides participants with the essential knowledge, skills, and confidence to operate lorry loaders safely and efficiently in various work environments. By covering topics such as safety procedures, operation techniques, load handling, site awareness, maintenance practices, and practical hands-on training, participants can enhance their proficiency and contribute to a safer and more productive workplace. Whether you’re a novice operator or an experienced professional, investing in lorry loader training is essential for ensuring compliance, reducing risks, and maximising productivity in lifting operations. Lorry Loader Training Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable instructors, who have a wealth of knowledge of lorry loader and the construction industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury. With its own purpose-built HIAB practical training area to simulate an actual working environment. Our Lorry Loader or clamshell bucket courses and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS LORRY LOADER Tester to your site nationwide, to reduce the amount of time away from work More courses: Polish your abilities with our dedicated Lift Supervision Training, Slinger Signaller Training, Telehandler Training, Cat & Genny Training, Plant Loader Securer, Ride-On Road Roller, Abrasive Wheel Training, Lorry Loader Training and Scissor Lift Training sessions. Learn the safe and effective operation of these vital machines, crucial for construction and maintenance tasks. Elevate your skills and career prospects by enrolling in our comprehensive courses today. Frequently Asked Questions 1. What is the aim of the Lorry Loader Training course? • The course aims to provide candidates with the basic knowledge and practical skills involved in operating a Lorry Loader (HIAB) or clamshell bucket. Successful completion of the practical test will result in receiving the NPORS Identity card with or without the CSCS logo. 2. What does the Lorry Loader training course cover? • The course covers various aspects, including: o Types and configurations of lorry loaders o Safety procedures and pre-operational checks o Operation basics, including controls and manoeuvring o Load handling techniques o Site safety and hazard awareness o Maintenance and inspection procedures o Practical hands-on training and assessments 3. What is the duration of the Lorry Loader Training course? • For experienced operators, the course is a 1-day test, accommodating up to 4 candidates. For novice operators, it is a 2-day training session, accommodating up to 3 candidates. 4. Where is the training conducted? • Training can be conducted at the client’s site nationwide, which helps reduce downtime and disruption to work. The training centre is located near the M5 junction 9 in Tewkesbury, with a purpose-built HIAB practical training area. 5. What are the certification options available? • There are two certification options: o NPORS traditional card (valid for 5 years) o NPORS card with CSCS logo (initial RED trained operator card valid for 2 years, upgradable to BLUE competent operator card upon completing relevant NVQ) For those looking for a “NPORS Lorry Loader Training near me,” our widespread operations make it convenient for you to access Vally Plant Trainings top-quality training no matter where you are in the UK

NPORS Crusher Training The aim of the NPORS Crusher Training is to provide theoretical and practical training for operators of Mobile Crushing equipment in the workplace. This Crusher training Course Or Test is carried out on your site using your own equipment. Please contact us for a competitive quote The Crusher Training Course is designed to provide candidates with the skills and knowledge required in order to operate a crusher safely and competently in the workplace. NPORS is an approved CSCS Partner Card Scheme, providing evidence that individuals working on construction sites have the appropriate Crusher training and qualifications for the Crusher Operation. Furthermore, training criteria is based on the approved standards of the Construction Leadership Council. Most major contractors should accept the NPORS Crusher card when presented on-site, which displays the silver CSCS logo. This NPORS crusher training meets the statutory requirements of the Health & Safety at Work Act 1974 and other relevant statutory provisions and Approved Codes of Practice. NPORS Crusher Test For Experienced Operators Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Crusher Experienced Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Crusher Experienced Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Crusher Test is for operators who have received some form of training in the past or alternatively has been operating Crusher for a number of years. If you are unsure if you qualify to go down the test route please contact us to discuss this in more detail. Discounts are available for multiple bookings There are two parts to the Crusher Test, a theory section comprised of 25 questions and a practical session operating the Crusher, revision notes are available when booking. Crusher Course Content Crushers are essential equipment in mining, quarrying, and construction industries, tasked with breaking down large rocks and materials into smaller, more manageable sizes. Operating mobile crushers requires specialised skills and knowledge to ensure safety, efficiency, and optimal performance. In this comprehensive course overview, we will explore the essential content covered in a crusher training course, designed to equip participants with the expertise needed to operate crushers safely and effectively in the workplace. 1. Introduction to Crushers: Overview of crusher types: jaw crushers, cone crushers, impact crushers, etc. Understanding the components and operating principles of crushers Different configurations and applications for specific tasks 2. Crusher Safety Procedures: Importance of safety in crusher operation Pre-operational checks and inspections Understanding crusher capacities and limitations Personal protective equipment (PPE) requirements Emergency procedures: shutdown, lockout/tagout, and evacuation protocols 3. Crusher Operation Basics: Starting, stopping, and controlling the crusher, including emergency stops Familiarisation with crusher controls: power source, conveyor belts, feeders, etc. Monitoring and adjusting crusher settings for optimal performance Understanding crusher dynamics: feed size, speed, and throughput 4. Material Handling and Crushing Techniques: Proper assessment of materials: hardness, size, and moisture content Loading and feeding materials into the crusher safely and efficiently Adjusting crusher settings for different material types and sizes Maximising crusher efficiency and product quality 5. Site Safety and Hazard Awareness: Identifying potential hazards in the crusher area Working safely around moving parts, conveyor belts, and rotating equipment Recognising environmental hazards: dust, noise, and vibration Understanding site-specific safety rules and regulations 6. Maintenance and Inspections: Importance of regular maintenance for crusher performance and reliability Daily, pre-shift, and post-shift inspection procedures Lubrication points and maintenance schedules Identifying and reporting mechanical issues and wear parts replacement 7. Practical Hands-On Crusher Training: Moving the crusher in reverse and forwards through obstructions Loading and feeding materials into the crusher using excavator and loading shovels Adjusting crusher settings and monitoring performance for efficiency Emergency response drills: simulated scenarios to test response and decision-making skills 8. Assessment and Certification: Written examination to assess theoretical knowledge Practical assessment of crusher operation skills Certification upon successful completion of the course Conclusion: A crusher training course equips participants with the essential knowledge, skills, and confidence to operate crushers safely and efficiently in various work environments. By covering topics such as safety procedures, operation techniques, material handling, site safety awareness, best maintenance practices, and practical hands-on training, participants can enhance their proficiency and contribute to a safer and more productive workplace. Whether you’re a novice operator or an experienced professional, investing in crusher training with Vally Plant Training is essential for ensuring compliance, reducing risks, and maximising productivity in crushing operations. Frequently Asked Questions About Crusher Training What is Crusher Training, and why is it necessary? Crusher Training provides individuals with the skills and knowledge required to safely and effectively operate crushers, heavy machinery used in mining, construction, and recycling industries. It’s essential for ensuring operator safety, maximising productivity, and preventing accidents on job sites. Who should undergo Crusher Training? Crusher Training is essential for anyone involved in operating or working around crushers, including quarry workers, machine operators, maintenance personnel, and site supervisors. Proper training ensures that individuals understand equipment operation procedures and safety protocols. What topics are covered in Crusher Training programs? Crusher Training programs cover a range of topics, as above, including equipment familiarisation, safety precautions, preventive maintenance, operational techniques, troubleshooting, and emergency procedures. Participants learn how to operate crushers efficiently while prioritising safety and minimising risks. How long does Crusher Training take? The duration of Crusher Training programs varies depending on factors such as the complexity of the equipment and the depth of the curriculum. Basic training courses may last a couple of days, while more comprehensive programs could extend over 1 week to cover advanced concepts and practical applications. Is Crusher Training mandatory in certain industries? While Crusher Training may not be legally mandated in all areas, many employers in the mining, construction, and recycling industries require operators to undergo training as part of their occupational health and safety policies. Compliance with training requirements helps prevent accidents and ensures regulatory compliance along with productivity. Where can I find reputable Crusher Training courses? Reputable Crusher Training courses are offered by various institutions, including industry associations, equipment manufacturers, and specialised training providers like Vally Plant Training. It’s important to choose a program that offers accredited certification and covers relevant industry standards and best practices. Crusher Courses Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable Crusher instructors, who have a wealth of knowledge of crushers and the construction industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury. With its own purpose-built practical training area to simulate an actual working environment, however, Crusher Training can only be conducted on your sites Our Crusher course and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS Crusher Tester to your site nationwide, to reduce the amount of time away from work and complete the crusher test Our more courses: Polish your abilities with our dedicated Lift Supervision Training, Slinger Signaller Training, Telehandler Training, Cat & Genny Training, Plant Loader Securer, Ride-On Road Roller, Abrasive Wheel Training, Lorry Loader Training and Scissor Lift Training sessions. Learn the safe and effective operation of these vital machines, crucial for construction and maintenance tasks. Elevate your skills and career prospects by enrolling in our comprehensive courses today.

360 Excavator Training Courses From The objective of the NPORS 360 Excavator Training courses is to deliver comprehensive theoretical and practical training, ensuring the safe utilisation of excavators. This course covers the proficient operation of both wheeled or tracked excavators, catering to potential Digger operators. Upon successfully completing the NPORS Excavator Training Course, participants will be awarded the red trained operator card or the NPORS Traditional card, signifying their competence in completing the 360 excavator courses. Book direct with Vally Plant Training Today. This Novice 360 Excavator courses span five days and provides personalised 1 on 1 training, offering participants a focused and tailored learning experience to enhance their skills in excavator operation. Our price is structured to 1 on 1 training helping you to gain the Digger Driver Ticket 360 Excavator courses or testing can be carried out on your site Nationwide or our site in Gloucestershire NPORS Excavator Test Book with Confidence at Vally Plant Training At Vally Plant Training, we guarantee unbeatable value with our Excavator Experienced Test Price Match Promise. When you choose us, you can book with confidence, knowing that we will not be beaten on price. If you find a lower price for the same NPORS Excavator Experienced Worker Test, we’ll match it—ensuring you receive top-quality training at the best possible rate. Click for our terms and conditions Your skills, our commitment—always at the best price. NPORS Excavator Test is for operators who have been using the excavators in the workplace for a few years or that they have had some form of in-formal training in the past. If you are unsure if you qualify to go down the test route please contact our team to discuss this in more detail. If you book this route with us you will receive revision notes for the 25 questions. Discounts are available for multiple bookings NPORS Lifting Operations, Excavator As A Crane is an add on to the excavator operator card to enable the operator to safely pick and carry underslung loads, you can add the excavator as a crane at the same time as your 360 Excavator Training Turn your Excavator red card to blue with our hassle free Excavator NVQ, for more information EXCAVATOR NVQ 360 Excavator Training Course: Mastering Operation, Safety, and Maintenance 360 Excavators are versatile and powerful pieces of machinery widely used in the construction industry for various tasks, from digging trenches to lifting heavy loads with the use of Quick Hitches and Tilt Rotators. However, operating an excavator requires more than just basic knowledge of its controls; it demands proficiency, safety consciousness, and a comprehensive understanding of its capabilities. In this detailed course outline, Vally Plant Training will delve into the essential content covered in an 360 Excavator training course, designed to equip participants with the skills and knowledge needed to operate, maintain, and safely manoeuvre excavators on construction sites. If you’re keen on mastering the art of manoeuvring those heavy-duty machines, the 360 digger training at Vally Plant Training is just what you need. This course is designed to transform you into a pro at operating 360-degree excavators, making you adept at a variety of tasks, from digging to precision handling. The program is tailored to cater to both beginners and experienced operators, ensuring that everyone walks away with valuable skills. For newcomers, there’s an extensive 5-day hands-on 360 digger training where you’ll be immersed in learning the ins and outs of these massive machines, ensuring you get ample time to practice and perfect your technique. The 360 excavator courses for a Novice are 1 on 1 training, this will give you 100% of available time on the excavator learning more than the basics to enable you to pass the NPORS 360 excavator training course first time. Introduction to 360 Excavator Training All Health and safety legislations covered Overview of excavator types and configurations Components and anatomy of an excavator Understanding hydraulic systems and controls 360 Excavator courses Safety Procedures Importance of safety in excavator operation Pre-operation inspection checklist Safe entry and exit procedures Personal protective equipment (PPE) requirements Emergency shutdown procedures 360 Excavator Operation Basics Starting and shutting down procedures Familiarisation with controls: joysticks, pedals, and switches Basic manoeuvres: moving forward, backward, turning, and slewing Operating the boom, arm, and bucket controls Operate Quick Hitches and Tilt Rotators if fitted Understanding machine stability and centre of gravity Excavation Techniques Digging trenches and excavating foundations Sloping and benching techniques for safe excavation Loading dumper trucks and stockpiling materials Precision excavation for utilities and pipelines Lifting and Rigging: Excavator as a crane Overview of Excavator lifting capacities and load charts Selecting appropriate lifting attachments Rigging techniques: using hooks, slings, and chains Safe lifting practices and procedures Excavator Maintenance Importance of regular maintenance for optimal performance Daily, weekly, and monthly maintenance checks Lubrication and greasing points Troubleshooting common issues and repairs Site Safety and Hazard Awareness Identifying and mitigating hazards on construction sites Understanding underground utilities and potential hazards Working safely near power lines and other overhead obstructions Site-specific safety protocols and regulations Practical Hands-On Training Practical exercises in operating an excavator under supervision Manoeuvring in various terrain conditions Excavation tasks: digging trenches, loading trucks, etc. Lifting and rigging exercises with simulated loads NPORS Assessment and Certification Written examination to assess theoretical knowledge Practical assessment of excavator operation skills Certification upon successful completion of the Excavator Course Excavator Variations Micro Excavator up to 1Tons: Excavator Below 10T Excavator above and below 10T Wheeled Or Tracked 180 excavator (3CX) Lifting Operations (additional) Quick Hitch Training Frequently Asked Questions 1. What is 360 excavator operator training, and why is it necessary? 360 Excavator training provides individuals with the skills and knowledge needed to safely and efficiently operate excavators, heavy machinery used in construction, mining, and other industries. It’s essential for ensuring the safety of operators, preventing accidents, and maximising productivity on job sites. All Vally Plant Trainings Excavator Novice courses are 1 on 1 training helping you to gain the digger driver ticket 2. Who should undergo 360 excavator operator training? Anyone who operates or intends to operate excavators should undergo proper excavator training. This includes construction workers, heavy equipment operators, site supervisors, and contractors. Training is also valuable for individuals seeking employment in industries where excavators are commonly used. 3. What topics are covered in excavator 360 course programs? Excavator training programs typically cover a range of topics, including equipment familiarisation, safety procedures, pre-operation inspection, proper operation techniques, trenching and excavation techniques, site hazards identification, and emergency procedures. Our Training programs include hands-on practical training. 4. How long does excavator 360 course take? The duration of excavator training programs can vary depending on factors such as the level of experience of the participants and the depth of the curriculum. Basic training courses may last anywhere from a few days to 2 weeks. Vally Plant Training can also offer shorter refresher courses for experienced Excavator operators. Contact Vally Plant Training For more information 5. Is 360 excavator training Courses mandatory? While excavator training may not be legally mandated,, many employers require operators to undergo 360 Excavator Training as part of their occupational health and safety policies. Additionally, regulatory bodies and industry associations often recommend or require training certification for operating heavy machinery like excavators on site. 6. Where can I find reputable excavator training courses? Reputable 360 excavator training courses are offered by a variety of sources, including vocational schools, community colleges, private training providers, and equipment manufacturers. It’s important to choose a program that is accredited, led by experienced instructors, and covers relevant industry standards and regulations. Additionally, employers may offer in-house training or provide recommendations for external training providers. Call Vally Plant Training for all reputable training including 360 excavator training. How much does a 360 excavator driver earn?A 360 excavator driver earns Approximately between £24,000 and £40,000 pa. This will depend on things like competence, qualifications, skills, and the amount of work you have completed over the years. holding the NPORS Excavator Operator card will give you a better chance of work.How To Apply For 360 Excavator TrainingIf you want to apply for the 360 excavator Training courses in Gloucestershire then please use our contact form to enquire about our excavator courses. Contact us to find more about the other courses that we offer, and any special offers we have running each month. Please give us as much information as possible about the course, like, is this the first time on the machine or have you had previous certification on the plant.. 360 Excavator Training Courses Available 7 days a week to suit your business requirements. VPT have a team of friendly and approachable instructors, who have a wealth of knowledge of the excavator and the Construction & Agricultural industry We have our own training centre conveniently located close to the M5 junction 9, In Tewkesbury. With its own purpose-built Excavator practical training area to simulate an actual working environment. Our 360 Excavator Training Courses and test packages are priced to be competitive. Discounts are available for multiple bookings We can send a fully qualified NPORS Excavator assessor to your site nationwide, to reduce the amount of time away from work to complete the 360 Excavator Training or travel to Vally Plant Training’s Facility in Gloucestershire. Our more courses: Polish your abilities with our dedicated Lift Supervision Training, Slinger Signaller Training, Telehandler Training, Cat & Genny Training, Plant Loader Securer, Ride-On Road Roller, Abrasive Wheel Training, Lorry Loader Training and Scissor Lift Training sessions. Learn the safe and effective operation of these vital machines, crucial for construction and maintenance tasks. Elevate your skills and career prospects by enrolling in our comprehensive courses today. Ever wondered what it feels like to take control of a 13-tonne excavator? Now’s your chance to find out with this thrilling 13T Excavator Digger Driving Experience. For a full two hours, you’ll be in the driver’s seat, operating one of these colossal machines just like the professionals you’ve seen on motorways and construction sites across the country. Under the expert guidance of the UK’s Number 1 accredited training organisation, you’ll learn how to manoeuvre this massive piece of machinery with skill and precision. From loading dumpers and moving dirt around to digging impressive holes, you’ll experience the raw power and versatility of a 13-tonne excavator first-hand. For those looking for a “NPORS Excavator Training near me,” our widespread operations make it convenient for you to access Vally Plant Trainings top-quality training no matter where you are in the UK

Overview Learn how to price equity options and the features that make them different from other asset classes. Explore how to use these products for taking equity risk, yield enhancement and portfolio protection Who the course is for Risk managers Bank treasury professionals Finance Internal Audit Senior management Fixed Income, FX, Credit and Equities traders Course Content To learn more about the day by day course content please request a brochure To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now

Overview 2 day applied course with comprehensive case studies covering both Standardised Approach (SA) and Internal Models Approach (IMA). This course is for anyone interested in understanding practical examples of how the sensitivities-based method is applied and how internal models for SES and DRC are built. Who the course is for Traders and heads of trading desks Market risk management and quant staff Regulators Capital management staff within ALM function Internal audit and finance staff Bank investors – shareholders and creditors Course Content To learn more about the day by day course content please request a brochure To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now

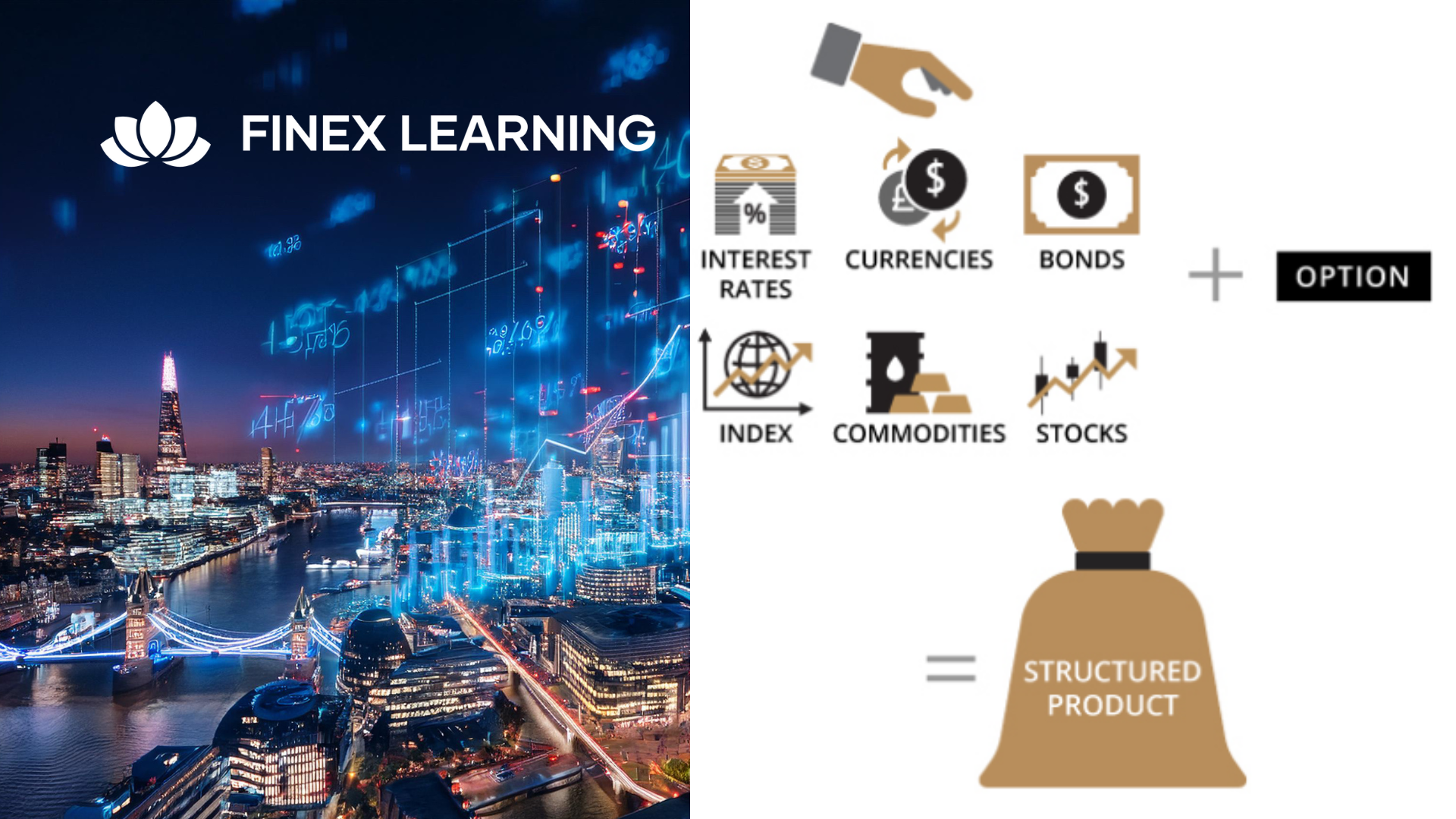
Overview A review of the most enduringly popular structured equity-linked products. This 1 day hands-on programme will help you gain familiarity with 1st generation & 2nd generation structured products convexity – and their applications. Discover techniques for maximising the participation rate to enhance returns for investors. Explore the trade-offs between coupon payments and gearing, and how they affect the risk-return profile of the notes. Explore ladder structures, their relationship to lookbacks, and the benefits they offer to investors. Learn about accumulators, their structuring, and the reasons behind their controversy in the market. Who the course is for Structured Products Desks, Financial Engineers, Product Controllers Traders, Dealing Room Staff and Sales People Risk Managers, Quantitative Analysts and Middle Office Managers Fund Managers, Investors, Senior Managers Researchers and Systems Developers Course Content To learn more about the day by day course content please request a brochure To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now
Overview This is a 2 day applied course on XVA for anyone interested in going beyond merely a conceptual understanding of XVA and wants practical examples of Monte Carlo simulation of market risk factors to create exposure distributions and profiles for derivatives used for XVA pricing Learn how to do Monte Carlo simulation of key market risk factors across major asset classes to create exposure distributions and profiles (with and without collateral) for derivatives used for XVA pricing. Learn how to calculate each XVA. Learn sensitivities of each XVA and how XVA desks manage these. Learn regulatory capital treatment of counterparty credit risk (both for CCR and CVA volatility) and how to stress test this within ICAAP or system-wide external, supervisor-led capital stress test. Who the course is for Anyone involved in OTC derivatives XVA traders XVA quants Derivatives traders and salespeople Risk management Treasury staff Internal audit and finance Course Content To learn more about the day by day course content please request a brochure To learn more about schedule, pricing & delivery options, book a meeting with a course specialist now

Search By Location
- SEN Courses in London
- SEN Courses in Birmingham
- SEN Courses in Glasgow
- SEN Courses in Liverpool
- SEN Courses in Bristol
- SEN Courses in Manchester
- SEN Courses in Sheffield
- SEN Courses in Leeds
- SEN Courses in Edinburgh
- SEN Courses in Leicester
- SEN Courses in Coventry
- SEN Courses in Bradford
- SEN Courses in Cardiff
- SEN Courses in Belfast
- SEN Courses in Nottingham