- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
694 Identity courses in Nottingham delivered Online
Cisco Introduction to 802.1X Operations for Cisco Security Professionals v1.0 (8021X)
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course is intended for Cisco Partner Sales Engineers and Field engineers supporting customers with 802.1x solutions. The primary audience for this course is Cisco Channel Partner SEs and FEs that are seeking to meet the education requirements to attain ATP authorization to sell Cisco ISE. The secondary audience for this course is security architects, design engineers, and others seeking hands-on experience with Cisco TrustSec 802.1X deployments with Cisco ISE Overview Upon completing this course, students will be able to meet these objectives:- Describe identity-based networking concepts and components - Define the components and processes of port-based authentication - Identify the 802.1X components and their interrelation at a high level - Identify requirements and options for non-supplicant devices - Position individual components of an 802.1X network and identify compatibilities Students will gain the foundational knowledge of IEEE 802.1X protocol; the skills that are needed to configure the Cisco Identity Services Engine (ISE) for 802.1X operation; hands-on experience configuring a network for 802.1X-based network services. Cisco TrustSec Surveying Cisco TrustSec Surveying Cisco TrustSec Architecture Components Port-Based Authentication Surveying the IEEE 802.1X Standard Surveying 802.1X and EAP Surveying 802.1X and EAP Configure Devices for 802.1X Operation Identifying 802.1X Components and Topologies Identifying 802.1X Components and Topologies Configuring Network Devices for 802.1X Configuring Supplicants for 802.1X Operation Configure Guest Access Configuring Cisco TrustSec for Non-Supplicant Devices Configuring Cisco WebAuth for Non-Supplicant Devices Design Cisco TrustSec Networks with Cisco ISE and 802.1X Identifying Component Compatibilities with 802.1X Reviewing 802.1X Design Considerations that Impact Implementation Reviewing Scalable 802.1X Architectures Additional course details: Nexus Humans Cisco Introduction to 802.1X Operations for Cisco Security Professionals v1.0 (8021X) training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Cisco Introduction to 802.1X Operations for Cisco Security Professionals v1.0 (8021X) course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Overview In today's competitive market, the power of branding cannot be overstated. The course 'Business Branding' delves deep into the nuances of creating a compelling brand identity specifically tailored for small businesses. Through a blend of theory and real-world examples, learners will grasp the essence of what makes a brand memorable and how to carve a distinct niche in the market. Furthermore, the curriculum sheds light on the strategies and techniques that can elevate a business's presence, ensuring it resonates with its target audience. By the end of this course, participants will be equipped with the knowledge and tools to transform their business into a recognisable and trusted brand. Transitioning from the basics to advanced concepts, this course ensures a holistic understanding of branding. It's not just about a logo or a catchy slogan; it's about creating a narrative, a story that speaks to the customers. Small businesses often face the challenge of standing out in a saturated market, and this course offers the blueprint to achieve that differentiation. With expert guidance and actionable insights, learners will navigate the branding journey with confidence. Lastly, the importance of consistent branding across all touchpoints is emphasised. Maintaining a cohesive brand image is paramount, Whether through digital platforms, print media, or in-person interactions. This course will empower businesses to create that consistency, fostering trust and loyalty among their customers. Learning Outcomes: Understand the fundamental principles of branding and its significance for small businesses. Recognise the elements that contribute to a strong brand identity. Develop strategies to differentiate a brand in a competitive market. Craft a compelling brand narrative that resonates with the target audience. Implement consistent branding across various platforms and touchpoints. Evaluate the effectiveness of branding strategies and make informed adjustments. Foster customer trust and loyalty through effective branding. Why buy this Business Branding? Unlimited access to the course for forever Digital Certificate, Transcript, student ID all included in the price Absolutely no hidden fees Directly receive CPD accredited qualifications after course completion Receive one to one assistance on every weekday from professionals Immediately receive the PDF certificate after passing Receive the original copies of your certificate and transcript on the next working day Easily learn the skills and knowledge from the comfort of your home Certification After studying the course materials of the Business Branding there will be a written assignment test which you can take either during or at the end of the course. After successfully passing the test you will be able to claim the pdf certificate for £5.99. Original Hard Copy certificates need to be ordered at an additional cost of £9.60. Who is this course for? This Business Branding course is ideal for Entrepreneurs looking to establish a strong brand presence for their startups. Small business owners seeking to rebrand or enhance their current brand image. Marketing professionals aiming to specialise in branding for small enterprises. Students of business and marketing keen to delve into the world of branding. Creative individuals aspiring to collaborate with businesses on branding projects. Prerequisites This Business Branding does not require you to have any prior qualifications or experience. You can just enrol and start learning.This Business Branding was made by professionals and it is compatible with all PC's, Mac's, tablets and smartphones. You will be able to access the course from anywhere at any time as long as you have a good enough internet connection. Career path Brand Strategist: Average salary range in the UK: £40,000 - £55,000 Per Annum. Brand Manager: Average salary range in the UK: £35,000 - £50,000 Per Annum. Marketing Manager: Average salary range in the UK: £30,000 - £45,000 Per Annum. Brand Consultant: Average salary range in the UK: £45,000 - £60,000 Per Annum. Creative Director: Average salary range in the UK: £50,000 - £70,000 Per Annum. Brand Analyst: Average salary range in the UK: £32,000 - £47,000 Per Annum. Course Curriculum Business Branding For Small Businesses Business Course Promo Video 00:03:00 Chapter 1 00:07:00 Chapter 2 00:12:00 Chapter 3 00:11:00 Chapter 4 00:09:00 Chapter 5 00:08:00 Chapter 6 00:07:00 Chapter 7 00:17:00 Chapte 8 00:25:00 Chapter 9 00:07:00 Chapter 10 00:03:00 Chapter 11 00:01:00 Resources Resources - Business Branding For Small Businesses 00:00:00 Assignment Assignment - Business Branding 00:00:00

Certificate in KYC and Customer Due Diligence
5.0(4)By LGCA | London Governance and Compliance Academy
Boost your customer service, administrative, and back-office skills by getting certified in KYC and CDD by AGRC! This certificate will provide you with the tools and knowledge required to become an invaluable member of any institution’s client onboarding and customer retention process. A key concern and significant risk for financial institutions remain the possibility of unknowingly becoming complicit in money laundering actions, where illegitimate money is moved into legitimate institutions. In order to mitigate such risk, FIs have strengthened their internal control systems by increasingly making use of Know Your Customer (KYC) and Customer Due Diligence (CDD) requirements, as part of their anti-money laundering (AML) strategies. Study method Distance learning, self-paced Duration 25 hours Access to content 360 days Certification Certificate in Know Your Customer & Customer Due Diligence Additional info Exam(s) / assessment(s) is included in price Description About the Certificate KYC/CDD is a critical element for effectively managing the risks posed by potential clients (thus protecting the organization against criminals, terrorists, and Politically Exposed Persons (PEPs) who might present a higher risk) and possible dubious actions by existing customers that need to be regularly reassessed. This certificate course provides essential knowledge for KYC and CDD procedures which are key tools in assessing customer risk and a legal requirement to comply with Anti-Money Laundering (AML) and Counter-Terrorist Financing (CFT) laws. Effective KYC/CDD involves knowing a customer’s identity and their financial activities, ongoing monitoring of business activities, and identifying and mitigating the AML/CFT risk a business relationship may pose on the regulated entity. Expected Learning Outcomes • Understand the importance of adopting effective KYC/CDD policies and procedures in a regulated entity • Review international guidance on the essential elements of KYC standards and the applicable regulatory framework • Have the ability to establish and maintain a solid KYC/CDD programme • Successfully assess the different levels of KYC/CDD that can be applied by an entity • Efficiently deal with higher risk situations and cases in an effective manner • Have a practical perspective on the adverse effects that can result from lack of efficient KYC/CDD procedures Topics covered • An introduction to KYC/Customer Due Diligence (CDD) • The value of Customer Due Diligence (CDD) • CDD: Establishing and maintaining a strong CDD programme • CDD in higher risk situations and record keeping requirements • AML Case Studies Format • Register at any time for this online, open Certificate • Study in your own time and at your own pace (you have up to 3 months to complete) • Assessed by online multiple-choice exam What is included • 25 hours of self-paced online interactive learning including analysis of 7 practical case studies • 1-year free AGRC membership • Online Exam and AGRC Certificate Who is this course for? This course is addressed to all individuals who practice KYC, CDD as well as Anti-Money Laundering such as Compliance/AML Managers in Banks, Investment Firms, Investment Funds, Trust Service Corporate Providers and Lawyers. Requirements No previous knowledge or experience is required though it is assumed that participants have good knowledge of English and sound educational background Career path Head of Back Office, Head of Customer Support, Compliance Assistant, Compliance Officer, AML Officer, MLRO.

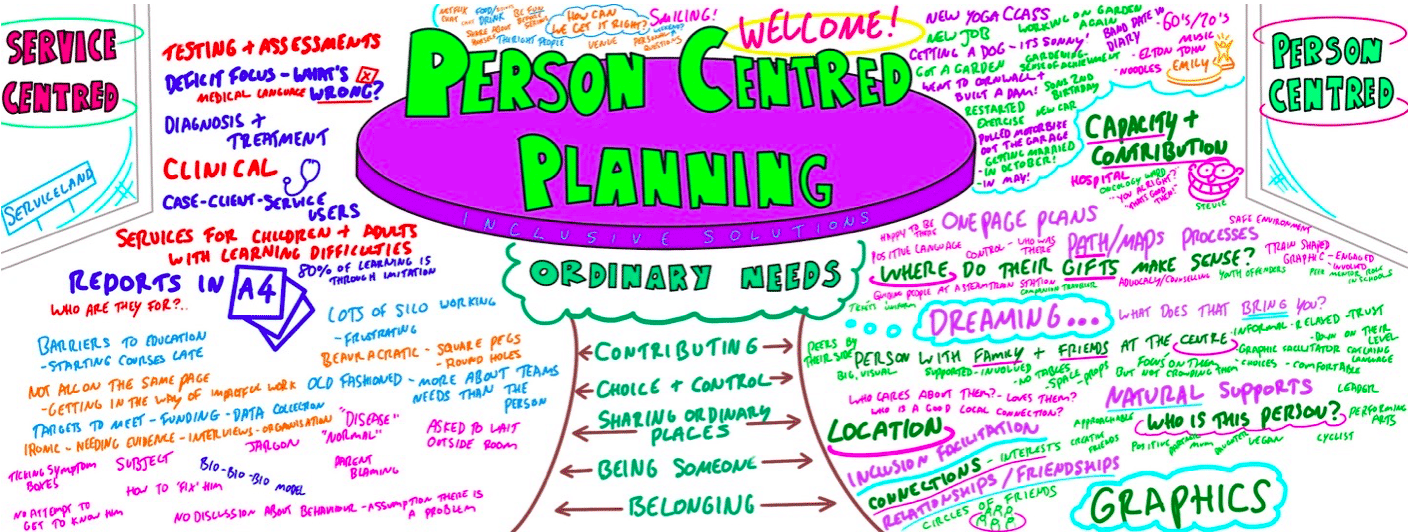
PERSON CENTRED PLANNING TRAINING
By Inclusive Solutions
Person Centred Planning (PCP) is a powerful tool for visioning, future planning and team building. It gets everyone on the same page and creates a progressive, constructive atmosphere so it is especially useful for people who are feeling ‘stuck’ or in a really desperate situation. The PCP processes we teach are called “PATH” and “MAPs”, and are both used for different situations. “To facilitate a group, family, team or organisation in thinking together around a given challenge or issue. Here is an opportunity to experience for real the person centred, futures planning tool – MAP/PATH” (Pearpoint, Forest, O’Brien. 1989). PCP can focus on an individual, with family and friends in the room supporting them, or focus on a group who want to set goals, and realise their potential as a team. PCP focuses on hopes and dreams, so is a very positive approach to planning, and utilises graphic facilitation, making it a very friendly way of working that is accessible to everyone. This unique, hands on PCP training course explores the difference between ‘person-centred thinking’ and ‘service-centred thinking’. Traditionally, we have not always listened deeply enough to the needs of those we are planning for. Often ‘medical model’ thinking dominates our planning for those with the most complex needs. Typically we plan ‘about’ rather than ‘with’ children and adults. We examine this ‘service centred’ approach that most professionals are used to, and question its limitations. This values based approach to inclusion will give participants the ‘theory’ behind why thinking and working in a person centred way is so important, and challenges people to strive for more for the people we are planning around. In addition to the knowledge and theory, this course empowers participants to facilitate their own Person Centred Plans using the PATH or MAPs process and provides the skills to do this effectively. Learning objectives Strengthen understanding of how to think in a person centred way Knowledge of the steps of PATH / MAPs process Ability to facilitate PATH/MAPs process Ability to graphically facilitate a PCP meeting Develop problem solving and planning skills Inclusive Solutions offer: We could provide training for a team of staff, or we could facilitate a PATH or MAP around a disabled person. We can also offer bespoke training packages, please enquire for more details. 1 day “Introduction to PCP” with up to 100 attendees focusing on ‘Person Centred Thinking’ – includes live demonstration of PATH or MAPs Process (for a member of the group / with a student and their family/friends). 2 day “PCP Skills training” – More skills focused, lots of practice. Includes Graphics academy, Process academy and Coaching (Best with under 30 attendees). 2 day “Introduction to PCP with Skills training” – includes live demonstration of PATH or MAPs process, Graphics academy, Process academy and Coaching (Best with under 30 attendees). Half day PATH or MAP for a disabled person, led by two experienced Inclusive Solutions facilitators. Full day PATH or MAP for a team, organisation or group such as a full school staff led by two experienced Inclusive Solutions facilitators. Typical Structure of 2-Day “Introduction to PCP with Skills” Training This course is most useful when delivered over 2 days so we have time to cover the ‘skills’ behind facilitating a PATH or a MAP. Here is an example of what usually happens. If you need us to, we can tailor any of our courses to suit your specific needs. Day 1 AM What makes a good welcome?Service centred thinking and working – what does it involve, how does it make people feel?Reflections on current practices – what is useful and what is harmful?Introduction to underpinning values of person centred thinking and working In depth exploration of the fundamentals of inclusion – encouraging identity, focusing on gifts and capacities Sharing success stories, and personal insight from experienced psychologistsShowcasing a number of practical PCP process in actionIntroduction to the “5 service accomplishments”, or “5 ordinary needs” PM Full PATH process demonstration, led by 2 experienced facilitators – one process facilitator and one graphic facilitatorVolunteers will make notes on what they see the facilitators doing and feedback at the end of the dayFeedback, Q&A Day 2 AM Graphics Academy – we will ease you into the world of graphic facilitation and show you how simple it really is – includes live coaching and graphics tutorial, then participants will practice on each other by facilitating the first 1 or 2 sections of the PATH Process Academy – we will give you some pointers about holding the group, and facilitating in an inclusive way, this is another chance to practice your new graphics skills PM The group is divided up, and volunteers are selected to facilitate PATH meetings The group then run the PATH’s simultaneously with an experienced coaches in the room to guide and to be available for questionsWe reconvene to feedback about the process and digest all we have learntBrief Q&A session and then final reflections
IGCSE Sociology
By Spark Generation
Unlock the dynamics of human society with Spark Generation! Dive into the realms of culture, identity, and social change. Gain a comprehensive understanding of how societies function thanks to this Cambridge self-paced course provided by Spark Generation. :)

Certificate in KYC & Customer Due Diligence
By Compete High
ð Unlock Your Potential with the Certificate in KYC & Customer Due Diligence! ð Are you ready to embark on a rewarding journey towards mastering KYC (Know Your Customer) and Customer Due Diligence? Look no further! Our comprehensive Certificate in KYC & Customer Due Diligence equips you with the essential knowledge and skills to thrive in the dynamic world of compliance and risk management. ð ð Benefits of Taking the Course: Stay Compliant: In today's regulatory environment, compliance is paramount. By enrolling in our course, you'll gain a deep understanding of KYC regulations and customer due diligence processes, ensuring your organization remains compliant with legal requirements. Risk Mitigation: Identify and mitigate potential risks associated with customer onboarding and ongoing monitoring. Learn effective risk assessment techniques to protect your organization from financial losses and reputational damage. Enhanced Career Opportunities: Stand out in the job market with a valuable certification in KYC & Customer Due Diligence. Whether you're looking to advance in your current role or explore new career opportunities, this certificate will open doors to a wide range of roles in banking, finance, consulting, and more. Confidence in Decision-Making: Develop the confidence to make informed decisions when it comes to customer onboarding, risk assessment, and compliance procedures. Gain practical insights from industry experts to navigate complex compliance challenges effectively. Professional Growth: Invest in your professional development and stay ahead of the curve in an ever-evolving industry. Our course provides you with the knowledge and skills needed to excel in your career and pursue exciting growth opportunities. ð¯ Who is this for? Compliance Professionals: Stay updated with the latest regulations and best practices in KYC and customer due diligence. Banking and Financial Services Professionals: Enhance your expertise in compliance and risk management to advance your career in the financial industry. Legal and Regulatory Specialists: Deepen your understanding of regulatory requirements and compliance frameworks to better serve your clients. Entrepreneurs and Business Owners: Ensure your business operates in accordance with regulatory standards and safeguards against potential risks. Anyone Interested in Compliance: Whether you're new to the field or seeking to broaden your knowledge, this course is suitable for individuals from diverse backgrounds interested in compliance and risk management. ð Career Path: Upon completing the Certificate in KYC & Customer Due Diligence, you'll be well-equipped for a variety of roles, including: KYC Analyst: Perform thorough due diligence on customers to verify their identities and assess associated risks. Compliance Officer: Ensure adherence to KYC regulations and implement robust compliance frameworks within organizations. Risk Manager: Identify, assess, and mitigate risks associated with customer relationships and transactions. AML (Anti-Money Laundering) Specialist: Detect and prevent money laundering activities by implementing effective AML procedures and controls. Financial Crime Investigator: Investigate suspicious activities and conduct forensic analyses to combat financial crimes. Consultant: Provide advisory services to organizations on KYC and customer due diligence best practices and regulatory compliance. Don't miss out on this opportunity to take your career to new heights! Enroll in the Certificate in KYC & Customer Due Diligence today and become a sought-after expert in compliance and risk management. ð¼ Ready to take the next step? Contact us now to learn more about our course offerings and kickstart your journey towards success! FAQ (Frequently Asked Questions) for Certificate in KYC & Customer Due Diligence Course Q1: What is KYC (Know Your Customer) and why is it important? A: KYC, or Know Your Customer, is a process through which businesses verify the identity of their clients. It involves collecting and assessing information about customers to ensure they are who they claim to be and to assess the risks associated with doing business with them. KYC is crucial for preventing financial crimes such as money laundering, terrorism financing, and fraud. By knowing their customers, businesses can mitigate risks and comply with regulatory requirements. Q2: What is Customer Due Diligence (CDD) and how does it relate to KYC? A: Customer Due Diligence (CDD) is a component of the KYC process. It involves gathering information about customers to assess their risk profile and to understand the nature and purpose of their transactions. CDD helps businesses make informed decisions about the level of risk associated with each customer and enables them to implement appropriate risk management measures. CDD is essential for ensuring compliance with anti-money laundering (AML) and counter-terrorism financing (CTF) regulations. Q3: What are the key components of a KYC/CDD program? A: A comprehensive KYC/CDD program typically includes the following key components: Customer Identification: Verifying the identity of customers using reliable and independent sources of information. Customer Risk Assessment: Assessing the risk associated with each customer based on factors such as their identity, occupation, transaction patterns, and geographic location. Ongoing Monitoring: Continuously monitoring customer transactions and behavior to detect any suspicious activity or changes in risk profile. Enhanced Due Diligence (EDD): Conducting enhanced due diligence on high-risk customers, such as politically exposed persons (PEPs) or customers from high-risk jurisdictions. Record-Keeping: Maintaining accurate and up-to-date records of customer information and due diligence activities to demonstrate compliance with regulatory requirements. Q4: Who should undergo KYC/CDD training? A: KYC/CDD training is essential for professionals working in industries such as banking, financial services, insurance, real estate, and gaming, where there is a high risk of financial crime. This includes compliance officers, risk managers, customer relationship managers, and frontline staff responsible for customer onboarding and due diligence processes. Additionally, regulatory bodies often require individuals working in these industries to undergo KYC/CDD training to ensure they have the necessary knowledge and skills to fulfill their compliance obligations. These FAQs provide a general overview of KYC and Customer Due Diligence. For more detailed information and specific training requirements, individuals should consult with accredited training providers or regulatory authorities in their jurisdiction. Course Curriculum Module 1 - Introduction to KYC Introduction to KYC 00:00 Module 2 - KYC Requirements in the UK KYC Requirements in the UK 00:00 Module 3 - Customer Due Diligence Customer Due Diligence 00:00 Module 4 - KYC Process _ Procedures Guide KYC Process Procedures Guide 00:00 Module 5 - AML (Anti-Money Laundering) AML (Anti-Money Laundering) 00:00 Module 6 - KYC and AML - Key Differences and How They Work Together KYC and AML - Key Differences and How They Work Together 00:00 Module 7 - KYC and AML Regulations in the UK KYC and AML Regulations in the UK 00:00 Module 8 - Reasonable Methods in KYC Verification Reasonable Methods in KYC Verification 00:00

VMware NSX-T Data Center: Install, Configure, Manage [V3.2]
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for Experienced security administrators or network administrators Overview By the end of the course, you should be able to meet the following objectives: Describe the architecture and main components of NSX-T Data Center Explain the features and benefits of NSX-T Data Center Deploy the NSX Management cluster and VMware NSX Edge⢠nodes Prepare VMware ESXi⢠and KVM hosts to participate in NSX-T Data Center networking Create and configure segments for layer 2 forwarding Create and configure Tier-0 and Tier-1 gateways for logical routing Use distributed and gateway firewall policies to filter east-west and north-south traffic in NSX-T Data Center Configure Advanced Threat Prevention features Configure network services on NSX Edge nodes Use VMware Identity Manager and LDAP to manage users and access Explain the use cases, importance, and architecture of Federation This five-day, fast-paced course provides comprehensive training on how to install, configure, and manage a VMware NSX-T? Data Center environment. This course covers key NSX-T Data Center features and functionality offered in the NSX-T Data Center 3.2 release, including the overall infrastructure, logical switching, logical routing, networking and security services, firewalls and advanced threat prevention, and more. Course Introduction Introductions and course logistics Course objectives VMware Virtual Cloud Network and NSX-T Data Center Introduce the VMware Virtual Cloud Network vision Discuss NSX-T Data Center solutions, use cases, and benefits Explain NSX-T Data Center architecture and components Describe the VMware NSXTM product portfolio and features Explain the management, control, data, and consumption planes and function Preparing the NSX-T Data Center Infrastructure Describe NSX Management Cluster Deploy VMware NSXTM ManagerTM nodes on VMware ESXi and KVM hypervisors Navigate through the NSX Manager UI Explain data-plane components such as N-VDS/VDS, transport nodes, transport zones, profiles, and more Perform transport node preparation and establish the data center infrastructure Verify transport node status and connectivity NSX-T Data Center Logical Switching Introduce key components and terminology in logical switching Describe the function and types of L2 segments Explain tunneling and the GENEVE encapsulation Configure logical segments and attach hosts using NSX Manager UI Describe the function and types of segment profiles Create segment profiles and apply them to segments and ports Explain the function of MAC, ARP, and TEP tables used in packet forwarding Demonstrate L2 unicast packet flow Explain ARP suppression and BUM traffic handling NSX-T Data Center Logical Routing Describe the logical routing function and use cases Introduce the two-tier routing architecture, topologies, and components Explain the Tier-0 and Tier-1 Gateway functions Describe the logical router components: Service Router and Distributed Router Discuss the architecture and function of NSX Edge nodes Discuss deployment options of NSX Edge nodes Configure NSX Edge nodes and create NSX Edge clusters Configure Tier-0 and Tier-1 Gateways Examine the single-tier and multitier packet flow Configure static routing and dynamic routing, including BGP and OSPF Enable ECMP on Tier-0 Gateway Describe NSX Edge HA, failure detection, and failback modes Configure VRF Lite NSX-T Data Center Bridging Describe the function of logical bridging Discuss the logical bridging use cases Compare routing and bridging solutions Explain the components of logical bridging Create bridge clusters and bridge profiles NSX-T Data Center Firewalls Describe NSX segmentation Identify the steps to enforce Zero-Trust with NSX segmentation Describe the Distributed Firewall architecture, components, and function Configure Distributed Firewall sections and rules Configure the Distributed Firewall on VDS Describe the Gateway Firewall architecture, components, and function Configure Gateway Firewall sections and rules NSX-T Data Center Advanced Threat Prevention Explain NSX IDS/IPS and its use cases Configure NSX IDS/IPS Deploy the NSX Application Platform Identify the components and architecture of NSX Malware Prevention Configure NSX Malware Prevention for east-west and north-south traffic Describe the use cases and architecture of NSX Intelligence Identify the components and architecture of VMware NSX© Network Detection and Response? Use NSX Network Detection and Response to analyze network traffic events. NSX-T Data Center Services Describe NSX-T Data Center services Explain and configure Network Address Translation (NAT) Explain and configure DNS and DHCP services Describe VMware NSX© Advanced Load Balancer? architecture, components, topologies, and use cases. Configure NSX Advanced Load Balancer Discuss the IPSec VPN and L2 VPN function and use cases Configure IPSec VPN and L2 VPN using the NSX Manager UI NSX-T Data Center User and Role Management Describe the function and benefits of VMware Identity Manager? in NSX-T Data Center Integrate VMware Identity Manager with NSX-T Data Center Integrate LDAP with NSX-T Data Center Identify the various types of users, authentication policies, and permissions Use role-based access control to restrict user access NSX-T Data Center Federation Introduce the NSX-T Data Center Federation key concepts, terminology, and use-cases. Explain the onboarding process of NSX-T Data Center Federation Describe the NSX-T Data Center Federation switching and routing functions. Describe the NSX-T Data Center Federation security concepts.
![VMware NSX-T Data Center: Install, Configure, Manage [V3.2]](https://cademy-images-io.b-cdn.net/9dd9d42b-e7b9-4598-8d01-a30d0144ae51/4c81f130-71bf-4635-b7c6-375aff235529/original.png?width=3840)
Oracle 12c SQL Fundamentals
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The target audience for this textbook is all Oracle professionals, both business and systems professionals. Among the specific groups for whom this textbook will be helpful are: ? Business and non-IT professionals ? Application designers and database developers ? Business Intelligence (BI) analysts and consumers ? Database administrators ? Web server administrators Overview The first portion of this textbook considers the logical models upon which a relational database is based and the various configurations and environments in which you may work with the Oracle database. The next segment focuses on the actual SQL syntax for writing database queries. You will begin with the simplest of queries and then proceed onto moderately complex query scenarios. Finally, this textbook covers the DDL, DML and transaction control portions of the SQL language that allow one to create, maintain and manipulate application database objects and application data. This textbook takes a unique approach to SQL training in that it incorporates data modeling theory, relational database theory, graphical depictions of theoretical concepts and numerous examples of actual SQL syntax into one learning vehicle. Relational Databases & Data Models About Data Models About the Relational Model The Electronics Data Model About the Relational DBMS Selection & Setup of the Database Interface Considering Available Tools Selecting the Appropriate Tool Oracle Net Database Connections Oracle PAAS Database Connections Setup SQL Developer Setup SQL*Plus Setup Jdeveloper Using the Database Interface About Bind & Substitution Variables Using SQL Developer Using SQL*Plus Introduction to the SQL Language About the SQL Language Characteristics of SQL Introducing SQL Using Select SQL Rules The Select Statement The Select Statement Distinct/Unique Keyword Using Alias Names Restricting Results with the Where Clause About Logical Operators Equality Operator Boolean Operators REGEXP_LIKE() In Operator Sorting Data with the Order By Clause About the Order by Clause Multiple Column Sorts Specify the Sort Sequence About Null Values within Sorts Using Column Aliases Pseudo Columns, Functions & Top-N Queries Rowid Pseudo Column ORA_ROWSCN PSEUDO Column ROWNUM Pseudo Column About the Built-In Functions SYSDATE User & UID SESSIONTIMEZONE Function Using the Dual Table Row Limiting & Top-N Queries FETCH First x Rows Only Clause OFFSET x Rows Clause FETCH?PERCENT Clause The WITH TIES Option Joining Tables About Joins Inner Joins Reflexive Join Non-Key Join Outer Join Using the Set Operators About the Set Operators SQL Set Operator Examples UNION Example INTERECT Example MINUS Example UNION All Summary Functions Using Sub-Queries Finding Data with Sub-Queries Standard Sub-Queries Correlated Sub-Queries The EXISTS Operator Aggregating Data within Groups About Summary Groups Find Groups within the Tables Select Data From the Base Tables Select Groups from the Results Use DDL to Create & Manage Tables Create Table Statement Column Data Types Not Null Default Describe Alter Table Statement Drop Table Statement Table DDL Using SQL Developer Alter User Statement Alter Session Statement NLS_Language NLS_Date Use DML to Manipulate Data The Insert Statement The Delete Statement The Update Statement About Transactions Transaction Rollback Transaction Commit Transaction Savepoint The Set Transaction Statement Set Transaction Read Only Statement Rules Understanding the Data Models The Company Data Model The Electronics Data Model About the SQL-99 Standard SQL-92 & SQL-99 Cross Joins Natural Joins Inner Joins Implicit Inner Join Outer Joins Anti Joins Named Sub-Queries Enhancing Groups with Rollup & Cube Using Rollup The Grouping() Function Using Cube SQL Functions: Character Handling What are the SQL Functions? String Formatting Functions UPPER(), LOWER() Example INITCAP() Example Character Codes Functions CHR((), ASCII() Examples PAD & TRIM Functions RPAD() Example RTRIM() Example TRIM() Example String Manipulation Functions DECODE () Example SUBSTR() Example INSTR() Example TRANSLATE() Example REPLACE() Example String Comparison Functions LEAST() Example Phonetic Search Function SOUNDEX() Example SQL Functions: Numeric Handling About the Numeric Data Functions GREATEST() Example ABS() Example ROUND() Example TRUNC() Example SIGN() Example TO_NUMBER() Example & Data ype Conversions NULL VALUES FUNCTIONS NVL() & NVL2() Function NVL() Example (Character) NVL() Example (Numeric Loss of Data) NVL() Example (Numeric Output) NVL2() Example COALESCE() Function NULLIF() Function SQL Functions: Date Handling Date Formatting Functions TO_CHAR() & TO_DATE() Format Patterns TO_CHAR() Examples TO_DATE() Examples EXTRACT() Example Date Arithmetic Functions MONTHS_BETWEEN() Example ADD_MONTHS() Example LAST_DAY() Example NEXT_DAY() Example TRUNC(), ROUND() Dates Example NEW_ TIME() Example About V$TIMEZONE_NAMES CAST() FUNCTION & TIME ZONES Database Objects: About Database Objects About Database Objects About Schemas Making Object References Database Objects: Relational Views About Relations Views The Create View Statement Why Use Views? Accessing Views with DML Maintaining View Definitions Alter View Drop View DDL Using SQL Developer Database Objects: Indexes About Indexes Create & Drop Index Statements Indexes & Performance Data Dictionary Storage Database Objects: Creating Other Objects About Sequences Referencing NEXTVAL Referencing CURRVAL Within the DEFAULT Clause Alter Sequence & Drop Sequence ALTER SEQUENCE DROP SEQUENCE About Identity Columns CREATE TABLE?GENERATED AS IDENTITY ALTER TABLE?GENERATED AS IDENTITY Start With Limit Value ALTER TABLE...DROP IDENTITY About Synonyms CREATE & DROP SYNONYM Statements CREATE SYNONYM DROP SYNONYM Public Vs Private Synonyms CREATE SCHEMA AUTHORIZATION Database Objects: Object Management Using DDL The RENAME Statement TABLESPACE Placement CREATE TABLE?TABLESPACE The Comment Statement The TRUNCATE TABLE Statement Database Objects: Security About Object Security Grant Object Privileges Revoke Object Privileges Object Privileges & SQL Developer Data Integrity Using Constraints About Constraints NOT NULL Constraint NOT NULL Example CHECK Constraint UNIQUE Constraint PRIMARY KEY Constraint REFERENCES Constraint ON DELETE CASCADE Example ON DELETE SET NULL Example Constraints on Existing Tables Constraints & SQL Developer Managing Constraint Definitions RENAMING & DROPPING Constraints ENABLING & DISABLING Constraints DEFERRED Constraint Enforcement SET CONSTRAINTS Handling Constraint Exceptions Constraints with Views DATA Dictionary Storage The Data Dictionary Structure More About the Data Dictionary OBJECT-SPECIFIC Dictionary Views USER_UPDATABLE_COLUMNS The Dictionary Structure METADATA & SQL Developer Additional course details: Nexus Humans Oracle 12c SQL Fundamentals training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Oracle 12c SQL Fundamentals course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

MD-102T00 Microsoft 365 Endpoint Administrator
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Microsoft 365 Endpoint Administrator is responsible for deploying, configuring, securing, managing, and monitoring devices and client applications in a corporate setting. Their duties include managing identity, access, policies, updates, and apps. They work alongside the M365 Enterprise Administrator to develop and execute a device strategy that aligns with the requirements of a modern organization. Microsoft 365 Endpoint Administrators should be well-versed in M365 workloads and possess extensive skills and experience in deploying, configuring, and maintaining Windows 11 and later, as well as non-Windows devices. Their role emphasizes cloud services over on-premises management technologies. In this course, students will learn to plan and execute an endpoint deployment strategy using contemporary deployment techniques and implementing update strategies. The course introduces essential elements of modern management, co-management approaches, and Microsoft Intune integration. It covers app deployment, management of browser-based applications, and key security concepts such as authentication, identities, access, and compliance policies. Technologies like Microsoft Entra ID, Azure Information Protection, and Microsoft Defender for Endpoint are explored to protect devices and data. Prerequisites The Modern Desktop Administrator must be familiar with M365 workloads and must have strong skills and experience of deploying, configuring, and maintaining Windows 11 and later, and non-Windows devices. 1 - Explore the Enterprise Desktop Examine benefits of modern management Examine the enterprise desktop life-cycle model Examine planning and purchasing Examine desktop deployment Plan an application deployment Plan for upgrades and retirement 2 - Explore Windows Editions Examine Windows client editions and capabilities Select client edition Examine hardware requirements 3 - Understand Microsoft Entra ID Examine Microsoft Entra ID Compare Microsoft Entra ID and Active Directory Domain Services Examine Microsoft Entra ID as a directory service for cloud apps Compare Microsoft Entra ID P1 and P2 plans Examine Microsoft Entra Domain Services 4 - Manage Microsoft Entra identities Examine RBAC and user roles in Microsoft Entra ID Create and manage users in Microsoft Entra ID Create and manage groups in Microsoft Entra ID Manage Microsoft Entra objects with PowerShell Synchronize objects from AD DS to Microsoft Entra ID 5 - Manage device authentication Describe Microsoft Entra join Examine Microsoft Entra join prerequisites limitations and benefits Join devices to Microsoft Entra ID Manage devices joined to Microsoft Entra ID 6 - Enroll devices using Microsoft Configuration Manager Deploy the Microsoft Configuration Manager client Monitor the Microsoft Configuration Manager client Manage the Microsoft Configuration Manager client 7 - Enroll devices using Microsoft Intune Manage mobile devices with Intune Enable mobile device management Explain considerations for device enrollment Manage corporate enrollment policy Enroll Windows devices in Intune Enroll Android devices in Intune Enroll iOS devices in Intune Explore device enrollment manager Monitor device enrollment Manage devices remotely 8 - Execute device profiles Explore Intune device profiles Create device profiles Create a custom device profile 9 - Oversee device profiles Monitor device profiles in Intune Manage device sync in Intune Manage devices in Intune using scripts 10 - Maintain user profiles Examine user profile Explore user profile types Examine options for minimizing user profile size Deploy and configure folder redirection Sync user state with Enterprise State Roaming Configure Enterprise State Roaming in Azure 11 - Execute mobile application management Examine mobile application management Examine considerations for mobile application management Prepare line-of-business apps for app protection policies Implement mobile application management policies in Intune Manage mobile application management policies in Intune 12 - Deploy and update applications Deploy applications with Intune Add apps to Intune Manage Win32 apps with Intune Deploy applications with Configuration Manager Deploying applications with Group Policy Assign and publish software Explore Microsoft Store for Business Implement Microsoft Store Apps Update Microsoft Store Apps with Intune Assign apps to company employees 13 - Administer endpoint applications Manage apps with Intune Manage Apps on non-enrolled devices Deploy Microsoft 365 Apps with Intune Additional Microsoft 365 Apps Deployment Tools Configure Microsoft Edge Internet Explorer mode App Inventory Review 14 - Protect identities in Microsoft Entra ID Explore Windows Hello for Business Deploy Windows Hello Manage Windows Hello for Business Explore Microsoft Entra ID Protection Manage self-service password reset in Microsoft Entra ID Implement multi-factor authentication 15 - Enable organizational access Enable access to organization resources Explore VPN types and configuration Explore Always On VPN Deploy Always On VPN 16 - Implement device compliance Protect access to resources using Intune Explore device compliance policy Deploy a device compliance policy Explore conditional access Create conditional access policies 17 - Generate inventory and compliance reports Report enrolled devices inventory in Intune Monitor and report device compliance Build custom Intune inventory reports Access Intune using Microsoft Graph API 18 - Deploy device data protection Explore Windows Information Protection Plan Windows Information Protection Implement and use Windows Information Protection Explore Encrypting File System in Windows client Explore BitLocker 19 - Manage Microsoft Defender for Endpoint Explore Microsoft Defender for Endpoint Examine key capabilities of Microsoft Defender for Endpoint Explore Windows Defender Application Control and Device Guard Explore Microsoft Defender Application Guard Examine Windows Defender Exploit Guard Explore Windows Defender System Guard 20 - Manage Microsoft Defender in Windows client Explore Windows Security Center Explore Windows Defender Credential Guard Manage Microsoft Defender Antivirus Manage Windows Defender Firewall Explore Windows Defender Firewall with Advanced Security 21 - Manage Microsoft Defender for Cloud Apps Explore Microsoft Defender for Cloud Apps Planning Microsoft Defender for Cloud Apps Implement Microsoft Defender for Cloud Apps 22 - Assess deployment readiness Examine deployment guidelines Explore readiness tools Assess application compatibility Explore tools for application compatibility mitigation Prepare network and directory for deployment Plan a pilot 23 - Deploy using the Microsoft Deployment Toolkit Evaluate traditional deployment methods Set up the Microsoft Deployment Toolkit for client deployment Manage and deploy images using the Microsoft Deployment Toolkit 24 - Deploy using Microsoft Configuration Manager Explore client deployment using Configuration Manager Examine deployment components of Configuration Manager Manage client deployment using Configuration Manager Plan in-place upgrades using Configuration Manager 25 - Deploy Devices using Windows Autopilot Use Autopilot for modern deployment Examine requirements for Windows Autopilot Prepare device IDs for Autopilot Implement device registration and out-of-the-box customization Examine Autopilot scenarios Troubleshoot Windows Autopilot 26 - Implement dynamic deployment methods Examine subscription activation Deploy using provisioning packages Use Windows Configuration Designer Use Microsoft Entra join with automatic MDM enrollment 27 - Plan a transition to modern endpoint management Explore using co-management to transition to modern endpoint management Examine prerequisites for co-management Evaluate modern management considerations Evaluate upgrades and migrations in modern transitioning Migrate data when modern transitioning Migrate workloads when modern transitioning 28 - Manage Windows 365 Explore Windows 365 Configure Windows 365 Administer Windows 365 29 - Manage Azure Virtual Desktop Examine Azure Virtual Desktop Explore Azure Virtual Desktop Configure Azure Virtual Desktop Administer Azure Virtual Desktop Additional course details: Nexus Humans MD-102T00 : Microsoft 365 Endpoint Administrator training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the MD-102T00 : Microsoft 365 Endpoint Administrator course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Welcome to the workshop on Marketing Your Hypnotherapy Business, where we delve into essential strategies to elevate your professional presence and attract a steady flow of clients. Today, we focus on entrepreneurial skills and actionable marketing techniques to drive your business forward.
