- Professional Development
- Medicine & Nursing
- Arts & Crafts
- Health & Wellbeing
- Personal Development
GRE Preparation - Verbal and Analytical Writing
By NextGen Learning
GRE Preparation - Verbal and Analytical Writing Course Overview: This course is designed to help learners prepare effectively for the GRE Verbal and Analytical Writing sections. Focusing on the key skills required for success in these areas, it equips learners with proven strategies to excel. By covering all aspects of verbal reasoning, reading comprehension, text completions, sentence equivalence, and analytical writing, the course provides in-depth preparation that leads to improved performance. Learners will develop their ability to analyse complex texts, improve their vocabulary, and refine their writing skills, essential for achieving a competitive GRE score. Course Description: The GRE Preparation - Verbal and Analytical Writing course provides comprehensive coverage of the verbal reasoning and writing sections of the GRE. It includes lessons on reading comprehension, the six critical question types, pivotal words, sentence structure, and writing techniques. The course utilises a variety of methods to strengthen analytical thinking, reading skills, and writing proficiency. Learners will acquire the tools to tackle both the Verbal and Analytical Writing sections effectively. Through structured content and engaging exercises, this course builds confidence and prepares individuals for the GRE with focused skill-building and practice. GRE Preparation - Verbal and Analytical Writing Curriculum: Module 01: Verbal Section – Orientation Module 02: Reading Comprehension Introduction Module 03: The Six Questions Module 04: Pivotal Words Module 05: The Three-Step Method Module 06: Text Completions Module 07: Sentence Equivalence Module 08: Writing (See full curriculum) Who is this course for? Individuals seeking to enhance their GRE score Professionals aiming to pursue graduate studies Beginners with an interest in GRE preparation Anyone looking to strengthen their verbal and writing skills for graduate-level tests Career Path Graduate school applicants Research assistants Academic advisors Educational consultants Policy analysts

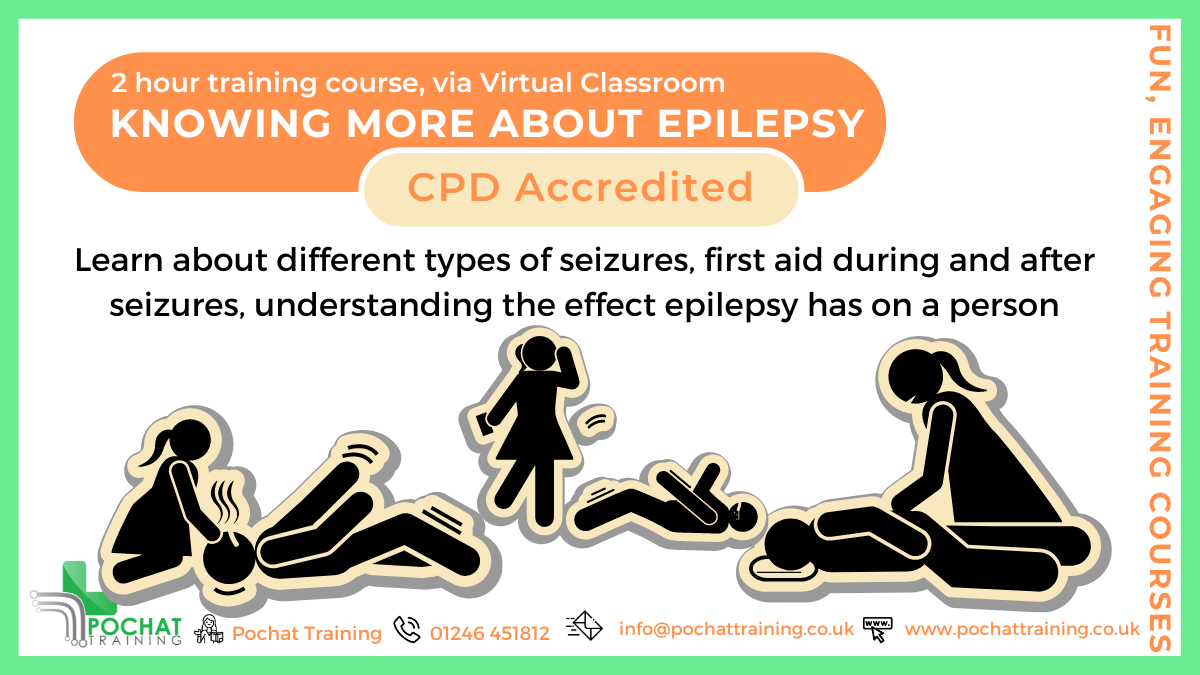
CPD Accredited, Interactive Short Course 2 hr session This training session gives a good introduction to epilepsy How can you best understand and help those affected with different types of seizures Great for those who have contact with people with epilepsy, such as family and friends, those working in education and afterschool clubs, sports and good CPD for nurses Course Contents: What is Epilepsy The different types of seizures Keeping someone safe while they're having a seizure Understand how having epilepsy affects someone's life Great for teachers and TAs in schools, for those working in care or community events, and those close to people with epilepsy Benefits of this Short Course: Epilepsy is one of the most common neurological conditions In the UK, there are over 600,000 people with a diagnosis of epilepsy That is about 1 in 103 people, or 1 child or young person in every 3 classrooms Every year, 1000 people in the UK die due to their epilepsy Help avoid unnecessary suffering or even death by knowing what to do to help while they're having an epileptic seizure, and keep them safe
Network virtualization training course description This course covers network virtualization. It has been designed to enable network engineers to recognise and handle the requirements of networking Virtual Machines. Both internal and external network virtualization is covered along with the technologies used to map overlay networks on to the physical infrastructure. Hands on sessions are used to reinforce the theory rather than teach specific manufacturer implementations. What will you learn Evaluate network virtualization implementations and technologies. Connect Virtual Machines with virtual switches. Explain how overlay networks operate. Describe the technologies in overlay networks. Network virtualization training course details Who will benefit: Engineers networking virtual machines. Prerequisites: Introduction to virtualization. Duration 2 days Network virtualization training course contents Virtualization review Hypervisors, VMs, containers, migration issues, Data Centre network design. TOR and spine switches. VM IP addressing and MAC addresses. Hands on VM network configuration Network virtualization What is network virtualization, internal virtual networks, external virtual networks. Wireless network virtualization: spectrum, infrastructure, air interface. Implementations: Open vSwitch, NSX, Cisco, others. Hands on VM communication over the network. Single host network virtualization NICs, vNICs, resource allocation, vSwitches, tables, packet walks. vRouters. Hands on vSwitch configuration, MAC and ARP tables. Container networks Single host, network modes: Bridge, host, container, none. Hands on Docker networking. Multi host network virtualization Access control, path isolation, controllers, overlay networks. L2 extensions. NSX manager. OpenStack neutron. Packet walks. Distributed logical firewalls. Load balancing. Hands on Creating, configuring and using a distributed vSwitch. Mapping virtual to physical networks VXLAN, VTEP, VXLAN encapsulation, controllers, multicasts and VXLAN. VRF lite, GRE, MPLS VPN, 802.1x. Hands on VXLAN configuration. Orchestration vCenter, vagrant, OpenStack, Kubernetes, scheduling, service discovery, load balancing, plugins, CNI, Kubernetes architecture. Hands on Kubernetes networking. Summary Performance, NFV, automation. Monitoring in virtual networks.

JIR - Junos Intermediate Routing
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for Network engineers, technical support personnel, reseller support engineers, and others responsible for implementing and/or maintaining the Juniper Networks products covered in this course. Overview Describe typical uses of static, aggregate, and generated routes. Configure and monitor static, aggregate, and generated routes. Explain the purpose of Martian routes and add new entries to the default list. This two-day course provides students with intermediate routing knowledge and configuration examples. The course includes an overview of protocol independent routing feature. Chapter 1: Course Introduction Course Introduction Chapter 2: Protocol-Independent Routing Static Routes Aggregated Routes Generated Routes Martian Addresses Routing Instances Chapter 3: Load Balancing and Filter-Based Forwarding Overview of Load Balancing Configuring and Monitoring Load Balancing Overview of Filter-Based Forwarding Configuring and Monitoring Filter-Based Forwarding Chapter 4: Open Shortest Path First Overview of OSPF Adjacency Formation and the Designated Router Election OSPF Scalability Configuring and Monitoring OSPF Basic OSPF Troubleshooting Chapter 5: Border Gateway Protocol Overview of BGP BGP Attributes IBGP Versus EBGP Configuring and Monitoring BGP Chapter 6: IP Tunneling Overview of IP Tunneling GRE and IP-IP Tunnels Implementing GRE and IP-IP Tunnels Chapter 7: High Availability Overview of High Availability Networks GR Graceful RE Switchover Nonstop Active Routing BFD VRRP Appendix A

Definitive VPNs training course description A hands on course covering VPNs from the basics of benefits and Internet vs. Intranet VPNs through to detailed analysis of the technologies involved in VPNs. All the major VPN protocols are covered including PPPoE, L2TP, SSL, IPsec and dynamic VPNs. MPLS L3 VPNs are also covered. What will you learn Describe what a VPN is and explain the difference between different VPN types. Recognise the design and implementation issues involved in implementing a VPN. Explain how the various technologies involved in a VPN work. Describe and implement: L2TP, IPsec, SSL, MPLS L3 VPNs. Evaluate VPN technologies. Definitive VPNs training course details Who will benefit: Network personnel. Prerequisites: IP Security foundation for engineers. Duration 3 days Definitive VPNs training course contents VPN overview What is a VPN? What is an IP VPN? VPNs vs. Private Data Networks, Internet VPNs, Intranet VPNs, Remote access VPNs, Site to site VPNs, VPN benefits and disadvantages. VPN Tunnelling VPN components, VPN tunnels, tunnel sources, tunnel end points, hardware based VPNs, Firewall based VPNs, software based VPNs, tunnelling topologies, tunnelling protocols, which tunnelling protocol should you use? requirements of tunnels. VPN security components Critical VPN security requirements, Encryption and authentication, Diffie Hellman, DES, 3DES, RSA, PKI, Ca server types, pre shared keys versus certificates, Enrolling with a CA, RADIUS in VPNs. PPP Encapsulation, operation, authentication. Hands on Setting up PPPoE and analysing PPP packets. PPTP Overview, Components, How it works, control and data connections, GRE. Hands on Building a PPTP VPN. L2TP Overview, components, how it works, security, packet authentication, L2TP/IPSec, L2TP/PPP, Layer 2 versus layer 3 tunnelling. Hands on Implementing a L2TP tunnel. IPSec AH, HMAC, ESP, transport and tunnel modes, Security Association, use of encryption and authentication algorithms, manual vs automated key exchange, NAT and other issues. Hands on Implementing an IPSec VPN. Intranet VPNs Headers, architecture, label switching, LDP, MPLS VPNs. VPN products and services PE and CPE, management, various VPN products. VPN issues and architectures VPN architectures: terminate VPN before/on/ after/in parallel with firewall, resilience issues, VRRP, performance issues, QoS and VPNs. documentation.

Digital Electronics Course Online
By Hi-Tech Training
This Digital Electronics Course is designed to give practical knowledge of the type of electronic circuitry used in a modern Computer System or in any type of Computer Controlled equipment such as Photocopiers, Cash Registers, Tablets, mobile phones and many other types of IT equipment. Digital Electronics involves the use of Silicon chips (Integrated Circuits). The internal structure of a computer is to a large extent comprised of Digital Electronic Circuits.
JL3V - Junos Layer 3 VPNs
By Nexus Human
Duration 3 Days 18 CPD hours This course is intended for This course benefits individuals responsible for configuring and monitoring devices running the Junos OS. Overview Describe the value of MPLS VPNs. Describe the differences between provider-provisioned VPNs and customer-provisioned VPNs. Describe the differences between Layer 2 VPNs and Layer 3 VPNs. List the provider-provisioned MPLS VPN features supported by the JUNOS software. Describe the roles of a CE device, PE router, and P router in a BGP Layer 3 VPN. Describe the format of the BGP routing information, including VPN-IPv4 addresses and route distinguishers. Describe the propagation of VPN routing information within an AS. List the BGP design constraints to enable Layer 3 VPNs within a provider network. Explain the operation of the Layer 3 VPN data plane within a provider network. Create a routing instance, assign interfaces to a routing instance, create routes in a routing instance, and import/export routes from a routing instance using route distinguishers/route targets. Describe the purpose of BGP extended communities, configure extended BGP extended communities, and use BGP extended communities. List the steps necessary for proper operation of a PE-CE dynamic routing protocol. List the troubleshooting and monitoring techniques for routing instances. Explain the difference between the bgp.l3vpn table and the inet.0 table of a routing instance. Monitor the operation of a CE-PE dynamic routing protocol. Explain the operation of a PE mulit-access interface in a Layer 3 VPN and list commands to modify that behavior. Describe ways to support communication between sites attached to a common PE router. Provision and troubleshoot hub-and-spoke Layer 3 VPNs, Describe the flow of control traffic and data traffic in a hub-and-spoke Layer 3 VPN. Describe QoS mechanisms available in L3VPNs. Configure L3VPN over GRE tunnels. Describe the RFC 4364 VPN options. Describe the carrier-of-carriers model. Configure the carrier-of-carriers and ''Option C'' configuration. Describe the flow of control and data traffic in a draft-rosen multicast VPN. Describe the configuration steps for establishing a draft-rosen multicast VPN. Monitor and verify the operation of draft-rosen multicast VPNs. Describe the flow of control traffic and data traffic in a next-generation multicast VPN. Describe the configuration steps for establishing a next-generation multicast VPN. Describe the configuration steps for establishing a next-generation multicast VPN. Monitor and verify the operation of next-generation multicast VPNs. This three-day course is designed to provide students with MPLS-based Layer 3 virtual private network (VPN) knowledge and configuration examples. Chapter 1: Course Introduction Course Introduction Chapter 2: MPLS VPNs MPLS VPNs Provider-Provisioned VPNs Chapter 3: Layer 3 VPNs Layer 3 VPN Terminology VPN-IPv4 Address Structure Operational Characteristics Chapter 4: Basic Layer 3 VPN Configuration Preliminary Steps PE Router Configuration Lab: Layer 3 VPN with Static and BGP Routing Chapter 5: Layer 3 VPN Scaling and Internet Access Scaling Layer 3 VPNs Public Internet Access Options Lab: LDP over RSVP Tunnels and Public Internet Access Chapter 6: Layer 3 VPNs ? Advanced Topics Exchanging Routes between Routing Instances Hub-and-Spoke Topologies Layer 3 VPN CoS Options Layer 3 VPN and GRE Tunneling Integration Layer 3 VPN and IPSec Integration Layer 3 VPN Egress Protection BGP prefix-independent convergence (PIC) edge for MPLS VPNs VRF Localization Provider Edge Link Protection Support for configuring more than 3 million L3VPN Labels Lab: GRE Tunneling Chapter 7: Interprovider Backbones for Layer 3 VPNs Hierarchical VPN Models Carrier-of-Carriers Model Option C Configuration Lab: Carrier of Carrier Layer 3 VPNs Chapter 8: Troubleshooting Layer 3 VPNs Working with Multiple Layers Troubleshooting Commands on a PE Device Multiaccess Interfaces in Layer 3 VPNs PE and CE-based Traceroutes Layer 3 VPN Monitoring Commands Lab: Troubleshooting Layer 3 VPNs Chapter 9: Draft Rosen Multicast VPNs Multicast Overview Draft Rosen MVPN Overvie Draft Rosen MVPN Operation Configuration Monitoring Chapter 10: Next Generation Multicast VPNs Multicast VPN Overview Next-Generation MVPN Operation Configuration Monitoring Internet Multicast Ingress Replication Internet Multicast Signaling and Data Plane Configuring MVPN Internet Multicast Monitoring MVPN Internet Multicast Lab: MVPN Internet Multicast

Catching the Wind
By SoulSpark Online
Training Trainers of Spiritual Directors Developing the abilities needed to facilitate Spiritual Direction formation programmes

Advanced Juniper Networks VPN Implementations
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This course is intended for network engineers, network support personnel, and reseller support. Overview After successfully completing this course, you should be able to:Configure LAN-to-LAN IP Security (IPsec) VPNs in various configurations. Configure VPN redundancy. Configure dynamic routing using IPsec VPNs. Configure remote access IPsec connectivity including group Internet Key Exchange (IKE) and shared IKE. Configure generic routing encapsulation (GRE) tunnels. This intermediate-level course focuses on the wide range of options available when configuring virtual private networks (VPNs) using Juniper Networks firewall/VPN products. Students attending the course will learn these various deployments through detailed lectures and hands-on lab exercises. Chapter 1: Course IntroductionChapter 2: ScreenOS VPN Basics Review VPN Review Verifying Operations VPN Monitor Lab: VPN Review Chapter 3: VPN Variations Dynamic Peers Transparent Mode Overlapping Addresses Lab: VPN Variations Chapter 4: Hub-and-Spoke VPNs Concepts Policy-Based Hub-and-Spoke VPNs Route-Based Hub-and-Spoke VPNs with No Policy and NHTB Route-Based Hub-and_Spoke VPNS with Policy Centralized Control Hub-and-Spoke VPNs ACVPNs Lab: Hub-and-Spoke VPNs Chapter 5: Routing over VPNs Routing Overview Configuring RIP Configuring OSPF Case Studies Lab: Dynamic Routing Chapter 6: Using Certificates Concepts and Terminology Configuring Certificates and Certificate Support Configuring VPNs with Certificates Lab: Using Certificates Chapter 7: Redundant VPN Gateways (Optional) Redundant VPN Gateways Other Options Demonstration: Redundant VPN Gateways Chapter 8: Generic Routing Encapsulation (Optional) Configuring GRE Chapter 9: Dial-Up IPsec VPNs (Optional) Basic Dial-Up Configuration Group IKE ID XAUTH and Shared IKE ID Additional course details: Nexus Humans Advanced Juniper Networks VPN Implementations training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the Advanced Juniper Networks VPN Implementations course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Mastering Speed Up Math Technique
By Course Cloud
Having trouble with your maths techniques? Enrol in this course today and learn to speed up your mental calculation ability. Quicken the calculation power of your brain with these easy techniques. The Mastering Speed Up Math Technique will brush up your maths skills and enhance your brain ability to work with mathematical operators. You will be able to perform multiplications between four-digit numbers within seconds. You will be able to work fluently with operators like division, squares and decimal systems. So if you are looking to appear GRE, GMAT, Banking or University exams then this Mastering Speed Up Math Technique course will come in very handy for you. You will find the mathematical problems easier. You can also enrol in the course if you are just looking to increase the ability of your brain's working capacity in general. Learning Maths is great fun. You will feel more motivated. When you perform calculations with the techniques to perform maths orally, it will generate positive waves inside you, giving you inner peace and eradicating your fear of maths. Building your confidence in working with numbers improves the reactive ability of the brain and improves concentration, making you many times faster. Upon completion of this CPD accredited course, you will be awarded a certificate of completion, as proof of your expertise in this field, and you can show off your certificate in your LinkedIn profile and in your resume to impress employers and boost your career. So, if you are looking to gain expertise in maths the skills will help you in every sphere of your life. Because Maths is everywhere. Our Mastering Speed Up Math Technique is packed with 58 modules and takes 7 hours, 17 minutes to study. You will be able to study this course at your own pace, from anywhere and at any time. Enrol today and see the wonders it does your maths skills
